Abstract
The fog computing paradigm is better for creating delay-sensitive applications in Internet of Things (IoT). As the fog devices are resource constrained, the deployment of diversified IoT applications requires effective ways for determining available resources. Therefore, implementing an efficient resource management strategy is the optimal choice for satisfying application Quality of Service (QoS) requirements to preserve the system performance. Developing an effective resource management system with many QoS criteria is a non-deterministic polynomial time (NP) complete problem. The study applies the Hybrid Prairie Dog and Dwarf Mongoose Optimisation Algorithm-based Resource Scheduling (HPDDMOARS) Technique to effectively position IoT applications and meet fog computing QoS criteria. This HPDDMOARS technique is formulated as a weighted multi-objective IoT application placement mechanism which targets optimizing the three main parameters that considered energy, cost and makespan into account. It employed Prairie Dog Optimization Algorithm (PDOA) for exploring the possibility that helps in mapping the IoT services to the available computing services in fog computing scenario. It also derived the significance of Dwarf Mongoose Optimization Algorithm (DMOA) which helps in exploiting the local factors that helped in satisfying at least one objective of QoS index. It hybridized the benefits of PDOA and DMOA mutually for the objective of balancing the phases of exploration and exploitation such that potential mapping between the IoT tasks and the available computational resources can be achieved in the fog computing environment. The experimental validation of the proposed HPDDMOARS achieved with different number of IoT applications confirmed minimized energy consumptions of 22.18%, reduced makespan of 24.98%, and lowered cost of 18.64% than the baseline metaheuristic application deployment approaches.
Similar content being viewed by others
Introduction
The quality of human life has evolved and enhanced undoubtedly with an increase in the utilization rate of Internet of Things (IoT) types of equipment in different types of fields that include automated industrial operations, intelligent transportation systems, agricultural monitoring, smart healthcare, and so on1. This diversified use of IoT devices results in the development and implementation of different complex and latency sensitive IoT applications such as video streaming applications, online gaming, Virtual Reality (VR), Augmented Reality (AR), etc. due to the tremendous rate of data generated through the inclusion of the devices2. The number of devices which are linked together is determined to reach a maximum of 2.5 billion by the end of 2025 as per the research report released by Cisco and IoT. However, IoT devices during the process of data generation are posed by the challenge of limited energy and required optimal mapping of computing resources. Thus, the process of data offloading need to be achieved in a particular layer which possesses a requisite number of intensive resources of computing This data offloading also need to be guaranteed for supporting the necessitated degree of execution of IoT tasks in the fog computing environment3. In this context, the paradigm of cloud computing can facilitate the resources that include management, networking, storage, and computation depending on the basic policy of pay-as-per-use. At this juncture, guaranteeing the requirements of Quality of Service (QoS) is determined to be a challenging herculean task due to two main reasons, such as (i) the amount of data generated by the IoT devices, and (ii) the existing distance between the IoT users and the cloud data centers. On the other hand, the rapid development of delay intensive IoT applications imposes stringent requirements during the process of satisfying the requirements strictly associated with the factors of QoS, availability, ultra-low requirement, deadline, security, etc. Thus, the deployment of IoT applications is not infeasible in cloud-based solutions4.
Fog computing according to the Open Fog Consortium represents a predominant computational framework which is developed for handling the inherent challenges that are related to the existing models of cloud computing that are related to storage, delay, and bandwidth5. This distinct design of Fog computing layer helps in achieving the aspects of intelligence and information processing at the edges of the network wherein the data is being generated and utilized. This Fog computing paradigm is developed to prevent the different issues of QoS and latency challenges that exist with the paradigm of cloud computing6. It is considered as a scalable model associated with centralized cloud computing which comprises of different layers network topology that helps in preserving the comprehensive merits of efficiency, manageability, orchestration, virtualization, containerization, etc. But the process of establishing a fog network is a herculean task concerning diverse scenarios over which it is implemented since it necessitates the process of defining and determining the requirements of different heterogeneous capabilities of fog devices to serve the use of IoT7. The requirements of fog computing layer completely depend on CPU, RAM, down-link capacity, up-link capacity, storage, communication, computing, etc. Moreover, factors such as mobility, types of environments used for execution, required number of services, service types, and possibly estimated amount of IoT application requests need to be determined before the process of implementing the fog service model. In this context, the base station, routers, and the smart gateway constitute the primitive networking equipment of the fog computing infrastructure8. These fog devices facilitate various computing resources for achieving real-time responses for various ranges of latency sensitive IoT data. On the other hand, fog computing possesses a few advantages over edge computing in terms of bandwidth efficiency, improvement in latency, flexibility in connectivity, distributed intelligence and reduced data dependency. From the bandwidth efficiency perspective, fog computing minimizes the degree of data forwarded to the cloud by locally processing the data. With respect to latency improvement, it minimizes latency by processing the data at the source such that it is suitable for handling the data associated with the applications like the medical data. It offers connectivity flexibility since it can utilize wired, Wi-Fi and 5G networks. It also facilitated distributed intelligence by facilitating the process of decision making at different levels, and it depended less on clouds as the necessity to communicate with the cloud has the possibility of saving high degree of costs.
The architecture of fog computing presented in the paper is a three-layer computing infrastructure which provides extensive capability for all the comprehensive cloud computing features that are related to vehicular IoT applications9. This architecture provides some additional characteristics which include context-sensitive services and mobility management associated with different mobile-based applications of IoT. It is responsible for minimizing the propagation delay to offer a wide range of services at the network edge which is close to the IoT devices. Further, the applications of IoT represent the software as a service which carries out different activities intended to receive the data from the IoT. This IoT application in turn consists of a collection of services, tasks or modules which necessitate different computing resources of configuration for the objective of accomplishing their executions10. However, the process of discovering service availability and estimating the exact computing resources is determined to be more complex for the service provider due to the dynamic and heterogeneous characteristics of IoT applications. Furthermore, a diversified number of IoT applications under different situations necessitates a different number of responsive requirements in real time apart from their dynamicity and heterogeneous characteristics. In addition, it is identified to be highly essential to assign or map the incoming collection of services to the existing computing resources. This mapping of services to computing resources needs to be performed with the intent of satisfying at least one objective that satisfies the index of QoS which prevents the challenges associated with the IoT applications11. At this juncture, IoT service placement is considered the ideal solution for optimizing and satisfying the required indexes of the QoS index that resolves the challenges of IoT applications. The problem of IoT service placement concentrates on determining the most optimal computing resources which could help in executing the services assisted by heterogeneous IoT12. The decision of optimal service placement handles different issues that target the process of maximizing the deployment of IoT applications that focus on optimizing the utilization of resources, achieving potential load balancing, and satisfying the deadline requirements for underloading and overloading in the fog computing environment. This process of achieving the decision concerning the optimal assignment of heterogeneous services of IoT to fog devices for their better execution with satisfied QoS requirements is identified to be a well-known problem of NP-Complete. Thus, most of the researchers working in this field of IoT service placement concentrated only on finding the near-optimal solution to their research problem. On the other hand, the process of identifying single or multi-objectives in the problem of IoT service placement adds more complexity in addition to the process of determining feasible and optimal mapping of different available services to the fog-cloud infrastructure.
Most of the researchers formulated the problem of IoT service placement by considering it as a problem of single objective optimization and determined its solutions through the adoption of models that include mixed integer non-linear programming, mixed integer linear programming (MILP), integer linear programming (ILP) and linear programming (LP), respectively13. The most recent research works which concentrated on the problem of IoT service placement in fog computing scenarios were mainly based on a single objective optimization function that concentrated on minimizing energy consumption, reducing cost, maximizing QoS and network utilization. This problem of IoT service placement in fog computing scenarios needs to optimize more than one objective in many real-time situations. In such real-time situations, the use of a single objective optimization function for solving the problem of IoT application placement is identified to be impractical and unrealistic. At the next level, some of the researchers formulated the IoT service placement problem in fog computing using a bi-objective or multi-objective optimization problem in the existing literature. Therefore, the problem of multi-objective service placement helps in attaining optimal mapping of IoT application services to the existing computing services. But this process of mapping needs to derive the benefits of more than a single optimization function in the environment of fog computing. However, these multi-objective optimization functions considered for optimization are generally conflicting and may get generated from the service provider or the IoT user side. For instance, maximizing reliability and performance from the viewpoint of the service provider or minimization of cost from the user dimension is considered as a conflicting objective in the process of IoT service placement. Hence, formulating a multi-objective IoT service placement problem in fog computing seems to be realistic. Moreover, the process of optimizing each objective function without getting dominated by the other solution is always important at an acceptance level. To determine a dominant solution for the multi-objective IoT service placement problem in fog computing, two approaches were used in the literature, these methods proven to be an NP-complete problem since identifying the comprehensive Pareto optimality for all the objectives is completely infeasible. In addition, most of the researchers implemented and solved the problems of IoT service placement using the merits of MINLP, MILP, ILP or LP approaches for optimizing a diversified number of objectives that focus on the factors of energy consumption, execution cost, service latency, etc.
Motivation
The time complexity involved during the process of achieving the multi-objective IoT service placement in fog computing using MINLP, MILP, ILP or LP approaches grows with the size of the problem. The metaheuristic population-based swarm intelligent algorithms which depend on the concept of survival of the fittest or natural selection is identified as reliable in locating the solution in the search process in an acceptable time. This is because metaheuristic approaches are guaranteed to be ideal in solving a wide range of problems related to NP-complete complexity14. The strong searching capability and simple implementation potential of the metaheuristic approaches make it ideal for solving the problem of multi-objective IoT service placement in the fog computing paradigm. Moreover, adopting hybrid metaheuristic swarm intelligent algorithms for solving the problem of multi-objective IoT service placement is determined to be more reliable in fog computing. This is due to the well-established balance achieved between the factors of cost, energy and makespan that aids in executing the IoT tasks in the fog-cloud system15. Motivated by these merits of metaheuristic swarm intelligent approaches, the proposed Hybrid Prairie Dog and Dwarf Mongoose Optimization Algorithm-based Resource Scheduling (HPDDMOARS) Technique concentrates on the process of identifying the plan for optimized service placement with respect to different numbers of heterogeneous IoT applications which in turn consist of multiple numbers of independent services. In the process of hybrid optimization algorithms, the classical and current metaheuristic algorithms are combined for integrating the potentialities of different algorithms for the objective of determining better results in the implemented problem of implementation. Thus, hybrid metaheuristic algorithms facilitated enhanced performance compared to the single metaheuristic algorithm since they help in providing a flexible and efficient algorithm. In specific, PDOA is potential in global optimization process and possesses limitations in terms of exploitation capability. On the other hand, DMOA is good in exploitation and possesses some limitations in terms of exploration capability. Thus, when PDOA and DMOA is combined for establishing a well-balanced degree of exploration and exploitation phases are guaranteed in the process of employing them in the process of placing the service in the Fog Computing Environment.
Key contributions
The key contributions of this manuscript are presented as follows.
-
i)
It employed Prairie Dog Optimization Algorithm (PDOA) for exploring the possibility that helps in mapping the IoT services set to the available computing services in fog computing scenario.
-
ii)
It utilized the significance of Dwarf Mongoose Optimization Algorithm (DMOA) which helps in exploiting the local factors that helped in satisfying the objective of QoS index.
-
iii)
It was implemented with the significance of a multi-objective metaheuristic swarm intelligent approach that hybridized the well-balanced exploration and exploitation merits of PDOA and DMOA remarkably for achieving optimized mapping of computing resources to different IoT applications.
-
iv)
It also adopted a weighted multi-objective IoT application placement mechanism which targets on the process of optimizing the three main parameters that considered energy, cost and makespan into account.
Novelty of the proposed work
This HPDDMOARS technique was proposed as one among the few approaches that established better load balancing between different fog nodes by processing the tasks of IoT applications in an efficient manner. It is developed as a two-level model which achieved the objective of task scheduling and resource scheduling in fog computing environment. It facilitated potential task scheduling process through the balanced exploration and exploitation benefits of EPDOA and DMOA algorithms for minimized the total energy utilization and total execution time of the system. It adopted a resource scheduling process which used EPDOA for allocating the fog nodes in the fog cluster and DMOA algorithm for addressing the problem between the fog clusters using the process of task scheduling. It is also implemented as a significant scheduling strategy of resource scheduling which maximized the degree of resource utilization and minimized service latency with extended overall task execution stability.
The remaining sections of the paper are structured as follows. Section 2 describes comprehensive literature studies related to the problem of multi-objective IoT service placement in fog computing with the identified research gaps. Section 3 presents the details related to the system model, the problem of a multi-objective application placement, and the proposed IoT service placement algorithms in fog computing environment. Section 4 demonstrates the results and discussion of the proposed HPDDMOARS scheme under the impact of a different number of IoT applications. Finally, the major contributions and future scope of enhancement related to the proposed work is presented in Sect. 5.
Related work
In this section, the comprehensive literature studies related to the problem of multi-objective IoT service placement in fog computing with the identified research gaps are presented.
Nashaat et al.16 contributed a Multi-Dimensional Quality of Experience (QoE) Model for satisfying the resource allocation of requests related to the process of application placement in the fog computing scenario. This QoE model comprises two phases, in which the first phase is responsible for determining the priority of different application placements depending on the impact factors that include user expectations, application utilization and context of environment runtime. It possessed the process of mapping and placing the user requests to the suitable fog node instance for deployment such that QoE is guaranteed in the implementation environment. This application placement approach used the parameters of expected response time, computing potentialities, and proximity into account during the process of achieving the objectives necessitated in the fog computing scenario. The simulation results of the MDQOE model conducted using iFogSim simulator confirmed better power consumption, network utilization, application delay and time of application placement Salimian et al.17 proposed a Grey Wolf Optimization Algorithm-Based IoT Application Placement (GWOAAP) scheme for addressing the process of resource scheduling into the fog nodes of the fog computing environment. It was proposed as one of the approaches that attempted to enhance the degree of user expectation and system performance. This GWOA-based application placement approach achieved minimized execution costs with enhanced systems’ performance. It was proposed with the merits of autonomic concepts which helped dynamic behavior of fog environments through the inclusion of a suitable autonomous management system. It also included a partitioning algorithm which splitted the applications into different numbers of independent clusters. It achieved reduced search space since it conserved system resources by considering reactive scheduling decisions. This simulation results of GWOAAP confirmed better mean waiting time and mean execution time compared to the baseline approaches used for evaluation.
Wu et al.18 proposed an Evolutionary Algorithm-Based Fuzzy Scheduler (EABFS) to attain multi-objective resource allocation in fog computing scenario. It adopted the merits of a fuzzy scheduler for the process of modelling the size of inter-task data and processing time. This evolutionary algorithm-inspired model considered the objectives of schedule robustness and customers’ agreement index into account for application placement in fog computing environment. It used the method of fuzzy logic and estimation of the distribution algorithm to attain the process of pre-partitioning and rule allocation. It further incorporated a fuzzy logic-based offloading mechanism which helped in the process of IoT application placement with due consideration of the uncertain factors that focussed on robustness and agreement index. The incorporated estimation of the distribution algorithm played an indispensable role in learning and optimizing the strategy of fuzzy offloading from the viewpoint of application diversity. It divided the entire search space into clusters such that each cluster could be mapped to its associated layer for subsequent processing. Simulation results of this EABFS scheme confirmed better Pareto sets, and hence they outperformed the traditional solutions in terms of efficacy and execution time under real-world vases. Goudarzi et al.19 proposed an IMPortance weighted Actor-Learner Architectures (IMPALA)-based IoT application deployment mechanism (IWALASADM) for attaining quick adaptability and preventing generalizability in centralized deep learning-based processes. This IWALASADM approach minimized the agents’ exploration costs obtained from the Directed Acyclic Graphs (DAGs)-modelled IoT applications that support diversified topologies. It reduced the placement problem complexity with minimized constraints during the process of satisfying the dependencies inherent in the applications of DAG-based IoT. It specifically used IMPALA optimization algorithm for the objective of generating an efficient distributed experience that helped in satisfying the dependencies inherent with the applications of DAG-based IoT. It also attained faster convergence of optimal solutions through the inclusion of a reactive off-policy correction method. It also adopted the recurrent layers for the objective of deriving input data temporal characteristics with the support of a replay buffer to improve the efficiency of the samples. The results of this IWALASADM approach guaranteed better execution time independent to the number of IoT applications to the maximum level under different configurations considered for evaluation.
Further Tavousi et al.20 proposed a Fuzzy Approach-based Heuristic algorithm (FAHAOP) for Optimal Placement of IoT applications in the fog computing environment. This FAHAOP approach classified the IoT applications depending on the properties of applications which need to be deployed over the virtualized computing resources. The adopted policy concentrated on the process of offering high quality service of the IoT users with due profit consideration of the fog service providers with maximized resource utilization degree. This approach was identified to attain better convergence to the solution in the process of near-optimal application deployment which is introduced over the fog nodes. The simulation results of this FAHAOP approach confirmed better resource wastage prevention rate, satisfied requests with deadlines, and mean response time under the impact of different number of IoT applications. Sriraghavendra et al.21 implemented a Genetic Algorithm (GA)-based QoS-aware service placement mechanism (GASDM) that helped the execution of IoT applications in the fog computing environment. This GASDM handled the challenging tasks that are related to the orchestrating of the time sensitive IoT applications of fog computing. It was proposed with a reliable multi-tier fog computing architecture which prevents the generic problem of deadlines which are inherent with the nodes of the cloud and fog. It was identified to adopt low-cost fog resources in an optimal way for guaranteeing the response time which is indispensable for satisfying the necessitated number of constraints in real time. It specifically used the merits of GA for the dynamic determination of service placement in the environment of fog computing. It was identified to possess a better service deadline during the process of application placement during the process of modelling using iFogSim simulator. It was also confirmed to confirm better overall response time and minimized service execution delay compared to the baseline approaches used for evaluation.
Taghizadeh et al.22 proposed a Non-Dominated Sorting Genetic Algorithm-based metaheuristic-based IoT application placement approach (NSGAMAP) which helped minimize the delay-sensitive requirements in the fog computing environment. This NSGAMAP approach handles the node with different hardware potentialities which impose the challenges that arise during traffic reduction and latency in fog computing paradigm. It was proposed with the benefits of NSGA for the objective of managing application deployment in fog-cloud computing scenarios. This approach evaluated using iFogSim simulator guaranteed minimized cost during data access and exhibited a decrease in terms of latency with a maximized degree of availability of fog nodes on par with the metaheuristic approaches used for evaluation. Ghobaei-Arani and Shahidinejad23 proposed another Evolutionary Whale Optimization Algorithm-based Meta-Heuristic Mechanism (EWOAMHM) for achieving an autonomic process of better application deployment in fog computing contexts. This EWOAMHM approach monitored different requirements of QoS that are associated with the available potentialities of fog nodes and IoT applications. It determined potential service placement using WOA for improving the throughput and energy consumption with the process of formulating the fitness function that helped in determining the optimal IoT service placement plan. It was implemented using an autonomous application deployment framework which inherited a three-tier architecture which necessitates the interaction between fog nodes and IoT devices. The simulation results of this EWOAMHM approach guaranteed better performance in terms of reduced energy consumption, service delay, service acceptance rate and resource utilization compared to the metaheuristic algorithms based IoT application deployment mechanisms.
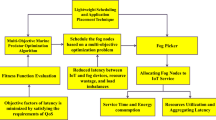
In addition, Subbaraj et al.24 proposed a Crow Search Algorithm-based Multi-Objective Metaheuristic Application Placement Algorithm (CSAMMAPA) which helped in the scheduling and allocation of resources in the fog computing environment. This CSAMMAPA approach considered the factors of security hit ratio and success ratio during the formulation and utilization of fitness function that helps in attaining IoT application placement. It concentrated on the process of maximizing the two objectives considered for the optimization process. It particularly used Crow Search Algorithm (CSA) for handling the issues that are related to the process of scheduling and allocation of resources in fog computing. It was determined to achieve the required objectives of QoS within the expected time with maximized efficiency and the least amount of execution time. Sabireen and Venkataraman25 contributed a Fog Picker and Multi-objective Particle Swarm Optimization-based clustering approach (FP-MPSOCA) for the objective of resource scheduling and application employment in fog computing environment. This FP-MPSOCA approach was proposed a lightweight algorithm which helped in the dynamic scheduling of the fog nodes depending on the problem of multi-objective optimization. This model included the merits of machine learning for enhancing the performance of PSO algorithm which attributed towards the minimization of latency between the IoT and fog nodes for preventing resource wastage and achieving a better load balancing process. It specifically used the benefits of fog picker for allocating the components of IoT to the fog nodes such that the time of turnaround and efficient use of resources depending on the attributes of QoS could be attained in fog computing scenario. The hypervolume and generational distance achieved by this FP-MPSOCA approach were identified to be better than the baseline approaches since they maintained steady performance, better convergence rate and well-distributed population in the search space.
Sun et al.39 proposed a Proximal Policy Optimization Algorithm-based Proportional Fairness-Aware Auction method (PPOAPFAAM) of attaining better task scheduling with potential resource allocation, This PPOAPFAAM approach decoupled the process of task scheduling for implementing decision making associated with task allocation and resource allocation under different competitive scenarios. It allocated different computing resources to each individual node using an auction algorithm after the process of completing the resource allocation. This method learned information from the behavior of UAVs for scheduling available computing resources to the offloaded destination. It further used the merits of the distributed deep reinforcement learning PPO algorithm depending on the tasks’ heterogeneous tasks for facilitating UAVs to make intelligent offloading decisions. The results of this PPOAPFAAM approach confirmed better performance in terms of system fairness, load balancing and system profit. Xia et al.40 proposed a Metalearning-Based Alternating Minimization Algorithm-based Nonconvex Optimization for reducing the degree of global losses over several iterations. This MAMANCO approach incorporated the principle of non-convex optimization for improving the degree of interpretability in an optimal manner. It included the merits of non-convex problem solutions for addressing the problem of non-linearity, matrix completion and bilinear inverse problem. It furthermore used the rule of fixed updating which partitioned the problem into set of sub-problems with respect to different variables used for optimization. The results of this MAMANCO approach confirmed better performance in terms of scheduling performance in terms of system throughput and response time.
Zhang et al.41 proposed a multiple time-scale dispatch model which used the merits of frequency dynamics of islanding awareness with load voltage for the objective of restricting the rate of frequency change associated with the micro-grid. This multiple time-scale dispatch model proposed for micro-grid power dispatch transformed the problem of micro-grid into a multi-objective optimization problem by considering the factors of frequency stability, voltage deviation and economic cost. It integrated the significance of an elite learning technique into the penalty-based boundary intersection (PBI) based multi-objective optimization approach for addressing the problem of micro-grid. This implemented approach confirmed better diversity distribution and better ability of convergence for implementing a deep deterministic policy gradient (DDPG) strategy for learning evolutionary factors that aids in determining the grid based alternating weight vectors. The results of this optimization approach confirmed minimized economic cost with simultaneous cost of frequency and voltage stability. Lin et al.42 proposed an entropy features-based optimized CatBoost model (EFOCBM) for attaining for an imbalanced industrial load identification process which helped in balancing the data categories of the load sample with minimized performance in terms of classification. This EFOCBM model selected the states of the switches with multiple number of original samples related to the load data from the dataset considered for evaluation. This samples are segmented into time domain by partitioning each sample data into intervals associated to three time-domains. This strategy included the merits of Prediction Value Change method for calculating the degree of feature importance and sorting them using the 27 time-domain features from which eight entropy features are determined from the original feature set. It used the decision variable of CatBoost classification accuracy for determining the optimal features of classification subset depending on the method of forward feature selection. It included the method of Borderline-SMOTE for preparing the sample data for the process of balancing the sample data with balanced switched process.
Ding et al.43 proposed an intelligent traffic flow control system framework for achieving traffic flow management and attaining real-time prediction in the process of communication technology. This framework improved urban safety and traffic efficiency for the purpose of reducing the accident rates and optimizing the signal control such that application layers, perception and network platform. It used the technology of vehicle networking for collecting the data traffic and at the same time, guaranteeing real-time transmission through 6G communication. It phenomenally improved the system systems’ overall efficiency for solving the problems of complex traffic optimization through the inclusion of optimized genetic algorithm which optimized the flow of the data traffic. It adopted the machine learning algorithms in the platform layer for exploring and processing the data and predicting the degree of traffic flow with different strategies of formulated traffic management. The results of this intelligent traffic flow control system framework confirmed minimized mean traffic delay, minimized signal control optimization with enhanced traffic flow prediction rate. Peng et al.44 a Dynamic Pricing Driven Double Broad Reinforcement Learning Model (DPDDRL) for making efficient decisions making during the process of task offloading. This DPDDRL model guaranteed safe vehicular operation for the objective of mitigating the degree of risks such that performance of the network can be improved with the required level of satisfaction. This offloading model used the characteristics of long decision time for deriving the large number of parameters in the results of the deep network with large utilization of computational resources. It specifically used the merits of DBRL for minimizing the degree of decision time and memory consumption by considering the degree of high-speed mobility. It also used the factors of resource variability and high speed mobility for implementing the scheme of efficient dynamic pricing that reduces the overall delay in task processing that are generated by the vehicular requests.
Xu et al.45 proposed a Value Transfer Incentive Model for enhancing the degree of incentives with respect to Artificial Intelligence of Things for the purpose of permitting the degree of active participation during the degree of training. This Value Transfer Incentive Model addressed the problem of restricted data owner engagement with personalized model construction. It ensured a fair benefit redistribution using the mechanism of bail and contribution assessment using the merits of InterPlanetary File System (IPFS) and Smart Contracts (SC) such that high reliability and security is improved in the implementation process. It secured the transactions with data integrity for confirming the execution of tasks in a more tamper-resistant and transparent manner. Sun et al.46 proposed a breadth-first search (BFS)-based SFC deployment optimization (SFCDO) algorithm for achieving the deployment of service function chain without impacting the performance of virtual network function. It specifically used a BFS-based algorithm for identifying the shortest oath between the source and the destination nodes. It also used the method of shortest path for selecting the process of SFC deployment with minimized number of hops on par with the simulated annealing and greedy algorithm. The results of this BFS-SFCDO algorithm confirmed superior bandwidth resource consumption and minimized end-to-end delay such that the nodes’ lead rate is achieved for attaining better network load balancing process.
In addition, Sun et al.47 implemented an online service function chain deployment (OSFCD) algorithm for determining the process of efficiently utilizing the resources of the network during the process of SFC deployment. This OSFCD method potentially handled the requests of SFC in the perspective of NFC in terms of 6G communication technology. This method selected the path for the objective of determining the length of SFC from the deployment perspective.
In addition, Table 1 presents a comprehensive summary of the research works related to the multi-objective IoT service placement in fog computing problem with the merits and limitations.
Research gap
The research gaps that are identified from the comprehensive survey of the existing literature studies related to the problem of multi-objective IoT service placement in fog computing are listed as follows,
-
i)
Most of the approaches19,20,21 were single objective and, were realized to enhance the overall system performance by compromising a slight increase in the energy consumption related to fog control nodes.
-
ii)
Most of the multi-objective optimization functions23,24,25 considered for optimization are generally conflicting and may get generated from the service provider or the IoT user side.
-
iii)
A potential number of approaches16,17,18 targeted on the process of optimizing each objective function without getting dominated by the other solution, which may not be realistic in most of the situations.
-
iv)
The metaheuristic algorithm used for application22,25,26,27,28,29,30,31 deployment either possessed the problem in deriving a solution with maximized diversity or the solutions that get struck into the local point of optimality.
Proposed hybrid Prairie Dog and Dwarf Mongoose optimization algorithm-based application placement and resource scheduling technique
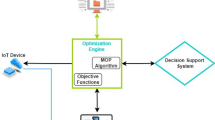
The proposed 3-layer Fog Computing (FC) system model includes IoT device layer along with the task model. The Fog Multi-Objective Service Placement (MOSP) problem is defined and formulated using traditional weighted sum approaches to enhance numerous parameters.
FC architecture
The architecture involves three hierarchical layers. The IoT device layer includes diverse sensors as well as IoT devices accountable for gathering data from the surrounding environment and forwarding them for processing at edge devices. Every geographically distributed IoT device is linked to Fog Node (FN) using Wi-Fi. FC devices positioned in dense networks establish the next level in the hierarchy. Potential candidates which qualify FC nodes include routers, proxy servers, switches, Base Station (BS) etc. Each FC layer comprises of different number of fog domains which are operated by the fog control manager (FCM) which is considered as a controller device in the architecture as shown in Fig. 1.
This FCM associated with each of the fog domains takes the responsibility of designing, mapping and implementing the application and services in the FC system. It is also responsible for detecting a necessary number of IoT tasks such that it could be organized by the IoT devices for the objective of executing them over a specific computing resource. It is also assumed that there always exists a communication between the FCMs in the architecture considered for implementation. FCM of FD communicates with FCM of another FD easily to determine the present state of diverse FC devices (Quantity of busy Virtual Machines (VMs), kind of computing resource employed). FC devices periodically forward the present status to conforming FCM. In the proposed model, FCM implements a placement scheme after each ‘\({\uptau}\)’ period. FC device is represented using 4 tuples \(\left[{\text{F}\text{C}}_{CC},{\text{F}\text{C}}_{DU},{\text{F}}_{\text{U}\text{L}}, {\text{F}}_{\text{D}\text{L}}\right],\)where ‘\({\text{F}\text{C}}_{CC}\)’ denotes Computing Capacity (CC), ‘\({\text{F}\text{C}}_{CD}\)’ signifies devices usage, ‘\({\text{F}}_{\text{U}\text{L}}\)’ and ‘\({\text{F}}_{\text{D}\text{L}}\)’ denote Uplink and Downlink capacities respectively. Hence, it aims at mapping requests of IoT applications to FC devices to ensure improved response time.
Fog-cloud-IoT model
The model includes 3 layers. The lowest layer includes diverse users and IoT devices. It focuses on smart monitoring, smart homes, healthcare devices, PCs, etc., each requesting for different types of applications. Every IoT device includes varying abilities based on computing, communication and storage resources. The computing capacities of IoT devices seem to be inferior to that of another layer. On generation of a request, it is sent to FC layer for processing at Fog Gateway (GW) associated with Base Station (BS) for transmitting data among end devices. Furthermore, IoT devices can send data to central CC layer that is linked through FC layer as in Fig. 2. Consider IoT devices, \({\text{D}}_{\text{I}\text{o}\text{T}}=\left\{{\text{d}}_{\text{I}\text{o}\text{T}}^{1}, {\text{d}}_{\text{I}\text{o}\text{T}}^{2}, {\text{d}}_{\text{I}\text{o}\text{T}}^{3}, \dots,{\text{d}}_{\text{I}\text{o}\text{T}}^{\left|\text{D}\right|}\right\},\) where ‘\({\text{d}}_{\text{I}\text{o}\text{T}}^{\left|\text{D}\right|}\)’ signify total quantity of IoT devices. ‘\({2}^{\left|\text{D}\right|}-1\)’ number of applications are produced. Consider applications \({\text{A}}_{\text{I}\text{o}\text{T}}=\left\{{\text{A}}_{\text{I}\text{o}\text{T}}^{1}, {\text{A}}_{\text{I}\text{o}\text{T}}^{2}, {\text{A}}_{\text{I}\text{o}\text{T}}^{3},\dots, {\text{A}}_{\text{I}\text{o}\text{T}}^{\text{n}}\right\},\) where ‘\({\text{A}}_{\text{I}\text{o}\text{T}}^{\text{i}}\)’\(,1\le \text{i}\le \text{n}\) involves finite amount of services denoted as \({\text{A}}_{\text{i}}=\left\{{\text{T}}_{\text{i}}^{1},{\text{T}}_{\text{i}}^{2}, {\text{T}}_{\text{i}}^{3},{\dots,\text{T}}_{\text{i}}^{\text{j}}\right\},\) ‘i’ and ‘j’ signify indices of application and service respectively. Every service is represented by size of input task \(\left({\text{I}}_{{\text{T}}_{\text{i}}^{\text{k}}}\right),\) size of output task \(\left({\text{O}}_{{\text{T}}_{\text{i}}^{\text{k}}}\right),\) amount of data required for implementation \(\left({\text{D}}_{{\text{T}}_{\text{i}}^{\text{k}}}\right)\) and the amount of resource required by every task for implementation \(\left({\text{R}}_{{\text{T}}_{\text{i}}^{\text{k}}}\right).\) Every task is considered to be latency-sensitive or tolerant. FC layer includes a limited amount of heterogeneous FC devices signified as \(\text{F}=\left\{{\text{F}}_{1}, {\text{F}}_{2}, {\text{F}}_{3},\dots,{\text{F}}_{\text{m}}\right\},\) where \(\left\{1,2,3\ldots\text{m}\right\}\)denotes the quantity of devices.
‘\({\text{F}}_{\text{m}}\)’ represents ‘\({\text{m}}^{{\rm th}}\)’ FD. Every FC device offers Type-1 hypervisor to afford an execution environment for implementing tasks signified as \({\text{F}}_{\text{i}}=\left\{{\text{V}\text{M}}_{\text{i}}^{1},{\text{V}\text{M}}_{\text{i}}^{2},{\text{V}\text{M}}_{\text{i}}^{3},\dots{\text{V}\text{M}}_{\text{i}}^{\text{j}}\right\},\) where, ‘i’ and ‘j’ signify FD index and VM number. Attribute of every FD is represented as \({\text{F}}_{\text{j}}=\left\{{\text{S}}_{\text{j}}^{{\rm Max}},{\text{C}}_{\text{j}}^{{\rm Max}},{\text{E}}_{\text{j}}^{{\rm Max}}\right\},\)where ‘\({\text{S}}_{\text{j}}^{{\rm Max}}\)’ represents represent storage capacity (MBs), ‘\({\text{C}}_{\text{j}}^{{\rm Max}}\)’ signifies computing capacity (CPU/cycles) in Million Instructions Per Second (MIPS) and ‘\({\text{E}}_{\text{j}}^{{\rm Max}}\)’ denotes the amount of energy consumed (Watt).
CC layer is the topmost layer consisting of numerous powerful PMs and servers for executing several compute-demanding applications. Consider ‘\(\text{k}\)’ physical servers, \(\text{P}\text{S}=\{{\text{P}\text{S}}_{1},{\text{P}\text{S}}_{2},{\text{P}\text{S}}_{3}\ldots{\text{P}\text{S}}_{\text{k}}\}\), \(1\le\text{j}\le\text{k},\) where every physical server ‘\({\text{P}\text{S}}_{\text{j}}\in\text{P}\text{S}\)’ may execute several resource-exhaustive tasks simultaneously. A host may position VMs to execute several tasks concurrently. Cloud host (\(k\)) is denoted as \({\text{R}}_{\text{k}}=\left({\text{R}}_{\text{k}}^{\text{C}},{\text{R}}_{\text{k}}^{\text{M}},{\text{R}}_{\text{k}}^{\text{S}},{\text{R}}_{\text{k}}^{\text{B}}\right),\) where ‘\({\text{R}}_{\text{k}}^{\text{C}}\)’ signify CPU capacity specified in MIPS, ‘\({\text{R}}_{\text{k}}^{\text{M}}\)’ denotes RAM capacity (MB) and ‘\({\text{R}}_{\text{k}}^{\text{S}}\)’ represents storage capacity (GB). Hosts are dynamically controlled by turning on or off depending on input workflow.
Multi-objective service placement (MOSP) problem
This MOSP focuses on determining the mapping of applications which offer dependent or independent services to available computation resources with objective subjects for satisfying conditions. Usually, SP problem is a Combinatorial Optimization (CO) problem with several solutions. Therefore, determining the best mapping takes more time and is tedious in case of heterogeneous IoT and computing devices32,33,34. Mathematically, SP represents a function \({\Pi}\left(\text{P}\text{l}\text{a}\text{c}\text{e}\text{m}\text{e}\text{n}\text{t}\right):\text{A}\to\text{R},\)where ‘\(\text{A}\)’ signifies a collection of applications with every application comprising of several services denoted as \(\text{A}=\left\{{\text{S}}_{1},{\text{S}}_{2},{\text{S}}_{3},.{\text{S}}_{\text{n}}\right\}\). The variable ‘\(\text{R}=\text{F}\cup\text{C}\)’ represents available computing resources, where ‘\(\text{F}\)’ denotes FDs and ‘\(\text{C}\)’ signifies available cloud servers. Every FD and cloud server includes a limited quantity of VMs \(\text{R}=\{{\text{V}\text{M}}_{1},{\text{V}\text{M}}_{2},{\text{V}\text{M}}_{3},\dots,{\text{V}\text{M}}_{\text{m}}\}\).
Theorem
MOSP is NP-complete.
To prove that MOSP is NP-complete, a reduction factor which focuses on dropping a problem (\({\text{P}}_{1}\)) to problem ‘\({\text{P}}_{2}\)’ is used under the assumption that an algorithm for ‘\({\text{P}}_{2}\)’ is available. Consider SP as ‘\({\text{P}}_{1}\)’ and 0/1 Knapsack problem as ‘\({\text{P}}_{2}\)’. The Knapsack problem is a tough CO problem which has gained much attention from diverse research communities for solving several practical problems including stone cutting, selection as well as resource distribution problems. ‘\({\text{P}}_{2}\)’ involves determining subgroup of items from definite item sets with some predefined items’ costs and weights such that overall profit is improved, and weight satisfies capacity of knapsack. There are ‘\(\text{n}\)’ disjoint item classes, \(\text{I}=\left\{{\text{I}}_{1},{\text{I}}_{2},.,{\text{I}}_{\text{n}}\right\},\) where ‘\({\text{I}}_{\text{k}}\)’ has profit \({{\upvartheta}}_{\text{k}}\ge 0\)and the weight vector is denoted as \(\text{W}=\left\{{{\upomega}}_{1},{{\upomega}}_{2},\ldots,{{\upomega}}_{\text{n}}\right\},\) where every component \({{\upomega}}_{\text{k}}\ge 0,\text{k}=1,2,\dots,\text{n}\) signifies weight of ‘\({\text{I}}_{\text{p}}\)’ in ‘\(\text{I}\)’. The objective function of ‘\({\text{P}}_{2}\)’ is given by,
Where, \(\text{i}=\text{1,2},\dots\text{n}\)
As the Knapsack problem is NP-hard, SP in Eq. (5) may be reduced to Eq. (1). Based on the transitivity rule, it is emphasised that SP problem is NP-complete.
Problem formulation
This problem of application placement and resource scheduling concentrates on the process of optimizing the factors of makespan, energy and service cost (explained in Sect. 3.4) such that optimal computing resources for the objective of executing the different number of services is achieved with the satisfaction of the required QoS factors in the fog computing environment. This problem focusses on the execution of a finite set of application services which needs to satisfy the demands of QoS with the constraints of response time, deadline and essential CPU cores, RAM and memory for execution. It finds computing resources for optimising QoS factors dependent on satisfying the constraints such an effective application placement and resource scheduling process can be attained by satisfying the influential factors at the same time for the objective of guaranteeing latency-tolerance and sensitivity. Hence the optimization objectives reducing makespan, service cost and amount of energy which represents the decision variables of the services to be mapped to FC layer resources as specified in Eqs. (2), (3) and (4)
Then the weighted sum multiobjective optimization problem of application placement and resource schedyling is defined based on Eq. (2) - Eq. (4) is represented in Eq. (5)
Where, ‘\({\upphi}\)’, ‘\({\uppsi}\)’ and ‘\(\text{\S}\)’ signify objective function weights defined by users, \({\upphi}+{\uppsi}+\text{\S}=1,{\text{x}}_{\text{i}}^{\text{j}}\in [1,0]\)specifies service ‘\({\text{S}}_{\text{i}}\)’ positioned in ‘\({\text{j}}^{{\rm th}}\)’ FDs if value is ‘1’. Else, service (\({\text{S}}_{\text{i}}\)) is positioned in CDC. ‘\({\text{f}}_{\text{m}}^{\text{s},\text{d}}\)’, ‘\({\text{f}}_{\text{e}}^{\text{s},\text{d}}\)’ and ‘\({\text{f}}_{\text{c}}^{\text{s},\text{d}}\)’ represent standardised values of makespan, cost as well as the amount of energy consumed. Min-max normalization as shown in Eq. (6) is used for getting standardized values of 3 factors. For every value of the variable, the distance from the minimum is determined and divided by range.
Where, \({\text{MS}}_{{\rm S}}=\left\{{\text{ms}}_{{\rm i}}^{{\rm j}}\left|\text{i}=\text{s},\text{j}\in\text{D}\right.\right\}\), \({\text{ms}}_{{\rm i}}^{{\rm j}}={{\text{t}}_{\text{i}}^{\text{j}}}^{{\rm Proc}}+{{\text{t}}_{\text{i}}^{\text{j}}}^{{\rm Comm}},{{\text{t}}_{\text{i}}^{\text{j}}}^{{\rm Proc}}=\frac{{\text{X}}_{\text{i}}}{{\text{Y}}_{\text{i}}},{{\text{t}}_{\text{i}}^{\text{j}}}^{{\rm Comm}}=\frac{{\text{I}}_{\text{i}}}{\text{B}\text{W}\left({\text{S}\text{r}\text{c}}_{\text{i}},j\right)}+\frac{{\text{O}}_{\text{i}}}{\text{B}\text{W}\left(\text{j},{\text{D}\text{s}\text{t}}_{\text{i}}\right)}\). The variable ‘\({{\text{t}}_{\text{i}}^{\text{j}}}^{{\rm Proc}}\)’ represents the processing time for execution of Service (\({\text{S}}_{\text{i}}\)) in device (\({\text{D}}_{\text{j}}\)). Similarly, ‘\({{\text{t}}_{\text{i}}^{\text{j}}}^{{\rm Comm}}\)’ signifies communication time essential for sending and receiving service input as well as output (\({\text{S}}_{\text{i}}\)) between devices ‘\({\text{d}}_{\text{i}}\)’ and ‘\({\text{d}}_{\text{j}}\)’. Normalized cost function and amount of energy consumed are shown in Eq. (8) and Eq. (11).
Where,
\({{\upeta}}_{\text{j}}^{{\rm Cost}}\)- Amount consumed for every unit time during implementation in device (j)
Where,
\({{\upeta}}_{\text{j}}^{{\rm Energy}}\)’ - Energy (Watts) for implementation of service (i) in ‘j’
Constraints used for optimization
This problem of optimization depends on the constraints associated with fog resources, and applications which are essential for application placement and resource schedyling as mentioned below.
Constraints related to Fog Resource
As shown in Eqs. (14)–(16), RAM, CPU as well as Storage demands of application tasks are less than or equal to available resources in FC layer i.e., FD (Fj).
Constraints related to application
Equation (17) specifies that the overall makespan of tasks must not go beyond deadline.
Where,
\({\text{F}\text{D}\text{s}:\text{F}}_{\text{j}}\in{\text{R}}^{\text{F}}\), \(\text{i}\in[1,\dots,\text{n}]\)
The parameters used for problem formulation
The problem of application placement in fog computing is formulated as a multi-objective optimization problem which involves the process of optimizing multiple number of conflicting objectives at the same time. In this problem of application placement, the parameters of makespan, energy, service cost are considered for optimizing them simultaneously.
Optimization factor 1: makespan
This makespan refers to the quantity of total time essential for processing a collection of services in the application that includes processing and communication time and queueing delay, where processing time refers to the quantity of time essential for computing task. It is also defined as the communication time refers to quantity of time essential for transferring service requests from IoT devices to FDs and sending response to actuators with the queueing delay considered as zero. This the makespan incurred during the process of application service placement is determined based on Eq. (18)
Where the processing time and communication time used for determining the makespan is specified in Eqs. (19) and (20)
Where, ‘\({\S}_{\text{j}}\)’ and ‘\({{\uppsi}}_{\text{f}}\)’ signify computation capacity (MIPS) and bandwidth amid IoT devices and FDs (Megabit/Sec) respectively. It is assumed that there is no queueing delay, \({\text{T}}_{\text{i}}^{\text{Q}\text{u}\text{e}\text{u}\text{e}}=0.\)
Optimization factor 2: energy
This optimization factors of energy is determined based on the amount of energy consumed at FC layer; 2 states of FD are assumed. In case of idle state, FD does not process tasks but consumes some quantity of energy, whereas in case of busy state, FD performs several kinds of computations. The amount of energy consumed by FDs in busy state is computed35. The total amount of energy consumed is considered to be total energy consumed during the process of data transmission and processing as specified in Eq. (21).
Where the total amount of energy (\({\text{E}}_{\text{f}\text{p}}^{\text{E}\text{n}\text{g}}\)) used at the fog devices (it further depends on energy incurred for data transmission (\({\text{E}}_{\text{t}\text{r}\text{a}\text{n}}^{\text{E}\text{n}\text{g}}\)) and data used for data processing (\({\text{E}}_{\text{P}\text{r}\text{o}}^{\text{E}\text{n}\text{g}}\))) are determined using Eq. (22)
Optimization factor 3: service cost
This service cost (\(S{\text{C}}_{\text{T}\text{o}\text{t}}\)) represents the amount of resources utilized for executing the complete set of tasks associated with different number of applications considered for placement in the fog computing environment. This service cost signifies total execution cost that includes total processing, storage and energy utilized at FC layer as shown in Eq. (25)
Where \({\text{C}}_{\text{P}\text{r}\text{o}\text{c}}\) represents the processing cost involved in executing the number of instructions referring to quantity of CPU resources as specified in Eq. (26)
This service cost at the second level depends on the storage cost as specified in Eq. (27)
In this case, the cost with respect to the amount of energy consumed is determined individually for every FD by finding the product with time, while total cost is the product of total amount of energy consumed in the FC layer and cost of a unit of amount of energy consumed in FC layer as mentioned in Eq. (28)
Then the makespan, energy and service cost which represents \({\text{f}}_{1}\), \({\text{f}}_{2}\) and \({\text{f}}_{3}\) are combined using the weights \({\text{w}}_{1}\), \({\text{w}}_{2}\) and \({w}_{3}\) as represented as \(f={\text{w}}_{1}\times{\text{f}}_{1}+{\text{w}}_{2}\times{\text{f}}_{2}+{\text{w}}_{3}\times{\text{f}}_{3}\). Then the multiobjective problem of application service placement is formulated as a minimizing objective condition \(Minimizef\) (discussed in Eq. 5) depending on the assumptions (Explained in Sect. 3.5) and constraints imposed (explained in Sect. 3.3) during the implementation process.
Assumptions
To mimic IoT SP problem by using propounded FC standard, the ensuing assumptions are made.
-
Propagation latency between FDs is negligible.
-
Pattern of task arrival is based on Poisson Distribution.
-
Every FD is protected and has adequate computational capacity for executing requests of applications.
-
Migration of tasks is not permitted.
-
Task and service may be interchangeably used as they are considered to have similar meaning.
-
Tasks of applications are taken as a Bag of Tasks (BoTs). The tasks are independent of others as no precedence limitations are seen to exist among them.
-
Fog as well as edge GWs function similarly and may be interchangeably used.
Random placement based on greedy approach (RPGA)
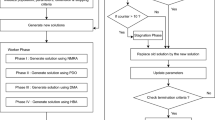
RPGA is a multi-start memoryless Meta-Heuristic (MH) for dealing with CO problem36. In every iteration, the algorithms generate arbitrary population and explore local optimum solution by fulfilling storage as well as RAM demands of every service. This RPGA method is a randomized greedy algorithm which plays a vital role in determining the placement of tasks into an appropriate node such that he cost can be significantly reduced with better guarantee of performance under the existence of heterogeneous resources like the cloud-fog computing scenario. Initially, feasible solution is determined by comparing resource demand as well as availability, followed by utilisation of RPGA. Initial feasible solution is taken as a basic local solution. Following a few iterations, the Algorithm 1 returns the best ideal solution.

Algorithm 1: RP Algorithm.
SP using Prairie Dog optimization algorithm (PDOA) by Dwarf Mongoose optimization algorithm (SP_PDOA_DMOA)
The original schemes employed in proposed scheme are detailed with main process of proposed method.
PDOA
PDOA proposed by Ezugwu et al.37 is a MH motivated by natural behavior of PDs. The algorithm involves 4 parameters namely, ‘\(\text{n}\)’, ‘\(\text{m}\)’, ‘\(\text{p}\)’ and ‘\(\in\)’. They are initialised during commencement of algorithm and are an alarm of specific source of food. ‘\(\in\)’ is a small number which denotes quality of food source. Like other MHs, PDO begins with arbitrary population (\(\text{n}\)) of solutions (PDs). Further, the populations are set to ‘\(\text{m}\)’ groups (coteries). In every iteration, solutions’ objective values are determined. The proposed scheme aids in performing exploration as well as exploitation through PD activities for switching between the 2 phases. Foraging and burrowing belong to exploration.
-
For \({\text{iter}}=\frac{{\text{Max}}_{\text{Iter}}}{4}\), foraging will be active.
Where ‘\({\text{P}}_{{\text{D}}_{\text{i}+1}^{\text{j}+1}}\)’ represents updation of position, ‘\({\text{G}}_{{\text{B}\text{e}\text{s}\text{t}}_{\text{i}}^{\text{j}}}\)’ signifies global best and ‘\({\uprho}\)’ is set to 0.1. ‘\(\text{L}\text{e}\text{v}{\text{y}}_{\text{n}}\)’ signifies Levy distribution. Further, ‘\({\text{e}\text{C}}_{{\text{B}\text{e}\text{s}\text{t}}_{\text{i}}^{\text{j}}}\)’ observes the influence of current ideal solution.
Where, ‘\(\text{U}{\text{B}}_{\text{i}}\)’ and ‘\(\text{L}{\text{B}}_{\text{j}}\)’ represent upper as well as lower bounds respectively to update position. Despite the fact that PDs are distinct from one another, implementation of PDO considers that they are alike and are represented by a small number (\(\varDelta\)). ‘\({\text{P}}_{{\text{D}}_{\text{i}}^{\text{j}}}\)’ signifies ‘\({\text{j}}^{{\rm th}}\)’ dimension of ‘\({\text{i}}^{{\rm th}}\)’ PD in Coterie, and ‘\({\text{C}}_{{\text{P}\text{D}}_{\text{i}}^{\text{j}}}\)’ denotes arbitrary cumulative effect of PDs in colony. ‘\({\text{P}}_{{\text{D}}_{\text{i}}^{\text{j}}}\)’ and ‘\({\text{C}}_{{\text{P}\text{D}}_{\text{i}}^{\text{j}}}\)’ are defined as shown below.
Where, ‘\(\text{U}\left(\text{0,1}\right)\)’ produces a random number within range [0, 1] with uniform distribution.
Where, ‘\({\text{r}.\text{P}}_{{\text{D}}_{\text{i}}^{\text{j}}}\)’ represents position of random solution.
-
For \(\frac{{\text{Max}}_{\text{Iter}}}{4}\le\text{iter}\le\frac{{\text{Max}}_{\text{Iter}}}{2}\), burrowing will be active.
Where, ‘\(\text{D}\text{S}\)’ represents Digging Strength of Coterie.
Food and anti-predation alarms fit into exploitation.
-
For \(\frac{{\text{Max}}_{\text{Iter}}}{2}\le\text{iter}\le\frac{3.{\text{Max}}_{\text{Iter}}}{4}\), food alarm is active.
Where, ‘\(\in\)’ denotes insignificant number that specifies total food food source quality and ‘\(\text{r}\text{a}\text{n}\)’ represents a random number in the range [0,1]
-
\(\frac{3.{\text{Max}}_{{\rm Iter}}}{4}\le{\text{iter}}\le{\text{Max}}_{\text{Iter}}\), anti-predation alarm is active.
Where, ‘\(\text{P}\text{E}\)’ refers to predator effect.
Algorithm uses established processes repeatedly so that it can examine potential locations of near-optimum solutions. Once algorithm finishes a loop, it finds an enhanced solution and substitutes the one it had formerly found based on the rule. PDO terminates with maximum number of iterations.
DMOA
DMOA model introduced by Agushaka et al.38 simulates foraging nature of DMs. The algorithm assigns the initial values of solutions as shown below.
Alpha group
As population is generated, fitness of every solution is determined. Probability of fitness of every population and alpha female (α) is chosen depending on ensuing probability.
‘\(n\)’ represents mongooses in ‘\({\upalpha}\)’ group and ‘\(BS\)’ signifies Babysitter, peep denotes vocalization of dominant female which that maintains the family on track. Updating of solutions is shown in Eq. (39).
Where, ‘\(\zeta\)’ signifies a random number within range [-1, 1] representing Sleeping Mound (SM) of mongoose as a collection of SMs. In Eq. (40), SM for every repeat is shown.
The mean weight of SM is shown in Eq. (41).
The algorithm moves to scouting phase when considering next source of food or SM once BS exchange requirement is fulfilled.
Scout group
Scouts search for next SM for ensuring exploration to circumvent former SM. This motion depends on finding a SM which may be successful or unsuccessful. Further, migration of mongoose depends on the overall performance. The group identifies a fresh SM when sufficiently forged. Equation (42) simulates scout mongoose.
Where, ‘\({\text{ran}}\)’ represents a random number in the range [0, 1]. On the other hand, CF is determined as shown in Eq. (43). Equation (44) gives the value of ‘\(\text{M}\)’.
In addition, BSs are lesser members in the group who pay attention to children and face frequent rotations. Mother, ‘α’ female may lead the Squad based on everyday hunting missions.
Proposed enhanced PDOA (EPDOA)
The proposed EPDOA method focuses on addressing the challenges of existing PDOA and DMOA which include poor convergence, imbalance between search processes and early convergence. It focuses on improving search procedure of PDOA by using primary updation scheme of DMOA. It is based on 2 principal search operators of PDOA and MDOA which are used based on a constraint; if \(\text{r}\text{a}\text{n}<0.5\), then implement anyone. Typically, when an optimization method tries performing the updating of candidate solution, low diversity is identified. This has an impact on performance of search operators by dropping performance. Furthermore, in case of reduced diversity of solutions, unevenness amid search processes occurs as operators’ emphasis on one portion of updating schemes, local and global searches. Change amid search schemes enhances searchability as well as performance, guiding to robust solutions. This aids in overcoming early convergence and unevenness amid search operators.
Time complexity
It denotes the quantity of time consumed by an optimization scheme for finding a solution to a problem size. It depends on the quantity of variables including search space dimensionality, problem’s difficulty, convergence rate and efficiency of operations of algorithm including assessment of fitness, updating of solution, exploration and exploitation. Precise modifications carried out in EPDOA and DMOA through process of hybridization might have an influence on the amount of time consumed and hence the total complexity of the proposed algorithm. Moreover, Algorithm 2 presents the details of EPDOA adopted for achieving application placement in fog computing environment.

Algorithm 2: EPDOA-based application placement process.
Integration of EPDOA and DMOA for balancing exploration and exploitation
Based on the above Algorithm 2, the process of integrating EPDOA and DMOA is achieved during application placement and resource scheduling in fog computing environment.
The algorithms of EPDOA and DMOA are accomplished in this problem of application placement and resource scheduling for attaining essential balance between the rate of exploration and exploration such that algorithm never prematurely determine the best solution in the search space. EPDOA specifically used the control parameter CF in the scout phase) for controlling the different behaviours of the search agents. It specifically used the parameter of \({\text{S}}_{\text{M}}\) which heled in transiting the algorithm from the global searching process to the local searching process such that optimal solutions are determined at the rapid rate by preventing the solution from being struck into the local optimal point of the solutions. The use of DMOA into the exploration phase of EPDOA helped in attaining the required degree of diversity for facilitating a wide range of searching which facilities the discovery of diversity global optima in real time. During the integration of EPDOA and DMOA, like most of the intelligent optimization algorithms the individuals of the population are randomly generated initially within the upper and lower threshold level. This random generation of initial population helps in attaining specific differences in the locations and eigen values associated with the individuals of the population to exist within a specific diversity degree. This enforcement of maximized diversity helped in better exploration of the search space. At the same time, the inclusion of DMOA into the exploitation phase of EPDOA aided in further improvement of the diversity with respective increase in the number of iterations which eventually increase the potential of the global search with falling into the local optimal point of convergence.
SP using hybrid SP_PDOA_DMOA
The proposed Hybrid SP_PDOA_DMOA involves fixed number of iterations. This service placement approach during the initial iteration generates random solution. Once the initial iteration is over, the populations are generated and updated recursively through the fitness valued solutions which helps in generating a set of determined solutions. This PDOA depends on the factors that helps in determining the population size, and DMOA associated with exploitation helps in determining the potential VMs. The capability of the VMs depends on the number of tasks or services which need to be executed in the implementation environment. Moreover, the proposed SP_PDOA_DMOA scheme employs arbitrarily generated candidate solutions during the employment of DMOA and PDOA used for determining feasible solutions in the search space such that all the set of QoS considered for evaluation are satisfied.
This process of service application and resource scheduling is accomplished over the Fog-cloud-IoT model (explained in Sect. 3.1 and 3.2) such that the tasks of the IoT application can be allocated to the fog resources for the objective of efficiently using the resources effectively and minimizing the delay during the execution of real time IoT applications since response time is more crucial for these applications. This proposed model determines the number of tasks associated with the IoT applications currently getting executed in the fog server. If the number of tasks associated with the fog server are greater or less than the predetermined threshold, then the problem of over-utilization is identified such that migration of application task from one fog server to the another is introduced in the implementation scenario, On the other hand, a greater number of tasks related to the IoT applications are allocated to the current utilized fog server under the realization of under-utilization condition. This method of handling the situation of over-utilization and under-utilization helped in better load balancing such that none of the tasks associated with the IoT applications never wait and starve for fog resources. This eventually reduced the energy incurred by the fog servers in the implementation scenario. This resource scheduling is more dynamic and hence takes decision depending on the constraints that are realized in the fog computing model. This energy optimization could be visualized at all the three layers of the considered fog computing architecture.
Simulation results and discussion
The simulation experiments of the proposed HPDDMOARS technique and the benchmarked approaches are conducted over a fog-cloud enabled IoT environment for the purpose of determining the efficiency towards the process of achieving IoT application deployment in fog nodes. In specific, Yet Another Fog Simulator (YAFS) is used as the simulator for achieving the evaluation process of the proposed HPDDMOARS technique and the benchmarked approaches under different number of IoT application and end user devices. The IoT applications used for placement and resource scheduling are associated with precision farming, smart irrigation, and livestock monitoring. In this implementation, it is assumed that the computing capacity of the fog devices is always lesser than the computing potentiality of the cloud data centres. It specifically used the model of Albert Barbasi for the objective of generating scale free network during the start of simulation, and then initiation of task lunch time is achieved such that all the algorithms begin its execution at the same time without any kind of bias. The above simulation experiments are conducted over the PC which has the configurations of Intel core i7 processor 3.6 GHz processor, 8 GB RAM with a clock rate of 2.53 GHz. This experiment is also conducted by changing the weights of the criteria considered for fitness function evaluation. Table 2 presents the simulation parameters considered for implementing the HPDDMOARS technique and the benchmarked approaches in fog computing environment.
Performance evaluation of HPDDMOARS technique based on number of IoT tasks
In this section, evaluation results of the proposed HPDDMOARS scheme and the benchmarked FP-MPSOCA25, CSAMMAPA24, EWOAMHM23 and NSGAMAP22 approaches achieved using the parameters of energy consumptions, cost, makespan, resource utilization rate, Optimal IoT application placement rate and execution time under the impact of different IoT tasks are presented with its inferences. Figures 3 and 4 depict the energy consumption and cost incurred by the proposed HPDDMOARS scheme and the benchmarked approaches with different number of IoT tasks. With increase in the number of IoT tasks, the overhead in executing tasks by offloading it to the fog nodes gets increased since the energy spent, and cost spent for resource allocation and mapping the tasks to suitable fog nodes is essential. When the number of IoT tasks gets increased then reactive decision making towards the mapping process of tasks to fog nodes increase the cost. The proposed HPDDMOARS scheme with increase in the number of IoT tasks performed well by balancing the tradeoff between the exploitation rate of PDOA and exploration rate of DMOA to the expected level. It is potent enough in reducing or enlarging the search space depending on the candidate solutions determined in the solution space. This application placement approach maximized the diversity and prevented premature convergence of the candidate solutions from being struck into local point of optimality. It also considered thresholds of under-utilization and over-utilization such that load balancing with energy optimization is achieved in the fog computing environment. In addition, the use of control parameters of DMOA mutually helped in better diversity with minimized makespan. Thus, the proposed HPDDMOARS scheme with different number of IoT tasks, on average minimized the energy consumptions by 15.48%, and cost by 13.42%, better than the baseline FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches.
On the other hand, Figs. 5 and 6 demonstrate the plots of makespan and resource utilization rate confirmed by the proposed HPDDMOARS scheme and the benchmarked approaches with different number of IoT tasks. The proposed HPDDMOARS scheme when implemented performs remarkably by preventing pre-mature convergence and attaining maximized diversity in the solution space. It mutually balances the rate of exploration and exploitation using the integration of EPDOA and DMOA such that solutions are highly explored for more optimal solutions by satisfying the requirements of QoS within the specified deadlines and constraints in fog computing. It used EPDOA to solve the problem of optimal load balancing for each of the tasks existing within a single fog cluster. It facilitated the option of allocating the tasks to each individual fog cluster in a more reasonable manner by considering the factor of transmission time into account. This scheduling approach used the optimization factors of makespan, service cost and energy consumptions into account. Thus, the proposed HPDDMOARS scheme with different number of IoT tasks, on average minimized the energy consumptions and cost by 21.86% and 24.98%, better than the baseline FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches. Moreover, the proposed HPDDMOARS scheme with different number of IoT tasks, on average minimized the makespan by 18.65%, and maximized the resource utilization rate by 18.76%, better than the baseline FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches.
Figures 7 and 8 present the optimal IoT application placement rate and execution time realized in the fog computing environment during the implementation of the proposed HPDDMOARS scheme and the benchmarked FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches with different number of IoT applications. The optimal IoT application placement rate guaranteed by the proposed HPDDMOARS scheme is identified to be better than the baseline approaches because it potentially handled the problem of conflicting multi-objective criteria used for fitness evaluation process. This capability of the proposed HPDDMOARS scheme helped in sustaining the rate of mapping the IoT tasks to the fog nodes by satisfying the QoS factors to the expected degree. It achieved the process of resource scheduling at the fog computing layer at two levels. In the first level, the bandwidth of each fog nodes and computational resources within the cluster for optimal allocating the tasks within the condition of load-balancing. At the second level, the task scheduling between the fog clusters is accomplished rationally such that the tasks never starve for execution process. Further the balance between the application placement and resource scheduling is established such that the required level of QoS is satisfied in the fog computing scenario. Thus, the proposed HPDDMOARS scheme with different number of IoT tasks, on average maximized the optimal IoT application placement rate by 18.54%, and reduced the execution time by 20.52%, better than the baseline FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches.
Performance evaluation of HPDDMOARS technique based on fog end node devices
In this section, evaluation results of the proposed HPDDMOARS scheme and the benchmarked FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches achieved using the parameters of latency, and execution time under the impact of different end user nodes. Figures 9 and 10 portray the latency and achieved by the proposed HPDDMOARS scheme and the benchmarked approaches with different numbers of end nodes. It handled the impact of fog end node devices reactively such that the task load is balanced in the fog cluster for the purpose of guaranteeing quantifiable degree of resource allocation within the required delay and energy essential for the process of maximizing the fog cluster. It computed the value of the objective function and updated the current optimal solution in each and every iteration such that ideal mapping of application tasks to the fog servers are always attained in the implementation platform. Thus, the proposed HPDDMOARS scheme with different number of IoT tasks, on average maximized the optimal IoT application placement rate by 18.54%, and reduced the execution time by 20.52%, better than the baseline FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches.
In addition, Fig. 11 presents the energy consumption incurred by the proposed HPDDMOARS scheme and the benchmarked FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches with different number of fog end nodes in the deployment environment. Energy consumption during the implementation of this experiment is potentially minimized since a greater number of tasks related to the IoT applications are allocated to the current utilized fog server under the realization of under-utilization conditions. This method of handling the situation of over-utilization and under-utilization helped in better load balancing such that none of the tasks associated with the IoT applications never wait and starve for fog resources. Thus, the proposed HPDDMOARS scheme with different number of IoT tasks, on average maximized the optimal IoT application placement rate by 18.54%, and reduced the execution time by 20.52%, better than the baseline FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches.
In addition, Table 3 presents the scalability study of the proposed HPDDMOARS scheme and the benchmarked FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches with different number of application tasks (ranging from 1000 to 3000) to understand which algorithm is potential to adapt well in the scaled environment of IoT networks.
This experimentation was conducted with 95% of confidence, and the results confirmed that the proposed HPDDMOARS scheme confirmed minimized makespan and energy utilization independent to the number of application tasks introduced into the fog computing environment.
Conclusions
The HPDDMOARS scheme achieved efficient IoT application placement by satisfying the requirements of QoS in fog computing. This HPDDMOARS technique is formulated as a weighted multi-objective IoT application placement mechanism which targets on optimizing the three main parameters that considered energy, cost and makespan into account. It specifically adopted the exploration capability of Prairie Dog Optimization (PDOA) and exploitation potentialities of Dwarf Mongoose Optimization Algorithm (DMOA) in a well-balanced manner due to the non-convexity nature of the solution space over which the process of resource scheduling needs to be attained. The simulation experiments of the proposed HPDDMOARS conducted with different number of IoT applications confirmed minimized energy consumptions of 22.18%, reduced makespan of 24.98%, and lowered cost of 18.64%, better than the baseline metaheuristic application deployment approaches used for comparison. the proposed HPDDMOARS scheme with different number of IoT tasks, on an average maximized the optimal IoT application placement rate by 18.54% and reduced the execution time by 20.52% than the baseline FP-MPSOCA, CSAMMAPA, EWOAMHM and NSGAMAP approaches.
Limitations
The proposed HPDDMOARS scheme can utilize the merits of deep learning or reinforcement algorithms for the objective of attaining IoT service placement in fog computing, and the use of deep learning has the possibility of increasing the process of predicting the data load which needs to be processed by the fog environment. The same IoT service placement approach can also be employed in edge computing since edge computing also possesses the merit of attaining delay sensitive execution of tasks compared to the fog computing environment.
Data availability
All data generated or analysed during this study are included in this published article.
References
Zolghadri, M., Asghari, P., Dashti, S. E. & Hedayati, A. Resource allocation in fog–cloud environments: state of the art. J. Netw. Comput. Appl. 227, 103891 (2024).
Ntumba, P., Georgantas, N. & Christophides, V. Adaptive scheduling of continuous operators for IoT Edge analytics. Future Generation Comput. Syst. 158, 277–293 (2024).
Lin, S. et al. Cocv: a compression algorithm for time-series data with continuous constant values in IoT-based monitoring systems. Internet Things. 25, 101049 (2024).
Apat, H. K., Sahoo, B., Goswami, V. & Barik, R. K. A hybrid meta-heuristic algorithm for multi-objective IoT service placement in fog computing environments. Decis. Analytics J. 10, 100379 (2024).
Devi, N. et al. A systematic literature review for load balancing and task scheduling techniques in cloud computing. Artif. Intell. Rev. 57(10), 276 (2024).
Pabitha, P., Nivitha, K., Gunavathi, C. & Panjavarnam, B. A chameleon and remora search optimization algorithm for handling task scheduling uncertainty problem in cloud computing. Sustainable Computing: Inf. Syst. 41, 100944 (2024).
Afzali, M., Samani, M. V., Naji, H. R. & A., & An efficient resource allocation of IoT requests in hybrid fog–cloud environment. J. Supercomputing. 80(4), 4600–4624 (2024).
Ghafari, R. & Mansouri, N. Fuzzy reinforcement learning algorithm for efficient Task Scheduling in Fog-Cloud IoT-Based systems. J. Grid Comput. 22(4), 66 (2024).
Asghari, A. & Sohrabi, M. K. Server placement in mobile cloud computing: a comprehensive survey for edge computing, fog computing and cloudlet. Comput. Sci. Rev. 51, 100616 (2024).
Nivitha, K., Pabitha, P. & Praveen, R. Self-regulatory fault forbearing and recuperation scheduling model in uncertain cloud context. In International Conference on Computational Intelligence and Data Engineering, 269–293 (Springer Nature Singapore, 2022)
Oliveira, L. T., Bittencourt, L. F., Genez, T. A., de Lara, E. & Peixoto, M. L. Enhancing modular application placement in a hierarchical fog computing: a latency and communication cost-sensitive approach. Comput. Commun. 216, 95–111 (2024).
Cao, K., Chen, M., Karnouskos, S. & Hu, S. Reliability-aware personalized deployment of approximate computation IoT applications in serverless mobile edge computing. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems (2024).
Pabitha, P., Sandheep, N., Nivitha, K. & Praveen, R. December). Proactive Fault Prediction and Tolerance in Cloud Computing. In Workshop on Mining Data for Financial Applications (527–550). Singapore: Springer Nature Singapore. (2022).
Jiang, D., Zhu, B., Liu, X. & Mumtaz, S. ALCoD: An adaptive load-aware approach to load balancing for containers in IoT edge computing. IEEE Internet Things J. (2024).
Daghayeghi, A. & Nickray, M. Delay-aware and energy-efficient task scheduling using strength pareto evolutionary algorithm II in Fog-Cloud Computing paradigm. Wireless Pers. Commun. 138, 409–457 (2024).
Nashaat, H., Ahmed, E. & Rizk, R. IoT application placement algorithm based on multi-dimensional QoE prioritization model in fog computing environment. IEEE Access. 8, 111253–111264 (2020).
Salimian, M., Ghobaei-Arani, M. & Shahidinejad, A. Toward an autonomic approach for internet of things service placement using gray wolf optimization in the fog computing environment. Software: Pract. Experience. 51(8), 1745–1772 (2021).
Wu, C. G., Li, W., Wang, L. & Zomaya, A. Y. An evolutionary fuzzy scheduler for multi-objective resource allocation in fog computing. Future Generation Comput. Syst. 117, 498–509 (2021).
Goudarzi, M., Palaniswami, M. & Buyya, R. A distributed deep reinforcement learning technique for application placement in edge and fog computing environments. IEEE Trans. Mob. Comput. 22(5), 2491–2505 (2021).
Tavousi, F., Azizi, S. & Ghaderzadeh, A. A fuzzy approach for optimal placement of IoT applications in fog-cloud computing. Cluster Comput. 25, 303–320 (2022).
Sriraghavendra, M., Chawla, P., Wu, H., Gill, S. S. & Buyya, R. DoSP: A deadline-aware dynamic service placement algorithm for workflow-oriented IoT applications in fog-cloud computing environments. Energy conservation solutions for fog-edge computing paradigms, 21–47 (2022).
Taghizadeh, J., Ghobaei-Arani, M. & Shahidinejad, A. A metaheuristic‐based data replica placement approach for data‐intensive IoT applications in the fog computing environment. Software: Pract. Experience. 52(2), 482–505 (2022).
Ghobaei-Arani, M. & Shahidinejad, A. A cost-efficient IoT service placement approach using whale optimization algorithm in fog computing environment. Expert Syst. Appl. 200, 117012 (2022).
Subbaraj, S., Thiyagarajan, R. & Rengaraj, M. A smart fog computing based real-time secure resource allocation and scheduling strategy using multi-objective crow search algorithm. J. Ambient Intell. Humaniz. Comput. 14(2), 1003–1015 (2023).
Sabireen, H. & Venkataraman, N. A hybrid and light weight metaheuristic approach with clustering for multi-objective resource scheduling and application placement in fog environment. Expert Syst. Appl. 223, 119895 (2023).
Kumar, M., Kishor, A., Singh, P. K. & Dubey, K. Deadline-aware cost and energy efficient offloading in mobile edge computing. IEEE Trans. Sustain. Comput. 9(5), 778–789 (2024).
Walia, G. K., Kumar, M. & Gill, S. S. AI-empowered fog/edge resource management for IoT applications: A comprehensive review, research challenges and future perspectives. IEEE Commun. Surv. Tutor. (2023).
Kumar, M., Walia, G. K., Shingare, H., Singh, S. & Gill, S. S. Ai-based sustainable and intelligent offloading framework for IIoT in collaborative cloud-fog environments. IEEE Trans. Consum. Electron. (2023).
Mangalampalli, S. et al. DRLBTSA: deep reinforcement learning based task-scheduling algorithm in cloud computing. Multimedia Tools Appl. 83(3), 8359–8387 (2024).
Goel, G. & Tiwari, R. IGWOA: Improved Grey Wolf optimization algorithm for resource scheduling in cloud-fog environment for delay-sensitive applications. Peer-to-Peer Netw. Appl. 17(3), 1768–1790 (2024).
Goel, G. & Tiwari, R. Task management in IoT-Fog-Cloud environment employing static scheduling techniques. ENP Eng. Sci. J. 2(1), 13–20 (2022).
Mahmud, R., Srirama, S. N., Ramamohanarao, K. & Buyya, R. Quality of experience (QoE)-aware placement of applications in fog computing environments. J. Parallel Distrib. Comput. 132, 190–203 (2019).
Baranwal, G., Yadav, R. & Vidyarthi, D. P. QoE aware IoT application placement in fog computing using modified-topsis. Mob. Networks Appl. 25(5), 1816–1832 (2020).
Nayeri, Z. M., Ghafarian, T. & Javadi, B. Application placement in fog computing with AI approach: taxonomy and a state of the art survey. J. Netw. Comput. Appl. 185, 103078 (2021).
Tang, Q., Xie, R., Yu, F. R., Huang, T. & Liu, Y. Decentralized computation offloading in IoT fog computing system with energy harvesting: a dec-POMDP approach. IEEE Internet Things J. 7(6), 4898–4911 (2020).
Feo, T. A. & Resende, M. G. Greedy randomized adaptive search procedures. J. Global Optim. 6, 109–133 (1995).
Ezugwu, A. E., Agushaka, J. O., Abualigah, L., Mirjalili, S. & Gandomi, A. H. Prairie dog optimization algorithm. Neural Comput. Appl. 34(22), 20017–20065 (2022).
Agushaka, J. O., Ezugwu, A. E. & Abualigah, L. Dwarf mongoose optimization algorithm. Comput. Methods Appl. Mech. Eng. 391, 114570 (2022).
Sun, G., Wang, Y., Yu, H. & Guizani, M. Proportional fairness-aware task scheduling in space-air-ground integrated networks. IEEE Trans. Serv. Comput. (2024).
Xia, J. Y. et al. Metalearning-based alternating minimization algorithm for nonconvex optimization. IEEE Trans. Neural Networks Learn. Syst. 34(9), 5366–5380 (2022).
Zhang, H., Yue, D., Dou, C. & Hancke, G. P. PBI based multi-objective optimization via deep reinforcement elite learning strategy for micro-grid dispatch with frequency dynamics. IEEE Trans. Power Syst. 38(1), 488–498 (2022).
Lin, L., Ma, X., Chen, C., Xu, J. & Huang, N. Imbalanced Industrial load identification based on optimized CatBoost with Entropy features. J. Electr. Eng. Technol. 19, 4817–4832 (2024).
Ding, C. et al. The intelligent traffic flow control system based on 6G and optimized genetic algorithm. IEEE Trans. Intell. Transp. Syst. (2024).
Peng, X., Song, S., Zhang, X., Dong, M. & Ota, K. Task Offloading for IoAV under extreme weather conditions using dynamic price driven double broad reinforcement learning. IEEE Internet Things J. (2024).
Xu, G. et al. A model value transfer incentive mechanism for federated learning with smart contracts in AIoT. IEEE Internet Things J. (2024).
Sun, G. et al. Low-latency and resource-efficient service function chaining orchestration in network function virtualization. IEEE Internet Things J. 7(7), 5760–5772 (2019).
Sun, G., Xu, Z., Yu, H. & Chang, V. Dynamic network function provisioning to enable network in box for industrial applications. IEEE Trans. Industr. Inf. 17(10), 7155–7164 (2020).
Funding
Not Applicable.
Author information
Authors and Affiliations
Contributions
All the authors are equally contributed to the paper.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Baskar, R., Mohanraj, E., Saradha, M. et al. Hybrid Prairie Dog and Dwarf Mongoose optimization algorithm-based application placement and resource scheduling technique for fog computing environment. Sci Rep 15, 1240 (2025). https://doi.org/10.1038/s41598-025-85142-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-025-85142-8
Keywords
This article is cited by
-
A refined Greylag Goose optimization method for effective IoT service allocation in edge computing systems
Scientific Reports (2025)
-
Hybrid multi objective marine predators algorithm based clustering for lightweight resource scheduling and application placement in fog
Scientific Reports (2025)
-
CAViaR Snow Leopard Optimization Algorithm for Multi-Objective IoT Service Placement Strategy in Fog Computing
SN Computer Science (2025)
-
I-OppoCSCA: an improved opposition-based chaotic sine cosine algorithm for IoT applications placement in fog computing
The Journal of Supercomputing (2025)