Abstract
Quantum teleportation is the process of transferring quantum information using classical communication and pre-shared entanglement. This process can benefit from the use of catalysts, which are ancillary entangled states that can enhance teleportation without being consumed. While chemical catalysts undergoing deactivation invariably exhibit inferior performance compared to those unaffected by deactivation, quantum catalysts, termed embezzling catalysts, that are subject to deactivation, may outperform their non-deactivating counterparts. In this work, we present teleportation protocols with embezzling catalysts that can achieve arbitrarily high fidelity. This enables the teleported state to closely approximate the original message state with arbitrary precision, while maintaining arbitrarily small variations in the catalytic system through the use of finite-dimensional embezzling catalysts. We show that some embezzling catalysts are universal, meaning that they can improve the teleportation fidelity for any pre-shared entanglement. We also explore methods to reduce the dimension of catalysts without increasing catalyst consumption, an essential step towards realizing quantum catalysis in practice.
Similar content being viewed by others
Introduction
Information transmission is essential for advancing technologies and scientific explorations. Entanglement, a distinctive phenomenon of quantum mechanics, revolutionizes communication by providing unparalleled security and efficiency, surpassing classical analogs. A typical example is quantum teleportation1,2,3, where sender and receiver use maximally entangled states and classical communication to simulate a noise-free quantum channel. As technology advances, the communication distance of quantum teleportation has increased from about 100 km using optical fibers4 to 1400 km using a low-Earth-orbit satellite5, paving the way for a global quantum internet6,7.
In realistic scenarios, noises stemming from imperfections in quantum devices and decoherence in the environment affects the performance of quantum teleportation. This results in the sharing of imperfectly entangled states between parties, lowering the fidelity of the transferred quantum information. To address the challenge, a concept borrowed from chemistry known as a catalyst has been employed, akin to enzymes in biology, leading to catalytic quantum teleportation8. In this approach, the catalyst comprises another pair of entangled states that become correlated with the entangled resource shared by the sender and receiver. Importantly, after the communication process, the catalyst remains unchanged.
Catalytic deactivation9, the loss of catalyst activity due to various factors, such as poisoning, fouling, carbon deposition, thermal degradation, and sintering, is unavoidable in most catalytic processes. While typically undesirable, catalytic deactivation, such as poisoning, may sometimes lead to improved catalyst selectivity, e.g., Lindlar catalyst10. This motivates us to ask: What would happen if we intentionally allow catalyst deactivation in quantum information tasks? More specifically, what if, during the process of catalytic quantum teleportation, we permit the catalytic system to undergo slight changes after its interaction with the pre-shared entanglement, known as embezzling catalyst in quantum information theory11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34 ? Could this give us some benefits? Given that certain benefits of conventional catalytic teleportation necessitate an infinite-dimensional catalyst, we may question whether the same performance can be achieved with a finite-dimensional catalyst by allowing embezzling catalyst?
In this work, we address these questions by designing teleportation protocols that incorporate embezzling catalysts. By slightly relaxing the constraint on maintaining the catalyst throughout the process, we demonstrate the feasibility of achieving teleportation with arbitrary precision. Here, the embezzling catalysts possess universality, enabling their application across teleportation tasks without prior knowledge of the shared state between sender and receiver. We conduct a comparative analysis of the dimensional requirements of catalytic systems across different protocols aimed at achieving the same precision. Additionally, we explore strategies to reduce the dimensionality of embezzling catalysts, thereby enhancing the practicality of quantum catalysis. Our work also investigates the fundamental trade-off between the dimensional requirements of embezzling catalysts and their consumption during teleportation. These findings open new avenues for exploring the generality and dimensional limits of quantum catalysis.
Results
Preliminaries
In this subsection, we start with a brief discussion of notations and terminologies, setting the stage for the forthcoming exploration.
Mathematical tools
Let \({{{{\mathcal{H}}}}}_{A}\) be a Hilbert space and let \({{{\mathcal{D}}}}(A)={{{\mathcal{D}}}}({{{{\mathcal{H}}}}}_{A})\) denote the set of quantum states (specifically, density operators) on it. To measure how close two quantum states are, we use the Uhlmann fidelity FU35. For any two states ρ and σ, FU(ρ, σ) is given by
In particular, when one of the states is pure, the fidelity simplifies to
The Uhlmann fidelity does not satisfy the properties of a mathematical distance, since it is equal to one for identical states. However, it induces a distance called the purified distance36 (also called the sine distance37):
which satisfies the following properties
-
Non-negativity: P(ρ, σ) ⩾ 0 with P(ρ, σ) = 0 when ρ = σ.
-
Symmetry: P(ρ, σ) = P(σ, ρ) holds for any quantum state \(\rho ,\,\sigma \in {{{\mathcal{D}}}}(A)\).
-
Triangle inequality: P(ρ, σ) ⩽ P(ρ, τ) + P(τ, σ) holds for any quantum state \(\tau \in {{{\mathcal{D}}}}(A)\).
-
Quantum data processing inequality (DPI): quantum channels can only reduce the purified distance, namely \(P({{{\mathcal{N}}}}(\rho ),{{{\mathcal{N}}}}(\sigma )) \, \leqslant \, P(\rho ,\sigma )\) holds for any quantum channel \({{{\mathcal{N}}}}\)38.
-
Tensor invariance: P(ρ ⊗ τ, σ ⊗ τ) = P(ρ, σ) holds for any quantum state \(\tau \in {{{\mathcal{D}}}}(A)\). This property comes from the multiplicativity of Eq. (1).
We end this subsection by introducing the max-relative entropy, a measure of distinguishability between two quantum states ρ and σ that satisfy supp(ρ) ⊆ supp(σ).
This quantity can be computed via the following semidefinite program (SDP):
Given that SDPs can be efficiently solved using interior point methods39,40,41, the majority of applications involving SDPs42,43,44,45,46, such as calculating max-relative entropy, can generally be addressed with high efficiency in practice.
Approximate catalyst
Some quantum state transformations from ρ to σ are impossible, even approximately, due to the limitations of quantum operations. Exact catalysts can facilitate some of these transformations, but they have stringent conditions: the final state and the catalyst must be uncorrelated, and the catalyst must be preserved. These conditions are often impractical, and they restrict our power to transform ρ to σ. We can overcome these restrictions by using an approximate catalyst, which has weaker conditions. We present a taxonomy of different kinds of catalysts in quantum information theory in our Table 1. An approximate catalyst is formally defined as follows:
Definition 1
(Approximate catalysts). A state transition from ρA to σA on system A is approximate catalytic with respect to free operations \({{{\mathcal{O}}}}\) if there is a quantum state τC on catalytic system C and a free operation \(\Lambda \in {{{\mathcal{O}}}}\) such that
and
Here ε > 0 and δ ⩾ 0 are the smoothing parameters, with D being a distance measure between states. We call the state τC an approximate catalyst.
Specially, if we set ε = 0 and δ = 0, these catalysts are referred to as exact catalysts. For example, suppose we have two states ρA and σA, and a set of free operations \({{{\mathcal{O}}}}\). If we cannot transform ρA into σA using only free operations, we write
However, if there exists a state τC such that we can transformρA ⊗ τC into σA ⊗ τC using free operations, we write
In this case, τC is an exact catalyst for the transformation from ρA to σA.
By allowing errors for catalysts, we can enhance our ability to transform states and achieve some otherwise impossible transformations. Depending on the value of δ, we use different terms. If δ > 0, we call it an embezzling catalyst, which means that the system gains some advantages at the expense of the τC. If δ = 0, we call it a correlated catalyst, which means it can help the transformation while being correlated with the system. For more details, we refer interested readers to some comprehensive reviews on the topic47,48.
Quantum teleportation
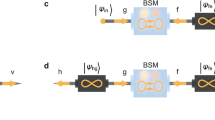
Quantum teleportation is a communication protocol for sending quantum information from Alice to Bob using three ingredients (see Fig. 1a): (i) An unknown message state ψ of system R that Alice wants to transmit. (ii) An entangled state ρAB of systems A and B shared by Alice and Bob. (iii) A local operation and classical communication (LOCC) protocol Θ0 ∈ LOCC(RA: B) that involves Alice performing a Bell measurement on systems R and A, and Bob applying a unitary transformation on system B depending on Alice’s outcome. After applying the LOCC operation Θ0: RAB → B, Bob’s system B will be in the state
a Standard teleportation, where the message encoded by ψR is transmitted from the sender Alice to receiver Bob. The protocol is enabled by implementing Θ0, which involves a Bell measurement on ψR ⊗ ρAB followed by unitary operations on Bob’s system B; b Teleportation with embezzling catalyst, where Alice and Bob have an additional catalyst \({\tau }_{C{C}^{{\prime} }}\) undergoing a transformation \(\Lambda \in {{{\rm{LOCC}}}}(RAC:B{C}^{{\prime} })\) and coming back slightly changed. The state \({\tau }_{C{C}^{{\prime} }}\) assists in improving the performance of teleportation protocol. Alice holds the part above the dashed line and Bob holds the part below it.
A measure for quantifying the performance of teleportation is the average fidelity49,
Here ψ is taken over all pure states with respect to the Haar measure, such that ∫ dψ = 1. For any bipartite state ρAB, its average fidelity is in [1/(d + 1), 1]. Let d denote the dimension of the message system R. It is 1 only for maximally entangled states between Alice and Bob. Errors, like device imperfection or environmental decoherence, make teleportation performance less than 1.
Given a bipartite state ρAB, its entanglement can be quantified through the entanglement fraction49,
where \({\phi }_{AB}^{+}:= | {\phi }^{+}\rangle {\langle {\phi }^{+}| }_{AB}\) stands for the maximally entangled state acting on systems AB with
Using state ρAB as the shared resource in quantum teleportation, its average fidelity and entanglement fraction are connected by the following formula
which shows that the capability of ρAB in quantum communication is completely determined by its entanglement50.
Teleportation with embezzling catalysts
Catalysts are essential for many quantum information tasks, such as resource distillation and communication (see Table 2), enabling performance that would otherwise be unatta- inable in their absence. However, embezzling catalysts for quantum teleportation are less explored than correlated ones. We fill this gap by showing that embezzling catalysts can achieve teleportation with any desired accuracy, even with noisy initial states. We also address the practical issue of high-dimensional catalysts and propose ways to lower their dimension without compromising their performance.
Main Results
Teleportation with embezzling catalysts, like the protocol with correlated catalysts introduced in ref. 8, has two steps. First, a LOCC operation Λ acts on ρAB and \({\tau }_{C{C}^{{\prime} }}\), and correlates them, where Alice has systems AC and Bob has systems \(B{C}^{{\prime} }\). Second, the standard teleportation procedure Θ0 (see Fig. 1a) is applied to systems RAB. The overall operation is Θ (see Fig. 1b), and is given by
This is a map from the systems \(RACB{C}^{{\prime} }\) to the system B. Here we do not require the catalyst to be returned exactly as its original form, that is, we allow
where P is the purified distance, defined in Eq. (3). After teleportation with embezzling catalysts, the resultant state on Bob’s system is
In this scenario, the efficacy of teleportation with embezzling catalysts is measured through the average fidelity fc which is defined as
and our primary findings indicate that
Theorem 1
Given any bipartite state ρAB and any positive numbers ϵ > 0 and δ > 0, we can find a finite dimensional embezzling catalyst \({\tau }_{C{C}^{{\prime} }}\) and a LOCC operation \(\Theta \in {{{\rm{LOCC}}}}(RAC:B{C}^{{\prime} })\) (see Fig. 1b) such that
and
Our theorem shows that with the help of an embezzling catalyst, we can simulate the noiseless channel idA→B with arbitrary precision, while keeping the catalyst’s consumption within an arbitrarily small range. The key idea behind the embezzling catalytic protocol is that we can use the catalyst to increase the entanglement of any initial state ρAB until it is arbitrarily close to a maximally entangled state \({\phi }_{AB}^{+}\). At the same time, we aim to ensure that the alteration of the embezzling catalyst remains within an acceptable error range. We will prove this statement in two different ways: one based on the convex-split lemma introduced in ref. 51, and another based on the entanglement embezzling states constructed in ref. 11. In addition, we will explore the possibility of reducing the dimension of the catalysts.
Convex-split-lemma-assisted teleportation
Originally proposed in ref. 51 to study communication cost, the convex-split lemma has become a powerful tool with many applications. It is useful in various domains, such as catalytic decoupling21, quantum resource theories23,24, and one-shot quantum communication26. Before we review its statement, we introduce some notations. We write t for the system AtBt, and omit the subscripts of ρAB and σAB, denoting them as ρ and σ. The context will make it clear which systems they refer to. Now we are ready to state the convex-split lemma.
Lemma 1
(Convex-Split Lemma51). Given quantum states \(\rho ,\tau \in {{{\mathcal{D}}}}(AB)\) with \(k:= {D}_{\max }(\rho \parallel \tau )\), then there exists a LOCC operation ΛCS (see Fig. 2) such that
We use a visual example with n = 4 to illustrate the convex-split lemma. Each color represents a different state: red for ρ, white for τ, and blue for the maximally entangled state ϕ+. The circle portrays a uniform mixture of 4 concentric circles. Each concentric circle, from the innermost to the outermost, is designated as the t-th layer, with t ranging from 1 to 4, and represents a quantum state. For instance, every concentric circle in (a) stands for a tensor product state of the form ρ1 ⊗ τ2 ⊗ τ3 ⊗ τ4, where i ∈ 1, …, 4 denotes systems AiBi. In (b), we take layer 2 as an illustration, depicting τ1 ⊗ ρ2 ⊗ τ3 ⊗ τ4. Finally, (c) showcases the state \({\phi }_{1}^{+}\otimes {\tau }_{2}\otimes {\tau }_{3}\otimes {\tau }_{4}\). The symbol ≈ indicates that the purified distance between the quantum states depicted in (b) and (c) is at most \(\eta =\sqrt{{2}^{k}/4}+P(\tau ,{\phi }^{+})\).
Here P is the purified distance (see Eq. (3)). The operation ΛCS proceeds in two steps: (i) Alice randomly generates an integer t from {1, …, n} with uniform probability 1/n, and communicates this number to Bob; (ii) Using this classical information, Alice and Bob perform a SWAP operation \({{{{\mathcal{E}}}}}_{1t}\) between 1 ≔ A1B1 and t ≔ AtBt. Mathematically, ΛCS is defined as follows
where the map \({{{{\mathcal{E}}}}}_{1t}\) represents the SWAP between 1 ≔ A1B1 and t ≔ AtBt.
By applying the convex-split lemma, we derive the following result for teleportation with embezzling catalysts, which constitutes the first proof of Thm. 1.
Theorem 2
(Convex-Split-Lemma-Assisted Teleportation). Consider a bipartite quantum state ρ on systems AB. Let τ be another bipartite state on the same space such that the support of ρ is contained in the support of τ, i.e., supp(ρ) ⊆ supp(τ). Define k as the max-relative entropy of ρ with respect to τ, that is, \(k:= {D}_{\max }(\rho \parallel \tau )\). Then, for any positive number ϵ > 0, there exists a catalyst
with integer n defined as
Here d stands for the dimension of message system R (see Fig. 1), namely \(d:= \dim {{{{\mathcal{H}}}}}_{R}\). Suppose that the entanglement fraction of τ is lower-bounded by
Then, by using the catalyst state τCS defined in Eq. (24) and the teleportation protocol Θ0 ∘ ΛCS described in Eq. (22), we can achieve the following performance of catalytic teleportation
Alternatively, if the number of copies of τ meets the requirement
then after catalytic teleportation, the embezzling catalyst’s consumption in terms of purified distance is limited to within an error tolerance of δ, i.e.,
Hence, when n satisfies
both Eq. (27) and Eq. (29) are guaranteed to be satisfied.
Remark that the embezzling catalyst τCS is a quantum state on the systems \(C{C}^{{\prime} }\), where C ≔ A2, …, An and \({C}^{{\prime} }:= {B}_{2},\ldots ,{B}_{n}\).
Proof
Let us first construct a set \({{{\mathcal{S}}}}\) that will be useful for choosing catalysts. Its rigorous construction is defined below, and we also provide an illustration that describes our main idea of the construction in Fig. 3a.
where \({{{\mathcal{D}}}}{(AB)}_{\ > \ 0}\) represents the set of positive states. It is worth highlighting that for any \(\tau \in {{{\mathcal{S}}}}\), we will have \({{{\rm{supp}}}}(\tau )={{{{\mathcal{H}}}}}_{AB}\), and hence satisfies supp(ρ) ⊆ supp(τ). By further choosing p in Eq. (31) such that
the entanglement fraction F of τ will meet Eq. (26). Defining τCS = τ⊗n−1 = τ2 ⊗ ⋯ ⊗ τn with n ≔ ⌈2k+2d/ϵ(d + 1)⌉, Lem. 1 then implies that
With the help of the triangle inequality, we obtain that the purified distance between ΛCS(ρ ⊗ τCS) and ϕ+ ⊗ τCS is bounded by
Now, let us come back to the result state on the systems AB, which is denoted by ρ(n) and formally expressed as
Consequently, the entanglement fraction F( ⋅ ) (see Eq. (12)) of ρ(n) is lower-bounded by
Thanks to Eq. (18), we can guarantee that a lower bound of the average fidelity is 1 − ϵ; that is
In (a), we sketch our idea and visualize the relation between the maximally mixed state \({\mathbb{I}}/{d}^{2}\) and the four random full-ranked states ζi with i ∈ {1, 2, 3, 4}. Each point of the line represents a possible τ considered in Eq. (24). In (b) to (e), the red and blue bar graphs respectively represent the number of copies of τ, with the red dotted line indicating the percentage of copy reduction, i.e., ϑ(ϵ), defined in Eq. (47).
In addition to achieving high performance in quantum teleportation with the help of τCS, we are also interested in minimizing the consumption of τCS during the process, as significant changes are undesirable. Specifically, in terms of purified distance, the change in the embezzling catalyst is upper bounded by
This inequality follows directly from Eq. (33) and the quantum data processing inequality. Consequently, this inequality indicates that when more copies of τ are used in the construction of τCS (see Eq. (24)), the overall consumption decreases, making the catalytic systems closer to their original form.
The performance of quantum teleportation systems varies, necessitating different error tolerances for different platforms52,53. Our focus is on determining the minimal dimensional requirements to ensure that the variation in the embezzling catalyst remains within an error δ. Specifically, for protocols assisted by the convex-split lemma, this issue can be framed in terms of the number of copies of the state τ required to construct τCS (see Eq. (24)). According to Eq. (38), the minimum number of copies, in terms of n, is determined by
which completes the proof. □
By using the insights from the convex-split lemma, it becomes evident that in the quest to fabricate a catalyst facilitating quantum teleportation, the key lies in identifying quantum states whose support encompasses that of the initial state ρAB. We denote the collection of all such states as
and it is clear that \({{{\mathcal{S}}}}\subset {{{{\mathcal{S}}}}}_{{{{\rm{supp}}}}}\). The demonstration of Thm. 2 establishes the existence of n (see Eq. (25)), enabling teleportation with embezzling catalysts. However, from a practical standpoint, our emphasis should be on optimizing the protocol to achieve equivalent performance in quantum teleportation with reduced dimensionality in the catalytic system.
Dimensionality reduction for catalysts
In the previous section, we discussed how embezzling catalysts can be used to simulate noiseless channels with arbitrary precision. Here, we further investigate whether the same performance can be achieved with lower-dimensional catalysts. Specifically, given an initial state ρ and an error ϵ, we ask whether we can satisfy Eq. (27) with a smaller n. To formulate this optimization problem more clearly, we ask the following question for a given quantum state ρ and error ϵ,
where \({{{{\mathcal{S}}}}}_{{{{\rm{supp}}}}}\) is defined in Eq. (40). Variable ϵ in Eq. (27) represents the allowable error of average fidelity, which guarantees the performance of quantum teleportation. The optimization problem of Eq. (41) is challenging, as it involves the set of \({{{{\mathcal{S}}}}}_{{{{\rm{supp}}}}}\) with a complex structure, and non-linear constraints. Solving this problem directly and finding an analytical solution are both very difficult, but we can attempt to bound its performance and investigate how to lower the dimension of catalytic systems.
A computable upper bound for \({n}_{\min }({{{{\mathcal{S}}}}}_{{{{\rm{supp}}}}},\epsilon )\) (see Eq. (41)) can be obtained by replacing the original \({{{{\mathcal{S}}}}}_{{{{\rm{supp}}}}}\) with the following subset, which avoids this difficulty.
Unlike Eq. (31), this set, i.e., \({{{{\mathcal{S}}}}}_{\zeta }\), has a fixed full-ranked state ζ inside its definition. Its relation with \({{{\mathcal{S}}}}\) and \({{{{\mathcal{S}}}}}_{{{{\rm{supp}}}}}\) is given by the inclusion chain below.
By replacing the set \({{{{\mathcal{S}}}}}_{{{{\rm{supp}}}}}\) inside \({n}_{\min }({{{{\mathcal{S}}}}}_{{{{\rm{supp}}}}},\epsilon )\), we can define \({n}_{\min }({{{\mathcal{S}}}},\epsilon )\) and \({n}_{\min }({{{{\mathcal{S}}}}}_{\zeta },\epsilon )\) respectively. Fix ϵ, then they satisfy the following inequality chain.
It is worth mentioning that, in lots of applications of the convex-split lemma, especially in the study of quantum resource theories, people will conventionally take ζ as the maximally mixed state \({\mathbb{I}}/{d}^{2}\) and obtain computable bounds. But we will show that, by choosing other full-ranked states, we may obtain an advantage in saving the dimension of the catalytic system. To show the statement, let us take \({n}_{\min }({{{{\mathcal{S}}}}}_{{\mathbb{I}}/{d}^{2}},\epsilon )\) as a benchmark, and compare the performance of our protocol with \({n}_{\min }({{{{\mathcal{S}}}}}_{{\mathbb{I}}/{d}^{2}},\epsilon )\).
Let’s begin our exploration with a random scenario: consider the initial state ρ that is shared between the sender, Alice, and the receiver, Bob, and is randomly chosen as
In this case, we select four random full-ranked states, denoted as ζ1 to ζ4. Our numerical examples show that with these states, fewer copies of τ (see Eq. (24)) are needed, and hence, they require less dimensions for catalytic systems, as illustrated in Fig. 3. Beyond the fact that
we have also defined the descent ratio,
portraying the conservation of catalyst dimensions. This is illustrated in Fig. 3 for ζ1 to ζ4. Through this exemplification, it becomes evident that the randomly selected full-ranked states exhibit superior performance compared to \({\mathbb{I}}/{d}^{2}\).
On the other hand, we have also learned that different full-ranked states will have different performance in the teleportation with embezzling catalysts. In Fig. 3, ζ4 requires the least dimension for catalyst with different values of ϵ. In practice, we can pick up a finite N full-ranked states ζi (i = 1, …, N) randomly, choose the best one, and denote the minimal copies for the catalytic system as \({n}_{\min }(N,\epsilon )\), which satisfies
Here we have three remarks: (i) The upper bound \({n}_{\min }(N,\epsilon )\) is constructed by exclusively selecting full-ranked states. This design choice allows our protocol to operate effectively with any bipartite state ρAB shared between Alice and Bob. However, opting for states containing only the support of the initial state ρAB may yield superior performance, facilitating embezzling with fewer catalytic systems. (ii) The bound \({n}_{\min }(N,\epsilon )\) can be computed efficiently as \({D}_{\max }(\rho \,\parallel \,\tau )\) forms a SDP. (iii) In principle, increasing the number of randomly chosen states by us can result in a tighter bound and the discovery of catalysts with lower dimensions. Surprisingly, the increase from 100 to 1000 samples does not yield a substantial enhancement in uncovering a catalyst with significantly reduced dimension, as depicted in Fig. 4. This modest gain, unfortunately, is accompanied by a considerable escalation in computational resource costs. Similar trends are observed in the descent ratio, which is defined as
Here we choose the initial state as the one considered in Eq. (45) and take N full-ranked states randomly, to construct τ (see Eq. (24)) and compare the number of copies that are needed to achieve higher fidelity in (a). Investigation of descent ratio ϑ(N, ϵ) (see Eq. (49)) with respect to different N is shown in (b).
No matter whether the initial state shared between the sender and the receiver is entangled or separable, our results tell us that embezzling can always enhance the performance of teleportation; but definitely with different precision, they will require different copies of τ (see Eq. (24)) and hence, different catalytic system dimensions. More numerical experiments are demonstrated in Fig. 5.
a illustrates the required copies for enhancing average fidelity in entangled initial states. Left for 0.75, right for 0.80. The red and blue bar graphs illustrate the copies of τ (see Eq. (24)) corresponding to \({n}_{\min }({{{{\mathcal{S}}}}}_{{\mathbb{I}}/{d}^{2}},\epsilon )\) and \({n}_{\min }(100,\epsilon )\), respectively. b The case of separable initial states, improved to 0.7. Here, the red and blue bar graphs represent the average fidelity before and after embezzling. In both (a) and (b), the red dashed line indicates the percentage reduction in copies of \({n}_{\min }(100,\epsilon )\) compared to \({n}_{\min }({{{{\mathcal{S}}}}}_{{\mathbb{I}}/{d}^{2}},\epsilon )\). The random states selected by us are provided in Supplementary Tables 1 and 2.
Finally, to ensure our method of reducing the dimension of embezzling catalysts by randomly choosing full-ranked states is statistically robust and unbiased with respect to the initial state shared between the sender and receiver, we conduct Monte Carlo simulations with 10,000 randomly selected initial states ρ. For each initial state, we obtain a result and then calculate the average over the 10,000 experiments. Additionally, we vary the number N of randomly chosen full-ranked states for constructing τ (see Eq. (24)) from 10 to 100. As shown in Fig. 6, improvements are observed for all chosen values of N, with the average descent ratio over 10,000 runs represented by the dashed blue line. The efficacy of our optimization method further increases with larger N. Notably, when N = 100, approximately 99.93% of the samples demonstrate an improvement.
We conduct 10,000 numerical experiments, where each experiment involves selecting a random initial state ρ and obtaining results. a–d Demonstrate the value of ϑ(N, ϵ) for N = 10, 20, 50 and 100, respectively. The dashed blue line in the figures represents the average descent ratio ϑ(N, ϵ) computed across all runs. Here, N denotes the number of randomly generated full-ranked quantum states used to construct τ (see Eq. (24)). The dashed red line represents the case where ϑ(N, ϵ) = 0, above which indicates a strict improvement compared to using the maximally mixed state \({\mathbb{I}}/{d}^{2}\) in constructing convex-split-lemma-assisted teleportation.
Embezzling-State-Assisted Teleportation
The concept of embezzling states was originally proposed by van Dam and Hayden in the context of entanglement theory11. Since then, it has found applications in various fields of quantum information, such as thermodynamics15,17, coherence13,23, and the quantum reverse Shannon theorem54,55, among others18,19. Using the idea of embezzling states, we can prove the following lemma. To enhance clarity, we will omit the subscripts AB and \(C{C}^{{\prime} }\) where their exclusion does not cause confusion.
Lemma 2
(Entanglement Embezzling11). Let τE be an embezzling state on systems \(C{C}^{{\prime} }\), defined as
with \({c}_{M}:= {\sum }_{j = 1}^{M}\frac{1}{j}\). Then for any bipartite state ρ on systems AB with \(d:= \dim {{{{\mathcal{H}}}}}_{A}=\dim {{{{\mathcal{H}}}}}_{B}\), there always exists an LOCC operation \({\Lambda }^{E}\in {{{\rm{LOCC}}}}(AC:B{C}^{{\prime} })\), such that
Proof
Let’s begin our proof by introducing the state ω on systems \(ABC{C}^{{\prime} }\).
where the coefficient of \(\left\vert \omega \right\rangle\), i.e.,
follows the dictionary order, namely
In particular, it is straightforward to check that the first M coefficients of \(\left\vert \omega \right\rangle\) are equal to
In this case, the inner product between \(\left\vert 11\right\rangle \otimes | {\tau }^{E}\rangle\) and \(\left\vert \omega \right\rangle\) is bounded from below by
The first inequality is derived from Eq. (55), the second stems from a direct calculation involving the initial d⌊M/d⌋ terms of the sum, and the third is obtained by employing the definite integral.
Next, let’s continue our proof by considering the rearrangement of the systems AC as follows
where k ≔ (i − 1)M + j − (l − 1)d and \(l:= \lceil \frac{(i-1)M+j}{d}\rceil\). Such a mapping UAC constitutes a unitary transformation on systems AC. Similarly, we can define unitary operations \({U}_{B{C}^{{\prime} }}\) on systems \(B{C}^{{\prime} }\). By applying \({U}_{ABC{C}^{{\prime} }}:= {U}_{AC}\otimes {U}_{B{C}^{{\prime} }}\) to \(\left\vert \omega \right\rangle\) (see Eq. (52)), we obtain
Setting
we establish the following chain of inequalities
Here, the first equality arises from the definition of the LOCC operation ΛE. With this, we complete our proof. □
Note that the construction of the unitary transforming \(\left\vert \omega \right\rangle\) into \(| {\phi }^{+}\rangle \otimes | {\tau }^{E}\rangle\) is not unique; an alternative approach is illustrated in Fig. 7. Thanks to Lem. 2, we can now present an alternative proof of Thm. 1, using the concept of embezzling states.
In (a), we present a graphical representation of the embezzlement protocol ΛE. In (b), we offer two examples of the operations UAC and \({U}_{B{C}^{{\prime} }}\) for the specific scenario where d = 2 and M = 3, demonstrating that the construction of local unitaries acting on AC and \(B{C}^{{\prime} }\) is not unique. This construction can be extended to arbitrary finite-dimensional systems.
Theorem 3
(Embezzling-State-Assisted Teleportation). Given any bipartite state ρ on systems AB and any positive number ϵ > 0, we can find an embezzling catalyst τE (see Eq. (50)) with Schmidt rank
where \(d:= \dim {{{{\mathcal{H}}}}}_{A}=\dim {{{{\mathcal{H}}}}}_{B}\), and a LOCC operation ΛE (see Eq. (59) and Fig. 7), such that
On the other hand, if the Schmidt rank M of τE satisfies
then after catalytic teleportation, the embezzling catalyst’s consumption, in terms of purified distance, remains within an error tolerance of δ, namely
Therefore, if the Schmidt rank M of τE satisfies
both Eq. (62) and Eq. (64) will be fulfilled.
Proof
At the beginning of teleportation with embezzling catalysts, we prepare the state ρ ⊗ τE. After applying LOCC operation ΛE, we denote the state on systems AB as ρ(M), whose entanglement fraction satisfies
where the first inequality relies on the quantum data processing, while the second is based on Lem. 2. Finally, using ρ(M) for standard teleportation, we obtain
which leads to Eq. (62).
In addition to demonstrating the improved performance of the embezzling-state-assisted protocol, we examine the consumption of the embezzling catalyst during catalytic teleportation. Specifically, we investigate the change in the embezzling catalysts using the purified distance. Let us consider the state of the catalytic system after teleportation, which is given by
where K ≔ ⌈m/d⌉ and ki ≔ m − ⌊(m − 1)/d⌋d + (i − 1)d. The consumption of the embezzling state during catalytic teleportation can be quantified by its change, which is given by
resulting in the exact form of the purified distance between ξE and τE, namely
Using Eq. (60) and the quantum data processing inequality, we can derive a much simpler upper bound
In embezzling-state-assisted teleportation, if the acceptable error is δ, the minimal dimension of the embezzling state – equivalently, the minimum Schmidt rank M of the embezzling state – necessary to ensure that the embezzling catalyst’s variation after catalytic teleportation remains within δ is determined by
which concludes the proof. □
Up to this point, we’ve explored two primary methods of embezzling quantum teleportation: one based on the convex-split lemma, and the other on embezzling states. The former can be further categorized based on the selection of full-ranked states, either through conventional means employing maximally mixed states or by randomly selecting finite full-ranked states. In our numerical experiments, we compare the performance of these protocols in terms of the dimensions required for catalytic systems, and the changes in these embezzling catalysts during catalytic teleportation, as measured by purified distance. For convex-split-lemma-assisted protocols, the approach using randomly chosen full-ranked states to construct τ outperforms the one using maximally mixed states \({\mathbb{I}}/{d}^{2}\). However, compared to the embezzling-state-assisted protocol, the latter achieves better performance with the same catalytic system dimension. This improved performance, however, comes at the cost of greater variation in the catalysts during the catalytic teleportation process, as demonstrated in Fig. 8.
a, c Illustrate the minimum dimension of embezzling catalysts needed to achieve a given performance of teleportation with random initial states ρ (see Fig. 1), with fidelities of 0.75 and 0.8, as presented in Supplementary Table 1. Here, τE indicates the catalyst dimension based on embezzling states (see Eq. (50)), while \({\tau }^{CS}({n}_{\min }(100,\epsilon ))\) and \({\tau }^{CS}({n}_{\min }({{{{\mathcal{S}}}}}_{{\mathbb{I}}/{d}^{2}},\epsilon ))\) denote the catalyst dimensions constructed using the convex-split lemma (see Lem. 1). The former employs a selection of 100 randomly chosen full-ranked states for constructing τ (see Eq. (24)), whereas the latter utilizes maximally mixed states \({\mathbb{I}}/{d}^{2}\). To enhance readability, we adjusted the proportions according to the varying average fidelity values across these figures. b, d Demonstrate the consumption of embezzling catalysts during the teleportation process in terms of purified distance. Specifically, the blue line denotes the upper bound of the consumption for the embezzling catalyst τCS (see Eq. (38)), while the pink line represents the exact consumption of the catalyst τE in catalytic teleportation (see Eq. (70)). These comparisons indicate that the superior performance of the embezzling-state-assisted protocol, with the same dimension as the convex-split-lemma-assisted protocol, comes at the cost of a greater change from its original form before catalytic teleportation.
Table 3 summarizes the state-of-the-art performance of various quantum teleportation systems without catalysts53. We will now explore how performance can be enhanced using an embezzling catalyst and examine the fundamental relationships between average fidelity and the consumption of catalytic systems. Assuming ground-to-satellite quantum teleportation has been implemented via entangled photons described in Supplementary Table 1, with an average fidelity of approximately 0.80 ± 0.015, the dimensional requirements for each embezzling catalyst to achieve fc ⩾ 1 − ϵ are presented in Fig. 8c. As the dimension of the catalytic system increases, the consumption of each embezzling catalyst, denoted as δ, decreases. The correlation between fidelity fc and consumption δ is shown in Fig. 8d.
Each embezzling catalyst has its own pros and cons. The convex-split lemma protocol generally offers comparable performance with less variation in the catalytic system after teleportation. However, if a lower-dimensional catalyst is required, the embezzling state protocol may be more suitable. Additionally, for quantum teleportation without prior knowledge of the initial state, the embezzling-state-assisted protocol is superior, as the convex-split-lemma-assisted protocol requires this information. Therefore, the choice of embezzling catalysts should depend on specific platform requirements and practical considerations.
Comparison with correlated catalysts
Catalytic quantum teleportation based on correlated catalysts was investigated in ref. 8, where Duan states56 were used to exceed the performance of standard teleportation (see also ref. 57 for its application in quantum thermodynamics). However, the protocol based on Duan states cannot guarantee that teleportation can be done with arbitrary precision, even though an infinite-dimensional Duan state has been considered. In Thms. 2 and 3, we showed that by allowing a small amount of catalyst consumption, we can overcome this limitation and succeed at the same task with a finite-dimensional catalyst. This demonstrates the power and versatility of embezzling quantum teleportation. Here, we present more numerical experiments and comparisons between catalytic teleportation with correlated catalysts and embezzling catalysts.
Let’s begin with the construction of the Duan state utilized in catalytic quantum teleportation, where the catalyst \({\tau }_{C{C}^{{\prime} }}^{D}\), namely the Duan state, is defined as
In Eq. (73), ρ stands for bipartite state shared between the sender Alice and the receiver Bob, and \({{{\mathcal{E}}}}\) is a LOCC operation. Systems C ≔ A2A3…AnT and \({C}^{{\prime} }:= {B}_{2}{B}_{3}\ldots {B}_{n}T\) are held by Alice and Bob respectively. \({{{{\rm{Tr}}}}}_{1\cdots t}\) denotes partial the trace over the first t copies of \({{{\mathcal{E}}}}({\rho }^{\otimes n})\). Let ΛD represents the process of establishing quantum correlations between the initial bipartite state ρAB and the catalyst \({\tau }_{C{C}^{{\prime} }}^{D}\), as outlined in Fig. 9. An alternate visualization of this procedure is presented in Fig. 1 of ref. 8.
Here we provide a visualization of the LOCC operation ΛD for the case where n = 4. Let’s begin with (a), where we employ concentric circles to depict quantum states that are uniform mixtures of four tensor product states. Each layer, labeled by a basis state \(\left\vert t\right\rangle\) of the auxiliary system T ranging from the innermost to the outermost for t = 1, …, 4, symbolizes a component of the state. Specifically, the innermost concentric circle represents \({\rho }_{1}\otimes {{{{\rm{Tr}}}}}_{1}[{{{\mathcal{E}}}}({\rho }^{\otimes 4})]\otimes \left\vert 1\right\rangle {\left\langle 1\right\vert }_{T}/4\), where i ∈ {1, …, 4} abbreviates systems AiBi. The red quarter stands for state ρ, while the white part in the t-th layer denotes \({{{{\rm{Tr}}}}}_{1\cdots t}[{{{\mathcal{E}}}}({\rho }^{\otimes 4})]\). Next, let’s discuss the construction of ΛD, which comprises three steps: First, applying \({{{\mathcal{E}}}}\) to the state with classical register \(\left\vert 4\right\rangle {\left\langle 4\right\vert }_{T}\) yields the state depicted in (b). Second, after implementing a permutation to the classical register system T: \({\left\vert t\right\rangle }_{T}\to {\left\vert t+1\right\rangle }_{T}\) for t < 4 and \({\left\vert 4\right\rangle }_{T}\to {\left\vert 1\right\rangle }_{T}\), we obtain (c). Third, a SWAP on systems 1 and t for in t-th layer leads to (d).
The performance of catalytic teleportation is characterized by the enhanced average fidelity, denoted as fD(ρAB), which is given by
The maximization is conducted over all LOCC operations \({{{\mathcal{E}}}}\in {{{\rm{LOCC}}}}({A}_{1}\ldots {A}_{n}:{B}_{1}\ldots {B}_{n})\) and positive integers. Further assurance regarding the enhancement of catalytic quantum teleportation with the aid of the Duan state is provided by the lemma from ref. 8.
Lemma 3
(8). For any pure bipartite state φAB shared between the sender, Alice, and the receiver, Bob, its performance with the Duan state is lower-bounded by
where ρA and σA represent the reduced systems of φAB and ϕAB on subsystem A, respectively, while S denotes the Shannon entropy.
The aforementioned lemma guarantees the efficacy of catalytic quantum teleportation when employing the Duan state. A comparison with embezzling catalysts is illustrated in Fig. 10a, focusing on qutrit scenarios. In the left portion of Fig. 10a, we depict the performance of catalytic quantum teleportation: the pink region denotes bipartite states with an original average fidelity already greater than or equal to 0.9, while the deep blue region represents states where, aided by the infinite-dimensional Duan state, i.e., n → ∞ in Eq. (73), the final performance can surpass 0.9. The light blue area signifies states for which we cannot ensure that their communication capability in teleportation can be elevated beyond 0.9, even with the assistance of an infinite-dimensional Duan state. Conversely, as shown in the right portion of Fig. 10a, all states with an original average fidelity less than 0.9 can be enhanced to exceed 0.9 through the use of embezzling catalysts.
a The triangle of all bipartite pure states of qutrits. Each point λ = (λ1, λ2, λ3) in the triangle represents a unique state (up to local unitaries) with Schmidt coefficients {λi} for 1 ⩽ i ⩽ 3. The left part of (a) illustrates the performance of quantum teleportation with correlated catalysts. The pink region indicates states that already have an average fidelity of at least 0.9 without any catalyst. The deep blue region indicates states that can achieve a fidelity higher than 0.9 with the help of Duan states. The light blue area indicates states for which we cannot guarantee that their communication capability in teleportation can be elevated beyond 0.9, even with the assistance of an infinite-dimensional Duan state. Similarly, the right part of (a) shows the performance of quantum teleportation with embezzling catalysts. The pink and deep blue regions have the same meaning as before, while the light blue region is absent, indicating that embezzling catalysts can boost the fidelity of any state above 0.9. b The lower bound on the catalytic fidelity achieved by infinite-dimensional correlated catalysts, as indicated by the red line. The red and blue bars compare the required dimensions of the catalytic systems, when using two different types of embezzling catalysts: \({\tau }_{C{C}^{{\prime} }}^{E}\) (see Eq. (50)) and \({\tau }_{C{C}^{{\prime} }}^{CS}\) (see Eq. (24)). The bars show the minimum dimension needed to reach the same lower bound as the correlated catalysts. c Illustrates the variation in different types of embezzling catalysts after the catalytic teleportation, measured in terms of purified distance.
This example shows two benefits of using embezzling catalysts. Firstly, if we restrict ourselves to strict catalysts—those that remain unchanged after the communication process— we may not observe significant enhancements in teleportation performance, even with an infinite-dimensional catalyst. In practice, preparing an infinite-dimensional catalyst and manipulating all systems is nearly impossible. Therefore, in such cases, embezzling catalysts with lower dimensions offer a more feasible solution. Secondly, the construction of \({\tau }_{C{C}^{{\prime} }}^{D}\) defined in Eq. (73) relies on the initial state shared between the sender, Alice, and the receiver, Bob, rendering it non-universal. Conversely, embezzling catalysts, such as \({\tau }_{C{C}^{{\prime} }}^{E}\) considered in Eq. (50), are universal, meaning they can be utilized without prior knowledge of the initial state shared between Alice and Bob.
Addressing the practicality of protocols often hinges on overcoming dimensional constraints. To further explore this, let’s explore another example regarding dimension requirements in catalytic teleportation and teleportation with embezzling catalysts. Consider a state \({\left| \varphi \right\rangle }_{AB}:= \sin \alpha {\left| 00\right\rangle }_{AB}+\cos \alpha {\left| 11\right\rangle }_{AB}\) with a varying parameter α. Its average fidelity with an infinite-dimensional Duan state is guaranteed to surpass a certain threshold, as depicted in Fig. 10b. However, achieving the same task is feasible using finite-dimensional embezzling catalysts. A comparison of dimension requirements for catalytic systems between the convex-split lemma (see Lem. 1) and embezzling states (see Eq. (50)) is also presented in Fig. 10b. The result highlights how embezzling techniques offer advantages in dimensionality reduction, thereby bringing them closer to practical implementation. However, it is important to note that these benefits come at the cost of increased catalyst consumption in terms of purified distance, as depicted in Fig. 10c. Both Figs. 8 and 10 indicate a fundamental trade-off between the dimension requirements for embezzling catalysts and the variation in the catalytic system necessary to achieve a fixed amount of improvement. Systematic investigation and formulation of this trade-off into a quantitative framework will require further research and is left for future exploration.
Entanglement distillation with embezzling catalysts
The essence of teleportation with embezzling catalysts lies in enhancing single-shot entanglement distillation using these catalysts. In the single-shot setting, if Alice and Bob share a noisy bipartite entangled state ρ, and they are limited to LOCC operations, the optimal performance they can achieve in single-shot entanglement distillation is given by
If Alice and Bob employ additional embezzling catalyst \({\tau }_{C{C}^{{\prime} }}\), the optimal performance of single-shot entanglement distillation can be increased to
The performance of catalytic single-shot entanglement distillation is clearly determined by the selection and design of the embezzling catalysts. In the embezzling-state-assisted protocol, as a direct consequence of Lem. 2, if an error tolerance of ϵ is permissible, employing an embezzling state τE (see Eq. (50)) with a dimension of at least \(\lceil {d}^{1/(1-\sqrt{1-\epsilon })}\rceil\) allows us to achieve a fidelity FU of at least 1 − ϵ. Alternatively, by replacing the embezzling state τE in catalytic single-shot entanglement distillation (see Eq. (77)) with τCS (see Eq. (24)), we can implement the convex-split-lemma-assisted single-shot entanglement distillation. The corresponding performance is detailed in the following theorem.
Theorem 4
(Convex-Split-Lemma-Assisted Single-Shot Entanglement Distillation). Given a bipartite quantum state ρ on systems AB with dimension d and an error threshold ϵ > 0, we can construct a bipartite state \(\tau := p{\phi }_{d}^{+}+(1-p)\zeta\) such that \(P(\tau ,{\phi }_{d}^{+}) \, \leqslant \, \sqrt{\epsilon }/2\). Here, ζ is a full-ranked quantum state. Define \(k:= {D}_{\max }(\rho \parallel \tau )\) as the max-relative entropy of ρ with respect to τ. Under these conditions, there exists a catalyst τCS ≔ τ⊗n−1 with n ≔ ⌈2k+2/ϵ⌉ that facilitates
The LOCC operation ΛCS is defined in Eq. (22), and the catalyst state τCS acts on systems \(C{C}^{{\prime} }\), where C ≔ A2…An and \({C}^{{\prime} }:= {B}_{2}\ldots {B}_{n}\), with Ai = A and Bi = B for all i.
Proof
Building on Lem. 1 and the triangle inequality of purified distance, we obtain
By further applying the quantum data processing inequality, we derive the desired result and complete the proof. □
We would like to highlight that the dimension-reduction method for catalytic systems discussed in the part of “Dimensionality Reduction for Catalysts,” which utilizes randomly generated full-ranked quantum states over the maximal mixed state, remains applicable to single-shot entanglement distillation. Similar to catalytic teleportation, the embezzling-assisted protocol generally achieves better performance compared to the convex-split-lemma-assisted single-shot entanglement distillation when the dimensions of the catalytic systems are identical. However, this advantage comes with increased variation in the catalysts. Numerical experiments illustrating these results are presented in Fig. 11.
a, c Depict the required catalyst dimensions for achieving the specified fidelity in catalytic single-shot entanglement distillation from random initial states, with fidelities of 0.70 and 0.75, as shown in Supplementary Table 3. In these figures, τE represents the catalyst dimension based on embezzling states (see Eq. (50)), while \({\tau }^{CS}({n}_{\min }(100,\epsilon ))\) and \({\tau }^{CS}({n}_{\min }({{{{\mathcal{S}}}}}_{{\mathbb{I}}/{d}^{2}},\epsilon ))\) indicate the catalyst dimensions constructed using the convex-split lemma (see Lem. 1). The former method involves selecting 100 randomly chosen full-rank states for constructing τ (see Eq. (24)), whereas the latter employs maximally mixed states \({\mathbb{I}}/{d}^{2}\). b, d Illustrate the consumption of embezzling catalysts during entanglement distillation, measured in terms of purified distance. The blue line represents the upper bound of the consumption for the embezzling catalyst τCS (see Eq. (38)), while the pink line indicates the exact consumption of the embezzling state τE in catalytic entanglement distillation (see Eq. (70)). These comparisons demonstrate that while the embezzling-state-assisted protocol exhibits superior performance at the same catalyst dimension as the convex-split-lemma-assisted protocol, it incurs a greater deviation from its original form during the catalytic entanglement distillation.
Discussion
In this work, we have introduced teleportation with embezzling catalysts, which uses an extra entangled resource, called an embezzling catalyst, to boost the fidelity of teleportation. Unlike exact catalysts, embezzling catalysts are only slightly changed after the teleportation, but can still be recycled for other purposes. By relaxing the constraint of preserving the catalysts throughout the information processing, we can achieve universal catalysts, and teleport quantum information with arbitrary accuracy. To implement our scheme, we constructed embezzling catalysts based on two different methods: the convex-split lemma51 and the embezzling state11. Both methods achieve teleportation with arbitrary precision and ensure arbitrarily small variations in the catalytic system through the use of finite-dimensional embezzling catalysts. As a by-product, we have also investigated single-shot entanglement distillation using the convex-split lemma.
Embezzling phenomena in quantum information theory is the surprising ability to extract resources, such as entanglement, from a reference state without significantly altering it. This is analogous to taking a cup of water from the sea and leaving the sea almost unchanged. However, the dimensionality of the reference state, or the catalyst, is crucial for this task. It is hard to manipulate entangled states precisely in high-dimensional systems. Therefore, we need to use low-dimensional catalysts for high-precision tasks. Here, we explore how to reduce the dimensionality of embezzling catalysts based on the convex-split lemma. We also perform numerical experiments to show that our method outperforms existing ones8 in dimensionality.
Quantum teleportation is one of many quantum communication protocols. It is natural to wonder if similar ideas can improve other quantum information-theoretic tasks58,59,60. For instance, can catalysts such as correlated catalysts or embezzling catalysts increase the capacities of communication channels? This question is fundamental in quantum information theory and has practical implications. However, it is beyond the scope of this work and we leave it for future research61.
Data availability
The data that support the findings of this work are available from the corresponding author Y. X. on request.
Code availability
The code used for the data analysis is available from the corresponding author Y. X. on request.
References
Bennett, C. H. et al. Teleporting an unknown quantum state via dual classical and einstein-podolsky-rosen channels. Phys. Rev. Lett. 70, 1895–1899 (1993).
Bouwmeester, D. et al. Experimental quantum teleportation. Nature 390, 575–579 (1997).
Boschi, D., Branca, S., De Martini, F., Hardy, L. & Popescu, S. Experimental realization of teleporting an unknown pure quantum state via dual classical and einstein-podolsky-rosen channels. Phys. Rev. Lett. 80, 1121–1125 (1998).
Yin, J. et al. Quantum teleportation and entanglement distribution over 100-kilometre free-space channels. Nature 488, 185–188 (2012).
Ren, J.-G. et al. Ground-to-satellite quantum teleportation. Nature 549, 70 (2017).
Liu, J.-L. et al. Creation of memory-memory entanglement in a metropolitan quantum network. Nature 629, 579 (2024).
Knaut, C. M. et al. Entanglement of nanophotonic quantum memory nodes in a telecom network. Nature 629, 573 (2024).
Lipka-Bartosik, P. & Skrzypczyk, P. Catalytic quantum teleportation. Phys. Rev. Lett. 127, 080502 (2021).
Forzatti, P. & Lietti, L. Catalyst deactivation. Catal. Today 52, 165–181 (1999).
Carey, F. & Sundberg, R. Advanced Organic Chemistry: Part A: Structure and Mechanisms Advanced Organic Chemistry (Springer US, 2007).
van Dam, W. & Hayden, P. Universal entanglement transformations without communication. Phys. Rev. A 67, 060302 (2003).
Brandão, F. G. S. L., Horodecki, M., Oppenheim, J., Renes, J. M. & Spekkens, R. W. Resource theory of quantum states out of thermal equilibrium. Phys. Rev. Lett. 111, 250404 (2013).
Åberg, J. Catalytic coherence. Phys. Rev. Lett. 113, 150402 (2014).
Leung, D. & Wang, B. Characteristics of universal embezzling families. Phys. Rev. A 90, 042331 (2014).
Brandão, F., Horodecki, M., Ng, N., Oppenheim, J. & Wehner, S. The second laws of quantum thermodynamics. Proc. Natl. Acad. Sci. U.S.A. 112, 3275–3279 (2015).
Dinur, I., Steurer, D. & Vidick, T. A parallel repetition theorem for entangled projection games. Comput. Complex. 24, 201–254 (2015).
Ng, N. H. Y., Mančinska, L., Cirstoiu, C., Eisert, J. & Wehner, S. Limits to catalysis in quantum thermodynamics. New J. Phys. 17, 085004 (2015).
Berta, M., Christandl, M. & Touchette, D. Smooth entropy bounds on one-shot quantum state redistribution. IEEE Trans. Inf. Theory 62, 1425–1439 (2016).
Palazuelos, C. & Vidick, T. Survey on nonlocal games and operator space theory. J. Math. Phys. 57, 015220 (2016).
Cleve, R., Liu, L. & Paulsen, V. I. Perfect embezzlement of entanglement. J. Math. Phys. 58, 012204 (2017).
Majenz, C., Berta, M., Dupuis, F., Renner, R. & Christandl, M. Catalytic decoupling of quantum information. Phys. Rev. Lett. 118, 080503 (2017).
Anshu, A., Hsieh, M.-H. & Jain, R. Quantifying resources in general resource theory with catalysts. Phys. Rev. Lett. 121, 190504 (2018).
Chen, S., Zhang, X., Zhou, Y. & Zhao, Q. One-shot coherence distillation with catalysts. Phys. Rev. A 100, 042323 (2019).
Lipka-Bartosik, P. & Skrzypczyk, P. All states are universal catalysts in quantum thermodynamics. Phys. Rev. X 11, 011061 (2021).
Beigi, S. & Renou, M.-O. Covariance decomposition as a universal limit on correlations in networks. IEEE Trans. Inf. Theory 68, 384–394 (2022).
Anshu, A. & Jain, R. Efficient methods for one-shot quantum communication. npj Quantum Inf. 8, 1–7 (2022).
Woods, M. P. & Horodecki, M. Autonomous quantum devices: When are they realizable without additional thermodynamic costs? Phys. Rev. X 13, 011016 (2023).
Ramakrishnan, N., Tomamichel, M. & Berta, M. Moderate deviation expansion for fully quantum tasks. IEEE Trans. Inf. Theory 69, 5041–5059 (2023).
Anshu, A., Bab Hadiashar, S., Jain, R., Nayak, A. & Touchette, D. One-shot quantum state redistribution and quantum markov chains. IEEE Trans. Inf. Theory 69, 5788–5804 (2023).
Luijk, L. V., Werner, R. F. & Wilming, H. Covariant catalysis requires correlations and good quantum reference frames degrade little. Quantum 7, 1166 (2023).
Cheng, H.-C. Simple and tighter derivation of achievability for classical communication over quantum channels. PRX Quantum 4, 040330 (2023).
Zanoni, E., Theurer, T. & Gour, G. Complete characterization of entanglement embezzlement. Quantum 8, 1368 (2024).
van Luijk, L., Stottmeister, A., Werner, R. F. & Wilming, H. Embezzling entanglement from quantum fields. Preprint at https://arXiv.org/abs/2401.07292 (2024).
van Luijk, L., Stottmeister, A., Werner, R. F. & Wilming, H. Embezzlement of entanglement, quantum fields, and the classification of von neumann algebras. Preprint at https://arXiv.org/abs/2401.07299 (2024).
Jozsa, R. Fidelity for mixed quantum states. J. Mod. Opt. 41, 2315–2323 (1994).
Tomamichel, M. A framework for non-asymptotic quantum information theory. Preprint at https://arXiv.org/abs/1203.2142 (2013).
Rastegin, A. E. Sine distance for quantum states. Preprint at https://arXiv.org/abs/quant-ph/0602112 (2006).
Nielsen, M. A. The entanglement fidelity and quantum error correction. Preprint at https://arXiv.org/abs/quant-ph/9606012 (1996).
Khachiyan, L. Polynomial algorithms in linear programming. USSR Comput. Math. Math. Phys. 20, 53–72 (1980).
Vandenberghe, L. & Boyd, S. Semidefinite programming. SIAM Review 38, 49–95 (1996).
Boyd, S. & Vandenberghe, L. Convex Optimization (Cambridge University Press, 2004).
Xiao, Y., Fang, K. & Gour, G. The complementary information principle of quantum mechanics. Preprint at https://arXiv.org/abs/1908.07694 (2019).
Xiao, Y., Sengupta, K., Yang, S. & Gour, G. Uncertainty principle of quantum processes. Phys. Rev. Res. 3, 023077 (2021).
Skrzypczyk, P. & Cavalcanti, D. Semidefinite Programming in Quantum Information Science 2053-2563 (IOP Publishing, 2023).
Xiao, Y., Yang, Y., Wang, X., Liu, Q. & Gu, M. Quantum uncertainty principles for measurements with interventions. Phys. Rev. Lett. 130, 240201 (2023).
Yuan, Y. et al. Strong majorization uncertainty relations and experimental verifications. npj Quantum Inf. 9, 65 (2023).
Datta, C., Kondra, T. V., Miller, M. & Streltsov, A. Catalysis of entanglement and other quantum resources. Rep. Prog. Phys. 86, 116002 (2023).
Lipka-Bartosik, P., Wilming, H. & Ng, N. H. Y. Catalysis in quantum information theory. Rev. Mod. Phys. 96, 025005 (2024).
Horodecki, M., Horodecki, P. & Horodecki, R. General teleportation channel, singlet fraction, and quasidistillation. Phys. Rev. A 60, 1888–1898 (1999).
Xing, J. et al. Fundamental limitations on communication over a quantum network. Preprint at https://arXiv.org/abs/2306.04983 (2023).
Anshu, A., Devabathini, V. K. & Jain, R. Quantum communication using coherent rejection sampling. Phys. Rev. Lett. 119, 120506 (2017).
Pirandola, S., Eisert, J., Weedbrook, C., Furusawa, A. & Braunstein, S. L. Advances in quantum teleportation. Nature Photon. 9, 641–652 (2015).
Hu, X., Guo, Y., Liu, B., Li, C. & Guo, G. Progress in quantum teleportation. Nat. Rev. Phys. 5, 339–353 (2023).
Datta, N. Min- and max-relative entropies and a new entanglement monotone. IEEE Trans. Inf. Theory 55, 2816–2826 (2009).
Berta, M., Christandl, M. & Renner, R. The quantum reverse shannon theorem based on one-shot information theory. Commun. Math. Phys. 306, 579–615 (2011).
Duan, R., Feng, Y., Li, X. & Ying, M. Multiple-copy entanglement transformation and entanglement catalysis. Phys. Rev. A 71, 042319 (2005).
Shiraishi, N. & Sagawa, T. Quantum thermodynamics of correlated-catalytic state conversion at small scale. Phys. Rev. Lett. 126, 150502 (2021).
Ekert, A. K. Quantum cryptography based on bell’s theorem. Phys. Rev. Lett. 67, 661–663 (1991).
Bennett, C. H. & Wiesner, S. J. Communication via one- and two-particle operators on einstein-podolsky-rosen states. Phys. Rev. Lett. 69, 2881–2884 (1992).
Żukowski, M., Zeilinger, A., Horne, M. A. & Ekert, A. K. “event-ready-detectors” bell experiment via entanglement swapping. Phys. Rev. Lett. 71, 4287–4290 (1993).
Li, Y. et al. Communication with quantum catalysts. Preprint at https://arXiv.org/abs/2406.14395 (2024).
Jonathan, D. & Plenio, M. B. Entanglement-assisted local manipulation of pure quantum states. Phys. Rev. Lett. 83, 3566–3569 (1999).
Daftuar, S. & Klimesh, M. Mathematical structure of entanglement catalysis. Phys. Rev. A 64, 042314 (2001).
Turgut, S. Catalytic transformations for bipartite pure states. J. Phys. A Math. Theor. 40, 12185 (2007).
Marvian, I. & Spekkens, R. W. The theory of manipulations of pure state asymmetry: I. basic tools, equivalence classes and single copy transformations. New J. Phys. 15, 033001 (2013).
Lostaglio, M., Jennings, D. & Rudolph, T. Description of quantum coherence in thermodynamic processes requires constraints beyond free energy. Nat. Commun. 6, 1–9 (2015).
Bu, K., Singh, U. & Wu, J. Catalytic coherence transformations. Phys. Rev. A 93, 042326 (2016).
Kondra, T. V., Datta, C. & Streltsov, A. Catalytic transformations of pure entangled states. Phys. Rev. Lett. 127, 150503 (2021).
Wilming, H. Entropy and reversible catalysis. Phys. Rev. Lett. 127, 260402 (2021).
Yadin, B., Jee, H. H., Sparaciari, C., Adesso, G. & Serafini, A. Catalytic gaussian thermal operations. J. Phys. A Math. Theor. 55, 325301 (2022).
Rubboli, R. & Tomamichel, M. Fundamental limits on correlated catalytic state transformations. Phys. Rev. Lett. 129, 120506 (2022).
Wilming, H. Correlations in typicality and an affirmative solution to the exact catalytic entropy conjecture. Quantum 6, 858 (2022).
Char, P., Chakraborty, D., Bhar, A., Chattopadhyay, I. & Sarkar, D. Catalytic transformations in coherence theory. Phys. Rev. A 107, 012404 (2023).
Lipka-Bartosik, P., Perarnau-Llobet, M. & Brunner, N. Operational definition of the temperature of a quantum state. Phys. Rev. Lett. 130, 040401 (2023).
Datta, C., Ganardi, R., Kondra, T. V. & Streltsov, A. Is there a finite complete set of monotones in any quantum resource theory? Phys. Rev. Lett. 130, 240204 (2023).
Ganardi, R., Kondra, T. V. & Streltsov, A. Catalytic and asymptotic equivalence for quantum entanglement. Preprint at https://arXiv.org/abs/2305.03488 (2023).
Datta, C., Kondra, T. V., Miller, M. & Streltsov, A. Entanglement catalysis for quantum states and noisy channels. Quantum 8, 1290 (2024).
Luo, Y. H. et al. Quantum Teleportation in High Dimensions. Phys. Rev. Lett. 123, 070505 (2019).
Wu, Y. et al. Multi-channel multiplexing quantum teleportation based on the entangled sideband modes. Photon. Res. 10, 1909–1914 (2022).
Sychev, D. V. et al. Entanglement and teleportation between polarization and wave-like encodings of an optical qubit. Nat. Commun. 9, 3672 (2018).
Langenfeld, S. et al. Quantum Teleportation between Remote Qubit Memories with Only a Single Photon as a Resource. Phys. Rev. Lett. 126, 130502 (2021).
Wan, Y. et al. Quantum gate teleportation between separated qubits in a trapped-ion processor. Science 364, 875–878 (2019).
Fiaschi, N. et al. Optomechanical quantum teleportation. Nat. Photon. 15, 817–821 (2021).
Lago-Rivera, D., Rakonjac, J. V., Grandi, S. & Riedmatten, H. D. Long distance multiplexed quantum teleportation from a telecom photon to a solid-state qubit. Nat. Commun. 14, 1889 (2023).
Acknowledgements
We would like to thank Xiao-Min Hu, and Yu Guo for fruitful discussions. This research is supported by the National Research Foundation, Singapore and A*STAR under its Quantum Engineering Programme (NRF2021-QEP2-02-P03), A*STAR Central Research Funds, and Q.InC Strategic Research and Translational Thrust. J. X., Z. F., and H. M. are funded by the laboratory stabilization supporting program (KY12400210010). D. Q., L. X., and P. X. are supported by the National Key R&D Program of China (Grant No. 2023YFA1406701), the National Natural Science Foundation of China (Grant Nos. 12025401, 92265209, 12104036, and 12305008), and the China Postdoctoral Science Foundation (Grant Nos. BX20230036 and 2023M730198).
Author information
Authors and Affiliations
Contributions
Y. X. supervised the project; J. X. performed numerical simulations; J. X., Y. L., D. Q., L. X., Z. F., H. M., P. X., K. B. and D. E. K. contributed through building the theoretical framework and analysing the numerical data; Y. X. wrote the manuscript with contributions from all authors.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Peer review
Peer review information
Communications Physics thanks Mahdi Chehimi and the other, anonymous, reviewer(s) for their contribution to the peer review of this work.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Xing, J., Li, Y., Qu, D. et al. Teleportation with embezzling catalysts. Commun Phys 7, 357 (2024). https://doi.org/10.1038/s42005-024-01828-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s42005-024-01828-x
This article is cited by
-
Artificial intelligence and blockchain for quantum satellites and UAV-based communications: a review
Quantum Machine Intelligence (2025)