Abstract
In view of the problems of false property rights and difficulties in identity authentication in intellectual property transactions, an identity authentication model for intellectual property transactions based on an alliance chain is proposed. Firstly, the two-factor identity authentication model’s roles, functions, and processes are constructed. Secondly, the two-factor authentication mechanism of ID password combined with physiological and property rights features is proposed, the identity identification generation method of fingerprint biometrics and intellectual property features is established, and the constraint compression strategy based on Poseidon hash is designed to reduce the workload of zero-knowledge proof algorithm and realize the consistency of property rights identity. Finally, the security and performance analysis of the authentication model is carried out, and the comparison and validation of related models are carried out, which shows that the model has good security and reliability.
Similar content being viewed by others
Introduction
In the era when the Internet was not yet popularized, intellectual property transactions primarily relied on traditional carriers such as books, magazines, films, patents, and trademarks. They were conducted through third-party institutions with high transaction costs and prone to disputes. The rise of the Internet has brought new opportunities for intellectual property transactions, and networked transactions have broadened the transaction channels and lowered the transaction threshold. However, at the same time, the infringement of intellectual property rights in the network environment has become increasingly rampant, and its low-cost and highly covert characteristics have posed a challenge to the traditional intellectual property protection mechanism. Blockchain technology provides a new solution for intellectual property protection1 with its data non-tampering and decentralized characteristics. It can ensure the authenticity of transaction data, effectively prevent fraud, and realize the traceability of transactions and the clear division of responsibility. The alliance chain stands out among the many branches of blockchain with its efficient transaction performance and superior privacy protection2 capabilities. By limiting the participating nodes, the alliance chain safeguards the transaction efficiency while considering the participants’ privacy rights and interests. Applying alliance chain technology to intellectual property transactions is expected to fundamentally improve the security and transparency of transactions, reduce transaction costs, shorten the transaction cycle, and simplify the rights protection process.
Identity authentication is a critical link in intellectual property transactions, ensuring that the property rights and property rights owners are authentic and reliable. However, identity authentication has problems and challenges that need to be solved, such as identity authentication centrality, low security of single-factor authentication, incomplete protection of identity privacy, and low efficiency of identity authentication3,4. In the current research on identity authentication, Li Xiangyang et al.5 realized a blockchain-based intellectual property transaction platform in which the identity authentication link ensures identity security and data tampering in intellectual property transactions through digital certificates and digital signatures, etc. Still, it needs to rely on a trusted third party, and when the third party is attacked, it will impact the identity authentication system. Zhuang et al.6 introduced a blockchain-powered platform for intellectual property transactions, incorporating an enhanced Shamir secret-sharing method to ensure privacy protection and traceability of identities. Wu Fei et al.7 proposed an identity authentication scheme based on face recognition, which gives a new idea of identity authentication using biometric features. Niu Xiaolin et al.8 proposed a music copyright protection and transaction system based on an alliance chain, applying music fingerprints to copyright authentication. Si Haiping et al.9 relied on a trusted third party by distributing digital certificates applied to the identity authentication of agricultural intellectual property. Xi Xin et al.10 used the ECDH algorithm for information encryption in the digital authentication process. Still, the ECDH algorithm has the problem of impersonation of identity by intermediaries, and there is no identity authentication to guarantee the authenticity of the identity. Yuan et al.11 proposed a privacy-preserving intellectual property identity authentication method based on blockchain, which uses zero-knowledge proof for privacy protection. Zhang Guangzong et al.12 proposed an improved zero-knowledge algorithm for privacy protection, which reduces the computation of generating proof. However, there is still the problem of authenticity and reliability of identity. Y. Cheng et al.13 proposed an efficient anonymization authentication and privacy-preserving reliability assessment scheme, which protects the privacy of vehicle identities through anonymization techniques while assessing the reliability of crowdsourced data. However, it lacks integration with emerging technologies and fails to incorporate blockchain for better performance. X. Feng et al.14 proposed the PBAG protocol, which utilizes blockchain and global update commitments to achieve privacy-preserving authentication, improve authentication efficiency and solve the certificate revocation problem. However, as the number of vehicles increases, the updating and management of global commitments may become complicated. H. Sun et al.15 proposed a MTDCAP protocol to secure CAN bus authentication against potential attacks using mobile target defense. However, the increase in mobile target defense and authentication process may lead to an increase in communication delay and authentication time, which affects the real-time performance of the system.
To summarize, scholars have done a lot of work on improving the security of identity authentication, but there are still problems, such as low security of one-factor authentication, low efficiency of identity authentication, etc. There is little research on using a two-factor identity authentication mechanism in the identity authentication of intellectual property transactions. Not enough attention is paid to the privacy protection problem in the identity authentication process. In view of the issues and challenges of identity authenticity, security, privacy protection, and authentication efficiency in the identity authentication of intellectual property transactions, this paper designs a two-factor identity authentication model for intellectual property transactions based on improved zero-knowledge proof, aiming to construct a comprehensive identity authentication framework that integrates the characteristics of alliance blockchain and intellectual property transactions, which is composed of three core entities: the regulator, the demand side and the supply side. The work of this article is as follows:
-
1.
An authentication method combining improved zero-knowledge proof with fingerprint biometrics and property right feature identification technology is designed to complete authentication without revealing the identity mark and protect privacy.
-
2.
Designed a two-factor authentication mechanism combining ID password with fingerprint and property right feature identification to improve the security and reliability of authentication.
-
3.
The zero-knowledge proof is improved to reduce the proof computation and size and improve the efficiency of proof generation and verification.
-
4.
This design uses alliance chain technology to construct a decentralized identity authentication model and combines smart contracts to execute the corresponding authentication process automatically.
The biggest innovation of this paper is to design a two-factor authentication model based on an alliance chain for intellectual property transactions. A two-factor authentication mechanism combining ID passwords with physiological and property rights characteristics is proposed. The integration of alliance chain technology and smart contracts constructs a decentralized and automated authentication process that improves the security and efficiency of intellectual property transactions. Combining improved zero-knowledge proof with fingerprint biometrics and property rights characterization, this approach ensures authentication without revealing sensitive information, thereby protecting privacy. In addition, improved zero-knowledge proofs reduce computational complexity and proof size, thereby increasing the efficiency of proof generation and verification.
Next, a two-factor authentication model for intellectual property transactions based on improved zero-knowledge proof will be presented, model analysis and experiments will be conducted, and conclusions will be drawn.
Two-factor authentication model for intellectual property transactions based on improved zero-knowledge proof
Overall framework model
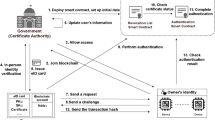
The overall framework model design is shown in Fig. 1. The model contains five entities: supply side, demand side, regulator, chain of alliance, and database, which play the following roles in this model:
-
(1)
Supply-side: It refers to the entity that owns intellectual property rights, including patents, trademarks, or copyrights, or an entity that has the right to authorize the disposal thereof and may put its intellectual property resources on the market for trading or licensing.
-
(2)
Demand-side: A person or organization needs to use or access intellectual property and wants to hide who they are and what they do.
-
(3)
Supervisors: Supervisors are responsible for supervising the process of intellectual property transactions to ensure their legality and compliance.
-
(4)
Alliance Chain: A platform for conducting intellectual property transactions, which ensures the proper conduct of transactions by incorporating intelligent contracts. It can be used to record transaction information and ensure the integrity and authenticity of data. It also combines cryptography and other technologies to protect identity privacy.
-
(5)
Database: Used to store user identity information, i.e., hashed fingerprint biometrics.
Two-factor authentication primary process for intellectual property transactions
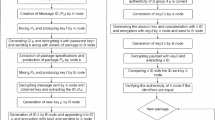
As shown in Fig. 2, the total two-factor authentication process is divided into four stages: the ID password identity registration stage, fingerprint and intellectual property identity registration stage, ID password identity authentication stage, and fingerprint and intellectual property identity authentication stage. The two-factor authentication stage is carried out through the two-factor authentication of ID password, fingerprint, and property rights recognition; firstly, according to the registered ID password to log in to the account belongs to the first factor of authentication, and then through the collection of fingerprint biometrics and intellectual property identity features to generate a zero-knowledge proof to the verifier for the second factor of authentication.
ID password identity registration phase
The transaction parties first register their identity information on the alliance chain, and this model proposes a two-factor identity registration mechanism with an ID password combining physiological and property rights characteristics. The identity registration stage first needs to carry out the design of ID password registration, enter the user ID and password, and determine whether it is empty; if it is empty, then registration failure, not empty, continue to determine whether the ID has been registered, if it has been registered, registration failure, if it is not registered, hash encrypted storage on the alliance chain, return “Success” indicates that Successful registration.
Fingerprinting and title identity registration phase
ID password identity registration after both parties go through the optical fingerprint identification module in accordance with the prompts to enter the fingerprint and extract the fingerprint features to generate a template to determine whether it is empty; if it is empty, then the registration fails, not empty, then the fingerprint biometrics encrypted with Poseidon hash function. Encrypting the fingerprint data first ensures that the fingerprint information is always processed and stored in an encrypted form, thus protecting the user’s privacy and improving data security. Then, determine whether the encrypted fingerprint has been enrolled; if it has been enrolled, the enrollment fails; if it has not been enrolled, the hash-encrypted fingerprint will be stored in the database and return “Success” to indicate successful enrollment. The supplier provides the intellectual property transaction certificate consisting of intellectual property introduction, encrypted intellectual property feature information, transaction money, and access time and publishes it on the alliance chain to complete the registration of intellectual property identity after the regulator’s audit.
ID password authentication phase
A transaction is initiated after the two-factor identity is registered and the two-factor identity authentication phase is entered. The demand side checks the intellectual property transaction certificate on the chain. If it wants to carry out a transaction, it initiates the transaction and then enters the identity authentication stage. In the authentication stage, it is necessary to design ID and password authentication first, input the user ID and password, and determine whether they are empty; if they are empty, the authentication fails; if they are not empty, then continue to query whether the ID has been registered on the alliance chain, if not, the authentication fails, if it has been registered, then verify whether the ID and password match and if it matches. It returns “Success. Successful matching will return “Success.”
Fingerprint and title identification phase
After successfully completing ID password authentication, the next step is to perform fingerprint and property rights authentication. In this phase, a zero-knowledge proof algorithm is used to handle biometric and intellectual property features for identification. This algorithm can generate and verify the required proof without revealing personal privacy information. Specifically, the system will ask for proof generated by the zero-knowledge proof algorithm, and if this proof passes the validation, the system will return “true,” indicating that the fingerprint and intellectual property identity verification was successful.
Improved zero-knowledge algorithm design for two-factor authentication in intellectual property transactions
The relevant notations are defined in Table 1.
In the fingerprinting and title authentication phase, an improved Plonk zero-knowledge proof algorithm is designed to generate zero-knowledge proof and validate it through regulators and counterparties. Plonk (Permutations over Lagrange-bases for Oecumenical Noninteractive arguments of Knowledge) is a zero-knowledge proof algorithm for generalized trusted settings. The general trusted setup allows the same SRS to be used for all circuits of a certain bounded size, and it can be updated by new parties without compromising security. And the soundness of the system requires only the honesty of one of all updates before that point in time. This feature removes a major obstacle to deploying zk-SNARKs in the real world. Polynomial commitments are a crucial part of PlonK, allowing the prover to commit to a polynomial and later prove evaluations of that polynomial at specific points. Plonk algorithm uses a batched version of the KZG polynomial commitment scheme to efficiently commit to and evaluate polynomials. Furthermore, Plonk is a non-interactive zero-knowledge proof protocol, meaning that no multiple rounds of interaction between the prover and the verifier are required.
The design of the improved zero-knowledge algorithm for two-factor authentication of intellectual property transactions is divided into three phases: initialization, generation of zero-knowledge proof, and verification of zero-knowledge proof. Firstly, initialization is carried out to design the private input carrying the private identity information of both parties of the transaction, such as fingerprint biometrics and intellectual property characterization information, and the public input is the encrypted fingerprint biometrics and encrypted intellectual property characterization information of both parties of the transaction, and the final output is the circuit to judge whether the private input and the public input are equal or not so as to generate the public parameter. Second, Plonk zero-knowledge proof is generated based on the public parameters, and a constraint compression strategy based on Poseidon hashing is designed to reduce the workload. Finally, the regulator and the counterparty view the zero-knowledge proof and verify it.
-
1.
Initialization: the circuit needs to be set up initially SRS (Structure Reference String). Since Plonk’s zero-knowledge proof algorithm is generalized and trustworthy, only one trustworthy communication setup is needed for the circuit. Then, the public parameter PP is generated based on the circuit’s design, which includes the initial setup and circuit parameters.
-
2.
Generating zero-knowledge proof: generating zero-knowledge proof based on the public parameter PP is divided into five steps as follows:
-
(a)
Compute polynomials a(x), b(x), c(x) over the multiplicative subgroup group H of order n, where a(x) is the private input of the private identity information of the two parties to the transaction, b(x) is the public input of the hashed encrypted identity information of the encrypted fingerprint biometrics in the database or of the intellectual property features in the intellectual property transaction certificates, and c(x) is the output for determining whether or not the outputs are equal if the output is 0 then it is equal, and if it is not 0, then it is not equal.
-
(b)
Perform permutation substitution constraint construction z(x).
-
(c)
The total constraint of Eq. (1) is constructed by transforming the gate constraint and the permutation substitution constraint into a polynomial t(x).
-
(d)
The construction of the critical intermediate function r(x) is represented in Eq. (2). This function encapsulates the components that need to be kept secret during the proof process. Because the polynomial promises the highest height of n + 2, we need to perform the power reduction operation; here, the Poseidon hash function is used to improve and simplify the size of the proof.
-
(e)
Construct polynomial commitments at \(\:{\uptheta\:}\),\(\:{\uptheta\:}{\upomega\:}\)two points to generate Plonk zero-knowledge proof \(\:{\uppi\:}\). Equation (3) denotes a polynomial over \(\:{\uptheta\:}\) points and Eq. (4) denotes a polynomial over \(\:{\uptheta\:}{\upomega\:}\).
The final proof of generation:
-
3.
Verifying zero-knowledge proof: The regulator and the counterparty check that the elements in the generated proof \({{\uppi}}\) satisfy the properties of the group and the domain.Calculated to validate the relevant commitments as in Eqs. (5–7).
Finally, through the Eq. (8) bilinear mapping verification proof, if the equation is valid, then it means that the input authentication information is consistent with the actual and successfully passes the fingerprint and title identity authentication stage; if the equation is not valid then it means that the input authentication information is inconsistent with the actual, and there may be the behavior of fake identity, and the regulator will be further regulated. Among them, a constraint compression strategy based on Poseidon hash is designed to generate zero-knowledge proof, which reduces the workload and complexity of zero-knowledge proof and, at the same time, improves the efficiency of generating and verifying zero-knowledge proof, thus improving the efficiency of the whole model.
Model analysis
Model security analysis
This model provides unforgeability, reliability, zero-knowledge, and completeness applicable to identity authentication by designing an improved Plonk algorithm for identity privacy protection and using two-factor authentication with ID password and fingerprint. Table 2 shows the comparison of security of authentication models, comparing this model with models of other schemes. As can be seen from the table, literature16,17,18 do not support two-factor authentication and perform poorly in terms of reliability, zero knowledge, and completeness. Literature19 and 20perform better in terms of identity unforgeability, reliability, zero-knowledge, and completeness but do not support two-factor authentication. Literature16,18 do not design algorithms for identity privacy preservation, and literature17,20 do not implement identity unforgeability.
Model performance analysis
Tables 3 and 4 show the model proof generation and validation performance analysis, respectively, where m denotes the number of wires, n denotes the number of multiplication gates, and a denotes the number of addition gates, \(\:{\mathbb{G}}_{1}\) and \(\:{\mathbb{G}}_{2}\) are groups defined on different elliptic curves, \(\:\mathbb{F}\) is a finite prime number field, \(\:\mathcal{l}\) indicates the number of public inputs, and \(\:\text{P}\) indicates the number of pairwise operations. As shown in Table 3, the Groth16 algorithm has some limitations in the general trusted setup, the Auroralight algorithm lacks simplicity, and in terms of the workload of the certifiers, it can be seen that the Sonic algorithm has an enormous amount of workload of the certifiers, while our algorithm has some advantages in terms of the relatively low workload of the certifiers. Among them, seven times in our algorithm perform exponential operation operations on the group \(\:{\mathbb{G}}_{1}\)defined by elliptic curves and compute the number of domain multiplications by eight FFTs of scale 4n, five FFTs of scale 2n, and twelve FFTs of scale n. Since n is related to a in the actual circuits, here n and a are combined and denoted as (n + a), which ultimately approximates to 7n + 7a and 54(n + a ) log(n + a) results. Our algorithm, onic algorithm, and Plonk algorithm all have a general trusted setup and simplicity, and as can be seen from the table, our algorithm is relatively small in terms of proof size. As shown in Table 4, there is Additional ancillary work for the Auroralight algorithm, in terms of the workload of validators, Plonk’s algorithm and our algorithm perform two matching operations and our algorithm performs relatively fewer exponential operations on group \(\:{\mathbb{G}}_{1}\) defined by elliptic curves.
Test
Experimental environment
The model is implemented by Snarkjs, the circuit is written by Circom language, the model implementation process is simulated, and finally, the verified smart contract is deployed in the Remix test. The experimental environment is as follows: host model ASUS ROG Strix Scar 7, Intel(R) Core(TM) i5-9300 H CPU @ 2.40 GHz.
Experimental process
First, the design of the circuit is carried out with private inputs for private information and public inputs for encrypted private information and outputs are equal if they are zero, as shown in Fig. 3.
The model circuit is designed, and the circuit is compiled, as shown in Fig. 4.
Generation and validation of the required public parameters and setup files through the Plonk zero-knowledge proof framework, as shown in Figs. 5 and 6.
This command is used to export the validation key from the generated .zkey file, which is the file used to validate the proof during the zero-knowledge proof process, as shown in Fig. 7.
Then, the property owner private inputs the intellectual property characterization information, such as the application number of the patent, and the regulator public inputs the encrypted property feature information obtained from the certificate of the intellectual property transaction, as shown in Fig. 8.
This command is used to verify that a given zero-knowledge proof witness file is consistent with the circuit, as shown in Fig. 9.
Perform 100 experiments for generating proofs and 100 experiments for verifying proofs and put the records in files, as shown in Fig. 10. The specific values are shown in Figs. 11 and 12.
The time for zero-knowledge proof generation is shown in Fig. 13, and the experiment was conducted to generate 100 proofs with an average proof generation time of 0.42346 s.
The time for verification of zero-knowledge proof is shown in Fig. 14; the experiment was carried out for 100 proofs, and the average proof verification time was 0.19119 s.
As shown in Fig. 15, for the verification pass, the verification experiment is carried out by deploying the verification smart contract to the chain, and the final output “true” indicates that the verification passes and the experiment is completed.
As shown in Table 5, as in the case of the same size of the circuit input data, this model improves the authentication time in the fingerprint authentication stage, thus improving the efficiency of identity authentication for intellectual property transactions.
Conclusions
In view of the problems of false property rights and difficulties in identity authentication in intellectual property transactions, this paper proposes an identity authentication model for property rights transactions based on the alliance chain, aiming to improve the security and credibility of the transactions. Firstly, by constructing a two-factor identity authentication model, the responsibilities, functions, and authentication process of each role in the model are clarified, which provides a theoretical basis for the realization of the model. On this basis, this paper proposes a two-factor authentication mechanism that combines ID passwords, individual physiological features, and property rights features and utilizes fingerprint biometrics and intellectual property features to generate identity markers, which ensures the uniqueness and authenticity of the identity of the subject of the transaction. In order to further enhance the efficiency and security of the authentication process, this paper designs a constraint compression strategy based on the Poseidon hash algorithm, which effectively reduces the computational burden of the zero-knowledge proof algorithm in the execution process and optimizes the performance of the authentication model. In addition, this paper also combines the models used in other kinds of literature to carry out a comparative analysis of the security of the authentication model, ensuring that this model is applicable to the characteristics of unforgeability, reliability, zero-knowledge, and completeness of identity authentication, and verifies the model performance. Through comparison and verification, the study shows that the two-factor identity authentication model based on the alliance chain can not only effectively reduce the risk of false identity and property right information forgery in intellectual property transactions but also ensure the accuracy of identity authentication of the two parties in the transaction while carrying out privacy protection, and improve the security and efficiency of the transaction process. This model has a wide range of potential applications, especially in the fields of digital assets and smart contracts, and can provide a more secure and reliable solution for the protection and transaction of intellectual property rights in the future.
In summary, the identity authentication model based on the alliance chain proposed in this paper shows strong advantages in intellectual property transactions, and its security, reliability, and efficiency make it an important technological breakthrough in the field of intellectual property protection, which provides strong support for further promoting the application of blockchain technology in intellectual property protection.
Data availability
The raw data used during the current study are available from the corresponding author upon reasonable request.
References
Huang, W. & Qiu, S. On the role of blockchain technology in the protection of intellectual property rights. J. Nanchang Univ. (Human. Soc. Sci.) 51(02), 67–76. https://doi.org/10.13764/j.cnki.ncds.2020.02.007 (2020).
Sun, S. et al. A survey on privacy Protection technologies for Consortium blockchains. J. Chongqing Univ. Posts Telecommunications (Natural Sci. Edition) 36(01), 9–19 (2024).
Kongolo, T. Intellectual Property and Emerging Technologies: Generated Global IP Issues and Challenges (Taylor Francis, 2024). https://doi.org/10.4324/9781003309086.
Jia, Y. & Yu, M. Exploration of the innovation and development path of intellectual property transaction system. China Dev. Observ. Z2, 157–162 (2023).
Li, X. et al. Research and implementation of blockchain-based intellectual property trading platform. Comput. Eng. Appl. 59(03), 308–316 (2023).
Zhuang, C., Dai, Q. & Zhang, Y. B. C. P. P. T. A blockchain-based privacy-preserving and traceability identity management scheme for intellectual property. Peer-to-Peer Netw. Appl. 2022, 1–15 (2022).
Wu, F., Zeng, W. & Wang, Y. Research and application of user identity reliable authentication technology based on face recognition. World Commun. 03, 190–192 (2015).
Niu, X., Han, D. & Sun, Z. Consortium blockchain-based music copyright protection and trading system. Comput. Application Res. 39(01), 18–23. https://doi.org/10.19734/j.issn.1001-3695.2021.06.0241 (2022).
Si, H. et al. Research on the confirmation of agricultural intellectual property rights based on consortium chain. Sci. Technol. Manage. Res. 43(13), 119–126 (2023).
Xi, X., Tang, J. & Zhao, P. Design and algorithm improvement of blockchain data sharing system based on ECDH algorithm. J. Taiyuan Normal Univ. (Nat. Sci. Ed.) 22(03), 51–58 (2023).
Yuan, S., Yang, W., Tian, X. & Tang, W. A blockchain-based privacy-preserving intellectual property authentication method. Symmetry 16(5), 622. https://doi.org/10.3390/sym16050622 (2024).
Zhang, G. & Research on the privacy protection model of data sharing based on blockchain. Cent. Univ. Finance Econ. https://doi.org/10.27665/d.cnki.gzcju.2022.001967. (2022).
Cheng, Y. et al. Efficient Anonymous authentication and privacy-preserving reliability evaluation for Mobile Crowdsensing in Vehicular Networks. IEEE Internet Things J. 10(17), 14925–14939. https://doi.org/10.1109/JIOT.2023.3259961 (2023).
Feng, X., Cui, K., Wang, L., Liu, Z. & Ma, J. PBAG: a privacy-preserving blockchain-based authentication protocol with global-updated commitment in IoVs. IEEE Trans. Intell. Transport. Syst. 25(10), 13524–13545. https://doi.org/10.1109/TITS.2024.3399200 (2024).
Sun, H. et al. MTDCAP: moving target defense-based CAN authentication protocol. IEEE Trans. Intell. Transport. Syst. 25(9), 12800–12817. https://doi.org/10.1109/TITS.2024.3384054 (2024).
Lai, T. et al. A privacy protection and authentication method for fingerprint biometric features. Commun. Technol. 54(09), 2202–2207 (2021).
Dai, J. Analysis of blockchain-based vehicle networking identity authentication scheme. Integr. Circ. Appl. 41(07), 52–53. https://doi.org/10.19339/j.issn.1674-2583.2024.07.020 (2024).
Wan, H. et al. A blockchain identity authentication method based on quantum key. Softw. Eng. 26(04), 38–41. https://doi.org/10.19644/j.cnki.issn2096-1472.2023.004.009 (2023).
Jiang, J. Research on blockchain-based privacy protection cross-domain identity authentication. Southeast. Univ. https://doi.org/10.27014/d.cnki.gdnau.2023.002373 (2023).
Zhu, J. Research on the identity authentication mechanism of technology services based on consortium chain. Hainan Univ. https://doi.org/10.27073/d.cnki.ghadu.2023.000377 (2023).
Liu, A., Du, X., Wang, N. & Li, S. Blockchain-based big data access control mechanism. J. Softw. 30(9), 2636–2654 (2019).
Gabizon, A., Williamson, J. Z., Ciobotaru, O. & Plonk Permutations over Lagrange-bases for Oecumenical Noninteractive Arguments of Knowledge 2019953 (IACR Cryptology ePrint Archive, 2019).
Yuan, S., Yang, W., Tian, X. & Tang, W. A. A blockchain-based privacy preserving intellectual property authentication method. Symmetry 16, 622. https://doi.org/10.3390/sym16050622 (2024).
Acknowledgements
This work was supported by the Key R&D Project of Hainan Province under Grant ZDYF2024GXJS024.
Author information
Authors and Affiliations
Contributions
Conceptualisation, S.M. and W.F.; methodology, S.M.; software, S.M.; validation, S.M., W.F., Z.W. and Y.L.; formal analysis, S.M.; investigation, S.M.; resources, M.H. and S.F.; data curation, S.M.; writing—original draft preparation, S.M.; writing—review and editing, W.F.; supervision, M.H.; project administration, S.F.; funding acquisition, W.F. All authors have read and agreed to the published version of the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Mo, S., Feng, W., Huang, M. et al. Two-factor authentication for intellectual property transactions based on improved zero-knowledge proof. Sci Rep 15, 5974 (2025). https://doi.org/10.1038/s41598-025-89597-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-025-89597-7
Keywords
This article is cited by
-
A consortium blockchain-based sealed electronic auction scheme utilizing attribute-based hybrid encryption
The Journal of Supercomputing (2025)