Abstract
The emergence of 6G cognitive radio IoT networks introduces both opportunities and complexities in spectrum access and security. Blockchain technology has emerged as a viable solution to address these challenges, offering enhanced security, transparency, and efficiency in spectrum management. This survey paper offers a thorough analysis of recent advancements in blockchain-enabled security mechanisms specifically for spectrum access within 6G cognitive radio IoT networks. Covering literature from 2019 to the present, the paper highlights significant contributions and developments in integrating blockchain technology with cognitive radio and IoT systems. It reviews spectrum access security and shows how blockchain’s decentralized approach can solve related issues. Key areas of focus include secure authentication systems, tamper-resistant spectrum sensing, decentralized databases, and smart contracts for spectrum management. The paper also addresses ongoing challenges like interoperability, scalability, and the need for comprehensive security frameworks. Future research directions are proposed, emphasizing the development of advanced blockchain protocols, integration with machine learning, and addressing regulatory and standardization concerns. This paper provides valuable insights for researchers and practitioners aiming to leverage blockchain technology, alongside ML/AI, to enhance security and efficiency in next-generation cognitive radio IoT networks.
Similar content being viewed by others
Introduction
As we enter the intelligent information age, sixth-generation (6G) networks promise to transform wireless communication, addressing challenges faced by current fifth-generation (5G) networks1. 6G will introduce highly flexible, scalable architectures, enabling applications in autonomous systems and smart cities2,3.
As globalization progresses, the amount of mobile data traffic is increasing at a fast and exponential rate. According to an ITU-R estimate, the monthly worldwide mobile data traffic was recorded at 390 exabytes in 2024 and is expected to reach 5016 exabytes by 20304. The Internet of Things (IoT) plays a key role in this transition, with 6G-enabled IoT ensuring reliable communication for billions of devices5.
The number of IoT devices is projected to grow from 15.4 billion in 2023 to over 29.4 billion by 20306. As IoT develops, 6G is set to exceed the limitations of 5G, boasting ultra-fast data rates, minimal latency, extensive coverage, precise localization, and supporting massive machine-type connections. Predicted to be approximately 1000 times faster than 4G and 100 times faster than 5G, 6G also promises enhanced network coverage and reliability7. The advent of 6G-IoT presents challenges in ensuring efficient spectrum access (SA) for diverse devices. With traditional narrow-band IoT (NB-IoT) unable to fully utilize spectrum resources, addressing scarcity becomes crucial for optimal performance in 6G networks.
The rapid proliferation of IoT devices exacerbates concerns about spectrum availability5,7,8. Cognitive Radio (CR) networks offer a promising solution to spectrum scarcity by sensing and utilizing unoccupied spectrum, known as spectrum holes9. CR within mobile communication networks is viewed as an emerging technology for implementing spectrum access and sharing mechanisms, to achieve optimal spectrum utilization10,11. The main concept of Cognitive Radio-enabled Internet of Things (CR-IoT) devices is to exploit unused spectrum (spectrum holes) and dynamically allocate it to secondary cognitive IoT devices, allowing them to opportunistically transmit data, thus enhancing overall spectrum utilization by enabling unlicensed users to access spectrum not in use by licensed users8,12,13.
Incorporating CR into IoT has paved the way for extensive connectivity within IoT networks, pledging to accommodate an unparalleled multitude of sensors and devices14. Integrating Cognitive Radio into 6G networks improves spectrum access efficiency and network performance, essential for IoT networks, by enabling dynamic spectrum allocation for diverse applications, but also introduces new security and privacy challenges15.
Blockchain technology (BCT) emerges as a significant player in bolstering the security of spectrum access within these networks, the integration of blockchain and 6G results in heightened security, expanded bandwidth, and decreased operational and capital expenditures16. Integrating blockchain technology with IoT systems enhances security by encrypting and digitally signing IoT data as blockchain transactions. Additionally, it utilizes smart contracts to automatically update device firmware and address vulnerabilities17,18.
This study discusses advancements in blockchain-enabled security for spectrum access in 6G cognitive radio IoT networks. It explores how Blockchain can address security challenges such as spectrum management, interference, and authentication. The paper reviews recent research, presents Blockchain-enabled security solutions, and highlights future research directions. The paper is organized as follows: Sect. 2 outlines the survey methodology. Section 3 provides context on 6G networks, cognitive radio, IoT, and spectrum access security challenges. Section 4 offers an overview of blockchain technology and its relevance to spectrum access security. Following this, Sect. 5 discusses security challenges in 6G cognitive IoT networks. Section 6 shifts the focus toward potential solutions through Blockchain-Enabled Security Solutions, including decentralized identity management and smart contracts. Section 7 covers future research directions. Finally, the paper concludes with Sect. 8, summarizing key findings and recommendations.
Survey methodology
The literature review approach for this research entails a systematic and comprehensive examination of recent advancements in blockchain-enabled security mechanisms for spectrum access in 6G cognitive radio IoT networks. The review focuses on studies published from 2019 to the present to ensure the inclusion of the latest developments and trends in the field. A structured search strategy is employed, utilizing databases such as Springer, IEEE Xplore, Google Scholar, Elsevier, ScienceDirect, MDPI, and IJRPR. Keywords such as “blockchain technology,” “6G networks,” “cognitive radio,” “IoT,” “spectrum access attacks,” and “smart contracts” are used to identify relevant literature. The initial screening involves reviewing titles and abstracts, followed by a full-text assessment to evaluate the relevance and contributions of each paper. This approach guarantees a thorough and up-to-date review of the literature, capturing key advancements and emerging trends.
Selection criteria for papers & sources
The selection criteria ensure that the review is comprehensive and relevant by including papers that focus on integrating blockchain technology with cognitive radio and IoT systems for spectrum access security. Only papers published from 2019 onward and sourced from peer-reviewed journals and reputable conferences are considered. The process encompasses various types of research—such as theoretical, empirical, case studies, and reviews—to provide a well-rounded perspective.
Scope and the contribution of the survey
This paper explores scholarly articles pertinent to the topic, emphasizing the substantial impact of blockchain technology on the security landscape of 6G cognitive radio IoT networks. Table 1 provides a comparative analysis of significant research in this field. Jahid et al.1 advocated blockchain integration in 6G and IoT to address 5G data challenges, benefiting IoT security and Industry 4.0. Pajooh et al.2 discussed the integration of blockchain in 6G IoT for decentralized access control and security, laying the groundwork for Industry 5.0. Xu et al.19 highlighted blockchain’s role in improving resource management and spectrum efficiency in 6G networks. Al-Dulaimi et al.20 examined cognitive radio’s role in alleviating spectrum scarcity in IoT, while Khasawneh et al.21 reviewed CRN-IoT systems to meet wireless communication demands.
Zainuddin et al.22 explored blockchain’s security enhancements in IoT networks, focusing on supply chains, healthcare, and smart cities, while addressing challenges like scalability and privacy. Bhaskar et al.23discussed how cognitive radio optimizes spectrum use in IoT, and Mathew24 highlighted the integration of edge computing and blockchain in 6G, emphasizing security challenges and emerging technologies like quantum computing.
However, while existing surveys focus on 6G IoT and blockchain integration, there is a gap in addressing blockchain’s role in spectrum access security for 6G cognitive radio IoT networks. Our survey fills this gap by analyzing recent developments, practical examples, and challenges in this area. It also presents a taxonomy of threats to spectrum access security and counter-threat technologies, providing valuable insights for researchers and practitioners in this specialized field.
Sixth-generation (6G) networks and spectrum access security
This section introduces key topics in advanced communication technology, including 6G networks, cognitive radio, IoT, and spectrum access security, establishing a framework for detailed analysis in subsequent sections.
Sixth-generation (6G) communication networks
The evolution of wireless technology has dramatically transformed communication, progressing from voice-only 1G networks to the high-speed, low-latency 5G. With each generation emerging roughly every decade, 6G is expected around 203025,26. Wireless technology has continually improved spectrum use, efficiency, reliability, and data rates27.
As of 2022, there were nearly 1 billion 5G subscriptions globally, with forecasts predicting growth to 4.7 billion by 202828. 5G’s innovations, such as ultra-reliable low-latency communication (URLLC), massive MIMO, and millimeter-wave (mmWave), enable applications like VR, UAVs, IoT, and autonomous vehicles, offering multi-gigabit speeds and millisecond latency27,29,30. However, the growing demand for smart devices and IoT is pushing 5G infrastructure to its limits31.
Research is now focused on 6G, which aims to enhance connectivity and security, supporting IoE applications with data rates of up to 1 Tb/s and latency under 1 ms. 6G will operate at frequencies that enable ultra-high-speed transmission, reliable communication, and advanced integration, such as satellite networks and AI-driven systems31,32,33,34.
This will further improve QoS, energy efficiency, and bandwidth, supporting the exponential growth of IoT devices and driving seamless interactions across interconnected networks35,36. To meet growing data demands, 6G expands into higher frequency bands like mmWave, terahertz (THz), and optical spectrums. While 5G uses 3 GHz to 6 GHz and mmWave (24 GHz to 50 GHz), 6G reaches THz and optical bands, boosting data rates by 100 to 1000 times. Regulators are now exploring frequencies like cmWave (3 to 30 GHz) and mmWave (30 to 300 GHz) to ease congestion37,38. The THz band (0.3 THz to 10 THz) bridges mmWave and infrared, with the 275 GHz to 300 GHz range overlapping mmWave37,39,40.
Cognitive radio and IoT networks
As 6G networks promise significant advancements in speed, connectivity, and latency, they face the challenge of spectrum scarcity due to the increasing number of connected IoT devices41, i.e., when massive IoT terminals access the spectrum for mobile communications, serving tens of thousands of users, available spectrum resources become limited, jeopardizing communication requirements for each terminal7,8. Cognitive Radio Networks (CRNs) provide a solution by enhancing spectrum allocation and utilization for IoT, addressing the limited availability of frequency resources13.
Currently, spectrum bands are underutilized by licensed holders (primary users, PUs)23, Cognitive radio (CR) technology, through opportunistic spectrum access, can alleviate bandwidth scarcity and improve spectrum efficiency42. CR monitors available spectrum in real-time, allowing secondary users (SUs) to access idle bands without interfering with PUs43. This enables spectrum sharing, with PUs retaining priority while SUs access unused frequencies without causing harmful interference44,45.
Spectrum sharing requires CRs to detect underutilized bands, enabling dynamic access46. Spectrum sensing identifies available channels, often referred to as spectrum holes, for CR access. When a PU signal is detected, CR systems must transition smoothly from the occupied channel42,47,48. CR can operate under interweave, underlay, or overlay paradigms. In underlay, SUs transmit at low power to avoid interference, while in overlay, they generate orthogonal signals to coexist with PUs. In interweave, SUs access the spectrum only when PUs are inactive49,50.
Dynamic spectrum access (DSA) allows flexible use of licensed bands, enabling smart radios (cognitive radios) to opportunistically share spectrum51. The growing number of IoT devices demands dynamic spectrum strategies, as static allocation results in low utilization. DSA has been proposed as a method to improve spectrum usability by exploiting spectrum holes and enhancing real-time network resource management42,52,53,54.
Spectrum access security
The integration of CR technology into 6G networks promises to enhance spectrum access efficiency and improve overall network performance. In 6G Cognitive Radio-Driven IoT Networks, dynamic and efficient spectrum allocation is crucial for supporting a diverse range of devices and applications. As the demand for high-speed data transfer increases and IoT devices proliferate, advanced spectrum access techniques become essential. However, the dynamic nature of spectrum access also introduces new challenges, including security and privacy threats. Protecting privacy is vital in CR networks, where data can be lost, stolen, or compromised. These networks are particularly sensitive to security threats due to inadequate cooperation between primary and secondary users. Additionally, the reliance on sensing information and machine learning in CR systems can lead to errors if the environment is misinterpreted, allowing malicious attacks to exploit these vulnerabilities with potentially long-lasting effects55,56. Attacks and threats to spectrum access in 6G cognitive radio-based IoT networks will be discussed in the next Section.
Blockchain technology overview
Blockchain technology has gained significant adoption in academia and industry due to its efficiency, particularly for distributed applications in 6G and industrial IoT. It transforms traditional centralized systems with key features like decentralization, immutability, transparency, and peer-to-peer communication1,57. Introduced by Satoshi Nakamoto in 2009 with Bitcoin, blockchain creates a secure, trustless network for decentralized peer-to-peer interactions58.
Blockchain operates as a decentralized network where nodes (personal computers) maintain and update transaction data. It includes key components like blocks (data units), nodes (computers), and miners (validators), ensuring reliability by continuously sharing data across the network59. Han et al.60 describe blockchain as a protocol for recording transactions rather than a standalone technology. Unlike the Internet, blockchain allows ownership transfer between parties.
As a distributed ledger, blockchain guarantees persistent, immutable, and consistent transaction records through public key cryptography, hashing, and distributed consensus. Timestamped blocks are cryptographically linked, creating an unalterable chain. Each node holds a copy of the ledger, ensuring a consistent view for all participants2,61,62. Blockchain enables seamless data transfer while maintaining data integrity63. As illustrated in Fig. 1, Blocks are organized using a Merkle tree, with hash pointers linking them securely64.
The four main pillars of blockchain technology are consensus, distributed ledger, cryptography, and smart contracts2. Consensus mechanisms (CM) ensure a clear transaction order and integrity across distributed nodes, influencing factors like throughput, latency, scalability, and security. Common consensus algorithms include Practical Byzantine Fault Tolerance (PBFT), Proof of Work (PoW), and Proof of Stake (PoS), each tailored to blockchain’s specific needs and performance criteria19,26. Blockchain records all transaction data in an immutable shared ledger. Transactions are grouped into blocks, which are sequentially linked and added to the ledger at regular intervals2,65.
Smart contracts are specialized codes stored on the blockchain that execute predefined instructions automatically, enhancing transaction efficiency and enabling flexible agreements. In 6G networks, they have the potential to improve network management and user-operator agreements1,26,66. Cryptography secures the blockchain, ensuring transaction integrity, user authentication, and confidentiality. Blockchains can be public/private or permissionless/permissioned, with varying levels of control over participation64,67,68.
Simplified blockchain structure69.
Security features of the blockchain
Blockchain uses a decentralized ledger to track changes and transfers, ensuring data integrity, trust, and resistance to attacks70. Key security features that benefit 6G networks include:
Decentralization
Blockchain’s distributed architecture minimizes reliance on centralized authorities, enhancing fairness and security. Consensus protocols (e.g., PoW, PoS, BFT) validate transactions, ensuring system integrity and trust70,71. PBFT, in particular, is considered highly suitable for energy internet applications72.
Immutability
Once recorded, blockchain data cannot be altered without majority node consent. Cryptographic hashing and block linking make historical data resistant to changes during the mining process67.
Transparency
Transactions are transparent to all participants. Updates require consensus, ensuring agreement among legitimate parties before any changes occur73.
Anonymity
Blockchain provides a degree of anonymity using recipient IDs, though complete privacy isn’t guaranteed. Each transaction block includes a unique cryptographic hash, linking it to previous blocks and preventing modifications67,70.
Cryptographic security
Blockchain employs cryptographic functions like SHA-256 to secure data, linking each block to its predecessor. Altering a block requires recalculating subsequent hashes, making tampering computationally impractical71.
Traceability
Blockchain’s timestamp feature ensures data reliability through encryption and signatures. Detailed transaction traceability improves transparency and allows for better monitoring in supply chains or financial systems1.
Relevance to spectrum access security
Current spectrum access techniques rely on centralized control, leading to issues like bias, distrust, data exposure risks, increased communication overhead, and challenges in interference management. Blockchain provides a decentralized solution by automating resource sharing, implementing fair incentives for operators, facilitating equitable resource trading, and ensuring unbiased spectrum access52. Integrating blockchain with cognitive radio technologies enhances transparency and trust in spectrum allocation through decentralized security, while CR optimizes spectrum utilization. For future 6G networks, ensuring the scalability and interoperability of blockchain is crucial, requiring effective integration techniques with CR platforms and spectrum environments74.
Blockchain improves spectrum access security through cryptographic hashing and smart contracts, safeguarding data and automating permission management. Decentralization and immutability prevent tampering and eliminate single points of failure. Consensus mechanisms ensure data visibility and verifiability, creating persistent, auditable records for traceability. This paper examines the security challenges related to spectrum access in 6G networks employing cognitive radio for the Internet of Things, explores current blockchain-based security solutions, and identifies existing research gaps.
Challenges in spectrum access security in 6G cognitive IoT networks
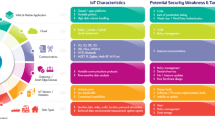
In 6G CR-IoT networks, security against unauthorized interference and ensuring data integrity are critical due to dynamic spectrum management and the growing number of connected devices. This section highlights key challenges, including data privacy, interference management, and the need for scalable, resilient solutions. Addressing these is vital for maintaining reliability and safety in 6G networks.
Spectrum sensing security
IoT applications rely on reliable, high-throughput connections, and spectrum sensing (SS) is essential for opportunistic access in spectrum-scarce environments44. CR networks use SS to identify available spectrum holes before transmission, helping manage underutilization75. Ensuring the integrity of spectrum sensing data is crucial, but it remains vulnerable to attacks.
Nasser et al.76 explore how learning techniques improve spectrum sensing and address security challenges. Furthermore, Aslam et al.55 discuss the vulnerabilities of CRs to data compromise, including potential destruction, eavesdropping, or unauthorized alteration. They also explore how attackers can disrupt transmissions from PUs or manipulate spectrum sensing data to favor SUs in channel access. Attacks such as SSDF exemplify these security challenges.
-
1)
Spectrum Sensing Data Falsification (SSDF) refers to situations in which attackers inject false sensing data into the network. This can result in inaccurate information regarding spectrum availability, prompting legitimate users to access occupied channels, which in turn causes interference and degrades service quality. Furthermore, malicious IoT devices can deliberately mislead the fusion center (FC) with false sensing results, leading to incorrect global decisions about the status of PUs77.
Authentication and access control
The application layer is crucial for securing IoT data through authentication, authorization, and restricting spectrum access to authorized devices25. The diverse nature of IoT devices complicates authentication, and unauthorized devices can cause interference and security breaches. Research focuses on improving these mechanisms to secure IoT systems.
According to Al-Sudani et al.44, a collision-free media access control mechanism is proposed that distributes channel sensing among users to enhance the performance of CR networks. Kokila et al.78 conducted a survey analyzing the latest authentication and access control mechanisms in the IoT, emphasizing the critical need for high levels of security, privacy, and resilience against attacks in this rapidly expanding domain. Their article offers a comprehensive review of the security challenges associated with IoT implementations. Below are the attacks most commonly linked to these security challenges.
-
1)
Unauthorized Access Attackers exploit weaknesses in access control to gain unauthorized entry to spectrum resources, risking data and user security25.
-
2)
Primary user emulation (PUE) attacks Malicious users mimic legitimate signals to mislead secondary users, causing interference and unauthorized access to spectrum79,80. These attacks degrade service quality, waste bandwidth, and may lead to Denial of Service (DoS)81.
-
3)
Replay Attack involves the retransmission of previously captured data16. These attacks compromise authentication by resending captured data to gain unauthorized access or manipulate controls. While they can indirectly affect spectrum allocation and resilience against jamming, their primary impact is on the integrity and security of authentication systems.
Privacy-preserving spectrum access
This involves strategies to protect IoT data by minimizing personal information collection while enabling secure data sharing82. Privacy preservation involves safeguarding sensitive data transactions from unauthorized malicious users (MUs) through various methods, including encryption, authentication, differential privacy, perturbation-based techniques, and blockchain technology80. During spectrum access involving sensitive information, it is crucial to implement encryption and privacy-preserving techniques to secure communication channels and prevent unauthorized data access.
Zainuddin et al.22 discuss privacy-preserving techniques using blockchain in 6G IoT networks. Vo et al.83 highlight AI-driven privacy threats in spectrum sharing for 6G. Below are the attacks most frequently associated with these security challenges.
1) EavesdroppingEavesdropping involves covertly monitoring communications to extract sensitive data, a heightened risk in IoT devices using shared spectrum. Attackers can intercept communications, compromising privacy, especially in critical applications. Machine learning can help detect eavesdropping patterns, improving IoT communication confidentiality and mitigating threats in 6G networks25,34
2) Location privacy attacks involve attackers utilizing spectrum access data to ascertain the physical location of users or devices, thereby raising significant privacy concerns. For instance, geolocation tracking entails analyzing spectrum usage patterns to estimate the locations of IoT devices, which can subsequently be exploited for targeted attacks or invasions of privacy. In cognitive IoT networks, where spectrum resources are shared, such attacks can result in considerable privacy and security challenges. Ahmed et al.84 provide an overview of location privacy attacks and propose solutions to address the issues these attacks present in IoT environments.
Jamming and interference resilience
Spectrum access in cognitive IoT networks is vulnerable to jamming and interference, where attackers intentionally disrupt communication. Jamming involves emitting disruptive signals, while interference includes any unwanted signals affecting communication.
1) Spectrum jamming attack: Involves transmitting noise into radio signals, disrupting communication and degrading the signal-to-noise ratio (SNR)85. According to86, jammers that share the wireless spectrum can be categorized into four main types: constant, deceptive, proactive/random, and reactive. Constant jammers continuously disrupt all network packets by emitting random signals, which are easy to detect and trace. Deceptive jammers transmit signals that mimic legitimate communications, making them traceable due to their consistent patterns. Both of these types require significant power. In contrast, proactive jammers alternate between active and idle phases without synchronizing with CR transmissions, while reactive jammers are more energy-efficient, activating only when they detect CR transmissions.
2) Coordinated co-channel interference attack: In this type of attack, malicious actors inundate the same frequency channel used by legitimate communications, thereby disrupting network operations. Managing interference in shared spectrum environments is challenging and necessitates strategies to minimize disruption while ensuring secure access for authorized users. According to87, a coordinated attack may involve multiple attackers conducting distributed scans to evade detection systems. This type of attack consists of two phases: cyber and physical. The authors examine both phases and propose a method that eliminates the need for complex manual rules or extensive prior knowledge to achieve effective results.
Dynamic spectrum allocation
Cognitive radio optimizes spectrum use by identifying and assigning unused frequency bands (“spectrum holes”). This involves algorithms to maximize usage, minimize conflicts, and maintain efficiency76,88.
Dynamic spectrum allocation in cognitive radio networks involves the frequent reallocation of spectrum to optimize usage, which can introduce vulnerabilities. Effective management requires regulating spectrum use, controlling interference, and implementing robust security measures. However, the frequent changes in spectrum availability can complicate the maintenance of secure access and pose challenges such as single points of failure, malicious activities, and other security issues12,89. Here are some key attacks that may impact DSA:
-
1)
Spectrum spoofing attack Attackers create false signals to mislead cognitive radios, making them believe certain spectrum bands are occupied or available, gaining unauthorized access or launching attacks90.
-
2)
DoS attackIn this type of attack, the perpetrator seeks to prevent users from accessing network resources and services84. DoS in CRNs occurs when all idle spectrum bands are compromised in a worst-case scenario involving PUE attacks. This prevents SUs from locating available spectrum, rendering the entire CRN incapable of serving any SUs81. In DSA, attacks primarily focus on DoS incidents. CR-based dynamic spectrum allocation methods in balancing minimal interference with optimal spectrum utilization, particularly due to malicious adversaries25.
-
3)
Collusion attacks Multiple malicious SUs collaborate to enhance the reputation of nearby nodes for their own benefit91. Collusion attacks occur when multiple attackers or malicious IoT devices collaborate to deceive the spectrum management system by providing false spectrum usage data. This undermines dynamic spectrum allocation and compromises spectrum access, particularly if security mechanisms are insufficient.
Each of these attacks can impair Dynamic Spectrum Allocation, leading to inefficient spectrum utilization, reduced network performance, and increased vulnerability to further attacks.
Secure spectrum database management
The CR is responsible for collecting the radio spectrum status from 6G networks and storing this information in databases74. This process enhances spectrum management by safeguarding incumbent users in white spaces92. Securing a database that contains spectrum information against unauthorized access and tampering is essential. A breach of this database could lead to incorrect spectrum allocation and unauthorized access by IoT devices.
According to26, blockchain can function as a secure and decentralized database for spectrum management, effectively recording all related activities. Spectrum database attacks target databases that manage spectrum information, which is crucial for allocating and controlling radio frequencies. These attacks can potentially compromise the security, integrity, and functionality of spectrum management systems.
-
1)
Injection attacks refer to attempts to alter or insert harmful code or data into existing systems93. These attacks involve malicious actors injecting harmful code or commands into the spectrum database or its interfaces. This category includes SQL Injection, which occurs when an attacker inserts malicious code into SQL statements to gain unauthorized access to the database and manipulate or extract data94, Another type is Command Injection, in which malicious commands are injected into the spectrum management system to alter its behavior. This can lead to unauthorized access, data modification, and disruptions in operations.
Trust and reputation management
Trust and Reputation Management (TRM) enhances security in networks, particularly in access networks. Trust refers to one entity’s belief in another, while reputation represents the collective opinion within a network community. TRM systems reward trustworthy behavior and penalize malicious actions, aiding in the detection and mitigation of harmful nodes to improve data authenticity and foster network collaboration95.
In decentralized environments, establishing trust among devices is challenging. Trust and reputation management are essential for secure spectrum access. Trust management facilitates reliable interactions among distributed nodes, while reputation management evaluates node credibility based on their behavior. These mechanisms optimize spectrum utilization, enhance network reliability, and mitigate security risks in dynamic settings. Sybil attacks are one of the significant challenges in this context.
-
Sybil attacks This type of attack is characterized by its ability to create fake nodes, referred to as Sybil nodes, which disrupt the network and lead to various issues96. Sybil attacks involve attackers creating multiple fraudulent identities or nodes to manipulate spectrum allocation and deceive the management system. This can result in unauthorized spectrum access and potential interference with legitimate users.
Intrusion detection and prevention
In 6G Cognitive IoT networks, Intrusion Detection and Prevention Systems (IDPS) are crucial for identifying and mitigating unauthorized access and malicious activities. These intelligent and robust systems utilize advanced techniques such as machine learning and artificial intelligence to analyze vast amounts of data from IoT devices and network traffic. By employing behavioral analysis, IDPS can detect subtle indicators of malicious activity that may evade traditional signature-based methods. They also enable real-time threat detection and response, streamline incident management, and coordinate actions across various security tools and teams.
In the dynamic and heterogeneous environments of 6G, IDPS must continuously adapt to emerging threats and vulnerabilities, thereby enhancing overall network security by detecting anomalies, preventing attacks, and ensuring data integrity and confidentiality97,98. Below is an example of an attack that is related to this challenge.
-
1)
Man-in-the-middle (MitM) attackis a type of cyberattack that enables an assailant to intercept and modify network traffic. This can result in the theft of sensitive data or the initiation of attacks on other connected devices90. By intercepting and manipulating communications between devices, an attacker can cause unauthorized data modifications or disrupt services.
Quantum-safe security
As 6G networks integrate with cognitive IoT systems, they must prepare for the implications of quantum computing, which could undermine traditional cryptographic methods such as RSA and Elliptic-Curve Cryptography (ECC). Implementing quantum-safe cryptography, including new algorithms and adaptations like enhanced AES key sizes and Quantum Key Distribution (QKD), is essential to safeguard against quantum threats and ensure robust privacy and data integrity in the face of future quantum threats99.
-
1)
Quantum-enabled cryptographic attacks These attacks could jeopardize 6G networks by undermining encryption and other security measures that are currently considered secure, utilizing quantum computers90. If quantum computers advance sufficiently, they could utilize Shor’s algorithm to compromise widely used public-key cryptographic systems such as RSA or ECC. This implies that an attacker equipped with a quantum computer could decrypt sensitive data encrypted with RSA or ECC, potentially exposing confidential communications and data within IoT devices and network infrastructure.
Figure 2 summarizes the challenges and potential attack examples discussed above. To address the security challenges in 6G cognitive radio–IoT networks, robust mechanisms such as secure spectrum access, authentication, and encryption are essential. Ongoing research and development will be crucial for identifying and mitigating emerging threats. Blockchain technology, along with other emerging technologies like artificial intelligence and secure hardware platforms, can significantly enhance the security of spectrum access. The following Section offers a comprehensive analysis of various blockchain-based solutions proposed in the literature, detailing how blockchain can improve the security of spectrum access in these advanced networks.
Recent advancements in blockchain-based research for spectrum access security
As 6G Cognitive Radio IoT networks continue to evolve, addressing security challenges is essential for ensuring reliable communication. These challenges, each revealing unique vulnerabilities to various attack vectors, highlight the necessity for robust security frameworks and protocols. Mitigating spectrum access attacks requires the implementation of secure protocols, cryptographic techniques, intrusion detection systems, and collaborative security measures. The integration of blockchain and Cognitive Radio technologies shows promise for enhancing transparency and trust in spectrum allocation while facilitating intelligent spectrum utilization. However, ensuring that blockchain systems are interoperable and scalable enough to meet the demands of 6G mobile communication—particularly when integrated with Cognitive Radio for efficient spectrum management—presents significant challenges. Blockchain’s decentralized and tamper-resistant model offers potential solutions, promising a more secure, transparent, and resilient framework for spectrum access. The integration of IoT and blockchain aims to optimize distribution within IoT, thereby enhancing the effectiveness of blockchain-based schemes in conjunction with 6G network architecture1,12,74.
This section offers a comprehensive analysis of nine blockchain-based solutions aimed at addressing security challenges and attacks associated with spectrum access. It emphasizes recent advancements in blockchain technology for secure spectrum sensing and access, while also identifying current research limitations.
Approaches for secure authentication and identity management
A recent study by Mughal et al.100 addresses the increasing interest in CRNs for spectrum sharing in IoT. It proposes a tree-centric approach using a Centralized Base Station (CBS) to dynamically allocate channels to Secondary Users, optimizing utilization and reducing interference. Simulations show the Channel Dynamic Control (CDC) mechanism provides channel access in one to two requests with an average delay of about 72 milliseconds.
The research conducted by Deepanramkumar et al.101 introduces BlockCRN-IoCV, which integrates authentication, density-aware clustering, dual-agent spectrum access, and secure beamforming to enhance security in the Internet of Connected Vehicles (IoCV). The authentication of primary and secondary users is achieved through blockchain technology, utilizing the Hybrid Advanced Encryption Standard and Hyper-elliptic Curve Cryptography (AES-HCC) algorithm. This process securely registers credentials such as ID, Physically Unclonable Function (PUF), and location. The secret key, generated by the hybrid AES-HCC algorithm, ensures the execution of authentication, effectively mitigating security threats posed by malicious secondary users.
Duraisamy et al.102 propose enhancing security in CRNs through the use of certificate linkable ring signature-based blockchains (CLRSB), which utilize cryptographic keys to identify trustworthy users. They implement a blockchain structure that incorporates smart contracts and public ledger principles, integrating PUs and SUs to improve spectrum sensing efficiency. Additionally, they apply the mayfly optimization algorithm (MFOA) and an improved convolutional neural network (ICNN) in spectrum sensing to reduce interference between PUs and SUs.
A paper by Sajid et al.103 proposes a blockchain-based method for detecting malicious users (MUs) in networks. This method differentiates MUs from legitimate users by utilizing cryptographic keys. If a user’s digital signature is verified, they are classified as Authenticated Users (AUs); otherwise, they are categorized as MUs. The process involves first verifying the public key and then the private key, both of which contribute to consensus on user validation. The efficiency of this mechanism is evaluated through MATLAB simulations, indicating its potential for authenticating participants in spectrum sensing processes within CRNs for IoT applications.
Venkatraman et al.104 propose a blockchain-based identity management system for computing assets within an IoT ecosystem, which integrates devices, software, users, and data operations. They develop a proof-of-concept prototype utilizing a federated and distributed blockchain platform with smart contracts, ensuring secure authentication and reliable data storage for IoT resources. This implementation aims to authenticate and authorize employee access to applications, systems, or networks by linking user rights and restrictions to established identities, thereby addressing the growing number of IoT devices within the organization’s network.
The Paper by V et al.34 proposes the Authentication and Acknowledgment (AA) approach to evaluate the effectiveness of a new 6G wireless security architecture. This architecture, which is based on secret key authentication and flexible position-based identification, establishes a foundation for assessing identity management and authentication. The authors demonstrate the advantages of this architecture by analyzing the Bit Error Rate (BER) in relation to the Signal-to-Noise Ratio (SINR) and measuring throughput across various SINR values. Additionally, the paper discusses the limitations of the proposed architecture and offers recommendations for enhancing security in 6G cellular networks.
Ghourab et al.105 propose a blockchain-based method for secure relay selection and spectrum access in cognitive radio systems. Their approach utilizes virtual wallets to manage spectrum access, assesses relay trustworthiness through a mathematical framework, and stores relay information on a blockchain. The system classifies relays based on cumulative intercept probability and digital signatures, thereby demonstrating enhanced security, credibility, and integrity.
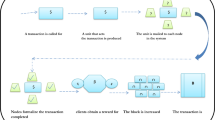
In summary, the reviewed works emphasize the use of blockchain and cryptographic techniques to enhance authentication and identity management in CRNs and IoT systems. These approaches improve spectrum management, mitigate malicious threats, and ensure secure, scalable solutions for 6G networks. Together, they highlight the critical role of secure authentication in next-generation wireless communications.
Figure 3 representing the authentication and identity management general framework for the related work. This diagram highlights the flow of processes starting from user registration and hybrid AES-HCC authentication, leading to blockchain ledger management, malicious user detection, certificate linkable ring signatures, relay trust assessment, and finally secure spectrum access. This framework shows how these components interact and contribute to the overall system for enhanced security and spectrum access management.
Tamper-resistant spectrum sensing data
Research conducted by106 investigates the use of CR to enhance spectrum efficiency in wireless multimedia communications, with a particular focus on spectrum sensing that enables SUs to identify vacant frequency bands. The study addresses the challenge posed by MUs who transmit false data, which degrades the performance of Cooperative Spectrum Sensing (CSS) and contributes to congestion in licensed bands. The paper proposes a blockchain-based CSS method to manage the spectrum and detect MUs, utilizing performance metrics such as sensitivity, node selection, throughput, and energy efficiency. This approach offers a more effective CSS solution with MU suppression, demonstrating a 15% improvement in MU detection when 40% of users are malicious, as indicated by simulation results.
Balakumar et al.107 focus on enhancing spectrum utilization in CR through blockchain-based spectrum detection methods. They evaluate the effectiveness of an energy sensor in detecting frequencies between 470 MHz and 790 MHz using additive white Gaussian noise (AWGN). Their study finds that the probability of detection (Pd) improves with an increased number of samples. Additionally, they introduce the M-ary Quadrature Amplitude Modulation (QAM) technique to enhance performance, reducing false alarms and missed detections by 5% during similar delay periods. The proposed method increases the likelihood of detecting a 3 dBm SNR for 64-QAM modulated signals by at least 15% compared to existing models, effectively addressing challenges such as shadowing and fading.
Marriwala et al.108 tackle the issue of spectrum scarcity by proposing CR as a solution to improve spectrum utilization. CR enables unlicensed secondary users to share the spectrum with licensed primary users without causing interference. This paper presents two key approaches: the Node Evaluation and Selection (NES) algorithm and a secure spectrum sensing mechanism. These approaches leverage blockchain technology to record user interactions and connection distances, thereby enhancing node selection and network security by mitigating attacks and improving spectrum efficiency.
Therefore, Hu et al.17 propose a blockchain-based dynamic spectrum access (DSA) framework in which secondary users conduct spectrum sensing and participate as miners and verifiers within the blockchain network, thereby eliminating the need for a central fusion point. Secondary users earn tokens for their contributions, which they can use to bid for spectrum access. The system’s efficiency is contingent upon its sensing, access, and mining policies. Simulations indicate that while higher probabilities of sensing and mining enhance transmission rates, they also increase energy consumption, highlighting the necessity for an optimal balance to achieve maximum efficiency.
The study conducted by Pari et al.9 integrates CRNs with the IoCV to address issues of spectrum scarcity and communication reliability. They propose a 6G CRN–IoCV approach along with a temporal-based logistic regression algorithm (STLR) to minimize collisions at intersections. Spectrum utilization is enhanced through spectrum sensing performed by SUs utilizing lightweight convolutional neural networks (Lite-CNNs), with encrypted reports transmitted to a fusion center. Optimal routing is achieved using the Dingo Optimization Algorithm (DOA) to increase throughput and packet delivery rates. Additionally, hybrid beamforming and a multi-agent-based categorical Deep-Q Network (categorical DQN) are employed to improve communication reliability and spectral efficiency.
In brief, these studies explore blockchain and CR-based methods to enhance tamper-resistant spectrum sensing. They focus on detecting MUs, improving spectrum efficiency, and ensuring secure spectrum access. Techniques such as Cooperative Spectrum Sensing, energy detection, node selection, and machine learning algorithms are employed to reduce false data and interference. Blockchain integration plays a key role in enhancing security and performance, demonstrating significant improvements in malicious user detection, throughput, and communication reliability across various CRN and IoT applications.
Decentralized spectrum database
Rather than relying on a centralized spectrum database that may be vulnerable to attacks, a blockchain-based decentralized ledger can be employed to manage spectrum information. This method renders the database tamper-resistant and trustworthy, significantly reducing the risk of data breaches. paper by62 examines the application of blockchain technology in radio spectrum management, with a particular focus on dynamic spectrum sharing applications. While blockchain technology has the potential to improve broader spectrum management, it functions as a decentralized database that allows data owners to retain control, distinguishing it from traditional cooperative approaches. Consequently, it is essential to explore how the database capabilities of blockchain could enhance the effectiveness of various spectrum-sharing methods.
Kotobi et al. n.d109. propose a blockchain verification protocol designed to enhance spectrum sharing in mobile cognitive radio networks and vehicular ad hoc networks (VANETs). By utilizing a virtual currency called Specoins and a decentralized auction mechanism, the protocol facilitates transactions and maintains a distributed database. Miner nodes earn Specoins for updating the blockchain, while non-miner CRs can lease spectrum through various methods. This system improves both efficiency and security, even in the presence of severe fading conditions.
Chen et al.110 highlight that traditional centralized platforms for electromagnetic spectrum monitoring suffer from significant data redundancy. They propose utilizing propagation loss and signal direction-finding data to enhance signal source estimation and introduce the Minimum Average Distance (MAD) method for improved collaborative detection in CRNs. Their solution incorporates a blockchain-based Distributed Electromagnetic Spectrum Database (BC-DSDB) and the Proof of High Confidence (POHC) consensus mechanism to manage and store data. Additionally, they introduce Spectrum Resource Currency (SRC) to prioritize secondary users and manage spectrum allocation during collisions. This approach reduces data redundancy and facilitates more effective spectrum access policies in distributed CRNs.
These approaches focus on using blockchain-based decentralized databases to enhance the security and efficiency of spectrum management. By replacing vulnerable centralized databases, blockchain creates tamper-resistant and trustworthy systems for managing spectrum information. Techniques such as Specoins, decentralized auctions, and the POHC consensus mechanism improve spectrum sharing and allocation in CRNs. This decentralized approach also reduces data redundancy and strengthens the integrity of spectrum databases.
Smart contracts for spectrum allocation
Smart contracts, which are self-executing programs on the blockchain, can automate and enforce spectrum allocation policies. This reduces the risk of unauthorized access and ensures compliance with established access rules. Research by61 proposes a blockchain-based platform that utilizes a digital token to manage spectrum access, track frequency usage, and prevent interference. Implemented on the Ethereum blockchain, this platform supports spectrum sharing through smart contracts, enabling automatic transactions and license transfers, which enhances both efficiency and trust.
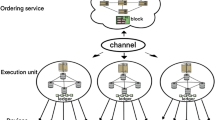
The Fig. 4 provides a detailed representation of the blockchain-based spectrum management framework proposed by Fan et al.53 to address spectrum utilization conflicts in Cyber-Physical-Social Systems (CPSSs). The framework consists of three planes: the Service Plane, Access Plane, and Transport Plane. The Service Plane includes a blockchain unit for ensuring data privacy and authenticity, a smart contract unit for automating third-party-free transactions, and a payment unit for managing users’ virtual wallets. This structure enables secure and efficient spectrum transactions, optimizing spectrum management for edge computing.
Blockchain-based spectrum management framework53.
Patel et al.111 propose Block6Tel, a blockchain-based scheme for secure and equitable 6G spectrum allocation. This system employs a 6G protocol stack and a blockchain auction algorithm utilizing smart contracts to facilitate transactions. Simulations demonstrate that Block6Tel outperforms traditional methods in terms of resource utilization, request overhead, and fairness.
In summary, these studies demonstrate the significant potential of smart contracts in automating and securing spectrum allocation. The approaches outlined not only improve efficiency and prevent interference but also ensure fairness and compliance with established policies. From managing license-free spectrum in CPSSs to optimizing 6G spectrum allocation, smart contracts are a promising solution for enhancing spectrum management in next-generation networks.
Secure communication with smart contracts
Communication between IoT devices and the spectrum management system, including smart contracts, can be secured through the use of blockchain technology. The integration of cryptographic techniques with blockchain ensures the confidentiality and integrity of communication channels, effectively preventing eavesdropping and unauthorized access. Recent research by Muhammad Asad et al.70 propose the integration of blockchain technology with private mobile networks to enhance next-generation train networks. By utilizing blockchain and smart contracts, their framework aims to improve security, privacy, and flexibility. This approach facilitates resource sharing and dynamic access, benefiting Beyond 5G (B5G) and 6G networks while promoting a decentralized future.
Rathod et al.89 explore the role of blockchain in enhancing security and reliability in 6G networks for applications such as autonomous vehicles and smart cities. Their study integrates AI, blockchain technology, and 6G to prevent data integrity attacks. They assess scalability and performance through the use of smart contracts and the Interplanetary File System (IPFS).
Study by Femenias et al.112 propose a dynamic spectrum sharing (DSS) scheme for cell-free massive MIMO networks, which enhances spectrum utilization. The scheme employs blockchain technology and smart contracts to ensure transparent and secure spectrum transactions. Participants utilize blockchain addresses for trading, while smart contracts manage the DSS protocol.
Raphaelle Akhras et al.113 propose utilizing an Ethereum-based blockchain and smart contracts to enhance the security of smart grid communication, ensuring both authentication and secure data reporting for smart meters. Simulations validate the security of this approach, but they also reveal challenges related to scalability and cost.
To summarize, integrating blockchain technology with smart contracts offers a robust solution for securing communication in IoT networks and beyond. These approaches effectively ensure data integrity, confidentiality, and secure resource sharing in dynamic and decentralized systems. From enhancing security in B5G and 6G networks to improving smart grid communications, the use of blockchain and smart contracts plays a crucial role in safeguarding communication channels and facilitating secure, transparent interactions.
Consensus mechanisms for decision-making
Blockchain consensus mechanisms like PoW or PoS ensure collective agreement on spectrum access decisions, thereby preventing manipulation by malicious actors. Recent paper by74 introduces Blockchain-based DSM for 6G Networks (BSM-6G), a novel spectrum management model designed to address scalability and interoperability challenges in 6G networks. Figure 5 illustrates the BSM-6G framework, which integrates blockchain with CR systems using an Oracle Interoperability Design to enable seamless communication between the blockchain and 6G cognitive sensing data. The model incorporates the Proof-of-History (PoH) consensus protocol for improved scalability and faster transaction validation. Additionally, the system features a Decentralized Application (dApp), which directly interacts with both the blockchain and CR modules, allowing SUs and PUs to securely access and share the available radio spectrum.
Hanwen Zhang et al.114 propose a novel distributed CBRS-Blockchain model to address the challenges associated with the Citizens Broadband Radio Service (CBRS) in 6G networks. Traditional CBRS encounters issues such as high administrative costs and privacy risks. The paper introduces a specialized consensus method called proof-of-strategy, which integrates with spectrum allocation to provide a robust consensus mechanism and mitigate the risk of single-point failures.
A recent study by Ameri et al.115 examines how AI can enhance blockchain technology, specifically focusing on consensus algorithms that ensure reliability in networks with untrusted nodes. The paper introduces a “cognitive blockchain” that utilizes the Cellular Game of Life (CGL) model to develop a new consensus protocol. This intelligent approach partitions nodes and verifies blocks, thereby improving fault tolerance, scalability, and performance while simultaneously reducing costs. Experimental results show the protocol effectively manages faulty nodes and improves scalability and throughput.
Blockchain-based consensus mechanisms such as PoW, PoS, and specialized protocols like Proof-of-History and Proof-of-Strategy play a critical role in securing spectrum access in 6G networks. These approaches ensure decentralized, transparent decision-making, effectively mitigating the risks of manipulation and enhancing network scalability. Models like BSM-6G, CBRS-Blockchain, and cognitive blockchain optimize spectrum allocation and management, addressing key challenges such as privacy concerns, interoperability, and fault tolerance, thus improving the overall efficiency and trustworthiness of spectrum management in next-generation networks.
BSM-6G spectrum management model for 6G networks74.
Immutable record of spectrum transactions
All spectrum transactions, including handoffs, can be recorded on the blockchain as immutable records. This guarantees a transparent and auditable history of spectrum access, making it more difficult for attackers to alter or tamper with previous transactions. Liang et al.116 investigate the integration of blockchain with Dynamic Spectrum Access DSA to improve spectrum management by leveraging the decentralization and tamper-resistance of blockchain technology. They propose a reference architecture that includes an interference-based consensus mechanism and a targeted validation system. Simulations demonstrate that these mechanisms enhance system fairness and Signal-to-Interference-plus-Noise Ratio (SINR), suggesting that blockchain provides a more secure and efficient solution for spectrum management.
Paper by Jain et al.117 propose a scheme to ensure the authenticity of Secondary Users by requiring them to deposit a monetary stake, with penalties for non-compliance. This approach secures transactions and maintains privacy in cognitive radio networks by utilizing blockchain-based smart contracts and a reputation system to evaluate user trustworthiness.
In summary, the use of blockchain for recording spectrum transactions ensures the creation of immutable and transparent records, which prevents tampering and enhances security. Research by Liang et al. and Jain et al. demonstrates how blockchain can improve spectrum management, from enhancing system fairness and SINR through decentralized consensus mechanisms to securing Secondary User transactions with smart contracts and reputation systems. These approaches offer reliable, tamper-resistant solutions for Dynamic Spectrum Access, ensuring both efficiency and trust in the spectrum sharing process.
Resilience against DoS attacks
Blockchain’s decentralized nature enhances resilience against denial-of-service attacks. Even if some nodes are compromised, the network’s distributed structure ensures continued operation, thereby strengthening the overall resilience of the spectrum access infrastructure. Xue et al.118 address the inefficiencies of Nakamoto consensus in spectrum management through their Spectrum Trading Blockchain (STBC) protocol, which enhances spectrum utilization and minimizes transaction delays. The STBC protocol incorporates a novel consensus mechanism, sharding for improved scalability, and privacy protection against DDoS attacks. It surpasses existing schemes by increasing spectrum utilization by 30% and reducing transaction delays by a factor of 125.
Recent research by Dansana et al.119 proposes a blockchain-based security model for Cognitive Radio Ad-hoc Networks (CRAHNs) aimed at enhancing attack resilience and QoS. The model employs a Mayfly Optimizer (MO) to efficiently select and deploy both active and redundant miners for secure data storage, thereby improving resource utilization and reducing costs. It effectively decreases communication delays by 18.5%, increases throughput by 19.5%, and enhances the Packet Delivery Ratio (PDR) by 19.4%, while also conserving 12.5% in energy. Additionally, the model incorporates protections against DDoS attacks and ensures high communication speed and efficiency.
Khorseed et al.120 propose utilizing Hyperledger Fabric to improve DDoS attack detection in Software-Defined Networks (SDNs) by compiling victim IP addresses into a blacklist and employing blockchain transactions to create a secure ledger. This approach enhances adaptability and flexibility, reduces mitigation times, and strengthens overall network security.
In conclusion, blockchain’s decentralized structure significantly enhances resilience against DoS attacks by ensuring continuous operation even when some nodes are compromised. Research by Xue et al., Dansana et al., and Khorseed et al. highlights various blockchain-based approaches that improve spectrum management, attack resilience, and QoS. These solutions, which include novel consensus mechanisms, sharding, and optimization techniques, successfully reduce transaction delays, improve spectrum utilization, and protect against DDoS attacks, strengthening the security and efficiency of the spectrum access infrastructure.
Privacy-preserving solutions
Blockchain can implement privacy-preserving features to keep sensitive spectrum access information confidential. Techniques such as zero-knowledge proofs and private transactions can be employed to protect the privacy of IoT devices. Research by Vuppula et al.80 proposed a novel Blockchain-oriented Location Privacy-preserving (BoLPP) framework for Cognitive Sensor Systems (CSS) in 6G networks. Figure 6 illustrates the BoLPP framework, which integrates blockchain with CRNs and employs energy detection techniques to enhance privacy and resilience against malicious attacks targeting Secondary Users. This approach addresses the challenge of maintaining privacy and security, outperforming existing methods like the Friend or Foe (FoF) and Tidal Trust Algorithm (TTA) across several metrics, including response time, consistency, false alarm probability, frame loss, network throughput, energy efficiency, and security.
The Paper by Manogaran et al.121 discusses the emerging 6G communication environment, which aims to deliver high throughput and low latency. Given the integration of diverse resources and standards, security has become a significant concern. The authors propose a blockchain-based integrated security measure (BISM) to enhance access control and user privacy. This measure utilizes virtualized resource states and Q-learning for dynamic access control, while privacy is preserved by optimizing service response longevity. Performance is evaluated using metrics such as true positives, access denial ratio, access time, memory usage, and time complexity. The BISM effectively enhances security by managing resource access and user privacy with minimal time and memory costs, achieving a high success rate and reducing false positives.
BoLPP framework for location privacy in 6G CSS networks80.
Nguyen et al.122 address the security and privacy challenges in the expanding IoT sector by proposing a privacy-preserving framework that combines Secure Ant Colony Optimization with Multi-Kernel Support Vector Machine (ACOMKSVM) and the Elliptic-Curve Cryptography (ECC). This approach utilizes blockchain technology to ensure data integrity and privacy during IoT data sharing. The system encrypts and records data on a distributed ledger, thereby protecting both data confidentiality and the parameters of the ACOMKSVM model. Performance tests conducted with datasets such as the Breast Cancer Wisconsin dataset and the heart disease dataset demonstrate superior results compared to existing methods.
To summarize, blockchain technology provides effective privacy-preserving solutions for spectrum access, ensuring the confidentiality of sensitive IoT data through methods like zero-knowledge proofs and private transactions. Research by Vuppula et al., Manogaran et al., and Nguyen et al. highlights blockchain-based frameworks that strengthen privacy, security, and access control in 6G and IoT systems. These approaches tackle privacy challenges effectively, offering improvements in metrics like energy efficiency, response time, and false alarm rates, while securing data integrity and confidentiality. The privacy-enhancing solutions presented show how blockchain can address security issues and improve the reliability of spectrum management.
Table 2 summarizes recent blockchain-based solutions developed to tackle the security challenges and attacks on spectrum access discussed above. It compares the various approaches based on the specific security challenges they address and the methods they employ, while also highlighting their limitations and potential future directions.
Future directions and research opportunities
By integrating blockchain technology into the security architecture of 6G Cognitive Radio IoT networks, it is possible to create a more secure, transparent, and resilient framework for spectrum access, effectively addressing many of the challenges and threats previously mentioned. However, it is important to recognize that blockchain alone is not a cure-all; its implementation should be viewed as a component of a comprehensive security strategy. Several potential challenges and future research directions still require attention, which are outlined as follows:
Advanced blockchain protocols for 6G networks
6G will surpass 5G by offering higher performance standards, including ultra-low latency, extremely high speeds, and support for a wide range of applications32. As 6G networks evolve to accommodate unprecedented numbers of devices and high-speed data transmission, particularly in cognitive IoT environments, blockchain protocols must also advance. To effectively manage the complexities of spectrum access in these dynamic, high-density 6G networks, blockchain solutions need to be highly scalable and capable of handling surges in transaction volumes and device interactions without compromising performance. This necessitates the optimization of consensus algorithms to reduce latency and enhance throughput. Hybrid consensus algorithms can improve both security and efficiency by integrating elements from various mechanisms. For instance, combining PoW with Delegated Proof of Stake (DPoS) enhances computational performance and security, with PoW responsible for block creation and DPoS overseeing block validation. Similarly, integrating PoS with PoW increases both security and decentralization. Additionally, combining DPoS with PBFT provides enhanced security, scalability, and efficiency123.
Additionally, Layer 2 scaling solutions, such as state channels and rollups, are essential for enhancing transaction speeds and reducing latency. State channels enable off-chain transactions that are recorded on-chain only, when necessary, while rollups consolidate multiple transactions into single batches, thereby increasing throughput and minimizing delays124. These advancements are essential for establishing blockchain as a viable solution for managing real-time spectrum access in the complex and high-demand environment of 6G networks.
Integration with machine learning for enhanced security
Integrating machine learning (ML) classifiers with blockchain technology presents a powerful strategy for enhancing security and efficiency in advanced networks such as 6G. This combination ensures the transparent and immutable recording of threats, providing a decentralized platform for sharing threat intelligence and executing automated responses, thereby strengthening the overall security infrastructure. By merging blockchain’s transparency with ML’s predictive capabilities, researchers can improve real-time threat detection and adaptive security measures.
Future research should prioritize the development of adaptive ML models that can adjust to evolving network conditions, as well as federated learning (FL) approaches that safeguard data privacy while incorporating insights into the blockchain for consensus and decision-making. Furthermore, ML can optimize blockchain consensus mechanisms and smart contract execution, enhancing spectrum management by predicting and mitigating threats and optimizing spectrum allocation. Employing ML and deep learning (DL) techniques—such as Decision Trees, Random Forests, Support Vector Machines (SVM), Neural Networks, and K-Nearest Neighbors (KNN)—in conjunction with blockchain can significantly improve spectrum management and overall security in cognitive radio networks. This integration also holds great promise for the IoT and 6G technology, offering enhanced security, privacy, and efficiency76,89,125.
Federated learning enables the training of models across decentralized devices while maintaining data privacy. Meanwhile, blockchain technology ensures that these insights are securely integrated for consensus and decision-making, making it especially effective in the vast landscape of the IoT126. Recent research demonstrates the effectiveness of secure federated deep learning in detecting false data injection attacks by combining Transformer-based detection, federated learning for collaborative training, and the Paillier cryptosystem to preserve data privacy127
Advanced cryptographic techniques
Advanced cryptographic techniques are essential for securing blockchain-based spectrum management in 6G cognitive radio IoT networks, where data integrity and privacy are paramount. As quantum computing poses a threat to traditional cryptography, research into post-quantum cryptography is vital for developing quantum-resistant algorithms.
Hybrid techniques that combine traditional cryptography with Quantum Key Distribution (QKD) or Post-Quantum Cryptography (PQC) provide enhanced security. For instance, symmetric encryption methods such as AES can be paired with QKD for secure key exchanges, while asymmetric methods like RSA or ECC combined with QKD improve key management and digital signatures. Zero-knowledge proofs further safeguard privacy by verifying transactions without revealing sensitive information. As 6G networks are expected to incorporate quantum communication, new strategies will be necessary to address quantum-specific properties, including QKD and quantum teleportation. Although QKD ensures secure key exchange, symmetric systems like AES are more resistant to quantum attacks compared to asymmetric methods like RSA and ECC, which are vulnerable to such threats128,128,130.
Thus, developing robust encryption methods and incorporating advanced security features such as quantum-resistant cryptography and network slicing, will be crucial for ensuring comprehensive protection for blockchain-based spectrum access in 6G cognitive IoT networks. As quantum computers become capable of breaking conventional cryptographic algorithms like RSA, (EC)DSA, and (EC)DH within a short time frame131. Integrating traditional cryptographic techniques with QKD or Post-Quantum Cryptography can significantly enhance the security of blockchain-based spectrum access systems. Each combination addresses specific aspects of cryptographic security, providing a multi-layered defense against both current and future threats, as illustrated in the Table 3.
Addressing regulatory and standardization challenges
Integrating blockchain technology for spectrum access in 6G networks presents regulatory and standardization challenges. Future research should align blockchain solutions with existing regulations and establish new guidelines for these technologies. Collaboration with standardization organizations such as IEEE and ITU-T is essential for creating interoperable protocols and security frameworks. The implementation of smart contracts can automate compliance with spectrum access regulations. A significant challenge is the lack of standardization, which results in interoperability issues among various blockchain systems. Therefore, developing comprehensive blockchain standards is vital to address this issue132.
Investigating the impact of regulatory requirements on blockchain deployments and developing strategies for compliance will facilitate broader adoption. This involves creating comprehensive regulatory frameworks that balance innovation with security and privacy concerns, establishing industry standards and best practices, and ensuring that blockchain solutions comply with both existing and emerging regulations12,25,129.
Standardization is essential for the advancement of 6G technology, with the European Telecommunications Standards Institute (ETSI) striving to keep pace with rapid developments. As discussions surrounding 6G progress even before the global adoption of 5G, updated standards are vital for ensuring seamless connectivity between networks and devices. Standardization bodies are dedicated to establishing independent standards for IoT and CRN, highlighting the necessity for cohesive and up-to-date regulatory and standardization efforts to address these challenges32,50.
Enhancing sustainability and energy efficiency
As blockchain technology becomes integrated into 6G networks, addressing its environmental impact is a significant concern. To minimize the carbon footprint of blockchain operations, future research should focus on developing energy-efficient algorithms and practices. For instance, transitioning from the energy-intensive PoW consensus mechanism to the less energy-consuming PoS method can lead to substantial energy savings. Energy efficiency is crucial for sustainable mobile communication, particularly in 6G and IoT networks where billions of devices are expected to connect and consume considerable amounts of energy133.
Exploring green consensus mechanisms, such as Proof-of-Authority (PoA) or PoS, which consume significantly less energy compared to PoW, is essential for reducing energy consumption in blockchain systems. In 6G networks, adopting PoS or Delegated Proof-of-Stake (DPoS) can significantly lower the overall energy footprint, which is particularly important for IoT devices with limited power resources. Furthermore, integrating blockchain with energy-efficient technologies and practices, such as lightweight blockchain protocols like IOTA’s Tangle or Hedera Hashgraph, can optimize resource usage, meet the demands of 6G networks, and minimize computational and storage requirements. These advancements will enhance the sustainability of spectrum access operations, aligning with the environmental goals of 6G networks134,135. Enhancing sustainability and energy efficiency in power systems can be further supported by incorporating advanced methods, such as spatio-temporal graph wavelet convolutional neural networks. These networks effectively detect and localize dummy data injection attacks (DDIAs) even in the presence of incomplete topological information, thereby maintaining grid stability and security136.
Implementation of cross-layer security approaches
To achieve comprehensive security in 6G cognitive IoT networks, it is essential to integrate blockchain technology across multiple network layers. Future research should investigate how blockchain can enhance security not only at the application layer but also at the physical, link, and network layers. This cross-layer integration could facilitate end-to-end security solutions that address various attack vectors and strengthen overall spectrum access security. For example, blockchain can safeguard physical layer signal processing from tampering and eavesdropping while ensuring transparency and trust at higher network layers. Furthermore, effective cross-layer security designs are critical for 6G, as they mitigate threats such as eavesdropping, DDoS attacks, and man-in-the-middle attacks. By leveraging cross-layer information, these designs reduce overhead, increase fault tolerance, and enhance power efficiency, making them particularly well-suited for resource-constrained and dynamic IoT networks137,138.
Real- world implementation and testing
Many blockchain-based solutions for 6G networks remain conceptual or experimental, posing challenges for practical deployment. Future research should prioritize pilot projects and testbeds to assess these solutions in real-world environments, documenting case studies and gathering data on performance, scalability, and security. Implementing blockchain in 6G networks necessitates addressing high costs associated with hardware, software, and training, as well as ensuring compatibility with existing spectrum management and security systems. Effective integration requires meticulous planning to guarantee compatibility and minimize disruption. Pilot projects can help identify potential issues and demonstrate feasibility prior to full-scale deployment. Successful integration will rely on collaboration among technology developers, network operators, and regulators to leverage insights from pilot projects for broader implementations.
Conclusion
This paper provides a comprehensive exploration of how blockchain technology can significantly enhance security for spectrum access within the context of advanced 6G cognitive radio IoT networks. By synthesizing research from recent years, it demonstrates how blockchain can address critical security challenges, such as efficient spectrum management, interference mitigation, and robust authentication. The discussion highlights blockchain’s potential through various solutions, including tamper-resistant spectrum sensing, decentralized databases, and smart contracts for dynamic spectrum allocation.
However, the paper also acknowledges the substantial challenges involved in integrating blockchain with 6G cognitive radio IoT networks, particularly regarding interoperability, scalability, and the development of comprehensive security protocols. It emphasizes that blockchain should be viewed as part of a broader security strategy rather than a standalone solution. Future research directions are identified, including the development of advanced blockchain protocols for 6G networks, integration with machine learning for enhanced security, exploration of advanced cryptographic techniques, and addressing regulatory and standardization issues. Overall, the paper underscores blockchain’s significant potential to revolutionize spectrum access security while recognizing the need for ongoing innovation and research to overcome existing challenges.
The datasets used and/or analyzed during the current study available from the corresponding author on reasonable request.
Data availability
We do not analyse or generate any datasets, because our work proceeds within a review approach. Example from: https://doi.org/10.1007/s11235-023-01079-1.
References
Jahid, A., Alsharif, M. H. & Hall, T. J. The Convergence of Blockchain, IoT and 6G: Potential, Opportunities, Challenges and Research Roadmap. (2021).
Pajooh, H. H., Demidenko, S., Aslam, S. & Harris, M. Blockchain and 6G-Enabled IoT, (2022).
Chataut, R., Nankya, M. & Akl, R. 6G networks and the AI Revolution—Exploring Technologies, Applications, and Emerging challenges. Sensors 24, 1888. https://doi.org/10.3390/s24061888 (2024).
BR: IMT traffic estimates. (2015).
Liu, X., Ding, H. & Hu, S. Uplink Resource Allocation for NOMA-Based hybrid Spectrum Access in 6G-Enabled cognitive internet of things. IEEE Internet Things J. 8, 15049–15058. https://doi.org/10.1109/JIOT.2020.3007017 (2021).
08. statistic_id1183457_number-of-iot-connected-devices-worldwide-2019-2023-with-forecasts-to-2030.
Qadir, Z., Le, K. N., Saeed, N. & Munawar, H. S. Towards 6G Internet of Things: Recent advances, use cases, and open challenges, (2023).
Khan, A. U. et al. Reliability Analysis of Cognitive Radio Networks with reserved spectrum for 6G-IoT. IEEE Trans. Netw. Serv. Manage. 19, 2726–2737. https://doi.org/10.1109/TNSM.2022.3168669 (2022).
Pari, D. & Natarajan, J. Secure Spectrum Access, Routing, and Hybrid Beamforming in an edge-enabled mmWave massive MIMO CRN-Based internet of connected vehicle (IoCV). Environ. Sens. 22 https://doi.org/10.3390/s22155647 (2022).
Liang, W., Zhang, J., Wang, D., Li, L. & Ng, S. X. NGMA-based intergrated communication and computing for 6G-enabled cognitive radio networks. IET Networks. https://doi.org/10.1049/ntw2.12102 (2023).
Fernando, X. & Lăzăroiu, G. Spectrum Sensing, Clustering Algorithms, and Energy-Harvesting Technology for Cognitive-Radio-Based Internet-of-Things Networks, (2023).
Reypnazarov, E. et al. Research of the application of blockchain and smart contract technologies in spectrum management and trading in cognitive radio networks. In: E3S Web of Conferences. EDP Sciences (2023).
Malik, T. S. et al. RL-IoT: reinforcement learning-based Routing Approach for Cognitive Radio-enabled IoT communications. IEEE Internet Things J. 10, 1836–1847. https://doi.org/10.1109/JIOT.2022.3210703 (2023).
Khaf, S., Alkhodary, M. T. & Kaddoum, G. Partially Cooperative Scalable Spectrum sensing in Cognitive Radio Networks under SDF attacks. IEEE Internet Things J. 9, 8901–8912. https://doi.org/10.1109/JIOT.2021.3116928 (2022).
Porambage, P. et al. The Roadmap to 6G security and privacy. IEEE Open. J. Commun. Soc. 2, 1094–1122. https://doi.org/10.1109/OJCOMS.2021.3078081 (2021).
Yadav, M. et al. Exploring synergy of Blockchain and 6G network for industrial automation. IEEE Access. 11, 137163–137187. https://doi.org/10.1109/ACCESS.2023.3338861 (2023).
Hu, S., Pei, Y. & Liang, Y. C. Sensing-Mining-Access tradeoff in Blockchain-enabled dynamic Spectrum Access. IEEE Wirel. Commun. Lett. 10, 820–824. https://doi.org/10.1109/LWC.2020.3045776 (2021).
Dai, H. N., Zheng, Z. & Zhang, Y. Blockchain for internet of things: a Survey. IEEE Internet Things J. 6, 8076–8094. https://doi.org/10.1109/JIOT.2019.2920987 (2019).
Xu, H. et al. Blockchain-enabled resource management and sharing for 6G communications. Digit. Commun. Networks. 6, 261–269. https://doi.org/10.1016/j.dcan.2020.06.002 (2020).
Al-Dulaimi, O., Al-Dulaimi, M., Al-Dulaimi, A. & Alexandra, M. O. Cognitive Radio Network Technology for IoT-Enabled devices †. Eng. Proc. 41 https://doi.org/10.3390/engproc2023041007 (2023).
Khasawneh, M., Azab, A., Alrabaee, S., Sakkal, H. & Bakhit, H. H. Convergence of IoT and Cognitive Radio networks: a survey of applications, techniques, and challenges. IEEE Access. 11, 71097–71112. https://doi.org/10.1109/ACCESS.2023.3294091 (2023).
Zainuddin, A. A., Omar, N. F., Zakaria, N. N. & Camara, M. Privacy-preserving techniques for IoT data in 6G networks with Blockchain Integration: a review. Int. J. Perceptive Cogn. Comput. 9, 80–92. https://doi.org/10.31436/ijpcc.v9i2.405 (2023).
Gowda, C. S. Cognitive Radio in IOT and Network Security. (2022).
Mathew, A. Edge Computing and its convergence with blockchain in 6G: Security challenges. Int. J. Comput. Sci. Mob. Comput. 10, 8–14. https://doi.org/10.47760/ijcsmc.2021.v10i08.002 (2021).
Rachakonda, L. P., Siddula, M. & Sathya, V. A comprehensive study on IoT privacy and security challenges with focus on spectrum sharing in Next-Generation networks (5G/6G/beyond). High-Confidence Computing 4, 100220. https://doi.org/10.1016/j.hcc.2024.100220 (2024).
Kalla, A., de Alwis, C., Porambage, P., Gür, G. & Liyanage, M. A survey on the use of blockchain for future 6G: Technical aspects, use cases, challenges and research directions, (2022).
Mathew, A. Artificial Intelligence and Cognitive Computing for 6G Communications & Networks. Int. J. Comput. Sci. Mob. Comput. 10, 26–31. https://doi.org/10.47760/ijcsmc.2021.v10i03.003 (2021).
Taylor, P. Forecast number of mobile 5G subscriptions worldwide from 2019 to 2028. (in billions). https://www.statista.com/statistics/760275/5g-mobile-subscriptions-worldwide/ (2024).
Bin Hasan, K. M., Sajid, M., Lapina, M. A., Shahid, M. & Kotecha, K. Blockchain technology meets 6 G wireless networks: A systematic survey, (2024).
Li, Y., Huang, J., Sun, Q., Sun, T. & Wang, S. Cognitive Service Architecture for 6G Core Network. IEEE Trans. Industr Inf. 17, 7193–7203. https://doi.org/10.1109/TII.2021.3063697 (2021).
Alsabah, M. et al. 6G Wireless communications Networks: a Comprehensive Survey. IEEE Access. 9, 148191–148243. https://doi.org/10.1109/ACCESS.2021.3124812 (2021).
Banafaa, M. et al. A.: 6G Mobile Communication Technology: Requirements, Targets, Applications, Challenges (Advantages, and Opportunities, 2023).
Siriwardhana, Y., Porambage, P., Liyanage, M. & Ylianttila, M. AI and 6G security: Opportunities and challenges. In: 2021 Joint European Conference on Networks and Communications and 6G Summit, EuCNC/6G Summit 2021. pp. 616–621. Institute of Electrical and Electronics Engineers Inc. (2021).
V, S. P., Albert, A. J., Thapa, K. N. K. & Krishnaprasanna, R. A novel enhanced security architecture for sixth generation (6G) cellular networks using authentication and acknowledgement (AA) approach. Results Eng. 21 https://doi.org/10.1016/j.rineng.2023.101669 (2024).
Hao, Y., Miao, Y., Chen, M., Gharavi, H. & Leung, V. C. M. 6 g cognitive information theory: A mailbox perspective. Big Data Cogn. Comput. 5 https://doi.org/10.3390/bdcc5040056 (2021).
Gupta, M., Jha, R. K. & Jain, S. Tactile Based Intelligence Touch Technology in IoT configured WCN in B5G/6G-A survey. IEEE Access. 11, 30639–30689. https://doi.org/10.1109/ACCESS.2022.3148473 (2023).
Alsaedi, W. K., Ahmadi, H., Khan, Z. & Grace, D. Spectrum options and allocations for 6G: a Regulatory and Standardization Review. IEEE Open. J. Commun. Soc. 4, 1787–1812. https://doi.org/10.1109/OJCOMS.2023.3301630 (2023).
Viswanathan, H. & Mogensen, P. E. Communications in the 6G era. IEEE Access. 8, 57063–57074. https://doi.org/10.1109/ACCESS.2020.2981745 (2020).
Nguyen, D. C. et al. 6G Internet of Things: A Comprehensive Survey. (2021). https://doi.org/10.1109/JIOT.2021.3103320
Abdel Hakeem, S. A., Hussein, H. H. & Kim, H. Security requirements and challenges of 6G Technologies and Applications. Sensors 22 https://doi.org/10.3390/s22051969 (2022).
Dursun, Y., Basit, A. & Ding, S. Wireless powered NOMA-based cognitive radio for 6G networks. Comput. Netw. 248 https://doi.org/10.1016/j.comnet.2024.110497 (2024).
Idris, M. Y. I. et al. Cognitive Radio and Machine Learning Modalities for Enhancing the Smart Transportation System (A systematic literature review, 2024).
Liu, M., Zhang, H., Liu, Z. & Zhao, N. Attacking Spectrum sensing with adversarial deep learning in cognitive radio-enabled internet of things. IEEE Trans. Reliab. 72, 431–444. https://doi.org/10.1109/TR.2022.3179491 (2023).
Al-Sudani, H., Thabit, A. A. & Dalveren, Y. Cognitive Radio and Its Applications in the New Trend of Communication System: A Review. In: IICETA 2022–5th International Conference on Engineering Technology and its Applications. pp. 419–423. Institute of Electrical and Electronics Engineers Inc. (2022).
Manco, J. et al. Spectrum sensing using Software defined radio for cognitive radio networks: a Survey. IEEE Access. 10, 131887–131908. https://doi.org/10.1109/ACCESS.2022.3229739 (2022).
Shi, S. et al. Challenges and new directions in securing Spectrum Access systems. IEEE Internet Things J. 8, 6498–6518. https://doi.org/10.1109/JIOT.2021.3064583 (2021).
Song, H., Bai, J., Yi, Y., Wu, J. & Liu, L. Artificial Intelligence enabled internet of things: Network Architecture and Spectrum Access. IEEE Comput. Intell. Mag. 15, 44–51. https://doi.org/10.1109/MCI.2019.2954643 (2020).
Ivanov, A., Tonchev, K., Poulkov, V. & Manolova, A. Probabilistic spectrum sensing based on feature detection for 6G cognitive radio: a Survey. IEEE Access. 9, 116994–117026. https://doi.org/10.1109/ACCESS.2021.3106235 (2021).
Li, X. et al. Physical layer security of cognitive ambient backscatter communications for green internet-of-things. IEEE Trans. Green. Commun. Netw. 5, 1066–1076. https://doi.org/10.1109/TGCN.2021.3062060 (2021).
Awin, F. A., Alginahi, Y. M., Abdel-Raheem, E. & Tepe, K. Technical Issues on Cognitive Radio-based internet of things systems: a Survey. IEEE Access. 7, 97887–97908. https://doi.org/10.1109/ACCESS.2019.2929915 (2019).
Gür, G. Expansive networks: exploiting spectrum sharing for capacity boost and 6G vision. J. Commun. Netw. 22, 444–454. https://doi.org/10.23919/JCN.2020.000037 (2020).
Muntaha, S. T. et al. Blockchain for Dynamic Spectrum Access and Network Slicing: a review. IEEE Access. 11, 17922–17944. https://doi.org/10.1109/ACCESS.2023.3243985 (2023).
Fan, X. & Huo, Y. Blockchain Based Dynamic Spectrum Access of Non-Real-Time Data in Cyber-Physical-SocialSyst. IEEE Access. 8, 64486–64498 https://doi.org/10.1109/ACCESS.2020.2985580 (2020).
Li, F., Lam, K. Y., Meng, L., Luo, H. & Wang, L. Trading-based dynamic Spectrum Access and Allocation in Cognitive Internet of things. IEEE Access. 7, 125952–125959. https://doi.org/10.1109/ACCESS.2019.2937582 (2019).
Aslam, M. M. et al. Sixth Generation (6G) Cognitive Radio Network (CRN) application, requirements, Security issues, and Key challenges. Wirel. Commun. Mob. Comput. 2021 https://doi.org/10.1155/2021/1331428 (2021).
Khalid, W. et al. Reconfigurable Intelligent Surface for Physical Layer Security in 6G-IoT: designs, issues, and advances. (2023). https://doi.org/10.1109/JIOT.2023.3297241
Rajasekaran, A. S., Azees, M. & Al-Turjman, F. A comprehensive survey on blockchain technology. Sustain. Energy Technol. Assess. 52, 102039. https://doi.org/10.1016/j.seta.2022.102039 (2022).
Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System.
Haleem, A., Javaid, M., Singh, R. P., Suman, R. & Rab, S. Blockchain technology applications in healthcare: An overview, (2021).
Han, H., Shiwakoti, R. K., Jarvis, R., Mordi, C. & Botchie, D. Accounting and auditing with blockchain technology and artificial intelligence: a literature review. Int. J. Acc. Inform. Syst. 48 https://doi.org/10.1016/j.accinf.2022.100598 (2023).
Institute of Electrical and Electronics Engineers. Dynamic Spectrum Access via Smart Contracts on Blockchain. (2019).
Weiss, M. B. H., Werbach, K., Sicker, D. C. & Bastidas, C. E. C. On the application of blockchains to spectrum management. IEEE Trans. Cogn. Commun. Netw. 5, 193–205. https://doi.org/10.1109/TCCN.2019.2914052 (2019).
Khan, L. U., Saad, W., Niyato, D., Han, Z. & Hong, C. S. Digital-Twin-Enabled 6G: Vision, Architectural Trends, and Future Directions. (2021).
Wang, J., Ling, X., Le, Y., Huang, Y. & You, X. Blockchain-enabled wireless communications: a new paradigm towards 6G, (2021).
Kumar, N., Reiffers-Masson, A., Amigo, I. & Rincón, S. R. The effect of network delays on distributed ledgers based on Directed Acyclic Graphs: a mathematical model. Perform. Evaluation. 163 https://doi.org/10.1016/j.peva.2023.102392 (2024).
Wu, Q. et al. SpectrumChain: a disruptive dynamic spectrum-sharing framework for 6G, (2023).
Vaigandla, K. K., Siluveru, M., Kesoju, M. & Karne, R. Review on Blockchain Technology: Architecture, Characteristics, Benefits, Algorithms, Challenges and Applications, (2023).
Komalavalli, C., Saxena, D. & Laroiya, C. Chap. 14 - overview of Blockchain Technology concepts. In: (eds Krishnan, S., Balas, V. E., Julie, E. G., Robinson, Y. H., Balaji, S. & Kumar, R.) Handbook of Research on Blockchain Technology. 349–371. Academic (2020).
Aslam, S., Tošić, A. & Mrissa, M. Secure and Privacy-Aware Blockchain Design: Requirements, challenges and solutions. J. cybersecur. priv.. 1, 164–194. https://doi.org/10.3390/jcp1010009 (2021).
Muhammad Asad, S. et al. Blockchain-Empowered Secure Spectrum sharing for Next Generation Train Networks. IEEE Access. 12, 66690–66700. https://doi.org/10.1109/ACCESS.2024.3398997 (2024).
Bhutta, M. N. M. et al. A Survey on Blockchain Technology: Evolution, Architecture and Security, (2021).
Zeng, Z. et al. Blockchain technology for information security of the energy internet: Fundamentals, features, strategy and application, (2020).
Shrimali, B. & Patel, H. B. Blockchain state-of-the-art: architecture, use cases, consensus, challenges and opportunities, (2021).
Cuellar, D., Sallal, M. & Williams, C. BSM-6G: Blockchain-based dynamic Spectrum management for 6G networks: addressing interoperability and scalability. IEEE Access. https://doi.org/10.1109/ACCESS.2024.3393288 (2024).
Muzaffar, M. U. & Sharqi, R. A review of spectrum sensing in modern cognitive radio networks, (2024).
Nasser, A., Hassan, H. A. H., Chaaya, J. A., Mansour, A. & Yao, K. C. Spectrum Sensing for Cognitive Radio (Recent advances and future challenge, 2021).
Zhu, G. et al. Dynamic sliding window-cooperative spectrum sensing against massive SSDF attack in interweave cognitive internet of things. Trans. Emerg. Telecommunications Technol. 35, e4955 (2024).
Kokila, M. & Reddy, K. S.: Authentication, access control and scalability models in Internet of Things Security–A review, (2024).
Singh, A. K. Murmu Mahendra Kumar and Security issues in Cognitive Radio Ad Hoc Networks. In: (eds Gupta Brij, B. & Perez, G. M.) and A.D.P. and G.D. Handbook of Computer Networks and Cyber Security: Principles and Paradigms. 247–264. Springer International Publishing, Cham (2020).
Vuppula, R. & Pradhan, H. S. Blockchain-oriented location privacy preserving for cooperative spectrum sensing in 6G wireless networks. IET Blockchain. 3, 74–97. https://doi.org/10.1049/blc2.12025 (2023).
Jin, F. Detecting Primary User Emulation Attacks in Cognitive Radio Networks, (2022).
Kavitha, T., Senbagavalli, G. & Saraswathi, S. Privacy-preserving Scheme for internet of things. In: Secure Communication in Internet of Things. pp. 117–129. CRC.
Vo, V. et al. Security and privacy of 6G Federated Learning-enabled dynamic spectrum sharing. arXiv preprint http://arxiv.org/arXiv:2406.12330. (2024)
Ahmed, N. et al. A Survey on Location Privacy Attacks and Prevention Deployed with IoT in Vehicular Networks. Wirel Commun Mob Comput. 6503299 (2022) (2022).
Lohan, P., Kantarci, B., Ferrag, M. A., Tihanyi, N. & Shi, Y. From 5G to 6G networks, a survey on AI-Based jamming and interference detection and mitigation. IEEE Open. J. Commun. Soc. https://doi.org/10.1109/OJCOMS.2024.3416808 (2024).
Khadr, M. H., Salameh, B., Ayyash, H., Elgala, M. & Almajali, H. S. Jamming resilient Multi-channel transmission for cognitive radio IoT-based Medical Networks. In: Journal of Communications and Networks. 666–678. Korean Institute of Communication Sciences. https://doi.org/10.23919/JCN.2022.000042 (2022).
Wang, L. et al. Method for extracting patterns of coordinated network attacks on electric power CPS based on temporal–topological correlation. IEEE Access. 8, 57260–57272. https://doi.org/10.1109/ACCESS.2020.2982057 (2020).
Nayanam, K., Gandhi, R. & Vishwavidyalaya, P. Cognitive radio based enhanced compressive spectrum sensing technique for 5G adhoc networks. Int. J. Eng. Res. https://doi.org/10.17577/IJERTV13IS020003 (2024).
Rathod, T. et al. Blockchain-Driven Intelligent Scheme for IoT-Based Public Safety System beyond 5G networks. Sensors 23 https://doi.org/10.3390/s23020969 (2023).
Saeed, M. M. et al. Anomaly detection in 6G networks using machine learning methods. Electron. (Switzerland). 12 https://doi.org/10.3390/electronics12153300 (2023).
Perera, L., Ranaweera, P., Kusaladharma, S., Wang, S. & Liyanage, M. A Survey on Blockchain for dynamic spectrum sharing. IEEE Open. J. Commun. Soc. (2024).
Liang, Y. C. Dynamic Spectrum Management: from Cognitive Radio to Blockchain and Artificial Intelligence (Springer Nature, 2020).
Gaber, T., El-Ghamry, A. & Hassanien, A. E. Injection attack detection using machine learning for smart IoT applications. Phys. Communication. 52 https://doi.org/10.1016/j.phycom.2022.101685 (2022).
Yarali, A. From 5G to 6G: Technologies, Architecture, AI, and Security (Wiley, 2023).
Ahmad, I., Yau, K. L. A., Ling, M. H. & Keoh, S. L. Trust and reputation management for securing collaboration in 5G access networks: the road ahead. IEEE Access. 8, 62542–62560. https://doi.org/10.1109/ACCESS.2020.2984318 (2020).
Adele, G., Borah, A., Paranjothi, A. & Khan, M. S. A survey and comparative analysis of methods for countering Sybil attacks in VANETs. In: 2024 IEEE 14th Annual Computing and Communication Workshop and Conference (CCWC). pp. 178–183. IEEE (2024).
Sankar Ganesh, S. et al. Next-Generation Threat Detection and Mitigation in 6G Wireless Networks Using IAM, ZTNA and Advanced Security Mechanisms. (2024).
Jagatheesaperumal, S. K. et al. Blockchain-Based Security Architecture for Unmanned Aerial Vehicles in B5G/6G Services and Beyond (A Comprehensive Approach, 2023).
Ziegler, V. et al. Security and trust in the 6G era. IEEE Access. 9, 142314–142327. https://doi.org/10.1109/ACCESS.2021.3120143 (2021).
Mughal, M. A., Ullah, A., Cheema, M. A. Z., Yu, X. & Jhanjhi, N. Z. An intelligent channel assignment algorithm for cognitive radio networks using a tree-centric approach in IoT. Alexandria Eng. J. 91, 152–160. https://doi.org/10.1016/j.aej.2024.01.071 (2024).
Deepanramkumar, P. & Jaisankar, N. BlockCRN-IoCV: secure Spectrum Access and Beamforming for defense against attacks in mmWave massive MIMO CRN in 6G internet of Connected vehicles. IEEE Access. 10, 74220–74243. https://doi.org/10.1109/ACCESS.2022.3187745 (2022).
Duraisamy, A. K., Ramaraj, R. G., Manoharan, M. & Alagarsamy, M. Certificateless linkable ring signature-based blockchains for securing cognitive radio networks. Concurr Comput. 34(24), e7235 (2022).
Sajid, A. et al. Securing cognitive radio networks using blockchains. Future Generation Comput. Syst. 108, 816–826. https://doi.org/10.1016/j.future.2020.03.020 (2020).
Venkatraman, S. & Parvin, S. Developing an IoT Identity Management System using Blockchain. Systems 10 https://doi.org/10.3390/systems10020039 (2022).
Ghourab, E. M. et al. Reputation-aware relay selection with opportunistic Spectrum Access: a Blockchain Approach. IEEE Open. J. Veh. Technol. 4, 389–403. https://doi.org/10.1109/OJVT.2023.3263804 (2023).
Balakumar, D. & Sendrayan, N. Enhance the Probability of Detection of Cooperative Spectrum Sensing in Cognitive Radio Networks Using Blockchain Technology. Journal of Electrical and Computer Engineering. (2023). (2023). https://doi.org/10.1155/2023/8920243
Balakumar, D. & Nandakumar, S. Cognitive Radio Spectrum Sensing-Based QAM Technique Using Blockchain. Int J Distrib Sens Netw. (2023). (2023). https://doi.org/10.1155/2023/7225260
Marriwala, N. K., Panda, S., Kamalanathan, C., Sadhasivam, N. & Ramaiah, V. S. An Analytical Model for Dynamic Spectrum Sensing in Cognitive Radio Networks Using Blockchain Management †. Engineering Proceedings. 59, (2023). https://doi.org/10.3390/engproc2023059163
Kotobi, K. & Bilen, S. G. Secure blockchains for dynamic Spectrum Access: a decentralized database in moving cognitive radio networks enhances security and user Access. IEEE Veh. Technol. Mag. 13, 32–39. https://doi.org/10.1109/MVT.2017.2740458
Chen, Z., Wang, L. & Zhang, Y. Blockchain structure electromagnetic spectrum database in distributed cognitive radio monitoring system. IEEE Trans. Cogn. Commun. Netw. 8, 1647–1664 (2022).
Patel, F. et al. Block6Tel: Blockchain-based spectrum allocation scheme in 6G-envisioned communications. In: 2021 International Wireless Communications and Mobile Computing (IWCMC). pp. 1823–1828. IEEE (2021).
Femenias, G., Francisca Hinarejos, M., Riera-Palou, F., Ferrer-Gomila, J. L. & Jaume-Barcelo, A. Dynamic spectrum sharing in a Blockchain Enabled Network with multiple cell-free massive MIMO virtual operators. IEEE Access. 12, 70615–70633. https://doi.org/10.1109/ACCESS.2024.3402318 (2024).
Raphaelle Akhras, W., El-Hajj, M., Majdalani, H., Hajj, R. & Jabr Khaled Shaban: Securing Smart Grid Communication using Ethereum Smart Contracts, (2020).
Zhang, H., Leng, S. & Chai, H. A Blockchain Enhanced Dynamic Spectrum Sharing Model Based on Proof-of-Strategy, (2020).
Ameri, R. & Meybodi, M. R. The cellular goore game-based consensus protocol: a cognitive model for blockchain consensus. Cluster Comput. 27, 2715–2740 (2024).
Liang, Y., Lu, C., Zhao, Y. & Sun, C. Interference-based Consensus and Transaction Validation mechanisms for Blockchain-based Spectrum Management. IEEE Access. 9, 90757–90766. https://doi.org/10.1109/ACCESS.2021.3091802 (2021).
Jain, A., Gupta, N. & Sreenu, M. Blockchain based smart contract for cooperative spectrum sensing in cognitive radio networks for sustainable beyond 5G wireless communication. Green. Technol. Sustain. 1, 100019. https://doi.org/10.1016/j.grets.2023.100019 (2023).
Xue, L., Yang, W., Chen, W. & Huang, L. STBC: a Novel Blockchain-based spectrum trading solution. IEEE Trans. Cogn. Commun. Netw. 8, 13–30. https://doi.org/10.1109/TCCN.2021.3086490 (2022).
Dansana, D. et al. BSMACRN: design of an efficient blockchain-based security model for improving attack-resilience of Cognitive Radio Ad-hoc networks. IEEE Access. 12, 10047–10058. https://doi.org/10.1109/ACCESS.2024.3350739 (2024).
Khorseed, W. S. & Hamad, A. H. Inter and Intra Domain DDoS Attack Mitigation for Software Defined Network based on Hyperledger Fabric Blockchain Technology. Ingenierie Des. Systemes d’Information. 29, 301–311. https://doi.org/10.18280/isi.290130 (2024).
Manogaran, G. et al. Blockchain based integrated security measure for reliable service delegation in 6G communication environment. Comput. Commun. 161, 248–256. https://doi.org/10.1016/j.comcom.2020.07.020 (2020).
Le Nguyen, B. et al. Privacy preserving blockchain technique to achieve secure and reliable sharing of IoT data. Computers Mater. Continua. 65, 87–107. https://doi.org/10.32604/cmc.2020.011599 (2020).
Venkatesan, K. & Rahayu, S. B. Blockchain security enhancement: an approach towards hybrid consensus algorithms and machine learning techniques. Sci. Rep. 14 https://doi.org/10.1038/s41598-024-51578-7 (2024).
Mohammed Abdul, S. S. Navigating Blockchain’s Twin challenges: Scalability and Regulatory Compliance. Blockchains 2, 265–298. https://doi.org/10.3390/blockchains2030013 (2024).
Liang, W., Zhang, L. & Kadoch, M. 6G IoT Tracking- and machine learning-enhanced Blockchained Supply Chain Management. Electron. (Switzerland). 12 https://doi.org/10.3390/electronics12010040 (2023).
Alghamedy, F. et al. Unlocking a Promising Future: integrating Blockchain Technology and FL-IoT in the journey to 6G. IEEE Access. PP. 1. https://doi.org/10.1109/ACCESS.2024.3435968 (2024).
Li, Y., Wei, X., Li, Y., Dong, Z. & Shahidehpour, M. Detection of false data injection attacks in smart grid: a secure federated deep learning approach. IEEE Trans. Smart Grid. 13, 4862–4872. https://doi.org/10.1109/TSG.2022.3204796 (2022).
Olaf Grote, A., Ahrens & C´ esar Benavente-Peces. : A Review of Post-quantum Cryptography and Crypto-agility Strategies, (2019).
Al-Ansi, A., Al-Ansi, A. M., Muthanna, A. & Koucheryavy, A. Blockchain technology integration in service migration to 6G communication networks: a comprehensive review, (2024).
Saini, R. et al. Designing quantum blockchain system integrated with 6G network. J. King Saud Univ. - Comput. Inform. Sci. 35 https://doi.org/10.1016/j.jksuci.2023.101847 (2023).
Allende, M. et al. Quantum-resistance in blockchain networks. Sci. Rep. 13 https://doi.org/10.1038/s41598-023-32701-6 (2023).
Kumari, A., Gupta, R. & Tanwar, S. Amalgamation of blockchain and IoT for smart cities underlying 6G communication: a comprehensive review. Comput. Commun. 172, 102–118. https://doi.org/10.1016/j.comcom.2021.03.005 (2021).
Alsamhi, S. H. et al. Towards sustainable industry 4.0: a survey on greening IoE in 6G networks. Ad Hoc Netw. 103610. https://doi.org/10.1016/j.adhoc.2024.103610 (2024).
Kumar, R. et al. (2023).
Ansere, J. A., Kamal, M., Khan, I. A. & Aman, M. N. Dynamic resource optimization for energy-efficient 6G-IoT ecosystems. Sensors 23 https://doi.org/10.3390/s23104711 (2023).
Qu, Z. et al. Localization of dummy data injection attacks in power systems considering incomplete topological information: a spatio-temporal graph wavelet convolutional neural network approach. Appl. Energy. 360, 122736. https://doi.org/10.1016/j.apenergy.2024.122736 (2024).
Lu, X. et al. Reinforcement Learning Based Physical Cross-Layer Security And Privacy in 6G.
Sefati, S. S. et al. A Comprehensive Survey on Resource management in 6G network based on internet of things. IEEE Access. https://doi.org/10.1109/ACCESS.2024.3444313 (2024).
Author information
Authors and Affiliations
Contributions
The first author (Nassmah Al-Matari) is a Master student and this paper is a part of the Master thesis. The role of Nassmah is mainly that she wrote the manuscript.The second author (Dr. Ammar Zahary) is the main supervisor of the Master thesis. His role was figuring out the ideas and methodology of the paper. He is the main advisor of the thesis and consequently the manuscript.The third author (Dr. Asma Al-Shargabi) has performed a valuable revision and proofreading of the paper.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Al-Matari, N.Y., Zahary, A.T. & A. Al-Shargabi, A. A survey on advancements in blockchain-enabled spectrum access security for 6G cognitive radio IoT networks. Sci Rep 14, 30990 (2024). https://doi.org/10.1038/s41598-024-82126-y
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-024-82126-y
Keywords
This article is cited by
-
A homotopy estimation based temporal-spatial spectrum prediction for UAV communications with arbitrary flight paths
Scientific Reports (2025)
-
Quantum deep learning-enhanced ethereum blockchain for cloud security: intrusion detection, fraud prevention, and secure data migration
Scientific Reports (2025)
-
Blockchain-Enhanced Deep Learning Framework for Secure Patient Data Management in IoT-Enabled Healthcare Systems
Cognitive Computation (2025)