Abstract
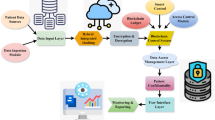
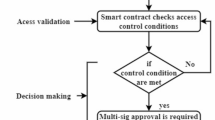
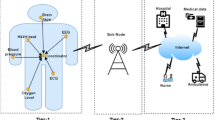
The rapid digitisation of healthcare services presents challenges in guaranteeing safe, scalable, and privacy-preserving access to sensitive medical information. This article presents BBAS, a blockchain-based authentication system for e-Health. BBAS incorporates a multi-factor authentication (MFA) framework that includes password hashing, one-time passwords (OTP), and biometric verification, with a hybrid access control model that combines role-based access control (RBAC) and attribute-based access control (ABAC). To guarantee enduring security, BBAS utilises post-quantum digital signatures (CRYSTALS-Dilithium) and exploits the InterPlanetary file system (IPFS) for off-chain data storage, assuring tamper-resistance and scalability. We implemented the system using solidity smart contracts on a permissioned Ethereum network and assessed via 500 authentication iterations. Results show BBAS outperforms benchmark models across all critical metrics: authentication success rate (ASR: 98.6%), latency (0.05 s), throughput (19,000 req/s), gas cost (35,000 gas/req), block confirmation time (10 s), and storage overhead (0.03 KB/record). Biometric error rates—false acceptance rate (FAR: 0.5%), false rejection rate (FRR: 1.2%), and equal error rate (EER: 0.85%)—are markedly decreased, therefore improving both security and usability. This research validates BBAS as a reliable, scalable, and quantum-resistant authentication framework for contemporary e-Health systems.
Similar content being viewed by others
Data availability
Data sets generated during the current study are available from the corresponding author on reasonable request.
References
Ayesha, N., Mujahid, M., Mirdad, A. R., Alamri, F. S. & Khan, A. R. Large Language model in healthcare for the prediction of genetic variants from unstructured text medicine data using natural Language processing. Computers Mater. Continua. 84 (1), 1883–1899. https://doi.org/10.32604/cmc.2025.063560 (2025).
Hemdan, E. E. D., Sayed, A. & Innovations, F. Smart and Secure Healthcare with Digital Twins: A Deep Dive into Blockchain, Federated Learning, and Algorithms18 (7), p. 401 https://doi.org/10.3390/a18070401 (2025).
Zamil, M. G. H. I. A. L. & Samarah, S. M. Privacy preserving activity recognition framework for high performance smart systems, Clust. Comput.,28 (6), 10.1007/s10586-025-05112-7.b Model for E-Health Users, Information (Switzerland). https://doi.org/10.3390/info16030219 (2025).
Model for E-Health Users. Information (Switzerland) 16 (3) https://doi.org/10.3390/info16030219 (2025).
Pokharel, B. P., Kshetri, N., Sharma, S. R. & Paudel, S. BlockHealthSecure: integrating blockchain and cybersecurity in Post-Pandemic healthcare systems. Inform. (Switzerland). https://doi.org/10.3390/info16020133 (2025).
Rani, D., Kumar, R. & Chauhan, N. A secure framework for IoT -based healthcare using blockchain and IPFS. Secur. Priv. https://doi.org/10.1002/spy2.348 (2024).
Abutaleb, R. A., Alqahtany, S. S. & Syed, T. A. Integrity and Privacy-Aware, Patient-Centric health record access control framework using a blockchain. Appl. Sci. (Switzerland). https://doi.org/10.3390/app13021028 (2023).
Kumar, P. et al. A blockchain-orchestrated deep learning approach for secure data transmission in IoT-enabled healthcare system. J. Parallel Distrib. Comput. https://doi.org/10.1016/j.jpdc.2022.10.002 (2023).
Nowrozy, R., Security, A. & privacy compliant data sharing solution for healthcare data ecosystems and, Victoria University. (accessed 24 June 2025); https://vuir.vu.edu.au/id/eprint/48047 (2024).
Maranco, M., Logeshwari, R., Sivakumar, M. & Manikandan, V. Improvised multi-factor authentication for end-user security in cyber physical system. Int. J. Intell. Syst. Applic. Eng. 12 15s, (2024).
Saha, S., Nova, S. N. & Iqbal, M. I. Healthcare professionals credential verification model using Blockchain-Based Self-sovereign identity. Lecture Notes Networks Syst. https://doi.org/10.1007/978-981-19-9483-8_32 (2023).
Ul Haq, M. et al. A comprehensive review of face detection/recognition algorithms and competitive datasets to optimize machine vision. https://doi.org/10.32604/cmc.2025.063341 (Tech Science Press, 2025).
Nasr, M. A. et al. A comprehensive survey of audio forgery detection: challenges and novel trends. J. Electr. Syst. Inform. Technol. 12 (1), 30. https://doi.org/10.1186/s43067-025-00225-w (2025).
Gharavi, H., Granjal, J. & Monteiro, E. Post-Quantum blockchain security for the internet of things: survey and research directions. IEEE Commun. Surv. Tutorials. https://doi.org/10.1109/COMST.2024.3355222 (2024).
Singh, M. K., Kumar Pippal, S. & Sharma, V. A Blockchain-IPFS framework for Secure, Scalable, and interoperable healthcare data management. SN Comput. Sci. https://doi.org/10.1007/s42979-025-03936-z (2025).
Dewangan, N. K. & Chandrakar, P. TreatChain: A patient-centric treatment cycle blockchain using proof-of-upload consensus. Peer Peer Netw. Appl. https://doi.org/10.1007/s12083-025-01984-z (2025).
Karthikeyan, V., Kirubakaran, G., Gopalakrishnan, K. & Sridhar Raj, S. Creative strategies to protect patients’ health records and confidentiality using blockchain technology. In Blockchain-Enabled Solutions for the Pharmaceutical Industry. https://doi.org/10.1002/9781394287970.ch14 (Wiley, 2024).
Haritha, T. & Anitha, A. Multi-Level security in healthcare by integrating Lattice-Based access control and Blockchain- based smart contracts system. IEEE Access. 11, 114322–114340. https://doi.org/10.1109/ACCESS.2023.3324740 (2023).
Pujari, C. et al. Identity resilience in the digital health ecosystem: A key recovery-enabled framework. Comput. Biol. Med. https://doi.org/10.1016/j.compbiomed.2023.107702 (2023).
Miao, J., Wang, Z., Wu, Z., Ning, X. & Tiwari, P. A blockchain-enabled privacy-preserving authentication management protocol for internet of medical things. Expert Syst. Appl. https://doi.org/10.1016/j.eswa.2023.121329 (2024).
Kormiltsyn, A., Iqbal, M., Dwivedi, V., Norta, A. & Matulevicius, R. Ontology of Blockchain-based Multi-Factor challenge set Self-Sovereign identity authentication. SSRN https://doi.org/10.2139/ssrn.5274964 (2025).
Mansoor, K. et al. PQCAIE: Post quantum cryptographic authentication scheme for IoT-based e-health systems. Internet Things (Netherlands) https://doi.org/10.1016/j.iot.2024.101228 (2024).
Abid, A., Cheikhrouhou, S., Kallel, S., Tari, Z. & Jmaiel, M. A smart contract-based access control framework for smart healthcare systems. Comput. J. https://doi.org/10.1093/comjnl/bxac183 (2024).
Azeri, N., Hioual, O. & Hioual, O. A distributed intelligence framework for enhancing resilience and data privacy in dynamic cyber-physical systems. Cluster Comput. https://doi.org/10.1007/s10586-024-04349-y (2024).
Padma, A. & Ramaiah, M. Blockchain based an efficient and secure privacy preserved framework for smart cities. IEEE Access. https://doi.org/10.1109/ACCESS.2024.3364078 (2024).
Padma, A. & Ramaiah, M. GLSBIoT: GWO-based enhancement for lightweight scalable blockchain for IoT with trust based consensus. Future Generation Comput. Syst. https://doi.org/10.1016/j.future.2024.05.008 (2024).
Padma, A. & Ramaiah, M. Lightweight privacy preservation blockchain framework for healthcare applications using GM-SSO. Results Eng. https://doi.org/10.1016/j.rineng.2024.103882 (2025).
Padma, A., Ramaiah, M. & Ravi, V. A comprehensive review of lightweight blockchain practices for smart cities: a security and efficacy assessment. https://doi.org/10.1007/s40860-025-00254-2 (2025).
Kumar, N. & Ali, R. Biometric and smart contract enabled secure data sharing in drone-assisted battlefield systems. Comput. Electr. Eng. https://doi.org/10.1016/j.compeleceng.2025.110407 (2025).
Kumar, N. & Ali, R. A smart contract-based robotic surgery authentication system for healthcare using 6G-Tactile internet. Comput. Netw. https://doi.org/10.1016/j.comnet.2023.110133 (2024).
Kumar, N. & Ali, R. Blockchain-enabled authentication framework for maritime transportation system empowered by 6G-IoT. Comput. Netw. https://doi.org/10.1016/j.comnet.2024.110353 (2024).
Kumar, N. & Ali, R. A smart contract-based 6G-enabled authentication scheme for Securing internet of nano medical things network. Ad Hoc Netw. https://doi.org/10.1016/j.adhoc.2024.103606 (2024).
Kumar, N. & Ali, R. A consortium blockchain-edge enabled authentication scheme for underwater acoustic network (UAN). Internet Things (The Netherlands). https://doi.org/10.1016/j.iot.2024.101426 (2024).
Prajapat, S., Kumar, N., Das, A. K., Kumar, P. & Ali, R. Quantum-safe blockchain-assisted data encryption protocol for internet of things networks. Cluster Comput. https://doi.org/10.1007/s10586-024-04688-w (2025).
Kumar, N. & Ali, R. Smart-FIoT: A smart contract based efficient authentication framework for forensics IoT. Cluster Comput. https://doi.org/10.1007/s10586-025-05649-7 (2025).
Al-Zubaidie, M. & Jebbar, W. A. Blockchain-Powered dynamic segmentation in personal health record. Mesopotamian J. Cybersecur. 5 (3), 953–976. https://doi.org/10.58496/MJCS/2025/054 (2025).
Tregi, T. G. & Al-Zubaidie, M. Enhancing traffic data security in smart cities using optimized Quantum-Based digital signatures and Privacy-Preserving techniques. Mesopotamian J. Cybersecur. 5 (1), 256–272. https://doi.org/10.58496/MJCS/2025/017 (2025).
Razzaq, R. H., Al-Zubaidie, M. & Atiyah, R. G. Intermediary decentralized computing and private blockchain mechanisms for privacy preservation in the internet of medical things. Mesopotamian J. Cybersecur. 4 (3), 152–165. https://doi.org/10.58496/MJCS/2024/020 (2024).
Jebbar, W. A. & Al-Zubaidie, M. Transaction-Based blockchain systems security improvement employing Micro-Segmentation controlled by smart contracts and detection of saddle goatfish. SN Comput. Sci. https://doi.org/10.1007/s42979-024-03239-9 (2024).
Luu, L., Chu, D. H., Olickel, H., Saxena, P. & Hobor, A. Mak. Smart Contracts Smarter. https://doi.org/10.1145/2976749.2978309. (2016).
Dóka, J. et al. Enablers of low-latency immersive interaction in future remote-rendered mixed reality applications. MMSys - Proceedings of the 16th ACM Multimedia Systems Conference Association for Computing Machinery, Inc pp. 170–180. https://doi.org/10.1145/3712676.3714448 (2025).
Albana’a, R. M. & Alsohybe, N. T. Optimizing latency for augmented reality applications via mobile edge computing. In 1st International Conference on Emerging Technologies for Dependable Internet of Things, ICETI 2024 , Institute of Electrical and Electronics Engineers Inc., https://doi.org/10.1109/ICETI63946.2024.10777191 (2024).
Tanveer, M., Chelloug, S. A., Alabdulhafith, M. & El-Latif, A. A. A. Lightweight authentication protocol for connected medical IoT through privacy-preserving access. Egypt. Inf. J. https://doi.org/10.1016/j.eij.2024.100474 (2024).
Hossam Eldein Mohamed, F. A. & El-Shafai, W. Cancelable biometric authentication system based on hyperchaotic technique and fibonacci Q-Matrix. Multimed Tools Appl. https://doi.org/10.1007/s11042-023-17855-9 (2024).
Assaqty, M. I. S. et al. SPUFChain: permissioned blockchain lightweight authentication scheme for supply chain management using PUF of IoT. IEEE Access. 13, 88662–88682. https://doi.org/10.1109/ACCESS.2025.3566478 (2025).
Farouk, G. & Alsamara, T. Legal view on blockchain technologies in healthcare: A European States case study. Int. J. Sociotechnology Knowl. Dev. https://doi.org/10.4018/IJSKD.333154 (2023).
Acknowledgements
The author would like to acknowledge the support of Prince Sultan University in paying the Article Processing Charges (APC) for this publication.
Funding
This work was supported and funded by the Deanship of Scientific Research at Imam Mohammad Ibn Saud Islamic University (IMSIU) (grant number IMSIU-DDRSP2603).
Author information
Authors and Affiliations
Contributions
**Rabia Latif: ** Conceptualization, Methodology, Software, Writing—Original draft preparation, Project administration, Funding acquisition, Resources.- **Bello Musa Yakubu** : Methodology, Data curation, Formal analysis, Writing—Original draft preparation, Project administration, Funding acquisition, Validation.- **Nor Shahida Mohd Jamail** : Visualization, Investigation, Resources, Supervision, Funding acquisition, Writing—Reviewing and Editing.- **Amir Mohamed Talib: ** Investigation, Resources, Formal analysis, Writing—Reviewing and Editing.- **Fahad Omar Alomary: ** Investigation, Resources, Formal analysis, Writing—Reviewing and Editing.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Latif, R., Yakubu, B.M., Jamail, N.S.M. et al. BBAS: A blockchain-based authentication system for e-health with multi-factor authentication, access control, and post-quantum security. Sci Rep (2026). https://doi.org/10.1038/s41598-026-39415-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-026-39415-5