Abstract
Medical image encryption is important for maintaining the confidentiality of sensitive medical data and protecting patient privacy. Contemporary healthcare systems store significant patient data in text and graphic form. This research proposes a New 5D hyperchaotic system combined with a customised U-Net architecture. Chaotic maps have become an increasingly popular method for encryption because of their remarkable characteristics, including statistical randomness and sensitivity to initial conditions. The significant region is segmented from the medical images using the U-Net network, and its statistics are utilised as initial conditions to generate the new random sequence. Initially, zig-zag scrambling confuses the pixel position of a medical image and applies further permutation with a new 5D hyperchaotic sequence. Two stages of diffusion are used, such as dynamic DNA flip and dynamic DNA XOR, to enhance the encryption algorithm’s security against various attacks. The randomness of the New 5D hyperchaotic system is verified using the NIST SP800-22 statistical test, calculating the Lyapunov exponent and plotting the attractor diagram of the chaotic sequence. The algorithm validates with statistical measures such as PSNR, MSE, NPCR, UACI, entropy, and Chi-square values. Evaluation is performed for test images yields average horizontal, vertical, and diagonal correlation coefficients of –0.0018, –0.0002, and 0.0007, respectively, Shannon entropy of 7.9971, Kolmogorov Entropy value of 2.9469, NPCR of 99.61%, UACI of 33.49%, Chi-square “PASS” at both the 5% (293.2478) and 1% (310.4574) significance levels, key space is 2500 and an average encryption time of approximately 2.93 s per 256 × 256 image on a standard desktop CPU. The performance comparisons use various encryption methods and demonstrate that the proposed method ensures secure reliability against various challenges.
Similar content being viewed by others
Introduction
In recent decades, a trend has been toward implementing revolutionary healthcare infrastructure, including digital health services, remote surgical assistance, image-based diagnosis, real-time health monitoring devices, and digitising patient medical data. The development of information exchange and the expansion of networks have led to security concerns in medical image information. The imaging modalities extract internal image features. The security of medical imaging has been increasing in importance in recent years. Medical images should be transmitted securely, ensuring privacy, integrity, and dependability. Patient data is highly valuable, encompassing personal health information and financial details, making healthcare data particularly sensitive and critical. Privacy and security issues in the digital health era are complex and multifactorial.
By considering enormous collections of medical imaging and patient record data, automated illness analysis is made feasible, greatly enhancing the precision and effectiveness of medical diagnostics. When medical data is managed and shared with external parties, as in publicly accessible, privately stored, or mixed cloud environments, many problems regarding its confidentiality and integrity may arise. However, the healthcare industry has ongoing security risks to medical data. A minor change in the medical images results in a life-threatening situation for the patients. Therefore, a reliable protection solution is required to transfer confidential medical information securely. Encrypting images, among other protection techniques, is a ubiquitous and efficient way to safeguard image data. Image encryption increases resilience against security attacks by using a mathematical method to transform the original image into a format that is difficult to interpret. Over the past few decades, researchers have presented numerous image encryption schemes employing various methodologies. The high redundancy and massive pixel density of medical images make traditional encryption techniques ineffective. Conventional encryption techniques, which depend on intricate mathematical operations, require much processing power. They are also resource-intensive and lack scalability, especially when working with extensive multimedia datasets or carrying out batch operations. They are also vulnerable to interference and attacks, such as custom-plaintext and data analysis attacks1.
Chaotic system image encryption has been used by scientists and professionals to address these problems. The use of chaos in cryptography has gained popularity in recent decades because of its essential characteristic of being hypersensitive to initial conditions, which produces chaotic sequences that appear random. The permutation and the diffusion are the two stages that usually comprise the chaos system-driven picture encryption framework2. The pixel rearrangement method, known as permutation, has altered the image into an unrecognisable format, which shifts the pixel positions throughout the image while maintaining the same pixel values. Since the first phase is inadequate and attackers can readily exploit it, the system implements the diffusion or spreading phase. As a result, chaotic systems generate a pattern that sequentially modifies the pixel values of the entire image when executing the spreading phase with a chaotic map. The system repeats the scrambling-spreading procedure multiple times until it attains sufficient security.
One of the most efficient ways to protect medical image information is through cryptography3. However, the information becomes vulnerable to attackers when it is decoded. Transferring and securing the key is very important for the authorised user of the algorithm. The key size increases the computational cost. Safety and confidentiality are affected when an unauthorised person discloses the key. Even the authorised individual may find it challenging to access the encrypted data in critical situations. A sophisticated encryption approach that considers these issues is necessary to provide total data safety.
Intelligent encryption using deep learning is gaining widespread popularity as a medical image encryption tool in digital health platforms. Integrating deep neural network architecture with chaotic systems holds significant potential for improving cryptographic techniques. Deep learning-powered picture encryption methods meet modern multimedia content security requirements. Several deep learning-based image encryption methods have been developed to protect privacy while computation is on. Artificial intelligence (AI) can produce complicated and resilient encryption algorithms that are challenging for unauthorised parties to crack. However, the amount and accuracy of training datasets determine how well AI secures medical images by increasing computational complexity4. Prognostic modelling, therapeutic decision-making, personalised treatment, and image interpretation can leverage deep learning strategies for better outcomes. In contrast to other deep learning frameworks, CNN-driven architectures have become increasingly popular for encrypting medical images. This work addresses the current challenges of medical image encryption by developing innovative image encryption that combines deep learning models, such as the U-Net network, with a novel 5D hyperchaotic system. The key generation uses U-Net for segmenting the significant features in medical images, for example, anatomical structures, tumour cells, and vessels/veins. The novel 5D hyperchaotic system generates unique and large random sequences using the initial conditions of segmented key values of the medical images. The novel hyperchaotic sequence and dynamic DNA encoding perform different stages of the encryption process in medical images, improving the security and privacy of individual health records. A two-stage permutation and diffusion process are used, along with a hyperchaotic system and dynamic DNA encoding. Dynamic DNA encoding with a hyperchaotic system gives significant parallelism, increased data density, and extremely low power utilisation. For the medical segmentation of complex forms, U-Net’s unique structure, which includes an encoder and a decoder, allows the network to preserve spatial detail while collecting contextual information. The proposed work integrating the hyperchaotic system with U-Net architecture provides efficient encrypted images and authenticated health data transfer.
Impact of deep segmentation network on the encryption technique:
-
1. U-Net removes critical regions of the medical image, and it is used for key generation.
-
2. The statistical data of critical regions can be used as dynamic encryption keys, so each image has a unique set of initial conditions.
-
3. The protection of medical images is increased with different sets of keys in the encryption algorithm.
-
4. U-Net can maintain high segmentation accuracy while reducing computing overhead because it can function well on small datasets with few training data.
-
5. The U-Net architecture preserves spatial information and ensures precise extraction of important image features by combining skip connections with an encoder-decoder design.
-
6. Segmenting critical regions is a single preprocessing step for each image with the lowest computing cost.
-
7. Training time and resource consumption are reduced when U-Net is trained on a small, specifically chosen dataset.
-
8. Stable key generation is guaranteed by constant and dependable segmentation across various images.
The proposed work is validated by calculating the statistical parameters and performing security analysis. The simulation results shows that the proposed work is validated for medical image encryption.
The key contributions of this proposed work are as follows:
-
A New 5D Hyperchaotic map is proposed for secure encryption.
-
Critical region-based key generation utilising U-Net segmentation to produce unique initial conditions for a novel 5D hyperchaotic map. Although the computational complexity has been marginally elevated due to U-Net, the key generation remains highly robust against security attacks.
-
An encryption strategy combines zig-zag scrambling, dynamic DNA encoding, Dynamic DNA flipping and XOR-based diffusion guided by chaotic sequences.
-
Comprehensive security analysis demonstrates robust resistance against common security attacks, ensuring the system’s reliability and protection. Quantitative performance evaluation on medical images, of the proposed method, achieves horizontal, vertical, and diagonal correlation coefficients of ≤|0.002|, Shannon entropy ≥ 7.9971, NPCR ≥ 99.61%, UACI ≥ 33.49%, Chi-square “PASS” at both 5% and 1% levels, large key space of 2500 and encrypts a 256 × 256 image in ≈ 0.018 s demonstrating both high security and computational efficiency of the algorithm.
This article presents the following sections: Section “Literature survey” discusses detailed literature surveys and contributions. Section “Preliminaries” outlines the preliminaries of the novel 5D hyperchaotic map and customised U-Net. Section “Proposed block diagram” explains the proposed block diagram and algorithm. Section “Experimental results” presents the experimental results. Section “Performance analysis” provides performance analysis, and Section “Performance comparison with existing algorithms” demonstrates a Performance Comparison with Existing Algorithms analysis of Computational complexity and Time Performance. Finally, Sect. “Conclusion and future scope” concludes the work and gives future directions.
Literature survey
Medical image encryption
The survey on medical image encryption demonstrates a different technique targeted at enhancing security and retaining efficiency. The paper5 proposes a new 1D-Cosine within Sine (1D-CwS) to permute and diffuse the medical images. The new chaotic map generates expanded random numbers, which are validated using the Lyapunov parameters and bifurcation plot. It resists the various attacks generated while transferring the medical images. The research6 presents Elliptic Curve Cryptography (ECC) and the Blum-Goldwasser Cryptosystem (BGC) to improve the encryption techniques in medical images. The algorithm’s adaptability to cipher keys increases the potential of the system to be resilient to threats. The method reduces the computation time, increases the entropy, and attains critical values in NPCR. Recently, the idea of DNA encoding in conjunction with chaotic sequences has gained popularity among academics studying permutation and Diffusion. The proposed technique7, a novel 2D Cosine-Sine map, generates the chaotic sequence for medical video confusion, and Diffusion uses chaotic sequences with dynamic DNA. The result proved that the technique based on chaotic sequences with dynamic DNA improves the security of medical videos. Researchers have also advanced the encryption technique for confidential areas8in medical images using Rubik’s cube-based bit plane shuffling with a logistic map. It reduces the algorithm’s complexity by considering the confidential area of medical images. Advantages include high security against data loss. The dual-image encryption technique9 was proposed in this paper by combining chaotic phase Fresnel diffraction with a fingerprint key. It guarantees enhanced security with strong robustness against noise attacks, plain test attacks, occlusion attacks, ciphertext attacks, and histogram attacks.
Another methodology proposed by the paper10 uses a biometric image as the key generated by extracting texture features in the circular pattern and finding spatial weighted averaging for the key image. The one-dimensional fractional trigonometric function chaotic map performs permutation and diffusion between the original image and the biometric fused key image. This method demonstrates strong sensitivity, robustness, and resistance to attacks. The technique proposed by11 utilises two logistic maps initiated by a four-power bit grey-level code. The algorithm encrypts the COVID-19 X-ray images with different sizes. Due to the more extended key size, the encrypted image is infeasible for a forced attack. The medical image encryption is enhanced in this paper12 by combining Chen’s chaotic map, Henon’s chaotic map, and Brownian motion. The technique attains the expected security level by analysing different statistical parameters such as pixel correlation, homogeneity, histogram, entropy, NPCR, and UACI analysis. Another new approach investigated in this paper13 is the integer wavelet transform combined with DNA and a chaotic map to obtain secure medical images in the transform domain. The technique obtains maximum entropy and outperforms the previous methods by applying two-stage shuffling and diffusion processes.
The paper14 introduced a new reconfigurable non-volatile array-type memristor implemented using a CMOS circuit to reduce the manufacturing cost, and it is used for power load forecasting. The existing work discusses deploying a chaotic system for data security in the memristor-based power load prediction. The complex dynamic behaviours are obtained by memristive FN-HNN neural networks, which can be used for image encryption applications to improve information security performance15. In this work16, the memristive array is introduced for parallel neural network computations to update the LSTM weights in the fault diagnosis operation. They achieved faster convergence and 98% accuracy, and this parallelisation strategy generalises to derive multiple secret keystream subblocks per cycle for image encryption. The research work17 proposed a memristive memory circuit with association capability to mimic the bioinspired brain network. The three-module memristive circuit emulates Drosophila associative learning (synapse/neuron, cross-modal synergy, and threshold detection) is implemented. While aimed at bionic AI, its adaptive weight modulation suggests a hardware approach for context-aware key updates, equivalent to adaptive diffusion rounds keyed by stimulus intensity in image encryption.
In this paper18, the source image is divided into a subblock of 8 × 8, and the transformation table is generated from a novel two-dimensional enhanced coupling Quadratic map and a dimension Tent Logistics map with a hash function. The scrambling is performed based on the Tent Logistics map, and the diffusion is implemented with the help of the transformation table, reducing the encryption method’s complexity. The paper referenced in19 gives asymmetric key management using an Elliptic Curve Diffie-Hellman (ECDH), Elliptic Curve Cryptography (ECC), and SHA-256 functions. DNA encoding integrates with the novel two-dimensional cross-sine-modular model(2D-CSMM) to construct the enhanced S-box to implement global shuffling and chaotic rotation to obtain the efficient cipher image.
The literature survey found that lightweight medical picture encryption systems with excellent transmission efficiency are necessary for real-world medical applications. However, medical image security and privacy must also be guaranteed to prevent unauthorised individuals from accessing them. The approaches used in existing methods are susceptible to complex attacks, have high computational complexity, and are limited in their capacity to handle big data sets. These issues show how difficult it is to achieve broader usability in real-time health information.
Medical hyperchaotic image encryption
Chaos-based image encryption algorithms have gained popularity across industries, but many current methods rely on low-dimensional chaos, which may compromise security. This study presents a 6D high-dimensional chaotic system combined with DNA encoding20 to enhance encryption robustness. The process involves DNA-level diffusion and shuffling, rearranging the original image sequences using random chaotic sequences. Experimental results show that the algorithm increases image complexity, reduces pixel correlation, improves entropy (near 8), and offers resilience against geometric and cut-off attacks. Another study proposes a 5D hyperchaotic system21 with quadratic nonlinearity for image encryption, using Hybrid Random Matrix Transform (HRMT) for confusion and diffusion processes. The investigation demonstrates the algorithm’s performance and durability against attacks.
In reference22, the encryption scheme generates a cipher image by combining Fisher-Yates confusion, Chen chaotic system, and DNA operation. After scrambling, DNA addition, XOR operation, and subtraction are performed between DNA sequences to increase the algorithm’s accuracy. Another novel approach is introduced in this paper23, which uses a random signal insertion as an initial condition for a 6D chaotic map. Each 8-bit pixel is divided into two 4-bit pixel parts and creates a new pixel matrix. Confusion, circular shift, and diffusion are performed in the new pixel matrix, improving the encryption scheme’s effectiveness. It also increases the key space and enables it to endure various attacks. The paper24 proposes an algorithm that combines integer wavelet transform, a new 3D hyperchaotic map, a bit-level permutation, and random DNA shuffling using a DNA base cube to guarantee the security of medical images. The study analysis in25 executed a 4D large-scale hyperchaotic map (4D-LSHM) for cross-permutation and shuffling in the different bit-level slices of the image. Compressed sensing is implemented along with encryption to improve the performance algorithm by reducing the size of the cipher image. Thus, the literature analysis shows that using hyper-chaotic maps such as 6D and 5D with DNA encoding reduces pixel correlation and substantially improves security. However, many encryption techniques depend mainly on chaotic maps for confusion and diffusion, limiting the algorithm’s flexibility if the chaotic map is compromised. So, real-time application issues demand further advances in widespread deployment.
Preliminaries
New 5D hyper chaotic system
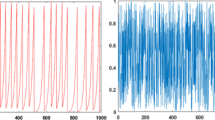
In the preliminary section of this article, we introduce a novel 5D hyperchaotic system that generates a chaotic sequence of five variables (x, y, z, u, and v), evolving dynamically over time. This dynamic, chaotic sequence ensures a non-linear and secure encryption process. The higher-dimensional phase space of the 5D chaotic system allows for greater complexity in trajectories and increases the system’s unpredictability, which makes it advantageous for encryption. This additional intricacy intensifies the diffusion and confusion effects essential for safe picture encryption. The control parameter values are α = 40, β = 8, \(\gamma\) = 40, ∂ = 1, €= −0.5, ϑ = −0.5, ρ = 25.5 and κ = 0.05. The statistics of critical regions of the medical image extracted from the U-Net network provide the initial conditions for the novel 5D chaotic map. Fig. 1 gives the attractor diagram, and Fig. 2 displays the time series plot of the New 5D hyperchaotic sequences. Fig. 3(a) represents the bifurcation diagram of the new 5D hyperchaotic system, and the bifurcation diagram represents complex, chaotic dynamics by exposing densely populated plot regions. The equations governing the New 5D hyperchaotic system are given in Eq. (1)
The Lyapunov exponents (LEs) characterise the chaotic nature and dimensionality of the attractor. The LEs are computed using the variational equations derived from the Jacobian matrix of the system, given in the Eq. (2)
The Lyapunov exponents are calculated using the QR decomposition method over many iterations, where QR refers to the decomposition of a matrix into an orthogonal matrix Q and an upper triangular matrix R. The time evolution of LEs is obtained from Eq. (3)
where \({{\varvec{R}}}_{{\varvec{i}}{\varvec{i}}\boldsymbol{ }}\left({\varvec{K}}\right)\) represents the diagonal elements of the R matrix obtained from QR decomposition at iteration K. The calculated Lyapunov exponents for the hyperchaotic system are λ1 = 19.3889, λ2 = 4.7545, λ3 = 0.3866, λ4 = −0.5982, and λ5 = −44.4191. The positive Lyapunov exponent represents the hyperchaotic nature of the system. The time histories of the Lyapunov exponent (λ) and control parameter (α) are shown in Fig. 3(b) and 3(c), respectively.
Kolmogorov entropy of the new 5D hyperchaotic system
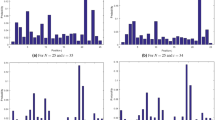
The Kolmogorov entropy (KE) calculates a system’s predictability, called the Kolmogorov–Sinai entropy. As long as two distinct locations on the attractor are spaced at a scale smaller than a threshold length, Kolmogorov entropy can be calculated by tracking them about time. Due to initial condition sensitivity, it assesses a system’s unpredictability by measuring how rapidly state-related information is lost. Finding Random points along a trajectory in phase space is an effective method for measuring KE and the reference paper26 details of KE calculation. Kolmogorov entropy is arbitrarily high for a stochastic system and equals zero for a predictable or fully periodic system. Thus, the KE entropy can estimate the nonlinear system’s chaos and complexity of motion. Table 1 compares KE with existing methods, and the high value of KE for our method ensures that it generates unpredictable data at the fastest rate. Figure 4. plots the KE values of the proposed method; it shows most of the values lie above 2.5, indicating the high chaotic property of the proposed system.
NIST test
NIST SP 800–22 Statistical Test Suite32 is a well-known framework designed to assess the statistical randomness of binary sequences produced by chaotic systems or pseudorandom number generators. It is necessary for validating the security and unpredictable nature of sequences employed in communication networks, encryption, and other applications where randomness is crucial. The sixteen statistical tests in the test suite analyse sequences to identify biases, trends, or deviations from randomness. Each test operates under the null hypothesis, which assumes the input sequence is random. The significance level (α), commonly set at 0.01, establishes the threshold for randomness.
A sequence passes a test when its p-value surpasses the α value, indicating no significant deviations from randomness. This research evaluated five chaotic sequences (x, y, z, u, and v) generated by a new proposed 5D hyperchaotic system for randomness using the NIST SP 800 test suite. All sixteen tests, including the Frequency Test, Block Frequency Test, Runs Test, and others, were used to test each chaotic sequence independently. These tests evaluate several attributes, including correlation qualities, uniform distribution, and lack of patterns. The research results revealed that all five chaotic sequences passed every test in the NIST suite, with p-values consistently passing the crucial 0.01 threshold shown in Table 2. The proposed New 5D Hyper chaotic system is appropriate for cryptography and secure communication applications since it produces random and unexpected sequences.
Customized U-Net architecture for segmenting images
A convolutional neural network (CNN) architecture called U-Net was created especially for image segmentation, as shown in Fig. 5. It was first utilized for medical image applications33 but is now widely applied in many domains. An asymmetric expansive path (decoder) for reconstructing high-resolution output and a contracting path (encoder) for feature extraction make the model symmetric design. The encoder generates hierarchical features by gradually down-sampling the image using max-pooling and convolutional layers. To restore spatial resolution, the decoder, on the other hand, up-samples the feature maps and refines them using more convolutional layers. Skip connections, which connect corresponding encoder and decoder layers and assist in retaining spatial information while enhancing localisation accuracy, are a fundamental component of U-Net. The final 1 × 1 convolution maps the feature maps to the desired output classes, making it practical for binary and multi-class segmentation tasks. U-Net’s ability to perform well with limited training data and data augmentation techniques makes it a powerful tool for image segmentation in various domains34, such as medical imaging and remote sensing. In this proposed work, the U-Net architecture segments the critical regions of medical images, which are then used as initial key values to generate the new 5D hyperchaotic map. Table 3. presents the customised U-Net architecture, detailing the number of layers and the specific operations performed at each layer.
Proposed block diagram
The block diagram in Fig. 6 illustrates an efficient medical image encryption method that combines New 5D hyperchaotic maps, U-Net architecture, and DNA-based encoding techniques to guarantee robustness and confidentiality. At the initial stage of the procedure, a U-Net architecture is used to process a medical image to extract significant regions. Critical regions set the parameters of a new five-dimensional (5D) hyperchaotic map to generate encryption keys. This chaotic map is essential to the encryption process because it generates chaotic sequences that add complexity and randomness at different points in time.
The two main stages of the encryption process are diffusion and confusion. During the confusion phase, the medical image utilizes chaotic index values, which further obfuscates the image structure with zig-zag scrambling and disturbs the spatial arrangement of pixels. The diffusion phase uses biological system-inspired dynamic DNA encoding methods. With specific mod 8 chaotic values determining the DNA rule selection and center location (mod 4) for encoding operations, chaotic sequences dynamically encode the image into DNA sequences. As a result, the image of data undergoes a more intricate and uncertain transformation. The dynamic DNA flip and an XOR operation comprise the two stages of the diffusion stage. The dynamic DNA flip uses the chaotic map’s center coordinates to scramble the DNA-encoded data further, and the XOR operation adds more diffusion by fusing the encoded image with the chaotic DNA sequence. As a result of this proposed method, the cipher image preserves highly confidential medical data and ensures the secure transfer of images. The algorithm adds the advantages of complex dynamic DNA-based encoding and the inherent randomness of chaotic systems by providing an extremely secure way to protect medical images. By highlighting significant features of the image as the key image, the U-Net architecture enhances the encryption process overall.
Proposed algorithm
Medical images are encrypted and decrypted using an innovative 5D hyperchaotic technique. The complex key created from the crucial areas of medical images enhanced the algorithm’s performance. The new high-dimensional chaotic system resists unwanted access to the medical image and expands the chaotic range to a broader spread. The proposed algorithm protects the medical image by incorporating two shuffling and diffusion operation stages.
A medical image is resized and then converted to grayscale to simplify the data for subsequent processing. The main target of the encryption is this grayscale image. The reduced U-Net architecture’s predicted image size matches the measurements of the grayscale medical image. U-Net learns more complicated features with its deep architecture and performs segmentation tasks more accurately, mainly when dealing with more complex image structures. The algorithm generates encryption keys using statistical features derived from the pixel intensity values of the critical region of the medical image, which indicates important structural features.
In order to prove the uniqueness of our contribution, the proposed algorithm dynamically integrates the initialization of a newly derived five-dimensional hyperchaotic map that maximizes the state space complexity to per-image statistics data extracted using a simplified U-Net. These statistics of key control the zigzag scrambling, permutation and two-stage DNA diffusion (new dynamic DNA flip followed by XOR), that maximizes confusion and diffusion operations. Combining image segmentation for key generation, chaotic sequence generation, permutation, and diffusion offers improved unpredictability and resilience to attacks.

Algorithm 1: Key Generation
Step 1: Key generation
The key generation process relies on a statistical analysis of the significant region in the medical image. The U-Net architecture uses different medical datasets, such as RITE35, DRIVE36, BRAT202037, Breast Ultrasound Images Dataset38, GlaS (Gland segmentation dataset)39, and Chest x-ray dataset40, for extracting critical regions from the medical image. All the databases used are publicly accessible. The U-Net architecture is used to segment significant images from medical images, which are the most important part of the image. This considerable image acts as a key to the original image. Each test image has its unique key, which is used to encrypt the image. Four key values (key_xo, key_yo, key_zo, key_wo)) are derived from the pixel values of critical regions in the medical image and allocated as initial conditions to five chaotic sequences. These keys are crucial for initializing the new 5D Hyper chaotic system, which drives the encryption. The statistics of the critical regions are derived from the Eqs. (4–6)
Key \({\mathbf{K}}_{\mathbf{x}}\): Sum of all pixel values, captures the overall brightness or intensity of the extracted (significant) image.
where:
-
\({\text{I}}_{1}\left(\text{i},\text{j}\right)\) is the pixel intensity at position (i,j),
-
R and C are the dimensions of the image.
-
R—Refers to the number of rows in the image.
-
C—Refers to the number of columns in the image.
-
Key \({\text{K}}_{\text{x}}\) : Sum of all Pixel Values
Measures the pixel intensity distribution asymmetry, indicating variations in contrast and structure.
where:
-
E is the mean pixel value
-
\({\upsigma }_{\text{a}}\) is the standard deviation of pixel values.
-
Key \({\text{K}}_{\text{y}}\): Skewness of Pixel Values
-
Key \({\mathbf{K}}_{\mathbf{z}}\): Sum of \({{\varvec{K}}}_{{\varvec{x}}}\) and \({{\varvec{K}}}_{{\varvec{y}}}\)
Combines overall intensity and skewness, providing a value reflecting brightness and contrast.
Key \({\mathbf{k}}_{\mathbf{w}}\): Kurtosis of pixel values
Indicates the concentration of pixel values around the mean, capturing the sharpness or flatness of the intensity distribution.
The subtraction of 3 adjusts for a normal distribution baseline, making it easier to interpret kurtosis relative to standard intensity distributions. These key values are normalised to fall within a suitable range for chaotic sequence generation. The initial condition for the chaotic sequence is allocated as xo = key_xo, yo = key_yo, zo = key_zo, uo = key_wo and vo = key_zo. After normalization, the initial conditions for one test image, such as the Drive test image-1, obtained from the segmented image of U-Net are xo = −0.5, and yo = −1.5, zo =—0.5 and uo = −1.5, vo = −0.5 Similarly, we extracted the initial conditions of the chaotic map for each test image from the critical region of corresponding medical images segmented by U-Net architecture.
Motivation for employing U-net-based segmentation:
U-Net is a comparatively reduced-overhead model with fast execution and provides a balanced architecture that minimizes the trade-off between data security and resource consumption. U-Net is a lightweight model that still achieves segmentation accuracy similar to more complex neural networks. U-Net is well suited technique for real-time encryption, ensuring that system resilience and encryption key computation accuracy are sustained without demanding much computing power.
For comparison of U-Net with different models, we use the Adam optimizer with the binary cross-entropy loss (fit for binary masks) for image segmentation. To prevent overfitting, the training is performed up to 200 epochs with early stopping based on validation loss with patience of ~ 10 epochs). Eight batches are used, and 20% of the training data is divided for validation The parameters are used to validate the performance of the U-Net network, and the performance comparison of the networks is given in Table 4.
Accuracy:
Accuracy is the ratio of actual positive pixels from the background and foreground pixels to the total number of pixels
Precision (Positive Predictive Value):
The proportion of detected positive foreground pixels (predicted positive pixels).
Recall (Sensitivity or True Positive Rate):
The metric measures the proportion of ground truth positive pixels correctly predicted out of all positive classes.
F1-Score:
The harmonic mean of Precision and Recall. It balances the trade-off between the precision and recall parameters.
IoU (Intersection over Union):
Overlap between predicted and ground truth segments divided by their union.
Dice Coefficient:
Measures similarity between predicted and ground truth segments.
Here, TP, TN, FP, and FN refer to the counts of true-positive, true-negative, false-positive, and false-negative pixels on the test data set. Dice and IoU capture region overlap, while Precision/Sensitivity captures pixel-wise accuracy. All metrics are computed on the final predicted binary versus ground truth masks.
As Table 4 shows that U-Net achieves 0.9606 accuracy and a 0.8110 Dice score. It is marginally below Attention U-Net (0.9835/0.9014) and significantly ahead of ResU-Net (0.9594/0.7430). Still, U-Net achieves the optimum balance between the quality of segmented data and computing efficiency for real-time encryption by using fewer parameters and inferring data 25–35% faster.
segmentation‐key robustness:
Segmentation accuracy directly impacts the chaotic sequence of encryption since the encryption key is generated from the segmented region. We use the following measures to reduce the likelihood of segmentation errors:
-
The segmentation output is consistent across samples because of early Stopping, which is based on validation loss and chooses the most generalizable U-Net weights.
-
Morphological Processing is applied to the predicted segmentation mask to suppress distortion and artifacts and ensure a better match with the ground truth region. The lightweight operation enhances privacy and robustness against attacks.
-
Validation metrics, such as IoU or Dice coefficient, are used to determine the quality of segmented regions and detect the degradation of segmented data on a validation dataset. If the segmentation probability falls below a threshold, the encryption process is retrained with a updated weights and corrected mask.
These security measures maintain reliability and safety by ensuring the encryption procedure is closely linked to precise and verifiable segmentation.

Algorithm 2: Function: encrypt_medical_image
Step 2: Zig-zag Scrambling (Confusion Phase)
The first stage of encryption, known as the confusion phase, begins with conventional zig-zag scrambling41. The grayscale image is rearranged in this process according to a zig-zag pattern, reorganising the pixels non-linearly. Zig-zag scrambling is applied iteratively (in this case, 50 iterations) to increase the randomness in the pixel arrangement further. The zig-zag pattern is generated by traversing the image in a diagonal zig-zag order shown in Fig. 7, beginning at the top-left corner and moving alternately up and down. This transforms the image’s pixel arrangement into a new order, creating structural confusion. After several iterations, the scrambled image no longer resembles the source image, making it difficult for an unauthorized person to discern the original data.

Algorithm 3: Zigzag_scramble (image, iterations)

Algorithm 4: Permute_pixels (image, sorted_indices)
Step 3: Chaotic pixel sorting (Permutation)
Next, zig-zag scrambled image pixels are further scrambled using chaotic values from the Z variable of the New 5D hyperchaotic system. The pixel values are arranged based on the chaotic sequence generated by Z. This process, known as chaotic pixel sorting, enhances the confusion by introducing an additional layer of randomness. Pixels are reorganized according to their association with the chaotic sequence, concealing any remaining structural patterns in Eq. (13).
where
-
\({\text{C}}_{1}\) is the confused image.
-
I is the zig-zag image
-
\(\text{Sort }\left(\text{Z}\right)\) provides the new arrangement based on the sorted indices.
Step 4: Dynamic DNA encoding
Four nucleic acid bases make up a DNA sequence: A (adenine), G (guanine), C (cytosine), and T (thymine). C and G are complementary, and A and T are complementary. Two bits, 01, 10, 00, and 11, are typically used to encode the four DNA bases A, C, G, and T. Since 0 and 1 are complementary in binary encoding, so are 00 and 11 and 01 and 10. There are 24 encoding rules when 01, 10, 00, and 11 are encoded using the four bases C, G, A, and T. Of these, only eight DNA rules shown in Table 3. meet the complete relations among the complementary bases.
In the next phase, diffusion is performed by converting the encrypted image from the first phase into a DNA image42, using one of the chaotic sequences as the DNA rule. The hyperchaotic sequence is generated and converted into the DNA rules from 1 to 8 for each pixel value in the encrypted image. Based on the DNA rule number43, each pixel in the confused image is converted into a four-base DNA variable.
where
-
\({C}_{1}\left(i,j\right)\) is pixel value at (i, j) in the Confused image,
-
\({\text{R}}_{1}\left(\text{i},\text{j}\right)\) is DNA rule derived from the 5D chaotic sequence.
-
\({\text{E}}_{\text{DNA}}\left(\text{i},\text{j}\right)\) is the resulting DNA sequence for the confused image at (i,j)
-
\({\text{DNA}}_{\text{Encode}}\) is function mapping pixel values to DNA sequences using \({\text{R}}_{1}\) (i,j).

Algorithm 5: Encode_image_to_dna (image, dna_rules).

Algorithm 6: Perform_dna_flip(dna_image, flip_positions)
Step 5: DNA Flip
Based on the chaotic value, the dynamic DNA flip is performed from the previous stage’s output, which is given in Eqs. (15-17). The hyperchaotic sequence V is converted into a mod 4 value, which gives the center position to the DNA image obtained from the previous step to swap each position of DNA value from left to right of the sequence and right to left of the sequence.
where is \({\text{P}}_{1}\left(\text{i},\text{j}\right)\) center position for the DNA swap (values 1 to 4,\({\text{V}}_{1}\left(\text{i},\text{j}\right) is\) hyperchaotic value at pixel (i, j)
\({\text{E}}_{\text{DNA}}\left(\text{i},\text{j}\right) :\) DNA value for pixel (i, j) with four DNA bases \(\left[{\text{B}}_{1},{\text{B}}_{2},{\text{B}}_{3},{\text{B}}_{4}\right]\)
where \(D^{\prime}_{DNA}\) is swapped DNA sequence for pixel (i, j).
Step 6: Diffusion using hyper chaotic XOR (Diffusion Phase)
In the second stage of the diffusion operation, the pixel values are altered using bitwise XOR operations in conjunction with.
chaotic values from the novel 5D Hyper chaotic system. In this process, the chaotic sequence ‘V’ from the hyperchaotic system is converted into 8-bit binary values. The DNA of the V-binary values is then XORed with the pixel values of the DNA Flip image. This XOR diffusion technique effectively spreads the impact of any single change throughout the entire image, ensuring that even minor changes in the input result in significant variations in the output, thereby enhancing security. The diffusion image is generated by applying the DNA XOR44 operation to the DNA flip image and chaotic sequence- ‘V’ DNA image. Table 5. and Table 6. show the DNA rule and DNA XOR.
where \(\text{V}\left(\text{i},\text{j}\right)\) is the chaotic value at (i,j),\(\text{Bin}\) () is conversion of V(i,j)) to an 8-bit binary value. DNATRANSFORM() is the conversion of binary to a DNA sequence.\({\text{V}}_{\text{DNA }}\left(\text{i},\text{j}\right)\) is the resulting DNA sequence for V image.
where Cipher Image(i,j)\(\text{is}\) pixel value at (i, j) in the diffused image in DNA format.
As steps 5 and 6 explain, the proposed 5D hyperchaotic sequence controls the two diffusion layers. Each pixel value of permuted image is encoded into DNA bases according to the chaotic sequence. Then, it is rotated by a per-pixel index based on the chaos mod four value, guaranteeing that every neighboring pixel exhibits different flip patterns. In stage II (step 6), another chaotic sequence is converted into DNA and XOR-ed with the flipped image individually on each DNA base. Thus, cascading stages of DNA flip diffusion with DNA XOR-ed ensure that even a one-bit change in the source image or the secret key disperses nonlinearly and chaotically across the entire encrypted image, achieving strong pixel dependency and a robust avalanche effect across the entire encrypted image. The simulation results show that NPCR > 99.6% and UACI > 33%, ensuring an intense avalanche effect and demonstrating the security strength of our diffusion process against differential attacks.(Fig. 8).

Algorithm7: dna_xor_diffusion(dna_image, chaotic_dna_sequence)

Algorithm 8: Function: decrypt_medical_image
Experimental results
The U-Net model trains on different medical images to extract critical regions, focusing on areas of interest. Figure 9 and Fig. 10 illustrate the U-Net architecture in action, showcasing the extraction of retinal vessels from original eye images. The U-Net architecture utilizes the RITE dataset from the various source images to extract the retinal vessels from the images. The model uses the RITE dataset, containing 80 training images, to predict retinal features accurately. The U-Net processes 10 test images from the RITE dataset and 20 from the DRIVE dataset during testing. By extracting retinal vessels, the U-Net model highlights significant details in each eye image, which play a crucial role in subsequent analyses. Figure 8 displays the accuracy and loss of the segmenting operations applied to a RITE test image. Figure 11 displays the step-by-step approach of the encryption technique with its corresponding histogram.Fig. 12 shows the two confused stage and two diffused stage outputs with original and decrypted images.
(a)original image, (b) key image, (c) zig-zag scrambled image, (d)confused image, (e) encrypted image (f) decrypted image (g) original image histogram, (h) key image histogram, (i) zig-zag scrambled image histogram, (j) confused image histogram, (k) encrypted image histogram, and (l) decrypted image histogram.
Performance analysis
Statistical analysis
Correlation analysis
Correlation analysis evaluates how effectively encryption disrupts patterns between neighboring pixels. Natural images, like face or retinal scans, often show high correlations due to similarities in structure and brightness. Effective encryption reduces these correlations to near zero, randomizing pixel values and breaking structural patterns. The proposed algorithm prevents attackers from extracting meaningful information from the cipher image. Figure 13 shows the correlation analysis for the original test eye image 1 and its encrypted version.
The correlation coefficient is essential for assessing an encryption algorithm’s security. An encrypted image with a low correlation indicates that the algorithm has successfully eliminated the relationships between nearby pixels, enhancing encryption security. The correlation coefficient rxy45 between two adjacent pixels, Xk and Yk is calculated as
where Xk and Yk are intensity values of adjacent pixels (for example, horizontally, vertically, or diagonally neighboring pixels), EX and EY are the mean intensities of the sets of pixels Xk and Yk, respectively and k refers to the total count of pairs in the image.
Table 7. shows the correlation coefficient value for the medical test image and the encrypted image in the horizontal, vertical, and diagonal directions. The efficacy of the encryption technique is indicated by the reduced correlation coefficient value, which is close to zero when comparing the values of the original test image.
Histogram analysis
By achieving an even distribution of pixel intensities, the algorithm guarantees a uniform histogram46in the encrypted image, effectively hiding patterns and defenses against statistical attacks. Because of this uniformity, which removes obvious connections in pixel values, attackers cannot deduce any information about the original image. Figure 14 shows the histogram of medical images and the encrypted images.
Random test analysis
Chi-square test
The Chi-Square test47 is a statistical technique to assess how well observed frequency distributions match expected ones. It is commonly applied to determine whether a dataset is random. In the context of image encryption, the Chi-Square test examines the arrangement of element values in protected images to ensure they appear random and lack discernible patterns. The chi-square test formula given in the equation
where \({\text{O}}_{\text{i}}\) = Observed frequency of pixel intensities and \({\text{E}}_{\text{i}}\)= Expected frequency (assuming a uniform distribution).
Hypothesis:
Null Hypothesis (H0): The observed pixel intensities follow a uniform distribution.
Alternative Hypothesis (H1): The observed pixel intensities deviate significantly from the uniform distribution.
Degrees of Freedom:
where k is the number of intensity scales (e.g., 256 for 8-bit grayscale images).
Decision rule:
The calculated χ2 value is compared with the critical value from the Chi-Square dispersion table at a given P- value, the significance level (α = 0.05 or α = 0.01) :
χ2 > critical value: Reject H0, indicating a non-uniform distribution.
χ2 ≤ critical value: Fail to reject H0, indicating a uniform distribution.
A low Chi-Square value suggests a uniform distribution of pixel intensities compared to critical values at conventional significance levels (5% or 1%). The chi-square value is given in Table 8. This test helps to validate the security of encryption techniques by making encrypted images resistant to statistical attacks. The algorithm consistently produces Chi-Square values below the critical threshold for all examined medical images.
Potential attack analysis
Cropping attack analysis
Cropping analysis evaluates encryption48 resilience by testing how well the original image recovers after removing portions of the encrypted images. In this study, researchers cropped the encrypted image by 5% and 25% in lateral, perpendicular, and middle directions. The results demonstrated that the encryption method maintains robustness, enabling visible recovery even after significant cropping. Central cropping assessed data protection in the image’s middle, while horizontal and vertical cropping impacted edge content. Figure 15 shows the cropping analysis and corresponding decrypted images. Increasing the cropping percentages introduced more distortion, but the encryption method successfully preserved essential image content despite partial data loss.
Noise attack analysis
Analyzing noise attacks45 is essential for evaluating the reliability of encryption algorithms, especially in real-world communication scenarios where various types of noise attack encrypted images. This proposed algorithm examines the effects of speckle and salt-and-pepper noise on encrypted images. Salt-and-pepper noise visibly distorts images by randomly replacing pixel values with extreme values, either black or white, with noise intensity of 1% 3% 10%. In contrast, speckle noise is a multiplicative noise that can severely degrade image quality, particularly at higher noise levels. This type of noise is introduced with strengths of 1% 3% and 10%., causing granular changes in pixel values and significantly reducing the quality of the decrypted image. Despite noise attacks, most of the source image remains in the decrypted image. Analyzing the effects of these types of noise on the decrypted image allows us to assess the encryption algorithm’s effectiveness and resilience in protecting image authenticity under challenging conditions, as shown in Fig. 16.
Geometric attack analysis
The three types of geometric attacks on the cipher images also evaluate our proposed method’s security. Each distorted cipher image generated by a geometric attack was created as follows as:
-
Rotation by ± 10°
-
Translation by ± 10 pixels along both axes
-
Scaling by factors of 0.8x, 0.9x
The geometrically attacked cipher image was decrypted with the correct key. Figure 17. shows the attacked cipher (top row) and the decrypted result (bottom row). In each case, the decrypted image is the same as the noise-like encrypted image, demonstrating that any geometric deviation restricts the exact decryption of the image. The parameter evaluation is performed for the random decrypted images, which give NPCR > 99.6% and UACI > 33%, quantitatively confirming the avalanche effect under strong geometric disruption. The results ensure that the proposed encryption method effectively withstands rotation, translation, and scaling attacks.
Security analysis
Key sensitivity analysis
The secure image encryption systems must have a key sensitivity factor, guaranteeing that even the slightest alteration to the encryption key produces an entirely different result. It ensures that an incorrect key cannot adequately decrypt the image, offering a strong defence against unwanted access. The experiment demonstrated the encryption technique’s extraordinary sensitivity to key variations when changing the keys x and y during decryption, which failed to generate the original image shown in Fig. 18. The algorithm demonstrates how much the system depends on exact key values to protect against brute-force attacks and maintain data integrity. This sensitivity is necessary to maintain the complexity and unpredictability of existing cryptographic systems.
The Fig. 17 demonstrates the effect of key variation by using the wrong key x and key y with a small change of 10–6 in the algorithm, which results in the incorrect prediction of the original image and validates that the algorithm is highly sensitive to the wrong key value.
Correct key | Wrong Key 1 (x altered) | Wrong Key 2 (y altered) |
|---|---|---|
x = − 1.001050000000000, y = − 1.039000000000000, z = 0.990050000000000, u = − 1.019500000000000, v = − 1.026550000000000 | x = − 1.001051000000000, y = − 1.039000000000000, z = 0.990050000000000, u = − 1.019500000000000, v = − 1.026550000000000 | x = − 1.001050000000000, y = − 1.039001000000000, z = 0.990050000000000, u = − 1.019500000000000, v = − 1.026550000000000x |
Key space analysis
The attacker has access to all encryption systems except the encryption key, which is crucial from the security perspective to protect the key. The brute force attack49 is resisted if the key space is more than 2128.The proposed algorithm has five initial conditions (xo, yo, zo, uo, vo) is specified to a precision of 1015, yielding 1015 ≈ 250 possible values per parameter. Consequently, the combined real‐value key space is (1015)5 = 1075≈2249. Including the permutation, dynamic DNA rule and DNA flip further enlarges the space to beyond 2500. This key size far exceeds the 2128 benchmark, ensuring immunity to brute‐force attacks. Table.9 compares the key space for different encryption methods with our method. It shows that the proposed method enlarges the key space sufficiently to avoid brute-force attacks.
Quantitative analysis
Entropy
Entropy50 quantifies the randomness or unpredictability of pixel values, reflecting an image’s information content. Complex or textured regions exhibit higher entropy due to more significant variability, while smooth areas show lower entropy for the original image. Entropy measures information density by calculating the frequency intensity values in grayscale images. Comparing the entropy of original and encrypted images reveals encryption effectiveness; higher entropy in the encrypted image indicates successful data randomization and enhanced security. Table 10. presents the original medical test image entropy values and encrypted versions.
Mean squared error and peak signal noise to ratio
To quantify their distortion, the Mean Squared Error (MSE) computes the average squared difference between the original and encrypted images’ respective pixel values. It offers an accurate estimate of image quality degradation by providing a clear metric for assessing how much the encrypted image differs from its original counterpart.
where \({{\varvec{I}}}_{1}\left({\varvec{i}},{\varvec{j}}\right)\) and \({{\varvec{K}}}_{1}\left({\varvec{i}},{\varvec{j}}\right)\) are the pixel values at the position \(\left({\varvec{i}},{\varvec{j}}\right)\) R and C represent the image dimensions in the original and encrypted images. It is difficult for unauthorized parties to recover or identify any portion of the original content when the MSE value is high, indicating that the encrypted image differs greatly from the original. Based on the MSE, PSNR51 offers a logarithmic assessment of the encrypted image’s quality compared to the original.
Peak signal noise to ratio
PSNR, which is commonly measured in decibels (dB), is used to evaluate the degree of distortion in the encryption52.
where MAX represents the maximum possible pixel value (255 for an 8-bit image), a larger degree of distortion from the original image is indicated by a lower PSNR, which implies an efficient encryption procedure. Table 10. shows the MSE and PSNR values of various medical images. For secure encryption, a high MSE and low PSNR value work together to ensure that the encrypted image cannot be identified from the original.
Differential attack analysis
A differential attack is a cryptanalysis technique that exploits the relationship between the original and encrypted images by introducing small changes to the original image and analyzing their impact on the encrypted output53. Secure encryption technology ensures that even minor changes to the source image produce significant and unpredictable alterations in the encrypted image. Metrics such as the Number-of-Pixels Change Rate (NPCR) and Unified Average Changing Intensity (UACI) measure the effectiveness of an encryption method in combating such attacks.
NPCR
When a single pixel value in the source image changes, NPCR calculates54 the proportion of pixels that change in the encrypted image. This test measures the avalanche effect, or how sensitive the encryption process is for slight modification of the original image pixel.
where R and C are the image dimensions (height and width),
\({\text{D}}_{1}\left(\text{i},\text{j}\right)\) is the change at each pixel, as defined as the total number of pixel variations between the two encrypted images counted, and the percentage result is displayed.
UACI
Unified Average Changing Intensity measures50 the mean pixel value difference between two encrypted images created from original images with a slight difference (such as a single pixel alteration). UACI measures the intensity of pixel changes, whereas NPCR counts them.
where \({\text{c}}_{1} \left(\text{i},\text{j}\right)\) and \({\text{c}}_{2}(\text{i},\text{j})\) are the image pixel values of the two encrypted images, R and C represent the image dimensions. The NPCR and UACI values of different medical images are given in Table 10.
The results in Table 10 show that NPCR values vary from 99.57% to 99.65%, revealing that all the pixel values between two different ciphered images obtained from the single bit change in the original image, resulting in different values for the encrypted image satisfy strong sensitivity to the input changes. The UACI values vary from 33.31% to 33.66%. The low value of UACI shows that the algorithm results in moderate variations in the pixel brightness, which is very important in the security measures of image encryption. In the paper42,55, the theoretical ideal value of NPCR is 99.6094%, and the UACI value is approximately 33.46% for 8-bit greyscale images. The values obtained by our proposed method for the various medical images equal the ideal value of the reference paper, proving the robustness of our process in defending against differential attack.
Performance comparison with existing algorithms
Critical metrics like correlation coefficients, entropy, NPCR, and UACI are used to assess the suggested encryption algorithm on six different kinds of medical images (RITE, DRIVE, Breast, Gland, Chest, and Brain) and compare it with previous techniques are shown in Table 11. The proposed method matches and consistently surpasses current algorithms’ performance, obtaining uniformly low horizontal, vertical, and diagonal correlation values. The Brain image, in particular, suggests excellent encryption quality and minimal inter-pixel dependency, further reinforcing the superiority of our proposed algorithm. Entropy values obtained by the suggested approach are around the optimal value of 8, indicating good unpredictability and robustness against statistical attacks that should validate the proposed work. The Chest image, in particular, outperformed most current techniques, achieving an entropy score of 8.0000. The NPCR values, which measure resistance to differential attacks, consistently meet or exceed the crucial threshold of 99.6%, with the method recording values of about 99.61% for most images. The UACI value of the breast image is approximately 33.5208, which is within the critical range (~ 33.46%), and it shows the encryption method adaptability.
The proposed work is strong and successful in securing medical data, which results in pixel decorrelation, significant uncertainty and resistance to differential attacks. The research performs better than conventional methods, ensuring robustness and optimal encryption for sensitive medical images.
Computational complexity and time performance analysis
An algorithm’s computation time58 is analyzed to assess its efficiency. In this proposed work, Critical region segmentation using U-Net and the encryption technique are the two phases of operations used to analyze computational overhead.
Critical Region Extraction (Segmentation Phase).
The computation time for the U-shaped encoder and decoder operation used to extract the critical regions is based on the depth and size of the input image.
L—Number of convolution layers in the customized U-Net model. N x N -represents the shape of the medical image. The segmentation precision and computation overload are balanced by a medical image size of 256 × 256.
Encryption Phase (5D Hyperchaotic and DNA Encoding):
After key generation using segmentation, encryption is performed using hyper chaotic systems and DNA-based operations. This process involves generating chaotic sequences, scrambling pixel positions, performing DNA encoding, dynamic DNA flipping, and dynamic XOR-based diffusion.
where the number of pixels in the input image is given as P, among the various encryption steps, the chaotic pixel sorting operation has the most significant impact on complexity, accounting for the logarithmic term.
The total computational complexity of the proposed algorithm is given in Eq. (31)
Time complexity (execution time)
The platform used to evaluate the overall run time of the encryption algorithm:
-
Segmentation phase for key generation: Google Colab with an NVIDIA Tesla T4 GPU
-
Encryption phase: MATLAB R2021a on a Dell i5 CPU (4 cores, 16 GB RAM).
The computational infrastructure, which includes processor design, system software, memory footprint, implementation specifics, and build parameters, significantly impacts cipher performance measures like encryption latency and bandwidth. As a result, comparing ciphers across different hardware and software stacks produces inaccurate comparisons56. The execution time for a single 256 × 256 grayscale medical image is given in Table 12.
Although U-Net inference for a single 256 × 256 image requires ≈0.03 s on a mid-range GPU, segmentation is performed only once offline to derive the chaotic-map key. For real-time or large-scale deployments, segmentation can be accelerated via (1) model compression (structure simplification, quantization), (2) lightweight U-Net variants (depth wise separable convolutions), (3) tiled or batch inference, and (4) deployment on hardware accelerators (GPUs, FPGAs). These strategies yield 2–10 × increase in speed with minimal accuracy trade-offs.
Feasibility on embedded medical IoT platforms:
The suggested encryption method is resource-efficient and customizable, facilitating deployment for embedded computing systems even though our work has been tested on general computing hardware. After architecture-aware refinement, devices like the NVIDIA Jetson Nano (with GPU acceleration and 4 GB RAM) and Raspberry Pi 4 (with a quad-core ARM Cortex-A72 processor and 2–8 GB RAM) may be able to support the algorithm. Future research will need to address actual deployment, but we predict that hardware acceleration, fixed-point implementation, and practical coding techniques may allow real-time processing on such devices, making the proposed algorithm feasible for safe medical IoT systems.
Conclusion and future scope
This paper shows that the proposed medical image encryption algorithm combines a new 5D hyperchaotic system with a U-Net network, demonstrating excellent security and computational efficiency. The confidential image extracted from the medical image is used as the chaotic system’s initial condition to prevent the medical image from being accessed by unauthorized people. The encrypted image’s high entropy, which is close to 8, indicates that it is more unpredictable than the original image. Additionally, Correlation coefficients close to zero in all directions indicate that the cypher image has minimal pixel correlation, disrupting patterns and enhancing security, and correlation analysis demonstrates a uniform distribution. A desirable aspect of encryption is the notable distortion between the original and encrypted images, characterized by low PSNR values and high MSE. The proposed algorithm achieves an NPCR of 99.67% and a UACI of 33.99%, which shows that it is sensitive to pixel-level changes to prevent differential assaults. These values are close to the critical threshold. The algorithm generates a larger key space of 2500 which is far beyond the 2128 to block the brute force attack. The algorithm (U-Net segmentation + encryption) completes approximately 2.93 s for 256 × 256 images, validating its suitability in real-time medical applications. Furthermore, the total computational complexity O (L × N2 + P log P) ensures that the algorithm is scalable for real-time implementation. A performance comparison of encryption algorithms with existing techniques confirms their security and effectiveness in safeguarding confidential medical images in real-world applications.
The proposed research is limited only to 2D images. Future research will use 3D U-Net and volumetric chaotic integrating to expand this method to 3D medical data (such as MRIs and CT scans), guaranteeing safe encryption of depth-wise structures. Lightweight segmentation and quick chaos-based operations will also be investigated for real-time encryption of video streams (such as ultrasound). The current method will improve in the future by using several dynamic strategies for dispersion and rearrangement procedures to achieve better results. Further investigations might use advanced deep learning models to generate complex, image-specific encryption keys obtained from anatomical data to increase medical image encryption’s versatility and safety. In future work, we plan to integrate the post quantum cryptographic techniques with our hybrid chaotic system to ensure resilience against the quantum attacks. Integrating real-time encryption methods for telemedicine and cloud storage paves the way for future innovations in patient data management to reinforce security and performance without ensuring significant advances in continuing research.
Data availability
The datasets generated during and/or analyzed during the current study are available from the corresponding author upon reasonable request. 2. All data generated or analyzed during this study are included in this published article. The datasets analyzed during the current study are available in https://www.sciencedirect.com/science/article/pii/S0933365721001093?via%3Dihub; https://link.springer.com/chapter/https://doi.org/10.1007/978-3-642-40763-5_54https://drive.grand-challenge.org/https://www.sciencedirect.com/science/article/pii/S2352340919312181https://ieeexplore.ieee.org/document/7,109,172https://ieeexplore.ieee.org/document/6,616,679.
References
Rohhila, S. & Singh, A. K. Deep learning-based encryption for secure transmission digital images: A survey. Comput. Electr. Eng. 116, 109236 (2024).
Zia, U. et al. Survey on image encryption techniques using chaotic maps in spatial, transform and spatiotemporal domains. Int. J. Inf. Secur. 21, 917–935 (2022).
Singh, A. K., Anand, A., Lv, Z., Ko, H. & Mohan, A. A survey on healthcare data: A security perspective. ACM Trans. Multimed. Comput. Commun. Appl. 17, 1–26 (2021).
Prasad, S. & Singh, A. K. Survey on medical image encryption: From classical to deep learning-based approaches. Comput. Electr. Eng. 123, 110011 (2025).
Khurana, N. & Dua, M. A novel one-dimensional Cosine within Sine chaotic map and novel permutation–diffusion based medical image encryption. Nonlinear Dyn. 109, 1–21 (2024).
Ningthoukhongjam, T. R., Heisnam, S. D. & Khumanthem, M. S. Medical image encryption through chaotic asymmetric cryptosystem. IEEE Access 12, 73879–73888 (2024).
Dhingra, D. & Dua, M. Medical video encryption using novel 2D Cosine-Sine map and dynamic DNA coding. Med. Biol. Eng. Comput. 62, 237–255 (2023).
Demla, K. & Anand, A. RISE: Rubik’s cube and image segmentation based secure medical images encryption. Multimed. Tools Appl. 83, 70343–70367 (2024).
Wang, B. et al. High-security dual-image encryption based on fingerprint key with strong robustness. Optik 288, 171245 (2023).
Liu, Z. & Xue, R. Medical image encryption using biometric image texture fusion. J. Med. Syst. 47, 112 (2023).
Bhattacharjee, S., Gupta, M. & Chatterjee, B. Time efficient image encryption-decryption for visible and COVID-19 X-ray images using modified chaos-based logistic map. Appl. Biochem. Biotechnol. 195, 2395–2413 (2023).
Masood, F. et al. A lightweight chaos-based medical image encryption scheme using random shuffling and XOR operations. Wirel. Pers. Commun. 127, 1405–1432 (2022).
Ravichandran, D. et al. An efficient medical image encryption using hybrid DNA computing and chaos in transform domain. Med. Biol. Eng. Comput. 59, 589–605 (2021).
Deng, Q. et al. Nonvolatile CMOS memristor, reconfigurable array, and its application in power load forecasting. IEEE Trans. Ind. Inform. 20, 6130–6141 (2023).
Wang, Y., Su, P., Wang, Z. & Sun, J. FN-HNN coupled with tunable multistable memristors and encryption by Arnold mapping and diagonal diffusion algorithm. IEEE Trans. Circuits Syst. I https://doi.org/10.1109/TCSI.2024.3516722 (2024).
Sun, J. et al. Memristor-based parallel computing circuit optimization for LSTM network fault diagnosis. IEEE Trans. Circuits Syst. I https://doi.org/10.1109/TCSI.2024.3516325 (2024).
Liu, J., Xiong, F., Zhou, Y., Duan, S. & Hu, X. Bioinspired memristive neural network circuit design of cross-modal associative memory. IEEE Trans. Cogn. Dev. Syst. 16, 794–808 (2023).
Islam, M. O. U., Parah, S. A., Malik, B. A. & Malik, S. A. Lightweight medical-image encryption technique for IoMT based healthcare applications. Multimed. Tools Appl. 83, 1–36 (2024).
Tang, J., Lu, M. & Zhang, Z. A novel asymmetric encryption framework based on a 2D hyperchaotic map and enhanced S-box for secure medical image transmission. Phys. Scr. 100, 015239 (2024).
Li, Q. & Chen, L. An image encryption algorithm based on 6-dimensional hyperchaotic system and DNA encoding. Multimed. Tools Appl. 83, 5351–5368 (2024).
Sheela, S. J., Sanjay, A., Suresh, K. V., Tandur, D. & Shubha, G. Image encryption based on 5D hyperchaotic system using hybrid random matrix transform. Multidimens. Syst. Signal Process. 33, 579–595 (2022).
Wang, X., Su, Y., Liu, L., Zhang, H. & Di, S. Color image encryption algorithm based on Fisher-Yates scrambling and DNA subsequence operation. Vis. Comput. 39, 1–16 (2023).
Sun, S. A new image encryption scheme based on 6D hyperchaotic system and random signal insertion. IEEE Access 11, 66009–66016 (2023).
Lai, Q. & Hua, H. Secure medical image encryption scheme for Healthcare IoT using novel hyperchaotic map and DNA cubes. Expert Syst. Appl. 264, 125854 (2025).
Lai, Q. & Ji, L. A bidirectional cross-scrambling medical image encryption scheme incorporates compressed sensing and its application in IoMT. IEEE Trans. Circuits Syst. Video Technol. (2025).
Grassberger, P. & Procaccia, I. Estimation of the Kolmogorov entropy from a chaotic signal. Phys. Rev. A 28, 2591–2593 (1983).
Şimşek, C., Erkan, U., Toktas, A., Lai, Q. & Gao, S. Hexadecimal permutation and 2D cumulative diffusion image encryption using hyperchaotic sinusoidal exponential memristive system. Nonlinear Dyn. 113, 1–32 (2025).
Ye, C., Tong, X., Zhang, M. & Wang, Z. A data hiding scheme in encrypted images using non-degenerate chaotic system and hybrid coding. Nonlinear Dyn. 113, 1–23 (2025).
Lai, Q., Hu, G., Erkan, U. & Toktas, A. A novel pixel-split image encryption scheme based on 2D Salomon map. Expert Syst. Appl. 213, 118845 (2023).
Ustun, D. & Sahinkaya, S. Design of secure S-Boxes via novel 2D-Zettle chaotic map and ABC algorithm for robust image encryption. Math. Comput. Simul. 210, 1–16 (2025).
Lai, Q., Zhang, H., Ustun, D., Erkan, U. & Toktas, A. Index-based simultaneous permutation-diffusion in image encryption using two-dimensional price map. Multimed. Tools Appl. 83, 28827–28847 (2024).
Jan, A., Parah, S. A. & Malik, B. A. IEFHAC: Image encryption framework based on Hasselberg transform and chaotic theory for smart health. Multimed. Tools Appl. 81, 18829–18853 (2022).
Li, S., Liu, J. & Song, Z. Brain tumor segmentation based on region of interest-aided localisation and segmentation U-Net. Int. J. Mach. Learn. Cybern. 13, 2435–2445 (2022).
Morano, J., Hervella, A. S., Novo, J. & Rouco, J. Simultaneous segmentation and classification of the retinal arteries and veins from color fundus images. Artif. Intell. Med. 118, 102116 (2021).
Hu, Q., Abramoff, M. D. & Garvin, M. K. Automated separation of binary overlapping trees in low-contrast color retinal images. In Med. Image Comput. Comput.-Assist. Interv. MICCAI, 16th International Conference, Nagoya, Japan, 436–443 (2023).
Staal, J., Abramoff, M. D., Niemeijer, M., Viergever, M. A. & van Ginneken, B. DRIVE: Digital retinal images for vessel extraction. Data set. https://drive.grand-challenge.org/ (2004)
Menze, B. H. et al. The Multimodal Brain Tumor Image Segmentation Benchmark (BRATS). IEEE Trans. Med. Imaging 34, 1993–2024. https://doi.org/10.1109/TMI.2014.2377694 (2015).
Al Dhabyani, W., Gomaa, M., Khaled, H. & Fahmy, A. Dataset of breast ultrasound images. Data Brief 28, 104863. https://doi.org/10.1016/j.dib.2019.104863 (2020).
Sirinukunwattana, K., Snead, D. R. J. & Rajpoot, N. M. A stochastic polygons model for glandular structures in colon histology images. IEEE Trans. Med. Imaging 34, 2591–2593. https://doi.org/10.1109/TMI.2015.2433900 (2015).
Jaeger, S. et al. Automatic tuberculosis screening using chest radiographs. IEEE Trans. Med. Imaging 33, 233–245. https://doi.org/10.1109/TMI.2013.2284099 (2024).
Wang, X. & Sun, H. A chaotic image encryption algorithm based on zigzag-like transform and DNA-like coding. Multimed. Tools Appl. 78, 34981–34997 (2019).
Liang, Q. & Zhu, C. A new one-dimensional chaotic map for image encryption scheme based on random DNA coding. Opt. Laser Technol. 160, 109033 (2023).
Belazi, A., Talha, M., Kharbech, S. & Xiang, W. Novel medical image encryption scheme based on chaos and DNA encoding. IEEE Access 7, 36667–36681 (2019).
Banu, S. A. et al. Healthcare with data care—a triangular DNA security. Multimed. Tools Appl. 83, 21153–21170 (2024).
Wang, M. et al. A new 2D-HELS hyperchaotic map and its application on image encryption using RNA operation and dynamic confusion. Chaos Solitons Fractals 183, 114959 (2024).
Yasser, I., Khalil, A. T., Mohamed, M. A., Samra, A. S. & Khalifa, F. A robust chaos-based technique for medical image encryption. IEEE Access 10, 244–257 (2022).
Haq, U. T. & Shah, T. 4D mixed chaotic system and its application to RGB image encryption using substitution-diffusion. J. Inf. Secur. Appl. 61, 102931 (2021).
Kumar, M. A new RGB image encryption algorithm based on hyper-chaotic-discrete-wavelet-packet-transform. Multimed. Tools Appl. 83, 58349–58374 (2024).
Long, B. et al. A novel medical image encryption scheme based on deep learning feature encoding and decoding. IEEE Access 12, 38382–38398 (2024).
Kamal, S. T., Hosny, K. M., Elgindy, T. M., Darwish, M. M. & Fouda, M. M. A new image encryption algorithm for grey and color medical images. IEEE Access 9, 37855–37865 (2021).
Zhang, Z., Tang, J., Zhang, F., Huang, T. & Lu, M. Medical image encryption based on Josephus scrambling and dynamic cross-diffusion for patient privacy security. IEEE Trans. Circuits Syst. Video Technol. 34, 9250–9263 (2024).
Man, Z., Gao, C., Dai, Y. & Meng, X. Dynamic rotation medical image encryption scheme based on improved Lorenz chaos. Nonlinear Dyn. 2024, 1–2 (2024).
Sahasrabuddhe, A. & Laiphrakpam, D. S. Multiple images encryption based on 3D scrambling and hyper-chaotic system. Inf. Sci. 550, 252–267 (2021).
Wu, Y., Zhang, L., Berretti, S. & Wan, S. Medical image encryption by content-aware DNA computing for secure healthcare. IEEE Trans. Ind. Informat. 19, 2089–2098 (2023).
Khan, M. S. et al. Chaotic quantum encryption to secure image data in post-quantum consumer technology. IEEE Trans. Consum. Electron. 70, 7087–7101 (2024).
Abdellatef, E., Naeem, E. A. & El-Samie, M. DeepEnc: deep learning-based CT image encryption approach. Multimed. Tools Appl. 83, 11147–11167 (2024).
Janakiraman, S., Sivaraman, R., Sridevi, A., Upadhyay, H. N. & Amirtharajan, R. Integrity-verified lightweight ciphering for secure medical image sharing between embedded SoCs. Sci. Rep. 15, 7465. https://doi.org/10.1038/s41598-025-91431-z (2025).
Zefreh, E. Z. An image encryption scheme based on a hybrid model of DNA computing, chaotic systems and hash functions. Multimed. Tools Appl. 79, 24993–25022 (2020).
Acknowledgements
The authors thank the Vellore Institute of Technology, Vellore, India for providing infrastructural support to carry out this research work
Funding
Open access funding provided by Vellore Institute of Technology.
Author information
Authors and Affiliations
Contributions
Subathra S. analyzed the data, conducted the experiments, and wrote the main manuscript text. Thanikaiselvan V. provided feedback, helped write and edit the manuscript, and guided the proposed work. Both authors reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Ethics approval
All authors have read, understood, and have complied as applicable with the statement on “Ethical responsibilities of Authors” as found in the Instructions for Authors.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Subathra, S., Thanikaiselvan, V. Enhanced security for medical images using a new 5D hyper chaotic map and deep learning based segmentation. Sci Rep 15, 22628 (2025). https://doi.org/10.1038/s41598-025-04906-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-025-04906-4
Keywords
This article is cited by
-
A lightweight multi round confusion-diffusion cryptosystem for securing images using a modified 5D chaotic system
Scientific Reports (2025)
-
Generating grid hyperchaotic attractors for image encryption application
Nonlinear Dynamics (2025)