Abstract
Chaos-based encryption methods have gained popularity due to the unique properties of chaos. The performance of chaos-based encryption methods is highly impacted by the values of initial and control parameters. Therefore, this work proposes Iterative Cosine operator-based Hippopotamus Optimization (ICO-HO) to select optimal parameters for chaotic maps, which is further used to design an adaptive image encryption approach. ICO-HO algorithm improves the Hippopotamus Optimization (HO) by integrating a new phase (Phase 4) to update the position of the hippopotamus. ICO-HO updates the position of hippopotamuses using ICO and opposition-based learning, which enhances the exploration and exploitation capabilities of the HO algorithm. ICO-HO algorithm’s better performance is signified by the Friedman mean rank test applied to mean values obtained on the CEC-2017 benchmark functions. The ICO-HO algorithm is utilized to optimize the parameters of PWLCM and PWCM chaotic maps to generate a secret key in the confusion and diffusion phases of image encryption. The performance of the proposed encryption approach is evaluated on grayscale, RGB, and hyperspectral medical images of different modalities, bit depth, and sizes. Different analyses, such as visual analysis, statistical attack analysis, differential attack analysis, and quantitative analysis, have been utilized to assess the effectiveness of the proposed encryption approach. The higher NPCR and UACI values, i.e., 99.60% and 33.40%, respectively, ensure security against differential attacks. Furthermore, the proposed encryption approach is compared with five state-of-the-art encryption techniques available in the literature and six similar metaheuristic techniques using NPCR, UACI, entropy, and correlation coefficient. The proposed methods exhibit 7.9995 and 15.8124 entropy values on 8-bit and 16-bit images, respectively, which is better than all other stated methods, resulting in improved image encryption with high randomness.
Similar content being viewed by others
Introduction
Recent growth in digital information technology has led to the transmission of many sensitive and confidential images over public networks. The availability of such crucial information over public networks raises concerns for image security. Image security can be achieved using steganography, watermarking, and encryption. Image steganography hides the secret data under another image, video, or audio. In this technique, only the intended recipient and the sender are aware of the data. Watermarking is placing an invisible or visible mark inside an image or document. This technique is popular for proving the ownership of an image or document. Image encryption is the conversion of a raw image into a cipher image, which can be decrypted at the receiver end. It is a prominent technique to ensure data security, confidentiality, and integrity over the public network1,2,3.
Image encryption techniques are of two types. One is the classical encryption techniques like RSA, AES, and DES. Traditional encryption techniques have proven their significance on text data and have been widely used for web security and banking. However, due to the high computation time, such techniques are not suitable for digital images, which contain highly correlated data4,5. The other category of image encryption techniques includes the confusion and the diffusion step6. These techniques are popular for image encryption due to their low computation time and robustness against several attacks. Different authors have used various techniques in the confusion and diffusion steps. However, Chaos-based image encryption methods have gained attention due to chaos properties such as ergodicity, sensitivity to initial conditions and control parameters, random-like behavior, and unpredictability7,8. The performance of these methods depends upon the initial and the control parameters, which led to the need for optimal selection of these parameters for better performance of chaos-based encryption methods9,10.
Metaheuristic optimization techniques have been widely used for behavioral pattern guidance11, and optimal parameter selection. Metaheuristic techniques are of two major types, i.e., single objective and multi-objective metaheuristic techniques. Different single and multi-objective metaheuristic techniques like Particle Swarm Optimization (PSO)12, Bald Eagle Search (BES)13, multi-objective Brown Bear Optimization14, and multi-objective cheetah optimization15 algorithms have shown better performance in selecting the optimal parameters for different algorithms due to their high exploration and exploitation capabilities. This makes metaheuristic techniques suitable for selecting the initial and control parameters for the chaos-based image encryption methods. Various authors have used different metaheuristic techniques to select the initial and control parameters for chaos-based image encryption methods16.
Noshadian et al.17 have proposed an optimized image encryption technique based on Teacher Learning-Based Optimization (TLBO), Gravitational Search Algorithm (GSA), and logistic map. The authors have used a logistic map as an encryption key for diffusion and TLBO and GSA to optimize the map parameters. Farah et al.6 have proposed a new hybrid chaotic map for image encryption and generated a new substitution box using the Jaya algorithm. Saravanan and Sivabalakrishanan18 proposed an optimized hybrid chaotic map for image encryption. The authors have hybridized the 2DLCM and PWLCM map and performed parameter tuning using the improved whale optimization algorithm. The authors have analyzed the performance of their proposed algorithm on medical, natural, and satellite images. Kaur and Singh19 have used multiobjective evolutionary techniques to select the optimal parameters for the chaotic maps. The authors used the optimal parameters to generate a secret key, which is used to encrypt the image. They performed key, statistical, and differential analyses to analyze the performance of the encryption algorithm.
Luo et al.20 have used the hyperchaotic system and the updating process of particle swarm optimization for image encryption. They used the secure hash algorithm 256 to generate the initial keys for the hyperchaotic Lu system. The authors have analyzed the proposed algorithm using several attacks. Toktas and Erkan21 have designed a 2D fully chaotic map by utilizing the Artificial Bee Colony (ABC) for image encryption. The authors used ABC to minimize the quadruple objective function, which consists of the entropy, correlation coefficient, 0–1 test, and the Lyapunov exponent. Sameh et al.16 analyzed the impact of optimization of initial and control parameters for eight chaotic maps using nine metaheuristic optimization algorithms. Authors have computed the performance of encryption using sine, Tent, Circle, Gauss, singer, piecewise, and logistic maps without any optimization. Then, the authors used the Sine Cosine Algorithm (SCA), Moth Flame Optimization (MFO), Particle Swarm Optimization (PSO), Grey Wolf Optimization (GWO), Genetic Algorithm (GA), Dragonfly Algorithm (DA), Ant Lion Optimizer (ALO), Whale Optimization Algorithm (WOA), and Multi-Verse Optimizer (MVO) to select the optimal value of the chaotic map parameters. The authors have compared the performance to analyze the impact of each optimization algorithm.
Sharma et al.22 utilized the Self Adaptive Bald Eagle Search (SABES) optimization algorithm to optimize the chaotic parameters of PWLCM, PWCM, and tent maps. The authors used the random permutation method in the confusion phase and optimized chaotic maps in the diffusion phase with the cyclic redundancy check and circular shift method to secure patient medical information, medical signals as well as medical images. Sharma and Sharma23 have used the Harris Hawk Optimization (HHO) algorithm to optimize the Duffing, Lorenz, and Henon maps parameters. The authors have used different chaotic maps at different stages, which led to larger key spaces and resulted in a highly robust method.
Novelty and contributions of the work
As mentioned earlier, different researchers have worked on image encryption using the chaotic map with optimized parameters using metaheuristic techniques. Still, to the best of our knowledge, a high-performance image encryption algorithm for different types of images consisting of hyperspectral images, grayscale, and RGB images is not available. This work designs a reliable image encryption algorithm based on a chaotic map optimized using the Iterative Cosine Operator (ICO) based Enhanced Hippopotamus Optimization (HO) algorithm. Overall, the main contributions of the paper are as follows:
-
i.
Designed ICO-HO, i.e., ICO-based HO, by integrating a new phase (phase 4) for position update of Hippopotamus Optimization (HO) by utilizing ICO and opposition-based learning to enhance the exploration and exploitation capabilities of the algorithm.
-
ii.
The proposed ICO-HO is used to design an adaptive image encryption method based on the chaotic maps, i.e., PWCM and PWLCM, with optimized parameters.
-
iii.
Analysis of the proposed encryption method on different types of images, including medical images, grayscale images, RGB images, and hyperspectral images.
The remaining paper has been divided into four more sections. The next section, section ii, elaborates on the Hippopotamus optimization algorithm. The proposed work, which consists of the ICO-HO algorithm and the image encryption architecture, is explained in section iii. The results are analyzed and discussed in section iv. Section v concludes the work and describes the future scope.
Understanding of Hippopotamus optimization
Hippopotamus optimization (HO)24 is inspired by the hippopotamus’s social behavior and defense process. Similar to the other population-based optimization algorithms, the Hippopotamus position is a candidate solution to the problem. The hippopotamus’s initial position is generated randomly, as given in Eq. (1).
Where \(\:{HO}_{ij}\) denotes the position of ith Hippopotamus in the jth dimension. \(\:{U}_{j},\:{L}_{j}\) denotes the upper and lower bounds for jth dimension, respectively. \(\:rand\) gives the random number between 0 and 1. Equation (2) gives the overall position matrix for M hippopotamus in the N dimension.
The position update of the hippopotamus to explore the search space in the HO algorithm consists of three phases. The fitness value of each hippopotamus is computed using the fitness function \(\:fit\left(\right)\). Phase 1 exhibits the exploration using the social behavior of the hippopotamus. The hippopotamus group consists of females, calves, males, and the leader hippopotamus, as given by Eq. (3).
where \(\:{HO}^{f},\:{HO}^{c},{HO}^{m},{HO}^{L}\) represents the females, calves, males, and leader hippopotamus, respectively. Each hippopotamus is labeled to \(\:{HO}^{f}or\:{HO}^{c}or\:{HO}^{m}or\:{HO}^{L}\) based on its fitness value only. The position update for the male hippopotamus inside the water bodies is given by Eq. (4).
where \(\:{C}_{1}\) is the constant integer between 1 and 2. The position update for the female hippopotamus and calves i.e., \(\:{HO}^{fc}={H}^{f}\cup\:{H}^{c}\) is given by Eq. (5).
where \(\:i=\:\text{1,2},3,\dots\:,\left[\raisebox{1ex}{$M$}\!\left/\:\!\raisebox{-1ex}{$2$}\right.\right]\:and\:j=\:\text{1,2},3,\dots\:.N\). The \(\:{v}_{1},\:{v}_{2}\) are generated using Eq. (6) and \(\:T\) is generated using Eq. (7). \(\:{C}_{2}\)is the constant integer between 1 and 2. \(\:{RG}^{m}\) is the mean of the randomly selected hippopotamus from the available \(\:M\) hippopotamus.
where \(\:Cu{r}_{itr}\) and \(\:Ma{x}_{itr}\) is the current and maximum iteration, respectively. \(\:{\vartheta\:}_{1},\:{\vartheta\:}_{2}\:\) are the random integers between 0 and 1. The updated position of hippopotamus is accepted only if it is better than the previous fitness value given by Eqs. (8) and (9).
where \(\:fit\left(\right)\) is the fitness function. Phase 2 of the HO algorithms exhibits exploration and mimics the defense methodology of hippopotamus against predators. The position of the predator is given by the Eq. (10).
The distance of a particular hippopotamus from the predator can be found using Eq. (11).
The hippopotamus decides its defensive action based on the \(\:\overrightarrow{Dist}\) value i.e., distance from the predator. If the hippopotamus is in close vicinity of the predator i.e., \(\:fit\left({P}_{j}\right)<fit\left({HO}_{i}\right)\) then hippopotamus turns to face the predator otherwise it moves towards the predator as shown in Eq. (12).
where \(\:i=\:\left[\raisebox{1ex}{$M$}\!\left/\:\!\raisebox{-1ex}{$2$}\right.\right]+1,\left[\raisebox{1ex}{$M$}\!\left/\:\!\raisebox{-1ex}{$2$}\right.\right]+2,\cdots\:M\:and\:j=\:\text{1,2},3,\dots\:.N\)
The updated position of the hippopotamus is accepted only if its fitness value is better than the existing fitness value as given by Eq. (13).
Phase 3 of the HO algorithm exhibits exploitation through the escaping behaviour of hippopotamus from the predator. Hippopotamus generally search for the nearest water bodies to escape from the predator. This phenomenon exhibits the exploitation search in the local region as hippopotamus explore the nearest water bodies. The local upper and lower bound for the current iteration can be found using the Eq. (14).
The updated position of the hippopotamus is given by the Eq. (15).
where \(\:\alpha\:\) is given by the Eq. (16).
where \(\:\overrightarrow{randn}\) gives the random number with normal distribution. Hippopotamus will move to safer place only i.e., updated position is accepted only if its fitness value is better than the existing fitness value given by Eq. (17).
The whole process i.e., three phases of the HO algorithm repeats for each candidate solution, for the \(\:Ma{x}_{itr}\) iterations. HO algorithm is improved and utilized to optimize the parameters of the chaotic map discussed in the next section.
Proposed work
This work proposes the ICO-HO, i.e., Iterative Cosine Operator-based Hippopotamus Optimization algorithm that adds a new phase to the HO algorithm for position updates using the ICO operator and opposition-based learning. The proposed ICO-HO is further used to optimize the initial and control parameters of chaotic maps. This work also proposes a security framework that uses the optimized chaotic maps in confusion and diffusion steps. Overall work is explained in two phases. The first phase defines the proposed ICO-HO, i.e., Iterative Cosine Operator-based Hippopotamus Optimization. The second phase describes the security framework for the image encryption approach based on ICO-HO.
ICO-HO
ICO-HO improves the HO algorithm’s exploration and exploitation capabilities by using an Iterative Cosine Operator (ICO). ICO performs exploration at the initial iterations, which converts to the exploitation of search space as the iteration increases. Unlike the HO algorithm, which completes in three phases, ICO-HO completes its process in four phases. The first three phases of ICO-HO are the same as those of the HO algorithm, while the fourth phase updates the Hippopotamus position using Eq. (18).
where, as presented in the previous section \(\:{HO}^{L}\) is the position of leader hippopotamus. \(\:Cu{r}_{itr}\:,\:Ma{x}_{Itr}\) are the current and maximum iterations, respectively. Equation (18) shows that the hippopotamus explores the search space toward the leader or opposite to the leader with a 50% probability of each case. This includes opposition-based leaning, as the optima may exist opposite the leader. This exploration at initial iteration converts to exploitation as the iteration increases due to the value of ICO i.e., \(\:cos\left(\raisebox{1ex}{$\left(\pi\:\times\:Cu{r}_{itr}\right)$}\!\left/\:\!\raisebox{-1ex}{$\left(2\times\:Ma{x}_{itr}\right)$}\right.\right)\) approaching towards zero. The updated position value of the hippopotamus is accepted only if it gives a better fitness value as compared to the existing fitness value, as represented by Eq. (19).
The whole process is repeated for the \(\:Ma{x}_{Itr}\) times. The overall algorithm for ICO-HO is as follows.

A framework to secure the image is designed using the ICO-HO algorithm explained in the next subsection.
Proposed framework for image encryption approach
This framework proposed for image encryption is demonstrated in Fig. 1. This framework uses chaotic maps to encrypt images and ICO-HO to select optimum parameters for chaoctic maps. The chaotic maps are selected for the encryption due to their properties: fast processing, determinism, aperiodic behavior, pseudo-randomness, boundedness, and dynamical nature. Encryption methods based on chaotic maps are also more robust because control parameters and initial conditions highly influence these maps. The complete process is divided into two stages i.e., the parameter optimization stage and the encryption stage. A description of each stage is given in the following subsections.
Parameter optimization stage
In this stage, the proposed ICO-EHO has been used to solve the parameter optimization problem of the chaos-based encryption methods. The initial and the control parameters of chaotic maps are optimized using the ICO-EHO algorithm. In the proposed encryption method, two chaotic maps have been utilized: the Piecewise Linear Chaotic Map (PWLCM) and the Piecewise Chaotic Map (PWCM). The mathematical formulation for PWLCM and PWCM maps are presented in Eqs. (20) and (21) respectively.
where the initial condition \(\:{x}_{i}\in\:\left[\text{0,1}\right]\) and the control parameter \(\:{\eta\:}_{1}\in\:\left[\text{0,0.5}\right]\) respectively
where the PWCM map parameters \(\:{\eta\:}_{2}\) and \(\:{y}_{i}\) are defined as \(\:{\eta\:}_{2}\in\:\left[\text{0,0.5}\right]\) and \(\:{y}_{i}\in\:\left[\text{0,1}\right]\), respectively. The parameters of both chaotic maps i.e., \(\:{{{x}_{i}\:,y}_{i},\eta\:}_{1},\:{and\:\eta\:}_{2}\) are optimized using the ICO-EHO algorithm.
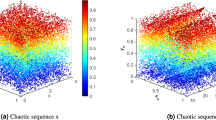
A bifurcation diagram of the chaotic maps shows the dynamic change in the behavior of the maps in terms of the control parameters. This diagram is used to analyze changes in the chaotic sequence in the whole definition of the control parameters. In Fig. 2, bifurcation diagrams of the PWLCM and PWCM maps are shown for the control parameter \(\:\eta\:ϵ[0,\:0.5]\) and initial parameter \(\:Xϵ\left[\text{0,1}\right]\).
The bifurcation diagram shows that both maps exhibit chaotic behavior across the entire range of the control and initial parameters. In Fig. 2(a), PWLCM maps show the period-doubling cascade behavior, characterized by two bifurcation divisions. In contrast, the PWCM map presented in Fig. 2(b) shows a smoother and more continuous change in the behavior as control parameters vary, reflecting its abrupt and less predictable transitions.
Lyapunov Exponent (LE) is used as a quantitative measure to analyze the perturbations in time series data. The positive value of the Lyapunov exponent reflects that neighboring trajectories are diverged with each other, showing instability within the time series. The negative values show that the neighboring trajectories converge to a single point, representing a stable trajectory. For the chaotic maps, the value of the Lyapunov exponent greater than 0 indicates that the map is reflecting the chaotic behavior. The change in the Lyapunov exponent values based on the control parameter is shown in Fig. 3.
Figure 3 indicates that the Lyapunov exponent of PWLCM maps is consistently greater than 0, indicating that the maps exhibit chaotic behavior in the entire range of control parameters. The LE values of the PWCM are higher than the PWLCM map values. Also, the PWCM map reaches its highest LE value at \(\:{\eta\:}_{2}=0.25\) after that, LE values decline but remain above 0.
Encryption stage
After optimizing the parameters of the chaotic maps, those parameters are utilized in the encryption process to enhance the security of the images. The encryption phase is divided into two phases: Confusion and diffusion phase. The confusion phase is responsible for breaking the correlation between the image pixel values by shuffling or scrambling the image pixel values. In the confusion phase, an optimized PWLCM map was used to shuffle the image pixel values. The map values have been generated with a size equal to the image size using the optimal parameters. Thereafter, the generated values of the map are sorted to give the scrambled indexes. The original image is rearranged using the scrambled index generated through sorted chaotic map values. The pseudocode of the confusion process is as follows:

After the confusion phase, the diffusion phase has been applied to the scramble image \(\:(scr\_img)\) pixels values. The optimized PWLCM and PWCM maps have been applied to modify the image pixel values in both row-wise and column-wise order. Firstly, the values of the chaotic map are generated using the optimized parameters, and then generated values are changed into discrete form using Eq. (22).
where \(\:max\left(inputvalue\right)\), is the maximum value of the input image. The pseudocode of the diffusion phase is as follows:

The analysis of the work has been done in the next section.
Results and analysis
The results and corresponding discussions have been explained in two subsections. Subsection 1, i.e., analysis of the ICO-HO algorithm, analyses the performance of the ICO-HO algorithm on CEC-2017 functions. The Friedman mean rank, analysis using qualitative metrics, and the convergence curve comparison are used for the performance analysis of ICO-HO. Subsection 2, i.e., analysis of the image encryption approach, comprises different attack analyses, key space analysis, and the comparison against different state-of-the-art techniques.
Analysis of ICO-HO algorithm
The performance of ICO-HO is compared with seven state-of-the-art algorithms namely HO24, WOA25, Arithmetic Optimization Algorithm (AOA)26, SCA27, MFO28, African Vultures Optimization Algorithm (AVOA)29, and RIME optimization algorithm (RIME)30 on CEC-2017 functions. The analysis has been done by comparing the best, average, and worst values and the Standard Deviation (SD), as shown in Table 1.
Table 1 shows the performance comparison of ICO-HO with seven state-of-the-art techniques using average, best, worst, and standard deviation values. The rank for each function is assigned for every algorithm based on the average value. It can be easily analyzed that ICO-HO achieved the first rank for twelve functions, while ICO-HO gives a competitive solution for the remaining functions. Friedman mean rank analysis is applied to analyze the performance of each algorithm, which results in 1.93, 3.68, 6.17, 7.62, 5.89, 3.82, 4.34, and 2.51 values for ICO-HO, HO, WOA, AOA, SCA, MFO, AVOA, RIME algorithms respectively. The p-value for the Friedman mean rank analysis is 3.56E-24, which is less than 0.05, resulting in the rejection of the NULL hypothesis, i.e., there is a significant difference between the performance of algorithms. On the basis of the mean value obtained, ICO-HO has obtained the first position, indicating better performance than the other existing state-of-the-art algorithms. ICO_HO has shown better performance due to its high and balanced exploration and exploitation capabilities. RIME and HO algorithms have obtained the second and third positions, respectively.
Convergence comparison of ICO-HO with HO algorithm
The comparison of the convergence curve for ICO-HO with the HO algorithm is shown on the randomly selected CEC-2017 functions, i.e., F5, F6, F8, F16, F20, and F26 in Fig. 4. The x-axis denotes the iterations, while the y-axis denotes the fitness value. A comparison was made with the 1000 iterations. The better convergence is exhibited by the ICO-HO as compared to the HO algorithm for all F5, F6, F8, F16, F20, and F26 functions. The better convergence is due to the newly added phase 4, which includes the position update based on ICO and opposition-based learning. The better exploration capabilities due to ICO at initial iterations in the ICO-HO show faster convergence by ICO-HO than the HO algorithm.
Analysis of proposed image encryption approach
The proposed encryption approach is tested on different types of medical images, including grayscale, RGB, and hyperspectral images. The medical images used for experimentation vary in size, file format, and bit depth, including both 8-bit and 16-bit images. The performance analysis has been done using visual analysis, statistical attack analysis (histogram, correlation analysis, variance analysis, chi-square analysis), differential attack analysis (NPCR and UACI), qualitative analysis (information entropy, MSE, and PSNR), key space and key sensitivity analysis. The visual analysis has been utilized to show the visual difference between the original, encrypted, and decrypted medical images31. Table 2 depicts the visual analysis of original, encrypted, and decrypted medical images.
The encrypted images in Table 2 clearly show that the visual information of the original images is completely hidden in the encrypted images generated using the propounded encryption method. This proves that the proposed encryption method effectively hides all the visual data of the images. Also, the visual appearance of the decrypted image is identical to the original image, indicating that the decrypted image maintains the same visual depiction as the original.
Statistical attack analysis
The presence of the relationship between the pixel values of the encrypted image, obtained using the encryption approach is analyzed through statistical methods. This analysis uses techniques such as histogram, variance, chi-square, and correlation coefficient measureo compute the pixel relationships in the encrypted images39. Histogram plots are used to visually analyze the uniformity of pixel values in the encrypted images. The uniformly distributed histogram of the encrypted images indicates that attackers cannot infer any information about the original image. Histogram plots of the original, encrypted, and decrypted images are depicted in Fig. 5 to analyze the uniformity of the encrypted images.
From Fig. 5, it can be observed that the pixel values of the encrypted images are uniformly distributed, in contrast to the pixel distribution of the original images. Moreover, the histograms of the original and decrypted images are visually identical, indicating a similarity in the pixel distributions of the decrypted images. The variance and chi-square techniques are used to calculate the uniformity analysis of the encrypted images by analyzing the pixel distribution of the histogram40. The mathematical formulation of variance and chi-square is given by Eq. (23) and Eq. (24), respectively.
where \(\:x\) be the vector of histogram values and \(\:x=\left\{{x}_{1},{x}_{2},\dots\:,{x}_{256}\right\}\), \(\:{x}_{i}\) and \(\:{x}_{j}\) represent the number of pixels with gray values equal to \(\:i\) and \(\:j\), respectively.
where \(\:e{x}_{i}\) is the expected frequency in a uniform distribution which is calculated as \(\:e{x}_{i}=\frac{width\times\:length}{256}\). The \(\:o{b}_{i}\) is the observed occurrence frequency of each gray level \(\:(0-255)\) in the histogram of the encrypted image and \(\:M\) represents the number of gray levels.
Table 3 shows the variance and chi-square values of the original as well as encrypted images. The variance of the encrypted images must remain below 5000, and the chi-square value should not exceed 29340.
Table 3 indicates that the encrypted images’ variance and chi-square values meet the required thresholds of 5000 and 293, respectively. The correlation plot analysis is used to visualize the relationship among the encrypted images’ pixel values. In Fig. 6, the correlation plots of the encrypted and original images are shown to depict pixel relationships horizontally, vertically, and diagonally.
The correlation plots of encrypted images are scattered and squared-shaped, showing no negative relationship, which ensures security from information leakage. The correlation coefficients of the original and encrypted images are listed in Table 4.
The correlation coefficient values of the encrypted images, which are close to zero or negative, indicate that the pixel values in the encrypted images have no relationship with neighboring pixels.
Differential attack analysis
A number of Pixel Change Rate (NPCR) and Unified Averaged Changed Intensity (UACI) methods are used to analyze the differential attack resistance of the encryption methods41. The NPCR and UACI values are calculated by generating two encrypted images, one from the original image and the other by changing a pixel value in the original image. The mathematical formulation of NPCR and UACI is presented by Eqs. (25) and (27) respectively.
where \(\:D\left(i,j\right)\) is given by Eq. (26)
\(\:{enc}_{1}\) and \(\:{enc}_{2}\) are two encrypted images, where \(\:{enc}_{1}\) is generated before and \(\:{enc}_{2\:}\)is generated after a one-pixel change in the original images. \(\:T\:\)denote the total number of pixels in each encrypted image.
where \(\:T\) is the total number of pixels and \(\:F\) is the largest supported pixel value of an image of an encrypted image. \(\:{enc}_{1}\:\)and \(\:{enc}_{2}\) are the encrypted images generated before and after the one-pixel change in the original image. For NPCR and UACI to be considered acceptable, their values should exceed 99.60% and 33.40%, respectively42. The computed values of the UACI and NPCR for the encrypted images are given in Table 5.
The UACI and NPCR values of the encrypted images show that values are within the desired range and successfully resist differential attacks.
Quantitative analysis
The information entropy, Peak Signal-to-Noise Ratio (PSNR), and Mean Square Error (MSE) metrics are used to quantify the encrypted images generated using the encryption methods43. The information entropy is used to measure the degree of unpredictability present in the information content of the encrypted images. For an encrypted image to exhibit pixel randomness, the entropy value should be close to 8 or 16. The MSE and PSNR are used to show discrepancies between the original and encrypted images to measure the image quality. An encryption algorithm having small PSNR values and high MSE values shows the presence of noise in the encrypted image. Table 6 shows the computed results of the metrics for the images.
Table 6 reveals that the proposed encryption approach is extremely efficient due to the small PSNR values and large MSE values. This illustrates the robustness, safety, and efficacy of the propounded encryption approach.
Key space analysis
The key space analysis is used to check the resistance of the encryption approach against brute-force attacks. The key space of the encrypted approach should be greater than the required \(\:{2}^{128}\:\)bits44. The key space of the propounded approach is \(\:{10}^{16\times\:6}={10}^{96}\), as it uses six secret keys, each with a precision of \(\:{10}^{16}\). Therefore, the proposed encryption approach is secure from brute force attacks.
Comparison with other state-of-the-art techniques
The performance effectiveness of the ICO-HO algorithm utilized in the proposed encryption method has been evaluated through comparisons with other state-of-the-art optimization algorithms, i.e., PSO12, BES13, Cheetah Optimization (CO)45, Self-adaptive Bald Eagle Search (SABES) optimization22, Brown Bear Optimization (BBO)46, and Hippopotamus optimization (HO)24algorithms. In this evaluation process, only parameter selection of the chaotic maps was made using different optimization algorithms. Table 7 presents the achieved values of the performance metrics (correlation coefficient, entropy, NPCR, UACI) for the DICOM lung CT scan 16-bit images47.
Table 7 shows that the proposed encryption method based on ICO-HO achieved the highest entropy value, which ensures randomness in the pixel values of the encrypted image. Also, all correlation coefficient values, i.e., H, V, and D are lower compared to the other comparative methods, indicating a weak relationship among the pixel values of the encrypted image. The efficacy of the proposed encryption approach is analyzed by comparing the results with existing encryption methods for DICOM lung CT scan images. Entropy, UACI, NPCR, and correlation coefficient metrics are used for the comparison, given in Table 8.
The proposed encryption method achieves competitive results across key performance metrics. It exhibits low correlation coefficients, ensuring weak pixel correlation among the encrypted pixel values. In the propounded approach, the entropy values are 7.9995 for 8-bit images and 15.8124 for 16-bit images, which are close to their respective ideals. Also, NPCR values were attained using the proposed encryption approach, which showed high sensitivity to pixel changes, while UACI values indicated strong encryption performance. The proposed technique maintains high entropy levels, ensuring that the encrypted images are nearly indistinguishable from random noise, thus providing robust protection against potential attacks and making it comparable to other state-of-the-art techniques.
Conclusions and future scopes
This paper proposes an adaptive encryption approach based on the optimized chaotic maps. The initial and control parameters of the chaotic maps are optimally selected utilizing the proposed Iterative Cosine Operator-based Hippopotamus Optimization (ICO-HO) algorithm. The efficacy of the ICO-HO algorithm is compared with seven state-of-the-art algorithms namely Hippopotamus Optimization (HO), Whale Optimization Algorithm (WOA), Arithmetic Optimization Algorithm (AOA), Moth Flame Optimization (MFO), Sine Cosine Algorithm (SCA), African Vultures Optimization Algorithm (AVOA), and RIME algorithm (RIME) on CEC-2017 functions. Friedman mean rank analysis gives 1.93, 3.68, 6.17, 7.62, 3.82, 5.89, 4.34, and 2.51 values for ICO-HO, HO, WOA, AOA, MFO, SCA, AVOA, RIME algorithms respectively with p-value 3.56E-24. This shows better performance of the ICO-HO algorithm than other comparative algorithms. The proposed encryption approach is applied to medical images of different modalities and sizes. The effectiveness of the proposed encryption approach is evaluated in RGB, grayscale, and hyperspectral medical images. The effectiveness of the adaptive encryption approach is analyzed using various performance metrics such as visual, histogram, chi-square, variance, NPCR, UACI, correlation coefficient, entropy, PSNR, and MSE. The histogram, chi-square, variance, and correlation coefficient analyses demonstrate the uniform distribution of the pixel values of encrypted images and show the security from the statistical attacks. The UACI and NPCR values for the encrypted images generated using the encryption approach are greater than 33.40% and 99.60%, respectively, which ensure security against differential attacks. The entropy values of 8-bit and 16-bit images are 7.9995 and 15.8124, respectively, which are closer to 8 and 16, which show the randomness of pixel values. Additionally, the propounded encryption approach is compared to the existing encrypted techniques, showing more randomness in the encrypted image than the other encrypted techniques. This work is being extended by designing new hybrid chaotic maps. The proposed ICO-HO algorithm can be applied to other optimization problems like band selection in hyperspectral images.
Data availability
All data used for analysis in this research is publically available on the National Institution of Health (NIH) websites (https://openi.nlm.nih.gov/gridquery? it=xg), Cancer imaging archive (https:// wiki.cancerimagingarchive.net/display/Public/CBIS-DDSM), Kaggle (https://www.kaggle. com/), Visual health IT (https://www.visus.com/en/downloads/jivex-dicom-viewer.html), Grand Challenge (https://drive.grand-challenge.org/DRIVE/), and University Medical Center Groningen (UMCG) website (http://www.cs.rug.nl/~imagi ng/databases/melanoma_naevi/).
References
Kumar, S., Panna, B. & Jha, R. K. Medical image encryption using fractional discrete cosine transform with chaotic function. Med. Biol. Eng. Comput. 57(11), 2517–2533. https://doi.org/10.1007/s11517-019-02037-3 (2019).
Belazi, A., Talha, M., Kharbech, S. & Xiang, W. Novel medical image encryption scheme based on chaos and DNA encoding. IEEE Access 7, 36667–36681. https://doi.org/10.1109/ACCESS.2019.2906292 (2019).
Sharma, S. R., Singh, B. & Kaur, M. A hybrid encryption model for the hyperspectral images: application to hyperspectral medical images. Multimed. Tools Appl. 83(4), 11717–11743. https://doi.org/10.1007/s11042-023-15587-4 (2024).
Bi, B., Huang, D., Mi, B., Deng, Z. & Pan, H. Efficient LBS security-preserving based on NTRU oblivious transfer. Wirel. Pers. Commun. 108(4), 2663–2674. https://doi.org/10.1007/s11277-019-06544-2 (2019).
Xu, Y., Ding, L., He, P., Lu, Z. & Zhang, J. META: a memory-efficient tri-stage polynomial multiplication accelerator using 2D coupled-BFUs. IEEE Trans. Circuits Syst. I Regul. Pap. https://doi.org/10.1109/TCSI.2024.3461736 (2024).
Farah, M. A. B., Farah, A. & Farah, T. An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 99(4), 3041–3064. https://doi.org/10.1007/s11071-019-05413-8 (2020).
Salleh, M., Ibrahim, S. & Isnin, I. F. Image encryption algorithm based on chaotic mapping. J. Teknol. 39(5), 1–12. https://doi.org/10.11113/jt.v39.458 (2003).
Nkandeu, Y. P. K. & Tiedeu, A. An image encryption algorithm based on substitution technique and chaos mixing. Multimed. Tools Appl. 78(8), 10013–10034. https://doi.org/10.1007/s11042-018-6612-2 (2019).
Qin, Q., Liang, Z., Liu, S. & Zhou, C. A self-adaptive image encryption scheme based on chaos and gravitation model. IEEE Access 11, 47873–47883. https://doi.org/10.1109/ACCESS.2023.3267485 (2023).
Lan, R., He, J., Wang, S., Liu, Y. & Luo, X. A parameter-selection-based chaotic system. IEEE Trans. Circuits Syst. II Express Briefs 66(3), 492–496. https://doi.org/10.1109/TCSII.2018.2865255 (2019).
Jin, W. et al. Enhanced UAV pursuit-evasion using boids modelling: a synergistic integration of bird swarm intelligence and DRL. Comput. Mater. Continua 80(3), 3523–3553. https://doi.org/10.32604/cmc.2024.055125 (2024).
Kennedy, J., Eberhart, R. & bls gov. Particle Swarm Optimization. In IEEE Int Conf Neural Networks. 1942–1948 (1995).
Alsattar, H. A., Zaidan, A. A. & Zaidan, B. B. Novel meta-heuristic bald eagle search optimisation algorithm. Artif. Intell. Rev. 53(3), 2237–2264. https://doi.org/10.1007/s10462-019-09732-5 (2020).
Mehta, P., Kumar, S., Tejani, G. G. & Khishe, M. MOBBO: a multiobjective brown bear optimization algorithm for solving constrained structural optimization problems. J. Optim. https://doi.org/10.1155/2024/5546940 (2024).
Kumar, S. et al. Optimization of truss structures using multi-objective cheetah optimizer. Mech. Based Des. Struct. Mach. https://doi.org/10.1080/15397734.2024.2389109 (2024).
Sameh, S. M., Moustafa, H. E. D., AbdelHay, E. H. & Ata, M. M. An effective chaotic maps image encryption based on metaheuristic optimizers. J. Supercomput. 80(1), 141–201. https://doi.org/10.1007/s11227-023-05413-x (2024).
Noshadian, S., Ebrahimzade, A. & Kazemitabar, S. J. Optimizing chaos based image encryption. Multimed. Tools Appl. 77(19), 25569–25590. https://doi.org/10.1007/s11042-018-5807-x (2018).
Saravanan, S. & Sivabalakrishnan, M. A hybrid chaotic map with coefficient improved whale optimization-based parameter tuning for enhanced image encryption. Soft Comput. 25(7), 5299–5322. https://doi.org/10.1007/s00500-020-05528-w (2021).
Kaur, M. & Singh, D. Multiobjective evolutionary optimization techniques based hyperchaotic map and their applications in image encryption. Multidimens. Syst. Signal. Process. 32(1), 281–301. https://doi.org/10.1007/s11045-020-00739-8 (2021).
Luo, Y., Ouyang, X., Liu, J., Cao, L. & Zou, Y. An image encryption scheme based on particle swarm optimization algorithm and hyperchaotic system. Soft. Comput. 26(11), 5409–5435. https://doi.org/10.1007/s00500-021-06554-y (2022).
Toktas, A. & Erkan, U. 2D fully chaotic map for image encryption constructed through a quadruple-objective optimization via artificial bee colony algorithm. Neural Comput. Appl. 34(6), 4295–4319. https://doi.org/10.1007/s00521-021-06552-z (2022).
Sharma, S. R., Singh, B. & Kaur, M. Improvement of medical data security using SABES optimization algorithm. J. Supercomput. 80(9), 12929–12965. https://doi.org/10.1007/s11227-024-05937-w (2024).
Sharma, V. K. & Sharma, J. B. Harris Hawk optimization driven adaptive image encryption integrating Hilbert vibrational decomposition and chaos. Appl. Soft. Comput. 164, 112016. https://doi.org/10.1016/J.ASOC.2024.112016 (2024).
Amiri, M. H., Mehrabi Hashjin, N., Montazeri, M., Mirjalili, S. & Khodadadi, N. Hippopotamus optimization algorithm: a novel nature-inspired optimization algorithm. Sci. Rep. https://doi.org/10.1038/s41598-024-54910-3 (2024).
Mirjalili, S. & Lewis, A. The Whale Optimization Algorithm. Adv. Eng. Softw. 95, 51–67. https://doi.org/10.1016/j.advengsoft.2016.01.008 (2016).
Abualigah, L., Diabat, A., Mirjalili, S., AbdElaziz, M. & Gandomi, A. H. The arithmetic optimization algorithm. Comput. Methods Appl. Mech. Eng. https://doi.org/10.1016/j.cma.2020.113609 (2021).
Mirjalili, S. SCA: a sine cosine algorithm for solving optimization problems. Knowl. Based Syst. 96, 120–133. https://doi.org/10.1016/j.knosys.2015.12.022 (2016).
Mirjalili, S. Moth-flame optimization algorithm: A novel nature-inspired heuristic paradigm. Knowl. Based Syst. 89, 228–249. https://doi.org/10.1016/j.knosys.2015.07.006 (2015).
Abdollahzadeh, B., Gharehchopogh, F. S. & Mirjalili, S. African vultures optimization algorithm: A new nature-inspired metaheuristic algorithm for global optimization problems. Comput. Ind. Eng. 158, 107408. https://doi.org/10.1016/j.cie.2021.107408 (2021).
Su, H. et al. RIME: A physics-based optimization. Neurocomputing 532, 183–214. https://doi.org/10.1016/j.neucom.2023.02.010 (2023).
Ramesh, R. K. et al. A novel and secure fake-modulus based rabin-ӡ cryptosystem. Cryptography 7(3), 44. https://doi.org/10.3390/cryptography7030044 (2023).
Cheng, J. et al. Enhanced performance of brain tumor classification via tumor region augmentation and partition. PLoS ONE https://doi.org/10.1371/journal.pone.0140381 (2015).
Cheng, J. et al. Retrieval of brain tumors by adaptive spatial pooling and fisher vector representation. PLoS ONE https://doi.org/10.1371/journal.pone.0157112 (2016).
Al-Dhabyani, W., Gomaa, M., Khaled, H. & Fahmy, A. Dataset of breast ultrasound images. Data Brief. https://doi.org/10.1016/j.dib.2019.104863 (2020).
Diagnostic Image Analysis Group at Radboud University Medical Center. DRIVE: Digital Retinal Images for Vessel Extraction https://drive.grand-challenge.org/DRIVE/.
Giotis, I. et al. MED-NODE: A computer-assisted melanoma diagnosis system using non-dermoscopic images. Expert Syst. Appl. 42(19), 6578–6585. https://doi.org/10.1016/j.eswa.2015.04.034 (2015).
Leon, R. et al. Hyperspectral imaging benchmark based on machine learning for intraoperative brain tumour detection. NPJ Precis. Oncol. https://doi.org/10.1038/s41698-023-00475-9 (2023).
Zhang, Q. et al. A multidimensional choledoch database and benchmarks for cholangiocarcinoma diagnosis. IEEE Access 7, 149414–149421. https://doi.org/10.1109/ACCESS.2019.2947470 (2019).
Ravichandran, D., Praveenkumar, P., Balaguru Rayappan, J. B. & Amirtharajan, R. Chaos based crossover and mutation for securing DICOM image. Comput. Biol. Med. 72, 170–184. https://doi.org/10.1016/j.compbiomed.2016.03.020 (2016).
Ramakrishnan, B. et al. Image encryption with a Josephson junction model embedded in FPGA. Multimed. Tools Appl. 81(17), 23819–23843. https://doi.org/10.1007/s11042-022-12400-6 (2022).
Wu, Y., Noonan, J. P. & Agaian, S. NPCR and UACI randomness tests for image encryption. Cyber J. Multidiscip. J. Sci. Technol. J. Sel. Areas Telecommun. 2(1), 31–38 (2011).
Amina, S. & Mohamed, F. K. An efficient and secure chaotic cipher algorithm for image content preservation. Commun. Nonlinear Sci. Numer. Simul. 60, 12–32. https://doi.org/10.1016/j.cnsns.2017.12.017 (2018).
Kumari, M., Gupta, S. & Sardana, P. A survey of image encryption algorithms. 3D Res. 8(4), 37. https://doi.org/10.1007/s13319-017-0148-5 (2017).
Subashanthini, S. & Pounambal, M. Three stage hybrid encryption of cloud data with penta-layer security for online business users. Inf. Syst. e-Business Manag. 18(3), 379–404. https://doi.org/10.1007/s10257-019-00419-6 (2020).
Akbari, M. A., Zare, M., Azizipanah-abarghooee, R., Mirjalili, S. & Deriche, M. The cheetah optimizer: a nature-inspired metaheuristic algorithm for large-scale optimization problems. Sci. Rep. https://doi.org/10.1038/s41598-022-14338-z (2022).
Prakash, T., Singh, P. P., Singh, V. P. & Singh, N. A novel brown-bear optimization algorithm for solving economic dispatch problem. In Advanced Control and Optimization Paradigms for Energy System Operation and Management, 137–164. https://doi.org/10.1201/9781003337003-6 (River Publishers, 2022).
VISUS Health IT GmbH. JiveX DICOM Viewer. https://www.visus.com/en/downloads/jivex-dicom-viewer.html.
Ravichandran, D. et al. An efficient medical image encryption using hybrid DNA computing and chaos in transform domain. Med. Biol. Eng. Comput. 59(3), 589–605. https://doi.org/10.1007/s11517-021-02328-8 (2021).
Meng, X., Li, J., Di, X., Sheng, Y. & Jiang, D. An encryption algorithm for region of interest in medical DICOM based on one-dimensional eλ-cos-cot map. Entropy 24(7), 901. https://doi.org/10.3390/e24070901 (2022).
Muthu, J. S. & Murali, P. A novel DICOM image encryption with JSMP map. Optik 251, 168416. https://doi.org/10.1016/J.IJLEO.2021.168416 (2022).
Wu, J., Zhang, J., Liu, D. & Wang, X. A multiple-medical-image encryption method based on SHA-256 and DNA encoding. Entropy 25(6), 898. https://doi.org/10.3390/e25060898 (2023).
Naguib, A., El-Shafa, W. & Shokair, M. DICOM medical image security with DNA-non-uniform cellular automata and JSMP map based encryption technique. Menoufia J. Electron. Eng. Res. 33(1), 1–16. https://doi.org/10.21608/mjeer.2023.246301.1085 (2024).
Funding
Open access funding provided by Óbuda University.
Author information
Authors and Affiliations
Contributions
Sachin Minocha: Conceptualization, Methodology, Validation, Writing Original Draft. Suvita Rani Sharma: Conceptualization, Methodology, Validation, Writing Original Draft. Birmohan Singh: Conceptualization, Writing Review and Editing, Supervision. Amir H. Gandomi: Writing Review and Editing, Supervision, Project Administration.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Minocha, S., Sharma, S.R., Singh, B. et al. Adaptive image encryption approach using an enhanced swarm intelligence algorithm. Sci Rep 15, 9476 (2025). https://doi.org/10.1038/s41598-025-86569-9
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-86569-9