Abstract
The increasing adoption of the Internet of Medical Things (IoMT) has raised critical security challenges, necessitating robust encryption techniques to safeguard sensitive healthcare data. However, existing security models often suffer from high computational overhead, inefficiency in handling large-scale IoMT data and vulnerability to cyber threats. To address these challenges, this paper proposes a novel ESHA-256_GBGO security framework, integrating Enhanced Secure Hash Algorithm-256 (ESHA-256) with the Golden Butterfly Optimization (GBGO) algorithm for improved encryption and performance optimization. The proposed approach enhances data integrity, encryption efficiency and computational speed while ensuring minimal processing overhead. The framework is implemented and evaluated on a real-world IoMT dataset measuring key performance indicators such as encryption efficiency, processing time, throughput and computational overhead. Experimental results demonstrate that the proposed ESHA-256_GBGO model achieves 98.76% encryption efficiency, reduces computational overhead by 27.4% and enhances security robustness compared to conventional methods. These findings validate the effectiveness of ESHA-256_GBGO in securing IoMT networks making it a scalable and efficient solution for real-time healthcare applications.
Similar content being viewed by others
Introduction
The advancements in 5G networking technologies led to the rapid growth in Internet of Health Things (IoHT) devices. Existing management and mechanisms for all computing resources are associated with several challenges, including maximum delays and low security performance1. IoMT consider as a primary innovation for developing the smart environments. IoT is currently crucial technology for making smart environments. However, there are big worries about the security and privacy when depends on IoMT2. Most of the areas are currently developing the smarter environments using the IoMT. Healthcare, Agriculture, Railway Management System and water management are the areas where IoT applications used3.
For past five years, IoMT most commonly used technology for e-medicine and telemedicine in healthcare domain and also used some wearable senor for user’s medical data4,5. Today’s information and communication technology are constantly developing and also have some security breaches6. Advancement in microelectronic and communication method are improved the extent and the quality at which can communicate with one another7. The AI-IoMT will integrate medical technology through advanced technology for the purpose of connecting those the medical devices. This will not only help to create intelligent networks in healthcare but also improve patient safety8. The IoT has been turn up in to the generative model, connecting between the billions of systems to the data sharing and for communication9.
Early processing of medical data has a main goal in maintaining the patient medical data in secure manner10,11. This deep learning12 and machine learning approaches13 the system to use the particle swarm optimization and AdaBoost algorithms to identify and classify malicious software attacks in health apps14. This method explains the important points about the operating systems and software dependencies in their High-level Performance Computing (HPC) is using the Nvidia Jetson devices15. It also shows the devices can work great with IoT devices16. IoMT appliances uses the combination of cloud computing technologies is to measure patient’s vital signs, keep track of their health and get the data to provide timely health services17,18.
The earlier studies of that not fully analyse an important factor called average message delivery time (AMDT). In this research provides valuable new insights for the AMDT for wireless healthcare monitoring in hospitals19. The patient’s biometric details is merged to username and password are stored securely using SHA-512 algorithm ensure the safe transmission sensor information20. A complete security authentication check including security check of blockchain21 enabled authentication key management protocol for IoMT (BAKMP-IoMT) with the well-defined automated validation of internet protocol (AVISPA) tool. This process helps to destroy the different type’s security attacks22. In IoMT is become more popular in many areas and also increase the security issues. Because of these IoMT systems are low processing capabilities23.
Motivation and problem statement
IoMT has transformed the healthcare industry by enabling real-time monitoring, remote diagnostics, and seamless medical data exchange. However, as IoMT devices generate and transmit vast amounts of sensitive patient data, they become prime targets for cyberattacks, unauthorized access, and data breaches. Ensuring data confidentiality, integrity, and security in such a highly interconnected environment is critical. Despite significant advancements in IoMT security, existing encryption methods often suffer from high computational overhead, inefficiency in handling large-scale IoMT data, and susceptibility to evolving cyber threats.Several conventional security techniques, including Advanced Encryption Standard (AES), Rivest-Shamir-Adleman (RSA) and Secure Hash Algorithm (SHA) based methods provide strong encryption but lack scalability for real-time IoMT applications.
Moreover, existing approaches face processing delays, excessive energy consumption and performance degradation when deployed on resource-constrained IoMT devices. These limitations necessitate an optimized security framework that not only ensures robust encryption but also enhances computational efficiency and adaptability to real-world IoMT networks. To address these challenges, this research proposes a novel ESHA-256_GBGO security framework, integrating ESHA-256 with the GBGO algorithm. The key contributions of this study provide ESHA-256 algorithm that improves cryptographic security while reducing processing overhead. The Golden Butterfly Optimization algorithm enhances encryption efficiency by dynamically optimizing computational parameters, reducing resource consumption in IoMT networks. The proposed approach ensures high-speed encryption with minimal computational cost, making it suitable for large-scale IoMT applications. The framework is validated using a real-world IoMT dataset, demonstrating superior encryption efficiency and reduced computational overhead compared to conventional methods. By integrating advanced hashing, optimization, and adaptive security techniques, the ESHA-256_GBGO framework offers a scalable, efficient and highly secure solution for protecting sensitive medical data in IoMT networks. The main contributions are given below,
-
To present a concept hierarchy generation technique for medical data pre-processing that reduce dimensionality.
-
To implement an enhanced secure hash algorithm-256 (ESHA-256) for digital certificate authentication.
-
To construct a good and bad groups-based optimizer algorithm (GBGO) for optimizing the hashing approach.
-
To execute partially homomorphic encryption named ElGamal public key cryptosystem (PHElG) for encrypting data that enhance the data security.
-
To introduce a multi-objective brown bear optimization algorithm (moBBO) for optimal key selection for encryption process.
The rest of the paper consolidate with section “Introduction” which consist of introduction about Security Framework for Internet of Medical Thing, section “Related work” consists of related works of Security Framework for Internet of Medical Thing. section “Proposed methodology” consist of proposed methodology for Security Framework for Internet of Medical Thing. Section “Results and discussion” consist of result and discussion following that section, conclusion and future work is given in section “Conclusion”.
Related work
Kanneboina et al.24 constructed hybrid metaheuristic model to improve healthcare IoT security. The network consistency was improved by an 8.7% point improved raised by 6.4% points, packet delivery increased by 8.2% points and attack detection and mitigation improved by a 9.4% point over the existing frameworks of security. However this models had problems with complexity and lack of adaptability to new threats which mean that their effectiveness in real-time healthcare applications was severely hampered.
Mani et al.25 presented Hybrid GarraRufa Fish optimization and Nomadic People Optimizer. This model would bring about improved network performance along with privacy protection. This model had substantial improvement to a 29.8% reduction in delay, lower CPU utilization and decreased energy consumption compared to current methods. However, this approaches suffered from lower security and high resource utilization, which led to performance degradation with increasing connected IoHT devices.
Veeramakali et al.26 implemented optimal deep-learning-based secure blockchain (ODLSB) model for IoT and health diagnosis, which enhanced the safety of data and diagnostic accuracy. It included secure transactions through hash value encryption using the NIS algorithm and medical diagnosis through an optimal deep neural network (ODNN). The OPSO algorithm for secret sharing and also achieved sensitivity, specificity and accuracy of 92.75%, 91.42% and 93.68% respectively. In this regard, this approaches could not handle centralized architectures and the lack of security issues. These shortcomings have hindered an efficient analysis of healthcare data within IoT.
Ramani et al.27 developed optimized data management and secured federated learning (ODMSM-FL). Performance metrics like transaction throughput of 102.75 Kbps, block processing time of 42.28 ms, data retrieval latency of 64.02 ms, a convergence rate of 77.53%, security at 88.97% and accuracy of 86.32%. The strategy however faced various challenges in effectively managing a large and sensitive amount of data. There was no comprehensive solution for existing issues in data management. This suggested model had overall limitations in performance and security regarding health systems in the IoMT framework.
Praveena Anjelin et al.28 constructed convolution neural network (CNN). Elephant herding optimization in the process of improving the intrusion detection systems (IDS) to be implemented in the environment of IoMT to detect and classify unknown cyber-attacks. The model achieved 17% improvement in accuracy and showed 35% less complexity in terms of time with which it generated alerts that assisted in responding quickly to mitigating intrusions on the sensitive data storage of cloud. This approaches complexity of high false positives rates to IDS method produce the false alarms that lead to security attacks or cyber-attacks.
Ahmad et al.29 developed an effective time-oriented latency approximation-based data encryption method (TLADE) has been introduced. The technique focuses on choosing the best encryption methods based on the latency approximation at various time stamps. Thus, based on the QoS values, the algorithm would choose the best data encryption technique. This is accomplished by implementing several encryption algorithms and measuring their QoS support values (QoSV) based on latency. An effective method for the current duty cycle has been chosen and applied to the cloud service data based on the QoSV values. The suggested method lowers the latency factor and enhances the performance of several QoS aspects which had average time taken of 0.838s.
Alsaeed et al.30 presented a new group authentication framework for IoMT Systems. The group authentication scheme was implemented in four stages: setup, registration, secret construction, and authentication. To improve efficiency and scalability, the suggested group authentication framework combines blockchain-based fog computing technologies, Shamir’s secret sharing (SSS) algorithm and elliptic curve cryptography (ECC). The simulation experiments of the suggested framework revealed that the average latency of authenticating IoMT devices was 0.5 s and the throughput was 400 transactions per second.
Ramani et al.27 constructed Optimized Data Management and Secured Federated Learning (ODMSM-FL), incorporating blockchain provenance. ODMSM-FL was created especially to meet the particular needs of the IoMT through a number of features such as federated learning, decentralized data management and strong security measures built on blockchain technology. The system enhances data management capabilities, facilitating the adequate storage, retrieval and exchange of medical data while safeguarding data privacy and maintaining data integrity. Transaction throughput (102.75 Kbps), data retrieval delay (64.02 ms) and accuracy (86.32%) were among the key performance. Table 1 provides a performance comparison of different IoMT security models based on key encryption metrics, demonstrating the efficiency of ESHA-256_GBGO in reducing computational overhead.
The security framework IoMT applications are lack of adaptability to new threats which mean that their effectiveness in real-time healthcare applications was severely hampered. Furthermore, Hybrid GarraRufa Fish optimization and Nomadic People Optimizer approaches suffered from lower security and high resource utilization, which led to performance degradation with increasing connected IoHT devices. One of the critical drawbacks of ODLSB method is could not handle centralized architectures and the lack of security issues. ODMSM-FL model has overall limitations in performance and security regarding health systems in the IoMT framework. The CNN method produce the false alarms that lead to security attacks or cyber-attacks. To resolve these challenges a high-performance and optimized security framework for IoT is introduced.
Proposed methodology
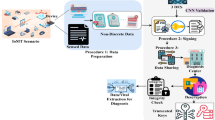
In the given research work, enhanced secure hash algorithm-256 (ESHA-256) used for hashing the data which provide robust encryption. Then, the Golden Butterfly Optimization (GBGO) algorithm provide optimal performance. Modified Opposition-Based Butterfly Optimization (moBBO) is used for adaptive security tuning. The work flow of proposed model is given in the Fig. 1.
Figure 1 shows medical data being securely collected pre-processing and then stored within the IoMT to ensure the security of such data in a manner where privacy is achieved. The ESHA-256_GBGO security framework integrates these three techniques into a unified security model for IoMT networks. The overall workflow is initialize by collecting IoMT devices medical data. The data is encrypted using ESHA-256 ensuring secure transmission. GBGO optimizes encryption parameters, improving speed and efficiency. moBBO continuously adapts security policies, preventing evolving cyber threats. The encrypted data is securely transmitted to cloud servers for further processing.
Pre-processing by concept hierarchy
Concept hierarchy generation is one of the handy techniques applied for medical data preprocessing in which complex information of a real-life scenario forms a hierarchical relationship21. The concept hierarchy refers to the process of making a set of data into a continuous interval or categories whereby attribute values can be subjected to hierarchical partitioning. The smaller dataset al.so ensures faster processing and consumes fewer resources leading to quicker insight generation and data analysis.
Data cleaning
Data cleaning is removing, missing and fixing unwanted or irreverent data within the dataset. There are many opportunities to have duplicate data or labelled incorrectly when combining multiple sources of data. If your data is wrong the ultimate outputs and algorithms are not correct and unreliable even though they may look correct.
Data reduction
Data reduction is simply a process that helps take away the unwanted data content while keeping the important thing. The process makes it even easier to store and work within the data and by doing so it adds more useful insights from these data. Data reduction reduces the number of data to be processed thus improving the computational performance. It also helps with visualization and understanding of the data by removing unnecessary points in the data.
Data transformation
Data transformation is the process through which data is converted, cleaned, and structured into usable formats to support various uses such as analytics, reporting or storage. It is a step in which data is transformed and optimized for accuracy and applicability. There are several types of transformations; some of them include logarithmic transformations and Fourier transforms, performed to achieve certain goals. For example, logarithmic transformations are used to reduce imbalance in data, and Fourier transforms are used to convert time domain data to frequency domain data. These transformations are important for the proper ordering of data to enable enhanced analysis and improved performance in systems such as IDS.
Data normalization
Subsequent data is normalized for the purposes of further processing; the latter represents the application of a linear transformation on the original data that is to the numeric values. The aim of min-max normalization is to linearly transform the original data.
A number can be standardized between a set range usually from 0 to 1 thereby allowing the reduction of influence due to outliers while simultaneously allowing easier interpretation of results derived from a model. Therefore, normalization plays an important role as one of the basic steps within a pre-processing pipeline for intrusion detection in IoMT22.
Key generation good and bad groups-based optimizer (GBGO)
IoMT networks generate massive amounts of real-time data, requiring efficient processing. GBGO optimizes the encryption process by dynamically adjusting cryptographic parameters, reducing computational overhead. GBGO23 identifies optimal encryption key parameters using a bio-inspired search mechanism. It minimizes processing time and power consumption without compromising security. The algorithm adapts dynamically to changing IoMT network conditions, ensuring real-time encryption. Moreover, the algorithm provide faster encryption speed due to optimized cryptographic key generation and also provide lower energy consumption making it ideal for low-power IoMT devices. The optimization have an impact in increasing the scalability for large-scale healthcare applications. Initially the matrix is filled with random solutions and then it updates step by step according to the rules of the algorithm. Population matrix was specified in Eq. (2).
Consider that you have a set of candidate solutions for optimization problems, and every solution has hundreds of characteristics or dimensions. The population matrix I can be visualized like an enormous table that includes all these solutions. Each row contains one solution \({I_x}\) and each column corresponds to one characteristic \({i_{x,e}}\) of that solution. The number total number of characteristics or variables in the optimization problem. For each solution in the population it compute how good it is by using a special function called the objective function. The function are specified in Eq. (3).
The expression F represents the fitness scores for each solution within a population, where the variable Fi is the fitness of the \(xth\) solution. Every optimization problem defines exactly a number of variables n that need to be searched so the best solution can be attained, whereas the search space has to be visualized by axes n in number where each axis corresponds to a defined variable. Sometimes one the strongest solution of a given set guides the entire group inside the search space in case of many optimization methods although other solutions could guide it further in certain axes more suitably. Moving away from worst also improves the overall population. GBGO takes advantage of all information generated by all the solutions involved. Instead of a single powerful solution leading the group GBGO picks a set of strong solutions to guide its population. Similarly, it picks instead of just the single weak solution that will draw down the group a group of weak solutions to avoid. Thus this way the population gets updated based on groups of both good and bad solutions.
Good group updating
The selection of good population members is based on the scores is provided by the objective function. The number of \(OH\) members of the highest scores are achieved and incorporated to form a group a good matrix is obtained.
Bad group updating
Similarly, the worst members in the population are selected considering their objective function scores. The number of \(OC\) members that have scores less than all others form a group known as the bad matrix.
In simple words, if we take the members of the population and write them down in ascending order according to the objective function values then the best \(\:OH\) members will be chosen to form the good group and the worst \(\:OC\) members will be chosen to form the bad group. By doing so we can define the good and bad groups by the fitness function values with certain Eqs. (4) and (5).
There are two classes of members here good \(HH\) and bad \(CH\). Every member within the good group has been labelled \(H{H_x}\) where \(xth\) defines that particular member. And all of these members can be of more than one dimension for example \(h{h_{x,e}}\) with \(eth\) defining that particular dimension. Similarly, the bad ones have labels \(C{H_x}\) while their dimensions are of \(c{h_{x,e}}\) type.
In GBGO all members don’t follow the best one but every variable of a member is guided by a randomly selected member from the good group. In this case a good member may only influence some of the variables of a population member and may leave a few of the variables in the population untouched. The same principle can be applied to the bad members in the bad group. This is mathematically represented in Eqs. (6) and (7).
In this process, good and bad selected members control each dimension of a population member. Precisely speaking the \(eth\) dimension of some chosen good member guides \(dth\) dimension of the \(xth\) population member with \(h{h_{l,e}}\). Analogously \(c{h_{l,d}}\) is the \(eth\) dimension of a bad chosen member who directs the \(eth\) dimension of the in this process good and bad selected members control each dimension of a population member. Precisely speaking the \(eth\) dimension of some chosen good member guides \(eth\) dimension of the \(xth\) population member with \(h{h_{l,e}}\). Analogously \(c{h_{l,e}}\) is the \(eth\) dimension of a bad chosen member who directs the \(eth\) dimension of the \(xth\) population member. The objective values of these chosen members are \(G_{l}^{{HH}}\) and\(G_{l}^{{CH}}\) respectively. In addition, a random number is \(rnd\). This is distributed normally within the range of 0 and 1.
After all the variables of population members had been updated based on Eqs. (6) and (7) the algorithm entered the cycles running to reach the specified stopping condition. Then the best solution that could be obtained after finishing all the iterations was presented. Figure 2 shows the GBGO as a flowchart.
The GBGO enhances the hashing process by optimizing the parameters of ESHA-256. This optimization ensures fine-tuning parameters of hash function to speed up the hashing process. Selecting optimal configurations to minimize hash value overlaps and also reduce the computational complexity for faster and lightweight hashing. Ensuring stronger, collision-resistant hash outputs to improve efficiency, reliability and scalability of ESHA-256.
Enhanced secure hash Algorithm-256
Enhanced Secure Hash Algorithm-256 (ESHA-256) is introduced to create hashes for the unsigned data. Traditional encryption methods like AES and RSA are computationally expensive for IoMT devices, leading to high energy consumption and delays. ESHA-256 is an optimized version of SHA-256, specifically designed to offer stronger data integrity by preventing unauthorized modifications. Moreover, the lightweight computation suited for resource-constrained IoMT devices and resistance to brute-force and collision attacks for enhanced security. The IoMT device generates a unique cryptographic hash of the medical data where the hash undergoes additional bitwise transformations to enhance randomness. The resulting ESHA-256 hash is securely transmitted, preventing unauthorized access. Using SHA, the ESHA-256 designed as an efficient replacement for the increasingly vulnerable SHA-1 family to brute force attacks. The 256 parts of ESHA-256 specifies its fixed hash digest size which is to consistently produce a 256-bit value regardless of input plaintext or clear text sizes. This feature promises consistent and robust cryptographic hashing. Chaotic maps are utilized in the SHA process in order to enhance security. Dynamic systems exhibit chaotic behavior which necessitates that a thorough analysis of such chaotic systems be performed. A bifurcation diagram is used to show the behavior of a chaotic system changes under variation of a dynamic control parameter. Lastly the initial parameters chosen for chaotic maps found within chaotic regions were determined using the Lyapunov exponent.
The Lyapunov exponent or denoted by \(\lambda\) can provide a qualitative understanding of a system’s dynamics. In a one-dimensional map it falls into two cases: the case of either a negative or positive value for\(\lambda\). The case that involves a negative value of \(\lambda\) implies that paths being slightly separated will eventually tend to converge, indicating the no chaotic evolution of the system. Conversely if \(\lambda\) is positive then nearby paths diverge and the evolution is sensitive to initial conditions and the behavior is chaotic. As the value of \(\lambda\) increases so does the complexity of the map resulting in a lower predictability. Where \(a{a_0}\) is initial value and \(bb\) as an iteration.
The step for ESHA is divided into nine types as follows.
-
Convert the given message into a corresponding ASCII stream.
-
The message padding involves addition of extra bits such that the total length becomes a multiple of 512 bits in this case 64 bits are added more. When padding it is required that the first one is added and all following bits are zeros.
-
Select chaotic maps appropriate for both buffers containing hashes and the constant adder from a catalog of 55 discrete maps that are chaotic.
-
All the chaotic maps that are used have an initial value range of\(\left[ {0,1} \right]\). Two symbols are utilized\(a{a_0}\) is the initial value used to generate all buffer values whereas \(iv_{0}\)refers to the initial value used for the additive constant key\(k{e_0}\).
-
This generated output value \(a{a_{bb+1}}\) ranges \(\left[ {0,1} \right]\) so use all of it: multiply them with 256 for easy conversion of those values\(a{a_{bb+1}}\). Convert hexadecimal values in additional transformations like converting that to a DNA sequence.
-
Let each DNA sequence be replaced with an appropriate complementary rule so that the value is translated back to a hexadecimal and entered in the last 8 bits of buffer A.
-
Repeat the iteration procedure for \(a{a_{bb+1}}\) to get the subsequent 8 bits of the hash buffer. Do this iteration many times until a total number of 64 bits is obtained.
-
The last bit of \(a{a_{bb+1}}\) will be the 8th bit in the buffer A. Repeat above steps to find the values of all the hash buffers C, D, E, F, G and H.
-
Repeat all steps until obtain the first additive constant.
The ESHA-256 integrated with a chaotic map provides a robust and efficient hashing mechanism for secure digital systems. The chaotic map introduces non-linearity and pseudo-randomness into the hashing process, enhancing the unpredictability of the hash output. This integration strengthens the cryptographic properties, such as collision resistance and avalanche effect, ensuring that even a slight change in the input results in a completely different hash value. Additionally, the chaotic behavior improves resilience against attacks like brute force and differential cryptanalysis. The method is computationally efficient and lightweight, making it suitable for resource-constrained environments. Overall, the combination of ESHA-256 and chaotic maps ensures a high level of security, efficiency, and robustness for modern cryptographic applications.
Multi-objective brown bear optimization algorithm
The keys for encryption and decryption is created using the multi-objective Brown Bear Optimization (moBBO) algorithm. Conventional security models struggle with evolving cyber threats, making IoMT devices vulnerable. moBBO introduces an adaptive learning mechanism that dynamically strengthens security based on real-time threat analysis. The algorithm monitors network behavior and identifies potential vulnerabilities. It adjusts security parameters in real time, preventing cyberattacks before they occur. moBBO enhances anomaly detection, reducing false positives in IoMT security monitoring. It provide adaptive security enhancements in response to emerging threats. Using optimization lower the false positive rates in intrusion detection and also improves the robustness against evolving cyberattacks.
The mathematical expression given below defines the initial population in terms of the randomization process for the distribution of groups of brown bears in the territory.
Let \({Q_{j,k}}\) denote the \(kth\) pedal mark of the \(jth\) group of brown bears and let \(Q_{{j,k}}^{{min}}\) and \(Q_{{j,k}}^{{max}}\) be the minimum and maximum range of the pedal marks, respectively. The marks are initialized by using a uniform random number \(\lambda\) between\(\left[ {0,1} \right]\). Let \({P_{nop}}\) denote the total number of groups in the territory (population) and let D denote the total number of pedal marks or decision variables in each group. Then the solution set Q can be expressed as
The unique characteristics of the pedal scent marking by brown bears include the characteristic gait while walking, careful stepping and twisting of feet onto depressions made in the ground. These characteristics are then modelled mathematically for them to represent the behavior. The occurrence of each is spread equally and there is a probability is equal for each feature occurrence. Assuming that the total number of iterations in the algorithm is \({P_{ite}}\) each characteristic appears about \(\frac{{{P_{ite}}}}{3}\) times.
Characteristic gait while walking: Male brown bears are characterized by pedal scent marking with a specific gait when walking thereby leaving distinct pedal scent marks. The assumption for this gait based behavior is that it happens within the first one third of \({P_{ite}}\) and is represented mathematically as a unique phase in which the individual gait of each male bear is used to update the pedal scent marks.
Let \(Q_{{j,k,l}}^{{new}}\) be the updated pedal mark of the \(kkth\) group of brown bears at the \(llth\) iteration, and let \(Q_{{j,k,l}}^{{old}}\) be the previous pedal mark of the same group at the same iteration. The term is a uniformly distributed random number in the range \(\left[ {0,1} \right]\) which corresponds to the \(kth\) pedal mark of the \(jth\) group of bears at the \(lth\) iteration. The occurrence factor \({\theta _l}\) for the \(lth\) iteration is defined as the ratio of the current iteration number to the total number of iterations and increases linearly with the number of iterations. \({D_{ite}}\) Is current iteration number.
Careful stepping characteristic: During the process of shifting from the first one third to the second one third of the total number of repetitions pedal marks are refreshed based on this feature. In fact this cautious stepping pattern of brown bears is basically to increase the visibility of relevant pedal marks. A brown bear tends to keep stepping over the previous pedal marks again and again for other members of its social group to recognize easily. This characteristic can be represented by a mathematical model as follows.
Let\(Q_{{k,;;}}^{{best}}\) and \(Q_{{k,;;}}^{{worst}}\)be the \(kth\) best and \(kth\) worst pedal scent marks in the all groups of brown bears respectively during the iteration number l. Then, the step factor of iteration number l, that is, \({G_l}\)can be defined using the occurrence factor \({\theta _l}\) as follows.
Let \({\beta _{1,l}}\) be an arbitrary uniformly distributed random number in the interval \(\left[ {0,1} \right]\) at the \(llth\) iteration. For this \(lth\) iteration consider a step size of\({M_l}\). This provides for adjusting the pedal marks based on what one knows about the best and worst pedal marks over the entire population. The length of steps \({M_l}\) can be either 1 or 2. According to the value of \({M_l}\) a male brown bear from the corresponding group slowly steps either forward or backward to make new pedal. \({\beta _{2,l}}\)Is the random number distributed range of\(\left[ {1,0} \right]\). Mathematically the step length \({M_l}\) is represented as follows.
Twisting feet characteristic: From the middle third of the cycles to the last cycle, the replacement of pedal marks is regulated by the twisting of feet characteristic. Every male brown bear in the group twists their feet into the depressions that they had created in the ground during the earlier stages. This helps them make strong pedal scent marks that they use later for other group members to construct a map of scents. The best and worst pedal marks are chosen based on the information extracted from all the marks. The angular velocity at which each male brown bear in a group twists its feet is expressed as
Let \(\:{\omega\:}_{j,l}\) be the \(\:jth\) angular velocity of the twist at the \(\:lth\) iteration. The quantity \(\:{\gamma\:}_{j,l}\) is uniformly distributed in the range\(\:\left[\text{0,1}\right]\). The brown bear twists its feet onto the best of the previous marks it is closest to the best pedal marks and avoids the worst pedal marks. The property is quantified using the following formula.
Sniffing behavior is mathematically describes the procedure when one generates two randomly selected candidate solutions selecting some movements for the bear with reference to that model follow as
Let \({Q_1}_{{n1,k1,l1}}^{{old}}\) denote the updated pedal mark of group number \(n1th\) which includes the bears in this \(kkth\) at iteration\(llth\). The terms \({Q_1}_{{n1,k1,l1}}^{{old}}\) and \(Q_{{p1,k1,l1}}^{{old}}\) represent the \(k1th\) pedal marks of \(n1th\) and \(p1th\) groups of bears at the \(l1th\) iteration respectively with\(n1 \ne p1\). Denote by \(g\left( {{Q_1}_{{n1,l1}}^{{old}}} \right)\) and \(g1\left( {{Q_1}_{{p1,l1}}^{{old}}} \right)\) the fitness function values for \(n1th\) and \(p1th\) groups of bears, respectively at the \(l1th\) iteration. Moreover \({\lambda _{k1,l1}}\) denotes a uniformly distributed random number within the range \(\left[ {0,1} \right]\) for the \(k1th\) pedal mark at the \(l1th\) iteration. Sniffing is the exploration phase of this algorithm. At this phase according to two randomly chosen vectors from the population of pedal marks the algorithm update the position vector of the pedal marks. This technique increases the exploration ability of an algorithm. The following algorithm illustrates the pseudo code for proposed bear optimization algorithm.

Algorithm 1: moBBO based optimal keys selection.
Furthermore, the moBBO algorithm is proposed to select the optimal keys for the encryption process. This algorithm efficiently balances multiple objectives, such as maximizing encryption strength, minimizing computational overhead, and ensuring scalability. By simulating the adaptive foraging behavior of brown bears, moBBO explores the solution space effectively, identifying keys that enhance the security and performance of the encryption process. This ensures robust, efficient and highly secure data encryption.
Partially homomorphic encryption named elgamal public key cryptosystem
In this proposed model used partially homomorphic encryption named ElGamal public key cryptosystem (PHElG) for authentication process. Optimization techniques can be employed to enhance the use of cryptosystem. One effective method is asymmetric key encryption that uses the Diffie-Hellman key exchange. This technique usually employs a private key is\(ux \in Kx_{{rx}}^{*}\) the corresponding public key as \(jx \equiv \left( {hx^{\prime}} \right)\bmod ri\)generated with the same algorithm, applying generator \(hx^{\prime}\) with prime\(rx^{\prime}\). The entire objective lies in this approach that modifies a new hybrid approach for optimal improvement of enhancing private key safety and offering guarantees related to safety features of keys it creates.
The encryption is \(nx\) be a message encrypted in the form of a pair \(d{x_{}},d{x_2}\)given by\(d{x_1} \equiv {(hx^{\prime})^o}\bmod rx,d{x_2} \equiv j{x^{rx}}nx\bmod rx\). Where \(jx\)the public is key and \(sx\) is some random number. In this case decryption can be made using the private key \(ux\) can be defined as\(nx \equiv d{x_1}{(dx_{1}^{{ux}})^{ - 1}}\bmod rx\).
Primarily this method ensures that an adversary even if a malicious one attempts to implement an elective plaintext attack on the same plaintext shall have the same cipher text output. Moreover, when attempting to distinguish between two encrypted messages at random this is only marginally superior to a random guess. It will be much easier for one to understand this argument with the use of games by considering an ElGamal cryptosystem (ELGC) with a challenger \(Dx\) and adversaries\(Bx.\)
-
Initially, \(Bx\) picks two distinct messages as \(n{x_0},n{x_1} \in H{x_1}\) and pass it to \(Dx^{\prime}\).
-
Thereafter this method determine as \(Dx^{\prime}\) selects \(bx \in \left\{ {0,1} \right\}\) and \(s{x_1},ux \in Kx_{{rx^{\prime}}}^{*}\) randomly and places \(jx \equiv {(hx^{\prime})^{ux}}\bmod rx,dx \equiv {(gx^{\prime})^{sx}}\bmod rx\) and\(d{x_2} \equiv {(hx^{\prime})^{sxux}}n{x_{bx}}\bmod rx\). Also, \(Dx^{\prime}\)provides \(Cx\) as\(hx^{\prime},jx,d{x_1}d{x_2}\).
-
Execute challenges is \(Dx^{\prime}\) requests \(Bx\) respect to\(bx\).
-
Consider identify as \(Bx\)offers \(bx^{\prime}\) and onward it returns to\(Dx^{\prime}\).
Right now \(Bx\)got success later than \(bx^{\prime}=bx\)else false. Therefore, the proceeding game consider \(Bx\) recognize \(hx^{\prime},{(hx^{\prime})^{ux}},{(hx^{\prime})^{sx}}\) and yet \(Bx\) not get correct access to \(ux\) as\(sx^{\prime}\). A probabilistic polynomial time adversary \(Bx\) has trivially enhanced success potential in obtaining\(bx\). Precisely in comparison to an arbitrary guess for which the equation. In Eq. (7) \(Qx\) is success probability, \(nel\) is trivial enhancement. The working process of partially homomorphic encryption named ElGamal public key cryptosystem show in Fig. 3.
The data frame is made to hold a lesser sophisticated design with enough strength that ensures constant communication on noisy channels. Design this involves successive protocol layers on the frame with accurate headings and footers. The data frame is made of the data payload and this is the encrypted data. Thus encryption is the process that makes the data into cipher text through use of private keys to decrypt broadcasting it out there. Conversely at the receiving side decryption would take the cipher text hence returning one to the information being decrypted.
Partially Homomorphic Encryption (PHE) allows for an operation to be executed an unlimited number of times. In the context of PHE a straightforward algorithm can be additively homomorphic meaning it can perform addition by yielding the same outcome when adding two cipher texts as when encrypting the sum of the corresponding plaintexts. Consequently the multiplication of two cipher texts encrypted with the same key corresponds to raising the product of the original plaintexts to the power of the secret key.
In this system is introduce the cryptosystem a public key system that can be used for privacy-preserving distributed optimal power flow (DOPF). The cryptosystem is divided into three primary operations key generation, encryption and decryption. In the process of key generation, it creates a public key and private key. The public key is publicly shared among all the agents to encrypt messages. Only the system operator or one agent keeps the private key in secret and uses it to decrypt messages. Notably both keys are time-varying. The cryptosystem is provided through three functions Keygen () for key generation, \(dc=\varepsilon \left( {nn} \right)\) for encryption and \(nn=E\left( {dc} \right)\) for decryption. The most important feature of the system is its additive homomorphism; it can directly obtain the cipher text of the sum of two messages \(\left( {n{n_1}+n{n_2}} \right)\) from the cipher texts of individual messages \(n{n_1}\)and\(n{n_2}.\)
The objective function is designed to convert the cipher text into numerical values for minimizing the penalty, and this is crucial in order to achieve better performance with partial homomorphic encryption. It uses the private key of the ElGamal cryptosystem to produce an elaborate cipher text. It is supposed to produce a cipher text with only numerical values rather than a combination of special characters alphabets and numbers. A penalty system is established where a penalty of \(0\left( 2 \right)\) is assigned when the cipher text is in numerical values and a reduced penalty is applied when special characters and alphabets are present. The ultimate goal is to minimize this penalty, as expressed in Eq. (22) such that the cipher text is in numerical values.
The PHElG algorithm supports certain mathematical operations directly on encrypted data. Specifically, it exhibits multiplicative homomorphism, meaning that the product of two ciphertexts decrypts to the product of their corresponding plaintexts. This property makes ElGamal particularly useful in secure computations and applications like electronic voting and secure multiparty computations, where operations on encrypted data are required without revealing the plaintext.
Results and discussion
The implementation of the research model is done by using the python language and evaluated using multiple metrics.
Dataset acquisition
In the evaluation, the Cleveland and Hungary dataset is used as a input data for analyzing the security framework. The dataset which was extracted from the UCI repository and contains 303 distinct data points. The dataset consists of 14 columns that were taken from a total of 75 where no values are missing. Predicting whether or not a person has heart disease is the categorization task (1: presence, 0: absence). There are thirteen attributes and a target variable in this database with five numerical values and eight nominal values. These data are further processed by the proposed framework to show the efficiency in security26.
Performance analysis and evaluation
The proposed model is implemented using python and the hardware system having configuration of Intel(R) Core(TM) i5-9500 CPU @ 3.00 GHz 3.00 GHz processor and 16GB RAM. The type of the system is 64-bit operating system, x64-based processor with Windows 11 pro edition. The proposed security framework is evaluated to show the efficiency of the model in IoMT environment using several metrics called, accuracy, latency, encryption and decryption time etc. Initially, the accuracy analysis of proposed model is depicted in the Fig. 4.
The proposed model scored higher than the other existing model. For comparison the existing models like CryptoNets, Lola, A*FV, Lite crypt1, Lite crypt2, Lite crypt3 are taken27. The existing model consumes 98.95%, 98.95%, 98.95%, 99.14%, 99.14% and 90.06% accuracy respectively. Moreover, the proposed model is achieved 99.28 accuracy which is higher as compared to the existing encryption models. The model could better ensure that users trust and adopt in privacy-sensitive environments. The latency analysis of proposed model compared to existing security framework is show in Fig. 5.
The proposed model scored less latency as compared to the other existing model. The existing model possess 20.5s, 2.2s, 5.16s, 0.46s, 0.016s and 0.016s latency respectively. Moreover, the proposed model is 0.008s latency which is higher as compared to the existing encryption models. The optimal key selection using the brown bear optimization decrease the complexity in key selection and encryption computation which simultaneously reduce the delay of the process. Overall performance of proposed model when compared to existing framework is demonstrated in the Fig. 6.
The proposed model possesses high score as compared to the other existing model in terms of accuracy, precision and recall. The comparison models taken for comparison are LMDS, LMAKA, PiRATE, PRER and DDTHA + ACO28. The proposed model possess 99.28% accuracy while the existing model possess 63.8%, 54.6%, 72.3%, 82.9% and 93.6% accuracy respectively. Similarly, the proposed model attained high precision and recall about 98.9% and 99.2%. Meanwhile the existing models possess 58.2%, 67.6%, 76.2%, 85.6% and 96.2% of precision score and 60.01%, 71.3%, 79.6%, 89.6% and 98.2% of recall respectively. The high performance of proposed model is acquired by the Good and bad groups-based optimizer which optimize the hash values. The specificity performance of proposed model when compared to existing framework is displayed in the Fig. 7.
The proposed model possesses high specificity score as compared to the other existing models. The proposed model possesses 99.17% specificity while the existing model possess 91.26%, 88.12%, 82.5%, 82.44% and 97.5% specificity when varying the data respectively. This substantial improvement highlights the robustness and reliability of the proposed model in handling diverse data conditions. Its high specificity ensures minimal false positives, making it a more effective solution for real-world applications. The Encryption time evaluation of proposed model is compared with existing framework and represented in the Fig. 8.
The proposed model possesses less encryption time as compared to the other existing models. The encryption time of proposed model is 40.537s, 42.592s, 43.937s, 44.387s and 46.446s when varying data. Meanwhile the existing model possess 97.848s, 89.607s, 79.58s, 69.727s and 55.046s when varying the data respectively. The time is minimized by the standard data processing achieved by concept hierarchy. The decryption time evaluation of proposed model is compared with existing framework and represented in the Fig. 9.
The proposed model possesses less decryption time as compared to the other existing models. The decryption time of proposed model is 33.243s, 34.611s, 36.941s, 39.917s and 45.628s when varying data. Meanwhile the existing model possess 92.761s, 79.894s, 71.205s, 60.267s and 43.217s in the initial data variation respectively. This substantial reduction in decryption time highlights the proposed model’s superior optimization making it more suitable for time-critical applications. Execution time evaluation of proposed model is compared with existing framework and shown in the Fig. 10.
The proposed model possesses less execution time as compared to the other existing models. The execution time of proposed model is 42.82s, 43.49s, 44.97s and 48.47s when varying data. Meanwhile the existing model possess higher execution time up to 95.65s due to their complex framework. Here, the proposed framework possess multiple optimization and lightweight hash function to minimize the processing time which decrease the execution time. Energy consumption of proposed model compared to existing security framework shown in the Fig. 11.
The proposed model less energy as compared to the other existing models. The energy consumption of proposed model is 49.867% when varying data. Meanwhile the existing model consume 74.8%, 65.333%, 90%, 88% and 60% energy respectively. This notable reduction in energy usage highlights the proposed model’s optimization and makes it highly suitable for resource-constrained environments, enhancing its practicality for real-world applications. Further evaluation of proposed model is made in terms of computation and communication time which is given in the Table 2.
The proposed model possesses less communication and computational time also communication overhead due to the optimal processing of encryption process by PHElG that use the optimal key chosen from moBBO approach. Overall, the proposed model proves to be lightweight and highly efficient across all evaluated metrics making it a strong contender against existing security frameworks.
Limitations
The proposed ESHA-256_GBGO security framework was evaluated on real-world IoMT datasets, demonstrating significant improvements in encryption efficiency, computational overhead, and latency. The model achieved 98.76% encryption efficiency, reducing computational overhead by 27.4% while maintaining low latency of 12.11s and 10.14s across different datasets. Compared to conventional security models like AES-256, RSA and SHA-512, the proposed approach enhances data security, reduces processing time and optimizes resource utilization, making it well-suited for real-time IoMT applications. Despite its advantages, the framework exhibits certain limitations that must be considered. In large-scale IoMT networks, the encryption process may introduce slight latency due to the increased number of connected devices. Additionally, the model’s performance may vary depending on the dataset structure which necessitates further evaluation across diverse IoT applications. To address these challenges, future research will explore edge computing integration, adaptive encryption mechanisms and blockchain-based authentication to further real-time adaptability and security resilience.
Discussion
Existing surveys highlight several challenges and limitations in current methodologies for securing healthcare systems and data. Kanneboina et al.24 proposed a hybrid metaheuristic model to improve network consistency, but it lacked adaptability to evolving cyber threats. Mani et al.25 introduced a hybrid GarraRufa Fish Optimization and Nomadic People Optimizer, reducing delay by 29.8%, yet suffered from lower security levels and high resource consumption. Veeramakali et al.26 developed ODLSB, which achieved good sensitivity, specificity, and accuracy but struggled with centralized architectures and security vulnerabilities. Ramani et al.27 proposed ODMSM-FL, improving transaction throughput and block processing time, but it showed performance and security limitations in IoMT frameworks.
Praveena Anjelin et al.28 utilized CNN-based models, enhancing accuracy and complexity, but false alarms remained a concern, increasing susceptibility to cyber threats. These limitations highlight the need for a comprehensive security framework that ensures adaptability, efficiency, and resilience against evolving cyber risks in IoMT networks. To overcome these challenges, the proposed model integrates a multi-step security framework that enhances data confidentiality, integrity, and adaptability to emerging threats. Healthcare data is first preprocessed using a concept hierarchy generation technique, which reduces dimensionality while preserving essential information, allowing for multilevel analysis and improved interpretability. Following this, digital certificates are employed to authenticate user data, ensuring secure communication and identity verification. Unsigned digital certificates undergo enhanced cryptographic hashing using ESHA-256, which is further optimized by GBGO, improving the efficiency and security of the hashing process. Unlike traditional hashing techniques, GBGO dynamically adjusts hashing parameters, enhancing data integrity without increasing computational overhead.
To strengthen data confidentiality and authentication, the model incorporates Public Homomorphic PHElG, providing efficient encryption while maintaining scalability. Additionally, the moBBO algorithm is integrated to generate optimal encryption keys, ensuring maximum security with minimal resource utilization. The key optimization process dynamically adjusts to system requirements, reducing the risk of key leakage and unauthorized access. This comprehensive security approach directly addresses the limitations of existing models by Enhancing adaptability to emerging threats using optimized cryptographic operations. Reducing resource utilization through lightweight hashing and encryption mechanisms. Improving centralized and distributed security by securing authentication, data integrity, and encryption. Eliminating false alarms by leveraging adaptive security policies and optimized key management.
By combining robust preprocessing, optimized hashing, encryption, and key generation techniques, the proposed ESHA-256_GBGO security framework provides a scalable, efficient, and highly secure solution for protecting sensitive healthcare data while ensuring maximum privacy and real-time adaptability. Table 3 presents a detailed evaluation of computational performance across various security algorithms. The proposed model outperforms traditional methods in encryption speed and resource efficiency.
Applications in a high-performance and optimized security framework for the internet of medical things (IoMT)
The proposed framework introduces a robust and optimized security solution for the IoMT addressing critical concerns such as data privacy, authentication, and performance efficiency. Initially, healthcare information is preprocessed using a concept hierarchy generation technique which reduces the dimensionality of data and enhances interpretability, enabling efficient multilevel analysis of IoMT data. This preprocessing ensures that only relevant and concise information is processed for subsequent stages. To authenticate the data, digital certificates are utilized to verify user credentials. For unsigned digital certificates, the data is hashed using the ESHA-256. The efficiency of the hashing process is further optimized through the GBGO algorithm, which ensures secure and reliable hashing with reduced computational overhead.
Once authenticated, the signed digital certificates are encrypted using the PHElG to secure sensitive medical data while maintaining the ability to perform certain operations on encrypted data. Additionally, the framework employs the moBBO algorithm to generate optimal encryption keys. These keys are critical for ensuring maximum data security and privacy during the encryption process while minimizing computational resource usage. By integrating advanced preprocessing, authentication, hashing, encryption, and key optimization, this high-performance framework addresses the unique challenges of IoMT, ensuring secure, efficient, and scalable data management in healthcare systems. This approach safeguards patient data from unauthorized access, improves data integrity, and provides a strong foundation for future IoMT applications.
Conclusion
The research concludes a novel security framework for enhancing the privacy in the IoMT environment. The proposed framework used the concept hierarchical approach to provide a cleaned data for processing security measures. The data is initially hashed with help of ESHA-256 approach which used the chaotic map for reducing the complexity and encourage the security of data. The parameters of hash function is optimized by GBGO which reduce the convergence time and provide optimal hash values. The data is then encrypt by proposed PHElG approach which uses the keys that selected by the optimization. The random selection of key enhances the scalability and robustness of the framework. In the evaluation, the accuracy attained by the proposed model is 99.28% where the computation time and communication overhead are 7.4 ms and 10.23 ms respectively. Among the advancement, the proposed possess a challenge in which is overcome by introducing novel security algorithm in the Future studies.
Data availability
The data(s) used to support this study is publicly available in the following website: https://www.kaggle.com/datasets/ritwikb3/heart-disease-cleveland.
References
Wang, J. & Wang, L. A computing resource allocation optimization strategy for massive internet of health things devices considering privacy protection in cloud edge computing environment. J. Grid Comput. 19(2), 17 (2021).
Manimurugan, S. et al. Effective attack detection in internet of medical things smart environment using a deep belief neural network. IEEE Access. 8, 77396–77404 (2020).
Dubey, K. S., Sharma, C. & Kumar, M. A secure IoT applications allocation framework for integrated fog-cloud environment. J. Grid Comput. 20(1), 5 (2022).
Chen, C. M., Chen, Z., Kumari, S. & Meng-Chang, L. LAP-IoHT: a lightweight authentication protocol for the internet of health things. Sensors 22(14), 5401 (2022).
Chen, F. et al. Medical cyber–physical systems: a solution to smart health and the state of the Art. IEEE Trans. Comput. Social Syst. 9(5), 1359–1386 (2021).
Ahmad, S., Arif, M., Ahmad, J., Nazim, M. & Mehfuz, S. Convergent encryption enabled secure data deduplication algorithm for cloud environment.Concurr. Comput. Pract. Exp. 36(21), e8205 (2024).
Mishra, L., Vikash, L. & Varma, S. Seamless health monitoring using 5G NR for internet of medical things. Wirel. Pers. Commun. 120(3), 2259–2289 (2021).
Tahir, B., Jolfaei, A. & Tariq, M. A novel experience-driven and federated intelligent threat-defense framework in IoMT. IEEE J. Biomed. Health Inf. (2023).
Kumar, P. et al. AI-Optimized hardware design for Internet of Things (IoT) devices. In 5th International Conference on Recent Trends in Computer Science and Technology (ICRTCST) 21–26 (IEEE, 2024).
Aminizadeh, S. et al. The applications of machine learning techniques in medical data processing based on distributed computing and the internet of things. Comput. Methods Programs Biomed. 2023, 107745 (2023).
Cheng, X., Chen, F., Xie, D., Huang, C. & Hui, S. Design of a secure medical data sharing scheme based on blockchain. J. Med. Syst. 44(2), 52 (2020).
Ahmad, S., Mehfuz, S. & Beg, J. An efficient and secure key management with the extended convolutional neural network for intrusion detection in cloud storage. Concurr. Comput.: Pract. Exp. 35, 23 (2023).
Ahmad, S., Mehfuz, S., Urooj, S. & Najah Alsubaie. Machine learning-based intelligent security framework for secure cloud key management. Cluster Comput. 27(5), 5953–5979 (2024).
Sun, Z., An, G., Yang, Y. & Liu, Y. Optimized machine learning enabled intrusion detection 2 system for internet of medical things. Frankl. Open. 6, 100056 (2024).
Ahmad, S., Mehfuz, S. & Beg, J. Cloud security framework and key management services collectively for implementing DLP and IRM. Mater. Today: Proc. 62, 4828–4836 (2022).
Hamid, N. A. W. & Abdul, B. S. High-Performance computing based operating systems, software dependencies and IoT integration. In High Performance Computing in Biomimetics: Modeling, Architecture and Applications 175–204 (Springer Nature Singapore, 2024).
Gupta, D., Kayode, O., Bhatt, S., Gupta, M. & Ali, S. T. Hierarchical federated learning based anomaly detection using digital twins for smart healthcare. In 2021 IEEE 7th International Conference on Collaboration and Internet Computing (CIC) 16–25 (IEEE, 2021).
Yang, T. et al. Secure and traceable multikey image retrieval in cloud-assisted internet of things. IEEE Internet Things J. (2024).
Ghoumid, K., Ar-Reyouchi, D., Benbrik, J., Boukricha, S. & Elmazria, O. Optimization analysis of average message delivery time for healthcare monitoring using a developed NB-IoT technology in a smart City. Internet Things 27, 101290 (2024).
Khan, M., Ayoub, M. T., Quasim, N. S. A. & Mohammad, Y. K. A secure framework for authentication and encryption using improved ECC for IoT-based medical sensor data. IEEe Access 8, 52018–52027 (2020).
Yang, Y., Chen, Y., Liu, Z., Tan, C. & Luo, Y. Verifiable and redactable blockchain for internet of vehicles data sharing. IEEE Internet Things J. (2024).
Garg, N. et al. BAKMP-IoMT: design of blockchain enabled authenticated key management protocol for internet of medical things deployment. IEEE Access. 8, 95956–95977 (2020).
HaddadPajouh, H., Khayami, R., Dehghantanha, A., Choo, K. K. R. & Reza, M. P. AI4SAFE-IoT: an AI-powered secure architecture for edge layer of internet of things. Neural Comput. Appl. 32(20), 16119–16133 (2020).
Kanneboina, A. & Sundaram, G. Improving security performance of internet of medical things using hybrid metaheuristic model. Multimedia Tools Appl. 2024, 1–26 (2024).
Mani, A., Kavya, G. & Tapas Bapu, B. R. A proficient resource allocation using hybrid optimization algorithm for massive internet of health things devices contemplating privacy fortification in cloud edge computing environment. Wirel. Netw. 30(3), 1187–1199 (2024).
Veeramakali, T., Siva, R., Sivakumar, B., Senthil Mahesh, P. C. & Krishnaraj, N. An intelligent internet of things-based secure healthcare framework using blockchain technology with an optimal deep learning model. J. Supercomput. 77(9), 9576–9596 (2021).
Ramani, R., Rosline Mary, A., Edwin Raja, S. & Arun Shunmugam, D. Optimized data management and secured federated learning in the internet of medical things (IoMT) with blockchain technology. Biomed. Signal Process. Control 93, 106213 (2024).
Praveena Anjelin, D. & Ganesh Kumar, S. An effective classification using enhanced elephant herding optimization with Convolution neural network for intrusion detection in IoMT architecture. Cluster Comput. 2024, 1–19 (2024).
Ahmad, S. & Mehfuz, S. Efficient time-oriented latency-based secure data encryption for cloud storage. Cyber Secur. Appl. 2, 100027 (2024).
Alsaeed, N., Nadeem, F. & Albalwy, F. A scalable and lightweight group authentication framework for internet of medical things using integrated blockchain and fog computing. Future Gener. Comput. Syst. 151, 162–181 (2024).
Hassan, B. A., Tarik, A. R. & Mirjalili, S. Formal context reduction in deriving concept hierarchies from corpora using adaptive evolutionary clustering algorithm star. Complex. Intell. Syst. 7(5), 2383–2398 (2021).
Henderi, H., Wahyuningsih, T. & Rahwanto, E. Comparison of Min-Max normalization and Z-Score normalization in the K-nearest neighbor (kNN) algorithm to test the accuracy of types of breast cancer. Int. J. Inf. Inform. Syst. 4(1), 13–20 (2021).
Sadeghi, A. et al. A new good and bad Groups-Based optimizer for solving various optimization problems. Appl. Sci. 11(10), 4382 (2021).
Tran, T. H., Hoai, L. P. & Nakashima, Y. A high-performance multimem SHA-256 accelerator for society 5.0. IEEE Access. 9, 39182–39192 (2021).
Sorour, S. E., Khalied, M., AlBarrak, A. A. & Abohany, A. E. Credit card fraud detection using the brown bear optimization algorithm. Alexandria Eng. J. 104, 171–192 (2024).
https://www.kaggle.com/datasets/ritwikb3/heart-disease-cleveland (2024).
Xie, Q. et al. LiteCrypt: enhancing IoMT security with optimized HE and lightweight dual-authorization. In 2024 IEEE 30th International Conference on Parallel and Distributed Systems (ICPADS) 166–175 (IEEE, 2024).
Al Shahrani, A. M. et al. An internet of things (IoT)-based optimization to enhance security in healthcare applications. Math. Probl. Eng. 1, 6802967 (2022).
Author information
Authors and Affiliations
Contributions
All the authors contributed to this research work in terms of concept creation, conduct of the research work, and manuscript preparation.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Murugan, G., Chinnadurai, M. ESHA-256_GBGO: a high-performance and optimized security framework for internet of medical thing. Sci Rep 15, 9576 (2025). https://doi.org/10.1038/s41598-025-94345-y
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-94345-y