Abstract
In this paper, we introduce a category of Novel Jerk Chaotic (NJC) oscillators featuring symmetrical attractors. The proposed jerk chaotic system has three equilibrium points. We show that these equilibrium points are saddle-foci points and unstable. We have used traditional methods such as bifurcation diagrams, phase portraits, and Lyapunov exponents to analyze the dynamic properties of the proposed novel jerk chaotic system. Moreover, simulation results using Multisim, based on an appropriate electronic implementation, align with the theoretical investigations. Additionally, the NJC system is solved numerically using the Dormand Prince algorithm. Subsequently, the Jerk Chaotic System is modeled using a multilayer Feed-Forward Neural Network (FFNN), leveraging its nonlinear mapping capability. This involved utilizing 20,000 values of x1, x2, and x3 for training (70%), validation (15%), and testing (15%) processes, with the target values being their iterative values. Various network structures were experimented with, and the most suitable structure was identified. Lastly, a chaos-based image encryption algorithm is introduced, incorporating scrambling technique derived from a dynamic DNA coding and an improved Hilbert curve. Experimental simulations confirm the algorithm’s efficacy in enduring numerous attacks, guaranteeing strong resiliency and robustness.
Similar content being viewed by others
Introduction
The exploration into chaotic systems has taken a turn and expanded beyond its traditional paradigms, leading to the discovery and investigation of novel feature chaotic systems1,2,3. These systems, characterized by their distinctive dynamical behaviors and emergent properties, have garnered significant attention because of their potential applications in numerous areas including cryptography4,5, secured communication6, and nonlinear control7. The Feature chaotic systems exhibit a rich spectrum of behaviors, ranging from irregular dynamics to complex attractors with intricate geometries. Unlike conventional chaotic systems, feature chaotic systems often possess unique characteristics, such as multiple coexisting attractors8, multi-spiral chaos9, Symmetric strange attractors10, extreme multistability11, mega-stable behavior12, multi-transient behavior13, intermittent transients14, high-dimensional chaos15, or specific synchronization phenomena16. These distinctive features challenge existing theoretical frameworks and computational methodologies, necessitating innovative approaches for their analysis and understanding.
Recently, machine learning has emerged as a prominent solution for addressing a multitude of challenges in chaotic systems, particularly in prediction and categorization tasks. For instance, Omidvar17 introduces an innovative algorithm aimed at determining the structure of RBF networks for dynamic modeling of chaotic time series. Meanwhile, Han et al.18 explore a novel methodology based on RPNN for modeling and predicting chaotic time series, outperforming Kalman filter and universal learning networks compared based on accuracy and RMSE. Additionally, Chang and Tsai19 present an advanced BPNN model specifically designed for analyzing signal deviation time series in the stock market, surpassing traditional approaches like ARMA and RBFNN, as evidenced by reduced MAD values. Using robust location estimates and neural networks, Chatzinakos and Tsouros20 propose a novel algorithm for estimating chaotic dynamical systems’ dimension, while Wichard21 develops a machine learning technique hybridizing three models namely the artificial neural network, 1-year-cycle, and the nearest trajectory, for NN5 time series forecasting. Furthermore, He et al.22 introduce a novel CBP neural network procedure, leveraging the advantages of the Chebyshev map to mitigate premature convergence issues. Despite these advancements, accurately reproducing signals and diagrams remains challenging due to the highly complex and nonlinear dynamics involved. Thus, we leverage the capability of ANN to learn the intricate nonlinear dynamics of this system.
The advancement of chaotic encryption algorithms has witnessed significant theoretical strides, with researchers discovering relationship between the degree of randomness exhibited by chaotic orders to the efficacy of encryption algorithm. Based on coupled TSM and coupled LTM, Luo et al.23 devised a fresh encryption framework incorporating permutation-EC-ElGamal encryption-diffusion, introducing a crossover permutation approach. Wang et al.24 defined an innovative color image encryption system utilizing a hyper-chaotic scheme built upon a tri-valued memristor. The generation of initial key makes use of the plaintext image, by incorporating a permutation sequence structured with a Hash table. Murali and Sankaradass25 proposed a straightforward and rapid image encryption method based on SFC, introducing a novel saw-tooth diffusion and square-wave confusion techniques for encrypting swift image. Shahna and Mohamed26 proposed a fresh symmetric key encrypting method employing cyclic shift operation, scan method, chaotic map, utilizing Hilbert curve and Henon map. Moysis et al.27 introduced a new B-spline encryption algorithm and analyzed mappings utilizing multiple remainder operators. Lai et al.28 investigated a novel medical image encryption scheme that leverages compressive sensing techniques based on a newly designed memristive hyperchaotic system and introduces a new HNN that utilizes a memristor designed with hyperbolic tangent functions as a synapse, enabling the generation of multiscroll attractors29. Acknowledging the challenges in fractal-based encryption methods, particularly regarding time consumption and encryption restrictions, we introduce a novel algorithm for image encryption utilizing Hilbert curve scrambling and dynamic DNA coding to enhance efficiency in encryption.
Many studies related to chaotic systems are applied using jerk systems such as Chen et al.30 presented a novel four-dimensional chaotic jerk system characterized by coexisting and hidden attractors, with only one constant term. The system was implemented on FPGA to facilitate the discretization and simulation of chaotic behavior. Folifack Signing et al.31 proposed a cryptosystem for encrypting both text and images, leveraging the special randomness of a chaotic Jerk system with a hump structure and DNA coding. Vivekanandhan et al.32 investigated chaotic jerk oscillator with non-polynomial and piecewise linear terms to shape attractors and its application in the image encryption.
Based on the motivation above, we introduced and analyzed a new category of chaotic oscillators termed NJC oscillators, distinguished by their symmetrical attractors using dynamical analysis. Furthermore, we illustrate the NJC system’s capability to exhibit chaotic behavior, irregular and regular reverse period-doubling phenomena, periodic behavior, and coexisting attractors. Besides that, the NJC System is modeled using a multilayer FFNN, leveraging its nonlinear mapping capability and identifies the most suitable FFNN architecture for modeling the NJC system accurately. Finally, the paper presented an image encryption scheme that integrates the NJC system, incorporating dynamic DNA coding and improved Hilbert curve scrambling.
Mathematical model of the proposed NJC system
This work proposed a novel NJC system defined as the follows:
We assume that X denotes the state \(({x}_{1},{x}_{2},{x}_{3})\) and \(a,b,c\) are positive constants.
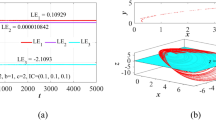
The NJC system (1) exhibits rotation symmetry centered around the \({x}_{3}\) coordinate axis. In this study, we showed that (1) is chaotic for \(a=4, b=0.72\) and c = 0.48, with \({x}_{1}\left(0\right)=0.1,\)\({x}_{2}\left(0\right)=0.1\) and \({x}_{3}\left(0\right)=0.2\) as the initial conditions. The Lyapunov exponents (LE) of the NJC formula (1) for these initial and parameter values were computed via MATLAB with \({L}_{1}=0.1866,\)\({L}_{2}=0\) and \({L}_{3}\)=\(-0.6666.\) Thus, the NJC scheme (1) has dissipative motion with a chaotic attractor. The chaotic NJC system (1) has the Kaplan dimension given by
Next, the rest points correspond to NJC system (1) are acquired in the chaotic case by arranging the values for \(a=4, b=0.72\) and c = 0.48, and thus solving the equations below:
Solving the equations (3a) and (3b), we get \({x}_{2}={x}_{3}=0.\) Then Eq. (3c) reduces to
Solving (4) we get three roots as follows: \({x}_{1}=0\) or \({x}_{1}=\pm 0.8814.\)
Thus, the proposed NJC system (1) has three rest points given by \({A}_{0}=\left(\text{0,0},0\right),\)\({A}_{1}=(\text{0.8874,0},0)\) and \({A}_{2}=\left(-\text{0.8874,0},0\right).\)
The linearization matrix’s eigenvalues for NJC scheme (1) at \({A}_{0}\) in the chaotic case are given by \(0.6705, -0.5753\pm 1.0773 i,\) demonstrating that \({A}_{0}\) unstable and a saddle-focus rest point.
Meanwhile, at \({A}_{1}\) and \({A}_{2}\), the linearization matrix’s the eigenvalues of (1) in the chaotic case are given by \(-1.0104, 0.2652\pm 1.0888 i,\) demonstrating that \({A}_{1}\) and \({A}_{2}\)are also saddle-foci rest points and unstable.
Since the rest points of the proposed NJC scheme (1) are unstable, in the chaotic case the system (1) is said to have a self-excited attractor.
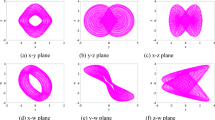
MATLAB signal plots for the NJC system (1) is shown in Fig. 1 with values of the parameter defined as \(a=4, b=0.72, c=0.48\) and the initial state \({x}_{3}\left(0\right)=0.2, {x}_{2}\left(0\right)=0.1,\) and \({x}_{1}\left(0\right)=0.1\).
Dynamical analysis
Fix b = 0.78, c = 0.48, and vary a
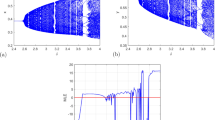
To determine the sensitivity behavior of proposed NJC system (1) to changes in parameter a, the LEs spectrum and the bifurcation figure are depicted in Fig. 2 with a increases from 4 to 20. By studying these two diagrams, we noted that the NJC system (1) can display a variety of behaviors dependent on the value of a. When a increases, the system (1) can display chaos, no-regular reverse period-doubling, and periodic behavior.
When a\(\in\)[4, 9.8], the new 3-D Jerk scheme (1) exhibits the ownership of one positive LE (refer to Fig. 2b). For this interval of parameter a, (1) exhibits chaotic behavior as demonstrated in Fig. 2a. In order to show an example of the chaotic attractors generated by NJC system (1) when a\(\in\)[4, 9.8], we select a value from this interval and set it to a as follow: a = 6. Then, the x1-x2 chaotic attractor of NJC system (1) is plotted for a = 6 as illustrated in Fig. 4a, the connecting LEs and DKY are:
-
LE1 = 0.146, LE2 = 0 and LE3=-0.624.
-
DKY=2.234.
When a\(\in\)[9.8, 20], the NJC system (1) experience the well-known dynamical feature of reversal period doubling cascade (RPDC) exiting from chaos. As shown in Fig. 2(a), system (1) shows a no-regular period doubling route described as follow (chaos ◊ period-10 ◊ period-5 ◊ period-3 ◊ period-2 ◊ period-1). A detailed description is given as follows:
When a\(\in\)[4, 9.8], system (1) displays chaotic behavior as shown in Fig. 3(a). When a\(\in\)[9.80, 9.94], system (1) generates period-10 attractor as shown in Fig. 3(b) which is plotted for a = 9.84. When a\(\in\)[9.94, 10.45], system (1) generates period-5 attractor as shown in Fig. 3(c) which is plotted for a = 10.35. When a\(\in\)[10.45, 12.01], system (1) generates period-3 attractor as shown in Fig. 3(d) which is plotted for a = 11. When a\(\in\)[12.01, 15.1], system (1) generates period-2 attractor as shown in Fig. 3(e) which is plotted for a = 13. When a\(\in\)[15.1, 20], system (1) displays period-1 attractor as shown in Fig. 3(f) which is plotted for a = 17.
Fix a = 4, c = 0.48, and vary b
To explore the behavior of proposed NJC scheme (1) against changes in parameter values of b, the LEs spectrum and the bifurcation plot are illustrated in Fig. 4 with b increasing from 0.7 to 1.2. By analysing these diagrams, we noted that, the NJC system (1) can display chaos, no-regular reverse period-doubling, and periodic behavior depending on the value of b.
When b\(\in\)([0.700, 0.810], [0.817, 0.858], [0.905, 0.920], [0.944, 0.950]), the NJC system (1) exhibits the ownership of one positive LE (refer to Fig. 4(b)). For this set of intervals, (1) exhibits chaotic behavior as demonstrated in Fig. 4(a). As example, we take b = 0.75. Then, the x1-x3 chaotic attractors for (1) is plotted as in Fig. 5(a), the corresponding LEs and DKY are:
-
LE1 = 0.237, LE2 = 0 and LE3=-0.717.
-
DKY=2.331.
When b\(\in\)([0.810, 0.817], [0.858, 0.905], [0.920, 0.944], [0.950, 1.200]), the NJC system (1) exhibits no ownership of positive LE (refer to Fig. 3(b)). Hence, the system is said to behave periodically for these regions of parameter b. Moreover, the NJC system (1) experiences the well-known dynamical feature of RPDC exiting from chaos. As shown in Fig. 3(a), system (1) shows a no-regular period doubling route described as follow (chaos ◊ period-10 ◊ period-5 ◊ period-3 ◊ period-2 ◊ period-1). A detailed description is given as follows:
When b\(\in\)[0.92, 0.93], system (1) generates period-10 attractor as depicted by Fig. 5(b) which is plotted for b = 0.924. When b\(\in\)[0.93, 0.96], system (1) generates period-5 attractor as shown in Fig. 5(c) which is plotted for b = 0.94. When b\(\in\)[0.96, 0.99], system (1) generates period-3 attractor as shown in Fig. 5(d) which is plotted for b = 0.98. When b\(\in\)[0.99, 1.06], system (1) generates period-2 attractor as shown in Fig. 5(e) which is plotted for b = 1.02. When b\(\in\)[1.06, 1.2], system (1) displays period-1 attractor as shown in Fig. 5(f) which is plotted for b = 1.14.
Fix a = 4, b = 0.72, and vary c
The sensitivity behavior of the NJC system (1) to the changes in parameter c will be studied in this subsection. For that reason, the LEs spectrum and the bifurcation plot are illustrated in Fig. 6 with c increasing from 0.45 to 1.2. By examining these two diagrams, we deduced that the NJC system (1) can display chaos, regular RPDC exiting from chaos, and periodic behavior depending on the value of c.
When c\(\in\)([0.450, 0.535], [0.550, 0.690], [0.696, 0.720], [0.733, 0.955]), the NJC system (1) exhibits the ownership of one positive LE (refer to Fig. 6(b)). For these regions of parameter c, (1) exhibits chaotic behavior as demonstrated in Fig. 6(a).
We take c = 0.5. Then, the x2-x3 chaotic attractor of system (1) is plotted in Fig. 7(a), the corresponding LEs and DKY are:
-
LE1 = 0.202, LE2 = 0 and LE3 = - 0.701.
-
DKY=2.288.
When c\(\in\)([0.535, 0.550], [0.690, 0.696], [0.720, 0.733], [0.955, 1.200]), the NJC system (1) exhibits no ownership of positive LE (refer to Fig. 6(b)). Hence, it is said to behave periodically for this set of intervals. Moreover, system (1) experiences the well-known dynamical feature of RPDC exiting from chaos. As shown in Fig. 6(a), the proposed scheme (1) shows a regular period doubling route described as follow (chaos ◊ period-8 ◊ period-4 ◊ period-2 ◊ period-1). A detailed description is given as follows:
When c\(\in\)[0.955, 0.960], system (1) has period-8 attractor as shown in Fig. 7(b) which is plotted for c = 0.958. When c\(\in\)[0.96, 0.98], system (1) has period-4 attractor as shown in Fig. 7(c) which is plotted for c = 0.965. When c\(\in\)[0.98, 1.08], system (1) has period-2 attractor as shown in Fig. 7(d) which is plotted for c = 1. Finally, when c\(\in\)[1.08, 1.2], system (1) has period-1 attractor as shown in Fig. 7(e) which is plotted for c = 1.14.
Multistability and coexisting attractors
In nonlinear dynamics, the study on multistability has recently gained a lot of attention due to its importance. A multistable chaotic system can produce different coexisting attractors while maintaining constant values of parameters but varying initial conditions33,34,35. Therefore, multistable chaotic systems provides a significant number of choices for the building chaos-based real-world applications. To show that our proposed Jerk system (1) experiences the phenomenon of multistability, we plotted the bifurcation graph of proposed scheme (1) against parameter c for two types of initial points.
For the new Jerk scheme (1), let’s define Y0 and Z0 as the two distinct initial points with their values given as:
The bifurcation plot of (1) for Y0 and Z0 is illustrated in Fig. 8 when c\(\in\)[0.45, 1.2]. The blue one is started from the initial point Y0 and the red one is started from Z0. From Fig. 8, we can observe that: when c\(\in\)[0.45, 0.75], the scheme (1) has almost the same chaotic attractor for both Y0 and Z0 as clearly shown in Fig. 9(a). When c\(\in\)[0.760, 0.955], (1) has coexistance of two distinct chaotic attractors instituting from Y0 and Z0 as clearly shown in Fig. 9(b). When c\(\in\)[0.955, 0.960], system (1) has coexistance of two period-8 attractors as shown in Fig. 9(c). When c\(\in\)[0.96, 0.98], system (1) has coexistance of two period-4 attractors as shown in Fig. 9(d). When c\(\in\)[0.98, 1.08], (1) has coexistance of two period-2 attractors as shown in Fig. 9(e). Finally, when c\(\in\)[1.08, 1.2], (1) has coexistance of two period-1 attractors as shown in Fig. 9(f).
Numerical phase plots of different coexisting attractors of scheme (1) in the x1-x2 plane: (a) chaotic attractors (c = 0.5), (b) two coexisting chaotic attractors (c = 0.85), (c) coexistance of two period-8 attractors (c = 0.958), (d) coexistance of two period-4 attractors (c = 0.965), (e) coexistance of two period-2 attractors (c = 1), (f) coexistance of two period-1 attractors (c = 1.14).
Circuit design
In this work, the system’s circuit is built utilizing Multisim 14.0, a circuit simulation software, to confirm the accuracy and viability of the scheme. Figure 10 displays the circuit schematic of proposed NJC scheme (1). The TL082CD operational amplifier is employed for circuit integration during simulation, while linear resistor and capacitor regulate system parameters. Additionally, the analog multiplier AD633JN, operating at a voltage range of ± 15 V, is utilized to introduce nonlinear terms. The equation of circuit for (1) can be derived from Kirchhoff’s circuit laws.
The electronic component depicted in Fig. 10 takes the following values: R1 = R3 = 400 kΩ, R4 = 555.56 kΩ, R5 = 833.33 kΩ, R6 = 40 kΩ, R17 = R16 = R15 = R14 = R13 = R12 = R11 = R10 = R9 = R8 = R7 = R2 = 100 kΩ, C1 = C2 = C3 = 1 nF. In Fig. 10, the circuit designed is the multi-wing chaotic circuit. The chaotic circuit evidently produces chaotic attractors (see Fig. 11), thereby confirming the preceding theoretical analysis and numerical simulation outcomes.
ANN-based new jerk chaotic (NJC) PRNG on FPGA
The main important features of chaotic systems are that they exhibit non-periodic behavior, that they are sensitive to initial conditions, that they exhibit non-periodic behavior in the system state space, and that they are extremely sensitive to changes in system parameters36. Chaotic signal generators, one of the most basic structures that should be used in chaotic systems, can be realized in two different ways: analog and digital. It is well-known that digital circuit-based chaotic generators are generally more advantageous than analog-structured chaotic generators. The best solution for these problems is to implement chaotic generators using digital hardware.
Digital circuit based chaotic generators can be implemented with different integrated structures in literature such as Digital Signal Processors (DSPs), Application Specific Integrated Circuits (ASICs) and Field Programmable Gate Arrays (FPGAs)37. FPGA chips have a very flexible structure, as well as being able to perform parallel processing. In addition, the design and testing costs of FPGA chips are much lower than ASIC-based applications. Another important point is that FPGA-based chaotic systems and the applications using these systems are more flexible thanks to their digital base and reprogrammability. Chaotic circuit models are suitable for implementation in reprogrammable or reconfigurable systems. In this way, chaotic systems can produce signals in different forms according to parameter changes. For such reasons, FPGA-based modeling of chaotic systems provides significant advantages over analog-based or other digital processor-based chaotic generators37,38,39,40,41.
Similar to the nonlinear structure of chaotic systems, an Artificial Intelligence (AI) scheme commonly referred to as Artificial Neural Network (ANN) has been known to be able to detect the nonlinearity properties in the formation of real-world problems, using its adaptive abilities and changing its own weights and biases according to the available data. Biologically inspired ANNs are distributed information processing systems and consist of massively parallel nonlinear computations. Therefore, we can exploit this sophistication for high-speed operations of real-time applications via the implementation of parallel hardware structure36.
Since FPGA chips are inherently parallel devices, they are very suitable for hardware applications of ANN. FPGA-based ANN applications not only maintain the parallel structure of the network and enable working but also provide flexible, reconfigurable designs that are suitable for hardware implementation37. At this point, ANNs are used in modeling systems thanks to their ability to map complex nonlinear relationships, error tolerance and handle noisy data.
Modeling chaotic systems with noise-like nonlinear properties using ANN has made it possible to use these modeled systems in cryptologic applications including secure communication, digital signature and embedded systems that today’s technology requires. In recent years, chaotic oscillator and chaotic-based random number generator designs using artificial neural networks (ANN) on FPGA have been published in the literature38,39,40,41.
Random numbers are used for specific purposes in many different disciplines of engineering. The success of these applications relies upon the generated sequence randomness, and therefore the process of generating these numbers is of primary importance. Random numbers are defined as a series of independent numbers having a predefined distribution and a determined probability of falling on values within a particular range is referred to as random numbers39. These generators are structures that have the capacity to generate output at a degree of unpredictability that is not predictable from historical data. Due to these features, many applications such that found in cryptography, equation solutions, numerical analysis, music and graphic composition, simulation, modeling and testing, digital signatures and secure communication making use of random number generators42,43.
In this study, the New Jerk Chaotic (NJC) system has been computationally solved via Dormand Prince technique. Input and output values consist of 10,000 samples generated with the technique. Then, for the process of the modelling the New Jerk Chaotic (NJC) system, since Feed-Forward Neural Network (FFNN) provides a general prediction method and having one hidden layer is sufficient in many cases, this FFNN structure having one hidden layer has been chosen. The network structure and its parameters are presented in Fig. 12; Table 1, respectively.
As can be observed from Fig. 12, the modeling of NJC system has been performed using 3 × 8 × 3 FFNN structure. In order to gain nonlinearity to model the New Jerk Chaotic system, 8 neurons, each containing a Log-Sigmoid activation function, were used in the hidden layer of the network structure and 3 neurons, each containing a linear activation function, were used for the output layer. In this step, 10,000 values of x1, x2 and x3 have been applied to the input of the FFNN structure for the train (70%), validate (15%) and test (15%) processes. Therefore, there are 3 neurons in the input layer. The target for x1, x2 and x3 values are the iterative values of x1, x2 and x3. So, there are 3 neurons in the output layer.
Since the number of neurons in hidden layer depends on the system to be modeled, various structures with different numbers of hidden neurons were tried, and several trainings were performed. There is one hidden layer with 8 neurons and an output layer with 3 neurons. MSE value has been obtained as 7.28e-08; the sensitivity with this level is enough for the modeling of NJC system using FFNN structure and the implementation of this structure on FPGA. On the one hand, using more than 8 neurons in hidden layer is possible and this gives more accurate results. On the other hand, this creates more computational cost, more resource utilization needs for the FPGA implementation and increases the response time of the network. In other words, there is a tradeoff between the modeling performance and computational performance and this is a challenging problem to be handled for the FPGA implementation of FFNN structures.
The network has been trained several times using different initial weights and biases. After 200,000 iterations, the outputs of the network model have been converged to the target values, with the precision of 1.6e-09 as shown in Fig. 13. An important tool for evaluating the network performance is the scatter plot of network outputs versus targets. As can be observed from Fig. 13, the points in the scatter plot fell close to the 45° output = target line. For this reason, the fit is almost excellent.
Figure 14 depicts the MSE against the number of iterations, with using the Levenberg-Marquardt training algorithm. MSE is an accepted measure of the performance index generally utilized in FFNN. The network has been trained for 200,000 iterations; at which time the performance changing has been very little as 7.28e-08. This value shows the network model can accurately map the input-output relationship.
As mentioned above, in the hidden layer, the size of neurons that has exponential activation function directly affects the chip utilization statistics of the implementation of FPGA. For this reason, not only to model the NJC system using FFNN but also to implement this model is an important trade-off that should be handled. Since the performance of the training network gives a satisfactory degree as 7.28e-08 using minimum number of neurons in hidden layer and the existence of 8 neurons in hidden layer does not create a problem related to the response time and resource utilization, as a result, implementation of FFNN structure on FPGA is continued with this selected structure.
After the successful results obtained from the training and testing stages in the process of developing the ANN-based chaotic model from the new 3-D Jerk system on FPGA, the real-time ANN-based NJC PRNG model stage on FPGA initiated. In this stage, to realize the PRNG design with the novel 3-D Jerk chaotic scheme on FPGA hardware, ANN-based NJC PRNG are modelled in VHDL via the high-precision floating point number standard (32-bit IEEE-754-1985). The top-level view of the proposed block diagram is given by Fig. 15. The module includes 1-bit input signals namely clk, start and reset, and 1-bit PRNG_out and Ready output signals.
Figure 16 illustrates the second top level block plot of the ANN-based NJC PRNG scheme implemented on FPGA. The design includes MUX, ANN_Based_Chaotic_Oscillator, Quantification, XOR_Unit and Ring_Osc units. The MUX unit is accounted for providing initial requirements needed by the chaotic oscillator. The chaotic oscillator takes the initial values as constant until it produces its first results. From the moment the oscillator starts to produce the first values, this value is sent to the MUX unit, and the MUX unit sends this value to the chaotic oscillator as an initial condition. ANN-based chaotic oscillator unit is designed for modeling chaotic system. The chaotic signals produced here are sent to the Quantification unit and discretized. In the design, a ring oscillator was used to increase the randomness quality of the ANN-based NJC PRNG system. Random values coming from Quantification and Ring oscillator are subjected to XOR operation in the XOR unit and transmit to the PRNG_out output. At this moment, the PRNG_Ready output is ‘1’.
A testbench was designed in VHDL to test the ANN-based NJC PRNG unit on the designed FPGA. The designed system was tested by running it with ISIM which is one of the Xilinx ISE Design Tools. The graph of testbench results is displayed in Fig. 17.
To assess the quality of randomness for the Random Number Generators (RNG) produced bit sequences, NIST 800-22 Statistical Test Set is preferred over other test packages. Therefore, in order to prove the random numbers produced by the PRNG design presented in this study is suitable to be used in cryptographic applications, the obtained bit sequences must pass a list of tests specified in the international guidelines found in the NIST 800-22 Test Suite. This statistical suite comprises fifteen tests designed to evaluate the unpredictability of binary sequences produced by cryptographic random or PRNG that are based on hardware or software. These tests concentrate on diverse forms of non-randomness that could be present in a series, and certain tests can be divided into multiple smaller tests. Performing NIST Tests would require bitstreams of 1 Mbit length. Subsequently after succeeding with the PRNG employing ANN-based chaotic oscillator, VHDL codes was generated for testing the output sequence according to NIST Test cases.
Xilinx ISE design tool was responsible for compiling the code while the random bit sequences generated from the simulated FPGA-based design were stored in a .txt format. When testing with more than one subtest, the p value was evaluated as the arithmetic mean. The test results for the proposed ANN-based NJC PRNG are presented in Table 2. Based on the Random-Excursions Test, 18 results were produced for the x value in the PRNG modelled with the chaotic entropy seeds, and only one test result was given in the table, while another 17 met the test criteria. The results for the other 15 different tests from the NIST 800-22 Test Suite were recorded by focusing to the p values (probability values). The fact that the \(p\) values \((p>0.01)\) from all tests proved that the generated bits sequence has shown excellent statistical properties.
The ANN-based NJC PRNG unit designed on Virtex-6 ML605 FPGA Evaluation Platform (device: XC6VLX240T, package: FF1156, speed: − 1) was synthesized with Xilinx ISE Design Tools. The chip resource utilization rates acquired after the Place & Route procedure are shown in Table 3. According to the results, the operating frequency maximum value of the proposed unit was found to be 114.903 MHz. In the design, since a random 1-bit value can be generated at each clock cycle, the designed systems’ bit generation rate was obtained as 114.9 Mbit/s.
Image encryption using 2-D Hilbert curve
This section deals with the implementation of the proposed 3D chaotic system to support image encryption. To verify the feasibility and effectiveness of this method, we selected five the standard grey-scale images (Moon surface, finger, hill, Boat, and Pepper) with a size of 256 × 256 from the image database http://sipi.usc.edu/database/. There are two categories of the encrypting algorithms: diffusion and permutation, and the image is encrypted according to the structure “permutation-diffusion-permutation-diffusion”. The design of the defined image encryption procedure is illustrated in Fig. 18.
The proposed image encryption algorithm
Key generation
The use of adaptive keys can significantly improve the security of encrypted images by increasing their resistance to attacks based on plaintext. The values for initial condition and other parameters of the chaos mapping are constructed from the hash value from the plaintext image.
A minor change in the plaintext image will tremendously change the hash value, and likewise significantly affecting the parameters and initial guesses of the chaotic scheme. The SHA-256 procedure is used to generate the 256 bits hash H by taking the plaintext image as an input. The 3D chaotic system transforms H into the initial values by byte-dividing into 32, denoted as h1, h2, …, h32.
Initial guesses x1(0), x2(0), and x3(0) needed by the 3D chaotic system need to be calculated upfront. We can use Eq. (6) to achieve this purpose.
where \({x}_{1}^{{\prime }}\)(0), \({x}_{2}^{{\prime }}\left(0\right)\), and \({x}_{3}^{{\prime }}\left(0\right)\) denotes the given values. The initial guesses produced by this technique have the benefits of randomness. Using these values, the 3D chaotic system can operate to generate three pseudo-random sequences, that are LX (Lx1), LY(Lx2), and LZ(Lx3).
Image permutation
The permutation method of information encryption involves rearranging the image pixel matrix in order to break the image matrix’s correlation. In this process, image transmission in a safe manner can be accomplished. In this paper, we use a combination of global permutation and local permutation to achieve the purpose of permutation.
Global permutation
Given a pseudo-random sequence LX, we proceed by sorting the sequence into an ascending order to produce another new sequence X and a permuted index sequence Index, and use the index sequence index as a scrambled vector to permute the image.
Local permutation
In 1891, the German mathematician Hilbert gave the Hilbert curve to fill a square grid, using this continuous curve to traverse every node. Figure 19 demonstrate a route of a Hilbert curve through the grid. The basic idea of applying the two-dimensional Hilbert curve to image scrambling is to scan the pixels of an image matrix in turn according to the traversal rules of the two-dimensional Hilbert curve, store them in a one-dimensional sequence, and then rearrange them to generate the scrambled image.
Pixel diffusion
Diffusion enhances the mutual influence between pixels, so that small changes in the plaintext can be diffused into the entire ciphertext, enhancing the algorithm’s ability to resist differential and statistical attacks. This paper uses the generated chaotic sequence and the previous pixel value to calculate according to the formula, and the calculated value is used as the current pixel value, which can effectively propagate the changes of a small amount of plaintext image to the entire encrypted image. According to Eq. (7), each element of the pseudo-random sequence LY and LZ sequence is preprocessed respectively.
The image matrix is converted into a one-dimensional sequence S = {s1, s2, s3 ,… sM×N } of length M × N in row-first order, and the image matrix after forward diffusion is noted as C = {c1, c2, c3 ,… cM×N }, and the matrix after backward diffusion is noted as D = {d1, d2, d3 ,… dM×N }. The forward diffusion process is shown in Eq. (8).
where the initial value c(0) = 127, and i = 1, 2, …, M*N. Meanwhile, the backward diffusion process is shown in Eq. (9).
where the initial value d(M + N + 1) = 127, and i = M*N, …,2, 1.
The proposed algorithm
The steps of the encryption scheme proposed in this paper are as follows.
Step 1: Convert the grey-scale image matrix P into a two-dimensional matrix P1of size M*N.
Step 2: Based on the given plaintext image, use the SHA-256 algorithm to obtain its hash value and calculate the initial values x0, y0, z0.
Step 3: Iterate over the proposed 3D chaotic system, eliminate a designated number of iterations to minimize transient effects, and obtain the three sequences LX, LY, and LZ, each with length M*N.
Step 4: Reconstruct the image matrix P1 into a one-dimensional sequence, sort in ascending order the sequence LX to produce the index sequence, which later be used to permute position-wise the pixel from the image sequence to obtain a scrambled image sequence P2.
Step 5: Preprocess LY(Eq. (7)) and perform the forward diffusion operation on the image sequence P2 (Eq. (8)), converting the diffused pixel sequence into an image matrix of M*N according to the length M as a row, which is the image matrix P3.
Step 6: Local permutate of the image matrix P3 using a Hilbert curve to produce a new image matrix P4.
Step 7: Preprocess LZ(Eq. (7)), backward diffused the image (Eq. (9)), transform the diffused pixel sequence into an M*N image matrix according to the length M as a row, the image matrix is named P5, correspond to cipher image.
Experimental results and analysis
To test our proposed image encryption algorithm, the standard grey-scale images Moon surface, finger, hill, Boat, and Pepper of size 256*256 are selected as plain images and the following initial values \({x}_{0}^{{\prime }}=0.1, {y}_{0}^{{\prime }}=0.1, {z}_{0}^{{\prime }}=0.2\) are chosen. Figure 20 shows the simulation results. It is clearly observable the capability of cipher image to hide the plaintext and render the information to unrecognizable. The decrypted image is identical to the plain image, which shows that the algorithm of this paper has good encryption and decryption effects. The effectiveness and security of the encryption algorithm are further demonstrated through histogram, information entropy, and correlation analyses.
Keyspace analysis
The key space is the range in which the encryption key can be selected in size and is generally measured in bits. The encryption scheme proposed uses a 3D chaotic system having a large parameter space and therefore a large key space can be obtained. The algorithm is considered to be effective against exhaustive attacks whenever its size get larger than 2128. This scheme makes use of the three initial parameters as the key, and the accuracy of the parameters and initial values of each system can reach 10− 14, and its space reaches 1042, which is much larger than 2128. Therefore, this algorithm can resist exhaustive attacks.
Histogram analysis
The histogram analysis shows how the pixel values are distributed across image. Based on some statistical properties of the plain image, an attacker may be able to break the encryption system if they count a certain amount of useful information. Therefore, the cipher images need to present as little useful information as possible to make the encryption system more secure. Figure 21 shows the histograms of the five sets of plain images and their corresponding cipher images, from which we can conclude that the histograms of the plain images are concentrated and follow a certain pattern, while the histograms of the cipher images are distributed evenly. This observation clearly evident the effectiveness of the proposed algorithm in hiding useful information in plain images while resisting statistical attacks.
Correlation coefficient analysis
This analysis determines how related are the adjacent pixels within an image. A safe and effective encryption system needs to have the characteristics of low correlation between adjacent pixels. In this paper, the correlation coefficient is used to measure the relation among adjacent pixels within an image. The formula is given by Eq. (10):
where x and y are pairs of neighboring pixels in plain or cipher image, E(x) is the expectation of x, D(x) is the variance of x, and N is the total number of pixels available.
Calculations were made for adjacent pixel in three directions; horizontal, vertical, and diagonal directions. The results are shown in Fig. 22, we can see that there is a strong correlation among neighboring pixels in all three directions within the plain image, which shows approximately a linear distribution. For cipher image, we can see that the scatter plot is close to random distribution, indicating the low correlation between adjacent pixels.
Table 4 shows the values of correlation coefficient measured in all three directions, between two adjacent pixels. By comparing and analyzing the values from each plain images and their respective cipher images, we observed a significantly reduction in the correlation factor among neighboring pixels in the original image.
Information entropy analysis
This type of analysis is commonly used for measuring the uncertainty within an image, and we use information entropy to measure the degree of chaos in a cryptographic system. The calculation is shown in Eq. (11).
Here p(x) is the probability of a greyscale value of i, and N = 256.
The local information entropy can further analysis of the level of chaos in an image. By dividing the image into regions, the information entropy is then calculated for each region and fused into the complete image. The results of information entropy and local information entropy are shown in Table 5, where we can see that the information entropy value before encryption is relatively small, while that of cipher image is nearing to 8. The local information entropy is also close to the ideal value of 8. This number evidently shows the good performance and effectively of the proposed algorithm in hiding the information into an image.
Chi-square test
The result of the chi-square test is that the amount of useful information in the cipher image can be examined quantitatively by the pixel distribution. It is calculated as shown in Eq. (12).
In general, when conducting the chi-square test, we use a significance level of α = 0.05 and a theoretical value of 293.24783. Both plain imagen and cipher image have undergone the test and their results can be found in Table 6. We can see that the chi-square test results for the plain images are all greater than the theoretical value, while the chi-square test results for the cipher images are all lesser.
Differential attack
A differential attack is used to break an encryption system by means of inducing a minor change to the plain image, and consequently begin an investigation based on the distinction between the altered cipher image against the normal encrypted cipher image. There are two parameters that are commonly used to determine the resistance of the proposed algorithm against differential attacks. The first one is called the number of pixels change rate (NPCR) calculated according to Eq. (13), while the second is the uniform average change intensity (UACI) calculated according to Eq. (14).
where M and N represent the width and height of the two images, C1 and C2 represent the two different cipher images, one corresponds to before pixel changes and the other after pixel changes, on the plain image respectively. In a case of C1(i, j) ≠ C2(i, j), we obtain D(i, j) = 1, while for others D(i, j) = 0. In theory, for the best encryption effect scenario, the respective values for NPCR and UACI are 99.6093% and 33.4635%. In our simulation, the results are shown in Table 7. It is observable that the test results for different images all float around the theoretical values, indicating that this algorithm can effectively resist differential attacks.
The proposed encryption method is evaluated against other schemes utilizing the Moon Surface image. The results, shown in Table 8, highlight the competitive advantages of the proposed approach.
Conclusions
This paper introduces NJC oscillators with symmetrical attractors, employing traditional methods to analyze their dynamics. The system exhibits chaotic behavior and various attractor types, validated through simulations and numerical solving. Additionally, a multilayer FFNN models the system, and an image encryption algorithm integrating the NJC system is proposed, showing effectiveness against attacks. This work contributes to understanding chaotic systems, utilizing neural networks, and developing secure encryption techniques.
The current study on the NJC system demonstrates good potential, particularly in image encryption and chaotic PRNG development, but it faces several limitations and offers opportunities for future research. One limitation is the computational complexity associated with the ANN-based model on FPGA, which may impact performance and resource utilization. Additionally, the study primarily focuses on a single application—image encryption—leaving other potential applications like secure communication or financial modeling underexplored. Future studies could address these limitations by optimizing FPGA implementations, expanding the scope to real-time systems and diverse cryptographic techniques, and investigating more complex neural network architectures like RNNs to enhance prediction accuracy in chaotic systems.
Data availability
The data that support the findings of this study are available from the corresponding author on reasonable request.
References
Al-Obeidi, A. S. & Al-Azzawi, S. F. Hybrid synchronization of high-dimensional chaos with self-excited attractors. J. Interdiscip. Math. 23(8), 1569–1584 (2020).
AL-Azzawi, S. F. & Al-Obeidi, A. S. Chaos synchronization in a new 6D hyperchaotic system with self-excited attractors and seventeen terms. Asian-Eur. J. Math. 14(05), 2150085 (2021).
Lai, Q., Yang, L. & Chen, G. Design and performance analysis of discrete memristive hyperchaotic systems with stuffed cube attractors and ultraboosting behaviors. IEEE Trans. Ind. Electron. 71(7), 7819–7828 (2023).
Chu, R., Zhang, S. & Mou, J. A multi-image compression and encryption scheme based on fractional chaotic map. Phys. Scr. 98(7), 075213 (2023).
Lai, Q., Yang, L. & Chen, G. Two-dimensional discrete memristive oscillatory hyperchaotic maps with diverse dynamics. IEEE Trans. Ind. Electron. 1, 1 (2024).
Rybin, V. et al. Prototyping the symmetry-based chaotic communication system using microcontroller unit. Appl. Sci. 13(2), 936 (2023).
Yang, M., Ren, X. & Cho, J. H. Nonlinear controller supported by artificial intelligence of the rheological damper system reducing vibrations of a marine engine. J. Low Freq. Noise Vib. Act. Control 42(4), 1919–1936 (2023).
Negou, A. N. & Tchiotsop, D. Periodicity, chaos and multiple coexisting attractors in a generalized moore–spiegel system. Chaos Solitons Fractals 107, 275–289 (2018).
Balaraman, S., Kengne, J., Fogue, M. K. & Rajagopal, K. From coexisting attractors to multi-spiral chaos in a ring of three coupled excitation-free duffing oscillators. Chaos Solitons Fractals 172, 113619 (2023).
Li, C., Li, Z., Jiang, Y., Lei, T. & Wang, X. Symmetric strange attractors: a review of symmetry and conditional symmetry. Symmetry 15(8), 1564 (2023).
Ahmadi, A. et al. Extreme multistability and extreme events in a novel chaotic circuit with hidden attractors. Int. J. Bifurcat. Chaos 33(07), 2330016 (2023).
Kuznetsova, O. I. Application of megastable system with 2-D strip of hidden chaotic attractors to secure communications. Chebyshevskii Sbornik 24(1), 89–103 (2023).
Liang, B., Hu, C., Tian, Z., Wang, Q. & Jian, C. A 3D chaotic system with multi-transient behavior and its application in image encryption. Phys. A Stat. Mech. Appl. 616, 128624 (2023).
Garcia, F., Ogbonna, J., Giesecke, A. & Stefani, F. High dimensional tori and chaotic and intermittent transients in magnetohydrodynamic couette flows. Commun. Nonlinear Sci. Numer. Simul. 118, 107030 (2023).
Zhou, T., Peng, Y. & Guo, T. Partial least squares-based polynomial chaos kriging for high-dimensional reliability analysis. Reliab. Eng. Syst. Saf. 240, 109545 (2023).
Weng, T. et al. Synchronization of machine learning oscillators in complex networks. Inf. Sci. 630, 74–81 (2023).
Omidvar, A. E. Configuring radial basis function network using fractal scaling process with application to chaotic time series prediction. Chaos Solitons Fractals 22(4), 757–766 (2004).
Han, M., Xi, J., Xu, S. & Yin, F. L. Prediction of chaotic time series based on the recurrent predictor neural network. IEEE Trans. Signal Process. 52(12), 3409–3416 (2004).
Chang, B. R. & Tsai, H. F. Forecast approach using neural network adaptation to support vector regression grey model and generalized auto-regressive conditional heteroscedasticity. Expert Syst. Appl. 34(2), 925–934 (2008).
Chatzinakos, C. & Tsouros, C. Estimation of the dimension of chaotic dynamical systems using neural networks and robust location estimate. Simul. Model. Pract. Theory 51, 149–156 (2015).
Wichard, J. D. Forecasting the NN5 time series with hybrid models. Int. J. Forecast. 27(3), 700–707 (2011).
He, Y., Xu, Q., Wan, J. & Yang, S. Electrical load forecasting based on self-adaptive chaotic neural network using Chebyshev map. Neural Comput. Appl. 29, 603–612 (2018).
Luo, Y., Ouyang, X., Liu, J. & Cao, L. An image encryption method based on elliptic curve elgamal encryption and chaotic systems. IEEE Access 7, 38507–38522 (2019).
Wang, X. et al. A color image encryption algorithm based on hash table, Hilbert curve and hyper-chaotic synchronization. Mathematics 11(3), 567 (2023).
Murali, P. & Sankaradass, V. An efficient space filling curve-based image encryption. Multimedia Tools Appl. 78, 2135–2156 (2019).
Shahna, K. U. & Mohamed, A. A novel image encryption scheme using both pixel level and bit level permutation with chaotic map. Appl. Soft Comput. 90, 106162 (2020).
Moysis, L. et al. Chaotification of 1D maps by multiple remainder operator additions—application to B-spline curve encryption. Symmetry 15(3), 726 (2023).
Lai, Q. & Hu, G. A nonuniform pixel split encryption scheme integrated with compressive sensing and its application in IoMT. IEEE Trans. Ind. Inf. 20(9), 11262–11272 (2024).
Lai, Q., Wan, Z., Zhang, H. & Chen, G. Design and analysis of multiscroll memristive hopfield neural network with adjustable memductance and application to image encryption. IEEE Trans. Neural Netw. Learn. Syst. 34(10), 7824–7837 (2022).
Chen, H. et al. A multistable chaotic jerk system with coexisting and hidden attractors: dynamical and complexity analysis, FPGA-based realization, and chaos stabilization using a robust controller. Symmetry 12(4), 569 (2020).
Folifack Signing, V. R., Fonzin, F., Kountchou, T., Kengne, M., Njitacke, Z. T. & J., & Chaotic jerk system with hump structure for text and image encryption using DNA coding. Circuits Syst. Signal. Process. 40, 4370–4406 (2021).
Vivekanandhan, G. et al. A new chaotic jerk system with hidden heart-shaped attractor: dynamical analysis, multistability, connecting curves and its application in image encryption. Phys. Scr. 98(11), 115207 (2023).
Sambas, A. et al. A new hyperjerk system with a half line equilibrium: multistability, period doubling reversals, antimonotonocity, electronic circuit, FPGA design and an application to image encryption. IEEE Access 12, 9177–9194 (2024).
Benkouider, K. et al. A new 5-D multistable hyperchaotic system with three positive Lyapunov exponents: bifurcation analysis, circuit design, FPGA realization and image encryption. IEEE Access 10, 90111–90132 (2022).
Benkouider, K. et al. S., A new 10-D hyperchaotic system with coexisting attractors and high fractal dimension: its dynamical analysis, synchronization and circuit design. PLoS ONE 17(4), e0266053 (2022).
Alçın, M., Pehlivan, İ. & Koyuncu, İ. Hardware design and implementation of a novel ANN-based chaotic generator in FPGA. Optik 127(13), 5500–5505 (2016).
Alcin, M., Koyuncu, I., Tuna, M., Varan, M. & Pehlivan, I. A novel high speed artificial neural network–based chaotic true random number generator on field programmable gate array. Int. J. Circuit Theory Appl. 47(3), 365–378 (2019).
Koyuncu, I. et al. Control, synchronization with linear quadratic regulator method and FFANN-based PRNG application on FPGA of a novel chaotic system. Eur. Phys. J. Spl. Top. 230(7), 1915–1931 (2021).
Kong, X. et al. Memristor-induced hyperchaos, multiscroll and extreme multistability in fractional-order HNN: image encryption and FPGA implementation. Neural Netw. 17, 85–103 (2024).
Yu, F. et al. Dynamics analysis, synchronization and FPGA implementation of multiscroll Hopfield neural networks with non-polynomial memristor. Chaos Solitons Fractals 179, 114440 (2024).
Tuna, M., Karthikeyan, A., Rajagopal, K., Alcin, M. & Koyuncu, İ. Hyperjerk multiscroll oscillators with megastability: analysis, FPGA implementation and a novel ANN-ring-based true random number generator. AEU Int. J. Electron. Commun. 112, 152941 (2019).
Naik, R. B. & Singh, U. A review on applications of chaotic maps in pseudo-random number generators and encryption. Ann. Data Sci. 11(1), 25–50 (2024).
Xu, W. et al. A simple 4D no-equilibrium chaotic system with only one quadratic term and its application in pseudo-random number generator. Chaos Solitons Fractals 182, 114752 (2024).
Zhang, R., Zhou, R. & Luo, J. Nonequal-length image encryption based on bitplane chaotic mapping. Sci. Rep. 14(1), 9075 (2024).
Zhao, H., Wang, S. & Fu, Z. A new image encryption algorithm based on cubic fractal matrix and L-LCCML system. Chaos Solitons Fractals 185, 115076 (2024).
Wu, W. & Kong, L. Image encryption algorithm based on a new 2D polynomial chaotic map and dynamic S-box. Signal. Image Video Process. 18(4), 3213–3228 (2024).
Zou, C., Wang, X. & Li, H. Image encryption algorithm with matrix semi-tensor product. Nonlinear Dyn. 105(1), 859–876 (2021).
Teng, L., Wang, X. & Xian, Y. Image encryption algorithm based on a 2D-CLSS hyperchaotic map using simultaneous permutation and diffusion. Inf. Sci. 605, 71–85 (2022).
Author information
Authors and Affiliations
Contributions
Conceptualization, A.S., S.V and X.Z; methodology, I.A.R.M., M.D.J and M.A.M; software, K.B., M.A., I.K and M.T; formal analysis, X.Z., M. A., and I.A.R.M.; investigation, I.K.A, M.A.M. and I. M. S; Funding, I.A.R.M ; writing—original draft preparation, A.S, K.B, X.Z. M.T and S.V; writing—review and editing, M.A, I.K, M.D.J and I.M.S.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Sambas, A., Zhang, X., Moghrabi, I.A.R. et al. ANN-based chaotic PRNG in the novel jerk chaotic system and its application for the image encryption via 2-D Hilbert curve. Sci Rep 14, 29602 (2024). https://doi.org/10.1038/s41598-024-80969-z
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-024-80969-z
Keywords
This article is cited by
-
Image cryptosystem based on hyper-chaos and optimized typhoon wind field model
Journal of King Saud University Computer and Information Sciences (2026)
-
A hybrid cryptosystem for medical image security: integrating finite fields with conservative hyperchaos
Nonlinear Dynamics (2026)
-
Image encryption and electronic circuit design using a novel five-term 3D chaotic jerk system
Indian Journal of Physics (2025)
-
Design of New Chaotic System with Hyperbolic Sine Function based on Pseudo-Random Number Generation for Medical Image Encryption
Journal of Nonlinear Mathematical Physics (2025)