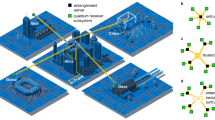
Abstract
Rapidly and randomly drifted reference frames will shorten the transmission distance and decrease the secure key rate of realistic quantum key distribution (QKD) systems. In this article, we present a free-running reference-frame-independent (RFI) QKD scheme, where measurement events are classified into multiple slices with similar estimated classification parameter. We perform the free-running RFI QKD experiment with a fiber link of 100 km and reference frame misalignment more than 29 periods in 50.7 h. A key rate as high as 742.98 bps is achieved at the total loss of 31.5 dB benefiting from both the new protocol design and the 80 MHz repetition rate system in use. Our system runs 50.7 h freely without any reference frame alignment. In the experiment, the misalignment variation rate tolerance of the experiment is 0.262 rad/s, and could be optimized to 1.309 rad/s. Therefore, our free-running RFI scheme can be efficiently adapted into the satellite-to-ground and drone-based mobile communication scenarios.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD) has the potential to generate the information-theoretical-secure keys between distant users (Alice and Bob)1,2,3. Since the first BB84 protocol proposed4, QKD has stepped into realistic applications from the laboratory5,6,7,8,9,10,11. The communication distance of QKD over different communication scenarios is significantly improved, such as 509, 511, 830 km with fiber link12,13,14, 4600 km space-to-ground communication network15, 1120 km space-to-ground entanglement distribution16, 1 km optical-relayed entanglement distribution over drones17.
In general, the realistic QKD systems have a common need of establishing a shared reference frame between distant users by characterizing and calibrating the polarization or phase of photons. Nevertheless, an actively or inappropriately implemented calibration scheme may increase the complexity of the systems and may open an unpredictable security loophole18,19.
Reference-frame-independent (RFI) QKD protocol, proposed in 2010, is robust for slowly varying reference frames and suitable to the satellite-to-ground and drone-based systems20,21. The secure key rate of RFI QKD systems varies a lot with given misalignment (θ0) of reference frames22. Furthermore, Wang et al. show that the valid condition of RFI-QKD is the misalignment variation Δθ ≤ π23. With the assumption of Δθ ≈ 0, the fiber link distance of RFI QKD reaches 300 km implemented with measurement-device-independent scheme11,24,25,26,27,28, and the free space RFI QKD experiment was demonstrated with a total loss of 38.0 dB9. However, the misalignment of reference frames in realistic RFI QKD scenarios varies randomly, the key accumulation time is limited by the upper bound of the variation, and the communication distance will be reduced heavily. W. Liang et al. performed a proof-of-principle experiment of RFI QKD with random θ0 in a slowly varying phase environment, nevertheless, the communication distance was limited to 65 km when considering the statistical fluctuations29,30.
In this article, we proposed a free-running RFI QKD scheme that can be adapted to the long-distance QKD systems with randomly and rapidly varying misalignment of reference frames. In our free-running RFI QKD scheme, the misalignment variation rate tolerance of the reference frame is highly enhanced, and the physical communication procedure is free-running without the limitation of Δθ ≤ π. We implemented a free-running RFI QKD experiment over 100 km fiber link with a total loss of 31.5 dB and system repetition rate of 80 MHz. The experiment is implemented with phase encoding, while our free-running RFI QKD scheme is not limited to the phase encoding. In the experiment, time-bin encoded photons in Z basis are used for generating secure keys and the phase-encoded photons in the X (Y) basis are used for quantifying the characteristics of the quantum link. The experiment ran for 50.7 h and the misalignment of reference frame between Alice and Bob varied for more than 29 periods. The secure key rate of our implementation reaches about 742.98 bps, which achieves the state-of-art performance of the long-distance RFI QKD systems.
Results
Model of free-running RFI QKD
The schematic diagram of our free-running RFI QKD scheme is shown in Fig. 1. The scheme mainly contains four phases: physical communication, data classification, secure key length estimation, and post-processing. In the physical communication phase, the communication parties (Alice and Bob) prepare and measure the quantum state as same as the original RFI scheme, and generate the raw data. Especially, the physical communication is free-running without considering the misalignment variation (Δθ < π in the original RFI schemes) of the reference frames. Then, the sifted data s0, s1, … , sn−1 of n intervals are generated after the basis/key sifting and quantum bit error rate (QBER) calculation procedures. Afterwards, each interval sifted data is split into m datasets according to the estimated classification parameter in the data classification phase. In the secure key length estimation phase, the leakage information and the single photon number of each dataset are calculated according to the decoy-state RFI analysis, and the secure key length L is estimated. Finally, the secure key K is generated in the post-processing phase.
The scheme mainly contains four phases: physical communication, data classification, secure key length estimation and post-processing. Alice (Bob) prepares (measures) the quantum state, and generates raw data. Then, n interval sifted data s0, s1, … , sn−1 are generated in the basis/sifting and quantum bit error rate (QBER) calculation procedure. Afterwards, s0, s1, … , sn−1 are classified into m datasets \(({{{{\mathscr{D}}}}}_{0},{{{{\mathscr{D}}}}}_{1},\ldots \,,{{{{\mathscr{D}}}}}_{m-1})\) according to the estimated classification parameter. The final secure key length is estimated based on the classified datasets \(({{{{\mathscr{D}}}}}_{0},{{{{\mathscr{D}}}}}_{1},\ldots \,,{{{{\mathscr{D}}}}}_{m-1})\). (ρ0, ρ1, … , ρn−1) represent the classification parameter of n interval sifted data. m and \({\rho }^{\prime}\) are used to split [0, 2π) as m slices: P0, P1, … , Pm−1.
In the free-running RFI QKD scheme, three encoding bases (X, Y, Z) are used and the reference frames of the bases are defined as
where θ is the misalignment angle of reference frames between Alice and Bob.
Alice randomly prepares the pulses with the bit s, the basis α and the intensity of k, where s ∈ {0, 1}, α ∈ {X, Y, Z} and k ∈ {μ, ν, 0} is the mean photon number of signal, decoy, and vacuum states. Bob randomly measures the received photons in the X, Y, and Z basis.
After repeating the preparation and measurement for Nt times, Alice and Bob acquire the raw data which contains n interval raw data of the interval time T.
Assume \({E}_{k}^{\alpha \beta }\) and \({N}_{k}^{\alpha \beta }\) represent the QBER and measured event number respectively, where k ∈ {μ, ν, 0}, α is the preparation basis, β is the measurement basis.
The key/basis sifting are conducted on the measured events of each interval with the basis of αβ and the measured event numbers \({N}_{k}^{\alpha \beta }\) of each interval are also calculated, where αβ ∈ {ZZ, XX, XY, YY, YX}. Meanwhile, the QBERs \({E}_{k}^{\alpha \beta },{E}_{l}^{ZZ}\) are calculated by exposing the corresponding quantum bits, k ∈ {μ, ν, 0}, l ∈ {ν, 0}, α, β ∈ {X, Y}. Meanwhile, the sifted keys Ks are generated from the quantum bits of the signal state on Z basis.
Here, the interval sifted data s0, s1, … , sn−1 are generated, each sifted data si contains the QBERs \({E}_{k}^{\alpha \beta },{E}_{l}^{ZZ}\), the measured event number \({N}_{k}^{\alpha \beta },{N}_{k}^{ZZ}\) and the sifted key of interval i, i = 0, 1, … , n − 1. Afterwards, s0, s1, … , sn−1 are classified into m datasets \({{{{\mathscr{D}}}}}_{0},{{{{\mathscr{D}}}}}_{1},\ldots \,,{{{{\mathscr{D}}}}}_{m-1}\) according to the estimated classification parameter, which is described in subsection “Data classification” in detail.
The sifted keys in the dataset \({{{{\mathscr{D}}}}}_{i}\) are merged to \({K}_{s}^{i}\), i = 0, 1, … , m − 1. The error estimation and error correction are conducted on \({K}_{s}^{0},{K}_{s}^{1},\ldots \,,{K}_{s}^{m-1}\) to gain the corrected keys \({K}_{{{{\rm{EC}}}}}^{0},{K}_{{{{\rm{EC}}}}}^{1},\ldots \,,{K}_{{{{\rm{EC}}}}}^{m-1}\), respectively. By comparing the corrected keys with the sifted keys, the QBERs of sifted keys are calculated, which is the QBER \({E}_{\mu ,i}^{ZZ}\) of the signal state on Z basis.
Afterwards, the bits in the corrected keys \({K}_{{{{\rm{EC}}}}}^{0},{K}_{{{{\rm{EC}}}}}^{1},\ldots \,,{K}_{{{{\rm{EC}}}}}^{m-1}\) are rearranged according the measurement order and merged as KEC. Finally, the privacy amplification is conducted on the corrected key KEC to generate the secure key K with the length L, which is described in subsection “Secure key length estimation and noise tolerance analysis”.
Data classification
After the key/basis sifting and the QBER calculation procedures, the interval sifted data is generated, which contains QBERs \({E}_{\mu }^{\alpha \beta }\) and \({E}_{\nu }^{\alpha \beta }\), α, β ∈ {X, Y}. According to the decoy-state practical RFI QKD protocol with weak coherent sources24, the QBER of X and Y bases varies approximately in a cosine curve when the misalignment θ changes. The QBER can be used to classify the generated interval sifted data into the datasets with the similar misalignment angles, but the classification interval is nonlinear and difficult to understand. Thus, we defined a classification parameter ρ ∈ [0, 2π) which is calculated according to the mapping from misalignment θ to QBER. The classification parameter is only used to classify the interval sifted data and cannot accurately characterize the misalignment of reference frames. The detailed description of the classification parameter is in Supplementary Note 1.
Then, the classification parameter ρ of the sifted data in each interval is calculated from the measured QBER as
where \(H({\widehat{E}}_{\mu }^{XX})\) and \({\widehat{E}}_{\mu }^{XX}\) are calculated as
dc is the dark count of detectors and es is the optical system error.
Especially, when \(\eta \mu (1-\cos \rho )/2\ll 1\), \(\eta \mu (1+\cos \rho )/2\ll 1\) and dc ≪ ημ, the ρ can also be calculated as
The detailed calculation is shown in Supplementary Note 1.
Meanwhile, we split the classification parameter \(\rho \in \left[0,2\pi \right)\) into m slices as
where i = 0, 1, …, m − 1, \({\rho }^{\prime}\) is constant and could be optimized to achieve the highest secure key rate.
The classification parameter ρ0, ρ1, … , ρn−1 of s0, s1, … , sn−1 are calculated, respectively. Afterwards, the measured data could be classified into m datasets \(\{{{{{\mathscr{D}}}}}_{0},{{{{\mathscr{D}}}}}_{1},\ldots \,,{{{{\mathscr{D}}}}}_{m-1}\}\) when the interval sifted data corresponding to the Pi are classified to the dataset \({{{{\mathscr{D}}}}}_{i}\).
Secure key length estimation and noise tolerance analysis
Assume the eαβ is the QBER of single-photons with preparation basis α and measurement basis β, \({N}_{1}^{Z}\) is the single photon number of Z basis.
After classifying the measured data into m datasets, each with similar classification angle, QBER \({E}_{k,i}^{\alpha \beta }\) and \({E}_{l,i}^{ZZ}\) of \({{{{\mathscr{D}}}}}_{i}\) are calculated from the measured event number and the QBERs of the composed interval sifted data, k ∈ {μ, ν, 0}, l ∈ {ν, 0}, α, β ∈ {X, Y}, i = 0, 1, … , m − 1. Meanwhile, the measured event number \({N}_{k,i}^{\alpha \beta }\) and \({N}_{l,i}^{ZZ}\) of \({{{{\mathscr{D}}}}}_{i}\) are also determined. The QBER \({E}_{\mu ,i}^{ZZ}\) and measured photons \({N}_{\mu ,i}^{ZZ}\) of dataset \({{{{\mathscr{D}}}}}_{i}\) are determined in the error estimation and error correction procedure. The \({e}_{\alpha \beta }^{i}\) and \({N}_{1,i}^{Z}\) of each dataset can be calculated according to the decoy-state protocol and statistical fluctuations analysis5.
Based on the RFI protocol20,31, we estimate the leakage information \({I}_{E}^{i}\) of each dataset as
where \({v}_{\max }\) and \(g({v}_{\max })\) are calculated as
The quantum channel quality C is estimated from the X, Y basis as
Then, the upper (lower) bounds of \({e}_{\alpha \beta }^{i}\), \({N}_{1,i}^{Z}\), and \({I}_{E}^{i}\) are estimated by considering the statistical fluctuation5,32. The superscript ‘+’ (‘−’) are used to represent the upper (lower) bound of the variable.
Finally, the secure key length L is calculated as
Li is the secure key length of dataset \({{{{\mathscr{D}}}}}_{i}\) and is estimated as
\({\lambda }_{{{{\rm{IR}}}}}^{i}\) is the leakage information bits of dataset \({{{{\mathscr{D}}}}}_{i}\) in the information reconciliation procedure and equals to
where f(x) is the reconciliation efficiency corresponding to QBER x.
Additionally, the secure key rate is calculated as
where ti is the enduring time of dataset \({{{{\mathscr{D}}}}}_{i}\).
Assume εPA is the failure probability of privacy amplification, εEC is the failure probability of information reconciliation and \(\overline{\varepsilon }\) measures the accuracy of estimating the smooth min-entropy.
Considering the finite-key analysis30, the secure key length LFK of our free-running RFI scheme is recalculated as
where σi = 0 (1) represents dataset \({{{{\mathscr{D}}}}}_{i}\) is (not) empty, \({N}_{i}^{ZZ}\) represents the measurement events number of Z basis in dataset \({{{{\mathscr{D}}}}}_{i}\), and Ni is the total measurement events number in dataset \({{{{\mathscr{D}}}}}_{i}\).
Furthermore, the secure key rate RFK with the finite-key analysis is calculated as
In our free-running RFI scheme, the misalignment variation Δθ of each dataset has the upper bound as
where ω is the experimental noise (variation rate of reference frames). Meanwhile, the variation Δθ and the interval T have the constraint conditions23 as
We set the standard deviation of the error rate estimation as 0.01 with the confidence level higher than 95.45%. Thus, the \({N}_{\min }\) should be larger than 2.5 × 103. The calculation procedure is described in Supplementary Note 2.
Thus, our free-running RFI scheme is valid as long as the experimental noise ω satisfies
In the experiment, photons encoded in Z basis are sent with the probability of 50%, photons encoded in X and Y basis are sent with the probability of 25%. The signal, decoy, and vacuum states are sent with the probability of 50, 40, and 10%, respectively. The mean photon number of the signal and decoy states are 0.722 and 0.104. The experiment has run free-running for about 50.7 h. The interval time T is set to 5 s. The information reconciliation efficiency is set to 1.1633.
Experimental QBERs, count rates, and secure key rates
Figure 2 shows the QBER of signal and decoy states for each basis and the count rate of Z basis. The QBER of the X, Y basis varied periodically with the time due to the environmental noise which affects the phase of the two interferometers, while the QBER of the Z basis maintained stable with small fluctuations. The intrinsic error of the optical system es is estimated as about 0.4% according to the upper (lower) bound of error rate on X, Y basis. The average QBER of the signal state on the Z basis is about 0.6%. The fluctuations in Z basis are caused by the active compensation, in which the intensity of signal quantum is monitored and the control signal of the intensity modulator IM2 (shown in section “Methods”) is adjusted when the misalignment of Z basis is out of the preset interval. The upper bound of the misalignment error on Z basis is set as 0.7%. Meanwhile, the jitters of the statistics might activate the feedback program even when \({E}_{\mu }^{ZZ}\) is smaller than 0.7%. And the small jitters of \({E}_{\mu }^{ZZ}\) causes the huge variation of error rate on decoy state, so that \({E}_{\nu }^{ZZ}\) jumps fast sometimes. The average count rate of the signal and decoy states of Z basis is about 2.6 and 0.4 kbps. During the whole experiment, the reference frame varied for more than 29 periods and the noise ω reaches an upper bound of 6.9 × 10−3 rad/s.
Each point is measured within 5 s. a, b shows the QBER of signal (decoy) state on X, Y basis for the total 50.7 h, c shows the QBER of signal state and decoy state on Z basis: \({E}_{\mu }^{ZZ}\) and \({E}_{\nu }^{ZZ}\), and d shows the count rate of signal and decoy state on Z basis: \({N}_{\mu }^{ZZ}\) and \({N}_{\nu }^{ZZ}\).
In the experiment, we first calculated the average secure key rate of the 50.7 h experiment with m = 3, 4, … , 40 and the optimal \({\rho }^{\prime}\). The result is shown in Fig. 3. The secure key rate reaches the maximum when m = 12 and \({\rho }^{\prime}=\frac{\pi }{12}\). The high secure key rate is achieved when m ∈ {4i∣i ∈ N+}, for the four datasets with the upper bound are acquired shown as Fig. 4. When m ≤ 14, the secure key rate is improved with the increase of m, which decreases misalignment variation in each dataset. When m ≥ 15, the secure key rate is reduced by the increase of m, which causes the higher statistical fluctuations.
a and b show the C value and secure key rate respectively. The C value and secure key rate varies corresponding to varying misalignment of reference frame leaks different amounts of secure key information22.
Figure 5 shows the average QBER of each dataset when m = 12. The QBERs of X, Y basis vary against the rotation ρ while the QBERs of signal and decoy state on Z basis are stabilized at around 0.6 and 2.3%.
The original RFI analysis is conducted on each dataset and the corresponding C value and secure key rate of each dataset are shown in Fig. 4 with red circles. The blue dash lines in Fig. 4 illustrate the simulated results with Nt = 1.46 × 1013 5,10,22,32. In principle, the C value and the secure key rate reach the maximum values with ρ ∈ {0, π/2, π, 3π/2}, which correspond to the dataset of {\({{{{\mathscr{D}}}}}_{0}\), \({{{{\mathscr{D}}}}}_{3}\), \({{{{\mathscr{D}}}}}_{6}\), \({{{{\mathscr{D}}}}}_{9}\)}, respectively. The experimental C value and secure key rate are slightly less than the simulated results due to the imperfect preparation and measurement of photons. Then, the measured average secure key rate in our experiment is calculated as 742.98 bps bps with our free-running RFI analysis when the finite length is 1.46 × 1013 and the acquisition time is 50.7 h.
The secure key rate of our experiment is also calculated with the different finite length of 1010, 1011, 1012, and 1013 when m and \({\rho }^{\prime}\) are both optimized. The average secure key rate is shown in Table 1 and the secure key rate in each run is shown in Supplementary Note 3.
The average secure key rate of our free-running RFI scheme is same to the original RFI scheme when the finite length Nt = 1010. Afterwards, our free-running RFI scheme achieves higher average secure key rate than the original RFI scheme with Nt = 1011 for the lower misalignment variation. Furthermore, the secure key rate is further improved as the finite length is increased to 1012 and 1013, while the original RFI scheme couldn’t generate secure key.
In addition, the average secure key rate RFK with the finite-key analysis of our free-running RFI scheme is also calculated with the finite-key analysis and different finite length. εPA, εEC and \(\overline{\varepsilon }\) are all set to 10−10. The secure key rate of 724.87 bps has been achieved with Nt = 1.46 × 1013.
Secure key rate with different misalignment variation rates
Furthermore, we simulated the average secure key rate of the free-running RFI QKD versus the total loss with Nt = 108, 109, 1010, 1011, 1012, 1013 and our experimental settings. In the simulation, the dataset size m is optimized for each point. The misalignment variation rate is set as 0 and 6.9 × 10−3 rad/s, respectively. Meanwhile, the secure key rate of the original RFI scheme is also simulated with the same settings. The simulation result is shown in Fig. 6.
Solid lines show the result of our scheme, while the dash lines with dots show the result of the original scheme. a–c show the simulated secure key rate when ω equals to 0, 6.9 × 10−3 rad/s and 3.3 × 10−2 rad/s, respectively. In b and c, the original RFI scheme couldn't generate secure key when Nt ≥ 1011. In the simulation, the dataset size m and \({\rho }^{\prime}\) are optimized.
When ω = 0, our free-running RFI scheme has the same performance with the original RFI scheme. The total loss tolerance is improved from about 16.65 dB to about 44.39 dB by increasing the finite length Nt from 108 to 1013.
When ω = 6.9 × 10−3 rad/s, the performance of the both RFI schemes are reduced by the reference frame misalignment variation in the key accumulation procedure as shown in Fig. 6b. In the original RFI QKD protocol, the increase of Nt would reduce the statistical fluctuations, and increase the secure key rate, however, the larger variation Δθ would decrease secure key rate. The performance of the original RFI scheme is improved when the finite length increases from 108 to 1010, however, no secure key could be generated with Nt ≥ 1011. Thus, the total loss tolerance of the original RFI QKD protocol is limited to 32.6 dB even with the optimized finite length. And the existing RFI QKD experiment reaches the distance of 65 km29. For Nt = 108, 109, 1010, our free-running RFI scheme achieves a slightly higher secure key rate than the original RFI scheme because the measured data are classified into optimal m slices instead of the random slice in the acquisition time. Nevertheless, for Nt = 1011, 1012, and 1013, our scheme can still generate secure key rate with better performance and achieves the total loss tolerance of 43.8 dB with Nt = 1013.
In the experiment, two asymmetric Mach–Zehnder interferometers (AMZI) are in the same room and the experimental noise is lower than the practical cases. We tested the experimental noise ω when the AMZIs are in different rooms, and the reference frame variation result is shown in Supplementary Note 4. The ω reaches upper bound of 3.3 × 10−2 rad/s. Figure 6c shows the simulated secure key rate of the free-running RFI scheme and the original RFI scheme with our experimental settings. We achieved a slightly higher secure key rate than the original RFI scheme when Nt = 108, 109. Then, the secure key rate of our scheme is further improved as the finite length increases and the total loss tolerance of 43.8 dB is achieved with the finite length of 1013. While the total loss of the original RFI scheme is reduced to about 2 dB as the finite length increases to 1010. And no secure key could be generated with Nt ≥ 1011.
Moreover, the proposed free-running RFI scheme can tolerate a faster drifting of reference frames than the original RFI scheme. Instead of the \(\omega \le \frac{\pi }{\sum {t}_{i}}\) in the original RFI scheme, the variation rate ω in our scheme is limited by the Eq. (18). With our experimental settings, the misalignment variation rate tolerance is up to 0.262 rad/s, which means the reference frame varies a period within 24 s.
Discussion
In this article, we proposed a free-running RFI quantum key distribution (QKD) scheme, and performed a 50.7-hours experiment test over 100 km fiber, which reaches the secure key rate of 742.98 bps. Our free-running RFI scheme increases the loss tolerance to 43.3 dB while the original RFI scheme reaches to 32.6 dB when the experimental noise ω is 6.9 × 10−3 rad/s. The reason why our free-running RFI scheme overcomes the original RFI QKD scheme is that the measured data could be accumulated for a long time and would not result in a higher misalignment variation Δθ in our scheme.
Besides, a 150 km free-running RFI QKD experiment running for about 0.5 h has been conducted with the optimized intensities of quantum states and the experiment is explained in Supplementary Note 5.
Moreover, the interval time T in our experiment can be reduced to 1 s, and the misalignment variation rate tolerance could be increased to 1.309 rad/s (4.8 s per period). Therefore, our free-running RFI scheme can be efficiently adapted into complex scenarios with rapid and random drifting reference frames, such as satellite-to-ground systems (≤0.12 rad/s)34 and drone-based systems.
Methods
Experimental setup
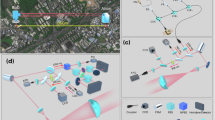
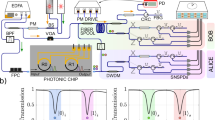
The setup of our free-running RFI QKD experiment is shown in Fig. 7. At Alice’s side, photons are generated by a homemade laser with a repetition rate of 80 MHz and a pulse width of 1.0 ns. The laser is driven by electronic pulses and vacuum state is modulated when no driving electronics pulse is sent to laser. An intensity modulator (IM1) and an attenuator (ATT) is used to modulate quantum (signal and decoy) states to the corresponding intensity. An asymmetric Mach–Zehnder interferometer (AMZI1) divides each pulse into two adjacent pulses (s and l) with a separation time of 4.6 ns. The intensity modulator IM2 prepares the bit 0 or 1 of Z basis by suppressing s or l randomly. When both s and l pulses pass through IM2, a phase of {0, π/2, π, 3π/2} will be randomly added to s pulse with two phase modulators (PM1 and PM2), where 0 and π indicate bit 0 and 1 in X basis, π/2 and 3π/2 indicate bit 0 and 1 in Y basis. Then, pulses are sent to Bob through a 100 km optical fiber with a loss of 0.235 dB/km. Meanwhile, an active feedback mechanism is performed to stabilize the intensity of the quantum states, which mainly consisted of a beam splitter (BS) and an avalanche photon detector (APD).
Two NI 6556 boards control the lasers and modulators. The computers are used for data acquisition, post-processing, and classical communication. An APD is used to measure the intensity of the signal and decoy states and the bits of Z basis, so that NI 6556 adjusts the control signal of IM1 and IM2. IM intensity modulator, BS beam splitter, PM phase modulator, PC polarization controller, AMZI asymmetric Mach–Zehnder interferometer, SNSPD superconducting nanowire single photon detector, TDC Time-to-Digital converter, APD avalanche photon detector, NI 6556 National Instruments 6556.
At Bob’s side, the detection basis (X and Y) is randomly chosen by the phase modulator (PM3), where a phase of 0 (π/2) is added to the s pulse. Then another asymmetric Mach-Zehnder interferometer (AMZI2) which has the same path difference with the AMZI1 divides each pulse into two pulses, resulting four pulses, {s + s, s + l, l + s, l + l}. s + l and l + s pulses will merge into one pulse due to the same arriving time and interfere at AMZI2. The interference determines the exiting port of the s + l (l + s) pulse at the AMZI2, indicating the bit 0 or 1 of X(Y) basis, respectively. s + s and l + l pulses represent bit 0 and 1 of Z basis. Then, photons are coupled to two channels of the superconducting nanowire single photon detector (SNSPD), and the arriving time is recorded with a time-to-digital converter (TDC). The optimal detection efficiency, about 80%, is ensured by the polarization controllers (PC2 and PC3). The dark count rate of the SNSPD is about 200 per second. Two programmable modules (National Instruments 6556) are used to control the laser and modulators. The total loss of Bob’s receiving module is around 8 dB. Furthermore, a programmable polarization controller (PC1) is used to compensate the polarization drift of the transmitted photons.
Data availability
The datasets analyzed during the current study are available from the corresponding authors on reasonable request.
Code availability
The code used in the current study is available from the corresponding authors on reasonable request.
References
Lo, H.-K., Curty, M. & Tamaki, K. Secure quantum key distribution. Nat. Photonics 8, 595 (2014).
Shannon, C. E. Communication theory of secrecy systems. Bell Syst. Tech. J. 28, 656–715 (1949).
Shannon, C. E. A mathematical theory of communication. Bell Syst. Tech. J. 27, 379–423 (1948).
Bennett, C. H. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Proc. IEEE Int. Conf. Comp. Systems Signal Processing 1, 175–179 (1984).
Lo, H.-K., Ma, X. & Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett 94, 230504 (2005).
Zhang, Z., Zhao, Q., Razavi, M. & Ma, X. Improved key-rate bounds for practical decoy-state quantum-key-distribution systems. Phys. Rev. A 95, 012333 (2017).
Kupko, T. et al. Tools for the performance optimization of single-photon quantum key distribution. npj Quantum Inf. 6, 29 (2020).
Wei, K. et al. High-speed measurement-device-independent quantum key distribution with integrated silicon photonics. Phys. Rev. X 10, 031030 (2020).
Chen, H. et al. Field demonstration of time-bin reference-frame-independent quantum key distribution via an intracity free-space link. Opt. Lett. 45, 3022–3025 (2020).
Wang, J., Liu, H., Ma, H. & Sun, S. Experimental study of four-state reference-frame-independent quantum key distribution with source flaws. Phys. Rev. A 99, 032309 (2019).
Liu, H., Wang, J., Ma, H. & Sun, S. Polarization-multiplexing-based measurement-device-independent quantum key distribution without phase reference calibration. Optica 5, 902–909 (2018).
Chen, J.-P. et al. Sending-or-not-sending with independent lasers: Secure twin-field quantum key distribution over 509 km. Phys. Rev. Lett 124, 070501 (2020).
Chen, J.-P. et al. Twin-field quantum key distribution over a 511 km optical fibre linking two distant metropolitan areas. Nat. Photonics 15, 570–575 (2021).
Wang, S. et al. Twin-field quantum key distribution over 830 km fibre. Nat. Photonics 16, 154–161 (2022).
Chen, Y.-A. et al. An integrated space-to-ground quantum communication network over 4600 kilometres. Nature 589, 214–219 (2021).
Yin, J. et al. Entanglement-based secure quantum cryptography over 1120 kilometres. Nature 582, 501–505 (2020).
Liu, H.-Y. et al. Optical-relayed entanglement distribution using drones as mobile nodes. Phys. Rev. Lett 126, 020503 (2021).
Jain, N. et al. Device calibration impacts security of quantum key distribution. Phys. Rev. Lett 107, 110501 (2011).
Dong, Z.-Y., Yu, N.-N., Wei, Z.-J., Wang, J.-D. & Zhang, Z.-M. An attack aimed at active phase compensation in one-way phase-encoded qkd systems. Eur. Phys. J. D 68, 230 (2014).
Laing, A., Scarani, V., Rarity, J. G. & O’Brien, J. L. Reference-frame-independent quantum key distribution. Phys. Rev. A 82, 012304 (2010).
Pramanik, T. et al. Robustness of reference-frame-independent quantum key distribution against the relative motion of the reference frames. Phys. Lett. A 381, 2497–2501 (2017).
Zhang, C.-M., Zhu, J.-R. & Wang, Q. Practical reference-frame-independent quantum key distribution systems against the worst relative rotation of reference frames. J. Phys. Commun. 2, 055029 (2018).
Wang, F., Zhang, P., Wang, X. & Li, F. Valid conditions of the reference-frame-independent quantum key distribution. Phys. Rev. A 94, 062330 (2016).
Zhang, C.-M., Zhu, J.-R. & Wang, Q. Practical decoy-state reference-frame-independent measurement-device-independent quantum key distribution. Phys. Rev. A 95, 032309 (2017).
Wang, C. et al. Phase-reference-free experiment of measurement-device-independent quantum key distribution. Phys. Rev. Lett 115, 160502 (2015).
Lu, F.-Y. et al. Efficient decoy states for the reference-frame-independent measurement-device-independent quantum key distribution. Phys. Rev. A 101, 052318 (2020).
Liu, J. Y. et al. Boosting the performance of reference-frame-independent measurement-device-independent quantum key distribution. J. Light. Technol. 39, 5486–5493 (2021).
Zhou, X.-Y. et al. Reference-frame-independent measurement-device-independent quantum key distribution over 200 km of optical fiber. Phys. Rev. Appl 15, 064016 (2021).
Liang, W.-Y. et al. Proof-of-principle experiment of reference-frame-independent quantum key distribution with phase coding. Sci. Rep. 4, 3617 (2014).
Sheridan, L., Le, T. P. & Scarani, V. Finite-key security against coherent attacks in quantum key distribution. New J. Phys. 12, 123019 (2010).
Wang, C., Sun, S., Ma, X., Tang, G. & Liang, L. Reference-frame-independent quantum key distribution with source flaws. Phys. Rev. A 92, 042319 (2015).
Lim, C. C. W., Curty, M., Walenta, N., Xu, F. & Zbinden, H. Concise security bounds for practical decoy-state quantum key distribution. Phys. Rev. A 89, 022307 (2014).
Tang, B.-Y., Liu, B., Yu, W.-R. & Wu, C.-Q. Shannon-limit approached information reconciliation for quantum key distribution. Quantum Inf. Process 20, 113 (2021).
Liao, S.-K. et al. Satellite-relayed intercontinental quantum network. Phys. Rev. Lett. 120, 030501 (2018).
Acknowledgements
This work was supported by National Natural Science Foundation of China under Grant No. 61972410 and No. 61971436, the Research Plan of National University of Defense Technology under Grant No. ZK19-13 and No. 19-QNCXJ-107 and the Postgraduate Scientific Research Innovation Project of Hunan Province under Grant No. CX20200003.
Author information
Authors and Affiliations
Contributions
B.L. proposed the scheme. B.Y.T. and H.C. designed, performed the experiment, and contributed equally. This work was supervised by B.L. and W.R.Y. and co-supervised by S.H.S., L.S., and W.P. J.P.W. and H.C.Y. contributed to the data collection and analysis. B.Y.T., H.C., and B.L. wrote the draft and all authors reviewed the manuscript.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Tang, BY., Chen, H., Wang, JP. et al. Free-running long-distance reference-frame-independent quantum key distribution. npj Quantum Inf 8, 117 (2022). https://doi.org/10.1038/s41534-022-00630-3
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41534-022-00630-3