Abstract
Internet of Vehicles consists of vehicular nodes that communicate with each other for making intelligent transportation systems, where cyber physical attacks are increasing continuously. Intrusion Detection System (IDS) is able to provide a better security solution for minimizing such cyber physical attacks. Many existing IDSs developed using classification algorithms fail to provide the expected intrusion detection accuracy and they exhibit higher false positive rates. Hence, an efficient Feature Selection Algorithm named Weightage and Ranking Based Feature Selection Algorithm and a Bagging based Fuzzy Convolutional Neural Network classification algorithm with Adam optimizer are proposed in this article which are used to identify the attacks more effectively using bagging with fuzzy inference in the deep convolutional neural network classifier. The proposed system was tested using benchmark and network trace datasets and proved that the proposed IDS enhances the detection accuracy and reduces the false positive rate.
Similar content being viewed by others
Introduction
The Internet of Vehicles (IoV) is a network of interconnected vehicles with sensors connected using Internet of Things (IoT) for performing vehicle to vehicle communication. Here, the sensors gather and transmit data without the need for human interaction across a wireless mobile ad-hoc network of vehicles with internet connection thorough IoT. Moreover, the IoT component of IoV has many real life applications including the monitoring and handling of smart wearables, smart health monitoring, traffic monitoring, the implementation of smart agriculture1. However, the network pertaining to the Internet of Vehicles has certain limitations including security challenges to be addressed for safeguarding the network communication from attackers.
Due to its resource constraints nature of sensor nodes used in IoV communication, the data collection and routing activities must be optimal. The network nodes and links of IoV are prone to attacks that come under both unknown and known types of attacks2. To overcome these security challenges in IoV, Intrusion Detection Systems (IDSs)3,4,5,6 are used to provide better security of communication. IDS is a software application that can monitor a networking system for the occurrence of any malicious activity. The major goals of IDS in IoV communication are to ensure secured communication by effective and in-depth monitoring of the network traffic7.
When an intrusion occurs in a IoV communication system for the first time, the IDS can be able to identify which vehicle’s devices have been compromised and can avoid the propagation of the malicious attacks to the other components of the network8. A typical IDS make use of two major intrusion detection methods namely signature and anomaly-based attack patterns9. Techniques used for classifying and detecting of the malicious and normal traffic are considered as a major challenge in the design of any IDS10. Moreover, the dataset used for developing an IDS consist of many features leading to increase in detection time and reduction in classification accuracy due to the presence of complementary information. It can be solved by employing only the best Feature Selection Algorithms (FSAs) and also classification algorithms. Here, IDS is mainly deployed for detecting the irregular behaviour by checking the access rights versus attempts to access the data for protecting the sensitive information from attacks11.
Based on literature, FSAs are classified into filter, wrapper-based and embedded FSAs12. The filter-based method uses a generic approach which do not depend on any specific ML13. Moreover, filter method is little inclined in over fitting. Filter method is mainly used for ordering the features which has inherited properties of the data. The advantages are wrapper method has better performance when compared to other FSAs14. One limitation of this FSA is that it is highly vulnerable to over fitting of data from the dataset by the learning model. The embedded method establishes one link between predictor function and feature search strategy. The algorithm used in embedded method has an inbuilt Feature Selection (FS) method. The limitations are this method is that it is slightly prone to over fitting during the training of data. The embedded method is suitable for predicting from huge amount of data sets but it is over dependent on the classifier model. Moreover in this model, it is difficult to identify the minute features15. In the development of an IDS for complex systems, a hybrid feature selection method is more convenient and powerfully built and extract the features for high dimensional data.
In the IDS process after feature selection, the dataset is classified based on the features using the classification algorithm. Many Classification Algorithms (CAs) namely Support Vector Machines (SVMs), Naïve Bayes (NB), Decision Tree (DT) and Random Forest (RF) are found in the literature as they are employed in most of the existing IDSs for efficient classification of data. Among Machine Learning (ML) based CAs, the DT algorithm is mostly used since it handles both numerical and categorical data16. In DT classifier, the classified data are represented in tree format where the nodes, branches and leaves represent features, decision rules and output. The decision nodes can take multiple decisions and it can create multiple branches, but the leaf nodes cannot create any further branches17. This algorithm replicates the human thinking in decision making process where the irrelevant features are removed using pruning process. Bagging algorithm is also named as bootstrap aggregation which combines multiple methods for performance enhancement. Mostly, Bagging is used in decision tree method18 but the concept can be extended to use in other classification algorithms as well. In this work, bagging is used because Bagging is one homogeneous learning model for the nodes of the vehicular network in which the each of the nodes learn from other nodes independently but in a parallel manner and finally the results are combined by the classifier to determine the model’s average performance. On the other hand, boosting is another homogeneous learning model that learns sequentially and adaptively from the data in order to improve the learning model’s prediction capability more effectively. Bagging is reducing the variance by considering the values obtained from all the nodes of the network based on the average computation and also by minimizing the deviations. This avoids overfitting which is not possible with boosting.
In this article, one new intelligent IDS is proposed for securing of communication in IoV networking system. For achieving this, one new FSA called Weightage and Ranking Based FSA (WRBFSA) is proposed in this work for selecting only the useful and contributing features. Additionally, one new Classification Algorithm called Bagging based Fuzzy Convolutional Neural Network (BFCNN) classification algorithm with Adam optimizer19 is also proposed here which is developed based on Convolutional Neural Network (CNN) with bagging and fuzzy inference modelling. The Fuzzy CNN consists of a fuzzy inference system which is integrated with the Convolutional Neural network consisting of input layer, convolution layer, pooling layer and fully connected network. The fuzzy inference system used in this work applies the triangular membership function for fuzzification and the Centre of Area method is used for Defuzzification. The linguistic variables Lower, Medium and Higher are used in this work to represent the number of logins failed, wrong fragments and the number of compromised conditions. The fuzzy rules formed are used to make decisions on Intrusion detection after the fully connected network provides a classification using the activation function. The final result of this proposed IDS is validated using ten-fold cross validation method and proved that it increased the Detection Accuracy (DA) and reduced the False Positive Rate (FPR). Bagging is used in this work since bagging is one homogeneous learning model for the nodes of the vehicular network in which the each of the nodes learn from other nodes independently but in a parallel manner and finally the results are combined by the classifier to determine the model’s average performance. On the other hand, boosting: is another homogeneous learning model that learns sequentially and adaptively from the data in order to improve the learning model’s prediction capability more effectively. Bagging is reducing the variance by considering the values obtained from all the nodes of the network based on the average computation and also by minimizing the deviations. This avoids overfitting which is not possible with boosting.
This proposed intelligent IDS is made by selecting optimal features by applying the proposed WRBFSA for effective feature selection by identifying the dominating attributes and also by using the recursive features selection approach by means of information gain ratio in the recursive feature selection algorithm with feature ranking20. Moreover, the proposed intelligent IDS employs bagging-based fuzzy CNN classifier for efficient categorization of attacks. This system was tested initially using the NSL-KDD as well as IoT-23 datasets21,22,23,24 and then it was also tested using the IoV trace data set made from the incoming network traffic of IoV network. The proposed intelligent IDS is able to detect both familiar and novel types of attacks in an effective manner by applying the efficient FSA namely WRBFSA along with the proposed intelligent classification algorithm called BFCNN with Adam optimizer. Moreover, 10-fold cross validation method is used in this work for validation. Therefore, each CNN is trained with 9 folds of each set of data and are tested with one-fold from each set of data. It is not random but, the data are selected sequentially.
The fuzzy logic performs deductive inference by applying the fuzzy rules using forward chaining inference method. In Vehicular Ad-hoc networks, the data are classified as genuine or attack using the fuzzy rules. If the attacks are not detected, the decisions made by the navigation and guidance system in vehicular networks will not be accurate and hence may degrade the performance. Hence, fuzzy logic improves IDS performance in vehicular networks.
The major contributions of this research work are given below:
-
1.
An efficient FSA called WRBFSA is proposed for extracting the dominating feature set by identifying the features recursively from the given dataset by means of information gain ratio values and the ranks.
-
2.
An intelligent Bagging based Fuzzy Convolutional Neural Network (BFCNN) classifier with Adam optimizer is proposed for increasing the intrusion detection accuracy and for minimizing the false positives.
-
3.
This proposed intelligent classifier applies intelligent fuzzy decision rules along with bagging process for supporting the convergence process of Convolutional Neural Network (CNN) classifier with Adam optimizer.
-
4.
The system has been tested using three datasets namely and is also validated using the tenfold Cross Validation (CV) method.
Literature survey
Numerous techniques for communication security using IDS were proposed in the past25,26,27,28,29,30,31,32,33,34,35,36,37,38. Amidst them, Deris Stiawan et al.39 introduced one enhanced ensemble IDS method to identify the appropriate features which are utilized as an essential feature in IDS. Their proposed system uses six different types of feature selection approaches. From the features selected, the best suitable features are acquired by employing the prioritizing attributes for selecting features.
Related work
Injadat M et al.40 proposed one IDS technique which is based on Machine Learning. Their proposed system aimed at minimizing the estimation error while managing its detection concert. They used oversampling approach to make accurate training using the dataset size. Their proposed system utilizes both the information gain and correlation-based approaches for feature selection. Kasongo S M41 proposed an IDS for securing industrial IoT. Their proposed system utilized both the Genetic Algorithm (GA) and Tree based algorithm for providing security, confidentiality and cohesion. Initially, an FSA using Random Forest (RF) was employed. As a result, it selected best features by utilizing Machine Learning (ML) classifiers for classification. Gaikwad D P et al.42 introduced one IDS with partial DT and bagging method to obtain the enhanced classification having higher precision and very low training time for the given dataset. In their proposed system, partial tree method plays a role of base classifier. It utilizes the bagging technique to execute the classification in IDS. Gao X et al.43 proposed one ensemble technique based on ML. This system employed various tree-based techniques which are integrated with group voting method. The group voting method is utilized to enhance overall DA rate. The advantage of their model is increase in overall DA and reduction in FPR. Here, the DA of RF was not shown to be better than the DT. Zhou Y et al.44 proposed one analytical oriented Correlation FSA with Bat optimizer for constructing of an effective IDS. Their proposed system helps to remove the redundant and noise data, and it utilizes more than one classifier in detection.
He H et al.45 suggested a multimodal classification technique with unique grouping network based IDS. This system was proposed by the authors to avail the full-fledged information that are available in network. It was developed by integrating Multimodal Deep Auto Encode (MDAE) and Long Short-Term Memory (LSTM) techniques to improve accuracy and also to avail network details. The advantage of it is that the usage of intelligent technique helps to improve DA. However, the system must be tested with real time data. Sabeel U et al.46 proposed a protective Artificial Intelligence (AI) based mechanism for designing an IDS which is incorporated with dual attribute extraction method with AI model. The authors proposed system in order to prevent various modern types of attacks. Moreover, their proposed system withstands against various types of malicious attacks during the data communication. The limitation of this model is that it considered only Denial of Service (DoS) attacks. Al-Abassi A et al.47 introduced one group Deep Leaning (DL) based attack detection method for Industrial Control System (ICS). Their proposed system was introduced for security enhancement and to protect the outcome of datasets without getting affected. This system employed group deep learning technique in order to build stability between the datasets.
Kim T et al.48 introduced one Hybrid classifier for making IDS. The hybrid classifier method used here is done by the integration of packet and session-based features to construct an IDS which results in usage of best classifier method. Papamartzivanos D et al.49 proposed one new Intrusion Detection (ID) algorithm namely dendron to identify different types of malicious attacks and to improve DA. In this proposed technique, the decision-based classification helps to identify the regulation precisely which detect the attacks better than other classification techniques. Kunal et al.50 proposed one FSA and ensemble classifier technique for IDS to impose strong security and to avoid the packet drop rate during various malicious attacks in the network. Their proposed technique employed different classification techniques for training the dataset which help to identify various malicious attacks.
Sharma N V et al.51 proposed one Recursive Feature Elimination (RFE) and ML classifiers to construct an effective IDS. Their system was developed to address various malicious attacks. Their RFE technique was used when there were unnecessary features in their dataset. Moreover, it eliminates excess or unwanted features from the dataset by evaluating it. Gupta N et al.52 proposed one DL-based grouping method for developing a network-oriented IDS. Their proposed system has two important levels. In the first level, the usage of deep learning technique helps to identify anonymous traffic. In the second level, the Gradient Boosting method is employed to identify attacks. Finally, the identified attacks from second level are tested with appropriate dataset for further process. This system must be deployed in the real world for testing.
Viegas E et al.53 proposed one effective anomaly based IDS for securing the embedded system and to address the issue of efficiency in the system. Their proposed system introduced two new feature extraction techniques with tables and hashes. The table-based method helps to protect the data that are transmitted between the two hosts in the network. The hash-based method was introduced to subdue the limitations of the table-based extraction technique. Herrera-Semenets V et al.54 proposed one IDS with a new FSA. In their proposed technique, the multiple feature selection with the help of parallel computation process. The advantage of the system is that it becomes more effective in terms of ID by reducing the size of the dataset and with best accuracy rate by selecting only best pair of features from the given dataset. Jenif Souza D W S et al.55 proposed an iterative feature rejection technique for IDS using machine learning to make the verification and authentication process more easier during the huge network congestion in the network. Teng S et al.56 proposed a versatile and collective IDS that employed DT algorithm with SVM to provide high level of security to the IoT network. It employed an adaptive mechanism which is more effective than support vector machine.
Halim Z et al.57 introduced one IDS using Genetic Algorithm (GA) based FSA to address issue related to datasets namely irrelevant and redundant data. Their proposed system utilized GA which helped to maximize the accuracy rate. Here, the accuracy rate is maximized and also provides good resistance against various types malicious attacks. However, it is necessary to test it with a real network. Kurniabudi et al.58 developed one effective FSA using information gain and anonymous feature detection technique to reduce the detection time. In their model, the execution time and computational time were reduced drastically when compared with the existing systems. However, the use of DL algorithm can improve the detection performance better.
Panda M et al.59 proposed various ML models for identifying various malicious-attacks in IoT network. Their proposed system employed a feature selection technique by integrating K-medoid and Scatter search methods to reduce FAR and to increase DA. However, their classification process needs further improvement for performance enhancement. Ustebay S et al.60 proposed an Iterative feature rejection-based IDS with ML for detecting the various cyberattacks in IoT networks. Their proposed system employed RF technique which helped to reduce the irrelevant features. The iterative feature rejection algorithm removed all the redundant and irrelevant features in iterative manner to give maximum accuracy rate for the intrusion detection system. Their proposed system utilized the Deep Multi-Layer Perceptron algorithm as a classification technique to provide the high accuracy during the intrusion detection. In this technique the dataset is classified into vulnerable and normal dataset. The advantage of the system is that it reduces the malicious attacks and protects the system against the attacks by using the ML and DL techniques during the intrusion detection. However, the use only DL can reduce the detection time.
Besharati E et al.61 introduced one Logistic Regression based IDS for cloud security to handle cyber-attacks. In the IDS, features were selected with the help of algorithmic regression and all the selected features were trained using regularization technique to detect attacks using bagging. The advantage of the system is that the strong security in cloud environment helps to prevent the system against cyber-attacks firmly. However, it must be tested with a real cloud network. Tama B A et al.62 proposed one new two-step group classifier for building the effective IDS in IoT environment. The proposed system employed two stages of group classification technique which results in hybrid classification. Pu G et al.63 proposed one hybrid based anonymous FSA to reduce the number of malicious attacks using One Class SVM to identify the information about the attacks in advance with helps to make the system more efficient during the intrusion detection.
Binbusayyis A et al.64 suggested one group classification-oriented IDS for providing strong security against many cyber-attacks and to filter out the unnecessary data in the network. Their proposed system employed various group classifiers for choosing the correct features from the dataset by checking the following parameters namely correlation, consistency, information and distance. Nazir A et al.25 introduced one group optimization-based FSA for making a network IDS to withstand against cyber-attack and reduce of dimensionality in the IoT based network dataset. Their proposed system employs Tabu Search – RF technique which is used by one wrapper-based FSA. The Tabu Search–RF is an algorithmic technique which is used for local search in mathematical optimization. The RF is one ML method that is utilized to handle redundant and classification problem. Nimbalkar P et al.26 proposed an IDS using information gain ratio to identify the various cyber-attacks. Their system employed filter-based FSA for identifying only contributing features from the given dataset.
Artur M et al.65 proposed an iterative feature rejection technique and a cross validation technique for securing IoT network. Their model employed a hybrid classification technique which integrates iterative feature rejection and cross validation techniques. It utilized naïve Bayes classifier to classify the datasets based on binary and multiclass classification. Kasongo S M et al.66 proposed one DL model combined with various FSAs to maintain effectiveness of intrusion detection. Their deep Neural Networks (NNs) helped to solve the complicated security problem which is motivated from organic classification methods. Rose et al.67 developed one hybrid anomaly IDS using k-means clustering and SVM classifier and achieved better DA than other known IDSs. However, their focus was to secure the Internet of Energy Environment part of IoT. Moreover, their system focused on the reduction of training and testing time as the main objective. Anand et al.68 proposed one IDS for securing IoV communication. Their work focused on the detection of DoS, fuzzy and spoofing attacks and was tested using car-hacking dataset. An IDS for vehicular network must focus on even novel attacks. This could be achieved by using better classifiers and data set. Mohammadi et al.27 developed one IDS with correlation coefficient analysis and cuttlefish optimizer for performing the FS effectively. Moreover, DT classifier was considered in their method. They achieved a detection rate of 95%. The accuracy can be improved further by using deep learning with an optimization technique.
Wisanwanichthan and Thammawichai28 proposed a new IDS that used Principal Components from the NSL_KDD dataset for FS and then applied a combination of Naive Bayes and SVM classifier in classification. The use of DL classifier with an optimizer can perform automatic FS and classification for achieving better DA. Ganapathy et al.29 presented one survey on IDSs that used ML algorithms for FS and classification. However, the use of DL algorithm with an optimizer can provide better DA with reduced FPR. Nancy et al.69 introduced an IDS by designing a dynamic FSA and also a fuzzy temporal DT classifier for enhancing the security in Wireless Sensor Networks (WSNs). However, for IoV having large number of vehicles, DL method can be more suitable for enhancing the detection accuracy than the use of ML methods.
Wang et al.70 proposed one representation learning-based NIDS that can capture explicit and implicit feature interactions for performing effective feature selection. Here, an unsupervised approach is used for FS based on learning and NN classifier. The DA achieved in their model could be enhanced by using DL classifiers. Biswas et al.71 proposed one multipath and Secured Routing Protocol (SRP) for providing secured communication in WSN. Their protocol incorporated only lightweight security methods namely one-way hashing chain, Message Authentication Code (MAC) and data encryption schemes to secure the network from malicious attacks. Santhosh Kumar et al.72 presented a survey of IDSs developed using ML methods. However, classification with DL methods can enhance DA in IDSs. Shalini and Selvi73 proposed one IDS using fuzzy CNN and mathematical modelling for securing the communication in WSN. The model can be improved by using an optimization algorithm that can reduce the complexity effectively.
Rajasoundaran et al.74 developed one optimized IDS with LSTM and MAC for securing underwater WSNs. Their model can be modified to suit the IoV environment by applying better operations in DL based classification. Yesodha et al.75 developed one IDS using enhanced CNN with an optimization algorithm for enhancing the security in WSN. However, one modern optimizer usage can provide security enhancement in IoV. Balakrishnan Senthilnayaki et al.76 proposed an IDS utilizing fuzzy rough sets in FS and one modified ML classifier for classification. However, the use of DL can classify the data set more accurately for detecting all types of attacks. Raghavendra et al.77 proposed one SRP using ML based IDS for securing IoT networks. However, DL and optimizer combination could enhance the security further.
Ganapathy et al.78 introduced one Fuzzy Clustering model with Immune GA for developing an IDS. However, classification-based systems provide better performance than cluster-based methods in the development of IDSs. Senthilnayaki et al.79 proposed one IDS developed using genetic FS method and SVM based classifier for final detection. However, a DL can perform both the tasks more effectively. Hizal et al.80 proposed a new IDS using DL for detecting the Distributed DoS attacks occurring in IoT. However, both known and novel attacks must be detected and prevented for enhancing the security in IoT. Heidari et al.81 presented one survey on IDSs which focused on IoT networking. However, their detection rate could be improved by using an effective optimization algorithm with DL so that it can reduce the error rate significantly. Maheswaran et al.82 developed a Hybrid IDS Using ML approach. The authors used Random Forest classifier and Gaussian mixture modelling based clustering for FS and ID. However, the use of IoV dataset needs to classify huge data which can be performed more effectively by applying optimization algorithm with a DL classifier. Table 1 shows the overview of the related work.
Research gaps
From the literature survey, the following research gaps are identified. From this literature survey, it is observed that many existing IDSs fail to provide required detection accuracy due to the limitations of the existing feature selection and classification algorithms used in those works for a given network traffic. Further, they are not able to provide necessary intrusion DA due to over fitting during classification. Moreover, the existing IDSs provide significant overhead during the intrusion detection process. Motivated from all these observations, an intelligent hybrid-based IDS is proposed in this work which employs information gain ratio and wrapper based recursive FSA called WRBFSA for feature selection process in the hybrid FSA and BFCNN with Adam optimizer for effective classification in intrusion detection process. Comparing with other CNN based IDSs, the proposed IDS is different in the following ways.
(i). A hybrid Feature Selection algorithm is proposed in this work that selects only the optimal number of features where the features are contributing the accurate decision making by the classifier.
(ii) Bagging based CNN is used in this work where the best performing CNNs support in increasing the detection accuracy.
(iii). Adam optimizer is used with CNN for enhancing the classification accuracy and to reduce the classification time.
(iv). Fuzzy inference method is used in the classification to make decisions with incomplete information.
Proposed system architecture
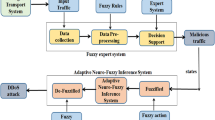
Figure 1 shows the architecture for this proposed system. It consists of 9 major components named Data collection module, Data Preparation (Pre-Processing) module, normalizing-module, Weighted and Ranking based Feature selection module, Bagging based Fuzzy CNN with Adam Optimizer classification module, Decision manager, Knowledge base, Admin Module for Intrusion Prevention and datasets. The data from NSL–KDD dataset or IoT-23 Dataset83 or IoV Network Trace data are read by the data collection module and it is given as input to the data preparation module for data cleaning. These cleaned data are given to normalization module for data integration. It performs data conversion with necessary formatting and then integrates the data which aids the feature selection process. Moreover, this module eliminates non number values for eliminating noise and also fills the missing values with averaged values during this normalization process. The main features of the normalization are to reduce the redundancy in the dataset and also scaling the data in the given dataset. The main advantage of these modules is that they validate the dataset and ensure that the correct data is only given to FSA and classifier for performing accurate ID by efficient identification and detection of malicious activities. In feature selection module, the pre-processed data is given as input for efficient feature selection. Moreover, this proposed system employs the effective technique namely weighted and ranking based feature selection method developed here. Moreover, Information gain method is employed for FS to reduce the entropy from the given data. Once the entropies are removed from the given data, the weightage for each feature are computed and finally the set or dominating features from the given dataset is produced as output from filter-based Information gain ratio. In addition, recursive feature dissemination technique has been employed by the proposed system. Based on this recursive feature selection method, the features are ranked and the features with high ranks are selected. Finally, the proposed system employs vote polling method which combines features of FS approaches to identity the most relevant features from the given dataset for an efficient detection of intrusion in IoV. In intelligent classification module, bagging based fuzzy CNN with Adam optimizer is employed for classification. The classifier generates intelligent fuzzy rules to be used by fuzzy inference method for making decisions. The bagging based fuzzy CNN with Adam optimizer classifies the dataset and detect the intrusions and then forwards them to the admin through the decision manager for prevention. The bagging technique is used here to reduce over fitting from the given data set. Finally, the bagging- based fuzzy CNN with Adam optimizer is tested and trained by using generated relevant features in order to evaluate the accuracy of the proposed intelligent IDS.
The decision manager is the overall controlling module and is connected to all the modules. The Knowledge Base (KB) stores the attack signatures in the form of rules. Based on the rules stored in KB and the classifier generated rules, the known attacks and unknown attacks are identified by the decision manager in the proposed IDS.
Intelligent classifier
The intelligent IDS design contains five important phases namely data preparation phase, normalisation phase, intelligent feature selection phase and intelligent bagging-based Fuzzy CNN classifier with Adam optimization phase84,85and decision-making phase.
Data preprocessing and normalization phases
In this proposed system, data are collected from NSL KDD dataset or IoT-23 dataset or IoV network trace data repositories and they are given to the data preparation phase86878388. The given data may consist of noise, non-numbers and missing values. The data pre-processing module converts all data uniformly into numerical values. In this module noises are removed, non-numbers and missing values are also replaced with zero or average values to ensure the accuracy of the data set67. After this process, a compact and accurate dataset is obtained from which the input is given to the FSA and classification algorithms for effective identification of normal and malicious data.
The proposed system focuses on 41 features from the NSL KDD dataset and similar features are extracted from other two datasets. From the given datasets, Normalization of the data is preformed to minimize the redundant data and achieve better input data. The proposed system employs Min-Max normalization for scale the data in the range from 0 to 1. The formula that computes the normalized values using Min-Max normalisation is given in Eq. (1).
V’ denotes normalized value; V is the feature value to be normalized. By normalizing, the accuracy of the dataset is improved, thereby it enhances the accuracy of the classifier.
Intelligent hybrid feature selection algorithm
A novel hybrid FSA is proposed here in this article by using filter and wrapper-based FS methods. In this proposed FSA for IDS, 41 features are shown in Table 2.
These features are considered in this work based on NSL_KDD CUP Dataset892122 which are selected from original datasets and are given as input to both filter as well as wrapper approaches for utilizing the advantages of both these methods. The pre-processed and normalised data set is given as input for the FS module. In this proposed system, the intelligent FS module is sub divided into filter and wrapper-oriented FS sub-modules. In the filter-oriented method, the information gain ratio is employed and wrapper-oriented sub module, the recursive feature elimination technique is employed. The features selected by the filter-method, wrapper method and the proposed hybrid method are namely 23, 20 and 17 features as given in Table 3, Table 4 and Table 5.
Finally, group vote polling technique is employed to select only the relevant features from the hybrid FSA.
Weightage and ranking based feature selection
In this work, filter-based FSA employs Information Gain (IG) to identify weightage attribute from the given dataset. It is one of the metrics that is used to train the dataset during feature selection process. Here, IG is utilized to determine the perfect selection of columns to be given to the classifier. Information gain is employed to compute the reduction in entropy after each split. The entropy is a measure which calculates the purity of the subset. Initially, the subsets are spitted based upon various attributes and the splitting occurs until all the same classes are contained in single subset which is referred as pure subset. In the proposed system, the entropy ranges from 0 to 1 which represents high entropy and low entropy respectively. The minimum count of entropies represents the highest amount of Information by the attributes in the dataset gained. In the proposed system, the noise is reduced which is caused by unwanted feature and simple attribute rank method is used to identify the feature which have most of the information. Entropy is calculated using Eq. (2).
where Pi represents count of attributes for class i. Moreover, c is count of values on the classification classes. By Using this formula, Information gain value is computed by using Eq. (3).
S→ Number of Sample, A→ Number of attributes, v→ value of attribute A.
\(\:values\left(A\right)\to\:Setof\:values\:for\:A\), \(\:\left|Sv\right|\to\:no\:of\:samples\:for\:value\:v\)
In the proposed system, the Information gain have been used in a filter-based method which is less inclined to over fitting. This feature selection method results in more relevant, important and required attributes which reduces execution time of classification algorithm. Based upon the weight value the features are grouped. Relevant FS is made to reduce the dimensions in dataset. With entropy, features are evaluated using information gain. Feature selection algorithm is implemented by using TensorFlow software. In wrapper-oriented FS method, Recursive FS (RFS) method is used. The major use of FS is for getting higher accuracy even by diminishing the multi-dimensional data. In this system, RFS technique collects relevant and irrelevant features during every iteration so that it can attain significant and relevant features. This method is efficient since it does not randomly select the feature it finds out which is the most relevant feature and performs iteration. Algorithm 1 gives the steps to be followed for computing information gain and ranking based feature selection from the given dataset.
Intelligent classification module
For this module, one bagging-based Fuzzy CNN algorithm is proposed which incorporates the concept of bootstrap aggregation and with fuzzy CNN for efficient classification. This fuzzy CNN algorithm called BFCNN uses fuzzy rules for implicit decision making and to control over fitting problem, the bagging concept is applied. The CNN classification algorithm is extended in this work with bagging and fuzzy rules. The major components of the CNN classifier used for extension in this work are the convolutional layers, max pooling layers, activation functions, and finally the fully connected layers31. In this CNN, 10 pairs of convolution and max pooling layers and 1 fully connected NN are used in this work. The mathematical operation shown in Eq. (7) named convolution operation is performed in the convolution layer.
Let the size of input matrix: N x N.
Let the size of filer: F x F.
Then the convolution operation is defined as:
-
Convolution operation is the product matrix:
Stride is used to decide on how much amount the kernel matrix will shift as it slides over the input matrix. For a stride of 1, the kernel moves one row/ column at a time. For a stride of 2, it will move two elements at a given time.
The size of the output matrix obtained after applying a convolution operation with a given stride s and padding p is calculated using the formula given in Eq. (8):
Moreover, the max pooling is a pooling operation is used here to select the maximum element from the region of the feature map covered by the filter. Finally, the output after max-pooling layer would be a feature map containing the most prominent features of the previous feature map. The CNN considered in this work uses the ReLU activation function for decision making. Here, ReLU is a piecewise linear function which is defined as shown in Eq. (9):
This ReLU activation function will replace all the negative values in the input with zeros. It means that this function is “activating” only the neurons which will contribute to the neural network with respect to decision-making. The fully connected layers are where each neuron in the CNN are connected to every neuron in the previous layer. Mathematically, this is a linear transformation followed by an activation function. The linear transformation is defined in Eq. (10) as follows: For a given input vector x and a weight matrix W, the output z is calculated as:
The proposed is also supported by the Adam optimizer90. The fuzzy membership functions used in the fuzzy rule generation are number of failed logins, number of comprised condition and wrong fragments. The fuzzy inference system proposed in this work for the CNN uses the triangular fuzzy membership functions that are given in Equations (11) as:
The variable x is the fuzzy variable and the symbols a, b, and c are the boundary values. Moreover, the fuzzy distance values are computed here by applying the values in the membership function. For de-fuzzification, the Centre of Area (COA) method as defined in Eq. (12) is used in this work.
where:
x is the value of the linguistic variable.
µ(x) is the membership function for the value x.
Algorithm 2 shows the steps of the Fuzzy Based CNN classification algorithm proposed in this work for the accurate detection of intrusions in IOV.
Fuzzy rules generated by fuzzy inference system is used the intrusion detection process. Table 6 gives the fuzzy inference rules of the proposed system.
The Main aim of bagging in the fuzzy CNN with Adam Optimizer is to decrease the false positives. From training sample, subgroup of data is chosen in random. Each and every model gains uniform weight. All the decisions coming from the classifier are taken into account and the average is calculated. Here, a dataset D is given as input and samples are split and are given to the model. The final output is obtained from every separate model. Algorithm 3 gives steps of Bagging based fuzzy CNN with Adam Optimizer in the proposed system.
Here, 10-fold cross validation method is used. Each CNN is trained with 9 folds of each set of data and are tested with one-fold from each set of data. It is not random but, the data are selected sequentially.
Performance evaluation and results
This work was carried out in Del Laptop with.
Processor: Intel Core i5-7300u (2.6 GHz base clock, 6 MB Cache).
Display: 14-inch FHD (1366 × 768), Slim, anti-glare, 220 nits.
Memory & Storage: 8 GB DDR4 SDRAM (1 × 8 GB) (Expandable upto 32GB)| 256 GB PCIe M.2 SSD.
Graphics : Integrated Intel HD Graphics 620.
OS: Windows 11 pro.
The softwares used for implementing this IDS are NS3, Python and Tensorflow.
The simulation parameters used in this work are shown in Table 7.
The evaluation of this proposed Intelligent IDS is measured using precision, recall, accuracy as well as F1-Score. This system was implemented with TensorFlow and Python. This evaluation employed the confusion matrix using four major components namely, True Positive (TP), True Negative (TN), False Positive (FP), False Negative (FN) whereas TP represents accurately of malicious attack in network. The TN indicates the identification of all the non-malicious attacks, FP assumes that all the non-malicious attacks as malicious attack and FN recognizes all the malicious attack falsely as not malicious attack. The metrics are computed by using Eqs.17182039.
.
Figure 2 gives Probe attack analysis by comparing BFCNN with other related classifiers namely SVM, RF, CNN, LSTM, CNN with LSTM.
From Fig. 2, it is clear that the proposed BFCNN with Adam Optimizer provides better Detection Accuracy than other classifiers namely SVM, RF, CNN, LSTM, CNN with LSTM due to fuzzy inference and Adam Optimization.
Figure 3 shows the DoS attack accuracy analysis of the proposed BFCNN by comparing with the existing classifiers namely SVM, RF, CNN, LSTM, CNN with LSTM. From Figure-3, it is verified that the proposed IDS increases the Detection Accuracy with respect to DoS attack detection in comparison with other related classifiers such as SVM, RF, CNN, LSTM, CNN with LSTM due to the use of fuzzy rules for traffic monitoring and bagging for reducing variations.
Figure 4 provides the R2L attack detection accuracy analysis of the proposed IDS developed using BFCNN with Adam Optimization by comparing it with the other existing classification algorithms namely SVM, RF, CNN, LSTM, CNN with LSTM.
From Figure-4, it is evident that the proposed BFCNN with Adam Optimizer shows higher Detection Accuracy in R2L attack detection when compared to relevant classifiers due to better Feature Selection and fuzzy inference with optimization. Here, the performance evaluation of R2L attack analysis is achieved here through the rule based approach.
Figure 5 depicts U2R attack analysis between BFCNN and other existing classifiers such as SVM, RF, CNN, LSTM, CNN with LSTM.
From Fig. 5, it is proved that the proposed BFCNN with Adam Optimizer classifier enhances the Detection Accuracy on U2R attacks when compared it with related classifiers namely SVM, RF, CNN, LSTM, CNN with LSTM by employing fuzzy rules, effective access control and optimization with bagging. Figure 6 provides the Packet Delivery Rate (PDR) analysis in presence of IDS and absence of IDS in the IoV network.
From Fig. 6, it is clear that the routing with IDS performs better in terms of PDR when compared with network routing without IDS. The IDS provides efficient authentication of network packets and provides the network traffic analysis to filter out the incoming malicious data from the network leading to enhanced PDR.
Figure 7 gives the Delay analysis in presence of IDS and absence of IDS in the IoV network.
From Fig. 7, it is clear that the network with IDS makes less delay when it is compared with the network without IDS. Moreover, the network with IDS provides efficient authentication of network packets and provides the network traffic analysis to filter out the incoming malicious data from the network.
Figure.8 shows the training accuracy analysis for the existing classifiers namely SVM, RF, CNN, LSTM, CNN with LSTM and the proposed BFCNN classification algorithm.
From Figure.8, it is proved that the training accuracy is more for the proposed work when compared to the existing works due to the use of bagging and fuzzy inference modelling used effectively in the training.
Figure.9 shows the Training loss analysis.
From Fig. 9, it is shown that the testing loss is less for the proposed BFCNN when compared to the existing classifiers namely SVM, RF, CNN, LSTM and CNN + LSTM.
Figure.10 shows the testing accuracy analysis for the existing classifiers namely SVM, RF, CNN, LSTM, CNN with LSTM and the proposed BFCNN classification algorithm.
From Figure.10, it is evident that the training accuracy is higher for the proposed BFCNN when compared to the existing algorithms namely SVM, RF, CNN, LSTM, CNN with LSTM due to the use of bagging and fuzzy inference modelling in training.
Figure.11 shows the testing loss analysis for the proposed BFCNN by comparing it with the existing algorithms namely SVM, RF, CNN, LSTM, CNN with LSTM.
From Fig. 11, it can be observed that the testing loss is minimum for the proposed BFCNN when it is compared with the testing loss occurred in the existing classifiers namely SVM, RF, CNN, LSTM and CNN + LSTM. This reduction in loss by the proposed BFCNN is due to the effective decisions made by the fuzzy inference rules.
The proposed system was tested with simulations and also tested with network test bed available at Madras Institute of Technology Campus, Anna University, Chennai. Hence, the analysis carried out in this work is almost near to the deployment of this model in a real network. So, it is feasible to perform analysis of training/inference time, model size, and deployment in real-time vehicular environments.
Figure 12 shows RoC curve of the proposed Bagging Fuzzy CNN (BFCNN). From Fig. 12 it is observed that the proposed system exibits better behaviour under RoC and has better AUC of 0.963 when it is compared with other existing models.
Conclusion and future work
In this paper, a novel hybrid-based IDS with effective feature selection and bagging based Fuzzy CNN classifier with Adam optimization is proposed to provide efficient detection of intrusions in Internet of Vehicles network. The proposed IDS uses WBRFSA for feature selection and BFCNN for classification. The proposed system employs fuzzy rules to classify the data using fuzzy CNN with Adam Optimizer in an effective manner. Moreover, the proposed IDS employs bagging technique along with fuzzy CNN with Adam Optimizer to improve the intrusion detection accuracy and reduce false data alarm by reducing the over fitting problem in classification process. The proposed IDS is implemented in Tensor Flow software with Python and it is tested for various types of attacks namely probe attack, DoS attack, R2L attack, U2R attack. The implementation results justify that the proposed IDS provides better intrusion detection accuracy, reducing false alarm rate in the IoV network. Moreover, the proposed IDS improves Packet delivery ratio, reduction in delay, improvement in throughput and reduction in computational and communicational overhead in IoV networks. The main limitation of this work is that it is carried out only using simulations. It is to be implemented in a real network and is to be tested as a future work. Another limitation is the detection accuracy which is another possible future work to the proposed system for improving the detection accuracy further using spatial and temporal analysis. The future work on this will be the extension of this proposed work to deploy this IDS in 5G-V2X environment by varying the parameters.
Data availability
The dataset used and analyzed during the current study available from the corresponding author on reasonable request.
References
Elrawy, M. F., Awad, A. I., Hamed, H. F. & A Intrusion detection systems for IoT-based smart environments: a survey. J. Cloud Comput. 7 (1), 1–20. https://doi.org/10.1186/s13677-018-0123-6 (2018).
Al-Naji, F. H. & Zagrouba, R. A survey on continuous authentication methods in Internet of Things environment, Comput. Commun. 163, 109–133, (2020). https://doi.org/10.1016/j.comcom.2020.09.006
Alzubi, O. A., Qiqieh, I. & Alzubi, J. A. Fusion of deep learning based cyber attack detection and classification model for intelligent systems. Cluster Comput. 26, 1363–1374 (2023).
Alweshah, M., Hammouri, A., Alkhalaileh, S. & Alzubi, O. Intrusion detection for the internet of things (IoT) based on the emperor Penguin colony optimization algorithm. J. Ambient Intell. Humaniz. Comput. 14 (5), 6349–6366 (2023).
Alzubi, O. A. A deep learning-based Frechet and dirichlet model for intrusion detection in IWSN. J. Intell. Fuzzy Syst. 42 (2), 873–883 (2022).
Alzubi, O. A., Alzubi, J. A., Qiqieh, I. & Al-Zoubi, A. M. An IoT intrusion detection approach based on salp swarm and artificial neural network. Int. J. Network Manage. 35 (1), e2296 (2025).
Khraisat, A., Gondal, I., Vamplew, P. & Kamruzzaman, J. Survey of intrusion detection systems: techniques, datasets and challenges. Cybersecurity 2 (1). https://doi.org/10.1186/s42400-019-0038-7 (2019).
Sheikh, T. U., Rahman, H., Al-Qahtani, H. S., Kumar Hazra, T. & Sheikh, N. U. Countermeasure of Attack Vectors using Signature-Based IDS in IoT Environments, 2019 IEEE 10th Annu. Inf. Technol. Electron. Mob. Commun. Conf. IEMCON pp. 1130–1136, (2019). https://doi.org/10.1109/IEMCON.2019.8936231
Chaabouni, N., Mosbah, M., Zemmari, A., Sauvignac, C. & Faruki, P. Network intrusion detection for IoT security based on learning techniques. IEEE Commun. Surv. Tutorials. 21 (3), 2671–2701. https://doi.org/10.1109/COMST.2019.2896380 (2019).
Omolara, A. E., Alabdulatif, A., Abiodun, O. I. & Alawida, M. Abdulatif alabdulatif,wafa’ Hamdan alshoura, Humaira Arshad the internet of things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 112, 102494. https://doi.org/10.1016/j.cose.2021.102494 (2022).
Tidjon, L. N., Frappier, M. & Mammar, A. Intrusion detection systems: A Cross-Domain overview. IEEE Commun. Surv. Tutorials. 21 (4), 3639–3681. https://doi.org/10.1109/COMST.2019.2922584 (2019).
Selvakumar, B. & Muneeswaran, K. Firefly algorithm based feature selection for network intrusion detection. Comput. Secur. 81, 148–155. https://doi.org/10.1016/j.cose.2018.11.005 (2019).
Di Mauro, M., Galatro, G., Fortino, G., Liotta, A. & March Supervised feature selection techniques in network intrusion detection: A critical review. Eng. Appl. Artif. Intell. 101, 104216, doi: https://doi.org/10.1016/j.engappai.2021.104216. (2021).
Maldonado, J., Riff, M. C. & Neveu, B. A review of recent approaches on wrapper feature selection for intrusion detection. Expert Syst. Appl. 198, 116822. https://doi.org/10.1016/j.eswa.2022.116822 (2022).
Zarpelao, B. B., Miani, R. S., Kawakani, C. T. & De Alvarenga, S. C. A survey of intrusion detection in Internet of Things, J. Netw. Comput. Appl. 84, 25–37, (2017). https://doi.org/10.1016/j.jnca.2017.02.009
Amrita & Ahmed, P. A study of feature selection methods in intrusion detection system: A survey. Int. J. Comput. Sci. Eng. Inf. Technol. Res. 2 (3), 1–25 (2012).
Hajiheidari, S., Wakil, K., Badri, M. & Navimipour, N. J. Intrusion detection systems in the internet of things: A comprehensive investigation. Comput. Networks. 160, 165–191. https://doi.org/10.1016/j.comnet.2019.05.014 (2019).
Upadhyay, D., Manero, J., Zaman, M. & Sampalli, S. Intrusion detection in SCADA based power grids: recursive feature elimination model with majority vote ensemble algorithm. IEEE Trans. Netw. Sci. Eng. 8 (3), 2559–2574. https://doi.org/10.1109/TNSE.2021.3099371 (2021).
Mehta, S., Paunwala, C., Vaidya, B. & Systems, C. CNN based traffic sign classification using Adam optimizer. International Conference on Intelligent Computing and (ICCS), Madurai, India, pp. 1293–1298. (2019).
Sivatha Sindhu, S. S., Geetha, S. & Kannan, A. Decision tree based light weight intrusion detection using a wrapper approach. Expert Syst. Appl. 39 (1), 129–141. https://doi.org/10.1016/j.eswa.2011.06.013 (2012).
Haider, W., Hu, J., Slay, J., Turnbull, B. P. & Xie, Y. Generating realistic intrusion detection system dataset based on fuzzy qualitative modelling. J. Netw. Comput. Appl. 87, 185–192 (2017).
Garcia, S., Parmisano, A. & Erquiaga, M. J. IoT-23: A labelled dataset with malicious and benign IoT network traffic, (2020).
Al-Hadhrami, Y. & Hussain, F. K. Real time dataset generation framework for intrusion detection systems in IoT. Future Generation Comput. Syst. 108, 414–423 (2020).
Kingma, D. P. & Ba, J. Adam: A method for stochastic optimization. arXiv preprint arXiv:1412.6980, (2014).
Nazir, A. & Khan, R. A. A novel combinatorial optimization based feature selection method for network intrusion detection. Comput. Secur. 102, 102164. https://doi.org/10.1016/j.cose.2020.102164 (2021).
Nimbalkar, P. & Kshirsagar, D. Feature selection for intrusion detection system in Internet-of-Things (IoT). ICT Express. 7 (2), 177–181. https://doi.org/10.1016/j.icte.2021.04.012 (2021).
Mohammadi, S., Mirvaziri, H., Ghazizadeh-Ahsaee, M. & Karimipour, H. Cyber intrusion detection by combined feature selection algorithm. J. Inf. Secur. Appl. 44, 80–88. https://doi.org/10.1016/j.jisa.2018.11.007 (2019).
Wisanwanichthan, T. & Thammawichai, M. A Double-Layered hybrid approach for network intrusion detection system using combined Naive Bayes and SVM. IEEE Access. 9, 138432–138450. https://doi.org/10.1109/ACCESS.2021.3118573 (2021).
Ganapathy, S. et al. Intelligent feature selection and classification techniques for intrusion detection in networks: A survey. Eurasip J. Wirel. Commun. Netw. 2013 (1), pp. 1–16, https://doi.org/10.1186/1687-1499-2013-271 (2013).
LeCun, Y., Bengio, Y. & Hinton, G. Deep Learn. Nat., 521, 7553, 436–444, (2015).
Alhaidari, F. A. & Alrehan, A. M. A simulation work for generating a novel dataset to detect distributed denial of service attacks on vehicular ad hoc network systems. Int. J. Distrib. Sens. Netw. 17 (3), 1–25 (2021).
Sokkalingam, Sumathi, and Rajesh Ramakrishnan. An intelligent intrusion detection system for distributed denial of service attacks: A support vector machine with hybrid optimization algorithm based approach. Concurr. Comput. 34 (27), e7334. (2022).
Sumathi, S., Rajesh, R. & Lim, S. Recurrent and deep learning neural network models for DDoS attack detection. J. Sens. 2022 (1), 8530312 (2022).
Sumathi, S., Rajesh, R. & Karthikeyan, N. DDoS attack detection using hybrid machine learning based IDS models. J. Sci. Ind. Res. 81, 276–286 (2022).
Sumathi, S. & Rajesh, R. A dynamic BPN-MLP neural network DDoS detection model using hybrid swarm intelligent framework. Indian J. Sci. Technol. 16 (43), 3890–3904 (2023).
Sumathi, S. & Rajesh, R. Comparative study on TCP SYN flood DDoS attack detection: a machine learning algorithm based approach. WSEAS Trans. Syst. Control. 16, 584–591 (2021).
Ramasubramanian, P. & Kannan, A. A genetic-algorithm Based Neural Network short-term Forecasting Framework for Database Intrusion Prediction System10pp.699–714 (soft Computing, 2006).
Subramani, S. et al. An intrusion detection system for securing iot based sensor networks from routing attacks. In International Conference on Computer, Communication, and Signal Processing (pp. 321–334). Cham: Springer Nature Switzerland. (2023).
Deris Stiawan, A., Heryanto, A., Bardadi, D. P. & Rini Imam much Ibnu subroto, Kurniabudi an approach for optimizing ensemble intrusion detection systems. IEEE Access. 9, 6930–6947. https://doi.org/10.1109/ACCESS.2020.3046246 (2021).
Injadat, M., Moubayed, A. & Nassif, A. B. Multi-Stage optimized machine learning framework for network intrusion detection. IEEE Trans. Netw. Serv. Manag. 18 (2), 1803–1816. https://doi.org/10.1109/TNSM.2020.3014929 (2021).
Kasongo, S. M. An advanced intrusion detection system for IIoT based on GA and tree based algorithms. IEEE Access. 9, 113199–113212. https://doi.org/10.1109/ACCESS.2021.3104113 (2021).
Gaikwad, D. P. & Thool, R. C. Intrusion detection system using bagging with partial decision tree base classifier. Procedia Comput. Sci. 49 (1), 92–98. https://doi.org/10.1016/j.procs.2015.04.231 (2015).
Gao, X., Shan, C., Hu, C., Niu, Z. & Liu, Z. An adaptive ensemble machine learning model for intrusion detection. IEEE Access. 7, 82512–82521. https://doi.org/10.1109/ACCESS.2019.2923640 (2019).
Zhou, Y., Cheng, G., Jiang, S. & Dai, M. Building an efficient intrusion detection system based on feature selection and ensemble classifier. Comput. Networks 174, 107247 https://doi.org/10.1016/j.comnet.2020.107247 (2020).
He, H. et al. A novel Multimodal-Sequential approach based on Multi-View features for network intrusion detection. IEEE Access. 7, 183207–183221. https://doi.org/10.1109/ACCESS.2019.2959131 (2019).
Sabeel, U., Heydari, S. S., Elgazzar, K. & El-Khatib, K. Building an intrusion detection system to detect atypical cyberattack flows. IEEE Access. 9, 94352–94370. https://doi.org/10.1109/ACCESS.2021.3093830 (2021).
Al-Abassi, A., Karimipour, H., Dehghantanha, A. & Parizi, R. M. An ensemble deep learning-based cyber-attack detection in industrial control system. IEEE Access. 8, 83965–83973. https://doi.org/10.1109/ACCESS.2020.2992249 (2020).
Kim, T. & Pak, W. Real-time network intrusion detection using deferred decision and hybrid classifier. Futur Gener Comput. Syst. 132, 51–66. https://doi.org/10.1016/j.future.2022.02.011 (2022).
Papamartzivanos, D., Gómez Mármol, F. & Kambourakis, G. Dendron: genetic trees driven rule induction for network intrusion detection systems. Futur Gener Comput. Syst. 79, 558–574. https://doi.org/10.1016/j.future.2017.09.056 (2018).
Kunal & Dua, M. Attribute Selection and Ensemble Classifier based Novel Approach to Intrusion Detection System. Procedia Comput. Sci. 167 (2019), 2191–2199. (2020). https://doi.org/10.1016/j.procs.2020.03.271
Sharma, N. V. & Yadav, N. S. An optimal intrusion detection system using recursive feature elimination and ensemble of classifiers. Microprocess Microsyst. 85, 104293. https://doi.org/10.1016/j.micpro.2021.104293 (2021).
Gupta, N., Jindal, V. & Bedi, P. CSE-IDS: using cost-sensitive deep learning and ensemble algorithms to handle class imbalance in network-based intrusion detection systems. Comput. Secur. 112, 102499. https://doi.org/10.1016/j.cose.2021.102499 (2022).
Viegas, E., Santin, A. O., Franca, A., Jasinski, R. & Pedroni, V. A. Towards an energy-efficient anomaly-based intrusion detection engine for embedded systems. IEEE Trans. Comput. 66 (1), 163–177. https://doi.org/10.1109/TC.2016.2560839 (2017).
Herrera-Semenets, V., Bustio-Martínez, L., Hernández-León, R. & Van Den Berg, J. A multi-measure feature selection algorithm for efficacious intrusion detection. Knowledge-Based Syst. 227, 107264. https://doi.org/10.1016/j.knosys.2021.107264 (2021).
Jenif Souza, D. W. S., Parvathavarthini, B. & Arunmozhi, A. Machine learning based intrusion detection framework using recursive feature elimination method. 2020 Int. Conf. Syst. Comput. Autom. Netw. ICSCAN 2020. https://doi.org/10.1109/ICSCAN49426.2020.9262282 (2020).
Teng, S., Wu, N., Zhu, H., Teng, L. & Zhang, W. SVM-DT-based adaptive and collaborative intrusion detection. IEEE/CAA J. Autom. Sin. 5 (1), 108–118. https://doi.org/10.1109/JAS.2017.7510730 (2018).
Halim, Z. et al. An effective genetic algorithm-based feature selection method for intrusion detection systems. Comput. Secur. 110, 102448. https://doi.org/10.1016/j.cose.2021.102448 (2021).
Kurniabudi, S. D., Darmawijoyo, Bin Bin Idris, M. Y. & Bamhdi, A. M. CICIDS-2017 dataset feature analysis with information gain for anomaly detection. IEEE Access. 8, 132911–132921. https://doi.org/10.1109/ACCESS.2020.3009843 (2020).
Panda, M., Mousa, A. A. A. & Hassanien, A. E. Developing an efficient feature engineering and machine learning model for detecting IoT-Botnet cyber attacks. IEEE Access. 9, 91038–91052. https://doi.org/10.1109/ACCESS.2021.3092054 (2021).
Ustebay, S., Turgut, Z. & Aydin, M. A. Intrusion Detection System with Recursive Feature Elimination by Using Random Forest and Deep Learning Classifier. Int. Congr. Big Data, Deep Learn. Fight. Cyber Terror. IBIGDELFT 2018 - Proc., pp. 71–76, (2019). https://doi.org/10.1109/IBIGDELFT.2018.8625318
Besharati, E. & Naderan, M. LR-HIDS: logistic regression host-based intrusion detection system for cloud environments. J. Ambient Intell. Humaniz. Comput. 10 (9), 3669–3692. https://doi.org/10.1007/s12652-018-1093-8 (2018).
Tama, B. A., Comuzzi, M. & Rhee, K. H. TSE-IDS: A Two-Stage classifier ensemble for intelligent Anomaly-Based intrusion detection system. IEEE Access. 7, 94497–94507. https://doi.org/10.1109/ACCESS.2019.2928048 (2019).
Pu, G., Wang, L., Shen, J. & Dong, F. A hybrid unsupervised clustering-based anomaly detection method. Tsinghua Sci. Technol. 26 (2), 146–153. https://doi.org/10.26599/TST.2019.9010051 (2021).
Binbusayyis, A. & Vaiyapuri, T. Identifying and benchmarking key features for cyber intrusion detection: an ensemble approach. IEEE Access. 7, 106495–106513. https://doi.org/10.1109/ACCESS.2019.2929487 (2019).
Artur, M. Review the performance of the Bernoulli Naïve Bayes Classifier in Intrusion Detection Systems using Recursive Feature Elimination with Cross-validated selection of the best number of features. Procedia Comput. Sci. 190 (2019), 564–570, https://doi.org/10.1016/j.procs.2021.06.066 (2021).
Kasongo, S. M. & Sun, Y. A deep learning method with wrapper based feature extraction for wireless intrusion detection system. Comput. Secur. 92 https://doi.org/10.1016/j.cose.2020.101752 (2020).
Rose, T., Kifayat, K., Abbas, S. & Asim, M. A hybrid anomaly-based intrusion detection system to improve time complexity in the internet of energy environment. J. Parallel Distrib. Comput. 145, 124–139. https://doi.org/10.1016/j.jpdc.2020.06.012 (2020).
Anand, M. et al. ‘Deep Learning Model based IDS for Detecting Cyber Attacks in IoT based Smart Vehicle Network’, International Conference on Sustainable Computing and Data Communication Systems (ICSCDS), Erode, India, pp. 281–286, (2023).
Nancy, P. et al. Intrusion detection using dynamic feature selection and fuzzy Temporal decision tree classification for wireless sensor networks. IET Commun. 14 (5), 888–895. https://doi.org/10.1049/iet-com.2019.0172 (2020).
Wang, W., Jian, S., Tan, Y., Wu, Q. & Huang, C. Representation learning-based network intrusion detection system by capturing explicit and implicit feature interactions. Comput. Secur. 112, 102537. https://doi.org/10.1016/j.cose.2021.102537 (2022).
Biswas, K., Muthukkumarasamy, C. V., Wu, M. J. M. & & Singh, X. W. K., A multipath routing protocol for secure energy efficient communication in Wireless Sensor Networks. Computer Networks 232, p. 109842. (2023).
Santhosh Kumar, S. V. N., Selvi, M. & Kannan, A. A comprehensive survey on machine Learning-Based intrusion detection systems for secure communication in internet of things. Comput. Intell. Neurosci. 2023 (1), 8981988 (2023).
Shalini, S. & Selvi, M. Intelligent IDS in Wireless Sensor Networks Using Deep Fuzzy Convolutional Neural Networkvol. 35pp. 15201–15220 (Springer, 2023). Neural Computing and Applications.
Rajasoundaran, S., Kumar, S. S., Selvi, M., Thangaramya, K. & Kannan, A. Secure and optimized intrusion detection scheme using LSTM-MAC principles for underwater wireless sensor networks. Wireless Netw. 30 (1), 209–231 (2024).
Yesodha, K., Krishnamurthy, M., Selvi, M. & Kannan, A. Intrusion detection system extended CNN and artificial bee colony optimization in wireless sensor networks. Peer-to-Peer Netw. Appl. 17, 1237–1262 (2024).
Balakrishnan Senthilnayaki, Venkatalakshmi, K. & Arputharaj Kannan Intrusion detection system using fuzzy rough set feature selection and modified KNN classifier. Int. Arab. J. Inform. Technol. 16 (4), 746–753 (2019).
Raghavendra, T., Anand, M., Selvi, M., Thangaramya, K. & Santhosh Kumar, S. V. N. Kannan a,an intelligent RPL attack detection using machine Learning-Based intrusion detection system for internet of things. Procedia Comput. Sci. 215, 61–70 (2022).
Ganapathy, S., Kulothungan, K. & Yogesh, P. Kannan A,A novel weighted fuzzy C –Means clustering based on immune genetic algorithm for intrusion detection. Procedia Eng. Elsevier. 38, 1750–1757 (2012).
Senthilnayaki, B., Venkatalakshmi, K. & Kannan, A. March. Intrusion detection using optimal genetic feature selection and SVM based classifier. In 2015 3rd international conference on signal processing, communication and networking (ICSCN) (pp. 1–4). IEEE. (2015).
Hizal, S., Cavusoglu, U. & Akgun, D. A novel deep learning-based intrusion detection system for IoT DDoS security. Internet of Things 28, p.101336. (2024).
Heidari, A. & Jabraeil Jamali, M. A. Internet of things intrusion detection systems: a comprehensive review and future directions. Cluster Comput. 26 (6), 3753–3780 (2023).
Maheswaran, N., Bose, S., Logeswari, G. & Anitha, T. Hybrid Intrusion Detection System Using Machine Learning Algorithm. In Proceedings of Data Analytics and Management: ICDAM 2022 (pp. 333–346). Singapore: Springer Nature Singapore. (2023).
Kamel, J. et al. VeReMi extension: a dataset for comparable evaluation of misbehavior detection in VANETs. In: International Conference on Communications (ICC), pp. 1–6. IEEE (2020).
Jais, I. K. M., Ismail, A. R. & Nisa, S. Q. Adam optimization algorithm for wide and deep neural network. Knowl. Eng. Data Sci. 2 (1), 41–46 (2019).
Sumathi, S., & Rajesh, R. HybGBS: A hybrid neural network and grey wolf optimizer for intrusion detection in a cloud computing environment. Concurr. Comput., 36(24), p.e8264. (2024).
Belenko, V., Krundyshev, V. & Kalinin, M. Synthetic datasets generation for intrusion detection in VANET. In: 11th International Conference on Security of Information and Networks, pp. 1–6. ACM (2018).
Haidar, F. et al. Dare: a reports dataset for global misbehavior authority evaluation in c-its. In: 91st Vehicular Technology Conference (VTC 2020-Spring), pp. 1–6. IEEE (2020).
Alzubi, J. A., Alzubi, O. A., Qiqieh, I. & Singh, A. A blended deep learning intrusion detection framework for consumable edge-centric IOMT industry. IEEE Trans. Consum. Electron., 70(1), pp.2049–2057, (2024).
Tavallaee, M., Bagheri, E., Lu, W. & Ghorbani, A. A. July. A detailed analysis of the KDD CUP 99 data set. In 2009 IEEE symposium on computational intelligence for security and defense applications, pp. 1–6. (2009).
Kalpani, N., Rodrigo, N., Seneviratne, D., Ariyadasa, S. & Senanayake, J. Cutting-edge approaches in intrusion detection systems: a systematic review of deep learning, reinforcement learning, and ensemble techniques. Iran. J. Comput. Sci.,8, pp.303–333, (2025).
Funding
There is no funding available.
Author information
Authors and Affiliations
Contributions
Mr.Anand M carried out the literature survey, analysis and design of the proposed the new Feature Selection Algorithm and the use of CNN for classification. He did the full implementation of the work in Python.Dr. S. Muthurajkumar has validated the design of Feature selection and classification algorithms and also developed the architecture of this system. Also, he formed the full structure of this article.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Research involving human participants and/or animals
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Anand, M., Muthurajkumar, S. An intelligent IDS using bagging based fuzzy CNN for secured communication in vehicular networks. Sci Rep 15, 26952 (2025). https://doi.org/10.1038/s41598-025-09633-4
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-09633-4