Abstract
This paper presents a new hybrid method for concealing images within a cover image using Integer Wavelet Transform and Singular Value Decomposition to enhance the imperceptibility and robustness of hidden images within a cover image. A custom graphical user interface has been developed to aid in evaluating performance metrics, allowing users to assess how various noise conditions affect stego images interactively. The technique shows minimal distortion with a Mean Squared Error of 9.6698 and a Bit Error Rate of 0.7205. Both the Structural Similarity Index Measure and Normalised Cross-Correlation are close to 1 while achieving a Peak Signal-to-Noise Ratio of 29.5665 dB. Our results surpass current methods, particularly when gauging resilience under noise such as Gaussian, speckle, and salt and pepper, proving that this proposed technique effectively maintains high image quality and steganographic security. The results establish the method’s potential for secure image transmission in applications such as defense communications, medical image confidentiality, forensic authentication, and digital rights protection, while providing a reproducible platform for future steganographic research.
Similar content being viewed by others
Introduction
Data transmission has become faster and easier with the development of 5G communication technology1. However, on the flip side, unauthorised users can easily access, modify, and erase the transmitted data over the wireless network. Thus, security is essential for the data that is being transmitted. Two primary methods utilised to uphold data confidentiality are data encryption and concealment. Encryption converts plain text to ciphertext using a specific algorithm and key to protect plain text from unauthorised access or interception. It secures the context of the message by making it unreadable without the decryption key. On the other hand, data hiding is mainly concerned with hiding secret data with the help of a carrier in an invisible manner2.
Steganography and watermarking are the two main techniques employed in data hiding. The present work deals with Steganography3. It conceals the existence of a message by using another medium. Image steganography has emerged as a widely adopted approach for concealing data due to its exploitation of the human visual system’s limited perceptual capabilities. Additionally, the high redundancy of bits in images facilitates the concealment of more secret data4. The original image is the carrier; the hidden data is embedded into the carrier using various embedding techniques, resulting in a stego image. The stego and cover images look almost identical; hence, an unauthorised person cannot distinguish the cover and stego images.
The steganographic techniques can be done in different forms, such as the spatial domain and transform domain, as explained by Hussain, Wahab, Idris, Ho, and Jung5. Dalal and Juneja explained the various types of steganographic techniques, real-life applications, and current trends in Steganography6. Spatial, transform, and adaptive steganographic methods proposed by multiple authors are compared by Kaur, Singh, Kaur and Lee7. Trivedi, Sharma, and Yadav discuss various image steganography techniques implemented in the spatial domain. The prevalent method for embedding data in digital images involves modifying the pixel values of the cover image. Various straightforward techniques leverage bit-wise strategies to achieve bit insertion in images8. Alhomoud also compared the various steganographic techniques in the spatial domain9. Several widely-used spatial domain steganographic methods encompass techniques such as Pixel Value Differencing (PVD) Steganography, Least Significant Bit (LSB) steganography, Pixel Indicator technique for colour images, Specific Regions of Interest (ROI), Pixel value modification, Edge region-based steganography, Adaptive Pixel Pair Matching and Chaos-based edge adaptive image steganography10.
Maji, Mandal and Sen vary the higher-order pixel intensity bits to encrypt the secret message using XOR encoding in the spatial domain. Later, Least Significant Bit (LSB) embedding is also done block-wise11. Abdulla proposed a steganographic technique to produce stego images with less distortion and more embedding efficiency12. Spatial domain steganography was performed by Liji, Indiradevi and Babu, in which the lifting approach based on integer-to-integer wavelet transform is used to hide the information in the LSB. Further, the information was scrambled inside the ECG signal with the help of a shared key and a scrambled matrix13. Some techniques focused on utilising edges for embedding the secret message. One such algorithm was proposed by Islam, Modi and Gupta14, where the data size is directly proportional to the size of the edges. This technique increased the capacity of the data that was being embedded and considered the significance of watermarking payload estimation in determining the embedding intensity, image size, roughness, visual sensitivity, and other factors. Jia-Fa, Zhang Ru, Xin-Xin, Yi-Xian, and Lin-Na15 proposed and validated a method for estimating watermarking payload. Selecting a cover image is one of the first and most essential steps in Steganography. Abed, Al-Roomi, and Al-Shayeji introduced the Most Suitable Cover Image (MSCI) framework, which automatically selects the cover image for the given secret image16.
Yadahalli, Rege, and Sonkusare17 proposed Steganography techniques utilising the Least Significant Bit (LSB) method and the Discrete Wavelet Transform (DWT) method, which concluded that the transform domain is better than the spatial domain. A novel steganography technique based on the color palate transformation in color space has been introduced by Margalikas and Ramanauskaitė18, which resulted in higher user perception. Gutub and Shaarani’s study included a comparative analysis of the least significant bit of steganographic algorithms and discrete wavelet transforms. Capacity is one of the essential traits of the steganographic technique. The methods will be less reliable when they transmit only a tiny amount of data using the carrier. The evaluation focused on assessing the capacity and efficiency for concealing multiple images within a single cover image in the frequency domain19. Wang, Yang, Zhu, Song, Liu and Lian have proposed a JPEG-based image steganography20 based on the Markov model of co-frequency sub-image. Miri and Faez have introduced image Steganography utilising the Integer Wavelet Transform, wherein the cover image is converted into the frequency domain, and edge coefficients are categorised according to their Most Significant Bits (MSBs). This method did not change the MSB so that the receiver could retrieve the data without errors21. The method proposed by Murugan and Subramaniyam22 was based on Discrete Wavelet Transform (DWT). Wavelet Space analyses image characters well, making it much more immune to geometric attacks.
Eyssa, Abdelsamie, and Abdelnaiem introduced an approach specifically for colour images over wireless channels, predominantly relying on Discrete Cosine and Discrete Wavelet transforms. This method involves concealing three colour images within a single-colour image, thereby enhancing the concealment capacity23. Additionally, Singh, Rajiv Singh, and Siddiqui24 proposed a steganographic method using Integer Wavelet Transform (IWT) to decompose the cover image, embedding in the LL band due to its energy compaction. Singular Value Decomposition (SVD) is applied to LL-band coefficients, while the secret image is first chaotically scrambled for enhanced security. This combination aims to maintain image quality and improve resistance to attacks. Gunjal and Mali25 introduced a watermarking technique that leverages Discrete Wavelet Transform (DWT) and Singular Value Decomposition (SVD) to enhance efficiency and generate highly effective images.
Liu and Lee26 proposed a unique steganography technique based on pixel value ordering (PVO). This improved the capacity. Zebbiche, Khelifi and Bouridane27 proposed an algorithm based on embedding the watermarks in the ridges of the fingerprint images using a transform domain, leading to high performance and resistance against cropping and segmentation attacks. Avcıbas, Kharrazi, Memon, and Sankur introduced a steganalysis method rooted in the observation that the bit planes’ correlation and binary texture attributes vary between stego and cover images28. Rossi, Garzia, and Cusani introduced a steganographic approach where the secret image is embedded in the Discrete Cosine Transform (DCT) domain, utilising the strength of modifiable coefficients and a novel block called discrepancy to identify appropriate areas for embedding29. Nashat and Mamdouh30 proposed a method where, instead of substituting the least significant bits (LSBs) of the cover image with secret data, certain LSBs of the cover image are inverted based on the hidden data for embedding. This approach significantly mitigates the impact of image quality degradation.
Recent advances in image processing offer useful insights for improving image steganography. For example, co-occurrence filters in the NSST domain help preserve edges and textures, which is key to hiding data without noticeable distortion31. Content-aware GANs can adaptively embed information by learning spatial and semantic features32, while models like TSJNet use semantic awareness to select optimal embedding areas, improving both invisibility and robustness33. These methods show promising directions for future steganographic techniques.
In recent years, the field of steganography has witnessed a significant increase in the adoption of deep learning techniques. These methods, which utilise architectures such as convolutional neural networks, generative adversarial networks, and attention mechanisms, have demonstrated advancements in embedding capacity, imperceptibility, and robustness. Consequently, DL-based approaches frequently surpass traditional transform-based methods, especially in tasks involving adaptive payload distribution and enhanced resistance to steganalysis. Nevertheless, DL techniques typically necessitate substantial training datasets, considerable computational power, and may present difficulties concerning interpretability and deployment within resource-limited settings. Although this research focuses on transform-based techniques due to their inherent simplicity, reduced resource requirements, and reproducibility, future research should prioritise integrating and comparing them with cutting-edge DL-based methodologies. Such an endeavour would foster a more thorough comprehension of the comparative advantages and disadvantages of traditional versus DL-driven approaches in practical scenarios.
Existing literature consistently demonstrates that transform-domain steganography techniques demonstrate superior imperceptibility and robustness relative to spatial-domain approaches. However, a critical review of contemporary research indicates that widely adopted methods—such as DWT–SVD, DWT–DCT, LWT–SVD, and standalone IWT schemes—often exhibit performance degradation when subjected to varied noise conditions under standardised testing parameters. Furthermore, the predominant practice of embedding secret data within low- or mid-frequency bands increases vulnerability to statistical detection and localised distortions. Another notable shortcoming is the limited exploration of integrating integer-based wavelet transforms, which preserve integer coefficients to enable lossless reconstruction, with coefficient-specific singular value embedding strategies. Equally, there exists a paucity of reproducible experimental platforms that facilitate systematic, multi-method comparative analysis.
To address these limitations, the key contributions of this research are as follows:
-
Introduction of a hybrid embedding framework that combines Integer Wavelet Transform (IWT) and Singular Value Decomposition (SVD) to enable lossless, coefficient-targeted data hiding.
-
Design of a selective corner-value modification approach within the singular value matrix, improving resilience to noise while maintaining high perceptual quality.
-
Execution of a detailed, side-by-side comparison with various transform-domain methods under uniform noise and testing conditions.
-
Development of an interactive MATLAB-based graphical interface that supports real-time embedding, extraction, and reproducibility of experiments.
The structure of this paper unfolds as follows: section “preliminaries” elucidates the overview of transform domain techniques for image steganography. Section “Proposed Methodology” provides a comprehensive exposition of the proposed algorithm’s procedures. Section “Experimental Setup” presents the outcomes, discourse, and a comparative analysis of performance vis-à-vis state-of-the-art methodologies. Lastly, section “results and discussion” summarises the paper’s notable discoveries and conclusions.
Preliminaries
Transform domain techniques
The transform domain techniques hide information in the coefficients of an image. Such techniques encompass various transforms like the Discrete Cosine Transform (DCT), Discrete Fourier Transform (DFT), Discrete Wavelet Transform (DWT), Integer Wavelet Transform (IWT), Combination of Transforms and Transform & Singular Value Decomposition (SVD).
Discrete cosine transform
Discrete cosine transform (DCT) is a mathematical tool for converting input signals, like images, from their spatial representation into the frequency domain. It expresses the input as a combination of weighted functions, providing insights into the frequency components within the data. Implementing the two-dimensional DCT involves applying one-dimensional transformations in horizontal (x) and vertical (y) directions. Upon application to an image, the DCT yields a weighted matrix, delineating the presence of each basis function in the original image. The matrix’s upper-left area contains the low frequencies, which have higher energies of the image signal, whereas the high-frequency components contain noise. The medium-frequency segment of the image is used to hide a message. This is done by dividing the image into eight-by-eight-pixel blocks and applying the DCT to each block. It is a faster and more precise algorithm.
Discrete fourier transform
The Discrete Fourier Transform is a technique in image processing that produces both real and imaginary components of an image signal while converting from the spatial domain to the frequency domain, unlike DCT, which only produces real components of the image. For this reason, it is less effective than other steganographic transforms, as data will be lost due to the elimination of the imaginary parts of the signal while forming a stego image.
Discrete wavelet transform
The Discrete Wavelet Transform breaks down the input signal into non-continuous wavelets, providing better temporal resolution than the Fourier transform. This improved resolution enhances the informativeness of DWT by effectively capturing a considerable amount of data in both frequency and time domains.
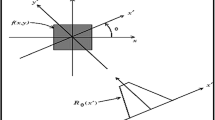
Upon performing a 1-level decomposition of the input image f(m, n) using DWT, we acquire both the approximation and three detailed transformation coefficients. Figure 1 illustrates the detail coefficients and approximation yielded by applying a 1-Level DWT to an image.
The discrete wavelet transform functions within the frequency domain, aiming to achieve multi-resolution decomposition for discerning frequency intricacies. In the initial stage of Discrete Wavelet Transform (DWT), the image is divided into four segments, i.e., LL1, LH1, HL1, and HH1, representing low, middle, and high frequencies. This division is achieved by applying horizontal and vertical down-sampling using low-pass and high-pass filters. The LL1sub-band obtained from the previous level serves as the input for further decomposition at subsequent levels. Further partitioning of the LL1sub-band results in four multi-resolution sub-bands, contributing to the production of coarser wavelet coefficients.
Lifting wavelet transform
The Lifting Wavelet Transform (LWT) offers a sophisticated method for hiding information within digital media, ensuring it remains undetected by plagiarism detectors and A.I. algorithms. The process begins by decomposing an image into different sub-bands through a sequence of lifting steps, which split the image data into high-pass and low-pass components.
Integer wavelet transform
The Integer Wavelet Transform is similar to LWT in producing the wavelet coefficients. It also follows the Predict, Split, and Update steps. It converts the image from the spatial domain into smaller wavelets. The advantage of IWT over LWT is that it ensures that the coefficients of wavelets formed are integers, which reduces data loss when rebuilding the image. For this same reason, IWT-based image steganography produces robust stego images.
Singular value decomposition
When the Singular Value Decomposition is used on a matrix representation of an image, it divides the image into three sub-arrays. Let us assume X is an image with P x K dimensions, where P denotes the number of rows and K represents the number of columns. The SVD decomposition yields three sub-arrays: A, B, and CT. The original image ‘X’ can be reconstructed using Eq. (3)
where A is a matrix of size P × P consisting of the orthogonal eigenvectors of XXT (A is an orthogonal matrix). CT denotes the transpose of K × K matrix containing the orthogonal eigenvectors of XTX (C is also an orthogonal matrix). B is a diagonal matrix with dimensions P x K, consisting of the square roots of the eigenvalues derived from singular values obtained from XTX.
Proposed methodology
The proposed steganographic technique uses a combination of Integer Wavelet Transform and Singular Value Decomposition for embedding and extracting secret images. This two-phase method ensures both secure embedding and accurate retrieval of the hidden image. This section provides detailed descriptions of both phases and block diagrams that clearly illustrate each step.
Preprocessing
Initially, the input images (cover and secret) are processed to match their dimensions and formats. If an image is in colour, it is converted to a grayscale image, as shown in Figs. 2 and 3 below for the cover images and secret image, respectively. The cover image is resized to 512 × 512 pixels, and the secret image is adjusted to 256 × 256 pixels to ensure compatibility with the embedding process. For the experimental evaluation, we utilised an image dataset sourced from an openly available repository, accessible at https://ccia.ugr.es/cvg/CG/base.htm.
Embedding process
-
1.
An Inverse Wavelet Transform is applied to the cover image, which produces four distinct sub-bands: LL1, LH1, HH1, and HL1. This step is essential for further dividing the image to embed the secret information.
-
2.
An additional IWT is applied to the previously obtained LL1 band, which further decomposes into four more sub-bands, namely, LL2, LH2, HL2, and HH2.
-
3.
Now, use the high-frequency band HH2 and apply Singular Value Decomposition, which further decomposes into Ai, Ei, and Ci.
-
4.
Next, we consider the secret image and divide the image into four equal parts and then reduce each part’s size by a factor of eight to reduce the area of embedding and then apply SVD to each part, which results in the formation of matrices Asi, Esi, Csi (where i = 1, 2, 3, 4).
-
5.
An embedding algorithm is used to insert these elements into the corners of the Ei matrix of the cover image. This process alters the corner values of Ei based on the following formula:
$${\text{New }}E_{i} \left( {{\text{corner}}} \right) \, = \, E_{i} \left( {{\text{corner}}} \right) \, + \, \alpha \, * \, E_{si}$$(4) -
6.
The HH2 sub-band is rebuilt using the formula:
$${\text{HH}}_{2} \left( {{\text{new}}} \right) \, = \, A_{i} *{\text{ New }}E_{i} * \, C_{i}$$(5) -
7.
A 2-level Inverse Wavelet Transform (IWT) is applied to all the sub-bands (LL2, LH2, HL2, HH2 (new)) to reconstruct the stego image.
Figure 4 shown below represents the block diagram of the embedding process of the proposed methodology.
Extraction process
The extraction process is essentially the reverse of the embedding process.
-
1.
Apply IWT to the stego image to obtain the four sub-bands: LLs1, LHs1, HLs1, and HHs1.
-
2.
Apply IWT to the LLs1 sub-band again to retrieve another set of distinct sub-bands: LLs2, LHs2, HLs2, HHs2.
-
3.
Apply SVD to the HHs2 sub-band to decompose it, and using the stored matrices from the embedding process, calculate :
$$E_{si} \left( {{\text{new}}} \right) \, = \, \left( {E_{y} {-} \, E_{i} \left( {{\text{corner}}} \right)} \right) \, / \, \alpha$$(6)where Ey is the extracted matrix and Ei is the original matrix used during embedding.
-
4.
Reconstruct the sub-bands of each part using the formula:
$${\text{Part}}_{i} = \, A_{si} * \, E_{si} \left( {{\text{new}}} \right) \, * \, C_{si}$$(7)where i=1,2,3,4. The Asi, Csi, and α values are obtained from the embedding side.
-
5.
Combine the four parts after resizing them to reconstruct the extracted secret image.
Figure 5 shown below represents the block diagram of the extraction process of the proposed methodology.
We closely examined the embedding strength parameter (α) in a narrow range between 0.008 and 0.012 to pinpoint the optimal value. As shown in Fig. 6, the PSNR reached its highest point of 29.5 dB at α = 0.01. This setting offered the best balance between keeping the stego image visually indistinguishable from the cover image and ensuring strong embedding quality. When α was slightly lower or higher, the PSNR dropped, showing that the image quality was more affected. Based on this o bservation, we chose α = 0.01 for all later experiments and kept it the same across comparisons with other algorithms to ensure fairness and consistency.
The grayscale cover image in our implementation is a 512 × 512 image comprising 262,144 pixels. The secret image, originally 256 × 256 pixels (65,536 pixels), is divided into four equal segments, each reduced to one-eighth of its original resolution. This results in 32,768 pixels for embedding, equivalent to 262,144 secret bits. A two-level Integer Wavelet Transform (IWT) is applied to the cover image, focusing on the LL1subband. The HH2 subband obtained has dimensions of 128 × 128, providing 16,384 coefficients. The overall embedding rate, calculated using the standard bits-per-pixel (bpp) definition, is 1.0 bpp, indicating that the total embedded bit count equals the number of pixels in the cover image.
When analysing the embedding within the HH2 subband specifically, the local embedding density reaches 16 bits per coefficient, as the complete payload is allocated to this subband
This high-capacity embedding is achieved through SVD-based blending rather than simple LSB substitution, ensuring improved robustness and imperceptibility of the hidden data.
Experimental setup
Experiments for this steganography project took place on a computer with an Intel Core i5 processor, 8 GB of RAM, and 512 GB of storage. With these specifications as a foundation, subsequent work was able to benefit from adequate data handling power and storage space far beyond any reasonable doubt. MATLAB was the tool of choice for building this system, making the user interface fast and comfortable, and providing a full range of image processing functionality. MATLAB provided a stable and effective environment for experimentation with the proposed steganography technique under different conditions.
GUI development and operation
For this work, we developed a specialised graphical user interface (GUI) in MATLAB to improve the user experience with the steganography system. When you start the GUI by running the LoginPage.m file, it opens a login page window, as shown in Fig. 7. Here, users are prompted to enter the correct password to access the system.
Once the user successfully logs in, the interface changes to the Image Steganography window, shown in Fig. 8. Here, the users can easily select the input cover and secret images using a user-friendly interface, as illustrated in Figs. 9 and 10.
It also offers various steganographic technique options available in the system. After making selections, this GUI enables performance evaluation of chosen steganographic methods, allowing real-time analysis and comparison of different techniques’ efficacy and robustness, as shown in Fig. 11. This GUI is an essential and easier means for conducting experiments and assessing steganographic processes’ performance as outlined in this study.
Results and discussion
Performance analysis
The assessment of cover and stego images using different statistical parameters is presented below.
Mean squared error (MSE)
The MSE indicates the average squared discrepancy between the corresponding pixels of the source cover picture and the picture containing hidden information.An MSE close to zero suggests minimal distortion in the cover image. The MSE is calculated using Eq. (8).
Root mean square error (RMSE)
RMSE is derived from the Mean Squared Error (MSE) and provides a more interpretable measure by taking the square root of the MSE.RMSE close to zero suggests minimal distortion in the coverimage.The MSE is calculated using Eq. (9).
Bit error rate (BER)
The BER measures the proportion of incorrect bits in relation to the total number of bits, as determined by Eq. (10). BER values vary between zero and one, where zero denotes a strong similarity between two images. A BER value approaching zero indicates minimal distortion in the cover image.
Correlation
Correlation refers to the degree of statistical association or relation between the original image and the image with hidden information.
A correlation value of one indicates perfect similarity between two identical images. Higher correlation values, closer to one, suggest less distortion in the cover image. Correlation is determined using Eq. (11).
Image fidelity (IF)
“Image fidelity” refers to the degree to which the steganographic process preserves the quality and authenticity of the original image, often referred to as the “cover image.” High image fidelity closely resembles the original, maintaining visual quality and structural integrity. Image fidelity, represented by the Image Fidelity (IF) metric, is perfect when comparing two identical photographs, yielding a value of 1 and is calculated using Eq. (12).
Average absolute difference (AAD)
The Average Absolute Difference (AAD) is the performance metric that calculates the average difference between the pixels of the cover image and the stego image. A higher AAD indicates a larger distortion due to the high difference between the images.It is calculated using Eq. (13).
For comparative analysis, baseline methods like “IWT + SVD” and “DWT + DCT”, etc., were reimplemented to ensure consistent experimental conditions. Table 1 details the transforms used for Cover and Secret Images in each baseline, with these configurations applied consistently thereafter. Wavelet transforms or combinations were implemented in the same frequency bands as the proposed methodology for the cover image, ensuring performance differences attributed from the method, rather than the implementation variations.
Figure 12 compares how different transform-based embedding techniques perform across several quality measures. Graphical analysis shows that traditional methods like DFT and DCT have much higher error values; techniques based on IWT—especially the proposed IWT + SVD method achieve significantly lower error values while maintaining high correlation and fidelity. This indicates that the proposed method offers an optimal balance between preserving the original content quality and minimising distortion, thereby demonstrating superior robustness and efficiency compared to the other approaches tested.
Normalised average absolute difference (NAD)
The Normalised Average Absolute Difference (NAD) is the ratio of change of pixels between the original cover image (O) and the stego image (S) to the sum of pixel values in the cover image, which indicates distortion. The NAD can be calculated using Eq. (14).
Table 1 compares various performance measures discussed previously that are used to assess the efficiency of our proposed steganography method in comparison to other techniques.
Noise attack analysis
In this section, we examine the performance of our proposed steganographic method against different types of noise, such as ‘Gaussian noise’, ‘Salt & Pepper noise’, and ‘Speckle noise’, by varying the respective parameters related to each noise attack. To measure the impact of these disturbances on the stego image quality, we use a range of performance metrics mentioned in the following sub-sections, which are used to assess the robustness of our proposed methodology.
Normalised cross-correlation (NCC)
NCC is a performance metric used to calculate the correlation between two images. The NCC between the original secret image (O.S.) and the extracted secret image (E.S.) can be calculated using Eq. (15). The higher the NCC value, the more similar are the original and extracted secret images.
Table 2 illustrates the degree of similarity between the original images and the secret images revealed through various steganographic techniques. These cross-correlation values provide insight into how effectively each method maintains the integrity and likeness of the original secret and extracted secret images, even when the stego images are exposed to noise.
Structural similarity index measure (SSIM)
SSIM is a metric that quantifies the resemblance between two images. SSIM can detect changes or distortions introduced by steganographic embedding techniques. Suppose the SSIM value between the original secret and extracted secret images is significantly low. In that case, it may indicate that the steganographic process has affected the structural information of the cover image.
An SSIM value of one indicates high similarity between two images, signifying minimal distortion in the stego image. Equation (16) provides the estimated Structural Similarity Index Measurement (SSIM) value.
where σi, σj,µi, μj, and σij denote the mean values, standard deviations (S.D.), and cross-covariances for images i and j. C1 and C2, representing (k1L)2 and (k2L)2, respectively, serve to stabilise the division with a small denominator. L signifies the images’ active range of pixel values, with default values of k1 = 0.01 and kc = 0.03.
Table 3 displays the SSIM values between the original and extracted secret images exposed to different forms of noise, such as Gaussian, Speckle, and Salt & Pepper. The SSIM values, which range from 0 to 1, offer an indication of how closely the luminance, contrast, and structure align between the original and extracted secret images. Higher SSIM values closer to 1 indicate that the images maintain a high level of visual accuracy and structural integrity even when affected by noise.
Peak signal-to-noise ratio (PSNR)
The peak signal-to-noise ratio assesses the extracted secret image qualities by evaluating them against a reference or original secret image and gauging the level of noise or distortion introduced during encoding or concealment procedures. Higher PSNR values indicate less distortion from the original secret image.
The PSNR value is typically around 50 dB for a high-quality image, measured in decibels. PSNR quantifies the reconstruction quality of images, and its value is determined by Eq. (17).
Table 4 presents the PSNR values between the original and extracted secret images for various steganographic techniques under various noise conditions, including Gaussian, Speckle, and Salt & Pepper noise.
Number of pixel change rate (NPCR)
NPCR is a metric used to evaluate how much the pixels of an image change when just one pixel is altered.
Consider an original secret image of dimensions M x N, denoted by O.S., and an extracted secret image, denoted by E.S. The NPCR can be calculated using Eq. (18).
Table 5 compares the resilience of original and extracted secret images to different types of noise based on their NPCR values.
Unified average change intensity (UACI)
The UACI is used to calculate the average difference in brightness in an image when a single pixel is modified.
Consider an original secret image of M x N dimensions. Let us denote the original secret image as O.S. and the extracted secret image as E.S. Then the UACI value is given by Eq. (19).
Table 6 shows how much the pixel intensity changes (UACI values) for secret images when different types of noise are added. The UACI values help us see how well the steganographic techniques handle the noise and maintain the quality of the hidden images.
Conclusion& future work
The proposed steganographic technique has made significant progress in producing robust stego images by using Integer Wavelet Transform and Singular Value Decomposition. Extensive testing demonstrates that our approach considerably improves the invisibility of images and their resistance to noise attacks compared to conventional methods. Our system demonstrates a Mean Squared Error of only 9.6698, indicating minimal deviation from the original image, and a Root Mean Squared Error of 3.1096, showcasing the accuracy of our embedding process. We have achieved superior data integrity with a Bit Error Rate of 0.7205 compared to other steganographic techniques. Furthermore, our Structural Similarity Index Measure and Normalised Cross-Correlation values approach 1, indicating that the images’ structural and visual quality is well preserved after embedding. The Peak Signal-to-Noise Ratio stands at 29.5665 dB, underscoring the images’ clarity despite the embedded data. This work represents a significant advancement in image steganography, establishing a new standard for secure digital communication. The results of these experiments highlight the efficiency and applicability of our approach, providing a solid solution for applications that demand high security and accuracy in transmitting image data.
These outcomes position the proposed scheme as a practical option for scenarios demanding both security and fidelity in image-based communication, including defence systems, protected medical image transmission, and copyright preservation. In future, the work can be expanded to handle colour images and video sequences, adopt adaptive embedding techniques, evaluate computational requirements, incorporate testing on curated datasets, perform various statistical tests and apply additional performance visualisation tools, such as intensity profiles and correlation heatmaps, to enhance interpretability and validation.
Data availability
The authors declare that any data related to this research will be made available on request to the corresponding author, Dr Rajesh Anbazhagan (rajesha@ece. [sastra.ac.in](mailto:rajesha@ece.sastra.ac.in)).
Code availability
The authors declare that any code related to this research will be made available on request.
References
Choi, Y.I. and Kim, J.H., 2020, October. Reliable data transmission in 5G Network using Access Traffic Steering method. In 2020 International Conference on Information and Communication Technology Convergence (ICTC) (pp. 1034–1038). IEEE.
Majeed, M. A., Sulaiman, R., Shukur, Z. & Hasan, M. K. A review on text steganography techniques. Mathematics 9(21), 2829 (2021).
Subramanian, N., Elharrouss, O., Al-Maadeed, S. & Bouridane, A. Image steganography: A review of the recent advances. IEEE Access 9, 23409–23423 (2021).
Xiang, Y., Xiao, D., Zhang, R., Liang, J. & Liu, R. Cryptanalysis and improvement of a reversible data-hiding scheme in encrypted images by redundant space transfer. Inf. Sci. 545, 188–206 (2021).
Hussain, M., Wahab, A. W. A., Idris, Y. I. B., Ho, A. T. & Jung, K. H. Image steganography in spatial domain: A survey. Signal Process: Image Commun. 65, 46–66 (2018).
Dalal, M. & Juneja, M. Steganography and steganalysis (in digital forensics): a Cybersecurity guide. Multim. Tools Appl. 80(4), 5723–5771 (2021).
Kaur, S., Singh, S., Kaur, M. & Lee, H. N. A systematic review of computational image steganography approaches. Arch. Comput. Methods Eng. 29(7), 4775–4797 (2022).
Trivedi, M.C., Sharma, S. and Yadav, V.K., 2016, March. Analysis of several image steganography techniques in spatial domain: A survey. In Proceedings of the Second International Conference on Information and Communication Technology for Competitive Strategies (pp. 1–7).
Alhomoud, A.M., 2021. Image Steganography in Spatial Domain: Current Status, Techniques, and Trends. Intelligent Automation & Soft Computing, 27(1).
Ghoul, S., Sulaiman, R. & Shukur, Z. A review on security techniques in image steganography. Int. J. Adv. Comput. Sci. Appl. 14(6), 361 (2023).
Maji, G., Mandal, S. & Sen, S. Cover independent image steganography in spatial domain using higher order pixel bits. Multim. Tools Appl. 80(10), 15977–16006 (2021).
Abdulla, A. A. Digital image steganography: Challenges, investigation, and recommendation for the future direction. Soft. Comput. 28(15), 1–14 (2023).
Liji, C. A., Indiradevi, K. P. & Babu, K. A. Integer-to-integer wavelet transform based ECG steganography for securing patient confidential information. Proc. Technol. 24, 1039–1047 (2016).
Islam, S., Modi, M. R. & Gupta, P. Edge-based image steganography. EURASIP J. Inf. Secur. 2014, 1–14 (2014).
Jia-Fa, M., Ru, Z., Xin-Xin, N., Yi-Xian, Y. & Lin-Na, Z. Research of spatial domain image digital watermarking payload. EURASIP J. Inf. Secur. 2011, 1–12 (2011).
Abed, S. E., Al-Roomi, S. A. & Al-Shayeji, M. Efficient cover image selection based on spatial block analysis and DCT embedding. EURASIP J. Image Video Process. 2019(1), 87 (2019).
Yadahalli, S.S., Rege, S. and Sonkusare, R., 2020, June. Implementation and analysis of image steganography using Least Significant Bit and Discrete Wavelet Transform techniques. In 2020 5th international conference on communication and electronics systems (ICCES) (pp. 1325–1330). IEEE.
Margalikas, E. & Ramanauskaitė, S. Image steganography based on color palette transformation in color space. EURASIP J. Image Video Process. 2019(1), 82 (2019).
Gutub, A. & Al-Shaarani, F. Efficient implementation of multi-image secret hiding based on LSB and DWT steganography comparisons. Arab. J. Sci. Eng. 45(4), 2631–2644 (2020).
Wang, J. et al. JPEG image steganography payload location based on optimal estimation of cover co-frequency sub-image. EURASIP J. Image Video Process. 2021, 1–14 (2021).
Miri, A. & Faez, K. An image steganography method based on integer wavelet transform. Multim. Tools Appl. 77, 13133–13144 (2018).
Murugan, G. V. K. & Uthandipalayam Subramaniyam, R. Performance analysis of image steganography using wavelet transform for safe and secured transaction. Multim. Tools Appl. 79(13), 9101–9115 (2020).
Eyssa, A. A., Abdelsamie, F. E. & Abdelnaiem, A. E. An efficient image steganography approach over wireless communication system. Wireless Pers. Commun. 110(1), 321–337 (2020).
Singh, S., Singh, R. and Siddiqui, T.J., 2016. Singular value decomposition based image steganography using integer wavelet transform. In Advances in Signal Processing and Intelligent Recognition Systems: Proceedings of Second International Symposium on Signal Processing and Intelligent Recognition Systems (SIRS-2015) December 16–19, 2015, Trivandrum, India (pp. 593–601). Springer International Publishing.
Gunjal, B. L. & Mali, S. N. MEO based secured, robust, high capacity and perceptual quality image watermarking in DWT-SVD domain. Springerplus 4, 1–16 (2015).
Liu, H. H. & Lee, C. M. High-capacity reversible image steganography based on pixel value ordering. EURASIP J. Image Video Process. 2019(1), 54 (2019).
Zebbiche, K., Khelifi, F. & Bouridane, A. An efficient watermarking technique for the protection of fingerprint images. EURASIP J. Inf. Secur. 2008, 1–20 (2008).
Avcıbaş, İ, Kharrazi, M., Memon, N. & Sankur, B. Image steganalysis with binary similarity measures. EURASIP J. Adv. Signal Process. 2005, 1–9 (2005).
Rossi, L., Garzia, F. & Cusani, R. Peak-shaped-based steganographic technique for JPEG images. EURASIP J. Inf. Secur. 2009, 1–8 (2009).
Nashat, D. & Mamdouh, L. An efficient steganographic technique for hiding data. J. Egypt. Math. Soc. 27, 1–14 (2019).
Sharma, S. & Sharma, K. K. Multi-modal medical image fusion framework using co-occurrence filter and local extrema in NSST domain. Biomed. Signal Process. Control 83, 104605 (2023).
Ma, Y., Ma, J., Li, C. & Wang, C. An end-to-end content-aware generative adversarial network based method for multimodal medical image fusion. IEEE Trans. Cybern. 52(3), 1515–1526 (2022).
Tang, B., Ma, J., Luo, W. & Zheng, Y. TSJNet: A multi-modality target and semantic awareness joint-driven image fusion network. Inf. Fusion 79, 99–112 (2022).
Funding
No funding was received for conducting this study.
Author information
Authors and Affiliations
Contributions
Conceptualization, Manikandan Chinnusami; Data curation, Dyutisri Koll; Methodology, Rajesh Anbazhagan; Software, Rengarajan Amirtharajan; Validation, Manikandan Chinnusami and Rajesh Anbazhagan; Visualization, Dyutisri Kolli; Writing—original draft, Shreela S; Writing—review & editing, Dyutisri Kolli.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Chinnusami, M., Kolli, D., Shreela, S. et al. Analysis of hybrid integer wavelet transform and singular value decomposition for image steganography under various noise conditions. Sci Rep 15, 31610 (2025). https://doi.org/10.1038/s41598-025-17020-2
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-17020-2