Abstract
With the widespread adoption of Internet of Things (IoT) technologies in healthcare systems, security issues related to user privacy during data transmission and sharing have become increasingly prominent. To address these challenges, this paper proposes a medical privacy protection and secure sharing scheme based on Quantum Key Distribution (QKD). The scheme integrates multiple technologies, including blockchain, smart contracts, zero-knowledge proofs, and Chebyshev chaotic mapping, to ensure secure data sharing and access control among multiple communication entities. Compared with existing solutions, our approach enhances key management security through quantum keys and improves communication resilience against attacks by leveraging chaotic systems. User identity privacy is protected via zero-knowledge proofs. Under the random oracle model, the security of the proposed scheme is formally proven. Moreover, comparative experiments with existing protocols demonstrate the scheme’s comprehensive advantages in terms of security and performance, evaluated across throughput, computational overhead, communication overhead, and storage overhead.
Similar content being viewed by others
Introduction
IOT is a new research topic with social, technical and economic significance. In the Internet of Things, daily items such as durable goods, vehicles, various public utility components, sensors, etc. are being associated with Internet connection and powerful data analysis capabilities to change our lifestyle1. With the rapid development of the IoT technology, the IoT has become closely related to our lives, and it has been applied in various fields, such as smart home2, healthcare3, intelligent bus4, industrial manufacturing5 and other fields. Today, with the rapid development of 5G networks, this growth trend will become more and more obvious. Faster 5G networks will also mean that the vast amounts of data collected from the IoT will be analyzed and managed faster6. Traditional IoT systems rely on data centers to store and process information. This makes the information surface a serious privacy risk, especially for individual users.
Private data on IoT devices can bring benefits to individuals as a personal digital asset. Taking the IoT medical scenario as an example, the application of IoT technology in the medical scenario stems from the monitoring of patients, using wearable medical devices embedded with wireless sensors to collect the patient’s physical parameters7 and send them back to the data center for analysis and evaluation. However, the high security of patient data has become a big problem faced by the development of Internet medicine.
In recent years, the development of various software is getting faster and faster, malicious software is becoming more and more difficult to detect and resist, and the security loopholes of medical information system lead to the leakage of medical information at any time. As a result, patients’ medical data is at risk8,9. For example, Anthem, the second largest health insurance provider in the United States, was hacked, resulting in the disclosure of 78 million customer information, including patients’ personal information, health data and other sensitive data. Therefore, how to intelligently obtain accurate medical results while protecting current patient information from being leaked has become the biggest problem in the development of IoT medical.
Blockchain technology can assist IoT systems in terms of privacy protection, traceability, and interoperability10. Blockchain is a distributed ledger. It comes from the Bitcoin Advanced System, which uses a consensus mechanism to make the data on the chain unfalsifiable and untampered. In addition, smart contract technology has also accelerated the application of blockchain. A smart contract defines an agreement between two communicating parties, according to which transactions are automatically executed in the form of executable code11. Therefore, blockchain technology is conducive to solving the privacy problem in the process of medical data sharing, opening up data islands, providing a safe sharing and trading platform for medical data, making clear the ownership of data, and effectively preventing data from being maliciously tampered with or abused and resold by third parties12. It is also widely used in digital currencies13,14,15, energy trading16, and car networking17,18.
This paper proposes a medical privacy protection sharing scheme based on quantum key on blockchain. Contributions are as follows:
-
(1)
This solution adopts the decentralized architecture of Hyperledger Fabric alliance chain to solve the problems of information asymmetry, easy tampering and leakage in traditional medical privacy solutions, and proposes a scheme combining virtual address and smart contract to apply for quantum keys. A user anonymous “virtual address” is introduced to replace the exposure of real identity information during the key request process. Combined with smart contracts, this enables automated and trustworthy tracking of key applications, which not only mitigates the risks of centralized key management but also enhances the privacy protection of user identities.
-
(2)
Zero-knowledge proof is used to verify the correctness of shared user information. Chebyshev mapping is used to construct the session key of user communication, and the protection and sharing of user privacy data are realized by combining quantum key and session key, which expands the key usage range of quantum key distribution platform.
-
(3)
Based on the random prediction model, the security of the scheme is proved and analyzed. In addition, compared with other schemes, this scheme has improved the computation overhead, communication overhead and storage overhead.
The organization of this paper is as follows: Section “Related work” reviews related work. Section “Preliminaries” introduces preliminary knowledge. Section “System model” details the design of our proposed scheme. Section “Safety analysis” presents the corresponding security analysis. and Section “Experimental analysis” evaluates the performance through experiments.
Related work
Many predecessors have used cryptographic tools19,20 to solve this problem, such as using Fully Homomorphic Encryption (FHE)21,22. However, due to the cost disadvantage of FHE, these solutions will bring huge computational overhead and are not suitable for large-scale application scenarios. In addition, Yu et al.23 proposed a blockchain privacy protection method based on homomorphic encryption. The verification node operates and verifies the encrypted user transaction information, which improves the data security and privacy of blockchain technology. Wu et al.24 combined homomorphic encryption with blockchain smart contracts to solve the problem of privacy leakage in the medical insurance claims process. Smart contracts operate on ciphertext data and can determine whether the claim conditions are met without viewing the patient’s plaintext data. They also implement automatic claims functions to prevent patients from leaking sensitive data when interacting with other roles. To enhance the security of private data in open environments, Souici et al.25 proposed a genetic algorithm-based image encryption method, offering a novel approach for achieving high-security and high-efficiency encryption in complex environments. This method provides a new perspective for the secure transmission of medical images. Muneeswari26 proposed an innovative self-diagnosis platform (SDP) that can securely retrieve patients’ private information and provide a point-to-point data encryption and authentication mechanism. Neither patients nor third parties can directly obtain each other’s identity information. However, since the scheme uses sensors for information collection, the encryption and decryption process may still cause a certain computing burden on edge devices (such as sensors), especially when dealing with high-frequency data collection.
The introduction of blockchain technology has provided a solution for the medical industry to solve large-scale data management. Its characteristics such as immutability, decentralization and traceability are considered by many scholars to be the key technology leading the transformation of the Internet from information characteristics to value characteristics27. Limbasiya128 proposed a privacy-preserving authentication and key agreement protocol for multi-server medical systems. The authentication process relies on the generation and verification of random numbers and timestamps. If there are vulnerabilities in the random number generator or time synchronization mechanism, it may lead to security risks. Li et al.29 borrowed the method of secure multicast communication and proposed an on-demand public blockchain privacy protection method. However, this method still uses the RSA asymmetric cryptographic algorithm to encrypt and protect privacy, so its efficiency is limited when encrypting long privacy30. Lee et al.31 proposed an electronic health record (EHR) sharing mechanism based on blockchain and smart contracts, using blockchain, smart contracts and de-identification to ensure data security. Although de-identification reduces the risk of direct leakage, complex association attacks may re-identify patients through other metadata, and the authorization process may not meet real-time requirements in specific scenarios. Zou et al.32 proposed a blockchain-based electronic medical system for medical data sharing and privacy protection. Patient electronic medical records are stored on special key blocks and microblocks for fast retrieval. However, the communication burden of this scheme is so large that the application scenarios are subject to many restrictions. We list the functional comparison of each scheme in Table 1.
Preliminaries
Blockchain technology
The emergence of blockchain began in 2008 with a paper published by Satoshi Nakamoto titled Bitcoin: A peer-to-peer electronic cash system33. The paper points out that blockchain technology is the basic technology to build the Bitcoin system, and the blockchain records all the metadata and encrypted transaction information, thus establishing an electronic cash system that is completely implemented through peer-to-peer (P2P) technology, and this system allows the two parties of online payment to transact directly without going through a third-party financial institution. Subsequently, the Bitcoin system became popular, and more and more people paid attention to and studied it, and the blockchain technology as the underlying technology of the Bitcoin system was also paid attention to, which opened the prelude to the study of blockchain technology.
Blockchain technology is a new technology, but it is not an innovative technology. It is a technology that integrates many existing interdisciplinary disciplines together, involving mathematics, cryptography, computer science and other fields. Bitcoin system is the first system built with blockchain technology as the underlying technology, and it is a decentralized, trustless, safe and reliable electronic cash system34. According to different trust scenario construction methods,it is divided into public chain, alliance chain and private chain.Public chain is a blockchain open to everyone, anyone can join and participate in the complete consensus accounting process, there is no need to trust each other, it has the characteristics of complete decentralization, but at the same time, it also brings a variety of problems such as waste of resources, inefficiency, public chain used in Bitcoin, Ethereum and other deregulated, anonymous, free cryptocurrency scene. The alliance chain is constructed by an alliance composed of multiple institutions, and the generation, consensus and maintenance of the ledger are completed by the members designated by the alliance. When combining blockchain with other technologies for scene innovation, the fully open and decentralized characteristics of the public chain are not necessary, and its low efficiency can not meet the demand, so the alliance chain has become a more practical blockchain selection in some scenarios. Compared with the alliance chain, the private chain is more centralized, and the process of data generation, consensus and maintenance is completely controlled by a single organization, and the members designated by the organization only have access to the ledger35. Blockchain uses distributed consensus algorithm to generate and update data, and uses peer-to-peer network for data transmission between nodes, combined with cryptography principles and time stamps and other technologies of distributed ledger to ensure that the stored data cannot be tampered with, the use of automated script code or smart contracts to achieve upper-layer application logic. If the traditional database realizes the unilateral maintenance of data, then the blockchain realizes the maintenance of the same data by multiple parties to ensure the security of data and the fairness of business. The workflow of blockchain mainly includes three steps: block generation, consensus verification, and ledger maintenance35.
-
(1)
Generate blocks. Blockchain nodes collect transactions that are broadcast across the network—data entries that need to be recorded, and then package those transactions into blocks—data sets with a specific structure.
-
(2)
Consensus verification. Nodes broadcast blocks to the network, and the nodes of the whole network receive a large number of blocks for sequential consensus and content verification, forming a ledger—a set of blocks with a specific structure.
-
(3)
Account maintenance. The node stores the verified ledger data for a long time and provides functions such as backchecking, providing the ledger access interface for upper-layer applications.
Blockchain ensures data immutability by dividing information into multiple blocks, each containing the hash of the previous block, thereby forming a chained structure. Its core lies in the consensus mechanism—such as the endorsement mechanism and ordering service adopted in Fabric—which ensures that only data authenticated by multiple parties can be written to the chain, effectively preventing single-point tampering and malicious writes. Meanwhile, data is distributed across multiple nodes, and, combined with cryptographic techniques and smart contracts, the system enables data integrity verification, access control, and traceability, significantly enhancing the security of data sharing processes.
Bilinear pairing and hard computational problems
Definition 1
Let \({(\mathbb {G}_1,+)}\) and \({(\mathbb {G}_2,\cdot )}\) be cyclic groups of prime order q, where q is a prime number. If the mapping \(e:{{\mathbb {G}}_{1}}\times {{\mathbb {G}}_{1}}\rightarrow {{\mathbb {G}}_{2}}\) satisfies the following properties, then e is called a computable bilinear mapping.
Bilinearity: \(\forall P,{{P}_{1}},{{P}_{2}}\in {{\mathbb {G}}_{1}}\),\(a,b\in Z_{q}^{*}\). \(e(P,{{P}_{1}}+{{P}_{2}})=e(P,{{P}_{1}})e(P,{{P}_{2}})\), \(e(a{{P}_{1}},b{{P}_{2}})=e{{({{P}_{1}},{{P}_{1}})}^{ab}}\).
Nondegeneracy: \(\exists {{R}_{1}},{{R}_{2}}\in {{\mathbb {G}}_{1}}\) and satisfies \(e({{R}_{1}},{{R}_{2}})\ne {{1}_{{{\mathbb {G}}_{2}}}}\).
Computability: \(\forall {{R}_{1}},{{R}_{2}}\in {{\mathbb {G}}_{1}}\), there exists an efficient algorithm to compute \(e({{R}_{1}},{{R}_{2}})\).
The definition of problems based on bilinear pairings is as follows.
Definition 2
Discrete Logarithm Problem: Given \({{R}_{1}},{{R}_{2}}\in {{\mathbb {G}}_{1}}\), find an integer \(c\in Z_{q}^{*}\) such that \({{R}_{1}}=c{{R}_{2}}\).
Definition 3
Computation Diffie–Hellman Problem(CDHP): Given \(P,{{a}_{1}}P,{{a}_{2}}P\) and assuming \(P\in {{\mathbb {G}}_{1}},{{a}_{1}},{{a}_{2}}\in Z_{q}^{*}\), compute \({{a}_{1}}{{a}_{2}}P\).
Chebyshev chaotic mapping
This section introduces the basic concepts of Chebyshev chaotic mapping36.
Definition 4
n is an integer, \(x \in [ - 1,1]\), and the Chebyshev polynomial is defined as follows:\({T_n}(x) = \cos (n\arccos (x))\). Its iterative relationship is as follows: \({T_n}(x) = (2x{T_{n - 1}}(x) - {T_{n - 2}}(x))\), when \(n \in [2, + \infty )\), \({T_0}(x) = 1\), and \({T_1}(x) = x\). In addition, Zhang37 proved that Chebyshev polynomials are still valid in intervals \(x \in ( - \infty , + \infty )\). It has an important semigroup property.
Semigroup: For \(x \in ( - \infty , + \infty ), n \in [2, + \infty )\), there is \({T_r}({T_s}(x)) = {T_s}({T_r}(x)) = {T_{rs}}(x)\bmod p\). r, s is a positive integer and p is a large prime number. In addition, the following problems are considered to be difficult to solve in polynomials.
Diffie Hellman Problem in Chaotic Mapping computation(CMCDHP): Given a variable \(x, {T_r}(x), {T_s}(x)\), the probability calculated \({T_{rs}}(x)\) by an opponent in probability polynomial time is negligible.
In the proposed scheme, the Chebyshev chaotic map is employed to generate session keys, which are combined with quantum keys to strengthen both the randomness and the resilience against attacks during the key agreement process.
Zero-knowledge proof
Zero-knowledgeproof (ZKP) is a cryptographic technique that can convince a verifier that a statement is true without providing any additional information to the verifier or revealing any information about the evidence. ZKP’s solutions are divided into interactive38 and non-interactive39. Compared with interactive non-interactive, multiple interactions are not required in the proof process, so collusion attacks are avoided and security is improved. Being non-interactive on the blockchain can avoid confusion in on-chain transactions and improve privacy. Currently, zkSNARKs is considered as an implementation of non-interactive zero-knowledge proof, and there are some excellent algorithms such as Groth1640 and PGHR1341. Compared with other algorithms, the verification of Groth16 requires less computation and is concise. Therefore, ZKP based on Groth16 is widely used in blockchain and various cryptocurrencies. Similarly, in this paper, the zero knowledge algorithm will adopt the Groth16 algorithm. Groth16 requires three steps for zero-knowledge proof:
-
(1)
\(Setup(R) \rightarrow \sigma\): Input polynomials R and execute Setup algorithms to generate common parameters \(CRS,\sigma\).
-
(2)
\(\Pr ove(R,\sigma ,\phi ,\omega ) \rightarrow \pi\): The prover takes R,\(\sigma\),using them and \(\phi\),\(\omega\) as input parameters to run the \(\Pr ove\) algorithm and produce the proof \(\pi\), which \(\phi\) is the public parameter of the prover and \(\omega\) is the private parameter to be proved.
-
(3)
\(Verify(\sigma ,\pi ) \rightarrow 0/1\): The verifier gets \(\sigma\) and \(\pi\) submitted by the prover performs the Verify algorithm to know if the prover knows the private parameter \(\omega\), and returns 1 if the answer is OK, otherwise returns 0.
To safeguard private data from leakage, the Groth16 algorithm is employed to implement a secure and efficient zero-knowledge verification mechanism.
System model
With the foundational cryptographic components in place, the following section introduces the overall system architecture and the key procedures of the proposed protocol.
The symbols and their meanings are shown in Table 2.
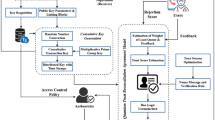
Our system primarily consists of the following entities, a Trusted Authority (TA), a user (UE), a blockchain network (BCN), and a Quantum Key Distribution Platform (QKDP), as shown in Fig. 1.
TA: Mainly responsible for system initialization, registration of system entities, and deployment of smart contracts.
UE: Users are divided into patients and doctors. Patients have their own Medical Privacy Data(abbreviation: MPD) and can request quantum keys from QKDP to encrypt their MPD and share it. The doctor can request the patient’s MPD as needed. The patient can decide whether to share the quantum key used for encryption with the doctor based on the doctor’s unique identification, and the doctor uses the quantum key to decrypt the MPD.
BCN: BCN is composed of multiple servers of the hospital, and the smart contract in BCN is responsible for the storage of public parameters and private data of the system. The blockchain framework used in this paper is the HyperLedgerFabric Consortium chain Framework.
QKDP: QKDP stores quantum keys. The user requests a quantum key from QKDP, and QKDP returns the quantum key to the user through a secure channel. QKDP internally maintains two lists, the encryption key table \({E_{List}}\) and the decryption key table \({D_{List}}\). When a user applies for a key, QKDP randomly selects a set of keys from \({E_{List}}\) and returns them to the user. At the same time, the key is stored in \({D_{List}}\) for use.
In the proposed scheme, the smart contracts are deployed onto the Hyperledger Fabric consortium blockchain by the Trusted Authority (TA) during the system initialization phase. These contracts define a set of operational logics related to quantum key management, including user key requests, storage of key distribution results, validation of key validity, and recording of shared keys. When a user applies for a quantum key or uploads ciphertext, the corresponding smart contract functions are invoked to record the user’s virtual address, encryption index, timestamp, and other related information on the blockchain. The smart contract automatically handles index generation, access verification, and data writing, ensuring that the key usage process is tamper-proof and fully auditable. Furthermore, the smart contract plays a critical role in the key-sharing process between users. It is responsible for recording key-sharing events and triggering verification mechanisms (such as timestamp checks and zero-knowledge proof verification), thereby effectively enabling decentralized key management and privacy-preserving sharing control.
Scheme description
The following description takes \(U{E_i}\) as the patient and \(U{E_j}\) as the doctor.
-
(1)
System initialization. The security parameter of the system is defined as \(\lambda\), and let \({\mathbb {G}_1}\) and \({\mathbb {G}_2}\) be the cyclic addition group and the cyclic multiplication group of prime q, \(\forall P \in {\mathbb {G}_1}\). TA selects three safe hash functions \({H_1}\), \({H_2}\), \({H_3}\). \({H_1}: {\{ 0,1\} ^*} \rightarrow Z_q^*\), \({H_2}: {\mathbb {G}_1} \rightarrow Z_q^*\), \({H_3}:{\{ 0,1\} ^*} \rightarrow {\{ 0,1\} ^l}\). At the same time, choose a large prime number p, and then randomly choose two integers \(x, sk \in ( - \infty , + \infty )\). TA publishes the system parameter \((x, {\mathbb {G}_1}, {\mathbb {G}_2}, {H_1}, {H_2}, {H_3},p)\) to the blockchain and deploys the smart contract. sk is TA’s private key. This paper sets the system security parameter as \(\lambda\), which is used to uniformly measure the security level of cryptographic constructions in the protocol. For example, large prime numbers p, hash function output length \(|H(\centerdot )|\), and chaotic mapping seed length all satisfy \(|p|\ge \lambda |H(\centerdot )|\ge \lambda\). In the subsequent security analysis, the probability that an adversary successfully breaks any cryptographic construction within the protocol is at most \({{2}^{-\lambda }}\), thereby ensuring that the overall system meets the semantic security objective.
-
(2)
User registration is shown in Fig. 2. \(U{E_i}\) registers with TA. The \(U{E_i}\) selects its own \(I{D_i}\) to send to the TA. The TA selects the random number \({r_1}\) and computes \({k_i} = {H_1}(I{D_i}||sk||{r_i})\). Send \(\{ {k_i},(x,{T_{{k_i}}}(x))\}\) to \(U{E_i}\) over a secure channel. The \(U{E_i}\) receives \(\{ {k_i},(x,{T_{{k_i}}}(x))\}\), saves \({k_i}\), and invokes the smart contract to upload the public key \((x,{T_{{k_i}}}(x))\) to the blockchain.
-
(3)
The process of user \(U{E_i}\) applying quantum key to QKDP is shown in Fig. 3. The \(U{E_i}\) randomly selects \((\phi ,\psi \in Z_q^*)\), calculates \(\Phi = \phi P,\Psi = \psi P\), and sends \(\{ I{D_i},\Phi ,\Psi \}\) to QKDP.
-
(4)
QKDP returns quantum key to \(U{E_i}\) as shown in Fig. 4. QKDP receives {\({ I{D_i}, \Phi , \Psi }\)} and calculates virtual address \(\hat{a} = {H_2}(\partial \Phi )P + \Psi ,\hat{A} = \partial P(\partial \in Z_q^*)\). \({a_1}, r\) is randomly selected and \(k = {H_3}(I{D_i}||{a_1}||r), HI{D_i} = {H_1}(I{D_i}||k)\) is calculated. Then, QKDP randomly selects a set of quantum keys \(ke{y_i}\) from \({E_{List}}\) list and calculates \(U{A_i} = {H_3}(\hat{a}) \oplus ke{y_i}, U{B_i} = {H_3}(ke{y_i})\). QKDP will take \(ke{y_i}\) out of \({E_{List}}\), then store it in \({D_{List}}\), finally send \(\{ k, U{A_i}, U{B_i}\}\) to \(U{E_i}\), call smart contract, will use \(index = HI{D_i}\) as index, store \(value = {\{ \hat{A}, {t_1}}\}\) to blockchain network BCN.
-
(5)
User \(U{E_i}\) uses quantum key to encrypt data as shown in Fig. 5. The \(U{E_i}\) gets \(\{ k,U{A_i},U{B_i}\}\), calculates the index \(HI{D'_i} = {H_1}(I{D_i}||k)\), and uses the index value \(HI{D'_i}\) to find \(\{ \hat{A},{t_1}\}\) on the blockchain. If the transaction exists, the \(U{E_i}\) verifies that the timestamp \({t_1}\) has expired, and if it has, the \(U{E_i}\) re-requests the quantum key from QKDP. Otherwise, calculate \(\alpha = {H_2}(\phi \hat{A}) + \psi\), \(\hat{a}' = \alpha P = ({H_2}(\phi \hat{A}) + \psi )P = {H_2}(\partial \Phi )P + \Psi,\) \(ke{y_i} = {H_3}(\hat{a}') \oplus U{A_i}\), calculate \(U{B_i}^\prime = {H_3}(ke{y_i})\) after obtaining the key, judge \(U{B_i}^\prime \mathop = \limits ^? U{B_i}\), if equal, use quantum key \(ke{y_i}\) to encrypt MPD, \(C{T_i} = {E_{ke{y_i}}}(MPD)\), and then randomly select \({a_2}\), calculate \(GL = {T_{{a_2}}}(x)\bmod p\), \(CI{D_i} = {H_1}((x,{T_{{k_i}}}(x)))\), call smart contract to \(index = CI{D_i}\) as the index, and upload \(value = \{ C{T_i},GL,{t_2}\}\) to the blockchain network BCN.
-
(6)
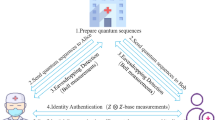
The process for user \(U{E_j}\) to obtain user \(U{E_i}\) privacy information is shown in Fig. 6. The \(U{E_j}\) computes \(CI{D_i}^\prime = {H_1}((x,{T_{{k_i}}}(x)))\) as an index to find \(\{ C{T_i},GL,{t_2}\}\) on the blockchain. If the transaction exists, \(U{E_j}\) verifies whether \({t_2}\) expires. If not, \({r_j}\) is randomly selected, \({M_1} = {H_3}({r_j}||I{D_j}||k{}_j),\) \({M_2} = {H_3}({r_j}||{M_1}),\) \({k_{{r_j}i}} = {T_{{r_j}}}({T_{{k_i}}}(x))\), \({k_{ji}} = {T_{{k_j}}}({T_{{k_i}}}(x))\), \({M_3} = {H_3}({k_{{r_j}i}}) \oplus ID{}_j \oplus {r_j}\) is calculated, \({k_{ji}}\) is used to encrypt \({M_3}\) to obtain ciphertext \({M_4} = {E_{{k_{ji}}}}({M_3})\), \({a_3}\) is randomly selected, \({D_1} = {T_{{a_3}}}(x)\), \({D_2} = {T_{{a_3}}}(GL),\) \({D_3} = {H_3}(C{T_i}) \oplus {D_2} \oplus I{D_j}\) is calculated, and \(\{ {M_1},{M_2},{M_3},{M_4},{T_{{r_j}}}(x),{T_{{k_j}}}(x),{D_1},{D_3},{t_3}\}\) is sent to user \(U{E_i}\). After getting the information, \(U{E_i}\) first calculates whether the timestamp \({t_3}\) is expired. If it is expired, it returns to \(U{E_j}\) that the information is expired; otherwise, it calculates \({D_2}^\prime = {T_{{a_2}}}({D_1})\), \(I{D_j}^\prime = {D_2}^\prime \oplus {H_3}(C{T_i}) \oplus {D_3}\). Calculate the key \({k_{ij}}^\prime = {T_{{k_i}}}({T_{{k_j}}}(x))\). Use key \({k_{ij}}^\prime\) to decrypt \({M_4}\) to get \({M_3}^\prime\), \({M_3}^\prime = {D_{{k_{ij}}^\prime }}({M_4})\). Then calculate \({k_{{r_j}i}}^\prime = {T_{{k_i}}}({T_{{r_j}}}(x))\), get the key \({k_{{r_j}i}}^\prime\), calculate \({r_j}^\prime = I{D_j}^\prime \oplus {H_3}({k_{{r_j}i}}^\prime ) \oplus {M_3}^\prime\), and judge \({M_2}^\prime = {H_3}({r_j}^\prime ||{M_1})\mathop = \limits ^? {M_2}\). If equal, the \(U{E_i}\) determines whether to share information with the \(U{E_j}\) based on the \(I{D_j}^\prime\). If information needs to be shared, \(U{E_i}\) randomly selects \({a_4}\) and calculates \({D_4} = {T_{{a_4}}}(x)\), \({D_5} = {T_{{a_4}}}({D_1})\), session key \(s{k_i} = {H_3}({H_3}(C{T_i}||ID{{}_j^\prime })||{D_5}||{r_j}^\prime )\), \({D_6} = {H_3}({D_4}||s{k_i}||{D_5}||{t_4})\). Send \(\{ {D_4},{D_6},{t_4}\}\) to \(U{E_j}\). After receiving the information, \(U{E_j}\) first verifies whether the timestamp \({t_4}\) is expired, if not, \(U{E_j}\) calculates \({D_5}^\prime = {T_{{a_3}}}({D_4})\), \(s{k_j} = {H_3}({H_3}(C{T_i}||I{D_j})||{D_5}^\prime ||{r_j})\). Verify \({D_6}^\prime = {H_3}({D_4}||s{k_j}||{D_5}^\prime ||{t_4})\mathop = \limits ^? {D_6}\). If they are equal, the \(U{E_j}\) requests the \(U{E_i}\) to send the quantum key. \(U{E_i}\) calculates \(C{T_{ke{y_i}}} = {E_{s{k_i}}}(ke{y_i})\). The ciphertext is sent to \(U{E_j}\). After receiving the ciphertext, \(U{E_j}\) decrypts the quantum \(ke{y_i} = {D_{s{k_j}}}(C{T_{ke{y_i}}})\) using \(s{k_j}\), decrypts the ciphertext \(C{T_i}\), and obtains the user’s MPD. User \(U{E_j}\) builds zero-knowledge proof \(\pi\), (MPD and \(I{D_j}\) for private input, \(PubIn = {H_1}(MPD)\) for public input) computes \(CI{D_j} = {H_1}(I{D_j}),\) invokes smart contract, uses \(index = CI{D_j}\) as index, uploads \(value = \{ \pi ,{t_5}\}\) to blockchain network BCN.
-
(7)
User \(U{E_i}\) confirms whether the information is securely shared, as shown in Fig. 7. The user \(U{E_j}\) builds an index \(CI{D_j}^\prime = {H_1}(I{D_j}^\prime )\) to look up on the blockchain and, if the transaction exists, verifies that the timestamp \({t_5}\) has expired. If there is no expiration, \(PubIn' = {H_1}(MPD)\) is built to verify the zero-knowledge proof \(\pi\), while the smart contract calculates \({\omega _i} = {H_1}(PubIn'||\pi )\) and uploads \({\omega _i}\) to the blockchain network BCN. After successful verification, repeat steps 3, 4, and 5 for \(U{E_i}\). Re-encrypt your private data and upload it to the blockchain network BCN. At the same time, QKDP deletes \(ke{y_i}\) corresponding to user \(U{E_i}\) in \({D_{List}}\) from the table.
Note: Due to the existence of length extension attacks by Groth16, this paper uses hash function \({\omega _i} = {H_1}(PubIn'||\pi )\) to mark the already used public input, avoiding the occurrence of extension attacks.
Discussion of correctness
The correctness of \({D_2},{D_5}\) and session key \(s{k_i}\) is verified according to the semigroup property of the Chebyshev mapping.
The correctness of \({D_2}\) is verified as follows.
The correctness of \({D_5}\) is verified as follows.
\(s{k_i}\) session key verification is as follows.
Safety analysis
Upon completing the system design, we proceed to formally verify the security of the protocol as follows.
Security model
Entities: Scheme participants include user \(U{E_i}\) and \(U{E_j}\), and each participant includes multiple entities such as \(UE_i^r\) and \(UE_j^r\).
Query: An attacker can make the following queries:
Execute: oracle returns a message sent over a public channel to the attacker. This query simulates a wiretapping attack.
Send: The attacker emulates the entity and sends a message m, which returns a response message if the sent message m is legitimate.
Reveal(\(UE_i^r,UE_j^r\)) : If instance \(UE_i^r,UE_j^r\) generates a session key SK, the attacker gets the key, otherwise it returns an invalid symbol \(\bot\).
Test: The query verifies that it is semantically secure, and the attacker can perform a maximum of one query. If \(UE_i^r,UE_j^r\) contains SK, oracle rolls a coin b. If b=1, it returns SK to the attacker, otherwise it immediately returns a string of equal length to the attacker. If \(UE_i^r,UE_j^r\) does not contain SK, \(\bot\) is returned.
Semantic security: \(Succ({\mathscr {A}})\) represents the probability that the opponent will win the game in polynomial time. Under the Random Seer, adversary \({\mathscr {A}}\) runs a series of games to distinguish between real session keys and random strings. \({\mathscr {A}}\) guesses that the value of Test is \(b'\). When \(b = b'\), guess is correct. \({\mathscr {A}}\)’s advantage in the semantic security of the solution in polynomial time is defined as:
Therefore, our scheme is secure, and \(Ad{v_R}({\mathscr {A}})\) of \({\mathscr {A}}\) is negligible in any polynomial time.
Security proof
Formal security analysis
Theorem 1
\(Succ({\mathscr {A}})\) represents that the proposed scheme is defeated by enemy \({\mathscr {A}}\) in polynomial time. Assume that \({\mathscr {A}}\) performs \({q_{exe}}\) Execute queries, \({q_{send}}\) Send queries, and \({q_h}\) Hash queries in polynomial time.
\(Adv_{\mathscr {A}}^{CMCDHP}(t)\) stands for \({\mathscr {A}}\)’s advantage in solving CMCDHP in polynomial time, so there is
where \({l_1}\) is the output length of the hash function.
Proof
We use a series of games \(Gam{e_i}\) to derive the advantage of \({\mathscr {A}}\) breaking our scheme in polynomial time.
\(Gam{e_0}\): The real attack launched by \({\mathscr {A}}\) against the scheme is simulated. Results:
\(Gam{e_1}\): The game uses all of the random and hash machines mentioned above. \({\mathscr {A}}\) uses passive attack to get messages between instances. This \(Gam{e_1}\) is basically the same as \(Gam{e_0}\). As a result:
\(Gam{e_2}\): In this game, because the messages in this scheme include hash function output and random numbers, \({\mathscr {A}}\) can find message conflicts through the Execute predictor and Send predictor, where, based on the birthday paradox principle42, the hash function conflict output is at most \(\frac{{{q_h}^2}}{{{2^{{l_1} + 1}}}}\). The collision of random numbers is at most \(\frac{{{{({q_{send}} + {q_{exe}})}^2}}}{{2p}}\). Therefore,
\(Gam{e_3}\):The session key is obtained by the Chebyshev mapping values \({T_{{a_4}}}({D_1})\) and \({T_{{a_3}}}({D_4})\), although the Chebyshev polynomials \({D_1}\) and \({D_4}\) are known, but calculating \({T_{{a_4}}}({D_1})\) and \({T_{{a_3}}}({D_4})\) is difficult because it is a CMCDHP problem. The maximum probability of \({\mathscr {A}}\) solving the CMCDHP problem in polynomial time is \(2{q_h}Adv_{\mathscr {A}}^{CMCDHP}(t)\) through the number of queries \({q_{send}} + {q_{exe}}\) to \(UE_i^r,UE_j^r\) and the number of hash queries \({q_h}\). As a result,
\({\mathscr {A}}\) executes the Test query after completing the above series of games and gets,
Through the derivation of the above formula, we can conclude:
\(\square\)
Informal security analysis
-
(1)
Anonymity: Because the real identity is not used in the process of mutual information authentication between the two parties, and the virtual address is also used when applying for the quantum key, the attacker cannot obtain the corresponding data by intercepting the authentication message.
-
(2)
Traceability: The system records all critical operations on the blockchain, including user registration, key requests, and data access. Each operation is bound with a timestamp and a virtual address, ensuring that system activities are auditable and accountability is traceable, while protecting users’ real identities from exposure.
-
(3)
Information confidentiality and authentication: Medical data during uploading, access, and sharing are recorded and verified through smart contracts and hash verification mechanisms. Combined with zero-knowledge proofs, this ensures the correctness of identity and permission verification processes, safeguarding the integrity of information exchange. A quantum key-based encryption mechanism, coupled with Chebyshev chaotic mapping, is employed to provide strong encryption protection for sensitive medical data, allowing only authorized entities to decrypt. Additionally, the virtual address mechanism further protects user identities, enhancing overall communication confidentiality.
-
(4)
Time stamp attack: The attacker intercepts and falsifies the authentication message between \(UE_i\) and \(UE_j\) to verify their identity. In this scheme, the message receiver uses Hash digest to check the integrity of the message, and discards the message if it is tampered with.
-
(5)
Man-in-the-middle attack: This scheme involves two-way authentication between \(UE_i\) and \(UE_j\) when obtaining private information. In addition, the authentication message is transmitted confidentially through XOR operation, and has an integrity Hash digest. Therefore, the man-in-the-middle attack by eavesdropping and tampering with information is invalid.
Experimental analysis
Hardware environment
The simulation environment of the experiment is a computer with Intel Core I9-13900H 2.60GHz dual-core processor, 16G running memory and Windows11 operating system. Using VMware Workstation Pro 16.2.3 set up to 4 GB memory, hard disk size for 50 GB ubuntu 20.04 system. With the help of the open source Hyperledge Fabric 2.2 version developed by IBM, an experimental environment was constructed in which the blockchain network was configured with 3 Org organizations, 6 Peer nodes and 3 Order nodes.
Scheme comparison
The comparison between the approach proposed in this paper and other similar approaches is shown in Table 3.
In the scheme, the amount of \(\oplus\) and || computation is very small, and the time cost can be ignored. \({\mathrm{{T}}_H}\) represents the time needed to calculate the hash function, \({T_{CM}}\) represents the Chebyshev chaos mapping time, \({T_{ECC}}\) represents the operation time of elliptic curve dot multiplication, and \({T_{D/E}}\) represents the time of symmetric encryption and decryption.To calculate the execution time, this paper uses the Golang language and the PBC library. By calculating the hash function operation time, elliptic curve dot product operation time, symmetric encryption/decryption time, \({\mathrm{{T}}_H}\), \({T_{CM}}\), \({T_{ECC}}\), \({T_{D/E}}\) time cost is 0.54 ms, 3.2 ms, 18.4 ms, 5.9 ms. The time cost of this scheme and related schemes is shown in Table 4. The total time cost of our scheme is \(10{T_{CM}} + 14{\mathrm{{T}}_H} + 4{T_{D/E}}\) when \(U{E_j}\) obtains the privacy information of \(U{E_i}\). The costs of the schemes mentioned in reference46 and reference47 are \(3{T_{ECC}} + 22{\mathrm{{T}}_H}\) and \(2{T_{D/E}} + 30{\mathrm{{T}}_H}\) respectively, and the calculation costs are 67.08 ms and 28 ms respectively. It can be seen from Table 4 that the scheme cost of reference47 is lower, because the scheme of reference47 is lightweight enough, resulting in relatively low communication cost. The cost of the scheme proposed by us is also better than that in reference46, and the advantage will be more obvious when the number of users increases.
Quantum key distribution time overhead
In order to evaluate QKDP distribution quantum key delay, we design the time cost of requesting quantum key from QKDP when the number of users is 100, 200, 300, 400, 500. In the experiment, QKDP returned two key lengths, 128 bit and 256 bit respectively. As shown in Fig. 8, when the length of the quantum key is 128bit, the delay is about 4.4 ms, and when the length of 256bit, the delay is about 5.3 ms on average. Due to the nature of the quantum key, which is one secret at a time and cannot be listened to, we give priority to the delay factor, so we use the 128 bit quantum key.
Scheme throughput testing
In order to understand the throughput of the entire scheme, we simulated scenarios with the number of users 10, 20, 30, 40, 50 and the number of transactions 1000, 2000, 3000, 4000, 5000, 6000, 7000. As shown in Fig. 9, the throughput of the solution eventually levels off as the number of users and the number of transactions increases. Because as the number of users and the number of transactions increases, the load on the blockchain network becomes larger, so the overall throughput becomes smooth when the number of transactions is 7000.
Communication overhead and storage overhead
In order to calculate the communication overhead, this paper assumes a random number, hash value, symmetric encryption algorithm and ID length of 128 bits, elliptic curve dot multiplication algorithm output length of 256 bits, Chebyshev mapping algorithm length of 160bits, and timestamp length of 32 bits. \(U{E_j}\) sends \(\{ {M_1},{M_2},{M_3},{M_4},{T_{{r_j}}}(x),{T_{{k_j}}}(x),{D_1},{D_3},{t_3}\}\) to \(U{E_i}\) to request privacy information. This message needs 128 + 128 + 128 + 128 + 160 + 160 + 160 + 128 + 32 = 1152 bits. The \(U{E_i}\) returns the verification message \(\{ {D_4},{D_6},{t_4}\}\), which requires 160 + 128 + 32= 320 bits. \(U{E_j}\) requests the quantum key from \(U{E_i}\), and \(U{E_i}\) returns the quantum key ciphertext \(C{T_{ke{y_i}}}\) to \(U{E_j}\), which requires 128 bits. Therefore, the communication overhead required by this scheme is 1152 + 320 + 128 = 1600 bits. Reference46 in the stage of identity authentication and session key generation, the communication overhead is 8 elliptic curve dot product outputs, 6 hash function outputs, and 5 timestamps, so the communication overhead of reference46 is \(8 \times 256 + 6 \times 128 + 32 \times 5\) = 2976 bits, reference47 in the whole communication process, there are 13 hash function outputs and 2 ID outputs. Therefore, the communication overhead of reference47 is \(128 \times 15\) = 1920 bits. Our scheme only needs three interactions during authentication. In reference46, it takes one communication for the user to send the login request to the edge node (EN), one communication for the EN to send the login request to the medical center node (MC), one communication for the MC to process the login request and then return to the EN, and one communication for the EN to authenticate the MC to return the message to the user. Finally, it takes one communication for the EN to compute the session key and distribute it to the user and MC, for a total of five. In reference47, the processes of user registration, sensor registration, authentication and session key negotiation require 1 communication each, and a total of 4 communication times are required. Therefore, our scheme has obvious advantages in communication cost, which will become more obvious with the increase of the number of users.
In our scheme, during the interaction phase of privacy information acquisition, UE needs to store one random number, one ciphertext of privacy information, one identity ID, one session key, and one Chebyshev polynomial, so the number of bytes to be stored is \(128 \times 4 + 160\) = 672 bits. \(U{E_j}\) needs to store two random numbers, one for each privacy ciphertext, identity ID, session key, and Chebyshev polynomial, so the number of bytes to be stored is \(128 \times 5 + 160\) = 800 bits. The total number of bytes to be stored is 1472 bits. In reference46, the number of bytes that the user needs to store is 256 + 128 + 128 = 512 bits (1 elliptic curve dot product, 2 identity IDs), EN needs to store \(128 \times 5 + 3 \times 256\) = 1408 bits (5 identity IDs, 2 elliptic curve dot product), MC needs to store \(256 + 128 \times 2 \times\) = 512 bits (2 identity IDs, 1 elliptic curve dot product). The total storage cost is 512 + 1408 + 512 = 2432 bits. In the scheme proposed in reference47, the user needs to store \(128 \times 3 + 128 + 128 + 128 + 128\) = 896 bits (3 identity IDs, 1 session key, 1 random number, 1 hash value, and 1 shared key each). The sensor needs to store \(128 \times 3 + 128 + 128 + 128 + 128 + 128\) = 1024 bits (3 identity IDs, 2 hash values, 1 session key, 1 random number, 1 shared key, and 1 random number each). The server needs to store \(128 \times 2 + 128 \times 2 + 128 \times 2\) = 768 bits (2 each for identity ID, shared key, and hash value), with a total storage cost of \(896 + 1024 + 768\) = 2688 bits. As can be seen from Fig. 10, our scheme has lower communication overhead and storage overhead compared with other schemes.
Conclusion
To address the challenges of privacy protection and data sharing in medical services, this paper proposes a quantum key-based privacy-preserving data sharing scheme for healthcare scenarios. In terms of scalability, the scheme leverages lightweight cryptographic primitives (such as chaotic maps and hash functions) in combination with smart contract mechanisms deployed on the blockchain, thereby eliminating the need for a centralized key management architecture. By utilizing the parallel processing capabilities and access control features of the Fabric consortium blockchain, the system maintains high responsiveness and processing efficiency even under large-scale user or device deployments. Regarding cost efficiency, the design focuses on reducing computational and communication overhead while minimizing on-chain data storage. Experimental evaluations further demonstrate that the proposed scheme outperforms several existing methods in terms of throughput, computation, communication, and storage efficiency. However, this paper does not consider bypassing the role of the trusted authority, but merely leveraging distributed ledger technology. In addition, many scholars predict that as quantum computing capabilities improve, existing encryption technologies will face serious challenges. Therefore, in the future, we need to deeply study the blockchain mechanism and design an efficient and secure sharing scheme. In the meantime, the risk of quantum attacks may need to be considered.
Methods
Topical subheadings are allowed. Authors must ensure that their Methods section includes adequate experimental and characterization data necessary for others in the field to reproduce their work.
Data availability
The datasets generated and/or analyzed during the current study are not publicly available due to privacy or ethical restrictions, but they are available from the corresponding author upon reasonable request.
References
Limbasiya, T. & Karati, A. Cryptanalysis and improvement of a mutual user authentication scheme for the internet of things. In 2018 International Conference on Information Networking, ICOIN 2018, Chiang Mai, Thailand, January 10–12, 2018, 168–173, https://doi.org/10.1109/ICOIN.2018.8343105 (IEEE, 2018).
Errapotu, S. M. et al. SAFE: Secure appliance scheduling for flexible and efficient energy consumption for smart home IoT. IEEE Internet Things J. 5, 4380–4391. https://doi.org/10.1109/JIOT.2018.2866998 (2018).
Sodhro, A. H., Pirbhulal, S. & Sangaiah, A. K. Convergence of IoT and product lifecycle management in medical health care. Futur. Gener. Comput. Syst. 86, 380–391. https://doi.org/10.1016/j.future.2018.03.052 (2018).
Zhu, F. et al. Parallel transportation systems: Toward IoT-enabled smart urban traffic control and management. IEEE Trans. Intell. Transp. Syst. 21, 4063–4071. https://doi.org/10.1109/TITS.2019.2934991 (2019).
Liu, Y., Dillon, T., Yu, W., Rahayu, W. & Mostafa, F. Noise removal in the presence of significant anomalies for industrial IoT sensor data in manufacturing. IEEE Internet Things J. 7, 7084–7096. https://doi.org/10.1109/JIOT.2020.2981476 (2020).
Ni, J., Lin, X. & Shen, X. S. Efficient and secure service-oriented authentication supporting network slicing for 5G-enabled IoT. IEEE J. Sel. Areas Commun. 36, 644–657. https://doi.org/10.1109/JSAC.2018.2815418 (2018).
Satija, U., Ramkumar, B. & Manikandan, M. S. Real-time signal quality-aware ECG telemetry system for IoT-based health care monitoring. IEEE Internet Things J. 4, 815–823. https://doi.org/10.1109/JIOT.2017.2670022 (2017).
Schwartz, P. & Reidenberg, J. R. Data privacy law: A study of United States data protection (1996).
Nissenbaum, H. Privacy in context: Technology, policy, and the integrity of social life. Privacy Context https://doi.org/10.1515/9780804772891 (2009).
Wang, Q., Zhu, X., Ni, Y., Gu, L. & Zhu, H. Blockchain for the IoT and industrial IoT: A review. Internet of Things 10, 100081. https://doi.org/10.1016/j.iot.2019.100081 (2020).
Buterin, V. et al. A next-generation smart contract and decentralized application platform. White Pap. 3, 2 (2014).
Liu, W. et al. A survey on medical information privacy protection based on blockchain. J. Zhengzhou Univ. (Nat. Sci. Ed.) 53, 1–18. https://doi.org/10.13705/j.issn.1671-6841.2020324 (2021).
van Saberhagen, N. Cryptonote v 2.0 (2013).
Sun, S.-F., Au, M. H., Liu, J. K. & Yuen, T. H. Ringct 2.0: A compact accumulator-based (linkable ring signature) protocol for blockchain cryptocurrency monero. In Computer Security–ESORICS 2017: 22nd European Symposium on Research in Computer Security, Oslo, Norway, September 11–15, 2017, Proceedings, Part II 22 456–474 https://doi.org/10.1007/978-3-319-66399-9_25 (2017).
Fuchsbauer, G., Orrù, M. & Seurin, Y. Aggregate cash systems: A cryptographic investigation of mimblewimble. In Advances in Cryptology–EUROCRYPT 2019: 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, May 19–23, 2019, Proceedings, Part I 38 657–689 https://doi.org/10.1007/978-3-030-17653-2_22 (2019).
Aitzhan, N. Z. & Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Trans. Dependable Secure Comput. 15, 840–852. https://doi.org/10.1109/TDSC.2016.2616861 (2016).
Li, L. et al. Creditcoin: A privacy-preserving blockchain-based incentive announcement network for communications of smart vehicles. IEEE Trans. Intell. Transp. Syst. 19, 2204–2220. https://doi.org/10.1109/TITS.2017.2777990 (2018).
Wang, H., Wang, Q., He, D., Li, Q. & Liu, Z. Bbars: Blockchain-based anonymous rewarding scheme for v2g networks. IEEE Internet Things J. 6, 3676–3687. https://doi.org/10.1109/JIOT.2018.2890213 (2019).
Feng, C. et al. Attribute-based encryption with parallel outsourced decryption for edge intelligent IoV. IEEE Trans. Veh. Technol. 69, 13784–13795. https://doi.org/10.1109/TVT.2020.3027568 (2020).
Yu, K., Arifuzzaman, M., Wen, Z., Zhang, D. & Sato, T. A key management scheme for secure communications of information centric advanced metering infrastructure in smart grid. IEEE Trans. Instrum. Meas. 64, 2072–2085. https://doi.org/10.1109/TIM.2015.2444238 (2015).
Gentry, C. A Fully Homomorphic Encryption Scheme (Stanford University, 2009).
Rajan, D. P., Alexis, S. J. & Gunasekaran, S. Dynamic multi-keyword based search algorithm using modified based fully homomorphic encryption and prim’s algorithm. Clust. Comput. 22, 11411–11424. https://doi.org/10.1007/s10586-017-1399-x (2019).
Ping, Y., Shufang, Z. & Jiang, Z. Block-chain privacy protection based on fully homomorphic encryption. In Proceedings of the 2019 3rd International Conference on Innovation in Artificial Intelligence 239–242 https://doi.org/10.1145/3319921.3319952 (2019).
Xu, W., Wu, L. & Yan, Y. Privacy-preserving scheme of electronic health records based on blockchain and homomorphic encryption. J. Comput. Res. Dev. 55, 2233–2243 (2018).
Souici, I., Mahamdioua, M., Jacques, S. & Ouahabi, A. Advanced genetic image encryption algorithms for intelligent transport systems. Comput. Electr. Eng. 123, 110162 (2025).
Muneeswari, G. et al. Self-diagnosis platform via IoT-based privacy preserving medical data. Meas. Sens. 25, 100636 (2023).
Yuan, Y. et al. Blockchain: The state of the art and future trends. Acta Automat. Sin. 42, 481–494. https://doi.org/10.16383/j.aas.2016.c160158 (2016).
Limbasiya, T., Sahay, S. K. & Sridharan, B. Privacy-preserving mutual authentication and key agreement scheme for multi-server healthcare system. Inf. Syst. Front. 23, 835–848 (2021).
Li, S., Wang, N. & Du, X. Privacy protection mechanism of on-demand disclosure on blockchain. Chin. J. Netw. Inf. Sec. 6, 19–29 (2020).
Chen, Y., Luo, H. & Bian, Q. A privacy protection method based on key encapsulation mechanism in medical blockchain. In 2021 IEEE 21st International Conference on Communication Technology (ICCT) 295–300 https://doi.org/10.1109/ICCT52962.2021.9658006 (2021).
Lee, J.-S., Chew, C.-J., Liu, J.-Y., Chen, Y.-C. & Tsai, K.-Y. Medical blockchain: Data sharing and privacy preserving of EHR based on smart contract. J. Inf. Sec. Appl. 65, 103117 (2022).
Zou, R., Lv, X. & Zhao, J. Spchain: Blockchain-based medical data sharing and privacy-preserving ehealth system. Inf. Process. Manag. 58, 102604 (2021).
Nakamoto, S. & Bitcoin, A. A peer-to-peer electronic cash system. Bitcoin.–URL: https://bitcoin. org/bitcoin. pdf 4, 15 (2008).
He, P., Yu, G., Zhang, Y. & Bao, Y. Survey on blockchain technology and its application prospect. Comput. Sci. 44, 1–7 (2017).
Zeng, S. et al. Survey of blockchain: Principle, progress and application. J. Commun. (2020).
Bergamo, P., D’Arco, P., De Santis, A. & Kocarev, L. Security of public-key cryptosystems based on chebyshev polynomials. IEEE Trans. Circuits Syst. I Regul. Pap. 52, 1382–1393. https://doi.org/10.1109/TCSI.2005.851701 (2005).
Zhang, L. Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons Fractals 37, 669–674. https://doi.org/10.1016/j.chaos.2006.09.047 (2008).
Fiege, U., Fiat, A. & Shamir, A. Zero knowledge proofs of identity. In Proceedings of the nineteenth annual ACM symposium on Theory of computing 210–217 https://doi.org/10.1145/28395.28419 (1987).
Lesavre, L., Varin, P., Mell, P., Davidson, M. & Shook, J. A taxonomic approach to understanding emerging blockchain identity management systems. arXiv preprint arXiv:1908.00929 (2019).
Groth, J. On the size of pairing-based non-interactive arguments. In Advances in Cryptology–EUROCRYPT 2016: 35th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Vienna, Austria, May 8–12, 2016, Proceedings, Part II 35 305–326 https://doi.org/10.1007/978-3-662-49896-5_11 (2016).
Parno, B., Howell, J., Gentry, C. & Raykova, M. Pinocchio: Nearly practical verifiable computation. Commun. ACM 59, 103–112. https://doi.org/10.1145/2856449 (2016).
Wang, D., He, D., Wang, P. & Chu, C.-H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Depend. Sec. Comput. 12, 428–442. https://doi.org/10.1109/TDSC.2014.2355850 (2014).
Lee, J., Choi, J., Oh, H. & Kim, J. Privacy-preserving identity management system. Cryptology ePrint Archive (2021).
Sonnino, A., Al-Bassam, M., Bano, S., Meiklejohn, S. & Danezis, G. Coconut: Threshold issuance selective disclosure credentials with applications to distributed ledgers. arXiv preprint arXiv:1802.07344https://doi.org/10.48550/arXiv.1802.07344 (2018).
Ra, G., Kim, T. & Lee, I. Vaim: Verifiable anonymous identity management for human-centric security and privacy in the internet of things. IEEE Access 9, 75945–75960. https://doi.org/10.1109/ACCESS.2021.3080329 (2021).
Soleymani, S. A. et al. A privacy-preserving authentication scheme for real-time medical monitoring systems. IEEE J. Biomed. Health Inform. https://doi.org/10.1109/JBHI.2022.3143207 (2022).
Yu, S. & Park, K. Sals-tmis: Secure, anonymous, and lightweight privacy-preserving scheme for IoMT-enabled TMIS environments. IEEE Access 10, 60534–60549. https://doi.org/10.1109/ACCESS.2022.3181182 (2022).
Funding
This work is funded by the Education Department of Jilin Province with Grants No. JJKH20251102KJ, the Science and Technology Department of Jilin Province with Grants Nos. 20250102045JC, 20250102055JC
Author information
Authors and Affiliations
Contributions
H.Z. conceived the study and designed the experiment. D.Z. participated in the research methodology and conducted the experiment. Z.Z. undertook the data collation and performed the formal job analysis. H.Z. and J.W. were involved in the preparation of the first draft. J.Z. and L.S. reviewed the first draft and edited the manuscript. All authors have read and agreed to the published version of the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Zhu, D., Zhou, H., Zhou, Z. et al. Quantum key-based medical privacy protection and sharing scheme on blockchain. Sci Rep 15, 27983 (2025). https://doi.org/10.1038/s41598-025-10832-2
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-10832-2