Abstract
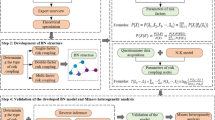
In coal mine production activities, unsafe behaviours of workers are one of the important factors leading to frequent accidents, with the complexity of risk transmission mechanisms posing significant challenges to safety management. To systematically reveal the risk transmission rule of unsafe behavior risks, this study proposes a multidimensional research methodology: First, based on 574 coal mine accident investigation reports from 2019 to 2024, text mining techniques were employed to extract 26 key influencing factors, establishing an indicator system encompassing five dimensions: environment, individual, group, organizational management, and leadership. Second, an integrated DEMATEL-ISM method was adopted to construct a hierarchical structure model of influencing factors, identifying work experience and psychological status as fundamental causal nodes. And then, Arena simulations revealed risk transmission rule: When the mean risk emergence rate increased from 0.5 to 2, the system’s residual risk entropy nearly diminished to zero. Enhanced node immunity (up to node 5) significantly reduced both system risk entropy and residual risk entropy. However, continued improvement of node 11’s immunity showed diminishing marginal effects, indicating that appropriately enhancing node 11’s immunity effectively reduces accident probabilities. Finally, targeted control strategies were proposed across five dimensions: safety management, individual factors, group dynamics, safety leadership, and physical environment. The results of this study can provide important theoretical support and practical guidance for coal mine safety production, help to reduce the accident rate, ensure the life safety of coal mine workers and the sustainable development of enterprises.
Similar content being viewed by others
Introduction
According to the 2023 National Economic and Social Development Statistics Bulletin issued by the National Bureau of Statistics of China, in 2023, 21,242 people died in various types of production safety accidents, a decrease of 4.7 per cent from the previous year. Among them st, the coal mine fatality rate per million tons reached 0.094 fatalities, marking a 23.7% increase. This figure sharply contrasts with the target of “a 10% reduction in the coal mine fatality rate per million tons1” proposed in the 14th Five-Year National Work Safety Plan, highlighting the severe challenges facing coal mine safety management. Despite the positive progress in mine safety production nationwide in 2023, mine safety production is still in a period of climbing over the hurdles. Heinrich2 believes 88% of accidents can be attributed to unsafe human behaviour, more than 95% of accidents in China’s coal mining industry are caused by recognised unsafe behaviours in coal mines3. In view of the fact that the unsafe behaviours of coal mine workers occupies a very high proportion in the occurrence of accidents, it is of great significance to analyze the influencing factors of the unsafe behaviours of coal mine workers and the internal mechanism of the occurrence of unsafe behaviours, and explore ways to reduce the unsafe behaviours of coal mine workers for effective prevention and control of accidents.
Current study primarily focuses on three dimensions: First, Individual Psychological Level. Scholars have conducted meticulous observations and descriptions of coal miners’ unsafe behaviors from diverse perspectives. Chen et al.4 revealed through questionnaire surveys and structural equation modeling that informal groups may amplify or mitigate the likelihood of direct unsafe behaviors. Liu et al.5 employed confirmatory factor analysis on frontline coal miners, demonstrating that disparities in risk perception significantly correlate with unsafe behavioral outcomes. Second, Organizational Management Level. Studies aim to elucidate how organizational management elements directly or indirectly shape safety behaviors. Liu et al.6 identified critical factors affecting miners’ safety psychology, highlighting that excessive workloads, inadequate compensation systems, and poor welfare policies exacerbate psychological stress, fostering grievance-driven unsafe production behaviors. Cao et al.7 applied a fuzzy DEMATEL method to analyze interactions among safety management behaviors and dimensions, proposing evidence-based strategies for optimizing managerial decision-making.Third, Risk Prediction Level. Chen et al.8 utilized a grey Markov model to predict coal mine fatality rates per million tons, emphasizing the necessity to enhance regulatory oversight and refine safety management systems. Li et al.9 integrated agent-based modeling and system dynamics to simulate unsafe behavioral evolution, developing targeted intervention strategies and establishing a foundational framework for behavioral control.
However, existing study still exhibits critical limitations: The multifaceted and complex nature of unsafe behaviors remains underexplored, particularly regarding comprehensive and systematic analyses of interactions between internal and external influencing factors. Prevailing static analytical approaches inadequately capture the dynamic coupling mechanisms among these factors. To address these research gaps, this study proposes three innovations: First, a 26-factor indicator system was developed through text mining of 574 accident reports. Second, a five-tier hierarchical structure model was established using the DEMATEL-ISM structured method, achieving organic integration of static analysis and dynamic simulation. Third, an Arena-based risk entropy dynamics model was implemented to quantify risk transmission efficiency at two essential nodes – work experience and psychological status. This study aims to: Establish a comprehensive indicator system for coal mine unsafe behavior influencing factors; Investigate risk transmission rule through simulation technologies; Ultimately enhance the effectiveness of coal mine safety management.
Methods
Establishment of the index system for influencing factors of coal mine workers’ unsafe behaviour
Text mining techniques
Text mining is a knowledge discovery technology that integrates multiple disciplines such as natural linguistics, statistics and machine learning10. It extracts key information with research value and uses value from a large amount of text data according to the established rules, with the help of text classification, keyword tracking, visualisation, etc., so as to achieve the purpose of discovering the rules of things11. It can achieve the purpose of discovering the law of things.
The analysis process of text mining generally consists of building a corpus, developing a thesaurus, text segmentation and result analysis, as shown in Fig. 1.
Mining the influencing factors of coal mine workers’ unsafe behaviour
Building the corpus
Accident investigation reports are accident information that records the cause of the accident, the course of the accident, the assignment of responsibility, etc. They are usually issued under the leadership of the governmental safety supervision department, and are therefore authoritative and objective12.
This study uses crawler technology to analyse incomplete statistics of 574 coal mine accident investigation reports that occurred in China during the period 2019–2024. The data analysed in this study comes from the content published by the State Administration of Mine Safety Supervision and the China Coal Mine Safety Production Network.
Development of a thesaurus
The research objective of this study is to mine and analyse the influencing factors of unsafe behaviours in the accident investigation report, and the thesaurus of the mining software itself does not contain professional words related to the coal mining industry, For instance, the phrase “deliberate concealment of operational zones” may be erroneously segmented by text processing algorithms into discrete units such as “deliberate”, “concealment”, “operation”, and “zone” (, thereby distorting the semantic integrity of the original expression, so it is necessary to import the professional thesaurus of the coal mining industry in advance to achieve better word separation effect. This study selected specialized word lexicon from the official website of Sogou Input Method, including domains such as mining engineering, mine emergency rescue, safety hazard information analysis, coal energy, coal mine disaster prevention, safety engineering, and workplace safety terminology. However, these lexicons demonstrate incomplete coverage of domain-specific vocabulary, necessitating further refinement.
In addition, there are a lot of words in the accident reports that appear more frequently but have no value to the research objectives, and these words need to be deactivated, so it is necessary to import the deactivated word list before the text mining, so that these worthless words can be eliminated during the mining. In addition, different accident investigation reports will have different expressions for the same semantic statement, which need to be statistically aggregated into unified phrases or short sentences to establish a group of subsumed word lists, so that they can be counted during text mining. Therefore, in order to achieve the expected mining lexical effect before the lexical processing, it is necessary to establish a specialised word lexicon, a deactivated word lexicon (Table 1) and a group of subsumed word lists (Table 2).
Segmentation processing
The above corpus database is imported into the mining software, and the original corpus data is decomposed into several words through the word separation procedure, which facilitates the extraction of key feature words, such as the factors influencing the unsafe behaviours of coal mine workers. The original feature words are obtained by pre-processing the original text data with word splitting.
The original feature word set is huge, in which a large number of words appear with high frequency but are useless for the study of coal mine workers’ unsafe behaviours and influencing factors, such as “coal mine”, “group”, “company”, etc. These words can be deleted by deactivating the thesaurus. “These words can be deleted by deactivating the thesaurus. Some seemingly useless but valuable words cannot be deleted, such as “safety”, “rules and regulations”, “attitude”, and so on. The list of subsumed words and the deactivated thesaurus may be modified and updated several times during the mining process in order to get the best mining results.
Analysis of results
Based on the final mining results, the frequency of occurrence of the influencing factors of unsafe behaviours appearing in the corpus of accident investigation reports is derived; the higher the frequency of occurrence, the greater the degree of influence of the factor on the unsafe behaviours in the accident reports. The frequency of occurrence of each influencing factor is shown in Fig. 2.
Establishment of an index system of factors influencing the unsafe behaviour of coal mine workers
Identification of factors influencing unsafe behaviour of coal mine workers
Through in-depth excavation of the root causes of coal mine employees’ unsafe behavioural accidents, the main causal factors inducing accidents are screened, and the deeper causes of accidents are further identified as the basis for the evaluation of coal mine employees’ safe behaviour13. According to the word frequencies of the influencing factors of unsafe behaviours derived from text mining, as shown in Table 3, the influencing factors of unsafe behaviours of coal mine employees are determined.
Establishment of an indicator system for unsafe behaviour of coal mine workers
The main causal factors of 574 coal mine accidents were extracted and summarised into five dimensions, namely: environmental factors, individual factors, group factors, organisational management factors, and leadership factors, and an indicator system for coal mine workers’ unsafe behaviours was established, as shown in Fig. 3.
Behavioural risk emerges from the delivery of formal descriptions
Description of behavioural risk emergence
In coal mine workers’ unsafe behaviour accidents, their influencing factors are a dynamic state of change, and changes in the factors lead to changes in the overall structure, and when this change exceeds the threshold of the accident’s influencing factor, it can be considered that the risk state of that influencing factor is triggered14.
In a behavioural safety management system, the occurrence of employee unsafe behaviours is seen as an undesirable systemic emergence. This undesirable system emergence is closely related to the work environment, leadership, organisation and other factors in which the employee works. Behavioural risk emergence means that the interaction of the influencing factors of an unsafe behavioural incident leads to the evolution of the state of a causal node factor, thus triggering its risk state, which is considered to be the state of behavioural risk emergence.
Considering the mathematical definition, the risk emergence15 definition can be understood as, let the state input of the causal node of a behavioural accident be\(\:{x}_{i}(i=\text{1,2},\dots\:,m)\) and the output quantity is\(\:{y}_{j}(j=\text{1,2},\dots\:,n)\), when\(\:\forall\:1\le\:j\le\:n\:{y}_{j}=0\) when, it indicates that the node risk state is not triggered, that is, the safe state; when\(\:\exists\:{y}_{j}=1, 1\le\:j\le\:n\:{y}_{j}=1\) when, it indicates that the node risk state is triggered, the node occurs risk emergence. Expressed in terms of risk entropy, define the node\(\:i\) The risk entropy of a node is\(\:{h}_{i}\left(\lambda\:\right)\), therefore, when\(\:{h}_{i}<{h}_{i}\left(\lambda\:\right)\) when, the node\(\:i\) is in a safe state; when\(\:{h}_{i}>{h}_{i}\left(\lambda\:\right)\) time, the node experiences risk emergence; when\(\:{h}_{i}={h}_{i}\left(\lambda\:\right)\) when, the node is in a critical state16.
Formal description of behavioural risk transfer
Each unsafe behaviour risk influencing factor is assigned a value, corresponding to the risk entropy of the factor itself, when the risk entropy of the factor itself exceeds the threshold, it is considered that the risk emergence occurs in the causative node of the factor, and the risk state is triggered, and the residual risk entropy exceeding the node itself will be transferred to the causative node adjacent to it until the risk residue is zero, and the accident does not occur, and if the risk of the unsafe behaviour has not been handled, the threshold will be breached and a safety accident will be triggered. This kind of risk entropy propagation becomes the kinetic propagation of risk entropy17.This kind of risk entropy propagation becomes the kinetic propagation of risk entropy. The mathematical propagation model of risk entropy of coal mine workers’ unsafe behaviours can be described as follows:
-
(1)
Let a consistent cause node\(\:i\) be the initial node of an insecurity incident. Risk emergence occurs at this node and exceeds the threshold value, the initial node occurs risk emergence and propagates risk entropy to the neighbouring nodes. The propagated risk entropy consists of the following parts as follows: ① \(\:{s}_{i}\left(t\right),\) the risk entropy that enters the node \(\:i\) at the moment \(\:t\); ② \(\:{k}_{i}^{d}\left(t\right)\), the risk entropy of the moment \(\:t\) entering the node \(\:i\); ③ \(\:{\delta\:}_{ij}\) is the risk propagation probability, which is related to the degree of association between the two causal nodes; ④ \(\:{s}_{j}\left(t\right)\) is the risk propagation probability \(\:t\) is the risk entropy propagated from other nodes to the node \(\:j\);⑤\(\:{\epsilon\:}_{j}\left(t\right)\) is the risk entropy transmitted by the node \(\:j\) to other nodes; ⑥ \(\:{k}_{j}^{d}\left(t\right)\) is the risk entropy that the node \(\:j\) can dispose of by itself.
Combining the above six parts, Eq. (1) indicates that the risk to the node \(\:j\) .It stops and the residual risk entropy is zero; Eq. (2) indicates that: after the node\(\:j\) the risk entropy is not disposed off by the node, the risk residual is greater than zero, and the risk entropy will continue to pass.
$$\:\left\{\left[{s}_{i}\left(t\right)-{k}_{i}^{d}\left.\left(t\right)\right]\times\:{\delta\:}_{ij}+{s}_{j}^{i}\left(t\right)+\left.{\epsilon\:}_{j}\left(t\right)\right\}\right.\right.\le\:{k}_{j}^{d}\left(t\right)$$(1)$$\:\left\{\left[{s}_{i}\left(t\right)-{k}_{i}^{d}\left.\left(t\right)\right]\times\:{\delta\:}_{ij}+{s}_{j}^{i}\left(t\right)+\left.{\epsilon\:}_{j}\left(t\right)\right\}\right.\right.\ge\:{k}_{j}^{d}\left(t\right)$$(2) -
(2)
After the subsequent nodes associated with the initial node are triggered, the nodes passing through \(\:j\) ,the residual risk entropy will continue to propagate to the neighbouring nodes. Therefore, this part of the risk entropy is formed when a participant risk entropy is accumulated, and then continue to propagate the process, when the risk entropy can be disposed of by the next node or is smaller than the threshold of the next node, the node will not occur risk emergence, and the risk will not continue to be passed on, which can be expressed by the following Eq. (3); but the accumulated participant risk entropy will continue to exceed the node’s threshold and will generate new residual risk entropy, which can be superimposed on the previous risk entropy, which can be expressed by the following Eq. (4). risk entropy superimposed, which can be represented by Eq. (4):
$$\left\{\sum_{i=1}^{Q}\left[{s}_{i}\left(t\right)-\right.\left.{k}_{t}^{d}\right]\times\:{\delta}_{ij}+\right.\left.\sum_{i=1}^{Q}{s}_{j}^{i}\left(t\right)+{\epsilon}_{j}\left(t\right)\right\}\le\:{k}_{j}^{d}\left(t\right)$$(3)$$\left\{\sum_{i=1}^{Q}\left[{s}_{i}\left(t\right)-\right.\left.{k}_{t}^{d}\right]\times\:{\delta}_{ij}+\right.\left.\sum:_{i=1}^{Q}{s}_{j}^{i}\left(t\right)+{\epsilon}_{j}\left(t\right)\right\}\ge\:{k}_{j}^{d}\left(t\right)$$(4)Eq:\(\:Q\) denotes the number of nodes where risk emergence has occurred.
-
(3)
As the number of nodes where risk emergence occurs continues to increase, an unsafe behaviour accident will be triggered when all triggered nodes reach or exceed the worker’s unsafe behaviour tolerance. By describing the mathematical model of unsafe act risk propagation, the transfer process of risk entropy among the influencing factors of unsafe acts can be clearly understood, which helps to analyse the mechanism of unsafe act risk transfer and can even be used to excavate some potential accident nodes18.
Behavioural risk transfer simulation process
The unsafe behaviour of coal mine workers itself is an extremely complex system as a whole, and its complexity and high risk cannot be confirmed by experimental methods, so it is not feasible to test it in the form of accidents. With the rise of simulation technology, combining it with the unsafe behaviours of coal mine workers and simulating the risk transfer of unsafe behaviours of coal mine workers can solve the above problem which can not be verified by experiments. Through the simulation of risk transfer of unsafe behaviours, the mechanism of risk transfer can be clearly understood, and a series of problems such as the risk disposal ability of the accident-causing node can be clarified19.
Unsafe behaviours are composed of several factors, including environment, people (individual and group), organisational management, and leadership, which involves the integration of multiple disciplines, and therefore the laws of unsafe behaviours risk transfer are extremely complex. However, numerical simulation of the risk transfer of unsafe behaviours can be used to understand the behavioural characteristics of risk dynamics of unsafe behaviours under the conditions of specific factors20. The specific simulation process is shown in Fig. 4.
As can be seen from the figure, the occurrence of behavioural accidents will clarify the goal of the simulation. In this study, Arena software will be used to simulate the process of unsafe behaviour risk transfer. By collecting data, Arena confirms the simulation goal, establishes the model, and finds out the key factors affecting the unsafe behaviour risk transfer through parameter changes, so as to establish the control countermeasures for the unsafe behaviour risk transfer according to the simulation results.
Behavioural risk coupling
Risk coupling concept21 from a macro perspective it can be understood as the interactive fusion of risk disciplines, risk prevention techniques, and even risk monitoring systems to form a new risk control mechanism; from a micro perspective it can be the cross-fertilisation of human behaviours, management status, organisational structures, equipment applications, and environments to produce cross-factorial accident risks. In this study risk coupling refers to the process of transferring the risk of unsafe behaviours by fusing together the node factors where the risk emergence occurs, which in turn creates a larger unsafe risk or a new risk. When a common risk emergence occurs in one or more key causal nodes, the coupled association between risk factors will form a new unsafe behavioural risk state, and when the value of this state reaches the behavioural risk tolerance level of coal mine workers, it will cause behavioural changes, which will lead to unsafe behavioural accidents22. The following is an example of the risk state of unsafe behaviours, as shown in Fig. 5.
Unsafe behaviour accidents of coal mine workers are causative nodes appear state deviation occurs risk emergence, in the process of risk transfer occurs risk coupling, ultimately leading to the behaviour into unsafe behaviour, when the risk is further coupled with the environment, organisational management and other more risks, it will be triggered by the unsafe behaviour of unsafe behaviour accidents23.
Mathematical model analysis of the risk coupling of unsafe behaviours, unsafe behaviours are regarded as a kind of system, and unsafe behaviour accidents are set to be composed of \(\:m\) subsystem factors, and each subsystem contains \(\:n\) nodes, so each subsystem is a \(\:n\) dimensional dynamical system, there is a coupling interaction between all nodes. Nodes \(\:i(1\le\:i\le\:m)\) at the moment \(\:t\) of \(\:n\) dimensional state variable is \(\:{x}_{i}\left(t\right), {x}_{i}\left(t\right)=\left({x}_{i1}t\right), {x}_{i2}\left(t\right),...,{x}_{in}\left(t\right){)}^{T}\in\:{R}^{n}\)
Let \(\:H:{R}^{n}\to\:{R}^{n}\) be the risk transfer function between the subsystems, then the coupling effect, the node\(\:i\) dynamics equations can be expressed by Eq. (5):
Where: the constant \(\:\sigma\:>0\) is the coupling strength of the network;\(\:{G}_{ij}\) is the out-coupling matrix \(\:G\) of the matrix elements.
At the moment \(\:{t}_{1}\), the causal node \(\:i\) risk emergence occurs, and due to the coupling effect, the node associated with \(\:b(b<m)\) nodes also undergoes risk emergence, and the newly deviated \(\:b\) nodes as the coupling action continues at the moment \(\:\:{t}_{2}\), there is:
Accident emergence is the progression of node risk emergence that results in the coupling of unsafe behavioural risk factors, ultimately resulting in an unsafe behavioural accident. The risk emergence of causal nodes is the key point of unsafe behavioural accidents, and when a sufficient number of nodes within the behavioural whole undergo risk emergence, it has already paved the way for the occurrence of accidents. How to achieve the control of unsafe behaviour accidents by avoiding the synchronisation of risk coupling between nodes becomes a focus of this study24.
Analysis of key factors of unsafe behaviour of coal mine workers
Analysis of key factors of unsafe behaviour of coal mine workers based on DEMATEL-ISM method
Decision making trial and evaluation laboratory (DEMATEL) is a method to analyze system factors using the principles of graph theory and matrix theory25. Interpretive structural modeling (ISM) is a qualitative analysis based method that can analyze whether the factor selection of a system is reasonable. Its role is to decompose the complex system into several subsystems, and finally form a multi-level hierarchical interpretive structural model26.
The causes of unsafe accidents are complex and there are many contributing factors. Structured processing of influencing factors of unsafe behaviours is the basis and premise for the analysis of unsafe behaviour accidents. Integrated DEMATEL-ISM structured method can be used to analyze the causal relationship among influencing factors of unsafe behaviours. The advantage of applying integrated DEMATEl-ISM structural method to the analysis of unsafe behaviour factors of coal mine workers is that, on the basis of DEMATEL method, ISM method can further divide the hierarchical structure among unsafe behaviour factors.
Only the DEMATEL method can find out the key factors of unsafe behavior and achieve key control over the factors with a high degree of centrality, but it cannot determine the complex correlation between various factors and lacks consideration of the influencing factors themselves. Therefore, it is necessary to combine the ISM method to divide the hierarchical structure. On the basis of the comprehensive influence matrix in method, the overall influence matrix is constructed by considering the influence of factors themselves and adding the identity matrix. The overall influence matrix is standardized and reachable through the given threshold, that is, the reachable matrix is obtained. If the element in the matrix is 1, there is an influence relationship between the factors, otherwise there is no mutual influence relationship27.
Integrated DEMATEL-ISM method on the one hand, the comprehensive influence matrix in DEMATEL method includes both the direct influence relationship between the factors influencing unsafe behavior and the indirect influence relationship of the factors themselves. On the other hand, the comprehensive influence matrix covers more information than the reachable matrix in ISM method. At the same time, it avoids the massive and complex matrix calculation in ISM method. Based on the comprehensive impact matrix of DEMATEL method, the reachability matrix of ISM method is constructed by considering the influence of factors on themselves, and the correlation relationship and logical structure among factors influencing unsafe behaviors can be further analyzed, so as to realize the structure and hierarchy of influencing factors of unsafe behaviors28. Therefore, DEMATEL method and ISM method complement each other effectively, and it is a new method to construct the hierarchy of influencing factors of unsafe behavior.
Based on DEMATEL-ISM method to analyse the interactions of factors influencing the unsafe behaviours of coal mine workers, it can be divided into the following steps.
-
(1)
Determination of systemic influences.
Let be a1, a2, a3,…,a, ani ∈ A(i = 1,2,…,n), where n bits are the number of system influences and A is the set of influences.
-
(2)
Establishment of a direct impact matrix.
A pairwise correlation analysis of influencing factors was conducted through expert scoring to obtain the direct influence matrix B. For each pair among the 26 factors (a1–a26), domain experts evaluated their mutual influences using five intensity levels: very strong (4), strong (3), moderate (2), weak (1), and none (0). Multiple expert evaluations were aggregated using an averaging method to mitigate individual knowledge bias, yielding the initial direct influence matrix as defined in Eq. (7). Subsequently, the matrix was normalized via Eq. (8) to derive the standardized direct influence matrix C.
$$B=\left[\begin{array}{cc}\begin{array}{cc}0& {\beta }_{12}\\ {\beta }_{21}& 0\end{array}& \begin{array}{cc}\cdots & {\beta }_{1n}\\ \cdots & {\beta }_{2n}\end{array}\\ \begin{array}{cc}\cdots & \cdots \\ {\beta}_{n1}& {\beta}_{n2}\end{array}& \begin{array}{cc}\cdots & \cdots \\ \cdots & 0\end{array}\end{array}\right]$$(7)$$C=\frac{1}{{\mathop {{\text{max}}}\limits_{{1 \leqslant i \leqslant n}} \sum\limits_{{j=1}}^{n} {\mathop \beta \nolimits_{{ij}} } }}B$$(8) -
(3)
Calculation of the integrated impact matrix.
The normalised direct impact matrix C is transformed into a composite impact matrix T according to Eq. (9).
$$T=C+{C^2}+\cdots+{C^n}=\sum\limits_{{i=1}}^{n} {{C^i}} .$$(9) -
(4)
Calculation of the degree of influence, the influenced matrix, the degree of cause and the degree of centrality.
Based on the composite influence matrix T, the respective influence, influenced, centrality and cause degrees were calculated for each of the 26 factors, as shown in Eqs. (10, 11, 12, 13), resulting in a centrality ranking of all factors and their respective corresponding factor attributes.
$${f_i}=\sum\limits_{{i=1}}^{n} {{t_{ij}}\left( {i=1,2,...,n} \right)}$$(10)$${e_i}=\sum\limits_{{j=1}}^{n} {{t_{ji}}\left( {i=1,2,...,n} \right)}$$(11)$${N_i}={f_i} - {e_i}\left( {i=1,2,...,n} \right)$$(12)$${M_i}={f_i}+{e_i}\left( {i=1,2,...,n} \right)$$(13) -
(5)
Calculation of overall impact matrix and reachability matrix.
The combined impact matrix is simply processed and the unit matrix is added to obtain the overall impact matrix.
From the overall influence matrix, it can be seen that all the factors affecting unsafe behaviours have a relationship with each other, and the greater the degree of mutual influence, the greater the value in the matrix, on the contrary, the smaller the value indicates that the degree of mutual influence between the factors will be smaller, and if it is equal to zero, then it is considered that there is no correlation between the two factors, and they cannot influence each other.
Calculate the standardised reachability matrix, by giving the threshold value λ (0.25, 0.3, 0.33, 0.35), take different values of λ, the number of nodes obtained is also different, nodes means that the number of nodes should be moderate when carrying out the value of λ, too much or too little is not allowed, at the same time, the factors with a larger number of nodes should be relatively coincident with the front of centrality as determined in the DEMATEL method29. Table 4 presents the distribution of nodes under different threshold, after comparison, λ = 0.33 is taken, which is in line with several key factors of the top centrality ranking identified by DEMATEL. The elements of the overall influence matrix were processed to obtain the reachability matrix K.
-
(6)
Plotting the hierarchical structure of factor progression.
On the basis of the reachability matrix K, it is judged whether the division of the elements of each level is established according to formula (14).
$$\mathop R\nolimits_{i} =\mathop R\nolimits_{i} \cap \mathop S\nolimits_{i} (i=1,2, \ldots ,n)$$(14)If Eq. (14) holds, it means that the element ai is the first layer element, and then the ith row and column of the reachable matrix K are removed; if the equation does not hold, the remaining matrix needs to be revalidated to find out the corresponding factors of the second layer or other layers. Repeat this procedure until all factors have been removed. Based on the order in which the factors are removed, the multilevel recursive order structure model is plotted as in Fig. 6.
Accident system model of unsafe behaviour of coal mine workers
The existence of the risk of unsafe behaviour is not only the cause of accidents, but also an inherent property of the safety system itself. Through reviewing the literature, it can be seen that the factors affecting accidents caused by unsafe behaviours are distributed in a net-like interactive structure, and there is a close connection between the different layers, so that any change in the state of any layer will cause a change in the state of the overall structure, and a new risk will exist at this stage. When the changing accident-causing nodes exceed their due thresholds, risk transfer occurs, which leads to accidents.
Re-arranged reachability matrices and complex network theory under λ = 0.33 determined based on the DEMATEL-ISM method ADDIN, the factor corresponding to column 1 in the row where the factor is located is regarded as the outgoing node direction of the factor, and the factor corresponding to behaviour 1 in the column where the factor is located is regarded as the incoming node direction of the factor, and the unsafe behavioural accident system model diagram is obtained by this method, as shown in Fig. 7.
Based on the hierarchical structure of unsafe behaviour factors, the 26 influencing factors are finally divided into five layers, with the first layer being the proximity causation layer, the second, third and fourth layers being the transition causation layer, and the fifth layer being the essential causation layer. The complex network of accident factors and the complex non-linear correlation relationship between accident factors is the whole unsafe behaviour accident system. From Fig. 7 unsafe behaviour accident system model, it can be seen that a18 education and training, a26 safety attitude, a24 safety investment, a20 organisational culture atmosphere, a13 psychological condition, a22 decision-making and management are factors with more nodes, which can also be considered as key factors that should be focused on, and these key factors are distributed in all layers. The factors that play a key role in the proximity causation layer are education and training and organisational culture; the nodes that play a key role in the transition causation layer are safety inputs, decision-making management and safety attitudes, respectively; and the psychological condition is located in the intrinsic causation layer along with the work experience, which can influence all the other factors of unsafe behaviours. Among these factors, the treatment of neighbouring causal factors has a more significant behavioural effect but is more difficult to control, whereas the treatment of the underlying essential causal factors, although less effective, can have a comprehensive effect on the whole system of unsafe behavioural factors. Therefore, a11 work experience and a13 psychological condition are the two most essential factors in this model, and the risk transmission law of these two nodes will continue to be analysed in depth in the subsequent research. The fact that no other factors are associated with a1 Site Environment and a2 Emergency Resources is due to the chosen eigenvalues, but in reality it is the closeness between the environment and the unsafe behaviour, which will be omitted from the subsequent analysis.
The emergence and transmission of behavioral risks of coal mine workers
Description of the model design
The risk disposal capability of the unsafe act accident system is the embodiment of the ability of the act itself to control the risk state, this thesis uses Arena software to analyse the impact of the initial risk emergence on the risk disposal capability of the whole unsafe act system by setting different parameters; and to analyse the impact of the parameters of the causative node on the disposal capability of the unsafe act system, and so on.
The probability density function of risk emergence is generally a random exponential function that obeys a certain mean, a certain mean in this considered to be a certain time interval30. Set a11 and a13 as two initial nodes, whose respective maximum risk emergence value is 200.At the initial moment of the whole accident, the two nodes share one risk disposal resource, i.e. Resource Capacity = 1. The risk disposal capacity of each causal node obeys the triangular distribution of TRIA (0.5, 1, 1.5). Causal node risk immunity capacity can be understood as the node itself also exists the corresponding risk identification and disposal capacity, when the entropy value of the risk to be processed within the node is less than 10, the node itself can dispose of the risk, and the risk that is not processed will be risk transferring to the node that is adjacent to it.
The unsafe behaviour risk transfer model stops simulation when there is no internal risk. System risk entropy, residual risk entropy, and intra-nodal risk entropy are mainly collected during model simulation. The maximum system risk entropy determines the limit of the system to carry risks, the maximum residual risk entropy relates to the possibility of causing accidents, and the maximum risk entropy of the node is to decide when to break the threshold value31,32.
In order to study the transmission law of the risk of unsafe behaviours, according to the model diagram of the unsafe behaviours accident system, it can be seen that the hierarchical structure relationship between the factors influencing unsafe behaviours determines the direction of the transmission of the risk of unsafe behaviours, i.e., from the bottom layer to the surface layer. Among them, it should be noted that since the discrepancy between factor a1 and factor a2 is zero, the analyses of these two factors will be omitted later.
Since a11 work experience and a13 psychological state as the most essential two factor nodes among the 26 unsafe behaviour influencing factors, these two factors are taken as the initial nodes of the unsafe behaviour risk transfer simulation model, which facilitates the exploration of the influence of the two essential causal factors on the whole unsafe behaviour system. Risk emerges at the initial node and then passes to the neighbouring causal nodes, and if its risk entropy is greater than the threshold value of the neighbouring causal nodes, it may trigger an unsafe behaviour accident.
The initial setup risk entropy of each node in the unsafe behaviour risk transfer model is shown in Fig. 8.
Arena simulation model construction
For the unsafe behaviour accident system model, the Arena software is used as a simulation tool. Arena, developed by Rockwell Software, Inc. (USA), is a general-purpose simulation software renowned for its powerful functionality, user-friendly interface, intuitive visualization, and dynamic animation capabilities. The software employs a hierarchical modeling architecture that enables flexible simulation development across multiple complexity levels, effectively balancing usability with adaptability. It has been extensively applied in manufacturing systems, logistics networks, service industries, healthcare operations, military systems, and global supply chains encompassing warehouse management, transportation, and material flow33.
With its graphical user interface and flowchart-based modeling methodology34, Arena’s versatility and flexibility make it particularly suitable for simulating behavioral risk transmission35. This approach adeptly captures the complex and dynamic characteristics of unsafe behaviors in operational environments.By rationally utilizing the basic process module, advanced process module, and advanced transmission module in Arena, we constructed the unsafe behavior risk transfer simulation model as shown in Fig. 9.
Figure 9 shows the main part of the model; Fig. 10 shows the sub-model of the causal node’s own risk disposal part of the path module, each causal node in the main body includes a sub-model, so the model contains a total of 24 sub-models, and the use of sub-models simplifies the main part of the model and makes the logic of the whole model clearer. It is assumed that each node has its own risk immunity and risk disposal speed, and risk may cause unsafe behaviour accidents if it is not effectively disposed of during the transmission process36. On the one hand, the unsafe act accident system should try to reduce the risk entropy in the system to avoid the appearance of large peaks; on the other hand, the residual risk passed backward through the neighbouring causal nodes should be as small as possible to avoid accidents. Therefore, system risk entropy and residual risk entropy are the two main evaluation indexes in the model37.
Analysis of the emergence and transmission patterns of behavioural risks among coal mine workers
Generally speaking, the speed of risk emergence rate is related to whether the risk is easy to be identified and controlled, the slower the risk emergence rate, the easier the risk is identified and controlled, on the contrary, it will be difficult to manage and control. In the process of general enterprise employee safety behaviour management, the risk management and control measures for employee behaviour must be targeted, according to the common insecurity risk emergence characteristics, to give the causative node of the corresponding risk immunity level. Setting the initial risk emergence obeys the stochastic exponential distribution, this section will analyse the impact of different mean values of initial risk emergence on the system risk entropy and residual risk entropy; analyse the impact of the initial node risk immunity on the system risk disposal ability; analyse the impact of different risk disposal rates of each node on the system risk disposal ability.
Impact of different emergence averages on the system’s ability to deal with risk
In Fig. 11a–d correspond to emergence means of 0.5, 1, 1.5, and 2, respectively. The red line represents the systematic risk entropy and the green line represents the residual risk entropy.
With the increase of the mean value of risk emergence, that is, the increase of the time interval of risk emergence, the increase of the mean value of risk emergence will reduce the growth rate of risk entropy, that is, the larger the mean value of risk emergence, the lower the growth rate of risk entropy. From the figure, it can be seen that with the increase of the mean value of risk emergence, the maximum system risk entropy and the maximum residual risk entropy are gradually reduced, and the simulation time of the model is also gradually shortened. At the same time, as the risk entropy emergence rate decreases, i.e., the interval time between risk emergence increases, the maximum value of system risk entropy and system residual risk entropy decreases, and when the interval time reaches 2 the residual risk entropy of the system is almost reduced to 0, which indicates that reducing the risk emergence rate allows each node to have sufficient time to dispose of the risk, thus reducing the possibility of accidents.
Impact of node immunity on systemic risk management capacity
In Fig. 12a–d correspond to risk immunity values of 2.5, 5, 7.5, and 10, respectively. The red line represents the systematic risk entropy and the green line represents the residual risk entropy.
Changing the node risk immunity is to change the node’s own risk disposal ability. Increased immunity of the lowest node increases the initial node’s ability to intercept risks and reduces the probability of risk transmission.
From Fig. 12, we can learn that the risk entropy change curve, in the case of risk emergence interval time of 2, when the immunity of node 11 is increased from 2.5 to 5, the system risk entropy and residual risk entropy are obviously reduced, but when continue to increase the immunity of node 11, the reduction of risk entropy is not obvious anymore, which indicates that appropriately increasing the immunity of node 11 has a significant impact on reducing accidents. And the increase of initial node risk immunity can drive the risk disposal ability of neighbouring associated nodes.
The values of risk immunity corresponding to (a) (b) (c) (d) in Fig. 13 are 2.5, 5, 7.5, and 10, respectively. the red line represents the systematic risk entropy and the green line represents the residual risk entropy. As can be seen in Fig. 4.6, the risk immunity of node 13 has the same effect on the risk disposal capability, except that the systematic risk entropy is relatively small.
Impact of node risk disposal rate
An increase in the rate of node risk disposal means that the time occupied by risk disposal resources is reduced, indirectly improving the utilisation of resources. At the same time, the entropy value of internal undisposed risks can be reduced, facilitating the disposal of more risks.
In Fig. 14 (a) indicates a risk disposal rate of 0.8 and (b) indicates a risk disposal rate of 1. The red line represents systematic risk entropy and the green line represents residual risk entropy.
From Fig. 14, it can be seen that when the risk disposal rate is 1, the node 11 single risk processing time is significantly reduced and the maximum system risk entropy value also appears to be reduced to a large extent when compared to a risk disposal rate of 0.8.
In Fig. 15, (a) indicates that the risk disposal rate is 0.8 and (b) indicates that the risk disposal rate is 1. The red line represents the system risk entropy and the green line represents the residual risk entropy. From Fig. 15, it can be seen that node 13 shows more obvious changes after increasing the risk disposal rate, not only the simulation time is obviously reduced, the maximum system risk entropy appears to be reduced to a large extent, and at the same time, the residual risk entropy is obviously disposed by the node itself. Therefore, from Figs. 14 and 15, it can be seen that the increase of the node’s risk disposal rate has a very significant effect on the node’s risk disposal ability.
Unsafe behaviour control countermeasures
Through the analysis of the influencing factors and risk transfer of unsafe behaviours, as well as the combination of several experts’ research on the pre-control of unsafe behaviours of coal mine workers, this study puts forward the specific control countermeasures against the unsafe behaviours of coal mine workers from five aspects, such as safety management, individual, group, safety leadership and physical environment.
Security management control measures
-
(1)
Safety education and training: Establish a systematic and effective safety education system according to the specific situation, in order to ensure that the education and training of workers is reasonable and operable.
-
(2)
Safety incentive mechanism: Establish a fair and reasonable reward and punishment system, a fair and reasonable reward and punishment system is more capable of mobilising the safety enthusiasm of the workers.
-
(3)
Leave and competition System: Formulate a reasonable incentive leave system and competitive selection system, fully mobilise the personal development of the coal mine workers, and guide them to take the initiative in choosing the safe way of behaviour.
-
(4)
Safety culture construction: Strengthen the construction of key elements in the safety culture.
-
(5)
Safety supervision and inspection: Develop areasonable plans and safety inspection cycles carry out special inspections and comprehensive inspections in a timely manner .
-
(6)
Safety input optimisation: Combine the principles of safety economics, optimise investment structure, including safety culture, education, inspections and so on.
Individual behavioural control responses
-
(1)
Employee qualification access management: Strengthen the management of physical, physiological, educational and professional experience access, and use the EAP plan to provide physiological counseling to employees.
-
(2)
Employee unsafe behaviour control: BBS behaviour observation method can be used to warn and control unsafe behaviours, and BBS behaviour observation can be regarded as a supplement to the safety inspection of the enterprise, the enterprise should take the results of the safety inspection as the main basis for rewards and punishments.
-
(3)
Operation standardisation management: To achieve refined management, to ensure the implementation of the safety management system, to ensure that the operation is safe, accurate, efficient and labor-saving, and to supervise and assess the implementation of the standardisation of operations.
Group behaviour control responses
-
(1)
Create a safe atmosphere for groups: Create a good group safety atmosphere through safety culture, education and publicity, and then curb the emergence of unsafe behaviours.
-
(2)
Improve the group safety norms: The idea of operation standardization is introduced, and the positive guiding function of the formal norms and the important role of informal norms are used to standardize the behaviour of employees.
-
(3)
Communication environment optimization: Broaden communication channels, improve communication efficiency and create a good communication environment38.
-
(4)
Group structure optimization: Control the group size, optimize the composition of members, and improve the efficiency of safety production.
Security leadership control responses
-
(1)
Safety incentives and communication: Reasonable incentives, prudent punishment, strengthen the communication with the workers to enhance the sense of mutual trust.
-
(2)
Safety control and guidance: Leaders lead by example, abide by rules and regulations, and provide specific guidance to workers so that they always maintain safe behaviour.
Physical environment control countermeasures
-
(1)
Identification of sources of danger and risk management: Conduct pre-danger analyses and identification of the sources of danger, assess the severity of the risks, and formulate coping strategies and management methods.
-
(2)
Working environment optimization: Combined with the 6 S39 management method to achieve site environment management, improve dust, toxic gas management, optimize lighting and working space.
-
(3)
Safety investment and equipment upgrade: Introduce advanced equipment, improve the level of mechanization, make maintenance plans, and achieve a reasonable match between an and machine.
Results
Work experience and psychological status are the two factors with the highest frequency of occurrence, indicating that their influence on unsafe behaviors is the most significant.
Integrating the DEMATEL-ISM method, 26 factors are divided into a five-level hierarchical structure. Work experience and psychological status, as the underlying essential cause nodes, can affect the entire system through risk transmission.
Through the Arena simulation calculation of risk transfer of unsafe behaviors, it is known that the larger the emergence mean, the better the risk disposal effect. After enhancing the immunity of the essential causative nodes to the threshold, the systematic risk entropy decreases significantly. Increasing the risk disposal rate of the nodes can significantly reduce the maximum system risk entropy and residual risk entropy.
Conclusion
Through text mining of 574 accident investigation reports, an indicator system for influencing factors of unsafe behaviors in coal mines was developed, encompassing 26 indicators across five dimensions: environmental, individual, group, organizational management, and leadership factors.
The DEMATEL-ISM method revealed a five-layer hierarchical structure of factors: the first layer is t adjacent cause-causing layer, the second to fourth layer are transitional causative layer, and the fifth layer is intrinsic causative layer. Key factors in the proximate causation layer include education and training and organizational cultural atmosphere; critical nodes in the transitional causation layers are securiy input, decision management, and security attitude; while psychological status resides in the essential causation layer (along with work experience), which exerts systemic influence on all other unsafe behavior factors.
The causal layer node 11 work experience and node 13 psychological status are used as the initial nodes of the model, and it is known through the unsafe behaviour risk transfer Arena simulation calculation that the larger the emergence mean value is, the longer the node itself disposes of the risk, and the better the effect of the risk disposal is; the increase of node immunity can improve the node’s risk interception ability, and reduce the transmission of the risk of unsafe behaviours; the increase in the node’s risk disposal rate can significantly reduce the maximum system risk entropy and residual risk entropy.
Carried out the research on the intervention and control countermeasures of unsafe behaviour of coal mine workers, and put forward specific control countermeasures against unsafe behaviours. Firstly, perfecting the safety management system; secondly, improving the quality of the workers themselves and strengthening the standardisation of operations; thirdly, optimising the group structure and safety norms; fourthly, strengthening the safety guidance of the leaders; and fifthly, improving the operating Fifth, improve the working environment to achieve a reasonable match between man and machine.
Discussion
This study systematically investigates the risk emergence and transmission mechanisms of unsafe behaviors among coal mine workers through an integrated methodology combining text mining, the DEMATEL-ISM method, and Arena simulation techniques. By revealing risk transmission rule at essential causation nodes and proposing targeted interventions based on simulation data, the research establishes both theoretical foundations and practical guidelines for enhancing coal mine safety management systems.
Existing studies predominantly focus on singular dimensions. For instance, Chen Zihan et al. employed structural equation modeling to examine the influence of informal groups on unsafe behaviors, while Liu Haibin et al. investigated individual-level effects of risk perception disparities. However, these works demonstrate limited systematic analysis of multifactorial interactions. Grounded in text mining of 574 accident reports, this research extracts 26 indicators spanning five dimensions—environmental, individual, group, organizational management, and leadership—encompassing broader influencing factors. Notably, it incorporates previously understudied indicators such as “leadership safety commitment” and “group cohesion”, thereby establishing a more comprehensive analytical framework for risk assessment.
Existing studies predominantly employs static analytical approaches (e.g., structural equation modeling, factor analysis), which inadequately capture the dynamic evolutionary patterns among influencing factors. In contrast, this study adopts an integrated DEMATEL-ISM methodology to construct a five-tier hierarchical structure model, identifying “work experience” and “psychological status” as essential causation nodes. Furthermore, Arena-based simulations were implemented to quantitatively characterize the dynamic transmission processes of risk entropy.
Existing control measures are mostly scattered across single domains. For instance, Cao Qingren et al. proposed differentiated implementation of safety management behaviors, while Liu Qi et al. emphasized psychological stress relief. This study proposes comprehensive management strategies from five dimensions: safety management, individual factors, group dynamics, safety leadership, and physical environment. By combining 6 S management to optimize the working environment and introducing BBS observation methods to strengthen individual behavior control, these strategies echo Zhang Guangyu et al.‘s recommendations regarding group safety behaviors. This approach provides more operational solutions for coal mine safety management, integrating multiple perspectives to address systemic challenges in the field.
Although this study has made progress in multi-dimensional modeling and dynamic simulation, there remain certain limitations. The simulation model assumes static environmental factors and fails to account for their dynamic interactions. Additionally, the generalizability of control strategies requires validation through field data from diverse coal mines. Future research could further explore the impact of environmental dynamic changes on risk propagation and optimize simulation parameters based on practical case studies to enhance the model’s applicability.
Data availability
All data generated or analysed during this study are included in this manuscript.
References
The 14th Five-Year National Work Safety Plan. (2021).
Heinrich, H. W. Industrial Accident Prevention (McGraw- Hill, New York, 1979).
Wang, J. F. & Li, W. J. Coal Accidents and Expert Commentary (Coal Industry, Beijing 2001).
Chen, Z. H., Li, L., Yang, O. & Li, Y. P. Analysis of group dynamics of coal mine workers on the drivers of unsafe behaviours from the perspective of informal organisation. China Prod. Saf. Sci. Technol. 20(03), 126–133 (2024).
Liu, H. B. & Liang, Z. D. Research on the influencing factors of employees’ intention to engage in unsafe behaviours. Chin. J. Saf. Sci. 21 (08), 15–21 (2011).
Liu, Q., Kong, Q. & Zhang, L. Y. Research on miners’ psychology and safety production. China Coal. 36(03), 107–110 (2010).
Cao, Q. R. & Li, K. Research on various coal mine safety management behaviours and their mutual influence role. J. Saf. Environ. 15(01), 6–10 (2015).
Chen, S. S., Xu, J. H. & Fan, Y. Evaluating the effect of coal mine safety supervision system policy in china’s coal mining industry: a two-phase analysis. Resour. Policy 46, 12–21 (2015).
Li, W. Z. L. Dynamic Simulation and Control Strategy Exploration of the Unsafe Behavior of Coal Mine Employees (Resources Policy, 2023).
Feldman, R. & Hirsh, H. Finding Associations in Collections of Text. Mach. Learn. Data Min. 199137 .
Wu, F., Jiang, F. C., Yao, H. J., Huang, M. & Ma, Q. D. Analysis of causal factors and risk prediction of inland ship collision accidents based on text mining. Transp. Inform. Saf. 36 (03), 8–18 (2018).
Li, Y. Q., Xie, C. B. & Gao, Y. Research on influencing factors of unsafe behavior of hydraulic engineering construction workers based on text mining. China Rural Water Hydropower (06): 150–155. (2024).
Zhu, Y. N., Heng, L. W. & He, G. Analysis of the Influencing Factors of Unsafe Behaviors of Coal Mine Employees. Min. Saf. Environ. Prot. 46(01), 104–108 (2019).
Zhang, G. Y., Cao, Q. G. & Yao, Q. G. Analysis of safety behavior model of coal mine employee groups. Coal Econ. Res. 31(11): 101–104 (2011).
He, P. et al. Examining influencing factors and their hierarchical relationships in flight crew resilient behavior through a hybrid ISM-DEMATEL approach. Sci. Rep. 15 (1), 1606–1606 (2025).
Li, M. H., Xia, J. B. & Chen, C. Q. A network lineage model with reachable influencing factors based on decision experiments and evaluation experiments and explanatory structure models. J. University(Engineering Technol. Edition), (03): 782–788. (2012).
Yan, M., Jia, J. & Chen, Y. Research on accident early warning of metallurgical enterprises based on grey DEMATEL/ISM and bayesian network. Sci. Rep. 14 (1), 18312–18312 (2024).
Yılmaz, M. & Kanıt, R. A practical tool for estimating compulsory OHS costs of residential Building construction projects in Turkey[J]. Saf. Sci. 101, 326–331 (2018).
Clothier Reece, A., Williams Brendan, P. & Hayhurst Kelly, J. Modelling the risks remotely piloted aircraft pose to people on the ground. Saf. Sci. 101, 33–47 (2018).
Chinniah, Y., Gauthier, F., Aucourt, B. et al. Validation of the impact of architectural flaws in six machine risk Estimation tools. Saf. Sci. 101, 248–259 (2018).
Tremblay Alec, B. & Adel Assessment of occupational health and safety performance evaluation tools: state of the art and challenges for small and medium-sized enterprises. Saf. Sci. 101, 260–267 (2018).
Su, G. & Hu, E. Research on coal mine safety risk evolution and key hidden dangers under the perspective of complex network. Sci. Rep. 14(1), 20624–20624 (2024).
Domeneghetti Bertrand, B. & Yasmine Wybo Jean-Luc. Analyzing nuclear expertise support to population protection decision making process during nuclear emergencies. Saf. Sci. 101, 155–163 (2018).
Chen, Y. & Yan, S. Y. Safety evaluation of human-machine interface of coal mine machinery based on ergonomics. J. Heilongjiang Univ. Sci. Technol. 25(06): 692–696 (2015).
Qin, S. S. Key Factor Selection Method of Complex System DEMATEL and its Application in a Logistics Enterprise (Kunming University of Science and Technology, Kunming 2017).
Gao, Y. Causes and countermeasures of employees’ unsafe behaviors. Manage. Technol. Small Medium-sized Enterprises (Next day). 07, 18–19 (2014).
Tang, H. C., Liu, X. D. & Li, M. Y. Research on the influencing factors of Chinese agricultural brand competitiveness based on DEMATEL-ISM. Sci. Rep. 14(1), 11363–11363 (2024).
Zhang, X. M., Yan, S. J. & Yao, Q. G. Research on coal mine safety management evaluation system based on DEMATEL method and ISM model. Coal Econ. Res. 31(06), 82–85 (2011).
Tian, S. et al. Predictive analysis of miners’ group unsafe behavior based on group dynamics and institutional environment. Sci. Rep. 15 (1), 9263 (2025).
Chu, X. P. Research on the Control Effectiveness of Coal Mine Safety Inspection Strength on Miners’ Unsafe Behaviour (Xi’an University of Science and Technology, Xi’an 2017).
Hao, G. Successful application and prospects of risk pre-control management system in Shenhua Group. Coal Mine Saf. 42(10), 149–153 (2011).
Fang, S. Q., Wei, K. & Chen, W. P. Modeling and simulation of station flight support process based on ARENA. J. Syst. Simul. (03), 746–750 (2008).
Cheng, L. J. Research on the Formation Mechanism of Miners’ Unsafe Behaviors and their Dual Effects (Liaoning Technical University, Fuxin 2015).
Zhao, J. Y. & Ma, C. P. Simulation and optimization of the operation time of logistics company B using arena. Sci. Technol. Manage. Res. 31(15), 121–124 (2011).
Wang, S., Wang, Y. & Du, C. Emergence and dynamic propagation analysis of risk entropy in complex systems. Saf. Environ. Eng. 20(02), 118–120 (2013).
Sizarta, S. & Stein, H. Visualizing risk related information for work orders through the planning process of maintenance activities. Saf. Sci. 101, 144–154 (2018).
Li, Y. W. Research on the Construction of Enterprise Safety Production Accident Hidden Danger Management System (Harbin Engineering University, Harbin 2007).
You, Q., Yao, Q. G. & Song, R. X. Multi-dimensional safety risk assessment on coal mines under the profitability dilemma. Sci. Rep. 13 (1), 2687–2687 (2023).
Alec, T. & Adel, B. A novel tool for evaluating occupational health and safety performance in small and medium-sized enterprises: the case of the Quebec forestry/pulp and paper industry. Saf. Sci. 101, 282–294 (2018).
Author information
Authors and Affiliations
Contributions
L.J. is responsible for accident investigation, data collection and analysis, analogue simulation, and manuscript writing.M.H. is responsible for method selection, validation and manuscript writing.K. is responsible for manuscript writing and reviewing.T.Y. is responsible for data collection and analysis.Z.X. is responsible for analogue simulation.Z.Y. is responsible for accident investigation.All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Zhou, L., Wang, M., Yu, K. et al. A simulation study on risk emergence mechanism and transmission path of coal mine workers’ unsafe behaviours based on DEMATEL-ISM and Arena simulation. Sci Rep 15, 24289 (2025). https://doi.org/10.1038/s41598-025-07478-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-025-07478-5