Abstract
With the continuous development of Airborne Wireless Sensor Networks (AWSN) in airplane monitoring systems, security isolation is facing increasingly serious insider threats. Due to the real-time bi-directional data exchange, attackers can exploit compromised nodes as the springboard to infiltrate the aircraft control domain and airline information services domain, thus stealing sensitive data or doing damage. However, existing zero-trust schemes have centralized deployment bottlenecks and static identity authentication problems, so it is difficult to combat insider threats caused by compromised nodes in the AWSN environments. In this paper, we propose a distributed zero-trust scheme with dynamic identity authentication called DzTrust in airborne wireless sensor networks. Distributed cross-domain deployment of zero-trust engines around dense AWSN nodes can decentralize the zero-trust processing load of centralized deployment. A lightweight Certificateless Aggregation Signcryption (CLASC) model suitable for AWSN is constructed to ensure the secure transmission of information flow. Meanwhile, we maintain a Regularized Behaviors Data Blockchain (RBD_chain) to securely store the behavioral data of AWSN nodes, which facilitates traceability and prevents information tampering. Incorporating dynamic trust evaluation with certificateless authentication, a dynamic identity authentication method is designed, which effectively identifies and mitigates compromised nodes. Security analysis shows that the DzTrust scheme has high security against eavesdropping attack, replay attack, impersonation attack, and man in the middle attack. Performance analysis shows that the DzTrust scheme has good performance in identifying compromised nodes, as well as high computational and communication efficiency.
Similar content being viewed by others
Introduction
In a typical commercial/military aircraft, the airplane monitoring system includes safety-critical systems (e.g., engine control systems, fight control systems) and non-safety-critical systems (e.g., structural and engine health monitoring systems, environmental control systems, and in fight entertainment system)1. Traditionally, a large number of wired sensors and data acquisition systems also cause problems in the airplane monitoring system, such as cumbersome wiring, heavy cables, and the inability to lay on moving parts2. In comparison, the wireless sensor network is flexible, easy to install, and not limited by field cable placement, and it is widely used in the industrial measurement and control field3. One major potential advantage of using Airborne Wireless Sensor Networks (AWSN) is the reduction of weight and installation time of airplane monitoring systems4. The adopted AWSN can reach savings of 14–60 millions of dollars per aircraft5.
With the rapid development of the civil aviation industry in the world, network security is one of the important aspects6. According to Aeronautical Radio Incorporated (ARINC) 8117, the domains for deploying wireless sensor networks inside aircraft include the Aircraft Control Domain (ACD), Airline Information Services Domain (AISD), and Passenger Information and Entertainment Services Domain (PIESD). The ACD domain includes flight control, avionics, fuel, environmental control, and other high-safety aircraft control systems to achieve safe flight of aircraft. The AISD domain includes airborne information servers, video surveillance, electronic flight bags, airborne air-ground wireless, and other low safety level avionics systems. To realize the information service of aircraft, a large amount of data needs to be exchanged bidirectionally between the ACD domain and AISD domain in real-time. As a result, the ACD domain faces security threats from the AISD domain8.
On the other hand, the AISD domain uses Ethernet and the communication interface unit of the PIESD domain for bidirectional data transmission. Currently, the gradual popularization of airborne WiFi has prompted many airlines to increase the functions related to Internet access to the PIESD domain, which enhances the interconnection and interoperability of the airborne network, but also brings great risks to network security. In this case, attackers can find vulnerable AWSN nodes in the PIESD domain for intrusion control or identity theft, and then exploit these compromised nodes as the springboard to gradually move into the AISD domain and ACD domain to implement insider threats. The compromised nodes can eavesdrop, intercept, modify, and replay messages in the AWSN broadcast channel, or inject false messages to destroy the integrity and correctness of the data, and even affect the system functional safety of the ACD domain and the airworthiness of the aircraft.
According to the 2022 Ponemon Cost of Insider Threats Global Report9, insider threat incidents have risen 44% over the past two years, with costs per incident up more than a third to $15.38 million. In the AWSN environments, the insider threats caused by compromised nodes may be more harmful than malicious insiders. Due to the large variety and number of AWSN nodes, the more compromised nodes controlled by attackers, the greater the chance of attack. The compromised nodes perform normal behaviors before being controlled, so attackers can suddenly do bad things under the cloak of “legal identity”, which can take full advantage of the time lag of attack detection.
Zero Trust is a new cybersecurity paradigm that centers on the concept of “never trust, always authenticate”, all user, transaction, and network traffic should be authenticated and authorized, and thus zero-trust combats insider threats by eliminating the boundaries between internal and external networks in traditional networks10. However, the existing zero-trust schemes are inclined to the centralized deployment of Zero-Trust Engine (ZTE), which makes it difficult to meet the constant identity authentication requirements in the scenario of mass AWSN node access. In addition, the current node identity authentication mechanism is still in the static authentication stage. If a node is successfully authenticated when it goes online, its credibility is always recognized until it goes offline, ignoring the situation that the node may be compromised to implement insider threats.
With the rapid development and widespread application of airborne wireless sensor technology, the number and network size of sensor nodes are constantly increasing. In AWSN, the important challenge in ensuring the normal operation of the system and information security is to solve the bottleneck of centralized zero-trust deployment and fill the security defect of static identity authentication. Traditional zero-trust schemes with identity authentication tend to adopt static identity authentication, lacking flexibility and the ability to monitor and respond to node behavior. In addition, the lack of secure transmission solutions for information flow can easily lead to sensitive data leakage and unauthorized access.
Through in-depth analysis of the constant identity authentication requirements of massive AWSN node access, zero-trust should be deployed from the center to the domain. Around the AWSN nodes to combat the potential inside threats of compromised nodes, we propose a distributed zero-trust scheme with dynamic identity authentication called DzTrust in the AWSN environments. The main contributions of this paper are as follows:
-
Design a distributed zero-trust deployment method with a signcryption transmission guarantee. Based on the Software Defined Boundary (SDP) zero-trust architecture, zero-trust engines are deployed across domains near ASWN nodes to distribute the pressure of detecting compromised node threats to various airborne network domains. Introducing lightweight certificateless aggregation signcryption, designing a two-way signcryption model to ensure the secure transmission of information flow for behavior data collection and authentication requirements from SDP clients to SDP gateways, as well as authentication information flow from SDP gateways to ADC. The certificateless cryptosystem avoids the burden of certificate management and improves security and ease of management. Completing signature and encryption in one logical step, as well as batch verifying signatures, not only improves operational efficiency and system response speed but also reduces resource consumption and system complexity. Compared with the traditional method of signing first and then encrypting, our model is more suitable for environments like ASWN which are resource-limited and have high requirements for real-time and security.
-
Design a dynamic trust evaluation model to improve the response capability to the abnormal behaviors of compromised nodes. Once the behavior of an AWSN node changes, the SDP recorder stores its behavioral data securely in the Regularized Behaviors Data Blockchain (RBD_chain) promptly to enable region-cross sharing of regularized behavioral data of AWSN nodes. To rapidly decay the trust value of the compromised AWSN node below the threshold value, a time decay factor, and a risk factor are introduced to form a dynamic trust evaluation model. The SDP recorder extracts the behavioral data from the RBD_chain, and the SDP controller calculates the dynamic trust value of AWSN nodes to identify the compromised nodes promptly.
-
Construct a dynamic identity authentication method that can more timely identify compromised nodes. Certificateless authentication is carried out for ASWN nodes when they pre-launch through the SDP gateway. After successfully verifying their identity, the SDP controller carries out online dynamic identity authentication in combination with trust value for ASWN nodes to continuously monitor and evaluate nodes’ activities in the network. Once a node has abnormal behavior and is determined to be a compromised node, the SDP controller will feed back to the SDP gateway, then the SDP gateway will immediately reject the node’s access request and terminate the session.
The organization of this paper is as follows. We introduce the related works in section “Preliminary and related work”. The design overview is described in section “Design overview”. Our DzTrust scheme is proposed in section “Scheme design”. The security analysis is given in section “Security analysis and comparison”. Next, the performance analysis of our DzTrust scheme is given in section “Performance analysis”. Finally, we conclude this paper in section “Conclusion”.
Preliminary and related work
Zero trust
Boundary-based network security is not enough to prevent further horizontal attacks, and the introduction of zero-trust has changed the traditional way of network security protection. The BeyondCorp11 architecture proposed by Google for its enterprise security has become a typical case of implementing access control under a zero-trust architecture. The Zero Trust Architecture (ZTA)12 is an end-to-end network/data protection methodology based on multiple aspects of identity, credentials, access management, operations, endpoints, host environments, and interconnected infrastructure.
The Cloud Security Alliance (CSA) proposes Software Defined Perimeter (SDP) as an effective zero-trust implementation13 to prevent, monitor, and respond to a wide range of cyber and cross-area attacks against applications and infrastructure. The revised and enhanced SDP 2.014 specification released in 2022 makes it even clearer that elements of SDP directly support ZTA principles. The boundary security capability of SDP to provide trust-based access control on any network effectively enables ZTA15. The components of the SDP architecture include the SDP controller, the Initiating Host (IH), and the Accepting Host (AH)16.
Zero-trust can effectively improve the defense of data centers against horizontal attacks from malicious nodes within the system as well as network penetration attacks17. Sultana et al.18 proposed a defense system for healthcare data vulnerabilities based on a zero-trust model where only authenticated users and devices can interact with the network and improve the security of healthcare data transmission. Chen et al.19 proposed a 5G intelligent healthcare security sensing and protection system based on a zero-trust architecture, which realizes network security situational awareness, continuous authentication, and access behavior analysis by constructing a trusted dynamic access control model. Mehraj et al.20 proposed a conceptual zero-trust access control policy, which can dynamically evaluate the trustworthiness of any user, device, or application joining the network through trust scoring.
Zhang et al.21 proposed a security protection system based on a zero-trust framework for power IoT, which adds an endpoint trust that introduces a new trust metric influencing factor and a trusted computing parameter to improve the accuracy of the endpoint trust metric. Chen et al.22 designed a zero-trust based security protection framework for the security problems facing electric power mobile interconnection. The scheme consists of components such as a trusted terminal device environment, trusted identity, and access control engine to realize the secure and efficient development of electric power mobile services.
Liu et al.23 proposed an innovative blockchain information sharing solution in a zero-trust environment, which introduces a detection mechanism and a punishment mechanism that facilitates information sharing, anonymous traceability, temporary authentication, and data privacy protection in a zero-trust Internet of Things (IoT) environment. Huang et al.24 proposed a ZT-Access scheme combining zero-trust access control and attribute-based encryption to secure sensitive data in power IoT environments, which continuously monitors the network behavior of the accessing entities and calculates their trust values.
Jingjing Guo et al.25 proposed a trust evaluation scheme for federated learning in Digital Twin for Mobile Networks, which can evaluate the trust values of users with different behavior patterns. This scheme calculates the user’s local trust value and recommended trust value by combining user behavior model data with an adaptive weight calculation method. Zhiquan Liu et al.26 proposed a novel Privacy-Preserving Reputation Updating (PPRU) scheme for cloud-assisted vehicular networks. This scheme collects and preprocesses reputation feedback in a privacy preserving manner through a cloud service provider (CSP), providing high security reputation management and acceptable computing and communication overhead.
Currently, the deployment of zero-trust engines tends to be centralized, which applies to scenarios with a limited number of terminals. However, the centralized zero-trust engine deployment in the AWSN environment with massive node access has the risk of a single point of failure, which makes it difficult to withstand the consistent authentication pressure of massive node access in a large-scale intranet environment.
Certificateless aggregation signcryption and authentication
In this section, we first provide a brief review of preparatory knowledge about elliptic curve cryptography. Secondly, we will introduce some typically related works on the research of certificateless aggregation signcryption and authentication.
In cryptography, elliptic curves are usually defined over a finite field, where all coefficients in the elliptic curve are taken from a finite field \(GF({p^n})\), where \({F_p}\) is a finite field containing p elements (p is prime and \(p>3\)), and the congruence equation on it is \({y^2}={x^3}+ax+b(\bmod p)\)\((a,b \in {F_p})\). (And satisfies the discriminant \(4{a^3}+27{b^2} \ne 0\bmod p\)), the elliptic curve determined by this congruence equation is the most commonly used for elliptic curve encryption. Using \({E_p}(a,b)\) to represent a set consisting of all solutions on an elliptic curve and an infinite point O, i.e. \({E_p}(a,b)=\{ (x,y)|x,y \in {F_p}\}\), and satisfying equation \(\{ {y^2}={x^3}+ax+b\} \cup \{ O\}\), q is called the order of the elliptic curve, representing the number of points on \({E_p}(a,b)\), and G is an additive group of prime order q.
Cryptographers seek to enhance data processing efficiency by integrating data encryption and digital signatures to build cryptographic schemes that guarantee confidentiality, integrity, and non-repudiation. Zheng27 introduced signcryption, addressing confidentiality and non-repudiation. Baek et al.28 designed a verification security model. In 2003, Al-Riyami et al.29 presented a certificateless system, removing certificate management issues. Chen et al.30 proposed identity-based signcryption in 2005, but faced private key leakage challenges. Brabosa et al.31 applied signcryption to practical environments in 2008. Selvi et al.32 introduced identity-based aggregation signcryption in 2009, while Lu et al.33 designed a Certificateless Aggregation Signcryption (CLASC) scheme in 2011, sparking research interest. However, Eslami et al.34 and CLASC schemes constructed by Basudan et al.35 in 2014 and 2017 suffered from low efficiency due to bilinear pair operations. Subsequently, Yu et al.36 and Luo et al.37 proposed CLASC schemes avoiding bilinear pair operations, relying on minimal dot multiplication and hash operations. Traditional public key cryptography’s high Certification Authority (CA)-issued certificate cost is unsuitable for large-scale use. Identity-based signcryption lacks certificates but faces key custody issues. Therefore, we construct a lightweight CLASC scheme without pairing operations, which aims to effectively address data security communication in AWSN.
Cryptography researchers have diligently pursued secure authentication schemes to efficiently authenticate and verify communication entities. Recently, researchers have proposed tailored authentication methods for IoT38,39,40,41,42, the Internet of Vehicles43, Vehicular Ad Hoc Networks (VANETs)44, smart grids45, and Wireless Body Area Networks (WBANs)46. The schemes in38,39,40,41,42 are deemed efficient but lack message integrity verification, posing tampering risks. Moreover, their computational and communication costs require optimization for lightweight applications. Li et al.39 presented an end-to-end authentication and key agreement protocol for IoT, leveraging certificateless public key cryptography and the Physical Unclonable Function (PUF) technology. However, it lacks user anonymity and traceability, is vulnerable to Man-in-the-Middle (MITM) attacks and insider attacks, involves many (16 rounds) of elliptic curve scalar multiplication, increases overhead, and introduces additional hardware costs with PUF. Garg et al.41 proposed a lightweight Authentication and Key Agreement (AKA) scheme using PUF for IoT node security. However, Bagheri et al.38 noted that Garg’s scheme allows passive attackers to track nodes, compromising location privacy. Proactive attackers can also compromise message integrity, and Garg’s approach lacks key privacy, enabling attackers to extract session keys. Tedeschi et al.40 presented a lightweight certificateless key agreement for IoT, but it cannot detect imposters. The lightweight authentication mechanism proposed by Jain et al.47 performs well in resource constrained micro wireless sensor networks, with the advantages of low computation, low communication, and low storage overhead, and can effectively resist various security attacks. However, the dependence on base stations and single point of failure issues of this mechanism may limit its application in large-scale or dynamic networks. A secure authentication protocol for wireless sensor networks used in military applications proposed by Jain et al.48 performs well in terms of security, computation, and communication overhead, making it particularly suitable for military applications. However, its dependence on base stations, computational overhead of public key encryption, and complexity of certificate management are areas that need further improvement.
Due to the fact that certificateless authentication schemes can avoid complex tasks such as certificate management in traditional PKI based public key cryptography and private key escrow in identity-based cryptography, in distributed systems where devices and users change frequently, certificateless authentication schemes can quickly adapt to the addition of new devices or users without the need to redeploy certificates or face the risks of private key escrow. By introducing a certificateless authentication scheme and assisting in dynamic identity authentication, the distributed zero-trust architecture can not only significantly improve security, simplify management, and improve user experience, but also reduce overall cost of ownership and support compliance requirements. This design has significant advantages in dealing with the complexity and dynamism of modern distributed environments, and is an ideal choice for building an efficient, secure zero-trust system. Therefore, we design a lightweight certificateless authentication algorithm that combines trust evaluation algorithm to achieve dynamic identity authentication of nodes in AWSN for AWSN and achieve the required security and lightweight performance.
Discussion on various security threats
In the process of data communication or information transmission, it is susceptible to attacks including but not limited to man in the middle attacks, replay attacks, Distributed Denial of Service (DOS) attacks, eavesdropping attacks, and impersonation attacks. We will discuss the above attacks and analyze the anti attack capability of the proposed solution in the security analysis based on the above security threats .
Man in the middle attack (MITM): Attackers place themselves between communicating parties, intercepting, tampering, or injecting data to achieve the goal of stealing sensitive information, tampering with communication content, or injecting malicious data.
Replay attack: Attackers intercept legitimate communication packets and resend them later to deceive the system into performing unauthorized operations, which may result in duplicate transactions, identity impersonation, and data tampering.
Eavesdropping attack: The attacker passively listens to data transmission in the network to obtain sensitive information, with the aim of disrupting the confidentiality of the information.
DOS attack: Attackers overload the target system by sending a large number of requests or data packets, resulting in service unavailability or interruption, affecting user experience, and causing economic losses.
Impersonation attack: Attackers impersonate legitimate users or systems to gain access or launch other attacks, which may result in compromised confidentiality, integrity, and authentication failure.
Design overview
In this section, we first present the design goals of our DzTrust scheme to combat compromised nodes in the AWSN environments. Meanwhile, we give the system architecture of DzTrust.
The key variables used in our scheme are listed in Table 1.
Design goals
To enhance the security and effectiveness of DzTrust in combating compromised nodes, we propose three design goals. These three design goals are interrelated and work together to achieve a secure zero-trust scheme in the AWSN environment. Our design goals are as follows:
Secure delivery of information flows
The information flow for deploying a zero-trust architecture mainly involves the behavior data collection and authentication requirements information flow from SDP clients to SDP gateways, as well as the authentication information flow from SDP gateways to airborne data centers (ADCs). The existing research on zero-trust neglects the secure transmission of information flow. If it is in a plaintext state, attackers can hijack and tamper with it during the transmission process. Therefore, it is necessary to design a signcryption based information flow transmission method to ensure confidentiality and anti-counterfeiting. The secure transmission of information flow between the components of the SDP zero-trust architecture is the foundation of the zero-trust architecture. This mechanism ensures that identity authentication information and behavioral data are not tampered with or stolen during transmission, providing reliable foundational data for subsequent dynamic trust evaluation. The specific design details of this approach can be found in the section Zero-trust deployment with signcryption transmission.
-
Rapid response to abrupt behaviors.
The compromised nodes have been engaged in normal behavior until it is invaded and controlled. Attackers can use the “legitimate identity” of the compromised node to infiltrate the network and suddenly do bad things, and this abnormal behavior can fully utilize the time lag of attack detection. Therefore, it is necessary to design a dynamic trust evaluation model to quickly respond to the abnormal behavior of fallen nodes. Dynamic trust evaluation calculates the trust value of each AWSN node in real-time based on trust data during secure transmission. This dynamic trust evaluation can quickly identify compromised nodes and provide a basis for subsequent dynamic identity authentication. The specific design details of this approach can be found in the section Dynamic Trust Evaluation.
-
Dynamic identity authentication.
The existing static identity authentication mechanisms make it difficult to deal with the situation of nodes being controlled and compromised by attackers in the AWSN environment. Therefore, based on the requirement of “always authentication” with zero-trust, a dynamic identity authentication method is designed by incorporating zero-trust elements, monitoring the fluctuation of trust values for dynamic authentication, and achieving timely identification of compromised nodes and blocking their network activities. Dynamic identity authentication combines lightweight certificateless authentication algorithm and trust evaluation results to continuously verify the identity of each AWSN node, ensuring that only trusted AWSN nodes can access network resources. This mechanism can adjust access permissions when detecting fluctuations in trust values. The specific design details of this approach can be found in the section Dynamic Identity Authentication.
System architecture
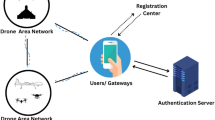
With the wireless connectivity of the airport monitoring system, the large number and wide range of nodes accessing AWSN have posed a huge challenge to the centralized deployment of zero trust components, delaying the application of zero-trust in AWSN. Therefore, a distributed architecture is needed to improve the detection efficiency of compromised node threats and avoid the problem of a single point of failure in a centralized deployment. As shown in Fig. 1, the distributed zero-trust model in AWSN can be implemented on the “Node”, “Management”, and “Cloud” system architecture.
-
1.
Node Layer (NL): The AWSN nodes that connect to the three domains of ACD, AISD, and PIESD within the aircraft form the NL. The assumption of zero-trust is inevitable, and to actively detect potential threats from the compromised nodes, it is necessary to configure an SDP client for each AWSN node, responsible for monitoring the network activity of AWSN nodes and collecting behavior data of AWSN nodes in a distributed real-time manner, which is transmitted to the Zero Trust Engine (ZTE) at the control layer.
-
2.
Management Layer (ML): The control layer is composed of zero-trust components such as SDP gateway, SDP controller, and SDP recorder in ZTE. It monitors the behavior of AWSN nodes in each domain, conducts continuous dynamic trust evaluation to actively detect compromised nodes, and uses dynamic identity authentication as the basis for data access and resource service authentication in the cloud layer. For suspicious behaviors such as control command tampering and malicious code injection, SDP client monitoring will directly inform the SDP gateway of the control layer to intercept them. For network behaviors that cannot determine suspicious situations, they need to be submitted to the SDP controller for analysis. The SDP recorder is a newly added zero-trust component, mainly responsible for extracting and storing rule-based behavior data. It can aggregate SDP recorders from all network domains to form a collection of storage engines, jointly maintaining the Regularized Behavior Data Blockchain (RBD_chain), and achieving cross-domain sharing of rule-based behavior data.
-
3.
Cloud Layer (CL): After dynamic identity authentication by the control layer, the Airborne Data Center (ADC) only needs to verify and issue authorization credentials, and then provide corresponding data access and resource services based on the request type. Under the premise of actively preventing the threat of compromised nodes, it helps to improve the verification efficiency of the cloud layer.
Scheme design
To meet the monitoring and authentication needs of massive nodes in AWSN scenarios, and achieve fast and effective detection of compromised nodes, a distributed zero- trust scheme is constructed.
As shown in Fig. 2, an overall scheme design framework is constructed. We propose a decentralized zero-trust framework known as DzTrust, tailored for airborne wireless sensor networks. By strategically placing zero-trust engines across different domains around dense AWSN nodes, the framework alleviates the processing burden typically associated with centralized zero-trust systems. We also develop a lightweight certificateless signcryption model suitable for AWSNs to secure the flow of information. Additionally, we implement a blockchain called RBD_chain to store securely the behavioral data of AWSN nodes, which aids in accountability and deters data manipulation. The framework integrates dynamic trust assessment with certificateless authentication to create a dynamic identity authentication approach that effectively detects and counters the threat of compromised nodes.
Zero-trust deployment with signcryption transmission
This section will provide a detailed introduction to our zero-trust deployment with signcryption transmission, which will achieve confidentiality protection for cross domain information flows in AWSN.
-
(1)
Cross-domain deployment.
Deploying a zero-trust engine across domains is the primary step in building a distributed zero-trust scheme. Using virtualization, three virtual machines were separated from the ZTE server to form the SDP gateway, SDP controller, and SDP recorder.
In airborne wireless sensor networks, the aircraft control domain, airline information services domain, and passenger information and entertainment services domain are all suitable for distributed zero-trust cross domain deployment. Each domain has its unique security requirements and dynamism, and the zero-trust architecture can effectively enhance the security and manageability of these domains through continuous authentication, dynamic access control, and fine-grained permission management. Especially in cross domain communication and dynamic network environments, zero-trust architecture can provide stronger security and adaptability. In each domain, the SDP gateway, SDP controller, and SDP recorder, three zero-trust components, work together to form the operational mechanism of the zero-trust scheme, which mainly includes five steps: (1) Data access and resource service requests issued by nodes active within the AWSN will be packaged by the SDP client as authentication requirements and reported to the SDP gateway; (2) The SDP gateway forwards the authentication requirements reported to the SDP controller; (3) The SDP controller retrieves behavior data from the SDP recorder based on the authentication status of the requesting node, calculates its trust value, performs dynamic identity authentication, and sends the authentication result to the SDP gateway; (4) For authenticated request nodes, the SDP controller generates access authorization credentials and hands them over to the SDP gateway; (5) The SDP gateway packages the authentication results and authorization credentials and sends them to the ADC. If it receives the verification validity and access permission returned by the ADC, it forwards them to the requesting node. Given the numerous types and quantities of AWSN nodes, if there is only one ZTE server inside the aircraft, frequent and frequent authentication can easily overload the zero-trust component composed of a single ZTE server. Specifically, attackers can control some compromised nodes to create a large amount of normal traffic without injecting any malicious code, without knowing the specific location of the zero-trust engine. This will automatically flow to the zero-trust engine through the SDP client, forming a blocking attack. Therefore, deploy one ZTE main engine and one secondary engine per airborne network domain. On this basis, a distributed cross-domain deployment is formed to form a set of zero-trust engines Φ={ZTE1,…, ZTEk,…, ZTE8}. The deployment rules for distributed cross domain cross domain are as follows:
Rule 1. The primary and secondary engines in each domain are dispersed in different locations to prevent attackers from detecting their location. The main engine is in operation and responsible for monitoring the AWSN nodes of the entire airborne network domain. The secondary engine is in standby mode.
Rule 2. Assuming ZTEk as the main engine, pk represents its processing power. Set the alarm threshold for processing capability to σ. Once pk ≥ pk ≥ δ,, ZTEk sends an offline notification to the secondary engine (ZTEh) in its domain, requesting ZTEh to go online and become the new primary engine. At the same time, ZTEk is moving towards Φ. The secondary engines of the remaining three domains in the collection broadcast offline notifications. Once ZTEh is overloaded, it can be temporarily replaced and brought online.
Rule 3. After ZTEk goes offline, it switches to a secondary engine and is in standby mode, waiting for ZTEh’s offline notification and back online.
Rule 4. Gathering SDP recorders from all network domains to form a collection of storage engines Ξ={RE1,…, REk,…, RE8}, jointly maintain the Regularized Behavior Data blockchain (RBD_chain), and achieve cross domain sharing of behavior data.
Rule 5. The SDP controller in the main engine only needs to use the SDP recorder to retrieve the behavior data on RBD_chain, and can quickly calculate the trust value of the requesting node. Even if the node moves across domains, it will not affect its trust value calculation.
The Software Defined Perimeter (SDP) is a network security architecture based on the zero-trust principle. Unlike traditional perimeter-based security models, SDP zero-trust architecture adopts a “authenticate first, connect later” mechanism. In the AWSN environment, the SDP zero-trust architecture monitors the behavior data of AWSN nodes in real-time through collaboration between various components, ensuring that only AWSN nodes that have passed identity authentication and trust evaluation can access network resources. In addition, the SDP architecture adopts a continuous and dynamic identity authentication mechanism to continuously evaluate the trust value of AWSN nodes during their operation. Once abnormal behavior is detected in the AWSN node, the SDP zero-trust architecture immediately adjusts the access permissions of the compromised node and restricts its network connections to effectively prevent the spread of security threats.
-
(2)
Two-way signcryption guarantee.
As shown in Fig. 3, a zero-trust engine is deployed across domains in a distributed cross-domain and a two-way signcryption model are designed to ensure the secure transmission of information flow.
The two-way signcryption model consists of 5 entities, namely the Key Generation Center (KGC), SDP client, SDP gateway, SDP controller, and Airborne Data Center (ADC). The roles of these 5 entities in the two-way signcryption model are as follows:
-
1.
KGC: Responsible for system initialization and providing partial private key for other entities.
-
2.
SDP Client: Before requesting the required recorded data, authentication, and authorization are obtained through the identity authentication of the SDP Gateway and the access request authentication and authorization of the SDP Controller. When interacting with the SDP Gateway for authentication, the authentication information flow is signed without a certificate, achieving confidentiality protection of the message and authentication of the message source.
-
3.
SDP Gateway: As a bridge between the SDP Client and the SDP Controller, as well as between the SDP Client and the ADC, responsible for certificateless aggregation signcryption of authentication results, authorization credentials, and data requested by the SDP Client, achieving confidentiality protection of messages and batch authentication.
-
4.
SDP Controller: responsible for authenticating access requests from SDP clients and generating authorization credentials.
-
5.
ADC: Based on the authentication results and authorization credentials of the SDP Controller, provide the required and authorized data for the SDP Client to access.
-
(3)
Signcryption model design.
Due to virtualization, the interaction between zero-trust components takes place within the ZTE server, and external nodes cannot access it, thus ensuring interaction security. For the behavior data collection and authentication requirement information flow from SDP Client to SDP Gateway, and the authentication information flow from SDP Gateway to ADC, we design a two channel signcryption model in our scheme to ensure the secure transmission of the information flow.
In the scenario of communication for airborne wireless sensor networks, the Certificateless Aggregation Signcryption (CLASC) model proposed in this paper involves participants including a Key Generation Center (KGC) as a trusted third party, a user group u composed of n AWSN nodes (SDP Clients) participating in aggregation signcryption, an Airborne Data Center (ADC) as a receiver, and an SDP Gateway as an aggregator. The two-way signcryption model in Figs. 4 and 5 demonstrate the roles played by the SDP Client, SDP Gateway, KGC, and ADC in the aggregation signcryption algorithms and the algorithms that need to be executed in the AWSN communication system.
The description of the seven polynomial time probability algorithms in the CLASC model proposed in this paper is as follows:
-
System Setup: KGC executes the algorithm, with security parameters k as the input, system parameters \(params\), and a master key s generated by a random number seed as the return value of the algorithm. The system parameters \(params\) are publicly published by KGC, while the master key s is secretly saved by KGC. The specific process is as follows:

Algorithm 1 System setup
-
Partial Private Key Extraction: This algorithm inputs system parameters \(params\), master key s, and identity information \(I{D_u} \in {\{ 0,1\} ^*}\) of an entity group u. The key generation center implements this algorithm to generate a partial private key \({d_u}\) and sends \({d_u}\) to the communication party u through a secure channel. The specific process is as follows:

Algorithm 2 Partial private key extraction
-
Key Generation: This algorithm takes system parameters \(params\) and the identity information \(I{D_u}\) of an entity as inputs, and returns a randomly selected secret value \(x_{u}\) and a communication public key \({P_{ID}}\) for the entity. The user u runs this algorithm to generate public-private key pair \((S{K_{ID}},P{K_{ID}})\) and allocates this public key \(P{K_{ID}}\) without authentication. The specific process is as follows:

Algorithm 3 Key generation
-
Signcryption: Each AWSN node (SDP Client \(ZT{C_i}\)) in the user group u participating in aggregation signcryption runs this algorithm. The user’s input is the system parameter \(params\), a message \({m_i}\), the identity information \(I{D_i}\) of user i, timestamp \({t_i}\), the communication public key \({P_{I{D_i}}}\) of user i, the private key \(SK_{{ID_{i} }} = (x_{{ID_{i} ,}} d_{{ID_{i} }} )\) of user i, the receiver’s identity information \(I{D_B}\), and the receiver’s communication public key \({P_{I{D_B}}}\). This is a polynomial algorithm, which outputs signcryption ciphertext \({\sigma _{\text{i}}}=({U_i},{c_i},s{}_{i})\). User \(I{D_i}\) sends signcryption ciphertext \({\sigma _{\text{i}}}=({U_i},{c_i},s{}_{i})\) to receiver \(I{D_B}\) and aggregator. The specific process is as follows:

Algorithm 4 Signcryption
-
Aggregate Signcryption: The aggregator runs this algorithm. After receiving n signcryption ciphertexts \({\sigma _{\text{i}}}=({U_i},{c_i},{s_i})\), the aggregator calculates \(S=\sum\nolimits_{{i=1}}^{n} {{s_i}}\), then the aggregation signcryption ciphertexts \(\sigma =\left\langle {\left\{ {{U_i},\left. {{c_i}} \right\}_{{i=1}}^{n},S} \right.} \right\rangle\), sending it to the receiver \(I{D_B}\).The specific process is as follows:

Algorithm 5 Aggregate signcryption
-
Unsigncryption: This algorithm will consist of a user group consisting of n AWSN nodes \({\text{\{ }}ZTC\} _{{i=1}}^{n}\) participating in the aggregation of signcryption, with the identity information \(I{D_u} \in {\{ 0,1\} ^*}\)of the AWSN node \({\text{\{ }}ZTC\} _{{i=1}}^{n}\)and the communication public key \({P_{I{D_i}}}\) of each AWSN node \(ZT{C_i}\), the identity information \(I{D_B}\) of the receiver, and the signcryption ciphertext \(\sigma_{i}\) as inputs to the algorithm. If the signature is valid, the output is correct; otherwise, the output is incorrect. The specific process is as follows:

Algorithm 6 Unsigncryption
-
Aggregate Unsigncryption: This algorithm takes aggregation ciphertext \(\sigma\), complete private key \(({x_{I{D_B}}},{d_{I{D_B}}})\) of the receiver, identity information \(I{D_B}\) of the receiver, identity information \(\{ ID\} _{{i=1}}^{n}\) of the sender, and communication public key \({\text{\{ }}{P_{I{D_i}}}\} _{{i=1}}^{n}\) of the sender as inputs. Output n plaintext \(\{ {m_i}\} _{{i=1}}^{n}\). Typically, the aggregate unsigncryption algorithm is a deterministic algorithm. The specific process is as follows:

Algorithm 7 Aggregate unsigncryption
-
Analysis of the correctness of the above CLASC model.
-
1.
The correctness of the key.
User \(I{D_{\text{i}}}\)verify the validity of some keys using the Eq. (1):
-
2.
The correctness of the message.
The receiver \(I{D_B}\) verifies the validity of some keys using the Eq. (2):
According to \(W_{{\text{i}}}^{\prime }={H_3}(I{D_B},K_{i}^{\prime },{t_i})={H_{\text{3}}}(I{D_R},{K_i},{t_i})={W_{\text{i}}}\), which can ensure the correct plaintext of receiver \(I{D_B}\)’s decryption through \(I{D_i}||{m_{\text{i}}}={c_i} \oplus {W_i}\).
-
3.
The correctness of the signature.
The receiver \(I{D_B}\) verifies the correctness of the signature using the Eqs. (3) and (4):
If \(K_{i}^{\prime }={K_i}\)holds, then\(h_{i}^{\prime }={h_i}\). If the equation holds, then the sender’s authentication is successful and the message \({m_i}\)can be accepted.
Dynamic trust evaluation
Dynamic trust evaluation is a core aspect of zero trust to support rapid authentication of AWSN nodes. Along with the distributed cross-domain deployment of the zero-trust engine, the dynamic trust evaluation model is proposed at the right time to help reduce the computational load in the cloud.
As shown in Fig. 6, the implementation of the dynamic trust evaluation model involves RBD_chain construction and trust value calculation.
-
(1)
RBD_chain construction.
During the monitoring of AWSN node network activity, the SDP client needs to collect real-time behavioral data based on changes in node behavior and submit it to the SDP recorder in the domain for chain storage.
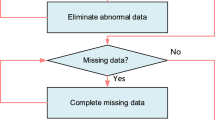
After extensive in-depth research and analysis, it has been found that the main types of abnormal behavior of attackers controlling the compromised nodes are shown in Table 2.
Define the set Ψ = {N1,…, Ni,…, Nm} of AWSN nodes in the edge region Aj. Taking Ni as an example, SCi represents the SDP client configured on it. Ni ‘s behavioral data includes two types: Ω={ RNi, RAi }. Among them, RNi is the time series set that records the normal behavior of Ni regularization, and RAi is the time series set that records the abnormal behavior of Ni regularization. Assuming in τ. At any moment, if Ni performs normally, record its normalized normal behavior rniτ =1. Otherwise, rniτ =0 and record regularized abnormal behavior raiτ = η. Among them, η represents the event type number that represents abnormal behavior.
Whenever there is a change in Ni’s behavior data, SCi sends real-time update information to the SDP recorder in the domain and connects it to RBD_chain in block form, forming behavior data sharing.
Given the characteristics of pre-selected consensus miners in the consortium blockchain, the SDP recorder in the set of storage engines Ξ={RE1,…, REk,…, RE8} serves as the miner for RBD_chain, divided into one proposer and multiple verifiers. The SDP recorder of the main engine in the domain where SCi is located plays the role of a Proposer, responsible for creating new blocks. As a distributed database, blockchain can ensure that the data stored in it will be immutable49,50. Due to the immutability of blockchain, whenever Ni behavior data changes, a new block needs to be created. In each round of block generation, randomly select 4 verifiers to verify the validity of the blocks. The behavior data sharing process based on RBD_chain is as follows:
-
Proposal phase: The Proposer proposes to create a new block to store updated behavioral data and randomly send it to the four SDP recorders in the set Ξ to serve as verifiers while broadcasting the ID of the new blocks and verifiers to the other SDP recorders.
-
Verification phase: After Verifiers verify that the block is valid, they submit it to the Ξ. All SDP recorders in the set broadcast confirmation messages.
-
Receiving phase: After receiving 4 confirmation messages, it indicates that the new block has been received, and all SDP recorders connect the new block to RBD_chain in timestamp order.
The block structure of RBD_chain consists of a block head and a block body, as shown in Fig. 7. Improve the block structure of Bitcoin51 by inheriting the original parameters {previous block hash, block ID, timestamp, Merkle root}, and adding the following elements to the block header:
Prom: Create the identity ID of the proposer’s proposer identity for the block to ensure traceability of the proposer’s identity.
Vern: The ID sets and corresponding verification results of the four Verifiers participating in the verification block are used to ensure transparency and traceability of the verification, where n = 1,2,3,4. If the verification is successful, then Vern = 1, and vice versa, Vern = 0.
Ni: The ID of AWSN node (for example, the identity is i ).
The behavior data of Ni is stored in the block body, and the SDP recorder finds the target block based on the timestamp in the block header and Ni, and obtains it from the block body τ Conduct behavior data of Ni within a certain time frame and complete the dynamic trust evaluation process of Ni.
-
(2)
Trust value calculation.
Beta distribution can fit well with the trust distribution and is one of the most classical and widely used trust evaluation models52. Beta distribution is characterized by simple computation, good flexibility, high statistical power, and applicability53. Therefore, Beta distribution is adopted as the basic probabilistic statistical model for calculating the trust value of AWSN nodes. The large probability density function of Beta distribution is as follows54:
where τ denotes the likelihood of node behavior, 0 < τ < 1, α > 0 and β > 0.
In AWSN, the basic trust value is calculated based on the historical behavior of the node. We take the ith node called Ni as an example.
The number of normal behaviors called nori is the total number of times of rniτ=1 in the set of statistic RNi, and the number of abnormal behaviors called abni is the total number of times rniτ=0 in the set of statistic RNi. When the behavior of Ni is normal, α = nori + 1. Otherwise, β = abni + 1. Therefore, the basic trust value of Ni can be calculated using the Beta distribution function as follows:
where 0 ≤ BTi ≤1. BTi= 1 means Ni is trusted when abni= 0 and nori ≥ 1. When the number of abnormal behaviors abni increases, the trust value decreases.
However, BTi has the property of static trust evaluation, which has a certain lag in reacting to the abnormal behavior of nodes. To accurately reflect the trust value of nodes, we introduce a time decay factor. We adjust the timeliness of node behavior to ensure greater sensitivity to the latest information, while gradually reducing its influence on past trust information. In the AWSN environments, the time decay factor ATFi of Ni is calculated as follows:
where τ denotes the current moment of trust evaluation, τn denotes the time of the last trust value calculation. λ denotes the decay rate.
The basic trust value BTi cannot decay to below the threshold value δ quickly when Ni has abnormal behaviors, which facilitates attackers to steal sensitive data in the AWSN. To respond to the behavioral changes of the compromised nodes promptly, we introduce the risk factor RPi to realize the dynamic trust evaluation. By considering potential losses and threats, we classify abnormal behaviors into high, medium, and low-risk levels. We assigned weights wi to each behavior to reflect the importance of the abnormal behavior in the overall risk, as shown in Table 3.
We analyze the overall risk level of Ni based on the abnormal behavior level and the number of abnormal trust factors abni. The risk factor RPi of Ni is calculated as follows:
where Φi={abni(1),…, abni(η),…, abni(10)} is the set of times of RAi. max(Φi) is the maximum number of times in the set Φi. Ψi={wi(1),…, wi(η),…, wi(10)} is the set of weights of all abnormal behaviors, and max(Ψi) is the largest weight among all abnormal behavior types for normalizing the anomaly factor.
To quickly regulate the dynamic trust value of Ni below the threshold value, the dynamic trust value DTi of Ni can be calculated as:
Dynamic identity authentication
Distinct from conventional static identity authentication, one-time authentication is no longer deemed reliable. AWSN nodes undergo authentication before online connectivity, accompanied by dynamic authentication that monitors trust value fluctuations during operation. If a node’s trust value dips below the threshold, an online authentication is initiated to promptly detect and block the compromised node.
To adhere to the “always authenticate and never trust” principle, we integrate basic and dynamic trust values int a lightweight certificateless authentication algorithm to prevent impersonation and swiftly identify compromised nodes. AWSN nodes require both initial and ongoing dynamic authentication, ensuring timely detection of compromised nodes. Our dynamic identity authentication comprises two stages: pre-launch authentication and online authentication.
-
(1)
Pre-launch authentication.
We combine certificateless authentication algorithm and trust evaluation to more comprehensively and accurately authenticate node identities to solve the problem of preventing malicious node impersonation in AWSN and understand the trust status of nodes. Even if the attacker successfully impersonates once, trust values based on node behavior can still reflect anomalies. When the AWSN node \({N_i}\) goes online for the first time, the SDP client submits \({N_i}\)’s identity information and uses a certificateless authentication algorithm to quickly verify the node’s identity and ensure its uniqueness and legality in the network. Then, send the verification results to the SDP controller.
This section will construct a certificateless authentication algorithm for dynamic identity authentication during the online authentication phase of AWSN nodes. The algorithm includes three phases: initialization phase, node registration phase, and node authentication phase. The entities participating in authentication include AWSN nodes and SDP gateways.
During the initialization phase, the AWSN node and SDP gateway need to interact with a trusted third-party KGC through a secure channel to obtain the necessary password elements for establishing a secret session key. At this phase, KGC establishes the following password elements:
Elliptic Curve E (equation of Curve-25,519 is \({y^2}={x^3}+4866662{x^2}+x\)), its prime finite field is\({F_q}\) and the generator is P.
-
1.
Using a cryptographic algorithm called Ascon-128 that satisfies both encryption and authentication, this algorithm is a lightweight algorithm based on compressed encryption authentication, which includes authentication encryption \(Enc()\), authentication decryption \(Dec()\), and hash function H.
-
2.
KGC generates its master key \(msk=s\) through system initialization algorithm \(Setup()\)and calculates the system public key \({P_{pub}}=sP\).
-
3.
KGC establishes a parameter list of system parameters \(params=\{ {F_q},q,x,y,P,{P_{pub}},H,Enc(),Dec()\}\)required for encryption and makes it public in the authentication system.
Figure 8 shows the registration phase, during which the AWSN node and SDP Gateway register their identity.
information through interaction with KGC and obtain the necessary password elements for encryption and authentication through a secure channel from KGC.
Figure 9 shows the authentication phase. In this phase, we combine the authentication process with key negotiation. The AWSN node interacts with the SDP gateway through an insecure channel. After three interactions, encryption and authentication can be completed.
When the SDP controller receives a result of true from certificateless authentication, the node successfully passes the initial verification. The SDP controller computes dynamic trust values by using Algorithm 3. The SDP controller forwards the final authentication result Ocri to the SDP gateway by combining the dynamic basic trust value and the certificateless authentication result. We formulate two pre-launch authentication results Ocri and set the threshold value of the trust value as δ.
Ocri=1: When DTi ≥ δ, Ni passes the pre-launch authentication. The SDP gateway agrees that Ni enters the on-line mode, and Ni starts the first session at the moment T10.
Ocri=0: When DTi < δ, Ni is a compromised. The SDP gateway denies the access request.

Algorithm 3 Pre-launch authentication of Ni
-
(2)
Online authentication.
When a node enters the session process, we periodically perform continuous dynamic authentication to improve timely identification of compromised nodes. At a certain moment, when the node’s online authentication is triggered, the SDP client sends instructions to the AWSN node, requiring the node to pause all interaction with the network to prevent potential compromised nodes from continuing network activities. We set the following parameters:
ΔT: The cycle of monitoring the dynamic trust value of Ni.
T10: The time of the first session of Ni.
T11: The moment when the node’s online authentication is triggered after ΔT.
Session: The stage from the moment the interaction request passes through, called T10, to the moment the interaction ends, called T11.
In addition, the SDP client collects the behavioral information of Ni during the ΔT period and forwards it to the SDP recorder. After obtaining relevant data on the blockchain, the SDP controller uses Algorithm 4 to calculate the risk factor RPi and update the dynamic trust value DTi of Ni. We set the risk threshold called σ, and establish the following two online authentication results called Pcri:
Pcri=1: When DTi ≥ δ and RPi < σ, it indicates that the authentication is passed, and continues to monitor the subsequent behavior of the node in the current session until the end of the next monitoring period called T2.
Pcri=0: When DTi < δ or RPi ≥ σ, it indicates that the authentication failed. Ni is recognized as a compromised node and the session is blocked.
During the monitoring of subsequent behavior, the behavior of Ni is monitored every Δt (Δt < ΔT), and the risk level of Ni is re-evaluated. If the level of risk is higher than the risk threshold during subsequent monitoring, Ni is considered compromised. If the level of risk is less than the risk threshold, Ni is considered normal and Ni proceeds to the next monitoring cycle.

Algorithm 4 Online authentication of Ni
Security analysis and comparison
Security analysis
The DzTrust scheme we propose is designed based on a constructed certificateless aggregation signcryption (CLASC) model and a certificateless authentication method. Therefore, it is necessary to conduct security analysis on these two parts.
-
(1)
Security analysis of CLASC model.
The CLASC model proposed in this paper satisfies these security attributes.
-
1.
Non-repudiation: Due to the involvement of a private key that is only owned by the operator during the signing and decryption process, the proposed model has non-repudiation.
-
2.
Public verifiability: When the ciphertext needs to be publicly verified, any trusted third party only needs to verify whether the equation is true, and this process does not require any secret information of the signer. Therefore, the CLASC model proposed in this paper has public verifiability.
Regarding its ability to resist attacks, the proposed CLASC model can resist or relieve the following attacks:
-
3.
Anti-man in the middle attack: The core of man in the middle attack is that the attacker impersonates one or both parties in communication, eavesdropping or tampering with the communication content. Our CLASC model has several mechanisms to resist man in the middle attacks. Firstly, in certificateless cryptography, the user’s public key is bound to their identity, and the private key is jointly generated by the user and the Key Generation Center (KGC), avoiding key custody issues. During the signing process, the sender uses a private key to sign the message, and the receiver can verify the authenticity and integrity of the message using the sender’s public key. This mechanism can prevent attackers from impersonating legitimate users. Secondly, signcryption technology simultaneously implements encryption and signature functions, ensuring the confidentiality and integrity of messages. Even if the attacker intercepts the ciphertext, they cannot decrypt or tamper with the content. In addition, due to the absence of certificates, the risk of certificate forgery or CA attacks in traditional PKI is avoided. Attackers cannot impersonate legitimate users by forging certificates. Finally, aggregation signcryption technology ensures the security of multiple signed ciphertexts through mathematical construction, so even if an attacker obtains some ciphertexts, they cannot deduce other ciphertexts or private keys.
-
4.
Relieve Denial of Service (DOS) attack: Our CLASC model combined with timestamps can indirectly alleviate DoS attacks from the following aspects. Firstly, timestamps can be used to verify the freshness of messages and prevent replay attacks. The communication entities in AWSN reduce the processing burden of invalid requests by checking timestamps and discarding expired requests. This indirectly reduces the possibility of attackers consuming physical resources by replaying old messages. Secondly, the certificateless aggregation signcryption technology ensures the legitimacy and integrity of requests through signature and encryption. Communication entities can quickly verify whether requests come from legitimate users and discard invalid or forged requests, reducing the resource consumption of handling malicious requests. In addition, aggregate signcryption technology combines multiple signcryption operations into one, reducing computational and communication overhead. When handling a large number of requests, communication entities can more efficiently verify and decrypt messages, thereby reducing resource consumption. Finally, certificateless cryptography avoids the overhead of certificate verification in traditional PKI and reduces the computational burden on servers. This has to some extent improved the system’s resistance to DoS attacks.
-
5.
Anti-replay attack: Our CLASC model uses timestamps and random numbers as input parameters to effectively enhance the resistance of the certificateless aggregation signcryption algorithm to replay attacks. Tampering resistant timestamps \(\{ {t_i}|1 \leqslant i \leqslant n\}\) and random numbers are used to avoid expired or duplicate messages.
-
(2)
Security analysis of certificateless authentication method.
Secret value security: Only KGC and the corresponding AWSN node or gateway know the secret value \(\{ {d_{I{D_i}}},{d_{I{D_j}}}\}\), while the secret value \(\{ {x_{I{D_i}}},{x_{I{D_j}}}\}\) is only known by the corresponding AWSN node or gateway. Therefore, this cannot obtain the secret value \(\{ {d_{I{D_i}}},{d_{I{D_j}}},{x_{I{D_i}}},{x_{I{D_j}}}\}\).
Authenticity: Every time an AWSN node goes online, it must be authenticated through an SDP gateway to ensure secure communication within the system. When the SDP gateway receives the message \({M_3}\) from the AWSN node, it calculates the secret session key \(S{K_i}=Hash({K_{j1}} \oplus {K_{j2}} \oplus {N_i} \oplus {N_j})\) and performs decryption operations to authenticate the AWSN node. During the decryption process, an internal authentication label \(A{T_j}\) is generated. If \(A{T_j}=A{T_i}\), it indicates that the SDP gateway has successfully authenticated the AWSN node.
Integrity: During the decryption process, an internal authentication label \(A{T_j}\) is generated and compared with the label \(A{T_i}\) in \({M_3}\). If \(A{T_j}=A{T_i}\), then it means that the ciphertext \(C{T_i}\) has not been changed during the communication process. On the contrary, if \(A{T_j} \ne A{T_i}\), it indicates that the ciphertext \(C{T_i}\) has been tampered with during communication, so the SDP gateway will not accept the tampered ciphertext. Therefore, the certificateless authentication method proposed in this paper ensures data integrity.
Regarding its ability to resist attacks, the proposed certificateless authentication method can resist the following attacks:
-
1.
Anti replay attack: Attackers can obtain historical messages \({M_1}=\{ I{D_i},{P_{I{D_i}}},{Y_{I{D_i}}},{T_i},{N_i}\}\), \({M_2}=\{ I{D_j},{P_{I{D_j}}},{Y_{I{D_j}}},{T_j},{N_j}\}\), and \({M_3}=\{ {T_i},C{T_i},A{T_i}\}\) by listening to the channel. The attacker replaying such messages will result in incorrect effects. In the proposed certificateless authentication method, the value of ciphertext \(C{T_i}\) and the authentication label \(A{T_i}\) are based on fresh random numbers \({N_i}\) and \({N_j}\). Therefore, for each new session, the values of \(C{T_i}\) and \(A{T_i}\) will be updated. In addition, the current timestamp generated by the AWSN node and SDP gateway is also taken into account. Therefore, attackers cannot use historical messages in subsequent communication sessions, and the certificateless authentication method proposed by the text has security against replay attacks.
-
2.
Anti-eavesdropping attack: The certificateless authentication method proposed in this paper transmits messages in the form of ciphertext, hash, and plaintext, while messages transmitted in plaintext do not contain any sensitive or useful information for attackers. In addition, all messages containing confidential information are transmitted through encryption and hash functions, making it impossible for adversaries to obtain any valid confidential information. Therefore, the certificateless authentication method proposed in this paper can resist eavesdropping attacks.
-
3.
Anti-DOS attack: The proposed certificateless authentication method requires participating nodes to first verify the validity of timestamps. If the timestamp is verified to be invalid, the message will be rejected. In addition, the messages being transmitted contain an integrity check using authentication tags, and each message being transmitted always contains a recent timestamp. Therefore, the certificateless authentication method proposed in this paper can identify invalid messages and resist DOS attacks by efficiently terminating sessions.
-
4.
Anti-impersonation attack: In the proposed certificateless authentication method, if the adversary imitates a legitimate AWSN node, during this process, the attacker generates a message \(\{ I{D_a},{P_{I{D_a}}},{Y_{I{D_a}}},{T_a},{N_a}\}\) and sends it to the SDP gateway, which responds with a message \(\{ I{D_j},{P_{I{D_j}}},{Y_{I{D_j}}},{T_j},{N_j}\}\). When the attacker receives a message from the SDP gateway, the message \(\{ {T_a},C{T_a},A{T_a}\}\) is generated and sent to the SDP gateway. When the SDP gateway receives a message from the attacker, the SDP gateway performs a decryption operation using the equation \(\{ A{T_j},P{T_j}\} =Dec(S{K_j},N,AD,C{T_a},A{T_a})\). However, the decryption operation will fail because, during the decryption process, the internal authentication label \(P{T_j}\) is calculated by the SDP gateway and compared with the authentication label provided by the attacker. The authentication label depends on the associated data, and the associated data provided by the adversary is different from the associated data calculated by the SDP gateway because the associated data contains partial private keys that only KGC and the corresponding AWSN or SDP gateway know. Attackers cannot generate a valid partial private key for AWSN, and the associated data is generated locally and not publicly transmitted in communication. The authentication label generated by the adversary using incorrect association data is different from the internal authentication label generated by the SDP gateway, resulting in authentication failure. Therefore, the certificateless authentication method proposed in this paper can resist impersonation attacks.
Security comparison
This section will first compare and analyze the security of the CLASC model proposed in this paper with four typical CLASC schemes in references34,35,36,37, as shown in Table 4. As both the proposed scheme and the schemes in the comparative references construct a certificateless aggregation signcryption scheme, they meet the basic security attributes of private key escrow, confidentiality, and unforgeability. However, the difference lies in the fact that the proposed CLASC model also has public verifiability. When there is controversy over the ciphertext, it can be publicly verified in a way that does not leak the secret information of the signer, which improves the performance of the model. In addition, the proposed model also has the advantage of resisting common attacks, which further strengthens the security of the system compared to the comparative schemes.
Next, a comparative analysis of the security between the certificateless authentication method proposed in this paper and the four typical authentication schemes in references38,39,40,41,42 will be conducted, as shown in Table 5. Compared with other comparison schemes, the proposed method has the advantage of resisting common attacks and can perform integrity verification on transmitted messages, further enhancing the system’s security. Overall security is better than the comparison schemes.
Performance analysis
Simulation analysis
Simulation analysis of supressing compromised nodes
In this section, we verify whether the DzTrust scheme can effectively identify the compromised nodes in the AWSN environment through simulation tests. We use Python 3.10.8 to build an experimental platform to simulate the DzTrust scheme and discuss the simulation results. The simulation environment parameters are set as shown in Table 6.
In zero-trust security architecture, the trust value is an effective basis for achieving fast authentication of nodes. In the simulation test, the change in the trust value of compromised nodes and their recognition under three different trust evaluation schemes are observed through 200 rounds of experiments.
As shown in Fig. 10, the lag of the static trust evaluation value BT makes it unable to react to the behavioral changes of the compromised nodes in time. The compromised nodes always authenticate successfully, which results in a continuous growth of the trust value. In the first 40 rounds, AWSN nodes are not compromised. In the first 10 rounds, the dynamic trust evaluation value DT with ATF and RP tends to increase because the historical behavior of the node is less affected by the time factor. Between rounds 10 and 40, the BT is subjected to a gradual and slow decay due to the time decay factor ATF, but is still not compromised. After the 40th round, the compromised nodes that occur abnormal behavior are added. At this moment, the DT can quickly identify the abnormal behaviour of the compromised node and quickly decay its trust value below the threshold value.
When the trust value of the compromised node is lower than the threshold value, then the node fails to pass the authentication and fails to implement the malicious threat. The number of nodes in the simulation test is 2000 and the percentage of compromised nodes is set to 40%. The suppression of the number of steganographic threats in this environment is shown in Fig. 11. After adding compromised nodes in the 40th round, the number of malicious threats present cannot be suppressed because BT is unable to decay the trust value of the compromised nodes. The DT with ATF and RP quickly reduces the trust value of the compromised node so that the compromise is recognized in time and the number of malicious threats is quickly suppressed.
The detection rate of compromised nodes is shown in Fig. 12. Since the static trust value BT cannot decay, the compromised node cannot be detected. Because the dynamic trust value DT with ATF and RP decays the trust value of compromised nodes quickly, the detection rate of compromised nodes increases after the 40th round when the compromised nodes show abnormal behavior.
Simulation analysis of CLASC model
This section first conducts simulation experiments on the CLASC model proposed in this paper, evaluating the efficiency of our model. The operating system used in the experiment is Windows 10 Professional Edition, with an Intel (R) Core (TM) i5-4200 H CPU of 2.80 GHz and an 8GB operating memory computer. The model is implemented using JAVA’s JPBC cipher library programming. Compared with the other five comparison schemes, this model uses Weil bilinear pairing. On the computer used in the experiment, the time required to perform one Weil bilinear pairing calculation is about 4.151ms, the time required to perform one MapToPoint hash operation is about 4.236ms, and the time required to perform one point multiplication operation is about 1.527ms. In the experiment, the time required to test the aggregate signcryption and aggregate unsigncryption algorithms of each CLASC model when the number of messages is n = 200, 300, and 500, respectively.
As shown in Fig. 13, the computation overhead of the aggregation signcryption and aggregation unsigncryption algorithms in our model is relatively low. The efficiency of the aggregation signcryption algorithm in our model is 81.84% and 74.30% higher than that in references34,35 at n = 100, 300, and 500, respectively. The computational cost is much lower than that in references34,35, which is the same as references36,37. The efficiency of the aggregation unsigncryption algorithm in our model has been improved by 75.09%, 64.91%, 0.13%, and 40.07% compared to the average efficiency of references34,35,36,37 at n = 100, 300, and 500, respectively. The computational cost is much lower than references34,35] and [37, and slightly lower than references36. Therefore, our model has significant advantages in computational efficiency.
As shown in Fig. 14, the aggregated signcryption ciphertext size in our model is smaller than that in references34,35, and the communication efficiency is improved by 64.29%, 60.47%, and 59.72% compared to references34,35 at n = 100, 300, and 500, respectively. Therefore, our model has higher communication efficiency.
Simulation analysis of certificateless authentication
This section conducts simulation experiments on the lightweight certificateless authentication method proposed in this paper to evaluate the efficiency of our method. The operating system still used in the experiment is Windows 10 Professional Edition, with an Intel (R) Core (TM) i5-4200 H CPU of 2.80 GHz and an 8GB running memory computer. Python’s hashlib library is used to calculate the running time of the one-way hash function, and the Crypto library is used to generate elliptic curve key pairs and perform point multiplication operations on the elliptic curve. On the computer used in the experiment, it takes about 0.024ms to perform one one-way hash operation and 1.502ms to perform one point multiplication operation. As shown in Fig. 15, the authentication method proposed in this paper has significant advantages in computational efficiency.
As shown in Fig. 16, the communication overhead of the authentication method proposed in this paper is mainly generated by the messages exchanged between the AWSN node and the SDP gateway during the authentication stage. The three exchanged messages are \({M_1}=\{ I{D_i},{P_{I{D_i}}},{Y_{I{D_i}}},{T_i},{N_i}\}\), \({M_2}=\{ I{D_j},{P_{I{D_j}}},{Y_{I{D_j}}},{T_j},{N_j}\}\), and \({M_3}=\{ {T_i},C{T_i},A{T_i}\}\), respectively. The lengths of \({M_1}\) and \({M_2}\) are both 16 + 256 + 32 + 32 = 592 bits, while the length of is 32 + 128 + 128 = 288 bits, resulting in a total communication overhead of 592 + 592 + 288 = 1472 bits. Obviously, the communication overhead of the certificateless authentication method proposed in this paper is much lower than other comparison methods, with higher communication efficiency and meeting lightweight characteristics.
Efficiency comparison analysis
This section will first compare and analyze the efficiency of the CLASC model proposed in this paper with the CLASC scheme in references32,33,34,35. The computation and communication overhead of some algorithms in the CLASC model will be compared in two dimensions. The computational costs of some algorithms in the CLASC model include signcryption, unsigncryption, and aggregate unsigncryption, which are more complex algorithms. The indicators for comparing communication costs mainly include the length of signcryption ciphertext and aggregated signcryption ciphertext, which occupy a larger storage space. Due to the involvement of bilinear pairing operations, MapToPoint hash operations, point multiplication operations, and addition operations in our model and other comparison schemes, bilinear pairing operations are more complex and require longer time compared to other operations, while addition operations have much lower time costs than other operations, so they are ignored.
As shown in the comparison of computational costs in Table 7, for ease of description, \({T_h}\) represents the time cost of one MapToPoint hash operation, \({T_{pm}}\) represents the time cost of one point multiplication operation, \({T_p}\) represents the time cost of one bilinear pairing operation, and represents the number of messages.
During the signcryption process, the time required for our model is the same as in references34,35, which only requires three point multiplication operations and has a lower time cost than the encryption algorithm in references32,33. In the process of unsigncryption and aggregation unsigncryption, our model does not involve bilinear pairing operation, and the time cost is smaller than other comparative schemes. As shown in the comparison of communication overhead in Table 7, \(|{G_1}|\) represents the length of elements in pairing based group \({G_1}\), \(|G|\) represents the length of elements in an elliptic curve based group G, and \(|Z_{q}^{*}|\) represents the length of elements in finite field \(Z_{q}^{*}\). The lengths of parameters \(|{G_1}|\), \(|G|\), and \(|Z_{q}^{*}|\) are shown in Table 8. The proposed model in this paper has a higher communication efficiency compared to the scheme in references34,35, as the length of the signcryption ciphertext and the aggregated signcryption ciphertext are smaller than those in references32,33.
Next, an efficiency comparison analysis will be conducted between the certificateless authentication method proposed in this paper and the authentication scheme in the references36,37,38,39,40. The computation and communication overhead of each scheme during the authentication process will be compared in two dimensions, as shown in the comparison of computation overhead in Table 9. For ease of description, \({T_H}\) and \({T_{pm}}\) respectively represent the time costs of one one-way hash operation and one elliptic curve point multiplication operation. It is not difficult to see from the comparison of total computational overhead that our method is the same as that in reference38. Throughout the entire authentication process, only 8 one-way hash function operations and 4 elliptic curve point multiplication operations are required, which is more efficient than other comparison schemes. The total communication overhead of each scheme is calculated from the length of the parameters that need to be transmitted during the authentication process. In the authentication phase of our method, the AWSN node interacts with the SDP gateway three times, transmitting three messages, namely \({M_1}=\{ I{D_i},{P_{I{D_i}}},{Y_{I{D_i}}},{T_i},{N_i}\}\), \({M_2}=\{ I{D_j},{P_{I{D_j}}},{Y_{I{D_j}}},{T_j},{N_j}\}\), and \({M_3}=\{ {T_i},C{T_i},A{T_i}\}\). Therefore, the communication overhead is the sum of the total length of three transmitted messages.
Conclusion
In this paper, we propose a distributed zero-trust scheme with dynamic identity authentication called DzTrust in airborne wireless sensor networks to address the bottleneck of centralized zero-trust deployment and static authentication issues. We construct a system architecture that combines “Node”, “Management”, and “Cloud”. To distribute the load of the zero-trust engine and reduce system risk caused by a single point of failure, we design a distributed cross-domain approach to deploy the zero-trust engine. A two-way certificateless signcryption model is constructed to address the privacy protection and secure transmission issues of sensitive data in ASWN, which can securely and efficiently protect the confidentiality, integrity, and non-repudiation of sensitive data. Secondly, we design a RBD_chain to securely store the behavior data of ASWN nodes and the SDP recorder is responsible for storing and extracting the behavioral data. Then, we use dynamic trust evaluation with the introduction of the time decay factor and the risk factor to timely respond to sudden changes in the behavior of compromised nodes and rapidly decay their trust values. Finally, we construct a dynamic identity authentication method combining certificateless authentication and dynamic trust evaluation to continuously and dynamically authenticate and monitor ASWN nodes. Security analysis shows that the DzTrust scheme can effectively prevent the risk of sensitive data being stolen and resist common attacks. Performance analysis results show that the DzTrust scheme can effectively identify compromised nodes and prevent the occurrence of malicious threat behavior, which has lightweight characteristics.
In the future, the behavior information of AWSN nodes will continue to dynamically change, which will generate a large amount of trust data. Therefore, we will design a storage scheme based on redactable blockchain to efficiently store the trust data of AWSN nodes without compromising the decentralization and immutability of blockchain. This scheme only updates relevant information on blocks when trust factors change, instead of generating new blocks every time, to improve storage efficiency and reduce block storage load. Research and design a lightweight attribute-based signcryption scheme that meets the requirements of secure data transmission for many to one in AWSN, and adopt a more fine-grained access control mechanism for AWSN node access to resources. Using zero knowledge proof, users can prove to validators that they meet the access policy without leaking specific attribute information. Combining trust evaluation mechanism, dynamically adjust user attributes or access permissions based on their behavior to achieve dynamic identity authentication.
Data availability
All data generated or analyzed during this study are included in this article, which has been stated in the section “Data availability”.
References
Mazumdar, H. & Chen, Q. Response of contaminant detection sensors and sensor systems in a commercial aircraft cabin. In Proceedings of the 10th International IBSPA Conference, Beijing, China 854–861 (2007).
Li, T. & He, J. Research on precise timing method of airborne wireless sensor network for flight test. In International Conference on Sensing, Measurement & Data Analytics in the era of Artificial Intelligence (ICSMD), Harbin, China 1–5 (2022).
Wang, J., Lin, J. & Xie, S. The environment monitoring system based on wireless sensor network. Chin. J. Sens. Actuat. 28, 1732–1740 (2015).
Shang, G., Xuewu, D., Yu, H., Yuyan, G. & Qian, J. Airborne wireless sensor networks for airplane monitoring system. Wirel. Commun. Mobile Comput. 18, 6025825 (2018).
Gomez, O. E. Fly-by-wireless (FBWSS): benefits, risks and technical challenges. In Proceedings of the CANEUS Fly-by-Wireless Workshop 14–15 (2010).
Jing, W., Jingwen, L., Guo, L. & Tianjing, H. An improved FAHP-cloud-based security risk assessment model for airborne networks. J. Comput. Methods Sci. Eng. 21(2), 277–291 (2021).
Werthwein, M., Brunner, M. & Annighoefer, B. A concept enabling cybersecurity for a self-adaptive avionics platform with respect to RTCA DO-326 And RTCA DO-356. In 2023 IEEE/AIAA 42nd Digital Avionics Systems Conference (DASC), Barcelona, Spain 1–10 (2023).
Shuang, Z. H. A. N. G. et al. Secure communication technology between network domains based on virtualization avionics platform. J. Northwest. Polytechnical Univ. 40(3), 530–537 (2022).
Ponemon. 2022 cost of insider threats: Global report. https://www.proofpoint.com/us/resources/threat-reports/cost-of-insider-threats (2022).
Kang, H. et al. Theory and application of zero trust security: a brief survey. Entropy 25(12), 1595 (2023).
Ward, R. & Beyer, B. BeyondCorp: a new approach to enterprise security. Mag. USENIX&Sage 39(6), 6–11 (2014).
Rose, S., Borchert, O., Mitchell, S., Connelly, S. & Connelly, S. Zero Trust Architecture, NIST Special Publication (SP) 800 – 207 (U.S. Department of Commerce, 2020).
Kumar, P. et al. Performance analysis of SDP for secure internal enterprises. In IEEE Wireless Communications and (WCNC), Marrakesh, Morocco 1–6 (2019).
Garbis, J. & Koilpillai, J. Software-Defined Perimeter (SDP) Specification v2.0 (SDP and Zero Trust, 2022).
Lefebvre, M., Nair, S., Engels, D. W. & Horne, D. Building a software defined perimeter (SDP) for network introspection. In 2021 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Heraklion, Greece 91–95 (2021).
Home, D. Leveraging software defined perimeter (SDP), software defined networking (SDN), and virtualization to build a zero trust testbed with limited resources. In Advances in Security, Networks, and Internet of Things (Springer, 2022).
Gao, P., Yang, R., Shi, C. & Zhang, X. Research on security protection technology system of power internet of things. In 2019 IEEE 8th Joint International Information Technology and Artificial Intelligence Conference (ITAIC), Chongqing, China 1772–1776 (2019).
Sultana, M. et al. Towards developing a secure medical image sharing system based on zero trust principles and blockchain technology. BMC Med. Inf. Decis. Mak. 20(1), 1–10 (2020).
Chen, B., Qiao, S. & Zhao, J. A Security Awareness and Protection System for 5G Smart Healthcare Based on Zero- Trust Architecture[J] (IEEE Internet of Things Journal, 2020).
Mehraj, S. & Banday, M. T. Establishing a zero trust strategy in cloud computing environment. In 2020 International Conference on Computer Communication and Informatics (ICCCI) 1–6 (IEEE, 2020).
Zhang, X., Chen, L. & Fan, J. Power IoT security protection architecture based on zero trust framework. In 2021 IEEE 5th International Conference on Cryptography, Security and Privacy (CSP) (IEEE, 2021).
Chen, L., Dai, Z. & Chen, M. Research on the security protection framework of power mobile internet services based on zero trust. In 2021 6th International Conference on Smart Grid and Electrical Automation (ICSGEA) (IEEE, 2021).
Liu, Y. A. et al. A Blockchain-based decentralized, fair and authenticated information sharing scheme in zero trust Internet-of-things. IEEE Trans. Comput. 72(2), 501–512 (2022).
Huang, W. et al. ZT-Access: A combining zero trust access control with attribute-based encryption scheme against compromised devices in power IoT environments. Ad Hoc Netw. (2023).
Guo, J. et al. TFL-DT: A trust evaluation scheme for federated learning in digital twin for mobile networks. IEEE J. Sel. Areas Commun. 41, 11 (2023).
Liu, Z. et al. PPRU: a privacy-preserving reputation updating scheme for cloud-assisted vehicular networks. IEEE Trans. Veh. Technol. 1, 1 (2023).
Zheng, Y. Digital signcryption or how to achieve cost(signature &encryption) < < cost(signature) + cost(encryption). In Advances inCryptology — CRYPTO ’97 (ed. Kaliski, B. S.) 165–179 (Springer, 1997).
Baek, J., Steinfeld, R., Zheng, Y. & Naccache, D. Formal proofs for the security of signcryption. In Public Key Cryptography (ed. Paillier, P.) 80–98. (Springer, 2002).
Al-Riyami, S. S. & Paterson, K. G. Certificateless public key cryptography. In Advances in Cryptology- ASIACRYPT 2003 (ed. Laih, C. S.) 452–473 (Springer, 2003).
Chen, L. & Malone-Lee, J.Improved identity-based Signcryption,in Public Key Cryptography—PKC 2005 (eds. Vaudenay, S.) 362–379 (Springer Berlin Heidelberg, 2005).
Barbosa, M. & Farshim, P.Certificateless Signcryption, Ser.ASIACCS ’08.New York 369–372 (Association for Computing Machinery, 2008).
Selvi, S. S. D., Vivek, S. S., Shriram, J., Kalaivani, S. & Rangan, C. P. Identity based aggregate signcryption schemes. In Progress in Cryptology - INDOCRYPT 2009 (eds. Roy, B. & Sendrier, N.) 378–397 (Springer, 2009).
Lu, H. & Xie, Q. An efficient certificateless aggregate signcryption scheme from pairings. In International Conference on Electronics,Communications and Control (ICECC) 132–135 (2011).
Eslami, Z. & Pakniat, N. Certificateless aggregate signcryption:security model and a concrete construction secure in the random oracle model. J. King Saud Univ. Comput. Inf. Sci. 26(3), 276–286 (2014).
Basudan, S., Lin, X. & Sankaranarayanan, K. A privacy-preserving vehicular crowd sensing-based road surface condition monitoring system using fog computing. IEEE Internet Things J. 4(3), 772–782 (2017).
Yu, H. & Ren, R. Certificateless elliptic curve aggregate signcryption scheme. IEEE Syst. J. 16(2), 2347–2354 (2022).
Luo, W. & Ma, W. Secure and efficient data sharing scheme based on certificateless hybrid signcryption for cloud storage. Electronics 8, 5 (2019).
Bagheri, N., Kumari, S. & Camara, C. & Peris-Lopez, P. Defending industry 4.0: an enhanced authentication scheme for Iot devices. IEEE Syst. J. 16(3), 4501–4512 (2022).
Li, S., Zhang, T., Yu, B. & He, K. A provably secure and practical puf-based end-to-end mutual authentication and key exchange protocol for Iot. IEEE Sens. J. 21(4), 5487–5501 (2021).
Tedeschi, P., Sciancalepore, S., DiPietro, R. & A.Eliyan, R. Like: lightweight certificateless key agreement for secure Iot communications. IEEE Internet Things J. 7(1), 621–638 (2020).
Garg, S., Kaur, K. Choo, K. K. R. & Kaddoum, G. Toward secure and provable authentication for internet of things:realizing industry4.0. IEEE Internet Things J. 7(5), 4598–4606 (2020).
Li, X. et al. A robust ecc-based provable secure authentication protocol with privacy preserving for industrial internet of things. IEEE Trans. Industr. Inf. 14(8), 3599–3609 (2018).
Hathal, W., Cruickshank, H., Sun, Z. & Maple, C. Certificateless and lightweight authentication scheme for vehicular communication networks. IEEE Trans. Veh. Technol. 69(12), 110–16125 (2020).
Sripathi Venkata Naga, S. K., Yesuraj, R., Munuswamy, S. & Arputharaj, K. A comprehensive survey on certificateless authentication schemes for vehicular ad hoc networks in intelligent transportation systems. Sensors 23, 5 (2023).
Deng, L. & Gao, R. Certificateless two-party authenticated key agreement scheme for smart grid. Inf. Sci. 543, 143–156 (2021).
Shen, J., Gui, Z., Ji, S., Shen, J. & Tan, H. Tang,Cloud-aided lightweight certificateless authentication protocol with anonymity for wireless body area networks. J. Netw. Comput. Appl. 106, 117–123 (2018).
Jain, U., Hussain, M. & Kakarla, J. Simple, secure, and lightweight mechanism for mutual authentication of nodes in tiny wireless sensor networks. Int. J. Commun. Syst. 33(9), e4384 (2020).
Jain, U. & Hussain, M. Securing wireless sensors in military applications through resilient authentication mechanism. Procedia Comput. Sci. 171, 719–728 (2020).
Lu, X., Wu, Z., Wu, Y., Wang, Q. & Yin, Y. ATMChain: blockchain-based solution to security problems in air traffic management. In 2021 IEEE/AIAA 40th Digital Avionics Systems Conference (DASC), San Antonio, TX, USA 1–8 (2021).
Meng Tianhui, Z. et al. On consortium blockchain consistency: a queueing network model approach. IEEE Trans. Parallel Distrib. Syst. 32(6), 1369–1382 (2021).
Nakamoto, S. Bitcoin: a peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260 (2008).
Ganeriwal, S., Balzano, L. K. & Srivastava, M. B. Reputation-based framework for high integrity sensor networks. ACM Trans. Sensor Netw. 4(3), 1–37 (2008).
Josang, A. & Ismail, R. The beta reputation system. In Proceedings of the 15th Bled Electronic Commerce Conference, vol. 5 2502–2511 (2002).
Jøsang, A. & Ismail, R. The beta reputation system. In Proc. 15th Bled Electron. Commence Conf. 1–14 (2002).
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Program No. U2133203), the Fundamental Research Funds for the Central Universities of CAUC (Program No. 3122022076), the Open Fund Information Security Evaluation Center of Civil Aviation (Program No. ISECCA-202104) and the Key Research and Development Projects of Shaanxi Province (Program No. 2024GX-YBXM-076).
Author information
Authors and Affiliations
Contributions
K.W. and Y. H. Wrote the main manuscript text. Y. L. and Y. R. Mainly responsible for creating charts and analyzing proposals. J. F. Responsible for supervising and conducting modifications and format checks. All authors have reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Wang, K., Hong, Y., Li, Y. et al. A distributed zero-trust scheme for airborne wireless sensor networks using dynamic identity authentication. Sci Rep 15, 8036 (2025). https://doi.org/10.1038/s41598-025-91957-2
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-91957-2
Keywords
This article is cited by
-
Brute-force attack mitigation on remote access services via software-defined perimeter
Scientific Reports (2025)