Abstract
Quantum secret sharing is a basic quantum cryptographic primitive, which plays an important role in robust key management and secure multiparty computation etc. In this work, we give a cryptanalysis of efficient controlled semi-quantum secret sharing protocol with entangled states proposed recently, which shows that the controller can recover the secret if he cooperates with any one participant. Furthermore, an external opponent can make participants recover a false secret without being detected by a special denial-of-service attack. Therefore, this protocol does not satisfy the security requirement that any unauthorized set can gain access to no information on the secret and cannot guarantee its correctness.
Similar content being viewed by others
Introduction
In 1979, the concept of secret sharing was firstly introduced by Shamir1 and Blakely2 independently, which allowed just authorized sets can recover the dealer’s secret, but unauthorized sets can learn no information on it. As a building block, secret sharing was often used to construct robust key management, secure multiparty computation, threshold digital signature and so on, which can function securely and reliably even when misfortunes destroy most of the shares and security breaches expose all but one of the remaining shares3,4,5.
In quantum cryptographic domain, Hillery et al introduced the concept of quantum secret sharing (QSS) and gave the first QSS protocol based on Greenberger-Horne-Zeilinger entangled states in 19996. In contrast to classical secret sharing, QSS is secure even against the opponents with powerful computing resources. Accordingly, QSS has attracted much attention and many proposals were reported one after another7,8,9,10,11,12,13,14,15,16. However, quantum resources and capabilities are not readily available to ordinary people in reality. In order to make QSS more practical, Li et al presented a semi-quantum secret sharing protocol using entangled states, which requires only quantum users to have full quantum capability, while the other participants are classical participants with limited quantum capability17. In 2012, a semi-quantum secret sharing protocol based on two-particle entangled state was proposed by wang et al, in which quantum Alice shares a secret key with two classical participants Bob and Charlie18. Instead of entangled states, Li et al proposed a new semi-quantum secret sharing protocol based on two-particle product states19. At the same time, a new construction of semi-quantum secret sharing was given, in which only 2nm qubits are required to produce an n-bit secret key in the (\(m+1\))-party protocol20. Subsequently, semi-quantum secret sharing continued to be concerned21,22,23,24. Especially, a controlled semi-quantum secret sharing protocol (named HHH-protocol hereafter) with entangled states was proposed recently, which achieves a lower cost by reducing returning qubits and entangled state measurement25.
In this work, we analyzed the HHH-protocol’s security and propose two new attacks (participant attack and denial-of-service attack). Using the first attack, the controller can recover the secret with just one participant’s cooperation. Using the second attack, an external opponent can make participants fail to recover the secret correctly. Therefore, the HHH-protocol does not satisfy the security requirement for secret sharing. In the end, we discuss how to resist these attacks.
Results
The HHH-protocol
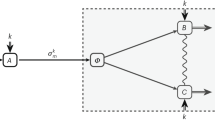
Before presenting the cryptanalysis, let us firstly give a brief description of HHH-protocol. For simplicity, we take participants to share one-bit message as an example. Assume that quantum user Alice wants to share a secret bit \(m_{A}\) with n classical users \(\hbox {Bob}_{{1}}\), \(\hbox {Bob}_{{2}}\), ..., \(\hbox {Bob}_{{n}}\), where \(\hbox {Bob}_{{1}}\) has limited quantum capabilities and the other \(n-1\) classical users can only perform Z-basis measurement. This protocol can be described as follows25.
-
(1)
Alice prepares L entangled states, each of which is denoted as
$$\begin{aligned}&|\varphi \rangle _{a_{1}a_{2}b_{1}\cdots b_{n}}=\frac{1}{2}[|000\rangle |0\rangle ^{\otimes n-1}+|010\rangle |1\rangle ^{\otimes n-1}\nonumber \\&+|101\rangle |0\rangle ^{\otimes n-1}+|111\rangle |1\rangle ^{\otimes n-1}]_{a_{1}a_{2}b_{1}\cdots b_{n}} \end{aligned}$$(1)where \(a_{1},a_{2},b_{1},\cdots ,b_{n}\) denotes \(n+2\) particles of the entangled state \(|\varphi \rangle _{a_{1}a_{2}b_{1}\cdots b_{n}}\), respectively. The particles of L entangled states are defined as \([P_{a_{1}a_{2}b_{1}\cdots b_{n}}^{1},P_{a_{1}a_{2}b_{1}\cdots b_{n}} ^{2},\cdots ,P_{a_{1}a_{2}b_{1}\cdots b_{n}}^{L}]\). Then she divides these particles into \(n+1\) sequences \(S_{A},S_{B_{1}},S_{B_{2}},\cdots ,S_{B_{n}}\), here \(S_{A}\) contains all the first two particles \(a_{1}a_{2}\) of L entangled states and \(S_{B_{i}}\) constitutes of all the particles \(b_{i}\) of L entangled states for \(i=1,2,\dots ,n\), i.e.,
$$\begin{aligned}&S_{A}=&(P_{a_{1}}^{1}P_{a_{2}}^{1},P_{a_{1}}^{2}P_{a_{2}}^{2},\cdots ,P_{a_{1}}^{L}P_{a_{2}}^{L})\\&S_{B_{1}}=&(P_{b_{1}}^{1},P_{b_{1}}^{2},\cdots ,P_{b_{1}}^{L})\\&S_{B_{2}}=&(P_{b_{2}}^{1},P_{b_{2}}^{2},\cdots ,P_{b_{2}}^{L})\\&\vdots \\&S_{B_{n}}=&(P_{b_{n}}^{1},P_{b_{n}}^{2},\cdots ,P_{b_{n}}^{L}) \end{aligned}$$For each entangled state, Alice holds the first and second qubits in her hands and randomly performs two unitary operations (H or I) on every particles of the randomly selected groups that are used to check the security of the quantum channels. Finally, Alice sends \(S_{B_{i}}\) to \(\hbox {Bob}_{{i}}\) for \(i=1,2,\dots ,n\).
-
(2)
When all users have reported that they have received the sequences \(S_{B_{1}},S_{B_{2}},\cdots ,S_{B_{n}}\), Alice announces the order of the particles. According to Alice’s announcement, \(\hbox {Bob}_{{i}}\) chooses these particles, and then \(\hbox {Bob}_{{2}}\), \(\hbox {Bob}_{{3}}\), \(\cdots\) , \(\hbox {Bob}_{{n}}\) measures them with Z-basis, and \(\hbox {Bob}_{{1}}\) randomly chooses either to measure the particle with Z-basis or to return it to Alice without any modification. When Alice receives the particle from \(\hbox {Bob}_{{1}}\), she measures it that depends on her choice. She uses the Z-basis to measure her particle and the received particle if she performs an I-operation on the particle in the preparation phase; otherwise, she uses the X-basis. The measurement outcomes should be correlated according to the Table 1 in25. If the error rate exceeds a predefined threshold, the protocol is aborted; otherwise, it continues.
-
(3)
Alice determines her specific information and measures the two particles \(a_{1}a_{2}\) held by her. Based on her measurements, she asks \(\hbox {Bob}_{{1}}\) to act as a controller and performs an appropriate unitary-operation on his particle according to the Table 2 in25.
-
(4)
All users \(\hbox {Bob}_{{1}}\), \(\hbox {Bob}_{{2}}\), ..., \(\hbox {Bob}_{{n}}\) respectively measure their own particles, and then recover Alice’s secret by performing an OR operation on the results \(r_{B_{1}}, r_{B_{2}}, \dots , r_{B_{n}}\) if they cooperate with each other, i.e.,
$$\begin{aligned} m_{A}=r_{B_{1}}\oplus r_{B_{2}}\oplus \cdots \oplus r_{B_{n}}. \end{aligned}$$(2)
Cryptanalysis of HHH-protocol
As we know, cryptanalysis is opposite but accelerative to cryptographic design, and therefore it is also indispensable to the development of cryptography. This is also the case for quantum cryptography26,27,28. However, it is not easy to analyze the security of multiparty quantum cryptographic protocols especially for QSS. This is because multiple participants are involved and some may cheat. Furthermore, the security of QSS requires that only authorized sets of agents can recover the secret distributed by the dealer, but unauthorized sets can get no information on it29,30,31,32. However, here we show that the HHH-protocol does not satisfy this requirement. Furthermore, an external opponent can make participants fail to recover the real secret without being detected.
As claimed in the HHH-protocol25, the secret can only be recovered by the cooperation of all classical users \(\hbox {Bob}_{{1}}\), \(\hbox {Bob}_{{2}}\), \(\cdots\) , \(\hbox {Bob}_{{n}}\), which means that the HHH-protocol is actually a (n, n) threshold QSS protocol. Therefore, the HHH-protocol has just one authorized set, i.e., {\(\hbox {Bob}_{{1}}\), \(\hbox {Bob}_{{2}}\), \(\cdots\) , \(\hbox {Bob}_{{n}}\)}, who can recover the secret \(m_{A}\) if and only all of them cooperate with each other in Step 4. In the semi-quantum HHH-protocol, \(\hbox {Bob}_{{2}}\), \(\hbox {Bob}_{{3}}\), \(\cdots\) , \(\hbox {Bob}_{{n}}\) are classical and \(\hbox {Bob}_{{1}}\) is required to have only limited quantum capabilities, which makes it more practical, but it also gives a good chance for opponents to launch attacks, which can be shown in Theorems 1 and 2.
Theorem 1
An unauthorized set {\(\hbox {Bob}_{{1}}\), \(\hbox {Bob}_{{i}}\)} can recover the secret \(m_{A}\) in the HHH-protocol, where \(1<i\le n\).
Proof.
From Eq. (2), it can be seen that all the n sub-secrets \(r_{B_{1}}, r_{B_{2}}\), ..., \(r_{B_{n}}\) are essential to recover the secret \(m_{A}\). Nevertheless, we can find that the measurement results of \(\hbox {Bob}_{{2}}\), \(\hbox {Bob}_{{3}}\), \(\cdots\) , and \(\hbox {Bob}_{{n}}\) are always the same in the Table 2, i.e.,
which means that any user \(\hbox {Bob}_{{i}}\) can deduce the other \(n-2\) users’ measurement results by virtue of his own. Therefore, if \(\hbox {Bob}_{{1}}\) cooperates with \(\hbox {Bob}_{{i}}\), they can recover the secret \(m_{A}\) by computing
The proof of Theorem 1 is completed.
Theorem 2
An external opponent Eve can make the users fail to recover the real secret \(m_{A}\) without being detected in the HHH-protocol.
Proof.
Without loss of generality, we take two users’ case as an example, i.e., there are three players Alice, \(\hbox {Bob}_{{1}}\), \(\hbox {Bob}_{{2}}\) in the HHH-protocol. In Step (1), when Alice sends the particle sequence \(S_{B_{2}}\) to \(\hbox {Bob}_{{2}}\), Eve intercepts it. For each particle \(P_{b_{2}}^{j}\) \((j=1,2,\dots ,L)\) of the sequence \(S_{B_{2}}\), Eve performs a CNOT operation on \(P_{b_{2}}^{j}\) and an auxiliary particle \(|0\rangle _{e}^{j}\) prepared in advance, where the particle \(P_{b_{2}}^{j}\) is control qubit and the auxiliary particle \(|0\rangle _{e}^{j}\) is target qubit, and
i.e., \(\texttt {CNOT}|00\rangle =|00\rangle\), \(\texttt {CNOT}|01\rangle =|01\rangle\), \(\texttt {CNOT}|10\rangle =|11\rangle\), \(\texttt {CNOT}|11\rangle =|10\rangle\). After this operation, the jth entangled state \(|\varphi \rangle ^{j}_{a_{1}a_{2}b_{1}b_{2}}\) and the auxiliary particle \(|0\rangle _{e}^{j}\) evolve in the state
From Eqs.(1) and (5), we can find that the state \(|\varphi \rangle _{a_{1}a_{2}b_{1}b_{2}e}\) is the same as that in the three users’ case, that is to say, Eve is equivalent to a new legal user. Furthermore, the auxiliary particle \(|0\rangle _{e}^{j}\) does not change the correlation among the four particles \(P_{a_{1}}^{j},P_{a_{2}}^{j},P_{b_{1}}^{j},P_{b_{2}}^{j}\) under the original operation and measurement, which means that the measurement results of the four particles \(P_{a_{1}}^{j},P_{a_{2}}^{j},P_{b_{1}}^{j},P_{b_{2}}^{j}\) also satisfy the 12 correlations in the Table 1. For example, the original measurement results of the four particles \(P_{a_{1}}^{j},P_{a_{2}}^{j},P_{b_{1}}^{j},P_{b_{2}}^{j}\) with Z-basis will be \(|0000\rangle _{a_{1}a_{2}b_{1}b_{2}},|0101\rangle _{a_{1}a_{2}b_{1}b_{2}},|1010\rangle _{a_{1}a_{2}b_{1}b_{2}},|1111\rangle _{a_{1}a_{2}b_{1}b_{2}}\) without Eve, but the measurement results of the four particles \(P_{a_{1}}^{j},P_{a_{2}}^{j},P_{b_{1}}^{j},P_{b_{2}}^{j}\) with Z-basis will also be \(|0000\rangle _{a_{1}a_{2}b_{1}b_{2}},|0101\rangle _{a_{1}a_{2}b_{1}b_{2}},|1010\rangle _{a_{1}a_{2}b_{1}b_{2}},|1111\rangle _{a_{1}a_{2}b_{1}b_{2}}\) when Eve entangles an auxiliary particle \(|0\rangle _{e}^{j}\). Therefore, Eve’s intercept-resend attack will introduce no error and hence can avoid the security check in Step (2). More importantly, when the security check is completed, she immediately measures the remaining auxiliary particles with X-basis.
Because
the four particles \(P_{a_{1}}^{j},P_{a_{2}}^{j},P_{b_{1}}^{j},P_{b_{2}}^{j}\) will collapse to one of the eight states \(|++++\rangle ,|+++-\rangle ,|+-++\rangle ,|+-+-\rangle ,|-+-+\rangle ,|-+--\rangle ,|-+-+\rangle ,|----\rangle\) according to Eve’s measurement result. When \(\hbox {Bob}_{{1}}\) and \(\hbox {Bob}_{{2}}\) measure their particles \(P_{b_{1}}^{j},P_{b_{2}}^{j}\) with Z-basis in Step (4), they will get a random result \(|0\rangle\) or \(|1\rangle\), which cannot satisfy the correlation in the Table 2 any longer. As a result, the users will recover a random bit, which is equal to \(m_{A}\) with the probability 50%. The proof of Theorem 2 is completed.
Obviously, the denial-of-service attack can also be performed by any participant \(\hbox {Bob}_{{j}}\) for \(j=1,2,\dots ,n\) and easily generalized to multiparty (\(n\ge 3\)) case. Furthermore, the above two attacks are also valid to the extension version of HHH-protocol with just simple repetitive operations.
Discussion
From the above cryptanalysis, it can be seen that the success of the first attacks is for the entangled state \(|\varphi \rangle\) has a special characteristic, which makes the \(n-1\) agents (\(\hbox {Bob}_{{2}}\), \(\hbox {Bob}_{{3}}\), \(\cdots\) , and \(\hbox {Bob}_{{n}}\)) have the same function to recover the dealer’s secret \(m_{A}\). The success of the second attacks is mainly for Eve’s deception can escape the security check of quantum channel. In order to deal with the security problems under the current model, a special entangled state instead of the state \(|\varphi \rangle\) should be introduced, which must guarantee any agent’s measurement result can not be deduced by the others. Furthermore, the security check of quantum channel should be strengthened, which can be solved by the way of inserting decoy states in7.
Conclusion
To sum up, we give a simple description of the HHH-protocol and then analyze its security. The security analysis shows that it is not secure in the sense that an unauthorized set can recover the secret. Furthermore, an external opponent can make participants recover a false secret without being detected by a special denial-of-service attack. Finally, we discuss how to improve the HHH-protocol’s security. We hope this work shed some lights on the development of quantum cryptography.
Availability of data and materials
Data is provided within the manuscript.
References
Shamir, A. How to shair a secret. Commun. ACM 22(11), 612–613 (1979).
Blakely, G. Safeguarding cryptographic keys. In Proc. the National Computer Conference, New York, AFIPS, Montvale: IEEE Press, 313–317 (1979)
Cramer, R., Damgård, I. & Maurer, U. General secure multi-party computation from any linear secret-sharing scheme. Phys. Rev. A 59(3), 316–334 (2000).
Parakh, A. & Kak, S. Space efficient secret sharing for implicit data security. Inf. Sci. 181(2), 335–341 (2011).
Cai, X. Q. et al. Cryptanalysis of secure multiparty quantum summation. Quant. Inf. Process. 21(8), 285 (2022).
Hillery, M., Buzěk, V. & Berthiaume, A. Quantum secret sharing. Phys. Rev. A 59(3), 1829–1834 (1999).
Wang, T. Y. et al. An efficient and secure multiparty quantum secret sharing scheme based on single photons. Opt. Commun. 281(24), 6130–6134 (2008).
Qin, H., Zhu, X. & Dai, Y. (t, n) Threshold quantum secret sharing using the phase shift operation. Quant. Inf. Process. 14, 2997–3004 (2015).
Song, Y., Li, Y. & Wang, W. Multiparty quantum direct secret sharing of classical information with bell states and bell measurements. Int. J. Theor. Phys. 57, 1559–1571 (2018).
Zha, X. W., Jiang, R. X. & Wang, M. R. Two schemes of multiparty quantum direct secret sharing via a six-particle GHZ state. Commun. Theor. Phys. 72(2), 025102 (2020).
Yin, A. & Chen, T. Authenticated semi-quantum secret sharing based on GHZ-type states. Int. J. Theor. Phys. 60(1), 265–273 (2021).
Tavakoli, A. et al. Secret sharing with a single d-level quantum system. Phys. Rev. A 92(3), 030302 (2015).
Song, X. L. et al. (t, n) threshold d-level quantum secret sharing. Sci. Rep. 7(1), 6366 (2017).
Qin, H., Tso, R. & Dai, Y. Multi-dimensional quantum state sharing based on quantum Fourier transform. Quant. Inf. Process. 17, 1–12 (2018).
Mashhadi, S. General secret sharing based on quantum Fourier transform. Quant. Inf. Process. 18(4), 114 (2019).
Cai, X. Q. et al. Measurement-device-independent quantum secret sharing. Adv. Quant. Tech. https://doi.org/10.1002/qute.202400060 (2024).
Li, Q., Chan, W. H. & Long, D. Y. Semiquantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010).
Wang, J. et al. Semiquantum secret sharing using two-particle entangled state. Int. J. Quant. Inf. 10(5), 1250050 (2012).
Li, L., Qiu, D. & Mateus, P. Quantum secret sharing with classical Bobs. J. Phys. A Math. Theor. 46(4), 045304 (2013).
Yang, C. W. & Hwang, T. Efficient key construction on semi-quantum secret sharing protocols. Int. J. Quant. Inf. 11(5), 1350052 (2013).
Ye, C. Q. & Ye, T. Y. Circular semi-quantum secret sharing using single particles. Commun. Theor. Phys. 70(6), 661 (2018).
Tsai, C. W., Yang, C. W. & Lee, N. Y. Semi-quantum secret sharing protocol using W-state. Mod. Phys. Lett. A 34(27), 1950213 (2019).
Li, C. et al. Cluster-state-based quantum secret sharing for users with different abilities. Quant. Inf. Process. 20, 1–14 (2021).
Ye, C. Q. et al. Multiparty semi-quantum secret sharing with d-level single-particle states. Int. J. Theor. Phys. 58, 3797–3814 (2019).
Houshmand, M., Hassanpour, S. & Haghparast, M. An efficient controlled semi-quantum secret sharing protocol with entangled state. Opt. Quant. Electron. 56(5), 759 (2024).
Lo, H. K. & Ko, T.-M. Some attacks on quantum-based cryptographic protocols. Quant. Inf. Comput. 5(1), 40-C47 (2005).
Qin, S. J. et al. Cryptanalysis of the Hillery-Buzek-Berthiaume quantum secret-sharing protocol. Phys. Rev. A 76(7), 062324 (2007).
Cai, X. Q. et al. Improving security of efficient multiparty quantum secret sharing based on a novel structure and single qubits. Sci. Rep. 14, 18385 (2024).
Gao, F. et al. Dense-coding attack on threeparty quantum key distribution protocols. IEEE J. Quantum Electron. 47(5), 630–635 (2011).
Cai, X. Q. et al. Security of verifiable threshold quantum secret sharing with sequential communication. IEEE Access 7, 134854–134860 (2019).
Yang, Y. G. et al. Participant attack on the measurement-device-independent protocol for deterministic quantum secret sharing. Sci. Chi. Phys. Mech. Astron. 64(26), 260321 (2021).
Wang, T. Y. et al. Security of a kind of quantum secret sharing with entangled states. Sci. Rep. 7, 2485 (2017).
Acknowledgements
We are grateful to the anonymous reviewers for helpful comments and detailed suggestions on revisions. This work was supported by the National Natural Science Foundation of China (Grant Nos. 62172196, 62272208, 61902166), and the Natural Science Foundation of Henan Province, China (Grant No. 212300410062).
Author information
Authors and Affiliations
Contributions
S. Li and X.Q. Cai gave the cryptanalysis, T.Y. Wang presented the improvement and wrote the main manuscript text. All authors reviewed the manuscript.
Corresponding authors
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Li, S., Cai, XQ., Song, SJ. et al. Cryptanalysis of efficient controlled semi-quantum secret sharing protocol with entangled state. Sci Rep 15, 15018 (2025). https://doi.org/10.1038/s41598-025-98734-1
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-98734-1