Abstract
The cyber-physical deep coupling makes distribution systems face severe operation risks under small-probability and high-impact disasters. To enhance the resilience of cyber-physical distribution systems against typhoons, this paper proposes a resilience-oriented robust optimization model, in which planning-operational restoration measures are incorporated into a prevention and emergency response framework. In the prevention response stage, line hardening, battery storage systems and soft open point deployment, as well as wireless communication configuration are conducted before typhoons. During the typhoons, the emergency response aims at mitigating power outages by regulating battery storage systems, soft open points, local controllers, and distribution generations. Moreover, considering the time-varying characteristics of typhoon path, a spatially and temporally extended N-k uncertainty set is constructed for overhead line status. Thereafter, the proposed robust optimization model is recast to a mixed-integer linear programming problem, which can be solved by a nested column-and-constraint generation algorithm. Numerical results show that the proposed resilience-oriented strategies can respond rapidly to the worst-case scenario of typhoon attacks with cost-effective performance.
Similar content being viewed by others
Introduction
Background and motivation
With the introduction of computing, communication, and sensing technologies, distribution systems are undergoing digital and intelligent transformation into cyber-physical distribution systems (CPDS)1. However, deep cyber-physical coupling makes the distribution system face severe operation risks under small probability and high-impact natural disasters. For example, the 2008 ice storm that caused outages in the Southern Chinese Power Grid and the 2016 Xiamen Island blackout caused by Typhoon Meranti provide a factual basis to confirm that cyber-physical coupling failures can lead to catastrophic cascading failures in the CPDS2. In recent years, the increasing frequency of extreme weather disasters due to global warming has posed significant challenges to the resilience of the CPDS3. Against this background, it is urgent to develop resilience strategies for the CPDS against cyber-physical coupling failures during extreme disasters.
State-of-the-Art
To realize the ambitious vision of the resilient power system, many studies make a great effort to develop effective resilience enhancement strategies. On the physical side, reinforcement strategies, as planning-oriented measures, can protect the CPDS from natural disasters4. However, strengthening and upgrading the entire CPDS is too expensive to achieve large-scale and all-around reinforcement. Accordingly, researchers try to achieve an economic combination of various planning strategies, including the deployment of distribution generators (DGs)5, battery storage systems (BSSs)6, and soft open points (SOPs)7, as well as microgrid formation in references8,9, etc. Notably, the effectiveness of these measures needs to be ensured with consideration of the interaction between the cyber and physical systems. The reason is that the CPDS relies on communication networks for control. However, since communication fiber is laid along the overhead ground wire to form an optical fiber composite overhead ground wire (OPGW), extreme disasters can simultaneously damage both power lines and communication links2,10,11, leading to cyber-physical coupling failures.
In terms of the impact of communication failures on distribution systems, an integrated planning framework is proposed for cyber-physical active distribution systems in reference12, where the working status of BSS relies on control commands from the control center. Nevertheless, the cyber-physical interdependence of DGs is ignored here. According to IEEE Standard 154713, it is recommended that DG disconnected from communication with the control center, shall be divorced from the distribution system14. Reference15 presents that the operational state of SOP is controlled by communication systems under cyber attacks. However, the advantages of DG and BSS to improve the resilience of CPDSs and the corresponding cyber-physical interaction are not discussed in reference15. Besides, the load control is also missing in references12,14,15. To this end, the authors of references16,17 believe that when load buses cannot receive control commands, local controllers are activated to support the continued operation of load buses if the load power can be supplied. Despite the cyber-physical coupling modeling for load buses in references16,17, other flexible resources like BSS and DG are utilized to improve the resilience of the CPDS therein. Based on the above discussion, it is necessary that multiple resources be coordinately planned and dispatched for resilient CPDS while modeling their cyber-physical interdependence.
Another measure to improve the resilience of CPDSs is designing redundant communication measures against communication failures. In reference18, a main-alternate routing strategy is proposed for the remedial control services of smart grids. On this basis, a saturation defense method is developed against cyber-attacks in reference19. To ensure the effectiveness of the strategy and method mentioned in the literature above, backup communication should be considered to support the operation of the CPDS. Due to advanced 5G technology, wireless communication technologies are competent alternatives as they can well ensure remote control and monitoring functions for the power grid20,21. In reference22, emergency communication vehicles are utilized to construct a wireless communication network, which helps restore the unserved customers as quickly as possible. In reference23, the ad hoc wireless device-to-device communication can assist the power network reconfiguration and form stable microgrids efficiently after disasters. However, wireless communication measures utilized in references20,21,22,23 are just for quick post-disaster restoration. How to effectively and economically deploy wireless communication before disasters is pending.
Moreover, it is essential to consider the uncertainty of cyber-physical coupling failures when making proactive decisions for the CPDS against natural disasters. As a result, numerous studies have focused on stochastic programming (SP)7,8,24,25, robust optimization (RO)8,12, and the combination of these two techniques26,27 to assess the effects of natural disasters on power systems. Notably, as the number of possible contingencies grows, solving the SP problem becomes increasingly challenging. In addition, RO often leads to overly conservative decisions without considering specific probability information. Although references26,27 avoid the disadvantages of RO and SP, they do not consider the sequential nature of typhoon attacks. Given that typhoons often exhibit varying tracks and intensities, overhead lines can be sequentially damaged as the typhoon evolves28,29, simultaneously causing interruptions both in power lines and communication links. To model these time-varying characteristics, considerable research has focused on capturing the spatiotemporal dynamics of outages in power systems, using methods like the Markov property28,29. Reference30 introduces a stochastic model for typhoon paths, where the probability of power lines being affected varies along each path. Furthermore, in references28,29, a multi-state regional weather model is developed to assess the reliability of the power system during hurricanes. Similarly, references31,32 present a multi-zone and multi-stage uncertainty set to capture the dynamic impact of typhoons on power systems. It should be noted that references28,29,30,31,32 only focus on the electrical component failures, but do not include the impact of dynamic typhoons on communication infrastructures and cyber-physical interaction. Therefore, in terms of the time-varying characteristics of typhoon path, it is necessary to construct a spatially and temporally extended N-k uncertainty set for the robust resilient-oriented design of CPDSs.
Contributions
This paper proposes a two-stage RO model to enhance the resilience of the CPDS. The contributions are summarized as follows:
-
To enhance the resilience of the CPDS against typhoons, this paper proposes a robust resilient-oriented design framework, in which comprehensive planning-operational measures are coordinated in terms of cyber-physical coupling. Specifically, line hardening, BSSs and SOPs deployment, and wireless communication configuration are conducted before typhoons. During the typhoons, the emergency response aims at mitigating power outages by regulating BSSs, SOPs, local controllers, and DGs through cyber-physical interaction.
-
The proposed robust optimization model is tailored for the resilient CPDS against typhoons. In view of the time-varying characteristics of typhoon paths, the Monte Carlo method is used to evaluate the vulnerable lines. On this basis, a spatially and temporally extended N-k uncertainty set is built for the status of overhead lines consisting of communication links and power lines. Then, the impact of cyber-physical coupling failures on CPDSs is considered to derive a robust decision-making.
The resilient CPDS formulation
Structure of the resilient CPDS
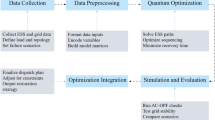
The framework of the resilient CPDS is presented in Fig. 1. When a typhoon occurs, overhead lines could be brought down due to collapsed poles caused by high winds4. Since the optical fiber of an EPON-based communication network is often placed on the ground wire of the overhead transmission line10, optical fibers and distribution lines are damaged with the same failure probability, which causes cyber-physical coupling failures modeled by a spatially and temporally extended N-k uncertainty set. As a result, communication between feeder terminal units (FTUs) and the control center is interrupted, and thus sequential outages will take place. To tackle this issue, line hardening, SOPs, DGs, BSS, and wireless communication configuration are regarded as a coordinated planning-operation strategy to enhance the resilience of CPDS.
Communication network modeling
In the wired communication network, the optical fiber between two cyber nodes stands for a cyber link. Accordingly, the wired network can be denoted as the connected graphs \({\mathcal {G}}_{C}\left( {\mathcal {N}}_{C}, {\mathcal {L}}_{C}\right)\), where \({\mathcal {N}}_{C}\) and \({\mathcal {L}}_{C}\) are the sets of cyber nodes and links, respectively. From the control center \({\mathcal {N}}_{C,con}\) to the destination node \(k\), the information flow can be modeled as
where Constraint (1) indicates the connectivity between the control center and other cyber nodes. Constraint (2) represents that the control center, as the sender of the information flow, has only outgoing traffic but no incoming traffic. Equation (3) ensures that the traffic incoming at the destination node is equal to the traffic required by communication services. Equation (4) enforces all relay nodes to satisfy the information flow balance. Constraint (5) restricts the transmission traffic of cyber links. Constraint (6) gives reference values of \(\phi _{ij,k,t}\). \(\left| \sigma _{ij,k,t} \right|\) in (5) can be linearized by \(\kappa \ge \sigma _{ij,k,t}\) and \(\kappa \ge -\sigma _{ij,k,t}\).
To ensure the reliable operation of the CPDS against typhoons, the buses of DG, BSS, and SOP can be configured with 5G wireless communication in case of wired communication interruption.
Cyber-physical coupling modeling
1) Control and operation constraints of DG
2) Control and operation constraints of BSS
where the first line of (9) limits the charging and discharging status of BSS. The second and third lines of (9) restrict the charging and discharging power of BSS. The energy level of BSS is expressed in the fourth line of (9). The fifth line of (9) gives the range limits of the energy level.
3) Control and operation constraints of SOP
where the first and second lines of (10) limit the active and reactive power outputs of SOP. The third line of (10) ensures the active power flow balance of SOP.
4) Control and operation constraints of load power
When communication is interrupted on some buses, local control on these buses can be activated to restore power supply if the load power can be fully met16. The corresponding constraints can be seen in Table 1. Based on the second line of Table 1, we can know that when loads can be fully met, there does not exist load shedding on bus i with the local control, even though bus i disconnects communication with the control center. However, when loads on bus i cannot be fully met and bus i disconnects communication with the control center, all loads on bus i should be shed on the third line of Table 1. In addition, if bus i is communication-connected with the control center, the corresponding load shedding amount can be controlled by the control center on the fourth and fifth lines of Table 1.
The nonlinear terms \(\psi _{i,t} \mu _{i,t}\) in Eq. (11) can be linearized as follows:
Two-stage robust optimization model
In this paper, a two-stage RO model is developed for the resilient CPDS. Set different weight coefficients for power loads, the objective function is represented as
Planning decisions in the first stage
Within a constrained budget \(\bar{C}\), line reinforcement, BSS and SOP deployment, and wireless communication configuration are preventive planning decisions in (14), (15), (16), and (17) against upcoming typhoons, respectively.
Uncertainty set of vulnerable lines
When encountering a typhoon, overhead line failures and distribution pole failures can be considered independent of each other. Therefore, mapping fragility curves30, the probability of transmission line failure can be obtained as:
As can be seen in Eq. (19), c and p are the number of wire segments and distribution poles, respectively.
Set a failure probability threshold \(\textrm{Pr}_{V.th}\) as the criterion to determine transmission line failure. When the failure probability \(\operatorname {Pr}(i j, t)\) exceeds the threshold, the overhead line ij is prone to failure.
Considering the sequential impact of typhoon attacks on the CPDS, we assume that a typhoon passes through the CPDS area \(\Omega _{1}\), \(\Omega _{2}\), \(\cdots\), \(\Omega _{\xi }\) in time series \(t_{1}\), \(t_{2}\), \(\cdots\), \(t_{\xi }\). To deal with the temporal uncertainty of line status, a multi-stage and multi-zone uncertainty set is constructed as
The line status depends on whether lines are reinforced or attacked30. Usually, the reinforced line can be immune to typhoon attacks. In addition, the N-k criterion is adopted to limit the contingencies of overhead lines. Therefore, a spatially and temporally extended N-k uncertainty set is constructed as
The bilinear terms \(h_{i j}u_{i j, t}\) of the two binary variables in (22) can be linearized as
Emergency response decisions in the second stage
Based on the resilient CPDS model (1)-(11), the power flow can be evaluated in the control center as
For the sake of clarity, the emergency operation set is denoted as \({\mathcal {Y}}\), constrained by (35). \(\varvec{y_{1}}\) contains the binary variables. \({\varvec{y}}_{2}\) includes the continuous variables and binary variables.
Solution method
To facilitate the solution of the proposed model, the first and second lines of (10) can be linearized as
Definition 1
Without loss of generality, the proposed two-stage RO model can be rewritten as compact matrices:
Remark
There exist variables \(y_{1}\) and \(y_{2}\) in the inner-level min problem of (38). The binary variables include charging indicator \(\beta _{b,t,\textrm{ch}}^{\textrm{BSS}}\) and discharging indicator \(\beta _{b,t,\textrm{dis}}^{\textrm{BSS}}\) of BSS, local control status \(\mu _{i,t}\), wired communication indicator \(v_{i,t}\), work status \(\phi _{i j,t}\) of cyber link, final communication status \(\psi _{k,t}\), as well as load shedding status \(\tau _{i,t}^{1}\) and \(\tau _{i,t}^{2}\).
Proposition
The two-stage model (38) can be efficiently solved with the enumeration of integer variables \(y_{1}\), which include just three binary variables \(\beta _{b,t,\textrm{ch}}^{\textrm{BSS}}\), \(\beta _{b,t,\textrm{dis}}^{\textrm{BSS}}\), and \(\mu _{i,t}\), ensuring the tractable solutions of the proposed model according to NC&CG33.
Proof
According to reference33, the tri-level model (38) is equivalent to the formulation (39) by separating enumeration variables \(y_{1}\) from other variables \(y_{2}\). Notably, \(y_{2}\) still contain some binary variables \(v_{i,t}, \phi _{i j,t}, \psi _{k,t},\tau _{i,t}^{1},\tau _{i,t}^{2}\), leading to challenges to the NC&CG utilization. In this regard, we further divided \(y_{2}\) into \(y_{21}\) in (39) and \(y_{22}\) in (40) as follows:
When \(y_{1}\) is fixed as \(y_{1}^{*}\) (charging indicator \(P_{b, t, \textrm{ch}}^{\textrm{BSS}}\) and discharging indicator \(P_{b, t, \textrm{dis}}^{\textrm{BSS}}\) of BSS, as well as local control status \(\mu _{i,t}\) are given), the indicator u of line attack directly determines binary variables \(y_{21}\). For clarity, we explain this mapping relationship one by one based on our communication model (1)-(6) and load control model (11) as below:
1) In the communication model (1)-(6), given the u and the fixed \(h_{i j}\) in the first stage, line status \(\theta _{i j,t}\) can be determined by (22). Then, \(v_{i,t}\) and \(\phi _{i j,t}\) obtained from (1)-(6) are exact, which means that u is the corresponding decision variable for \(v_{i,t}\) and \(\phi _{i j,t}\). Moreover, since \(\omega _{i}\) is the indicator of wireless communication configuration that has been fixed in the first stage, \(\psi _{k,t}\) can be derived from Eq. (7). Therefore, u directly determines binary variables \(v_{i,t}\), \(\phi _{i j,t}\), and \(\psi _{k,t}\).
2) Based on the confirmed \(\psi _{k,t}\) in 1) and the fixed \(\mu _{i,t}\) in (33), we can further derive the load shedding status \(\tau _{i,t}^{1}\), and \(\tau _{i,t}^{2}\) according to (11). Thus \(\tau _{i,t}^{1}\), and \(\tau _{i,t}^{2}\) also depends on u.
According to the analysis in 1) and 2), we know that given the fixed \(y_{1}^{*}\), there exists a mapping \(f:\varvec{u} \rightarrow \varvec{y}_{21}\). Thus, the problem (38) is equivalent to problem (41), and further to problem (42) where the binary variables \(\varvec{y}_{21}\) in the inner fourth-layer “min” can be put in the inner second-layer “max”. Then, the problem (42) can be effectively solved with the enumeration of integer variables \(y_{1}\) by the customized nested column-and-constraint generation (NC&CG) algorithm33 with two nested loop frameworks in Algorithm 1. As a result, the problem (42) is decomposed into a master problem (MP) (44) and a subproblem (SP) (43). Nonlinear terms \({\varvec{u}}^{\textrm{T}} {\varvec{G}}^{\textrm{T}} \varvec{\zeta }^{l_2}\) in (46) can be linearized by the big-M method4.
Case study
In this section, simulation experiments are carried out on a MATLAB /YALMIP simulation platform using a laptop with an Intel i9-10855H CPU and 16 GB of RAM.
The modified IEEE 33-bus CPDS
The modified IEEE 33-bus CPDS is shown in Fig. 2. The topology of the communication network is the same as the distribution system. Buses of the distribution system and communication nodes correspond one-to-one. The voltage base is 12.66 kV, and the secure voltage range is set as 0.9-1.1 p.u. The active and reactive power capacities of the DGs are 0.4MW and 0.35Mvar. The critical power users are located on buses 10, 19, 24, 26, 29, and 32, respectively. The penalty cost of non-critical load shedding is set to $5000/MW, while the cost of critical load shedding is 100 times as much as that. The cost of line hardening is $240,000/km. The total budget is $300,000. The maximum number of hardened lines is 3. \(a ^{\text {BSS}}\) and \(a ^{\text {SOP}}\) are set as 0.1. In addition, the parameters of BSS and SOP are listed in Table 2. Other parameters can be found in reference34.
Impact of typhoon attacks on the CPDS
To evaluate the impact of typhoons on the CPDS, we use the Monte Carlo method to simulate 400 typhoon attack events based on Batts model30, where the top 5 events are shown in Table 3. Then, we solve the resilience-oriented two-stage RO model with the scenarios of the top 5 typhoon events, respectively. The simulation results are listed in Tables 4 and 5. As illustrated in Table 4, there are some worst-case contingencies in common in the case of the top 5 events, such as the collapse of lines 21-22, 6-7, 7-8, 32-33 and 14-15, which is conducive to evaluating the weak cyber-physical coupling parts of the CPDS during typhoons. The corresponding load shedding cost is given in Table 5. Compared to Zones 1 and 2, Zone 3 is vulnerable to typhoons and thus has the largest load-shedding cost.
Defense strategies under various attacks
To demonstrate the advantage of the proposed planning-operation strategy against typhoons, the following three cases are utilized to be investigated under \(k_{\gamma }=3\).
Case 1: In the resilience-oriented two-stage RO model, the SOP is not considered to be deployed in the CPDS.
Case 2: In the resilience-oriented two-stage RO model, the BSS is not considered to be deployed in the CPDS.
Case 3: In the resilience-oriented two-stage RO model, the proposed defense strategies are considered therein.
It can be seen from Fig. 3 that four BSSs are deployed on buses 10, 19, 24, and 32, respectively, in Case 1. Meanwhile, Case 2 in Fig. 3 deploys SOPs on buses 8, 14, 22, 24, 27, and 32 to transmit power flow. However, Case 3 deploys the same number of SOPs as Case 2 but less 2 BSSs than Case 1. Notably, the number of wireless configuration buses is 8, 7, and 9 for Cases 1, 2, and 3, respectively, indicating that the backup communication plays a critical role in sustaining the power supply during disasters. Besides, the same reinforcement strategies can be found in Cases 1, 2, and 3 of Fig. 3, where overhead lines 26-27, 27-28, and 28-29 are hardened. Furthermore, compared to Case 1 in Fig. 3, Case 2 cannot ensure the critical load power supply on buses 10 and 19, which means that BSS deployment provides better resilience than SOP allocation. It is validated in Table 6 that Case 2 has the largest load-shedding cost among all cases. Based on Case 1, Case 3 further reduces load-shedding cost with additional SOP deployment. Therefore, the proposed planning-operation strategy has the best resilience to resist typhoon attacks. Moreover, in Table 6, the solution time of Case 3 is just tens of seconds longer than that of the other cases, which further demonstrates the feasibility of the proposed strategy. Furthermore, it can be seen in Fig. 4 that Case 3 enables more communication connections than Cases 1 and 2. As a result, fewer local controllers are activated in Case 3 than in Cases 1 and 2 for the load power supply. Based on the above results, the proposed planning-operation strategy is capable of mitigating cyber-physical coupling failures.
Sensitivity analysis
To explore the impacts of investment budgets and typhoon attacks on the resilient CPDS, a sensitivity analysis for the resilience-oriented RO model in Case 3 is further performed. It can be seen in Fig. 5 that load-shedding cost changes with differences in typhoon attacks and investment budgets. To be specific, when budgets are inadequate, load-shedding costs rise significantly with the increasing number of attacks. The reason is that critical loads cannot be supplied during typhoons. Furthermore, as investment costs increase from $200K to $300K, load-shedding costs go through rapid reduction due to the timely supply of critical loads by BSSs and SOPs. Nevertheless, there has not been any change in load-shedding costs, although budgets have increased to $400K. Thus, system planners should allocate investment budgets reasonably according to the degree of typhoon attacks to balance economic benefits. In addition, the solution time of the proposed model under various typhoon attacks is given in Table 7. The increase in typhoon attacks can impose the additional burden of solving the model, however, which is in a reasonably acceptable range. As seen in Table 7, this is because more iterations are needed to obtain worse-case scenarios of typhoon attacks.
The validation of the modified IEEE 123-bus CPDS
The modified IEEE 123-bus CPDS is utilized to further validate the effectiveness of the proposed model and method. For the convenience of representation, we just give the distribution system as shown in Fig. 6. It should be noted that power buses and communication nodes correspond one-to-one, and thus the topology of the communication network is the same as the distribution system. The control center is located on bus 150. The total budget is $600,000. The maximum number of hardened lines is 6. Other parameters can be found in Part A of this section.
Taking \(k_{\gamma }\)=4 as an example in Fig. 7, there are 4 BSSs deployed in buses 38, 65, 70, and 103, as well as 3 SOPs deployed on buses 4, 16, 18, 57, 151, and 300. Besides, wireless communication is configured to ensure communication for DGs, BSSs, and SOPs with the control center during typhoons. The overhead lines 18-19, 64-65, 65-66, 102-103, 103-104, and 108-109 are hardened against typhoon attacks. Furthermore, it can be seen in Table 8 that with the increasing number of typhoon attacks, the load shedding cost and solution time first significantly grow and then steadily rise.
Conclusion
To improve CPDS resilience, this paper proposes a resilience-oriented two-stage RO model for planning-operational restoration measures, which can be effectively solved by the customized NC&CG method. Numerical studies in Section V illustrate the advantage of the proposed model and approach. The conclusions are summarized as
1) According to Monte Carlo simulation of the sequential typhoon attacks, the vulnerable cyber-physical coupling parts of the CPDS can be identified in advance of the typhoon, which is conducive to making an effective resilience-oriented defense strategy for the CPDS against the upcoming typhoon.
2) Three cases are compared to validate the advantage of the proposed planning-operation measures. The proposed measures can not only ensure the load power supply but also reduce the risk of communication interruption, exhibiting better resilience for cyber-physical coupling failures.
3) A sensitivity analysis enables the system planner to readily achieve a tradeoff between strategy robustness and economic benefits. Moreover, the solution time of the proposed model is reasonably acceptable, although the uncertainty of typhoon attacks increases, demonstrating the good practicality of the model.
Data availability
The data of BSS, SOP, and the IEEE-33 bus and IEEE-123 bus test systems generated or analyzed during this study are included in this paper. The other data that support the plots within this paper and other findings of this study are available from the corresponding authors upon reasonable request.
Abbreviations
- \(\text {BSS}\) :
-
battery storage systems
- \(\text {CPDS}\) :
-
Cyber-physical distribution system
- \(\text {DG}\) :
-
Distributed generator
- \(\text {FTU}\) :
-
feeder terminal unit
- \(\text {NC[NONSPACE] \& CG}\) :
-
Nested column-and-constraint generation
- \(\text {OPGW}\) :
-
Optical fiber composite overhead ground wire
- \(\text {RO}\) :
-
Robust optimization
- \(\text {SOP}\) :
-
Soft open point
- \(\text {SP}\) :
-
Stochastic programming
- \(\varvec{\mathcal { X }}\) :
-
Planning set including \(\varvec{x}_{1}\), \(\varvec{x}_{2}\), \(\varvec{x}_{3}\) and \(\varvec{x}_{4}\)
- \(\varvec{\Theta }\) :
-
Spatially and temporally extended N-k uncertainty set of line status
- \(\varvec{U}_{l}\) :
-
Uncertainty set of line status
- \(\mathcal {Y}\) :
-
Emergency operation set including \(\varvec{y}_{1}\), \(\varvec{y}_{2}\)
- \(\Omega ^{\textrm{BR}}\) :
-
Set of overhead lines
- \(\Omega ^{\textrm{BSS}}\) :
-
Set of BSS
- \(\Omega ^{\textrm{DG}}\) :
-
Set of DG
- \(\Omega ^{\textrm{DN}}\) :
-
Set of power buses
- \(\Omega ^{\textrm{SOP}}\) :
-
Set of SOP
- \(\Omega ^{\textrm{TN}}\) :
-
Set of buses connecting to the transmission network
- \(\Omega _{N,t}\) :
-
Set of overhead lines that are not prone to attacks
- \(\Omega _{V,t}\) :
-
Set of lines that are prone to attacks
- \(\Omega _{\zeta }\) :
-
Zone \(\zeta\) of distribution systems
- b, g, s :
-
Indices of BSS, DG, and SOP
- e :
-
Indices of buses connecting to the transmission network
- i, j, k :
-
Indices of power buses and cyber nodes
- ij :
-
Indices of power lines and cyber links
- t :
-
Indices of time
- \(\mathcal {L}_{C}\) :
-
Set of cyber links
- \(\mathcal {N}_{C,\text {con}}\) :
-
Set of control center
- \(\mathcal {N}_{C}\) :
-
Set of cyber nodes
- \(\Gamma _{k}\) :
-
Information flow traffic of cyber node k
- \(\lambda _{\textrm{ch}}^{\textrm{BSS}}\),\(\lambda _{\textrm{dis}}^{\textrm{BSS}}\) :
-
Charging and discharging efficiency of BSS
- \(\operatorname {Pr}(i j, t)\) :
-
Probability of line ij
- \(\operatorname {Pr}_{V,th}\) :
-
Probability of line ij
- \(\sigma ^{\textrm{BSS}}\) :
-
Maximum discharging depth of BSS
- \(\underline{Q}_{g}^{\textrm{DG}}\) :
-
Lower reactive power limit of DG
- \(\xi _{i j}\) :
-
Length of line
- \(a^{\textrm{BSS}}\), \(a^{\textrm{SOP}}\) :
-
Capital recovery factors of BSS and SOP
- \(c_{H}\) :
-
Reinforcement cost of per kilometer of line
- \(c_{i}\) :
-
Weight coefficient of loads
- \(k_{\gamma }\) :
-
Number of vulnerable lines in zone \(\Omega _{\gamma }\)
- \(k_{\textrm{S}}\), \(k_{\textrm{E}}\), \(k_{\textrm{M}}\) :
-
Unit costs of the power/energy/operation and maintenance of the BSS
- \(N_{\xi \text{,max } }\) :
-
Total number of overhead lines in zone \(\Omega _{\zeta }\)
- \(P_{i j \max }\) :
-
Maximum active power on line ij
- \(P_{i,t}^{\textrm{L}}\) :
-
Load active power
- \(Q_{i j \max }\) :
-
Maximum reactive power on line ij
- \(r_{\textrm{S}}\), \(r_{\textrm{M}}\) :
-
Unit costs of the power/operation and maintenance of SOP
- \(r_{i j}\), \(x_{i j}\) :
-
Resistance and reactance of line ij
- \(\bar{P}_{g}^{\textrm{DG}},\bar{Q}_{g}^{\textrm{DG}}\) :
-
Upper active and reactive power limit of DG
- \(\alpha _{b}\) :
-
1 if BSS b is deployed, otherwise 0.
- \(\alpha _{s}\) :
-
1 if SOP s is deployed, otherwise 0.
- \(\beta _{b, t, \text {ch}}^{\textrm{BSS}}\) :
-
1 if BSS is charging power, otherwise 0.
- \(\beta _{b,t,\text {dis}}^{\textrm{BSS}}\) :
-
1 if BSS is dcharging power, otherwise 0.
- \(\omega _{i}\) :
-
1 if wireless communication on the cyber node i is configured b, otherwise 0.
- \(\theta _{i j,t}\) :
-
1 if the status of line ij is normal, otherwise 0.
- \(h_{i j}\) :
-
1 if line ij is hardened, otherwise 0.
- \(u_{ij,t}\) :
-
1 if line ij is attacked, otherwise 0.
- \(\mu _{k}\) :
-
1 if local controller on bus k is activated, otherwise 0.
- \(\omega _{k}\) :
-
1 if the cyber node k is connected with the control center by wireless communication, otherwise 0.
- \(\psi _{k}\) :
-
1 if the cyber node k has communication with the control center, otherwise 0.
- \(v _{k}\) :
-
1 if the cyber node k can be controlled by wired communication, otherwise 0.
- \(C^{BSS}\) :
-
Cost of BSS deployment
- \(C^{SOP}\) :
-
Cost of SOP deployment
- \(C_{\textrm{on}}^{\textrm{BSS}}\), \(C_{\textrm{on}}^{\textrm{SOP}}\) :
-
Operation and maintenance expense of BSS and SOP
- \(C_{\text{ inv } }^{\textrm{BSS}}\), \(C_{\text{ inv } }^{\textrm{SOP}}\) :
-
Investment cost of BSS and SOP
- \(C_{H}\) :
-
Cost of hardened lines
- \(C_{W}\) :
-
Cost of wireless communication configuration
- \(E _{b.t}^{\textrm{BSS}}\) :
-
Energy level of BSS b
- \(E_{b}^{\textrm{BSS}}\) :
-
Energy capacity of BSS
- \(P _{b,t,\text {ch}}^{\textrm{BSS}}\) :
-
Charging power of BSS
- \(P _{b,t,\text {dis}}^{\textrm{BSS}}\) :
-
Discharging power of BSS
- \(P_{b}^{\textrm{BSS}}\) :
-
Power capacity of BSS
- \(P_{e, t}^{\textrm{TN}}\), \(Q_{e, t}^{\textrm{TN}}\) :
-
Active and reactive power from the transmission network
- \(P_{i j, t}\), \(Q_{i j, t}\) :
-
Active and reactive power flow on line ij
- \(P_{i, t}\), \(Q_{i, t}\) :
-
Total active and reactive power injection for bus i
- \(P_{i,t}^{\textrm{LS}}\) :
-
Active power shedding
- \(P_{s.t}^{\textrm{SOP}}\) :
-
Active power of SOP
- \(Q_{s.t}^{\textrm{SOP}}\) :
-
Reactive power of SOP
- \(S_{s}^{\textrm{SOP}}\) :
-
Power capacity of SOP
- \(U_{i , t}\) :
-
Voltage on bus i
- \({P}_{g,t}^{\textrm{DG}}\) :
-
Active power output of DG
- \({Q}_{g,t}^{\textrm{DG}}\) :
-
Reactive power output of DG
References
Wang, Y., Chen, C.-F., Kong, P.-Y., Li, H. & Wen, Q. A cyber-physical-social perspective on future smart distribution systems. Proceedings of the IEEE 111, 694–724 (2022).
Xu, L., Guo, Q., Sheng, Y., Muyeen, S. & Sun, H. On the resilience of modern power systems: A comprehensive review from the cyber-physical perspective. Renew. Sustain. Energy Rev. 152, 111642 (2021).
Liu, Z. & Wang, L. A distributionally robust scheme for critical component identification to bolster cyber-physical resilience of power systems. IEEE Trans. Smart Grid. 13, 2344–2356 (2022).
Huang, Z., Zhang, Y. & Xie, S. A comprehensive strategy for the distribution network resilience enhancement considering the time-varying behaviors of typhoon path. Electric Power Systems Research 214, 108819 (2023).
Dehghani, N. L. & Shafieezadeh, A. Multi-stage resilience management of smart power distribution systems: A stochastic robust optimization model. IEEE Trans. Smart Grid. 13, 3452–3467 (2022).
Huang, W. et al. Resilience oriented planning of urban multi-energy systems with generalized energy storage sources. IEEE Trans. Power Syst. 37, 2906–2918 (2021).
Yang, X. et al. Resilience-oriented co-deployment of remote-controlled switches and soft open points in distribution networks. IEEE Trans. Power Syst. 38, 1350–1365 (2022).
Zhao, Y., Lin, J., Song, Y. & Xu, Y. A robust microgrid formation strategy for resilience enhancement of hydrogen penetrated active distribution networks. IEEE Trans. Power Syst. 39, 2735–2748 (2023).
Cai, S. et al. Frequency constrained proactive scheduling for secure microgrid formation in wind power penetrated distribution systems. IEEE Trans. Smart Grid. (2025).
Ti, B., Zhang, C., Liu, J., Wu, Z. & Huang, Z. Cyber-physical collaborative restoration strategy for power transmission system considering maintenance scheduling. CSEE Journal of Power and Energy Systems 10, 1331–1341 (2023).
Ti, B., Li, G., Zhou, M. & Wang, J. Resilience assessment and improvement for cyber-physical power systems under typhoon disasters. IEEE Trans. Smart Grid. 13, 783–794 (2021).
Gao, H. et al. Integrated planning of cyber-physical active distribution system considering multidimensional uncertainties. IEEE Trans. Smart Grid. 13, 3145–3159 (2022).
Photovoltaics, D. G. & Storage, E. Ieee standard for interconnection and interoperability of distributed energy resources with associated electric power systems interfaces. IEEE Std. 1547, 2018 (2018).
Li, X. et al. Distributionally robust coordinated defense strategy for time-sensitive networking enabled cyber-physical power system. IEEE Trans. Smart Grid. 15, 3278–3287 (2024).
Jing, X., Qin, W., Yao, H., Han, X. & Wang, P. Resilience-oriented planning strategy for the cyber-physical adn under malicious attacks. Applied Energy 353, 122052 (2024).
Kong, P.-Y. Routing in communication networks with interdependent power grid. IEEE ACM Trans. Netw. 28, 1899–1911 (2020).
Tian, M., Dong, Z., Gong, L. & Wang, X. Coordinated repair crew dispatch problem for cyber-physical distribution system. IEEE Trans. Smart Grid. 14, 2288–2300 (2022).
Xu, L., Guo, Q., Yang, T. & Sun, H. Robust routing optimization for smart grids considering cyber-physical interdependence. IEEE Trans. Smart Grid. 10, 5620–5629 (2018).
Yang, T., Cai, S., Yan, P., Li, W. & Zomaya, A. Y. Saturation defense method of a power cyber-physical system based on active cut set. IEEE Trans. Smart Grid. doi: https://doi.org/10.1109/TSG.2022.3154839 (2022).
Huang, Z. et al. Enhancing the self-healing capability of cyber-physical distribution systems: A uav-5g hybrid wired/wireless communication method. IEEE Trans. Smart Grid. https://doi.org/10.1109/TSG.2025.3527818 (2025).
Liu, Z., Wu, Q., Shen, X., Tan, J. & Zhang, X. Post-disaster robust restoration scheme for distribution network considering rerouting process of cyber system with 5g. IEEE Trans. Smart Grid. 15 (5), 478-4491 (2024).
Ye, Z. et al. Boost distribution system restoration with emergency communication vehicles considering cyber-physical interdependence. IEEE Trans. Smart Grid. 14, 1262–1275 (2022).
Wang, C., Yan, M., Pang, K., Wen, F. & Teng, F. Cyber-physical interdependent restoration scheduling for active distribution network via ad hoc wireless communication. IEEE Trans. Smart Grid. 14, 3413–3426 (2023).
Younesi, A., Shayeghi, H., Safari, A. & Siano, P. Assessing the resilience of multi microgrid based widespread power systems against natural disasters using monte carlo simulation. Energy 207, 118220 (2020).
Wang, C. et al. Chance-constrained primary frequency reserve optimization considering stochastic disturbances and contingencies. IEEE Trans. Power Syst. https://doi.org/10.1109/TPWRS.2024.3510780 (2024).
Cai, S. et al. Distributionally robust microgrid formation approach for service restoration under random contingency. IEEE Trans. Smart Grid. 12, 4926–4937 (2021).
Cai, S. et al. Hybrid stochastic-robust service restoration for wind power penetrated distribution systems considering subsequent random contingencies. IEEE Trans. Smart Grid. 13, 2859–2872 (2022).
Shi, W., Liang, H. & Bittner, M. Stochastic sequential restoration for resilient cyber-physical power distribution systems. IEEE Transactions on Industrial Informatics 21 (2), 1200-1209 https://doi.org/10.1109/TII.2024.3475420 (2024).
He, Z., Li, Z., Xiao, X., Wang, C. & Ju, P. Dynamic resilience region-based proactive scheduling for enhancing the power system resilience. IEEE Trans. Power Syst. 40 (3), 2336-2348 https://doi.org/10.1109/TPWRS.2024.3468643 (2024).
Hu, B. et al. Hardening planning of overhead distribution lines in typhoon-prone areas by considering the typhoon motion paths and the line load reliability. International Journal of Electrical Power & Energy Systems 129, 106836 (2021).
Zhang, H., Ma, S., Ding, T., Lin, Y. & Shahidehpour, M. Multi-stage multi-zone defender-attacker-defender model for optimal resilience strategy with distribution line hardening and energy storage system deployment. IEEE Trans. Smart Grid. 12, 1194–1205 (2020).
Xiong, H. et al. Resilience enhancement for distribution system with multiple non-anticipative uncertainties based on multi-stage dynamic programming. IEEE Trans. Smart Grid. 15, 5706–5720 (2024).
Zhao, L. & Zeng, B. An exact algorithm for two-stage robust optimization with mixed integer recourse problems (2012).
Ghasemi, S. & Moshtagh, J. Radial distribution systems reconfiguration considering power losses cost and damage cost due to power supply interruption of consumers. IInt. J. Electr. Eng. Informatics 5, 297–315 (2013).
Acknowledgements
This work was supported by the Science and Technology Project of China Southern Power Grid Company Ltd. under Grant 031900KC23120066.
Author information
Authors and Affiliations
Contributions
S.L., Z.H., J.L., and J.Z. conceptualized the study. S.L. and Z.H. provided the methodology and carried out the experiments and visualizations. The original draft was written by S.L. and Z.H., with review and editing by J.L., J.Z., D.C., Y.L., Y.N., and W.C. Funding acquisition was by S.L., J.L., L.L., X.L., L.Y., and K.W.L.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Li, S., Huang, Z., Luo, J. et al. A robust resilient-oriented design for the cyber-physical distribution system against sequential typhoons. Sci Rep 15, 21037 (2025). https://doi.org/10.1038/s41598-025-05593-x
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-05593-x