Abstract
The integration of cyber-physical systems (CPS) with the Internet of Things (IoT) in smart city transportation systems presents promising opportunities, however poses challenges in data privacy and security. This paper proposes a novel approach to address these challenges by incorporating Elliptic Curve Cryptography (ECC) for heightened data security in CPS-IoT integrated transportation. ECC serves as a robust cryptographic solution, safeguarding data confidentiality and integrity during exchanges between IoT devices and infrastructure. Through an in-depth examination of privacy threats and vulnerabilities inherent in such systems, the paper highlights ECC’s potential to mitigate risks. Furthermore, it explores the implementation of ECC-based encryption and decryption mechanisms to ensure secure communication and data exchange. Additionally, the paper discusses the adoption of Transport Layer Security (TLS) as a secure data communication protocol and enhancing the overall security and efficiency of CPS-IoT transportation systems. To validate the effectiveness of our framework, we compare it with an assumed framework that utilizes Differential Privacy method and SSL, highlighting the advantages of our approach in terms of security, efficiency, and practicality. By fostering a secure data environment, ECC and TLS contribute to informed decision-making, resource optimization, and the advancement of sustainable transportation infrastructure, thus fostering a circular economy.
Similar content being viewed by others
Introduction
The convergence of Cyber-Physical Systems (CPS) and the Internet of Things (IoT) is a major advancement in the digital era1. CPS integrates physical components with computing and networking, enabling real-time interaction with the physical world2. The IoT, a vast network of interconnected sensors, amplifies this by facilitating data communication3. This synergy allows CPS to leverage IoT’s data collection for real-time insights, while CPS empower IoT with data analysis and control4. This drives innovation in areas like Industry 4.0, smart cities, and sustainability5. Research on CPS-IoT integration highlights its potential to revolutionize manufacturing, with security as a key concern6,7. AI integration with CPS-IoT offers further optimization, while smart grids benefit from these technologies for efficient energy management8,9. Advancements in low-power sensors and miniaturization trends further fuel CPS development10,11.
Overall, CPS-IoT integration holds immense potential for shaping the future of digital innovation12. Cloud computing integration empowers CPS by providing vast storage and processing for massive data analysis in real-time6,13. This transforms how we interact with the physical world across sectors like transportation, energy, healthcare, and smart cities7,9. In smart cities, CPS and IoT enable innovative solutions for traffic management, resource optimization, and citizen services9. This integration is exemplified by Intelligent Transportation Systems (ITS) that leverage advanced technologies for safer, more efficient transportation networks2. Intelligent Transportation Systems (ITS) leverage real-time sensor data to optimize traffic flow14. Sensors on vehicles, pedestrians, and infrastructure collect data that’s analyzed centrally to dynamically adjust traffic signals via actuators10. This collaboration improves safety and efficiency, reducing collisions10,14. V2V and V2R communication protocols enable data exchange within the ITS network, tackling issues like traffic congestion and fuel inefficiency15. As these systems become central to smart cities, robust security measures are crucial for urban resilience14. Security in CPS for smart cities demands data protection, integrity, and controlled access14,15. This includes confidentiality (authorized users only), integrity (preventing data tampering), authentication (verifying data sources), and access control (restricting system access)15. Dependability ensures reliable operations without performance issues, crucial for critical infrastructure16. Safety is paramount, especially for applications involving heavy machinery or where malfunctions endanger lives14.
To meet the rising need for secure communication in CPS-IoT systems, recent research has focused on efficient authentication methods. Cloud-enhanced IoT helps address device limitations by enabling remote management but also raises security concerns due to system complexity and scale. A lightweight multi-factor authentication framework has been proposed to reduce gateway node load while ensuring strong security. Its effectiveness is confirmed through formal tools like the Scyther Tool and comparative evaluations showing minimal overhead17. The integration of 6G, blockchain, and UAVs in the IoV framework is transforming smart transportation by moving from traditional V2X systems to decentralized, drone-based models. These models face challenges like latency, energy use, and security risks. The IoV-6G + framework addresses these issues using lightweight blockchain, UAV data collection, and secure edge-cloud communication. Edge servers gather data, while cloud nodes validate and store it via blockchain. Security analysis using Scyther and the RoR model confirms reduced overhead, improved energy efficiency, and strong protection against attacks18. Taken together, these advancements underline the urgent need for scalable, secure, and lightweight frameworks in CPS-IoT systems for smart cities. Whether through ECC-based encryption, multi-factor authentication, or blockchain-driven vehicular communication, the emphasis remains on preserving privacy, ensuring dependability, and enabling secure data-driven innovation for the future of intelligent transportation. This study addresses these concerns by proposing a secure collaboration framework for communication within smart city transportation networks. The proposed framework prioritizes the privacy of intelligent transportation data. This is paramount in the context of smart cities, where data collected from vehicles, sensors, and infrastructure can be highly sensitive. To address this challenge, this study proposes a multifaceted approach to secure data communication and unlock the full potential of CPS and IoT integration within smart city transportation systems. To ensure robust data security, we leverage ECC. ECC’s efficient key management and faster computation speeds make it ideal for resource-constrained IoT devices within the CPS network. Furthermore, the Transport Layer Security (TLS) protocol is implemented to establish secure communication channels between these devices and infrastructure components. This layered approach ensures data confidentiality and integrity throughout its transmission. However, striking a balance between robust security and user privacy is paramount. By implementing a privacy-preserving communication framework, we can safeguard sensitive user data while still enabling the data-driven decision making crucial for optimizing resource allocation and promoting sustainable practices. This transparency fosters trust among citizens, encouraging their participation in smart city initiatives, and ultimately contributing to a more efficient and environmentally friendly urban landscape. The convergence of CPS and IoT goes beyond secure communication. While this study focuses on secure data transmission within CPS and IoT integrated transportation systems, the real-time analysis of this data is crucial for optimizing resource usage. This subsequent processing, beyond the scope of this work, can inform strategies like promoting electric vehicles through efficient charging infrastructure or identifying opportunities for material reuse within the transportation network. This data-driven approach paves the way for a thriving circular economy within the smart city, laying the foundation for a more sustainable future. The contributions of the study can be summarized as follows:
-
To identifies the critical challenge of securing communication within CPS-IoT integrated transportation systems in smart cities. It emphasizes the importance of protecting sensitive data exchanged between various entities in this network.
-
The research proposes a novel approach to enhance data security by leveraging ECC.
-
The study goes beyond just proposing a solution. It conducts a comprehensive analysis of potential privacy threats and vulnerabilities within these systems. This analysis delves into how ECC can mitigate these identified risks and ensure data confidentiality and integrity.
-
The study advocates for the adoption of TLS as a secure data communication protocol, further enhancing the security of CPS-IoT transportation systems. By incorporating TLS, the framework ensures secure transmission of data, safeguarding it against unauthorized access or manipulation.
-
The study explores the broader impact of secure data communication on sustainability. It highlights how a secure data environment fostered by ECC can contribute to a sustainable and resilient transportation infrastructure. This includes enabling data-driven decision making for resource optimization, promoting electric vehicles, and facilitating material reuse and recycling within the smart city transportation network, ultimately leading to a circular economy.
The subsequent sections of this academic paper are organized as follows: Section "Background" provides the background information. Section "Methodology" offers outline of the proposed Framework. Section "Results and discussion" delves into the results and discussion. Section "Evaluation and validation" covers the evaluation and validation. Section "Conclusion" offers conclusion and future scope.
Background
The integration of CPS and IoT is transforming modern urban infrastructure, particularly in the domain of sustainable transportation. A key enabler of this transformation is the adoption of evolving standards that ensure functionality, interoperability, and security within CPS-IoT systems15. These standards, as illustrated in Fig. 1, span a variety of domains including wide-area monitoring, smart grids, and communication protocols16. International bodies such as the IEC and IEEE have been instrumental in their development16. Examples include IEC 61,850 for substation communication and IEC 62,351–6 for cybersecurity in energy systems15,16, while standards like PRIME and ANSI C12 further enhance interoperability across various platforms15. Additionally, CPS-IoT interoperability is not limited to functionalities alone; it extends to network protocols and communication within smart grid environments, facilitated by standards such as IEEE 1815 and IEEE 203015. Security standards also play a vital role, with ENISA, ISA-62443, and ISO/IEC 27,014 providing cross-sectoral security frameworks13,19. To address emerging technologies, newer standards like IEEE 2418.7 for blockchain and SAE JA7496 for CPS risk management have been introduced20,21, all contributing to a secure and interoperable CPS landscape21.
Within the context of smart cities, particularly in sustainable transportation, secure and seamless data exchange across CPS and IoT systems is fundamental12. Although distinct standards govern these domains—such as IEC 62,056 for Advanced Metering Infrastructure (AMI) and IEEE P2510 for IoT data quality (see Fig. 2)—interoperability remains key15. For example, secure substation communication is supported by IEC 62,351–6, while ISO/IEC 27,400 addresses privacy and security concerns specific to IoT. These standards underpin reliable data exchange that enables data-driven decision-making and supports a sustainable circular economy in urban mobility12. By safeguarding data integrity and enabling system compatibility, this framework empowers the collection and utilization of traffic flow data to implement strategies like congestion pricing, thereby reducing fuel consumption and emissions. Furthermore, leveraging data on vehicle health and location enables predictive maintenance and facilitates recycling or reuse of materials at the end of a vehicle’s lifecycle. Such data-driven mechanisms are essential for minimizing resource depletion in the transportation sector and advancing sustainable urban mobility.
As smart city systems become increasingly interconnected, the threat landscape they face continues to evolve. Ensuring data security across CPS-IoT transportation systems is not only a technical necessity but also a foundational component for building a sustainable, trustworthy urban environment22. The rising prevalence of cyber threats—ranging from social engineering and supply chain attacks to system misconfigurations and poor cyber hygiene—requires a comprehensive and proactive cybersecurity approach23. In response, a diverse toolkit of cyber defense mechanisms has become essential for protecting these systems24. Key elements of such a toolkit include:
-
Machine learning algorithms that automatically detect anomalies in network traffic and system behaviors25,26.
-
Network security monitoring tools that continuously evaluate network health to promptly identify potential threats27.
-
Dedicated network defense tools for securing wireless networks, including Wi-Fi encryption and intrusion detection28.
-
Web vulnerability scanners that identify and mitigate weaknesses in web applications29.
-
Antivirus software for detecting and eliminating malware30.
-
Encryption tools to secure data both in transit and at rest, ensuring it remains unreadable to unauthorized parties31.
-
Firewalls to control and filter traffic between trusted and untrusted networks32.
Together, these tools establish a secure data environment that enables informed and sustainable decision-making. For instance, traffic data securely collected through CPS-IoT systems can inform congestion management policies, while vehicle diagnostics data can enhance predictive maintenance and material recovery efforts. In this way, cybersecurity is not only about protection but also a catalyst for sustainable innovation in transportation.
To further strengthen secure data exchange, particularly in resource-constrained mobile environments, advanced cryptographic techniques like ECC have gained prominence. ECC presents a robust alternative to Differential Privacy (DP)40, moving beyond noise addition by employing mathematical properties of elliptic curves to achieve high encryption strength without compromising data fidelity33. ECC offers several distinct advantages:
-
Stronger security: ECC generates complex encryption keys via elliptic curve operations, offering superior protection over the randomized noise methods used in DP34,40.
-
Efficiency with small key sizes: A 256-bit ECC key offers security comparable to a 3072-bit traditional key, making ECC ideal for mobile and embedded systems33.
-
Faster performance: ECC implementations can improve server response times, enhancing user experience in web and mobile applications33.
Despite these benefits, ECC introduces challenges related to its computational complexity. Unlike the simpler noise-based calculations of DP42, ECC involves intricate encryption and decryption processes35. To overcome this, researchers are exploring several efficiency-enhancing strategies:
-
Hardware accelerators, such as Application-Specific Integrated Circuits (ASICs), are being developed to offload ECC computations from general-purpose processors33,34.
-
Algorithm optimization: Techniques like coordinate representation and exponential addition chain methods aim to reduce the number of operations during scalar multiplication, a core ECC task35,36.
-
Curve selection: Ensuring security in ECC relies on selecting elliptic curves with a common mathematical property known as "order." Early methods to find such curves were computationally expensive, but improvements have emerged:
These advances collectively address key security and performance concerns, positioning ECC as a viable and efficient cryptographic solution for modern CPS-IoT applications in sustainable transportation.
Methodology
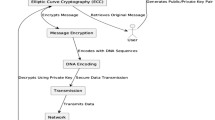
In this section, we present the methodology behind the proposed framework for preserving data privacy of communication in CPS-IoT integrated transportation for smart cities using ECC33 depicted in Fig. 3. Figure 3 illustrates the proposed methodology for securing transportation data in IoT-based smart city systems using Elliptic Curve Cryptography (ECC). The process begins with the initialization of ECC parameters, followed by the generation of unique public–private key pairs for each IoT device. For every data packet generated within the transportation system, the data is encrypted using the recipient’s public key to ensure confidentiality. These encrypted packets are then transmitted securely via a TLS-encrypted channel. Upon receiving data, the recipient device decrypts it using its private key and processes the decrypted information for transportation analytics. This methodology ensures secure, end-to-end encrypted communication, preserving data integrity and privacy across the network.
The proposed framework outlines the distinct phases involved the preserving data privacy of communication in CPS-IoT integrated transportation for smart cities using ECC33, as the following:
Initialization phase
During the initialization phase, the necessary groundwork is laid to enable the application of ECC for preserving data privacy of communication in CPS-IoT integrated transportation for smart cities. This phase involves two key steps:
Initialize ECC parameters
-
This step involves generating the essential parameters required for ECC, such as curve parameters and the base point.
-
The choice of curve parameters and base point plays a crucial role in determining the security and efficiency of the ECC implementation.
-
By carefully selecting these parameters, the cryptographic system can achieve the desired level of security while optimizing performance.
Setup cryptographic environment
-
In this step, the cryptographic environment is established by importing the necessary libraries and initializing ECC parameters within the programming environment.
-
This includes importing ECC libraries or modules that provide functions for key generation, encryption, and decryption operations.
-
Initializing ECC parameters ensures that the cryptographic operations performed during key generation and data encryption/decryption are conducted using the specified ECC settings.
By completing the initialization phase, the foundation is laid for subsequent phases of the framework, enabling the secure and privacy-preserving exchange of communication data in CPS-IoT integrated transportation systems for smart cities.
Key generation phase
The Key Generation Phase is pivotal in establishing the cryptographic infrastructure necessary for secure communication and data exchange within CPS-IoT integrated transportation systems. This phase comprises two essential steps:
Generate key pairs
-
In this step, public–private key pairs are generated for each IoT device participating in the CPS-IoT integrated transportation system, leveraging the power of ECC.
-
The ECC algorithm computes a public key and a corresponding private key unique to each device.
-
The public key is intended for distribution to other devices, while the private key remains securely stored on the respective IoT device.
-
Generation of these key pairs lays the foundation for secure communication channels and data encryption using ECC.
Distribute keys
-
Once the key pairs are generated, the public keys are distributed to other devices within the CPS-IoT system.
-
Distribution of public keys enables secure communication and data exchange between devices.
-
Each device stores the public keys of other devices with which it needs to communicate securely.
-
This step ensures that all devices within the CPS-IoT system possess the necessary cryptographic keys to establish secure channels for data transmission.
Through the Key Generation Phase, the cryptographic keys required for establishing secure communication channels and protecting data integrity are created and distributed among the IoT devices, laying the groundwork for subsequent phases of the framework.
Data encryption phase
The Data Encryption Phase is a critical stage where transportation data is safeguarded against unauthorized access or tampering through the application of ECC. This phase encompasses the following detailed steps:
Encrypt transportation data
-
During this step, transportation data packets are encrypted using the recipient’s public key, which is derived from ECC.
-
Each IoT device encrypts the transportation data packets intended for transmission using the public key of the recipient device.
-
ECC encryption ensures that the data is transformed into an unintelligible form that can only be decrypted by the recipient possessing the corresponding private key.
-
This cryptographic process ensures the confidentiality and integrity of the data during transit, mitigating the risk of data interception or tampering.
Ensure confidentiality
-
The primary objective of data encryption using ECC is to ensure the confidentiality of sensitive transportation data.
-
By encrypting the data packets with the recipient’s public key, unauthorized parties are prevented from deciphering the contents of the transmitted data.
-
ECC encryption provides a robust cryptographic mechanism for protecting the confidentiality of transportation data, even in the event of unauthorized access to the transmitted packets.
-
This step plays a crucial role in safeguarding the privacy of transportation data and maintaining the integrity of CPS-IoT integrated transportation systems.
Through the Data Encryption Phase, transportation data is transformed into a secure and unintelligible format using ECC encryption, ensuring confidentiality and integrity throughout the data transmission process within CPS-IoT integrated transportation systems.
Secure transmission phase
The Secure Transmission Phase focuses solely on ensuring the secure and reliable delivery of encrypted data packets within CPS-IoT integrated transportation systems. This phase comprises the following detailed steps:
Transmit encrypted data
-
Encrypted data packets, generated during the Data Encryption Phase, are transmitted securely over the network or storage medium to their designated recipients.
-
Each IoT device initiates the transmission of encrypted data packets to their intended recipients, establishing secure communication channels within the transportation system.
-
The encrypted data packets contain sensitive transportation information that has been safeguarded using ECC encryption, guaranteeing confidentiality and integrity during transit.
Implement TLS38 protocol for securing communication
-
To bolster the security of data transmission, the Transport Layer Security (TLS) protocol is exclusively implemented.
-
TLS establishes encrypted communication channels between transmitting and receiving devices, effectively thwarting eavesdropping or data interception by unauthorized entities.
-
The TLS protocol employs cryptographic techniques, including encryption, authentication, and integrity verification, to fortify the confidentiality and integrity of transmitted data.
-
By exclusively employing the TLS protocol, the Secure Transmission Phase ensures that encrypted data packets are transmitted over trusted and secure channels, thereby safeguarding transportation data from external threats.
Secure data exchange is the cornerstone of successful Intelligent Transportation Systems (ITS) in smart cities. Transport Layer Security (TLS)38 emerges as a robust solution for guaranteeing data confidentiality and integrity. TLS utilizes encryption to safeguard data in transit, preventing unauthorized access and manipulation. This protects sensitive information like traffic flow data, vehicle location, and sensor readings exchanged within the ITS ecosystem. Additionally, TLS verifies communicating parties through authentication mechanisms, mitigating spoofing attacks and ensuring data originates from legitimate sources. By fostering trust and data security, TLS facilitates seamless communication within the ITS network. While TLS offers a strong foundation, other secure transmission protocols exist. Datagram Transport Layer Security (DTLS)38 is optimized for real-time communication in resource-constrained environments, making it suitable for ITS applications with stringent latency requirements. However, compared to TLS, DTLS might offer slightly lower security due to its smaller key size. Secure Sockets Layer (SSL), while a predecessor to TLS, is still used in some legacy systems. However, its vulnerabilities make it less secure than TLS for contemporary ITS implementations. Ultimately, the choice of protocol depends on specific needs. TLS offers a strong balance between security and efficiency for most ITS applications, whereas DTLS can be considered for scenarios demanding ultra-low latency communication. Through the Secure Transmission Phase, encrypted data packets are securely transmitted over the network using the established TLS protocol. This phase guarantees the confidentiality, integrity, and reliability of data transmission within CPS-IoT integrated transportation systems, thereby augmenting the overall security and privacy of the system.
Data decryption phase
The Data Decryption Phase is a crucial step in the process of receiving and accessing encrypted data within CPS-IoT integrated transportation systems. This phase involves the following detailed steps:
Decrypt received data
-
Upon receiving encrypted data packets, the recipient IoT device utilizes its private key associated with the ECC public key used for encryption to decrypt the received data.
-
The recipient device employs its private key, which corresponds to the public key of the sender device used during the encryption process, to decipher the encrypted data packets.
-
Through the ECC decryption algorithm, the encrypted data is transformed back into its original plaintext form, allowing the recipient to access the transportation information contained within.
Ensure data integrity
-
Following decryption, the integrity of the received data is verified to ensure that it has not been tampered with or altered during transmission.
-
Various integrity verification techniques, such as cryptographic hashing or message authentication codes (MACs), may be employed to validate the authenticity and integrity of the decrypted data.
-
By comparing checksums or MAC values computed before and after decryption, the recipient device can confirm that the decrypted data remains unchanged and has not been subject to unauthorized modifications.
-
Ensuring data integrity is essential for maintaining the trustworthiness and reliability of transportation data within CPS-IoT integrated systems, preventing potential security breaches or data manipulation attempts.
Within CPS-IoT integrated transportation systems, secure data exchange is crucial. The proposed framework prioritizes data security throughout its lifecycle. The Data Decryption Phase utilizes ECC private keys to securely decrypt information received by IoT devices, ensuring data integrity and authenticity. This focus on secure communication, often achieved through protocols like Transport Layer Security (TLS), lays the foundation for informed decision-making and a sustainable circular economy. While detailed data analysis is beyond this study’s scope, the potential applications are significant. Extracted insights on traffic patterns can inform congestion pricing strategies, leading to reduced fuel consumption and emissions. Similarly, data on vehicle health and location can be leveraged to optimize maintenance schedules and identify opportunities for material reuse and recycling. These data-driven approaches are fundamental for promoting a circular economy within transportation. The delineated phases establish a robust mechanism for secure and privacy-preserving data exchange, enhancing the reliability and trustworthiness of smart city infrastructure. Key processes – key generation, encryption, transmission, decryption, and data processing – work in concert to safeguard sensitive information. Cryptographic techniques like ECC and stringent security protocols ensure data confidentiality and protection from unauthorized access. This approach fosters trust in smart city transportation systems, encouraging broader adoption of innovative technologies for sustainable urban mobility management.
Finally, the following presented pseudocode encapsulates the foundational architecture of the proposed framework, serving as a comprehensive illustration of the privacy-preserving communication in CPS-IoT integrated transportation for smart cities using ECC. Algorithm 1 presents the pseudo code of the proposed framework.

Algorithm 1: Proposed framework’s pseudo code

The provided pseudocode utilizes ECC to enhance data privacy in CPS-IoT integrated transportation systems for smart cities. It initializes ECC parameters and defines key generation, encryption, decryption, secure transmission, and data processing functions. Public–private key pairs are generated for each IoT device, and transportation data is simulated. The data is then encrypted using the recipient’s public key and securely transmitted using TLS38. Within the system, data decryption is a crucial step. Received data, encrypted for security, is decrypted using the device’s private key. While this study focuses on secure transmission, subsequent phases involve data processing for transportation analytics. This processing goes beyond the scope of this work. This pseudocode demonstrates the sequential steps involved in securing and analyzing transportation data within a CPS-IoT environment using ECC, thereby contributing to the privacy and security of smart city infrastructure.
Results and discussion
To provide sample execution results for the given pseudocode, we’ll simulate the behavior of the functions by displaying messages indicating the steps being executed and the data being processed. In this study, a comprehensive dataset comprising attributes relevant to the proposed system is generated using Python for a hypothetical set of 10 IoT devices. This dataset encompasses parameters vital for effective operation, including Traffic Management Parameters such as Traffic flow, Travel time, and Parking availability, as well as Vehicle Monitoring Parameters, which encompass Vehicle health, Vehicle location, and Vehicle occupancy. Additionally, Safety Parameters such as Air quality, Noise pollution, and Incident detection are included. These attributes are exemplified in Table 1, providing detailed information pertaining to each device within the system.
Table 1 presents assumed transportation data for 10 devices within the system, each characterized by distinct attributes across three categories: Traffic Management Parameters, Vehicle Monitoring Parameters, and Safety Parameters. The Traffic Management Parameters include Traffic flow, Travel time, and Parking availability, which provide insights into the current traffic conditions and parking availability at various locations. For instance, Device 2 exhibits heavy traffic flow, requiring 45 min of travel time, and indicating full parking availability. Moving to the Vehicle Monitoring Parameters, these attributes offer details on the health, location, and occupancy status of vehicles. For example, Device 5 demonstrates fair vehicle health, with all five seats occupied, and coordinates indicating its location in a specific geographical area. Furthermore, the Safety Parameters encompass Air quality, Noise pollution, and Incident detection, shedding light on environmental and safety conditions. Notably, Device 8 indicates poor air quality and high noise pollution levels, likely due to an accident occurring in its vicinity. Overall, the information presented in Table 1 serves as a comprehensive overview of the transportation data captured by the IoT devices, facilitating informed decision-making and enabling effective management of transportation systems in smart cities.
The Key Generation Phase is crucial for establishing secure communication in CPS-IoT transportation. Public–private key pairs are generated for each IoT device using ECC. Public keys enable trust and encrypted transmission, while private keys ensure data decryption on designated devices. The generation of these intricate key pairs serves as the cornerstone for erecting impregnable bastions of secure communication channels and data encryption within the CPS-IoT integrated transportation framework. The utilization of ECC engenders an environment characterized by fortified data security, thereby fostering the seamless exchange of sensitive information while safeguarding against potential security breaches and vulnerabilities. Table 2 provides a comprehensive overview of the public and private keys assigned to each device.
Table 2 delineates the allocation of public and private keys to individual devices within the CPS-IoT integrated transportation framework, thereby facilitating a secure milieu for communication and data interchange. These cryptographic keys assume pivotal roles in upholding the confidentiality and integrity of information traversing among IoT devices and infrastructure components. During the system’s inception phase, cryptographic algorithms are leveraged to generate public and private key pairs for each device. These keys, imbued with uniqueness, assume dual roles as authenticators and encryptors. Within the transportation domain, the public key serves as a digital lock, encasing data, while its corresponding private counterpart assumes the mantle of unlocking, thereby decrypting the encapsulated information. For instance, Device D1 is entrusted with a public key denoted by “3a91de7d925c2c5ff5625d2e49e7a1a3” and a private key represented by "efb0e6c36e3a5c5d43efad0c5b24b3fc." The symbiotic relationship between these keys, forged through mathematical linkage, mandates that data encrypted with the public key can solely be deciphered utilizing its private counterpart. This mechanism fortifies the sanctity of data, ensconcing it within a cocoon of security and privacy. The meticulous generation and custodianship of each key pair are instrumental in forestalling unauthorized access and fortifying defenses against potential security breaches. Furthermore, the intricate complexity and stochasticity inherent in these keys bolster their resilience against cryptographic assaults, thereby engendering robust security protocols for the transportation ecosystem. Throughout the operational epoch, these keys serve as enablers for secure communication and seamless data transmission among devices, thereby facilitating real-time monitoring, analysis, and decision-making endeavors. Notably, Device D8, armed with its public key denoted as "7f8a9b0c1d2e3f4a5b6c7d8e9a0b1c2," can securely dispatch data to fellow devices, ensconcing sensitive information, such as incident detection or vehicle health status, within a bastion of confidentiality and tamper resistance. Moreover, the idiosyncratic coupling of public and private keys to individual devices affords traceability and accountability in data transactions. This delineation ensures that any data exchanged within the system can be traced back to its originator via the associated public key, thereby fostering transparency and integrity in data management paradigms. The Data Encryption Phase is crucial for securing transportation data in CPS-IoT integrated systems. Utilizing ECC, transportation data packets are encrypted using the recipient’s public key, ensuring confidentiality and integrity during transit. This phase ensures that sensitive information remains inaccessible to unauthorized parties, mitigating the risk of data interception or tampering. Secure communication protocols such as Transport Layer Security (TLS)38 further enhance data transmission security. The Secure Transmission Phase complements encryption by ensuring the reliable delivery of encrypted data packets over secure channels, enhancing overall system security and privacy.
Table 3 provides the encrypted data for each device within the CPS-IoT transportation system. These encrypted data packets, generated using ECC encryption during the Data Encryption Phase, contain confidential transportation information. Each device’s encrypted data ensures that sensitive data remains protected during transmission, maintaining the system’s integrity and confidentiality. Through the encryption and transmission phases, the system establishes secure communication channels, safeguarding transportation data from unauthorized access and external threats.
Table 3 provided presents the encrypted data for each device within the CPS-IoT integrated transportation system. These encrypted data strings are generated during the Data Encryption Phase, where transportation data is safeguarded against unauthorized access or tampering using ECC. Let’s delve into a detailed discussion regarding the significance and implications of this encrypted data in ensuring the security and privacy of the transportation system. Each entry in the table represents the encrypted data corresponding to a specific IoT device within the transportation system. For instance, Device D1 has an encrypted data string of "3e9b7e3d7a2c5f9b7d5e2f1a8b4c2d6," while Device D2’s encrypted data is "1f8e6b9d3f6a7e5c1b9d2e8f6a3c5d7," and so forth. These encrypted data strings serve as the encrypted form of transportation data packets, ensuring confidentiality and integrity during transmission over the network or storage medium. The utilization of ECC for data encryption ensures robust security measures, as ECC offers strong cryptographic properties suitable for securing sensitive information. Each encrypted data string is generated by encrypting transportation data packets using the recipient device’s public key, derived from ECC. This encryption process transforms the transportation data into an unintelligible form, ensuring that only authorized recipients possessing the corresponding private key can decrypt and access the original information. By encrypting transportation data, the system mitigates the risk of data interception, tampering, or unauthorized access, thereby safeguarding sensitive information such as traffic flow, vehicle health, and incident detection. The encrypted data strings act as a protective layer, ensuring that even if intercepted, the data remains incomprehensible and inaccessible to unauthorized parties.
Moreover, the encrypted data strings reinforce the system’s adherence to privacy and data protection regulations, ensuring compliance with legal and regulatory requirements. By adopting strong encryption mechanisms like ECC, the transportation system demonstrates a commitment to preserving user privacy and maintaining data confidentiality. The Data Decryption Phase in CPS-IoT transportation systems is vital for securely accessing encrypted data as mentioned before. It involves recipient IoT devices using private keys linked to ECC public keys to decrypt received data. After decryption, data integrity is verified using techniques like cryptographic hashing or MACs. This phase ensures secure data exchange, enhancing overall privacy and security in transportation systems. The decrypted output for each device within the CPS-IoT integrated transportation system reveals critical insights into the current state and conditions of the transportation environment. Device D1, for instance, indicates moderate traffic flow with a travel time of 30 min and limited parking availability. Vehicle health is assessed as good, with two out of five seats occupied, suggesting moderate vehicle occupancy. Air quality is moderate, while noise pollution remains low, indicating relatively favorable environmental conditions. Moreover, no incidents are detected, reflecting a stable transportation scenario. Device D2, on the other hand, reports heavy traffic flow with a longer travel time of 45 min and full parking availability. The vehicle’s health status is fair, with four out of five seats occupied, pointing to moderate vehicle occupancy. However, poor air quality and moderate noise pollution levels suggest suboptimal environmental conditions. The occurrence of a road closure indicates potential disruptions to traffic flow, necessitating appropriate mitigation measures. Similarly, Device D3 records light traffic flow, a shorter travel time of 20 min, and limited parking availability. The vehicle is in excellent health, with minimal occupancy of one out of five seats. Good air quality and low noise pollution levels indicate favorable environmental conditions. However, an accident is reported, underscoring the importance of timely intervention to address safety concerns and restore normal traffic operations. Devices D4, D6, D7, and D9 exhibit variations in traffic flow, travel time, parking availability, and environmental conditions, with no incidents detected. Conversely, Devices D5, D8, and D10 report heavy traffic flow, longer travel times, full parking availability, and adverse environmental factors such as poor air quality and high noise pollution levels. Incidents such as road closures and accidents further exacerbate the transportation challenges faced by these devices, highlighting the need for proactive measures to mitigate disruptions and ensure the safety and efficiency of the transportation system. Overall, the decrypted data provides valuable insights into the operational status and prevailing conditions of each device within the CPS-IoT integrated transportation system. By analyzing this information, stakeholders can make informed decisions, optimize transportation operations, and implement targeted interventions to enhance the overall efficiency, safety, and sustainability of the transportation infrastructure.
Evaluation and validation
This section presents a comprehensive comparative analysis, encompassing 15 evaluation points, aimed at validating the proposed method by juxtaposing it with a hypothetically assumed framework grounded in Differential Privacy (DP), as delineated in the Appendix. The objective is to meticulously evaluate the efficacy, efficiency, and overarching performance of the proposed framework vis-à-vis the DP-based alternative. By adopting this methodological approach, critical insights are gleaned regarding the inherent strengths, weaknesses, and prospective advantages of the proposed method, thus illuminating its feasibility and aptness for the intended applications delineated within the study.
Comparative analysis
To validate the effectiveness of the proposed framework based on ECC for secure and privacy-preserving communication in CPS-IoT integrated transportation systems, a comprehensive comparative evaluation was conducted against a differential privacy (DP)-based framework as detailed in the Appendix. This assessment covered fifteen evaluation points and focused on core dimensions such as computational efficiency, scalability, privacy preservation, regulatory compliance, and practical applicability in smart city environments. The analysis, summarized in Table 4, reveals that ECC offers superior cryptographic security, lower computational overhead, better data integrity, and enhanced scalability, especially when dealing with large datasets. It preserves data utility by avoiding distortion and enables fine-grained control over data access through encryption. ECC is also more resource-efficient and easier to implement without requiring deep technical expertise, making it practical for wide-scale deployment. Conversely, DP provides quantifiable privacy guarantees and may be preferable in specific applications where absolute anonymity is paramount. However, DP’s dependence on complex privacy budget management and its potential to degrade data utility are notable drawbacks. Overall, ECC achieved an 80% effectiveness score compared to DP’s 20%, demonstrating its robustness in securing CPS-IoT systems for smart transportation.
Beyond technical performance, the proposed framework offers significant practical and strategic advantages. From a system design perspective, it enhances data security by encrypting sensitive information such as vehicular location and user identity, thereby protecting against unauthorized access and cyber threats. It also strengthens privacy safeguards, increases system resilience against cyberattacks, and supports sustainability through improved traffic optimization and emission reduction. Furthermore, ECC facilitates secure data-driven decision-making in areas such as infrastructure development, public transportation planning, and electric vehicle management, all of which are crucial for promoting circular economy principles. Secure data sharing also enables effective tracking of resource consumption, optimization of EV charging patterns, and the promotion of material reuse and recycling. These benefits translate into actionable managerial implications: ECC’s robust security framework fosters user trust and broader adoption, enabling improved data collection, optimized resource allocation, and long-term strategic planning. Although initial investments in cryptographic infrastructure and key management are required, these costs are offset by the prevention of data breaches and the enablement of innovative practices like shared mobility and circular supply chains. However, some limitations persist. Key management remains a complex challenge in large, heterogeneous networks—compromise of even a single key can jeopardize system-wide security. Additionally, ECC, like all cryptographic methods, must evolve to counter emerging cyber threats. Ongoing monitoring, timely algorithm updates, and proactive cryptographic research are essential to ensure the framework’s continued effectiveness. Therefore, while ECC provides a solid foundation for secure, sustainable urban transportation, its long-term viability depends on adaptive maintenance and sustained innovation.
Conclusion
This study addresses the critical challenge of privacy-preserving communication within CPS-IoT integrated transportation systems for smart cities by proposing a novel approach leveraging ECC to enhance data security. In addition to ECC, we incorporate Transport Layer Security (TLS) as a secure data communication protocol, further fortifying our framework. The comprehensive analysis of privacy threats and vulnerabilities, coupled with the implementation details of ECC-based encryption and decryption mechanisms, underscores the effectiveness and feasibility of our approach. Our research extends beyond secure communication to foster a secure data environment, paving the way for a more sustainable and resilient transportation infrastructure within smart cities. The assumed transportation data presented for the 10 devices highlights the potential of this framework. Data encompassing traffic management parameters like traffic flow, travel time, and parking availability empower authorities to optimize traffic flow and improve efficiency. Vehicle monitoring parameters such as health, location, and occupancy can be used to optimize maintenance schedules and resource allocation. Most importantly, safety parameters like air quality, noise pollution, and incident detection enable authorities to identify and address potential hazards, promoting a safer urban environment. This secure data environment facilitates data-driven decision-making across various aspects of smart city transportation, promoting resource optimization, electric vehicle adoption, and a flourishing circular economy within the transportation sector. A comprehensive comparative analysis evaluated the proposed ECC framework against a hypothetical Differential Privacy (DP) approach. This analysis, detailed in the Appendix, revealed that ECC outperforms DP in most aspects. ECC demonstrates lower computational overhead, better scalability, and easier implementation, while preserving data utility and offering robust cryptographic security. However, DP provides quantifiable privacy guarantees which may be advantageous in specific scenarios. Future research directions can explore the integration of this secure communication framework with other smart city initiatives, such as interfacing with energy grids for demand-responsive charging of electric vehicles or integrating with resources management systems to optimize collection routes based on real-time data. Additionally, further research could investigate the implementation of advanced privacy-preserving techniques alongside ECC to ensure the highest level of user privacy while maintaining the benefits of data-driven decision-making in smart city transportation. In conclusion, this research paves the way for a secure and sustainable future for smart city transportation. By ensuring data security through ECC, and TLS, we unlock the full potential of CPS-IoT integration, enabling data-driven decisions that promote resource optimization, electric vehicle adoption, and a flourishing circular economy. The journey towards a sustainable and resilient urban environment requires ongoing research and development, and this work presents a significant step forward in that direction.
Data availability
The data that support the findings of this study are available from the corresponding author upon reasonable request. Access to the data is restricted and will be granted to qualified researchers upon request for academic and non-commercial purposes.
References
Chui, K. T. et al. A survey of internet of things and cyber-physical systems: Standards, algorithms, applications, security, challenges, and future directions. Information 14(7), 388 (2023).
Ammi, M., Adedugbe, O., Alharby, F. M. & Benkhelifa, E. Taxonomical challenges for cyber incident response threat intelligence: A review. Int. J. Comput. Appl. 12, 1–14 (2022).
Nguyen, G. N. et al. Secure blockchain enabled Cyber–physical systems in healthcare using deep belief network with ResNet model. J. Parallel Distrib. Comput. 153, 150–160 (2021).
Gaurav, A., Psannis, K. & Perakovi´c, D. Security of cloud-based medical internet of things (miots): A survey. Int. J. Softw. Sci. Comput. Intell. 14, 1–16 (2022).
Singh, A. & Gupta, B. B. Distributed denial-of-service (DDoS) attacks and defense mechanisms in various web-enabled computing platforms: Issues, challenges, and future research directions. Int. J. Semant. Web Inf. Syst. 18, 1–43 (2022).
Pivoto, D. G. et al. Cyber-physical systems architectures for industrial internet of things applications in Industry 4.0: A literature review. J. Manuf. Syst. 58, 176–192 (2021).
Franco, J., Aris, A., Canberk, B. & Uluagac, A. S. A survey of honeypots and honeynets for internet of things, industrial internet of things, and cyber-physical systems. IEEE Commun. Surv. Tutor. 23, 2351–2383 (2021).
Sharma, R., Sharma, T. P. & Sharma, A. K. Detecting and preventing misbehaving intruders in the internet of vehicles. Int. J. Comput. Appl. 12, 1–21 (2022).
Liu, Y., Yang, X., Wen, W. & Xia, M. Smarter grid in the 5G Era: A framework integrating power internet of things with a cyber physical system. Front. Commun. Netw. 2, 689590 (2021).
Rani, S. et al. Security and privacy challenges in the deployment of cyber-physical systems in smart city applications: State-of-art work. Mater. Today Proc. 62, 4671–4676 (2022).
Barroso, S., Bustos, P. & Núñez, P. Towards a cyber-physical system for sustainable and smart building: A use case for optimizing water consumption on a SmartCampus. J. Ambient Intell. Humaniz. Comput. 14, 6379–6399 (2023).
Gaggero, G.B.; Rossi, M.; Girdinio, P.; Marchese, M. Cybersecurity Issues in Communication-Based Electrical Protections. In Proceedings of the 2022 International Conference on Electrical, Computer and Energy Technologies, Prague, Czech Republic, 20–22 July 2022.
Gaggero, G. B., Girdinio, P. & Marchese, M. Advancements and research trends in microgrids cybersecurity. Appl. Sci. 11, 7363 (2021).
Khan, F., Kumar, R. L., Kadry, S., Nam, Y. & Meqdad, M. N. Cyber physical systems: A smart city perspective. IJECE 11(4), 3609 (2021).
Kwon, Y., Lee, S., King, R., Lim, J. I. & Kim, H. K. Behavior analysis and anomaly detection for a digital substation on cyber-physical system. Electronics 8, 326 (2019).
Hands, J. & Coughlin, T. New IEEE Media Sanitization Specification Enables Circular Economy for Storage. Computer 56, 111–116 (2023).
Vipin Kumar, Rifaqat Ali, Pawan Kumar Sharma. A Secure Multi-factor Authentication Framework for IoT-Environment Using Cloud Computing. Springer Nature Link, Conference paper, First Online: 24 July 2024 pp 477–494
Kumar, V., Ali, R. & Sharma, P. K. IoV-6G+: A secure blockchain-based data collection and sharing framework for Internet of vehicles in 6G-assisted environment. Vehic. Commun. 47, 100783 (2024).
Hinkel, G. The TTC 2017 Outage System Case for Incremental Model Views. In Proceedings of the 10th Transformation Tool Contest, Marburg, Germany, 21 July 2017.
Nweke, L. O., Weldehawaryat, G. K. & Wolthusen, S. D. Threat modelling of cyber–physical systems using an applied _-calculus. Int. J. Crit. Infrastruct. Prot. 35, 100466 (2021).
Balijepalli, V.M.; Sielker, F.; Karmakar, G. Evolution of power system cim to digital twins-a comprehensive review and analysis. In Proceedings of the 2021 IEEE PES Innovative Smart Grid Technologies Europe, Espoo, Finland, 18–21 October 2021.
Georgiadou, A., Mouzakitis, S. & Askounis, D. Working from home during COVID-19 crisis: A cyber security culture assessment survey. Secur. J. 35, 486–505 (2022).
Chetioui, K., Bah, B., Alami, A. O. & Bahnasse, A. Overview of social engineering attacks on social networks. Procedia Comput. Sci. 198, 656–661 (2022).
Liao, B., Ali, Y., Nazir, S., He, L. & Khan, H. U. Security analysis of IoT devices by using mobile computing: A systematic literature review. IEEE Access 8, 120331–120350 (2020).
Bovenzi, G. et al. Network anomaly detection methods in IoT environments via deep learning: A Fair comparison of performance and robustness. Comput. Secur. 128, 103167 (2023).
Wang, Y., Kong, L., Lin, S. & He, L. Detecting engine anomalies using batteries. IEEE Trans. Mob. Comput. 22, 2069–2083 (2023).
Du, M. Application of information communication network security management and control based on big data technology. Int. J. Commun. Syst. 35, e4643 (2022).
Sheikh, A. Hacking Wireless Networks. In Certified Ethical Hacker (CEH) Preparation Guide: Lesson-Based Review of Ethical Hacking and Penetration Testing; Apress: Berkeley, CA, USA, 2021.
Tundis, A.; Mazurczyk,W.; Mühlhäuser, M. A review of network vulnerabilities scanning tools: Types, capabilities and functioning. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018.
Garba, F.A.; Kunya, K.I.; Ibrahim, S.A.; Isa, A.B.; Muhammad, K.M.; Wali, N.N. Evaluating the state of the art antivirus evasion tools on windows and android platform. In Proceedings of the 2019 2nd International Conference of the IEEE Nigeria Computer Chapter, Zaria, Nigeria, 14–17 October 2019.
Gupta, B. B., Li, K. C., Leung, V. C., Psannis, K. E. & Yamaguchi, S. Blockchain-assisted secure fine-grained searchable encryption for a cloud-based healthcare cyber-physical system. IEEE CAA J. Autom. Sin. 8, 1877–1890 (2021).
Anwar, R. W., Abdullah, T. & Pastore, F. Firewall best practices for securing smart healthcare environment: A review. Appl. Sci. 11, 9183 (2021).
Y. Yan, “The Overview of Elliptic Curve Cryptography (ECC),” J. Phys.: Conf. Ser., vol. 2386, no. 1, p. 012019, Dec. 2022.
Ye, N., Zhu, Y., Wang, R., Malekian, R. & Qiao-min, L. An efficient authentication and access control scheme for perception layer of internet of things. Appl. Math. Inf. Sci. 8(4), 1617–1624 (2014).
Verri Lucca, A. et al. A review of techniques for implementing elliptic curve point multiplication on hardware. JSAN 10(1), 3 (2020).
Gao Wei, Luo Yixuan, Li Jiakun, Wu Haixia <High Performance Hardware Implementation of Elliptic Curve Cryptography Point Multiplication over GF(p)>, 2021–09, Beijing Institute of Technology, Transaction of Beijing Institute of Technology.
Wei Wei, Chen Jiazhe, Li Dan, Zhang Baofeng <Research on the Bit Security of Elliptic Curve Diffie-Hellman>, 2020–04–24, Journal of Electronics & Information Technology.
Y. Sheffer, P. Saint-Andre, and T. Fossati, “RFC 9325: Recommendations for Secure Use of Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS)”.
Nir, Y., Josefsson, S. & Pegourie-Gonnard, M. Elliptic curve cryptography (ECC) cipher suites for transport layer security (TLS) versions 12 and earlier. RFC https://doi.org/10.17487/RFC8422 (2018).
S. Gopi, Y. T. Lee, and L. Wutschitz, “Numerical Composition of Differential Privacy,” JPC 14 1, Feb. 2024.
M. Yang, L. Lyu, J. Zhao, T. Zhu, and K.-Y. Lam, “Local Differential Privacy and Its Applications: A Comprehensive Survey.” arXiv, Aug. 09, 2020. Accessed: May 14, 2024.
Husnoo, M. A., Anwar, A., Chakrabortty, R. K., Doss, R. & Ryan, M. J. Differential privacy for IoT-enabled critical infrastructure: A comprehensive survey. IEEE Access 9, 153276–153304 (2021).
Acknowledgements
The authors express their gratitude to the Research Management Center (RMC), Multimedia University for their valuable support in this research.
Author information
Authors and Affiliations
Contributions
Mazin Abed Mohammed: Conceptualization, Methodology, Formal analysis, Investigation, Data duration, Writing—original draft, Visualization. Zainab Khalid Mohammed, Abdullah Lakhan: Conceptualization, Methodology, Formal analysis, Investigation Writing—review & editing, Supervision. Karrar Hameed Abdulkareem, Hussein Waheed Aziz, Muhammet Deveci: Conceptualization, Formal analysis, Data curation, Project administration. Radek Martinek: Software, Writing—review & editing, Supervision, Project administration, Funding acquisition. Mohammed Al-Andoli: Writing—review & editing, Visualization, Funding acquisition.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix

Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Mohammed, Z.K., Mohammed, M.A., Ghani, M.K.A. et al. Privacy-preserving communication in smart city transportation using elliptic curve cryptography. Sci Rep 15, 34342 (2025). https://doi.org/10.1038/s41598-025-16810-y
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-16810-y