Abstract
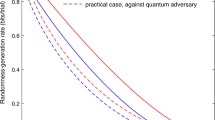
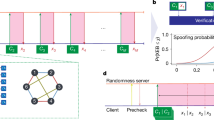
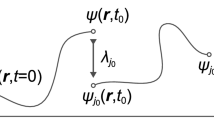
The unpredictability of random numbers is fundamental to both digital security1,2 and applications that fairly distribute resources3,4. However, existing random number generators have limitations—the generation processes cannot be fully traced, audited and certified to be unpredictable. The algorithmic steps used in pseudorandom number generators5 are auditable, but they cannot guarantee that their outputs were a priori unpredictable given knowledge of the initial seed. Device-independent quantum random number generators6,7,8,9 can ensure that the source of randomness was unknown beforehand, but the steps used to extract the randomness are vulnerable to tampering. Here we demonstrate a fully traceable random number generation protocol based on device-independent techniques. Our protocol extracts randomness from unpredictable non-local quantum correlations, and uses distributed intertwined hash chains to cryptographically trace and verify the extraction process. This protocol forms the basis for a public traceable and certifiable quantum randomness beacon that we have launched10. Over the first 40 days of operation, we completed the protocol 7,434 out of 7,454 attempts—a success rate of 99.7%. Each time the protocol succeeded, the beacon emitted a pulse of 512 bits of traceable randomness. The bits are certified to be uniform with error multiplied by actual success probability bounded by 2−64. The generation of certifiable and traceable randomness represents a public service that operates with an entanglement-derived advantage over comparable classical approaches.
This is a preview of subscription content, access via your institution
Access options
Access Nature and 54 other Nature Portfolio journals
Get Nature+, our best-value online-access subscription
$32.99 / 30 days
cancel any time
Subscribe to this journal
Receive 51 print issues and online access
$199.00 per year
only $3.90 per issue
Buy this article
- Purchase on SpringerLink
- Instant access to the full article PDF.
USD 39.95
Prices may be subject to local taxes which are calculated during checkout




Similar content being viewed by others
Data availability
All data and information used to generate each randomness pulse are publicly available at https://random.colorado.edu. Additional data used for diagnostic plots shown in the Supplementary Information are available by request from the corresponding authors. Source data are provided with this paper.
Code availability
The code used to run the beacon, analyse the data, and verify or trace the randomness in a pulse is publicly available via GitHub at https://github.com/buff-beacon-project. Code used to generate the figures is available by request from the corresponding authors.
References
Buchmann, J. A. Introduction to Cryptography (Springer, 2004).
Eastlake, D. E. 3rd, Crocker, S. & Schiller, J. I. Randomness Requirements for Security. Request for Comments 4086 (Internet Engineering Task Force, 2005).
Stone, P. Why lotteries are just. J. Polit. Philos. 15, 276–295 (2007).
Duxbury, N. Random Justice: On Lotteries and Legal Decision-Making (Oxford Univ. Press, 1999).
Menezes, A. J., Van Oorschot, P. C. & Vanstone, S. A. Handbook of Applied Cryptography 1st edn (CRC, 2018).
Bierhorst, P. et al. Experimentally generated randomness certified by the impossibility of superluminal signals. Nature 556, 223–226 (2018).
Liu, Y. et al. Device-independent quantum random-number generation. Nature 562, 548–551 (2018).
Colbeck, R. Quantum and relativistic protocols for secure multi-party computation. Preprint at https://arxiv.org/abs/0911.3814 (2011).
Pironio, S. et al. Random numbers certified by Bell’s theorem. Nature 464, 1021–1024 (2010).
CURBy CU Randomness Beacon (University of Colorado Boulder, 2024); https://random.colorado.edu/
Bosley, C. & Dodis, Y. in Theory of Cryptography Vol. 4392 (ed. Vadhan, S. P.) 1–20 (Springer, 2007).
Stipčević, M. & Koç, Ç. K. in Open Problems in Mathematics and Computational Science (ed. Koç, Ç. K.) 275–315 (Springer, 2014).
Aaronson, S. & Hung, S.-H. Certified randomness from quantum supremacy. In Proc. 55th Annual ACM Symposium on Theory of Computing (eds Saha, B. & Servedio, R. A.) 933–944 (ACM, 2023).
Koç, Ç. K. (ed.) Cryptographic Engineering (Springer, 2009).
Herrero-Collantes, M. & Garcia-Escartin, J. C. Quantum random number generators. Rev. Mod. Phys. 89, 015004 (2017).
Rabin, M. O. Transaction protection by beacons. J. Comput. Syst. Sci. 27, 256–267 (1983).
Kelsey, J., Brandão, L. T. A. N., Peralta, R. & Booth, H. A reference for randomness beacons. Preprint at https://doi.org/10.6028/NIST.IR.8213-draft (2019).
Bonneau, J., Clark, J. & Goldfeder, S. On bitcoin as a public randomness source. Preprint at https://eprint.iacr.org/2015/1015 (2015).
Syta, E. et al. Scalable bias-resistant distributed randomness. In Proc. 2017 IEEE Symposium on Security and Privacy (SP) (ed. Butler, K. R. B.) 444–460 (IEEE, 2017).
Fischer, M. J., Iorga, M. & Peralta, R. A public randomness service. In Proc. International Conference on Security and Cryptography (eds Lopez, J. & Samarati, P.) 434–438 (IEEE, 2011).
Micali, S., Rabin, M. & Vadhan, S. Verifiable random functions. In Proc. 40th Annual Symposium on Foundations of Computer Science (Cat. No.99CB37039) (ed. Mitsenmacher, M.) 120–130 (IEEE, 1999).
Gras, G., Martin, A., Choi, J. W. & Bussières, F. Quantum entropy model of an integrated quantum-random-number-generator chip. Phys. Rev. Appl. 15, 054048 (2021).
Abellán, C., Amaya, W., Mitrani, D., Pruneri, V. & Mitchell, M. W. Generation of fresh and pure random numbers for loophole-free Bell tests. Phys. Rev. Lett. 115, 250403 (2015).
Soucarros, M., Canovas-Dumas, C., Clediere, J., Elbaz-Vincent, P. & Real, D. Influence of the temperature on true random number generators. In Proc. 2011 IEEE International Symposium on Hardware-Oriented Security and Trust (eds Schaumont, P. & Karri, R.) 24–27 (IEEE, 2011).
Ragab, H., Milburn, A., Razavi, K., Bos, H. & Giuffrida, C. Crosstalk: speculative data leaks across cores are real. In Proc. 2021 IEEE Symposium on Security and Privacy (SP) (eds Oprea, A. & Holz, T.) 1852–1867 (IEEE, 2021).
Shalm, L. K. et al. Device-independent randomness expansion with entangled photons. Nat. Phys. 17, 452–456 (2021).
Li, M.-H. et al. Experimental realization of device-independent quantum randomness expansion. Phys. Rev. Lett. 126, 050503 (2021).
Liu, W.-Z. et al. Device-independent randomness expansion against quantum side information. Nat. Phys. 17, 448–451 (2021).
Shalm, L. K. et al. Strong loophole-free test of local realism. Phys. Rev. Lett. 115, 250402 (2015).
Giustina, M. et al. Significant-loophole-free test of Bell’s theorem with entangled photons. Phys. Rev. Lett. 115, 250401 (2015).
Hensen, B. et al. Loophole-free Bell inequality violation using electron spins separated by 1.3 kilometres. Nature 526, 682–686 (2015).
Rosenfeld, W. et al. Event-ready Bell test using entangled atoms simultaneously closing detection and locality loopholes. Phys. Rev. Lett. 119, 010402 (2017).
Storz, S. et al. Loophole-free Bell inequality violation with superconducting circuits. Nature 617, 265–270 (2023).
Zhang, Y., Knill, E. & Bierhorst, P. Certifying quantum randomness by probability estimation. Phys. Rev. A 98, 040304 (2018).
Dupuis, F., Fawzi, O. & Renner, R. Entropy accumulation. Commun. Math. Phys. 379, 867–913 (2020).
Ma, X. et al. Postprocessing for quantum random-number generators: entropy evaluation and randomness extraction. Phys. Rev. A 87, 062327 (2013).
Trevisan, L. Extractors and pseudorandom generators. J. ACM 48, 860–879 (2001).
Mauerer, W., Portmann, C. & Scholz, V. B. A modular framework for randomness extraction based on Trevisan’s construction. Preprint at https://arxiv.org/abs/1212.0520 (2012).
Zhang, Y. et al. Experimental low-latency device-independent quantum randomness. Phys. Rev. Lett. 124, 010505 (2020).
Lamport, L. Password authentication with insecure communication. Commun. ACM 24, 770–772 (1981).
Dworkin, M. J. SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions. Technical Report NIST FIPS 202 (National Institute of Standards and Technology, 2015).
Cormen, T. H., Leiserson, C. E., Rivest, R. L. & Stein, C. Introduction to Algorithms 3rd edn (MIT Press, 2009).
Thulasiraman, K. & Swamy, M. N. S. Graphs: Theory and Algorithms (Wiley, 2011).
Gailly, N. et al. drand/drand: A Distributed Randomness Beacon Daemon - Go implementation. GitHub https://github.com/drand/drand (2024).
Grassi, P. A., Garcia, M. E. & Fenton, J. L. Digital Identity Guidelines: Revision 3. Technical Report NIST SP 800-63-3 (National Institute of Standards and Technology, 2017).
Benet, J. IPFS - content addressed, versioned, P2P file system, Preprint at https://arxiv.org/abs/1407.3561 (2014).
Reddy, D. V., Nerem, R. R., Nam, S. W., Mirin, R. P. & Verma, V. B. Superconducting nanowire single-photon detectors with 98% system detection efficiency at 1550 nm. Optica 7, 1649–1653 (2020).
Dowling, J. P. & Milburn, G. J. Quantum technology: the second quantum revolution. Philos. Trans. R. Soc. A 361, 1655–1674 (2003).
Chambers, C. D. & Tzavella, L. The past, present and future of Registered Reports. Nat. Hum. Behav. 6, 29–42 (2021).
Gheorghiu, A. & Vidick, T. Computationally-secure and composable remote state preparation. In Proc. 2019 IEEE 60th Annual Symposium on Foundations of Computer Science (FOCS) (ed. Zuckerman, D.) 1024–1033 (2019).
Cojocaru, A., Colisson, L., Kashefi, E. & Wallden, P. QFactory: classically-instructed remote secret qubits preparation. In Proc. Advances in Cryptology – ASIACRYPT 2019 (eds Galbraith, S. D. & Moriai, S.) 615–645 (Springer, 2019).
Mahadev, U. Classical verification of quantum computations. In Proc. 2018 IEEE 59th Annual Symposium on Foundations of Computer Science (FOCS) 259–267 (IEEE, 2018).
Zhu, D. et al. Interactive cryptographic proofs of quantumness using mid-circuit measurements. Nat. Phys. 19, 1725–1731 (2023).
Brakerski, Z., Christiano, P., Mahadev, U., Vazirani, U. & Vidick, T.A cryptographic test of quantumness and certifiable randomness from a single quantum device. J. ACM 68, 31 (2021).
Acknowledgements
This work includes contributions of the NIST, which are not subject to US copyright. The use of trade names does not imply endorsement by the US Government. The work is supported by the National Science Foundation RAISE-TAQS programme (award 1840223), the CU through the ‘QuEST Seed Award: A Quantum Randomness Beacon’, the Colorado Office of Economic Impact (award number DO 2023-0335), in part by the European Union ‘NextGenerationEU/PRTR’. Spanish Ministry of Science MCIN: project SAPONARIA (PID2021-123813NB-I00) and ‘Severo Ochoa’ Center of Excellence CEX2019-000910-S. Generalitat de Catalunya through the CERCA programme and grant number 2021 SGR 01453; Fundació Privada Cellex; Fundació Mir-Puig. This work was performed in part at Oak Ridge National Laboratory, operated by UT-Battelle for the US Department of Energy under contract number DE-AC05-00OR22725. We thank S. Glancy, B. Chen, L. Norton, E. Some and R. Snyder for discussions regarding the project, and J. G. Price for providing the image used in Fig. 2.
Author information
Authors and Affiliations
Contributions
G.A.K. built and performed the experiment with assistance from L.K.S., M.D.M. and M.J.S., and collected and analysed data. J.P. and L.K.S. developed the Twine protocol with inputs from L.T.A.N.B., H.B. and R.P., and implemented it with assistance from J.M.C. and A.D. D.V.R. provided the high-efficiency detectors. Y.Z., M.A.A., A.U.S., L.K.S., G.A.K. and E.K. participated in the data analysis. J.C.B. provided electronics and hardware RNGs. C.A., W.A. and M.W.M. provided hardware RNGs. P.D.B. and J.P. developed a software RNG used in CURBy. J.P., K.E.S., L.K.S. and P.D.B. developed the hardware and software at CU to run the CURBy network. L.K.S., S.W.N. and R.P.M. supervised the project. G.A.K. led the writing of the manuscript with all authors contributing.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Peer review
Peer review information
Nature thanks the anonymous reviewers for their contribution to the peer review of this work. Peer reviewer reports are available.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Source data
Rights and permissions
About this article
Cite this article
Kavuri, G.A., Palfree, J., Reddy, D.V. et al. Traceable random numbers from a non-local quantum advantage. Nature 642, 916–921 (2025). https://doi.org/10.1038/s41586-025-09054-3
Received:
Accepted:
Published:
Version of record:
Issue date:
DOI: https://doi.org/10.1038/s41586-025-09054-3
This article is cited by
-
Applications of certified randomness
Nature Reviews Physics (2025)
-
Cheat-proof random numbers generated from quantum entanglement
Nature (2025)
-
Quantum physicists unveil most ‘trustworthy’ random-number generator yet
Nature (2025)
-
Experimenting with Quantum True Random Number Generators on NISQ Computers Using High-level Quantum Programming
International Journal of Theoretical Physics (2025)