Abstract
In intrusion detection, imbalanced datasets often degrade the accuracy of certain detections, potentially allowing malicious traffic to remain undetected and leading to significant losses. The multi-layer perceptron (MLP) offers distinct advantages for intrusion detection, as attack patterns often follow complex, nonlinear relationships. These patterns can be effectively captured through MLP’s multiple nonlinear transformations, such as ReLU and Sigmoid activation functions, which are especially beneficial for intrusion detection. Additionally, MLP exhibits low resource consumption, making it suitable for resource-constrained environments. However, MLP often struggles to accurately classify minority classes in imbalanced datasets due to its limited feature extraction capabilities. In contrast, convolutional neural networks (CNNs), particularly AlexNet’s small convolutional filters, offer more precise feature extraction for detailed dataset features. Therefore, this study integrates AlexNet’s feature extraction module with MLP and incorporates the SKNet attention mechanism to improve the recognition of minority classes. Experimental results show that our enhanced MLP algorithm outperforms the standard MLP across all seven proposed classification tasks. Specifically, the F1 scores for BotnetARES and PortScan show significant improvements of 18.93% and 26.57%, respectively, validating the efficacy of the algorithmic enhancements.
Similar content being viewed by others
Introduction
Information has become a crucial strategic resource for social development. Social informatization is a central trend in today’s global development, and information security plays an essential role in the information society, directly impacting national security, business operations, and daily life. Intruders can exploit IoT networks to launch malicious attacks, such as DoS (Denial of Service) or DDoS (Distributed Denial of Service), making online services temporarily or permanently inaccessible, thereby disrupting normal business operations1. Cyberattacks on critical infrastructure can cause large-scale social disruption and even pose a threat to public safety. As computer networks grow larger and more complex, effective security measures are becoming increasingly crucial. To address this issue, a more comprehensive intrusion detection system is required, making the application of deep learning techniques in intrusion detection a key focus of related research2.
Intrusion detection systems are mainly categorized into signature-based and behavior-based approaches. Signature-based intrusion detection systems rely on attack signatures from known threats and require regular updates to maintain effectiveness. Broad signatures may trigger false alarms, while overly specific signatures may miss similar attacks. Deep learning models facilitate automated feature extraction, improving the accuracy of target identification2. Integrating deep learning into intrusion detection systems significantly enhances both accuracy and robustness3.
In 2015, Alom et al.4 proposed using a deep belief network (DBN), consisting of stacked restricted Boltzmann machines, for intrusion detection. This method automatically learns complex features from network traffic, demonstrating the potential of DBNs to process high-dimensional data and enhance detection performance. In 2017, Yin et al.5 introduced a novel network architecture and training strategy to optimize recurrent neural networks (RNNs) for intrusion detection tasks. In 2019, M. Roopak et al.6 proposed a deep learning-based security framework utilizing convolutional and recurrent neural networks to capture spatio-temporal features in network traffic, enhancing scalability and robustness in intrusion detection models. Shone et al.7 proposed a deep learning-based intrusion detection method combining convolutional neural networks (CNNs) and long short-term memory (LSTM) networks. Their comprehensive performance evaluation highlighted the method’s potential in analyzing complex network traffic. In 2022, Abdallah et al.8 reviewed commonly used supervised learning algorithms, such as decision trees, support vector machines, random forests, and neural networks. They discussed how to select the appropriate algorithm, emphasizing the capabilities of automatic feature learning and complex pattern recognition, and explored the future integration of supervised learning techniques to enhance intrusion detection.
The Multilayer Perceptron (MLP) is a feed-forward neural network model with significant expressive power and a broad range of applications. It is capable of learning and representing complex nonlinear relationships and is widely used in classification, regression, and other machine learning tasks9. In intrusion detection systems, the problem of complex and nonlinear network traffic data is common, and MLP offers several advantages over traditional attack detection classifiers, particularly in handling nonlinear data. Traditional classifiers are linear by nature10, and such linear structures often fail to capture the intricate relationships in high-dimensional data, as is the case with network traffic. In contrast, MLPs generally exhibit superior capabilities in processing high-dimensional data, a key advantage in analyzing network traffic in intrusion detection systems. The key design of the intrusion detection system involves extracting multiple features from network traffic, which enhances the performance of the MLP relative to linear classifiers.
To overcome the limitations identified in previous research, we propose the MLP-AS model. By leveraging MLP’s multilayer nonlinear transformations, complex nonlinear relationships within input data can be captured, which is especially crucial in intrusion detection tasks, where attack patterns are typically nonlinear. MLP also has low resource consumption, which is crucial for maintaining accuracy in resource-constrained environments, contributing to its continued widespread use. However, MLP still has limitations in accurately detecting minority classes. To overcome these limitations, our proposed MLP-AS model incorporates AlexNet’s feature extraction module and integrates the SKNest attention mechanism, improving MLP’s ability to recognize features of minority classes and thereby enhancing detection accuracy for these classes.The primary contributions of this study are as follows:
-
In this study, we incorporate AlexNet’s feature extraction module into the MLP and modify its structure and parameters to better adapt to smaller datasets in intrusion detection. This adjustment enables the capture of smaller receptive fields in the early layers to extract detailed features, ensuring that minority classes are not overlooked.
-
To better capture minority class features, we introduce SKNets, which utilizes SK convolution to dynamically select the convolutional kernel size. This allows the network to automatically adjust its receptive field based on image content, capturing multi-scale information more effectively. By employing an attention mechanism to weigh and combine outputs from different kernel sizes, the network focuses on more critical features, improving feature representation efficiency across varying data amounts.
These enhancements enable the model to leverage CNN’s feature extraction strengths while selectively emphasizing key features through the attention mechanism. This combination provides a distinct advantage in learning and recognizing minority classes in large datasets, improving detection accuracy and reducing computational resource demands.
The remainder of the paper is structured as follows: “Related work” section reviews the development and research of intrusion detection systems and MLP; “Methods” section presents an improved approach to MLP-based intrusion detection systems; “Experimental analysis” section discusses the experimental design and analyzes the results; and “Result and discussion” section concludes the paper and outlines future research directions.
Related work
In 1980, James Anderson11 conducted the first study on computer security threat monitoring and auditing, exploring methods for identifying and responding to these threats, marking the introduction of the concept of intrusion detection. As intrusion detection evolved, models and systems for detecting intrusions were progressively developed. In 1987, Dorothy E. Denning12 published a paper proposing a comprehensive theoretical model of intrusion detection, which laid the foundation for rule-based detection methods. Heberlein et al.’s13 1990 paper described a distributed detection system, whose design philosophy and methodology profoundly influenced later distributed security monitoring systems. In 1996, Stephanie Forrest et al.14 introduced the concept of detecting intrusions by monitoring system behavior, one of the early works on behavior-based detection methods. In 1997, Philip A. Porras et al.15 presented the EMERALD framework, an early multi-layered intrusion detection system. The framework demonstrated the potential of multi-layered intrusion detection systems and laid the foundation for subsequent research and development. In 1999, Martin Roesch16 introduced Snort, an open-source, lightweight network intrusion detection system. The paper described how to use signature detection to build an effective intrusion detection system designed to analyze network traffic and detect specific attack patterns.
Traditional Intrusion Detection Systems (IDS) typically rely on rule-based or pattern-matching techniques, which makes it difficult to adapt to novel attack patterns and rapidly evolving attack strategies. A. Bivens, C. Palagiri, et al.17 employed an MLP-based core model and developed a feature selection method that combines multiple signature types to improve detection accuracy and comprehensiveness. Experimental results on the KDD1999 dataset show that this approach outperforms traditional signature-based methods across several performance metrics; however, it struggles with accurately classifying different attack types. Moradi and Zulkernine18 explored a neural network-based intrusion detection system for attack classification, aiming to address key challenges in network security: detecting intrusions and classifying attack types to enhance system security and responsiveness. Neural networks enhance detection adaptability under high data traffic and complex attack conditions, achieving high accuracy in both intrusion detection and attack categorization, especially for known attack types. However, high false positive rates remain a significant issue, leading to the potential misclassification of malicious traffic as normal.
Roy et al.19 proposed a deep learning-based artificial neural network (ANN) approach for intrusion detection, utilizing deep learning’s feature extraction and pattern recognition capabilities to improve system accuracy and efficiency. Instead of relying on manual feature engineering, this approach employs a data-driven deep ANN to automatically extract features, minimizing human intervention and adapting to dynamic network environments. Experimental results show that the method not only improves detection accuracy but also effectively reduces false alarms, although further improvements in generalization are necessary.
Shone et al.17 proposed a deep learning-based intrusion detection method combining unsupervised autoencoders with supervised Deep Neural Networks (DNNs) to enable end-to-end processing from raw data to detection results, minimizing reliance on domain knowledge and improving model automation and adaptability. Furthermore, traditional IDSs suffer from high false alarm rates and performance degradation with large-scale network data. Kim et al.20 proposed a CNN-based intrusion detection method that leverages CNNs’ feature extraction strengths from computer vision for network traffic analysis. This model enables automatic feature learning, reducing reliance on manual features and significantly improving both precision and recall. Farahnakian and Heikkonen21 introduced a Deep Auto-Encoder (DAE)-based intrusion detection method that extracts latent network traffic features via unsupervised learning, improving detection accuracy and the generalization of anomalous behavior detection.
MLP has been widely utilized in intrusion detection systems due to its excellent performance in handling nonlinear and complex relationships. Hajimirzaei et al.22 combined an artificial bee colony optimization algorithm with neural networks for anomalous behavior identification in cloud environments, which can adapt well to the high dynamics and complexity of these environments. Shettar et al.23 developed a hybrid modeling framework combining MLPs and CNNs, which enhances the expressive power of the model and excels in handling complex and dynamically changing data. Zhang et al.24 proposed a GAN-based intrusion detection model that includes an MLP encoder, which significantly enhances feature extraction capability and improves both training efficiency and model expressiveness. Ali et al.25 in 2024 proposed a BERT-based approach using MLP for classification, which significantly improves accuracy in handling complex and high-dimensional data.
These studies show that current models demonstrate average performance in detecting minority classes and still require improvements in computational efficiency26. In this study, we applied MLP to capture potential nonlinear patterns, incorporating AlexNet’s feature extraction capabilities from computer vision to automatically extract complex features from large datasets, thereby improving intrusion detection accuracy and robustness. The addition of SKNet further enhances our model’s computational efficiency.
Methods
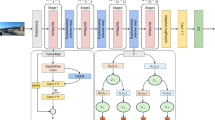
To enhance minority class classification accuracy, we integrate AlexNet’s feature extraction module into the MLP framework. AlexNet’s smaller convolutional kernels enable the model to capture finer details, ensuring that minority class features are detected during the early processing stages. Additionally, the SKNet attention mechanism dynamically adjusts the receptive field according to input characteristics, enabling the network to capture multi-scale information more effectively. This approach improves feature recognition, enhancing the model’s overall expressiveness and generalization. The enhanced algorithm structure is illustrated in Fig. 1:
In a paper published in 2017, Amato et al.27 explored the application of multilayer perceptron (MLP) models for classification and intrusion detection. Their study compares MLP performance with that of traditional machine learning algorithms, such as Decision Trees, Naive Bayes, and Support Vector Machines. The study concludes that MLP outperforms these traditional algorithms in terms of intrusion detection accuracy. The paper also highlights MLP’s advantage in capturing complex patterns within high-dimensional data, enhancing its effectiveness in intrusion detection tasks. This supports the feasibility of enhancing our selected MLP algorithm to improve detection accuracy within intrusion detection systems.
The improved model begins by transforming input dimensions, duplicating channels, and applying interpolation to meet dataset requirements. The adjusted dataset is then processed by AlexNet for feature extraction. To enhance accuracy for minority classes, refined feature extraction is essential; therefore, we preserve the small convolutional kernel structure from AlexNet. The convolution operation is expressed by the following formula 1:
\(F\) represents the input feature map. \(K\) is the convolution kernel,\((x,y)\) is the position on the output feature map, and \(*\) is the convolution operation.K the convolution kernel.
In this study, we reduced the initial five convolutional layers to three, each utilizing a 3x3 convolutional kernel, and adjusted the corresponding channel counts. We maintained the maximum pooling layer after each convolutional layer, but reduced the pooling window size and stride. The pooling operation is defined as formula 2:
\(F\) is the input feature map,\(P\) is the pooled feature map, \(a\) is the pooling window size, \(s\) is the stride, and \((x,y)\) is the position on the pooled feature map. The structure of the improved AlexNet model is illustrated in Fig. 2.
The extracted features are weighted by the SKNet module, which utilizes multi-scale convolution and attention mechanisms. It performs several convolution operations on the input tensor and combines the resulting outputs into a unified tensor. The convolution outputs are summed and averaged across each channel, with the weights derived from mappings through fully connected layers. These weights are then applied to generate the final feature map. The structure of the improved SKNets model is illustrated in Fig. 3.
After feature extraction through SmallAlexNet and SKAttention, the MLP model propagates data through a fully connected layer and utilizes cross-entropy loss to quantify the error between predictions and true labels. Cross-entropy loss, based on probability distribution, allows the model to produce a probability distribution, providing a confidence level for each category rather than a single classification result. This process aids the model in learning more accurate category boundaries during classification tasks.
After feature extraction by SmallAlexNet and SKAttention, the MLP model propagates the data through the fully connected layer and applies a cross-entropy loss function to quantify the error between the predicted output and the true label. Cross-entropy loss, based on a probability distribution, allows the model to produce a probability distribution, providing a confidence level for each category rather than a single classification result. This facilitates the model’s learning of more accurate category boundaries in classification tasks. The cross-entropy loss function is illustrated in formula 3:
Included among these, \(y_i\) is truthful labeling, \(\hat{y}_i\) is probability distribution of model predictions.
Extending the feature maps from 7 \(\times\) 7 to 224 \(\times\) 224, followed by the extraction of 256 \(\times\) 6 \(\times\) 6 features, may introduce some redundancy. However, AlexNet’s feature extraction typically retains the essential information effectively. While SKAttention preserves both spatial and channel dimensions, it enhances multi-scale feature extraction, thereby improving performance. The fully connected layer follows a conventional structure, which prevents abrupt dimensionality changes and reduces the risk of overfitting.
Experimental analysis
Dataset
The dataset used in this paper is the CICIDS2017 dataset, created by the Canadian Institute for Cybersecurity Research. It offers high authenticity, diversity, rich features, and high-quality labelling, but also has limitations, including data imbalance and feature redundancy. Panigrahi et al.28 evaluated existing datasets in a 2018 paper, highlighting that the CICIDS2017 dataset, derived from real-world network traffic, contains various types of cyberattacks and detailed labelling, yet suffers from data imbalance and complex features.
Datasets not selected in this paper, such as Darpa 1998/9929, KDD 99, and NSL-KDD, are outdated for current use. The NSL-KDD dataset, in particular, has been criticized for its high false positive rate and lack of realism30, making it unsuitable for model training and prediction.
In this study, 17 highly correlated features and 10 features with no variance were removed to reduce dataset redundancy. The dataset was divided into training, validation, and test sets in a 60%, 20%, and 20% ratio. Outliers were addressed by applying quantile transformation to standardize features into a uniform distribution between [0,1].
Few classes with similar features were merged to create new attack categories. To reduce the dimensional feature space and simplify the learning process, we applied Principal Component Analysis (PCA) to the dataset, retaining as much relevant information as possible. Experiments revealed that retaining 25 principal components ensures that no critical information is lost while significantly reducing the feature space. The categories of the adjusted dataset are shown in Table 1.
Model evaluation
The main metrics used in this paper are precision, recall, and the F1-score. Precision refers to the proportion of positive predictions that are actually correct. It measures the model’s accuracy in predicting positive instances. Recall refers to the proportion of actual positive instances that are correctly identified by the model. It measures the model’s ability to detect all positive instances. The F1-score is the harmonic mean of Precision and Recall. It evaluates the model’s performance by balancing Precision and Recall, particularly when a trade-off exists between the two. The F1-score is especially useful in unbalanced datasets, as it prevents overemphasis on a single metric.
The formula is:
Where TP (True Positive) is the true class, FP (False Positive) is the false positive class, and FN (False Negative) is the false negative class.
Result and discussion
Experimental results of MLP-AS
In intrusion detection tasks, accuracy alone does not adequately reflect model performance due to the high class imbalance. Therefore, we selected F1-score, precision, and recall as evaluation metrics. As shown in the table below, recall and F1-score improved in detecting minority classes while maintaining comparable performance for majority class intrusions. The data visualizations are presented in Figs. 4, 5, and 6.
The experimental results for the MLP-AS algorithm, shown in the images above, demonstrate that the improved model achieves a notably higher F1-score for minority classes while maintaining similar overall accuracy, as displayed in Table 2. According to Figs. 7 and 8, F1-scores for the minority classes BotnetARES and PortScan increased significantly by 18.93% and 26.57%, respectively, with recall scores rising by 26.23% and 37.54%. The ROC curves indicate comparable performance levels, highlighting enhanced classification accuracy for minority classes under consistent conditions.
Table 3 presents a comparison of MLP and MLP-A results, highlighting a significant improvement in either recall or F1-score for minority class detection. This improvement suggests that AlexNet’s feature extraction enhances the recognition of positive samples in minority class intrusion detection.
Table 4 compares the results of MLP and MLP-S, showing no significant improvement in recall or F1-score for minority class detection. This outcome suggests that the features extracted by MLP alone are insufficient to distinguish minority class samples, and thus, SKNet does not enhance the model’s performance in detecting minority classes.
Table 5 compares the results of MLP-A and MLP-AS, revealing further improvements in recall and F1-score for minority class detection. The results indicate that, beyond accurately identifying positive samples, the model with AlexNet feature extraction reduces misclassifications of both negative samples as positive and positive samples as negative. This enhanced feature extraction from AlexNet, combined with SKNets, further improves the model’s detection of minority classes in intrusion detection.
Comparison experiment
To validate the performance of our proposed algorithm for minority class detection, we conducted comparative experiments using other classical classification models for intrusion detection-specifically, DBN31, Logistic Regression, and Naive Bayes-under the same processed dataset and training parameters. The comparison results with the DBN model are presented in the table below.
As shown in Tables 6 and 7, MLP-AS achieves comparable or superior performance to Logistic Regression, Naive Bayes, DBN, D-CNN, and LSTM, even with a higher number of classification categories. In particular, MLP-AS shows improved ROC performance and exceptional minority class detection ability compared to DBN in Fig. 9, while maintaining comparable overall performance. These results indicate that our model improvement is meaningful and effective.
Conclusion
This paper explores the feasibility of leveraging neural networks to enhance the multilayer perceptron (MLP) model, aiming to improve the accuracy of minority class attack identification in intrusion detection systems (IDS). To achieve this, we design and implement an IDS that combines convolutional neural networks (CNN) with machine learning techniques to effectively identify anomalous behaviors in the network. The CICIDS2017 dataset is selected as a benchmark for evaluating the performance of the proposed model, with the parameter optimization method adjusted accordingly.
During the feature extraction stage, the SmallAlexNet architecture is employed to accommodate the characteristics of unbalanced datasets, ensuring that key information is accurately captured from complex backgrounds. Additionally, the SKNet mechanism is incorporated to enhance feature expression, allowing the model to dynamically adjust attention allocation based on the input data, thereby focusing on the most discriminative features. Finally, the classification task is performed by the fully connected layer.
Experimental results demonstrate that the improved MLP model not only outperforms the original version and popular methods, such as Deep Belief Networks (DBNs), in overall performance, but also excels in recognizing rare attack types. Specifically, the F1 scores for the BotnetARES and PortScan attacks have increased by 18.93% and 26.57%, respectively. Moreover, the overall accuracy and recall of the model are significantly enhanced, demonstrating its potential and value in practical applications.
Although the proposed model performs better than some traditional methods, it still consumes more computational resources during training, especially with larger datasets, where training time and computational overhead may increase. This aspect can be further optimized to enhance the model’s computational efficiency32.
Data availability
The dataset used in this study can be accessed through the following link: CIC-IDS2017: https://www.unb.ca/cic/datasets/ids-2017.html
References
Duy, P. T. et al. Digfupas: Deceive ids with gan and function-preserving on adversarial samples in sdn-enabled networks. Comput. Secur. 109, 102367 (2021).
Lin, Z., Shi, Y. & Xue, Z. Idsgan: Generative adversarial networks for attack generation against intrusion detection. In Pacific-Asia Conference on Knowledge Discovery and Data Mining 79–91 (Springer, 2022).
Maseer, Z. K., Yusof, R., Bahaman, N., Mostafa, S. A. & Foozy, C. F. M. Benchmarking of machine learning for anomaly based intrusion detection systems in the cicids2017 dataset. IEEE Access 9, 22351–22370 (2021).
Alom, M. Z., Bontupalli, V. & Taha, T. M. Intrusion detection using deep belief networks. In 2015 National Aerospace and Electronics Conference (NAECON), 339–344 (IEEE, 2015).
Yin, C., Zhu, Y., Fei, J. & He, X. A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5, 21954–21961 (2017).
Roopak, M., Tian, G. Y. & Chambers, J. Deep learning models for cyber security in IoT networks. In 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), 0452–0457 (IEEE, 2019).
Shone, N., Ngoc, T. N., Phai, V. D. & Shi, Q. A deep learning approach to network intrusion detection. IEEE Trans. Emerg. Top. Comput. Intell. 2, 41–50 (2018).
Abdallah, E. E. et al. Intrusion detection systems using supervised machine learning techniques: A survey. Proc. Comput. Sci. 201, 205–212 (2022).
Dalatu, P. I., Fitrianto, A. & Mustapha, A. A comparative study of linear and nonlinear regression models for outlier detection. In Recent Advances on Soft Computing and Data Mining: The Second International Conference on Soft Computing and Data Mining (SCDM-2016), Bandung, Indonesia, August 18–20, 2016 Proceedings Second, 316–326 (Springer, 2017).
Widodo, A. & Handoyo, S. The classification performance using logistic regression and support vector machine (SVM). J. Theor. Appl. Inf. Technol. 95, 19 (2017).
Anderson, J. P. Computer Security Threat Monitoring and Surveillance, Technical Report (James P. Anderson Company, 1980).
Denning, D. E. An intrusion-detection model. IEEE Trans. Softw. Eng. 2, 222–232 (1987).
Heberlein, L. T. et al. A network security monitor. Tech. Rep., Lawrence Livermore National Lab. (LLNL), Livermore (1989).
Forrest, S., Hofmeyr, S. A., Somayaji, A. & Longstaff, T. A. A sense of self for unix processes. In Proceedings 1996 IEEE Symposium on Security and Privacy, 120–128 (IEEE, 1996).
Porras, P. A. & Neumann, P. G. Emerald: Event monitoring enabling response to anomalous live disturbances. In Proceedings of the 20th National Information Systems Security Conference, vol. 3, 353–365 (1997).
Roesch, M. et al. Snort: Lightweight intrusion detection for networks. Lisa 99, 229–238 (1999).
Bivens, A. et al. Network-based intrusion detection using neural networks. Intell. Eng. Syst. Artif. Neural Netw. 12, 579–584 (2002).
Moradi, M. & Zulkernine, M. A neural network based system for intrusion detection and classification of attacks. In Proceedings of the IEEE International Conference on Advances in Intelligent Systems-Theory and Applications, 15–18 (IEEE Lux-embourg-Kirchberg, 2004).
Roy, S. S., Mallik, A., Gulati, R., Obaidat, M. S. & Krishna, P. V. A deep learning based artificial neural network approach for intrusion detection. In Mathematics and Computing: Third International Conference, ICMC 2017, Haldia, India, January 17–21, 2017, Proceedings 3, 44–53 (Springer, 2017).
Kim, J. et al. An intrusion detection model based on a convolutional neural network. J. Multimed. Inf. Syst. 6, 165–172 (2019).
Farahnakian, F. & Heikkonen, J. A deep auto-encoder based approach for intrusion detection system. In 2018 20th International Conference on Advanced Communication Technology (ICACT), 178–183 (IEEE, 2018).
Hajimirzaei, B. & Navimipour, N. J. Intrusion detection for cloud computing using neural networks and artificial bee colony optimization algorithm. Ict Express 5, 56–59 (2019).
Shettar, P., Kachavimath, A. V., Mulla, M. M., Hanchinmani, G. et al. Intrusion detection system using mlp and chaotic neural networks. In 2021 International Conference on Computer Communication and Informatics (ICCCI), 1–4 (IEEE, 2021).
Zhang, X. et al. Gan-based intrusion detection model using mlp encoder. In 3rd International Conference on Applied Mathematics, Modelling, and Intelligent Computing (CAMMIC 2023), vol. 12756, 1226–1232 (SPIE, 2023).
Ali, Z., Tiberti, W., Marotta, A. & Cassioli, D. Empowering network security: Bert transformer learning approach and mlp for intrusion detection in imbalanced network traffic. IEEE Access (2024).
Goodfellow, I. J., Shlens, J. & Szegedy, C. Explaining and harnessing adversarial examples. arXiv preprint arXiv:1412.6572 (2014).
Amato, F., Mazzocca, N., Moscato, F. & Vivenzio, E. Multilayer perceptron: An intelligent model for classification and intrusion detection. In 2017 31st International Conference on Advanced Information Networking and Applications Workshops (WAINA), 686–691 (IEEE, 2017).
Panigrahi, R. & Borah, S. A detailed analysis of cicids2017 dataset for designing intrusion detection systems. Int. J. Eng. Technol. 7, 479–482 (2018).
Tavallaee, M., Bagheri, E., Lu, W. & Ghorbani, A. A. A detailed analysis of the kdd cup 99 data set. In 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, 1–6 (IEEE, 2009).
Al Tobi, A. M. & Duncan, I. Kdd 1999 generation faults: A review and analysis. J. Cyber Secur. Technol. 2, 164–200 (2018).
Doriguzzi-Corin, R., Millar, S., Scott-Hayward, S., Martinez-del Rincon, J. & Siracusa, D. Lucid: A practical, lightweight deep learning solution for ddos attack detection. IEEE Trans. Netw. Serv. Manag. 17, 876–889 (2020).
Hnamte, V. & Hussain, J. Dcnnbilstm: An efficient hybrid deep learning-based intrusion detection system. Telemat. Inf. Rep. 10, 100053 (2023).
Author information
Authors and Affiliations
Contributions
Qihao Zhao wrote the main manuscript text. Fuwei Wang provided the theoretical guidance. Tianxin Zhang and Haodong Wu prepared figures and tables. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Zhao, Q., Wang, F., Wang, W. et al. Research on intrusion detection model based on improved MLP algorithm. Sci Rep 15, 5159 (2025). https://doi.org/10.1038/s41598-025-89798-0
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-89798-0
This article is cited by
-
Clinical and MRI markers for acute vs chronic temporomandibular disorders using a machine learning and deep neural networks
Communications Medicine (2025)
-
Design of an iterative method for adaptive federated intrusion detection for energy-constrained edge-centric 6G IoT cyber-physical systems
Scientific Reports (2025)