Abstract
Underwater wireless sensor networks (UWSNs) are an emerging research area that is rapidly gaining popularity. However, it has several challenges, including security, node mobility, limited bandwidth, and high error rates. Traditional trust models fail to adapt to the dynamic underwater environment. Thus, to address these issues, we propose a dynamic trust evaluation and update model using a modified decision tree algorithm. Unlike baseline methods, which often rely on static and generalized trust evaluation approaches, our model introduces several innovations tailored specifically for UWSNs. These include energy-aware decision-making, real-time adaptation to environmental changes, and the integration of multiple underwater-specific factors such as water currents and acoustic signal properties. Our model enhances trust accuracy, reduces energy consumption, and lowers data overhead, achieving a 96% accuracy rate with a 2% false positive rate. Additionally, it outperforms baseline models by improving energy efficiency by 50 mW and reducing response time to 20 ms per packet. These innovations demonstrate the proposed model’s effectiveness in addressing the unique challenges of UWSNs, ensuring both security and operational efficiency goals. The proposed model effectively enhances the trust evaluation process in UWSNs, providing both security and operational benefits. These key findings validate the potential of integrating modified decision tree algorithms to improve the performance and sustainability of UWSNs.
Similar content being viewed by others
Introduction
The exploration of oceans has always been a testament to human curiosity. This attitude possesses the human to the technological advancement. As we delve deeper into the marine world. The tools we employ become crucial in understanding this vast and complex environment1. One such tool that has gained prominence in recent years is the UWSN. UWSNs are specialized wireless networks conceptualized and designed for the unique challenges of aquatic environments, ranging from the deep oceans to serene lakes. Unlike their traditional networks, UWSNs operate under conditions influenced by the physical properties of water and the marine ecosystem. The evolution of UWSNs was initially motivated by defense and military applications, such as submarine communication and underwater surveillance. Figure 1 illustrates an overview of the UWSN environment. The network architecture incorporates traditional UWSNs. However, with the advancements in technology, their utility has expanded to encompass areas like environmental monitoring, marine biology, offshore exploration, and even disaster prediction2.
Communication in UWSNs primarily relies on acoustic waves. Radio frequencies suffer from significant attenuation in underwater networks, so acoustic waves offer a feasible solution. The key challenges include limited bandwidth, latency, and the influences of marine conditions like salinity, temperature, and water currents on signal propagation, etc3. The importance of UWSNs in modern marine research and exploration is a hot issue. They play a pivotal role in the real-time monitoring of marine ecosystems, early detection of underwater seismic activities, and facilitating underwater robotics and exploration missions4,5,6. The sensors communicate with others using specific communication protocols. Security is the main concern when communicating nodes. For ensuring security, trust plays a pivotal role in the effective functioning of UWSNs. Given the remote and often inaccessible nature of underwater deployments, ensuring the reliability and authenticity of data becomes paramount. Trust mechanisms and proposals help discern the credibility of sensor nodes and the data they transmit. Data accuracy is crucial in marine ecosystem monitoring or underwater seismic detection applications. From that aspect, the compromised or malfunctioning node can transmit erroneous data, leading to incorrect analyses or conclusions7. In addition, UWSNs are vulnerable to various security threats, including eavesdropping, man-in-the-middle attacks, and node impersonation. Trust mechanisms are used to identify and isolate malicious nodes, ensuring the overall security of the network8. In the resource-constrained underwater environment, where energy is at a premium, trust mechanisms ensure that communication resources are not wasted on unreliable or malicious nodes. This prolongs the network’s operational lifespan9. Nodes may frequently lose connectivity in the dynamic underwater environment due to water currents or marine life interference. Trust mechanisms can aid in making informed decisions about routing data through the most reliable nodes, ensuring data reaches its destination10. Traditional trust evaluation models in UWSNs rely on direct observation, indirect evaluation, and data-centric approaches. These models often fail to adapt to the dynamic underwater environment, leading to high energy consumption, limited scalability, and attack vulnerability. The development of a robust and adaptive trust evaluation model for UWSNs that efficiently addresses node mobility, energy constraints, and high error rates while ensuring high accuracy and security. Enhancing UWSNs’ security and operational efficiency is crucial for environmental monitoring and marine research applications. Improved trust mechanisms are needed to ensure reliable data transmission and network resilience in dynamic underwater conditions. This research proposes a dynamic trust evaluation and update model using a modified decision tree algorithm tailored for UWSNs. It incorporates node energy levels, water currents, and acoustic signals to dynamically update trust values dynamically, demonstrating superior accuracy, energy efficiency, and data overhead performance. This research aims to develop a dynamic trust evaluation and update model tailored for UWSNs that addresses the unique challenges of the underwater environment, including security vulnerabilities, energy constraints, and the dynamic nature of node mobility. By leveraging a modified decision tree algorithm, the research aims to enhance the accuracy of trust assessments, improve energy efficiency, and ensure reliable data transmission, ultimately contributing to the overall robustness and operational efficiency of UWSNs. The research enhances UWSNs’ security and reliability, extends sensor node lifespan, reduces maintenance costs, and provides a framework for future underwater monitoring and exploration advancements. Briefly, our research aims to:
-
A dynamic trust evaluation model is proposed that considers multiple attributes related to node behavior and data transmission, focusing on improving trust accuracy and energy efficiency issues.
-
A dynamic update mechanism is introduced that adapts to the changing conditions and challenges of the underwater environment.
-
For efficiency, several experiments were performed, and the proposed and traditional models were validated using simulations and real-world deployments. The proposed model demonstrated superior performance in trust evaluation, achieving an accuracy of 96%, a false positive rate of 2%, and reduced data overhead by 10 KB per node. Compared to baseline models, the proposed model showed improved energy efficiency by 50 mW and a response time of 20 ms per packet.
-
This research highlights the implications of integrating the proposed trust model in UWSNs and its potential benefits in enhancing network performance, security, and reliability.
The rest of the paper is organized as follows. Section “Related work” discusses a recent literature review. Section “Proposed model” presents the Modified Decision Tree Algorithm. Section “Trust evaluation process” presents models for the proposed scheme. Section “Experiments, simulation, and performance evaluation” presents the trust evaluation process. Section “Results and discussion” presents the performance evaluation, and Sect. “Conclusion and future work” presents the conclusion and future work.
Related work
The research UWSNs has witnessed significant research attention over the past few decades. One of the critical areas of focus has been the establishment and evaluation of trust within these networks. Trust mechanisms play a pivotal role in ensuring the reliability, security, and overall performance of UWSNs.
Research on traditional trust evaluation models for UWSNs
Trust evaluation in UWSNs has traditionally revolved around a few key methodologies. This paper examines the conventional methodologies utilized for trust evaluation in UWSNs, highlighting various approaches proposed by researchers. Feng et al.11 proposed a straightforward method where nodes evaluate the trustworthiness of their neighbors based on direct interactions. If a neighboring node consistently forwards packets, it is deemed trustworthy. Conversely, if it frequently drops packets or sends malicious data, its trust score diminishes. Anwar et al.12 proposed that the nodes rely on the feedback or reputation reports from other nodes in the network. This method is particularly useful when direct observations are limited or inconclusive. Wang et al.13 proposed an approach that focuses on the data transmitted by the sensor nodes. By analyzing the consistency, accuracy, and timeliness of data, nodes can evaluate the trustworthiness of the data source. Kaur and Joshi14 presented a combination of direct, indirect, and data-centric methods to create a more comprehensive and robust trust evaluation mechanism. Table 1 shows the comparison of existing trust evaluation mechanisms.
Research on decision tree-based approaches
Decision trees have been widely adopted in various network scenarios due to their simplicity, interpretability, and effectiveness in handling large datasets. These hierarchical models make decisions based on sequentially evaluating certain criteria. Decision trees have been employed for various network tasks, from intrusion detection to quality of service (QoS) optimization. Alshiekh et al.15 presented that decision trees have been used to detect and classify malicious activities in wireless networks. Decision trees can effectively identify threats and intrusions by analyzing network traffic patterns and behaviors. Xie et al.16 proposed that decision trees be employed to optimize the quality of service in networks. By evaluating factors like bandwidth, latency, and packet loss, decision trees can make real-time decisions to enhance network performance. Saeed et al.17 presented that decision trees can diagnose network faults by analyzing network logs and metrics. They can pinpoint the root cause of network issues, facilitating quicker resolution. Mazidi et al.18 discussed the cloud computing environments regarding resource allocation; decision trees have been used to allocate resources efficiently. They evaluate the demands and priorities of various tasks to optimize resource distribution. Comparison of the decision tree-based approaches are discussed in Table 2 in terms of various similar networks.
Recent advancements in Wireless Sensor Networks (WSNs) and their specialized applications, such as underwater environments and the Internet of Things (IoT), have introduced innovative techniques that improve data gathering, energy efficiency, and security. The study19 explores the use of Autonomous Underwater Vehicles (AUVs) to enhance data collection in underwater environments by employing clustering and matrix completion techniques. This approach addresses challenges similar to those in UWSNs, such as data reliability and energy efficiency, which are also key concerns in our proposed model. Additionally20, introduces a novel approach to optimizing energy consumption while considering risk factors in IoT networks. This study is particularly relevant to our work as it underscores the importance of energy-efficient algorithms, especially in constrained environments like UWSNs. Integrating Tiny Machine Learning (TinyML) with UAVs demonstrates the potential for lightweight, adaptive models that could be further explored in UWSNs to enhance trust evaluation mechanisms. In the context of trust evaluation in wireless sensor networks, Han et al.21 proposed a model based on anomaly detection, effectively identifying and mitigating malicious behaviors within the network. Goyal et al.22 introduced a probabilistic trust framework tailored for smart environments, focusing on enhancing trust accuracy by considering environmental factors and node behaviors. Zhang et al.23 We developed a machine learning-based trust management approach that leverages classification techniques to dynamically evaluate the trustworthiness of sensor nodes, improving the network’s overall security and reliability. These studies provide valuable insights into trust evaluation mechanisms, which have informed the development and comparison of our proposed model. In addition to traditional models, we compare our approach with recent schemes like PPRU24, a privacy-preserving reputation updating scheme for cloud-assisted vehicular networks, and TFL-DT, a trust evaluation scheme for federated learning in mobile networks. PPRU emphasizes privacy in reputation updates, which is crucial for vehicular networks. However, our model focuses on energy efficiency and real-time adaptability in UWSNs, incorporating environmental factors like water currents and energy levels. TFL-DT leverages federated learning for trust management without sharing raw data, which is vital for mobile networks25. In contrast, our model is tailored to the unique challenges of UWSNs, such as acoustic signal transmission and energy constraints. While PPRU and TFL-DT excel in their domains, our model’s specialization in underwater environments, emphasizing energy-aware and real-time trust evaluation, distinguishes it as an effective solution for UWSNs. An auv-assisted data gathering scheme based on clustering and matrix completion for smart ocean is proposed by26. Joint optimization risk factor and energy consumption in IoT based networks proposed by27.
Identified gaps in recent literature
While a plethora of research has been conducted on trust evaluation mechanisms in UWSNs and the application of decision trees in various network scenarios, a comprehensive review of the literature reveals several gaps that warrant further exploration. Mejjaouli and Babiceanu28 discussed integration issues. Despite the proven efficacy of decision trees in other network types, there is a noticeable lack of research on their integration within UWSNs for trust evaluation. Li et al.2 discussed the dynamic environment regarding trust evaluations. The traditional trust evaluation mechanisms in UWSNs are designed for static or semi-static environments. The dynamic nature of underwater environments, influenced by water currents, marine life, and temperature gradients, necessitates more adaptive trust evaluation mechanisms. As UWSNs grow and complexity, scalability becomes a pressing concern. Many traditional trust evaluation mechanisms may not scale efficiently, leading to increased computational overhead and energy consumption2,29,30. Current trust evaluation mechanisms often focus on singular metrics, such as data integrity or node behavior. There is a gap in the literature for holistic trust evaluation mechanisms considering a broader range of metrics, from data timeliness to node mobility31. While Saeed et al.8 present numerous trust evaluation mechanisms proposed in the literature, there is a lack of studies that validate these mechanisms in real-world UWSN deployments. Such validations are crucial to understand the practical challenges and limitations. With the evolution of cyber threats, UWSNs are susceptible to more sophisticated attacks. The literature often overlooks these advanced threats when designing trust evaluation mechanisms, leading to potential vulnerabilities32. Decision trees are a popular machine learning (ML) technique for classification and regression tasks. They work by recursively splitting the dataset into subsets based on each level’s most significant attribute(s), making decisions at every node33. A decision tree consists of nodes that form a rooted tree, meaning it is a directed tree with a node called the “root” with no incoming edges. Every node has zero or more outgoing edges. The nodes can be of three types: The root node is the topmost node that is considered the best predictor34. It splits the dataset into two or more homogeneous sets. An internal node represents a feature or attribute that will be tested, leading to further subdivisions. The terminal node is not split and represents the outcome. The notations used in this study are summarized in Table 3.
The primary challenge in constructing a decision tree is identifying the attributes we should consider and the sequence in which they should be considered. The popular metrics used for this purpose include:
It measures the impurity or randomness in the dataset. The formula for entropy for a binary classification problem is:
where \(p+\) and \(P-\) are proportions of positive and negative examples of \(S\).
It measures the effectiveness of an attribute in classifying the data. It’s the difference between the entropy of the original dataset and the sum of the entropies of the subsets formed by splitting the dataset based on the attribute. The attribute with the highest information gain is chosen for the split.
where \(S\) is the dataset, \(A\) shows the attributes, \({S}_{v}\) is the subset of S for each attribute A, which has value v.
Advance tailored for UWSNs
UWSNs present unique challenges due to their dynamic environment, limited energy resources, and the specific nature of underwater communication. To make decision tree algorithms more suitable for UWSNs, several modifications are proposed:
Traditional decision trees do not consider the energy consumption of sensor nodes. In UWSNs, energy is a premium. Therefore, the modified decision tree will prioritize splits that consider the energy levels of nodes. The energy of a node can be represented as \(E\), and a threshold \({E}_{thresh}\) can be set. If \({E<E}_{thresh}\), the node might be considered unreliable.
where \(\sum\:{E}_{node}\)is the energy of a specific node and \(N\) is the total number of nodes.
The decision tree will incorporate attributes related to water currents, as they can affect node mobility and communication reliability. A variable \(C\) can represent the current’s strength, and the tree will adapt its decisions.
Acoustic communication is predominant in UWSNs. When making decisions, the modified tree will consider acoustic signal attributes like signal-to-noise ratio (SNR) and bit error rate (BER). Given the dynamic nature of UWSNs, the decision tree will have a feedback loop. If a decision leads to unreliable communication or data transfer, the tree will adapt its future decisions based on this feedback. For the feedback loop, if \(F\) represents the feedback from a decision and \(D\) represents the decision’s reliability score.
where \(\alpha\) is a learning rate that determines how much the decision tree should adapt based on feedback.
Attribute selection and weighting
Not all attributes are equally important in UWSNs. Due to the unique challenges of underwater environments, some attributes might significantly impact the decision-making process. Therefore, a systematic approach to attribute selection and weighting is crucial.
Attribute selection
-
Energy Level (E): Given the limited energy resources in UWSNs, a node’s energy level is a critical attribute.
-
Signal-to-Noise Ratio (SNR): This represents the quality of the acoustic communication channel.
-
Node Mobility (M): Given the dynamic nature of underwater environments, a node’s mobility can affect its reliability.
-
Data Transmission Rate (DTR): The rate at which a node can transmit data can influence decision-making, especially in time-sensitive applications.
Weighting
Each attribute is assigned a weight based on its importance. The weights can be determined using expert judgment, historical data, or ML techniques. For example:
-
Weight for Energy Level (\({W}_{E}\)) = 0.4
-
Weight for SNR (\({W}_{SNR}\)) = 0.3
-
Weight for Node Mobility (\({W}_{M}\)) = 0.2
-
Weight for Data Transmission Rate (\({W}_{DTR}\)) = 0.1
The weighted sum for a node can be calculated as:
Pruning techniques for UWSNs
Pruning is essential to prevent overfitting and to ensure the decision tree is not overly complex, which can be especially crucial in UWSNs due to limited computational resources. One of the simplest and most effective pruning techniques. Each node is replaced with its most popular class starting at the leaves. If the prediction accuracy is not affected, the change is kept. Second, the cost complexity pruning technique introduces a penalty term for the tree’s complexity. It prunes the tree based on a complexity parameter, ensuring it is not overly complex for UWSNs. The Minimum Description Length (MDL) Pruning technique aims to minimize the information required to represent the data and the tree, making it suitable for UWSNs where memory and computational resources are limited.

Algorithm 1. Attribute selection and weighting.
Algorithm 1 represents a set of attributes i.e. {E, SNR, M, DTR}. The importance score and weight of an attribute a are denoted as and respectively. For each node in the decision tree, indicates the weighted sum of its attributes and represents the value of attribute a for that node. These elements facilitate the computation and decision-making processes within the decision tree. The algorithm commences with Step 1, initializing a predefined set of attributes crucial for decision-making in the network. Subsequently, Step 2 determines each attribute’s importance score and weight, ensuring the weight is normalized by considering the sum of all importance scores. Finally, Step 3 meticulously calculates the weighted sum of attributes for every node in the decision tree, utilizing the derived value to execute a decision or initiate a split, thereby navigating through the decision tree effectively.
Algorithm complexity and computational cost
This study presents a detailed analysis of the proposed algorithm’s time complexity and computational cost to provide a comprehensive understanding of its efficiency.
The time complexity of the proposed modified decision tree algorithm can be broken down into the following key steps.
-
Attribute selection and splitting.
The time complexity for selecting the best attribute at each node is \(O(NlogN)\), where \(N\) is the number of nodes (or data points) being considered. The algorithm evaluates all possible splits and chooses the one that optimizes the selected criteria (e.g., information gain, energy level).
-
Tree construction.
The overall construction of the decision tree involves recursively splitting the data until the stopping criteria are met. For a dataset with \(M\) attributes, the worst-case time complexity for building the tree is \(O(M\times\:NlogN)\), assuming the tree grows to its maximum depth.
-
Dynamic updates.
The dynamic update mechanism, which adjusts the trust scores based on changes in the network (e.g., node addition/removal), primarily involves updating specific nodes in the tree. Since these updates are localized, the time complexity is reduced to \(O(logN)\) per update, reflecting the depth of the tree where the update is applied.
The computational cost of the algorithm is a critical factor in resource-constrained environments like UWSNs. We consider the following aspects:
-
Memory usage.
The memory usage for storing the decision tree is proportional to the number of nodes, \(O(NlogN)\), Each node in the tree requires storage for the attributes, thresholds, and associated metadata (e.g., trust scores). Our algorithm’s optimized design ensures minimal memory usage, which is crucial for UWSNs with limited resources.
-
Energy consumption.
The algorithm’s energy consumption primarily arises from the computations required for attribute selection, tree construction, and dynamic updates. By incorporating energy-aware splits and minimizing unnecessary updates, our algorithm is designed to operate efficiently within the energy constraints of UWSNs. The energy cost is further reduced by limiting the frequency of trust score updates, as described in the dynamic update mechanism.
-
Computational overhead.
The computational overhead is managed by ensuring that most operations, such as attribute evaluation and tree traversal, are performed in \(O(logN)\) time. This approach balances the need for accurate trust evaluation with the practical limitations of underwater sensor nodes.
The proposed algorithm balances accuracy and computational efficiency. The decision tree structure, enhanced with energy-aware and dynamic update features, ensures that the algorithm operates within the acceptable limits of time complexity and computational cost for UWSNs. This analysis supports the viability of the proposed model for real-world deployments, where both computational resources and energy are at a premium.
Proposed model
In this section, we present and explain our proposed model.
Proposed system model
The proposed system model presents a structured illustration of the UWSN. It is a two-phase model. In phase 1, the data preprocessing is performed. In the second phase, the modified decision tree is employed. The system model shows its components, their interactions, and the environment. The UWSN is conceptualized as a collection of sensor nodes deployed underwater to monitor and collect data from the marine environment. These nodes communicate with each other and with surface stations or buoys using acoustic signals. The choice of decision trees as the foundation for our trust evaluation mechanism is motivated by their interpretability, simplicity, and efficiency—key requirements in resource-constrained environments like UWSNs. While more advanced techniques, such as deep learning or ensemble methods, could offer higher accuracy, they typically demand significant computational and energy resources, often limited in UWSNs.
Our approach goes beyond traditional decision tree applications by introducing several novel modifications tailored specifically for UWSNs. These include energy-aware decision splits, incorporating environmental factors like water currents and dynamic feedback loops that allow the model to adapt to the constantly changing underwater environment. These enhancements ensure that our model not only maintains low computational and energy costs but also responds effectively to the unique challenges posed by UWSNs.
In terms of UWSNs, several components and attributes are pivotal, as shown in Table 4. The Sensor Node (SN) is the fundamental unit endowed with sensing, processing, and communication capabilities, playing a crucial role in data acquisition and transmission. The Surface Station (SS), floating or anchored, serves as a data collection and relay point, interfacing between underwater nodes and on-land data centers. Communication Link, facilitated by acoustic signals, enables data transmission amidst the underwater milieu. Node Depth (D) indicates the deployment depth of a sensor node, while Node Mobility (M) reflects its potential movement, influenced by various environmental factors. Communication Range (CR) denotes the maximum distance allowing reliable data transmission between nodes, and Battery Life (BL) represents the operational lifespan of a node, dictated by its energy source, underscoring the network’s operational sustainability.
Figure 2 shows the visual representation of the UWSN. It depicts sensor nodes scattered at various depths underwater, with communication links (represented by lines) connecting them. Some nodes would be connected to surface stations, which float on the water surface. The nodes’ varying depths and potential mobility paths could be indicated using arrows. Sensor nodes are capable of sensing, processing, storage, communication, mobility, and energy management are summarized in Table 5.
Figure 3 illustrates the distribution of components in an underwater sensor node, indicating its role in energy harvesting for the node.
Network model
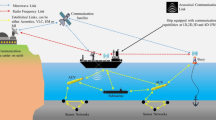
The network model is intricately designed around adaptive routing protocols, ensuring optimal data transmission amidst the dynamic underwater conditions. Characterized by node mobility and variable water currents, UWSNs necessitate a real-time model that can dynamically adjust data paths. Adaptive routing protocols, therefore, dynamically select the most efficient data transmission paths, considering various metrics like energy consumption and delay, ensuring data navigates effectively through the ever-changing network topology, thereby maintaining communication integrity amidst the fluid underwater environment. A network model, as shown in Fig. 4, visual representation of the communication paradigm might depict a network of interconnected nodes underwater. Curved lines (representing acoustic waves) would show data transmission between nodes. Dotted lines could represent multi-hop paths, and a surface station would be shown receiving data from multiple nodes.
Threat model
Understanding the threat model is crucial in the realm of UWSNs. It provides insights into potential vulnerabilities, helping design robust and secure networks. The threat model encompasses various potential attacks and their implications for the network’s integrity, availability, and confidentiality.
Selective forwarding
A malicious node might selectively drop packets while forwarding, disrupting the network’s information flow and leading to incomplete or delayed data reaching the destination.
Data tampering and replying attack
Malicious nodes can alter the content of data packets, introducing false information or modifying genuine data, leading to incorrect decisions or actions based on this tampered data. Attackers capture legitimate data packets and retransmit them later, causing confusion or triggering unintended actions.
Black hole attack and false reporting
A malicious node advertises itself as the shortest path to the destination. Once the surrounding nodes start routing their packets through this node, it drops them, creating a “black hole” in the network. Such nodes can generate and send false data or alarms to mislead the network or drain the resources of other nodes and surface stations. The attacker deploys nodes in the network that mimic the identity of legitimate nodes. This can lead to data integrity issues and can compromise network operations.
Sybil attack
A single malicious node presents multiple identities to the network, potentially affecting voting-based schemes, redundancy mechanisms, or data aggregation processes. An attacker uses two or more malicious nodes to create a shortcut in the network. This can disrupt the normal functioning of routing protocols and can be used to capture a significant portion of the network traffic.
Energy consumption model
Our energy consumption model considers the energy required for data transmission, reception, processing, and sensing in UWSNs. Transmission energy \(\left({E}_{tx}\right)\) is calculated as \({E}_{tx}={E}_{elec}\times\:k+{E}_{amp}\times\:k\times\:{d}^{2}\), where \({E}_{elec}\) is the energy per bit for the circuitry, \({E}_{amp}\) is the amplifier’s energy, \(k\) is the number of bits, and \(d\) is the distance. Reception energy \({(E}_{rx})\)is \({E}_{elec}\times\:k\). This model helps evaluate the network’s energy efficiency and longevity.
Signal transmission model
The signal transmission model accounts for acoustic signal attenuation and the Signal-to-Noise Ratio (SNR) in underwater environments. Attenuation is modeled as \(A(d,f)={d}^{n}\times\:\alpha\:\left(f\right)\), where \(n\) is the spreading factor, and \(\alpha\:\left(f\right)\) is the absorption coefficient. SNR is calculated by considering transmission power and ambient noise, which affect the Bit Error Rate (BER). These factors are critical for assessing the reliability of underwater communication.
Trust evaluation process
In this section, we present the trust evaluation process. Trust evaluation is a critical component in UWSNs to ensure reliable data communication and mitigate the effects of malicious nodes. It involves assessing the trustworthiness of nodes based on their behaviors and past interactions.
Data acquisition and preprocessing
Before trust can be evaluated, relevant data regarding the behavior and interactions of nodes must be acquired and processed to be used effectively. Briefly describe the data acquisition and preprocessing steps are described in Table 6. The data acquisition and preprocessing steps lay the foundation for the subsequent trust evaluation. By ensuring that the data is comprehensive, consistent, and relevant, the trust evaluation process can yield more accurate and reliable results.
Trust score computation
Trust score computation is a systematic process that quantifies the trustworthiness of nodes based on their behaviors, interactions, and other relevant attributes.
Attribute evaluation
Before computing the trust score, it’s essential to evaluate the attributes that influence trust:
-
Behavioral Reliability (BR): This attribute measures the consistency of a node’s behavior over time. For instance, a node consistently forwarding packets would have a high BR score.
-
Interaction Success Rate (ISR): This measures the success rate of interactions between nodes, such as successful data transmissions.
-
Energy Sustainability (ES): Given the importance of energy in UWSNs, this attribute evaluates a node’s energy consumption pattern, indicating its potential longevity in the network.
-
Feedback Score (FS): Based on feedback from neighboring nodes, this attribute provides a peer-based perspective on a node’s trustworthiness.
Score calculation using the modified decision tree
Once the attributes are evaluated, they are fed into the modified decision tree to compute the trust score. Node attributes for evaluation are (BR, ISR, ES, FS). The modified decision tree uses energy-aware splits, acoustic signal metrics, and other tailored modifications to traverse the tree and reach a decision node. The trust score is between 0 (completely untrustworthy) and 1 (completely trustworthy).
where \({w}_{1}\), \({w}_{2}\), \({w}_{3}\), and \({w}_{4}\) are the weights assigned to each attribute based on their importance in the trust evaluation process. The sum of all weights is equal to 1. The trust score computation process ensures that nodes’ trustworthiness is quantified based on multiple attributes, providing a comprehensive and reliable measure that can be used for decision-making in UWSNs.
Dynamic update model
In this section, we propose a dynamic update model. The dynamic update mechanism is crucial for maintaining the accuracy and relevance of trust scores in a UWSN, as it adapts to nodes’ changing behaviors and network conditions.
Triggers for trust score update
Trust scores need to be dynamically updated to reflect the current state of nodes. Several triggers can initiate a trust score update:
Time-based trigger
Trust scores are updated at regular intervals to incorporate recent behaviors and interactions.
where \(\varDelta\:T\) is the predetermined time interval for updates.
Behavioral change trigger
Significant changes in a node’s behavior, like a sudden drop in packet forwarding rate, can trigger an update.
where \(\varDelta\:B\) is the behavior change and \(\theta\:B\) is the threshold.
Network topology change trigger
Modifications in the network structure, such as adding or removing nodes, initiate a trust score reassessment.
Feedback-based trigger
Feedback from neighboring nodes about a particular node can also initiate a trust score update.
Handling false positives and negatives
False positives (misidentifying trustworthy nodes as malicious) and false negatives (failing to identify malicious nodes) can occur. Strategies to handle these are:
Adaptive thresholding
Adjust thresholds used in trust evaluation dynamically based on network conditions to minimize false classifications.
Feedback verification
Implement mechanisms to verify the authenticity and reliability of feedback received from other nodes to prevent misinformation.
Historical data analysis
Analyze nodes’ historical behavior to identify patterns and trends, which can help distinguish between temporary anomalies and genuine malicious activities.
Consensus mechanism
Herein, we employ a consensus mechanism where decisions are made based on the agreement of multiple nodes, reducing the likelihood of false classifications. Trust scores remain accurate and relevant through a dynamic update mechanism, providing a reliable basis for decision-making in UWSNs. The mechanism also minimizes the impact of false positives and negatives, enhancing the network’s security and functionality.
In the consensus mechanism, trust decisions are based on the agreement among multiple nodes. This reduces the likelihood of false classifications. The trust score \({T}_{i}\) for node iii is updated dynamically based on the consensus of \(N\) neighboring nodes.
Let \({T}_{i,n}\) be the trust score of node \(i\) as evaluated by neighboring node \(n\).
The consensus trust score \({T}_{i}\) is calculated as the weighted average of trust scores provided by \(N\) neighboring nodes:
where:
-
\({T}_{i}\) is the updated trust score for node \(i\).
-
\({T}_{i,n}\) is the trust score of node \(i\) as evaluated by the neighboring node \(n\).
-
\({w}_{n}\) is the weight assigned to the trust score provided by the neighboring node \(n\).
Dynamic update mechanism
The dynamic update mechanism ensures that trust scores remain accurate and relevant by incorporating feedback over time. If \({T}_{i}^{new}\) is the new trust score after feedback, it can be adjusted based on a feedback factor \(F\):
where:
-
\({T}_{i}\) is the current consensus trust score for node \(i\).
-
\(\alpha\) is the learning rate or adaptation factor.
-
\(F\) is the feedback from the consensus mechanism indicating the reliability of the current trust score.
This approach ensures that trust scores are continually refined based on the collective evaluation of multiple nodes, thus enhancing the security and functionality of the UWSN by minimizing false positives and negatives.
Experiments, simulation, and performance evaluation
In this section, we evaluate the proposed model as an indispensable step, shedding light on the resilience and efficiency of the proposed trust evaluation mechanism within UWSNs. By simulating real-world scenarios, the mechanism’s performance is critically assessed, offering a clear picture of its strengths and potential areas of refinement.
Experimental setup
In the experimental setup, the parameters were carefully selected based on established benchmarks from prior work and the specific requirements of our study. The node density of 500 nodes and their distribution across various depths were chosen to align with typical scenarios found in previous research on UWSNs, ensuring relevance and comparability to existing studies. The signal reach of 100 m is derived from studies on acoustic communication in UWSNs, where similar ranges have been shown to balance coverage and energy consumption effectively. This value was tailored to reflect the operational characteristics of the sensor nodes used in our simulations. The node mobility, with potential movements of up to 2 m/s due to underwater currents, is based on empirical data from prior research on underwater node behavior, chosen to realistically simulate the impact of environmental factors on network performance, which is crucial for evaluating the robustness of our proposed trust evaluation model. The 5% ratio of malicious nodes was selected to reflect conventional practices in WSN research while providing a challenging environment to stress-test our model. This ratio aligns with other studies investigating the resilience of WSNs to malicious behavior. Additionally, the standardized packet size of 512 bytes is consistent with widely accepted benchmarks, ensuring that our simulation results are comparable to existing studies while meeting the specific data transmission needs of UWSNs. These parameters were chosen to provide a realistic and rigorous evaluation of the proposed model, balancing the need for relevance to the broader field with the specific challenges posed by UWSNs.The significance of a robust performance evaluation in research, particularly when introducing innovative mechanisms such as the trust evaluation system for UWSNs, is paramount. It bridges the gap between theoretical constructs and practical applications, offering a holistic view of the mechanism’s potential and efficiency in real-world scenarios. Central to this assessment is the experimental setup, a meticulously designed framework that mirrors the intricate dynamics of UWSNs. The simulation environment, powered by sophisticated tools like NS-3, replicates the nuances of underwater communication. Within this simulated marine expanse, 500 sensor nodes are strategically positioned across various depths, with a select group of 10 designated as surface stations. The simulation captures the challenges of underwater acoustic communication, accounting for factors such as signal degradation and marine current-induced delays. To rigorously test the trust mechanism’s resilience, 5% of the nodes are coded to display malicious behaviors. However, the true essence of the simulation is captured by its governing parameters and the metrics that measure its outcomes. The node density is fixed at 500, with a signal reach extending up to 100 m. The marine environment’s unpredictability is reflected in the node dynamics, with currents potentially pushing nodes at speeds of up to 2 m/s. The adversarial component is represented by 5% of the nodes exhibiting malicious tendencies, and data packets in this network have a standardized size of 512 bytes. Table 7 encapsulates the parameters and metrics:
This structured performance evaluation offers a comprehensive insight into the trust mechanism’s capabilities, laying the groundwork for its potential deployment in real-world UWSN.
This study evaluates the proposed trust evaluation model under two distinct network scenarios: Homogeneous Network and Heterogeneous Network. In a Homogeneous Network, all sensor nodes are identical regarding hardware capabilities, energy resources, and communication protocols. This scenario assumes uniformity across the network, where each node has the same processing power, memory, battery life, and transmission range. The Homogeneous Network scenario allows us to assess the performance of the trust evaluation model in a controlled environment where variability in node characteristics does not influence the outcomes. This scenario is commonly used in WSN research to establish baseline performance metrics. Conversely, the Heterogeneous Network scenario introduces diversity among the sensor nodes. In this setup, nodes may vary in hardware specifications, energy capacities, and communication ranges. Some nodes might have more powerful processors or larger batteries, while others may have limited resources. This heterogeneity reflects real-world deployments where nodes with different capabilities are often deployed together to achieve specific objectives, such as balancing energy consumption or optimizing coverage. The Heterogeneous Network scenario is particularly important for evaluating the adaptability and robustness of the proposed trust evaluation model, as it must account for and manage the differing capabilities of the nodes effectively. These scenarios are crucial for understanding how the proposed model performs under different network conditions, from a uniform network environment to a more complex and varied one. By testing the model in both Homogeneous and Heterogeneous Networks, we can better assess its generalizability and effectiveness in real-world UWSN deployments.
Results and discussion
The results derived from the performance evaluation serve as a mirror, reflecting the nuances and capabilities of the trust evaluation mechanism within UWSNs. By dissecting these results, we gain a deeper understanding of the mechanism’s prowess and potential areas of enhancement.
Accuracy of trust evaluation
The cornerstone of the trust evaluation mechanism is its accuracy. This metric gauges the mechanism’s proficiency in distinguishing between benign and malicious nodes, ensuring the integrity and security of the network. Table 8 illustrates the accuracy of malicious node identification across different network scenarios: homogeneous, heterogeneous, high traffic, and low traffic, each with 500 nodes. Notably, the system demonstrates accuracy, ranging from 92 to 96%, in identifying malicious nodes across all scenarios, albeit with minimal false positives.
Table 9; Fig. 5 provide malicious node identification across different network scenarios, revealing a false negative rate between 4% and 8% across Homogeneous, Heterogeneous, High Traffic, and low-traffic networks, each with 500 nodes. Despite the varied environments and malicious node counts, the system demonstrates a notable ability to identify malicious nodes with minimal missed identifications, reflecting a balance of accuracy and areas poised for improvement in diverse network conditions.
The results underscore the mechanism’s robustness, especially in diverse network conditions. The slight variations in accuracy across scenarios emphasize the mechanism’s adaptability. However, the false negatives, though minimal, highlight areas that could benefit from further refinement.
Figure 6 shows the accuracy trend in terms of time. We can chart a path forward by delving deep into these results, optimizing the trust evaluation mechanism to ensure a fortified and reliable UWSN environment.
Comparison with state-of-the-art model
The domain of UWSNs has witnessed a plethora of trust evaluation mechanisms. To ascertain the effectiveness of our proposed mechanism, it’s imperative to juxtapose it against mechanisms presented in existing research literature.
The proposed model merits become evident as shown in Table 10. It offers superior accuracy and boasts reduced data overhead compared to other mechanisms documented in recent research. The balance it strikes between power usage and response time further accentuates its potential for UWSN deployments.
Figure 7 shows the accuracy of the comparison of state-of-the-art models.
The proposed mechanism’s nuances shine when contextualized within UWSNs. Its efficient bandwidth utilization, signified by reduced data overhead and optimal power usage, ensures longevity in underwater deployments. The power usage distribution is mentioned in Fig. 8. Figure 9 shows the response trend over time. The proposed trust evaluation mechanism stands out. Its harmonized performance metrics and adaptability make it an optimal choice for fortifying UWSNs.
Network performance metrics
Network performance metrics provide a comprehensive lens through which the efficacy and efficiency of a system, especially in the context of UWSNs, can be assessed. These metrics offer insights into various facets of the network, from throughput and latency to energy consumption and scalability, as shown in Table 11.
From Table 11, the proposed mechanism demonstrates a competitive edge across various metrics. It achieves the highest throughput and scalability while ensuring minimal latency and energy consumption.
Figure 10 compares existing methods35,36,37 in terms of throughput in UWSNs. The throughput performance of different methods is in terms of Mbps. The proposed method demonstrates a slightly higher throughput of 5.3 Mbps, outperforming the existing method. Figure 11 presents the latency trends over time. Illustrates the latency trend over a series of time intervals. The graph shows a steady decrease in latency, starting from 20 milliseconds (ms) and gradually reducing to approximately 12 ms as time progresses. This downward trend indicates an improvement in the system’s responsiveness or efficiency, with latency consistently decreasing over the observed intervals. The overall trend suggests that the evaluated method or system is becoming more efficient in handling data transmission as time progresses.
Figure 12 shows the distribution of energy consumption by sensing, processing, communication, and idle. Scalability ensures the mechanism can handle the increased load as the network grows without compromising performance. The proposed mechanism’s network performance metrics underscore its robustness and adaptability. When benchmarked against contemporary research, it emerges as a front-runner, promising enhanced network performance and reliability in UWSNs.
Conclusion and future work
An underwater wireless sensor network with a proposed model can provide more secure, reliable, and efficient packet forwarding services. The proposed model leverages a modified decision tree algorithm incorporating several key innovations. The model prioritizes energy efficiency by considering the energy levels of sensor nodes during trust evaluations. This ensures trust computations do not overly deplete node resources, prolonging network lifespan. The model dynamically adjusts trust scores based on the changing underwater conditions by integrating environmental factors such as water currents and acoustic signal properties. This adaptability is critical in maintaining reliable and secure communication in UWSNs. The model supports real-time trust score updates triggered by changes in network topology, node behavior, or environmental conditions. This feature ensures that the trust management process remains responsive to the dynamic nature of underwater environments. The model demonstrates superior performance in trust accuracy, achieving a 96% accuracy rate with a 2% false positive rate. It also improves energy efficiency by 50 mW and reduces response time to 20 ms per packet, outperforming baseline models in various metrics. The proposed model significantly benefits UWSNs, enhancing network security and operational efficiency. By ensuring accurate and energy-efficient trust evaluations, the model contributes to the overall reliability and sustainability of UWSNs. Integrating environmental factors into the trust evaluation process sets a new standard for managing trust in such specialized and challenging environments. While the proposed model shows promising results, it is important to acknowledge certain limitations. The model’s performance was primarily validated through simulations, which, while comprehensive, may not fully capture all the complexities of real-world underwater environments. Future research should focus on deploying the model in real-world UWSN scenarios to validate its effectiveness further and identify any additional challenges. Additionally, the model does not incorporate advanced privacy-preserving mechanisms, which are increasingly important in trust management. Future work could explore integrating privacy-preserving techniques, such as differential privacy or secure multiparty computation, to enhance the model’s security features. Finally, while the model is designed explicitly for UWSNs, its principles could be adapted for other wireless sensor networks or IoT environments. Exploring such adaptations could broaden the impact of this research. Overall, this research significantly contributes to the field of UWSNs by introducing a novel, dynamic trust evaluation model that addresses the unique challenges of underwater environments. The model’s ability to enhance trust accuracy, energy efficiency, and adaptability to environmental changes represents a meaningful advancement in trust management for UWSNs. As UWSNs play a crucial role in various underwater applications, such innovations will ensure their security, reliability, and operational longevity.
Data availability
Data is provided within the manuscript or supplementary information files.
References
Levin, L. A. et al. Global observing needs in the deep ocean. Front. Mar. Sci.6, 241 (2019).
Li, N., Martínez, J. F., Meneses Chaus, J. M. & Eckert, M. A survey on underwater acoustic sensor network routing protocols. Sensors. 16, 414 (2016).
Zhu, F. & Wei, J. An energy-efficient routing protocol based on layers and unequal clusters in underwater wireless sensor networks. J. Sensors. 1–10 (2018).
Pal, A. et al. Communication for underwater Sensor networks: A comprehensive summary. ACM Trans. Sens. Netw. 19, 1–44 (2022).
Mohsan, S. A. H. & Amjad, H. A comprehensive survey on hybrid wireless networks: Practical considerations, challenges, applications and research directions. Opt. Quant. Electron.53, 523 (2021).
Shah, S. et al. Enhancing security and efficiency in underwater wireless sensor networks: A lightweight key management framework. Symmetry. 15, 1484 (2023).
Huang, D., Zhao, D., Wei, L., Wang, Z. & Du, Y. Modeling and analysis in marine big data: Advances and challenges, Math. Problems Eng. 2015 (2015).
Saeed, K. et al. A comprehensive analysis of security-based schemes in underwater wireless sensor networks. Sustainability. 15, 7198 (2023).
Doosti-Aref, A. & Arslan, H. Resource allocation optimization in Multiuser OFDM Relay-assisted underwater Acoustic Sensor Networks. Veh. Commun. 100625 (2023).
Du, J., Han, G., Lin, C. & Martinez-Garcia, M. ITrust: An anomaly-resilient trust model based on isolation forest for underwater acoustic sensor networks. IEEE Trans. Mob. Comput.21, 1684–1696 (2020).
Feng, R., Xu, X., Zhou, X. & Wan, J. A trust evaluation algorithm for wireless sensor networks based on node behaviors and ds evidence theory. Sensors. 11, 1345–1360 (2011).
Anwar, R. W., Zainal, A., Outay, F., Yasar, A. & Iqbal, S. BTEM: Belief based trust evaluation mechanism for wireless sensor networks. Future Generation Comput. Syst. 96, 605–616 (2019).
Wang, D., Yi, Y., Yan, S., Wan, N. & Zhao, J. A node trust evaluation method of vehicle-road-cloud collaborative system based on federated learning. Ad Hoc Netw.138, 103013 (2023).
Kaur, S. & Joshi, V. K. Hybrid Soft Computing technique based Trust evaluation protocol for Wireless Sensor Networks. Intell. Autom. Soft Comput.26 (2020).
Alsheikh, M. A., Lin, S., Niyato, D. & Tan, H. P. Machine learning in wireless sensor networks: Algorithms, strategies, and applications. IEEE Commun. Surv. Tutorials. 16, 1996–2018 (2014).
Xie, S., Hu, G., Wang, X., Xing, C. & Liu, Y. A Decision tree-based online traffic classification method for QoS routing in data center networks. Security Commun. Netw.2022 (2022).
Saeed, U., Jan, S. U., Lee, Y. D. & Koo, I. Fault diagnosis based on extremely randomized trees in wireless sensor networks. Reliab. Eng. Syst. Saf.205, 107284 (2021).
Mazidi, A., Mahdavi, M. & Roshanfar, F. An autonomic decision tree-based and deadline‐constraint resource provisioning in cloud applications. Concurrency Comput. Pract. Experience. 33, e6196 (2021).
Huang, H. et al. A review on underwater autonomous environmental perception and target grasp, the challenge of robotic organism capture. Ocean Eng.195, 106644 (2020).
Lin, M., Peng, L., Liu, T. & Zhang, L. Novel approach to energy consumption estimation in smart homes: Application of data mining and optimization techniques. Front. Energy Res.12, 1361803 (2024).
Han, G. et al. A synergetic trust model based on SVM in underwater acoustic sensor networks. IEEE Trans. Veh. Technol.68, 11239–11247 (2019).
Bangotra, D. K., Singh, Y., Selwal, A., Kumar, N. & Singh, P. K. A trust-based secure, intelligent, opportunistic routing protocol for wireless sensor networks. Wireless Pers. Commun.127, 1045–1066 (2022).
Zhang, D., Yu, F. R., Yang, R. & Tang, H. A deep reinforcement learning-based trust management scheme for software-defined vehicular networks, in Proceedings of the 8th ACM Symposium on Design and Analysis of Intelligent vehicular networks and Applications, 1–7. (2018).
Liu, Z. et al. PPRU: A privacy-preserving reputation updating scheme for cloud-assisted vehicular networks. in IEEE Trans. Vehicular Technol. (2023).
Goebel, R., Yu, H., Faltings, B., Fan, L. & Xiong, Z. Trustworthy Federated Learn, Vol. 13448. (Springer, 2023).
Huang, M., Zhang, K., Zeng, Z., Wang, T. & Liu, Y. An AUV-Assisted data gathering Scheme based on clustering and Matrix Completion for Smart Ocean. IEEE Internet Things J.7, 9904–9918 (2020).
Liu, R., Xie, M., Liu, A. & Song, H. Joint optimization risk factor and energy consumption in IoT networks with TinyML-enabled internet of UAVs. IEEE Internet Things J.11, 20983–20994 (2024).
Mejjaouli, S. & Babiceanu, R. F. RFID-wireless sensor networks integration: Decision models and optimization of logistics systems operations. J. Manuf. Syst.35, 234–245 (2015).
Vihman, L., Kruusmaa, M. & Raik, J. Systematic review of fault tolerant techniques in underwater sensor networks. Sensors. 21, 3264 (2021).
Khan, I. A., Ullah, F., Abrar, M., Shah, S. & Taj, F. M. I. K. Khalil, et al. Ransomware early detection model using API-calls at runtime by random decision forests.
Alhandi, S. A., Kamaludin, H. & Alduais, N. A. M. Trust evaluation model in IoT Environment: A Comprehensive Survey. IEEE Access. (2023).
Fattah, S., Gani, A., Ahmedy, I., Idris, M. Y. I. & Targio Hashem, I. A. A survey on underwater wireless sensor networks: Requirements, taxonomy, recent advances, and open research challenges. Sensors. 20, 5393 (2020).
Park, S., Byun, J., Shin, K. S. & Jo, O. Ocean current prediction based on machine learning for deciding handover priority in underwater wireless sensor networks. in 2020 International Conference on Artificial Intelligence in Information and Communication (ICAIIC), 505–509 (2020).
Ullah, F. et al. Modified decision tree technique for ransomware detection at runtime through API calls. Sci. Program. (2020).
Sathish, K., Ravikumar, C., Srinivasulu, A., Rajesh, A. & Oyerinde, O. O. Performance and improvement analysis of the underwater WSN using a diverse routing protocol approach, J. Comput. Netw. Commun. 9418392 (2022).
Panahi, U. & Bayılmış, C. Enabling secure data transmission for wireless sensor networks based IoT applications. Ain Shams Eng. J.14, 101866 (2023).
Han, S., Liu, X., Huang, H., Wang, F. & Zhong, Y. Research on energy-efficient routing algorithm based on SWIPT in multi-hop clustered WSN for 5G system, EURASIP J. Wireless Commun. Netw. 49 (2021).
Acknowledgements
This research was supported by the Researchers Supporting Project number (RSP2024R244), King Saud University, Riyadh, Saudi Arabia.
Author information
Authors and Affiliations
Contributions
“Sabir Shah. Abdu Salam and Farhan Amin. wrote the main manuscript text and Asim Munir.Abdusalam.Faizan ullah.Hussain AlSalman and Qaisar Javeed prepared all figures . All authors reviewed the manuscript.”
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Shah, S., Munir, A., Salam, A. et al. A Dynamic Trust evaluation and update model using advance decision tree for underwater Wireless Sensor Networks. Sci Rep 14, 22393 (2024). https://doi.org/10.1038/s41598-024-72775-4
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-024-72775-4
Keywords
This article is cited by
-
Exploration of contemporary modernization in UWSNs in the context of localization including opportunities for future research in machine learning and deep learning
Scientific Reports (2025)
-
Trust model for hybrid security attack mitigation in underwater acoustic wireless sensor networks using LSTM and whale optimization algorithm
Proceedings of the Indian National Science Academy (2025)
-
Theoretical modelling for optimised energy efficiency in IoUT networks using hybrid QL-based meta-heuristic and MCDM approaches
Discover Internet of Things (2025)