Abstract
We propose a fault-tolerant scheme for generating long-range entanglement at the ends of a rectangular array of qubits of length R with a square cross-section of \(m=O({\log }^{2}R)\) qubits. It is realized by a constant-depth circuit producing a constant-fidelity Bell-pair (independent of R) for local stochastic noise of strength below an experimentally realistic threshold. The scheme can be viewed as a quantum bus in a quantum computing architecture where qubits are arranged on a rectangular 3D grid, and all operations are between neighboring qubits. Alternatively, it can be seen as a quantum repeater protocol along a line, with neighboring repeaters placed at a short distance to allow constant-fidelity nearest-neighbor operations. To show our protocol uses a number of qubits close to optimal, we show that any noise-resilient distance-R entanglement generation scheme realized by a constant-depth circuit needs at least \(m=\Omega (\log R)\) qubits per repeater.
Similar content being viewed by others
Introduction
The ability of operating on spatially separated qubits has been recognized early on as a key requirement for a working quantum computer1,2. Long-range quantum communication is also a fundamental primitive at the core of quantum information-theoretic3,4,5 and cryptographic6,7 protocols in quantum networks, as well as e.g., distributed quantum computation8,9,10 or distributed sensing11,12. With increasingly powerful capabilities of present-day devices that can act as local nodes in such a network, finding appropriate protocols for entanglement sharing and quantum communication over faulty networks remains an active and central theme of present-day research.
Here we focus on long-range entanglement generation schemes which can be used in quantum computing devices where two-qubit operations are restricted to be geometrically local. This kind of restriction typically arises from technological constraints and is determined by the geometric arrangement of qubits in space as well as limits on the ability to couple distant qubits. Quantum algorithmic and fault-tolerance-related constructions, on the other hand, typically do not refer to notions of geometric locality. For example, while recent quantum low-density parity check (LDPC) codes are seen as excellent candidates for resource-efficient realizations of fault-tolerant quantum computing, their application involves long-range interactions when qubits are embedded in Euclidean space: A recent result implies that the number of such long-range gates needed scales at least polynomially with the size of the code13. This motivates the need to design protocols for realizing long-range interactions. Using teleportation, this goal can be rephrased as that of generating a long-range Bell pair in a short time with local operations. Any corresponding construction, such as ours, can be used as a quantum (data) bus in scalable quantum devices14.
Our proposal addresses the specific constraints on near-term devices by optimizing the following aspects:
-
(i)
qubit efficiency versus distance: Our protocol fault-tolerantly generates a Bell pair on two qubits separated by distance R, using a grid of qubits of size d × d × R with \(d=O(\log R)\). That is, it uses only \(O(R{\log }^{2}R)\) qubits in total.
-
(ii)
simplicity (geometric locality) of operations: Our scheme only involves one- and two-qubit gates between nearest-neighbor qubits in the architecture. The architecture could be realized, e.g., by stacking planar chip-like devices, and connecting neighboring devices through the third dimension.
-
(iii)
resilience to general errors: we provide a rigorous proof of the robustness of our scheme in the form of a fault-tolerance threshold theorem allowing for fully general (circuit-level) local stochastic noise15. In this model, a random (multiqubit) Pauli error Et acts on the system at each time step t of the quantum circuit. The probability that the Pauli error Et at each time step t acts non-trivially on any subset of k qubits is assumed to be at most pk for some p ∈ [0, 1]. The parameter p is called the strength of the local stochastic noise, and we write \({E}_{t} \sim {\mathcal{N}}(p)\). This notion only depends on the marginal distribution of Et. In particular, our analysis captures situations where errors are correlated both in space and time, and we assume all involved operations (state preparation, gates and measurements) to be non-ideal, i.e., affected by noise. We note that – because of the simplicity of the scheme — we can explicitly specify and analyze all involved operations without resorting to fault-tolerant gadgets (e.g., for encoding and recovery) that are often treated in a black-box manner.
-
(iv)
short coherence times and minimal latency: The required coherence time of each qubit is independent of the overall communication distance R: It only needs to be of the order of the local operation time tlocal. This is the maximal time needed to perform a single- or two-qubit gate, a single-qubit measurement, or an entangling gate between two neighboring qubits.
Our protocol minimizes the amount of time Tent it takes to establish long-range entanglement from a product state of all qubits. The long-range entangled state is available after a time of order Tent = O(tlocal).
In the area of quantum computing architectures, our protocol could be especially beneficial in settings where gates or measurements need to be performed between spatially distant qubits. Such a need arises for example when using a quantum low-density parity check (LDPC) code whose stabilizer generators are not spatially local. With our scheme, we can design a quasi-2D architecture that allows for the application of joint measurements on any subset of size ℓ = O(1) of a total of n qubits, see Fig. 1. Each such ℓ-qubit measurement is executed with constant fidelity in a constant amount of time (up to Pauli correction whose classical postprocessing can typically be deferred to a later stage). The architecture requires \(O(n\cdot {\mathsf{polylog}}(n))\) qubits in total. When combined with the recently discovered good quantum LDPC codes that have parameters close to optimal16, this logarithmic overhead only leads to an encoding rate that decays as an inverse polylogarithmic function.
This architecture allows to perform a joint measurement on any subset of ℓ qubits (illustrated here for ℓ = 3) with constant fidelity by “busing” the corresponding qubits to the same location before the measurement, and subsequently transferring the qubits back. The transfer is achieved by teleporting the qubits using the long-range entanglement established with our protocol on each bus.
Our scheme provides a candidate architecture for transferring quantum information within a quantum device, but can alternatively also be used to transfer information between devices. In this setting, one typically considers a line of R equidistantly placed repeaters, where each repeater controls m qubits, neighboring repeaters are connected by (imperfect) quantum communication as well as classical communication links, and the goal is to establish entanglement between the first and the last repeater (separated by a distance proportional to R − 1). Assuming that every repeater has full control over its qubits, i.e., can apply any quantum circuit, this setup allows (by teleportation between repeaters) to imperfectly realize an adaptive quantum circuit on mR qubits which only uses gates between pairs of qubits associated with neighboring repeaters, and gates acting only on its own qubits. Any repeater protocol for distance-R entanglement generation amounts to a circuit of this form, and, conversely, circuits with these restrictions can be seen as repeater protocols.
In our architecture, qubits are located on the sites of a slab-like 3D rectangular lattice of dimensions d × d × R. We can define, for each j ∈ {1, …, R}, a repeater \({{\mathcal{R}}}_{j}\) which is composed of the qubits in the “slice” {1, …, d} × {1, …, d} × {j}. Then our circuit construction immediately translates into a repeater protocol with the following desirable features for each repeater:
-
(a)
long communication distance: As a function of the total communication distance R, every repeater only needs to manipulate \(m=O({\log }^{2}R)\) number of qubits. This is in line with the best currently known proposals17,18 which have poly-logarithmic scaling for long-range quantum communication. We also provide a converse bound \(\Omega (\log R)\) on the number of qubits per repeater for low-latency protocols as considered in this work.
-
(b)
simplicity of involved operations: Assuming the repeaters are connected appropriately (by m links along the direction of communication), all operations at each repeater \({{\mathcal{R}}}_{j}\), j ∈ {1…, R} are geometrically local when the \(m=O({\log }^{2}R)\) qubits are arranged on a 2D array.
In contrast, in existing works on repeater-based quantum communication, repeaters are often assumed to provide universal quantum computing power locally, and no geometric locality considerations are taken into account. For example, in ref. 19, the authors discuss entanglement distribution protocols which use quantum error-correcting codes17,18,20,21. This family of protocols proceeds by communicating encoded quantum information: Repeaters apply a recovery operation to each codeblock before retransmitting the entire block to the next repeater. This operation is arguably more involved that the operations required in our scheme.
Purely error-correction based schemes have a loss-tolerance limited by 50% because of the no-cloning theorem. To sidestep this limitation, the more recent work22 combines error correction with hashing-based entanglement purification. In this scheme, intermediate error correction operations are realized based on stabilizer (resource) states prepared at each repeater. The proposed scheme achieves a constant rate of qubit transmission. Here error correction is based on measurement-based gate teleportation using special (graph) states encoding the recovery map at each repeater location. While such schemes are ultimately desirable, the generation of these resource states is arguably more challenging to realize with near-term devices than the protocol discussed here. In particular, protocols preparing these resource states require long-range gates and non-constant circuit depth in each repeater. These operations are more involved that those in our scheme, and, in particular, do not give a low-latency scheme because of the extensive circuit depth.
-
(c)
resilience to full circuit-level local stochastic noise: It is sufficient if each repeater realizes circuits up to local stochastic noise. In particular, no fault-tolerant quantum computer is needed at any one of the repeaters.
In contrast to our circuit-level analysis, existing proposals often resort to the black-box use of fault-tolerant gadgets (e.g., for encoding and recovery), essentially amounting to the assumption that each repeater has full quantum fault-tolerance capabilities. Furthermore, existing works on quantum repeaters argue that faulty operations can be modeled by erroneous communication links (or corresponding Bell states) by commuting errors forward respectively backward in time. Errors arising in this way are generally not going to identically and independently distributed. Nevertheless, the provided analysis in existing works typically assumes this i.i.d. form of the noise. Our work overcomes this mismatch between the actually occuring noise and the error analysis by avoiding such simplistic assumptions altogether.
-
(d)
constant coherence times and minimal latency: Every repeater only needs to maintain coherence for a time of order tlocal. Furthermore, the long-range entangled state is available after a time of order Tent = O(tlocal). In particular, no quantum memory with a scalable qubit lifetime is required.
In contrast, the time Tent to establish long-range entanglement scales at least linearly with the total communication distance R in several existing protocols based, e.g., on transmitting encoded information successively between neighboring repeaters18,21. We note that these protocols reach the scaling O(tlocal) per generated Bell pair asymptotically when operated continuously, i.e., this is an achievable rate of communication. In contrast, the quantity Tent measures the latency when starting to run the scheme, and may be particularly relevant in near-term applications in scenarios where continuous operation is challenging.
Entanglement distribution protocols satisfying a low-latency property can be considered as those with repeaters that cannot store quantum information fault-tolerantly for a long time. In ref. 23, entanglement distribution protocols are classified into the following two groups: The first group involves quantum memories of limited lifetime24,25,26, whereas the second group relies on quantum memories with sufficiently long lifetimes23,27,28,29,30,31,32,33,34,35. The protocols belonging to the first group are closer to our criteria. We emphasize, however, that our protocol does not assume the availability of any quantum memory: all qubits, including idling ones, are assumed to be affected by noise.
While these properties are desirable features of quantum repeater protocols, we emphasize that our construction applies only to a certain regime where the inter-repeater links are relatively noise-free. This is a fundamental difference between the noise model considered here, and that typically studied in the long-distance quantum communication setting. It is only because of our assumptions on the noise model that we can achieve the low-latency property (d).
In more detail, most existing works discussing long-distance entanglement distribution consider error models motivated by quantum communication applications, e.g., transmission of qubits over an optical fiber. To highlight the main difference to our setup, consider first the error strength. In the optical setup, it is typically assumed that the fidelity of entangling gates between neighboring repeaters is very low. This assumption is meaningful when repeaters are separated by a certain distance, and entanglement is established by distributing a (physical) Bell state through the optical fiber. The loss (or error) rate then depends on the distance between repeaters, and can be any (small) constant for a fixed inter-repeater distance. This issue is typically addressed by generating higher-fidelity Bell pairs between repeaters by means of extra processes such as entanglement distillation. The complexity of these distillation steps precludes the possibility of a generation scheme having the low-latency property (d) in the setting of high error rates. (We refer to ref. 19 for a comparative study of different approaches to long-distance entanglement distribution. This includes a classification of protocols into three generations and a discussion of what kind of noise is handled by each generation of protocols).
In contrast, we assume constant-strength local stochastic noise – which, in the setting of repeaters, roughly means that entangling gates between neighboring repeaters can be realized with a fidelity above some threshold value. Such a regime of low error rates corresponds to a setting where the spacing between repeaters is limited, i.e., they cannot be arbitrarily far apart. In this case, low-latency long-distance entanglement is possible.
Our setup (as described by (c)) differs in another important aspect from commonly made assumptions in quantum communications: Our analysis also applies to correlated errors. This makes our protocol particularly attractive for using it as a quantum bus (rather than for point-to-point communication), as quantum computations can propagate errors leading to correlations between different timesteps. Analysing only independent errors will generally not be sufficient to ensure the protocol is suitable for use in noisy quantum computational devices.
To motivate the problem of fault-tolerant long-distance entanglement generation with low latency, let us recall entanglement swapping. We consider R sites (or “repeaters”) lying on a line, where each pair of neighboring sites shares a Bell state \(\left\vert \Phi \right\rangle :=(\left\vert 00\right\rangle +\left\vert 11\right\rangle )/\sqrt{2}\), see Fig. 2(a). Suppose we measure two qubits at each site in the Bell basis. Then, the resulting two-qubit state on two opposite sites on the line is one of the Bell basis states, which is determined by the measurement results. By applying an appropriate Pauli correction operator, we obtain the Bell state \(\left\vert \Phi \right\rangle\) with certainty if all operations are perfect.
Every gate acts on qubits within a single repeater or on a pair of qubits associated with two neighboring repeaters. Each construction has a constant circuit depth independent of the entanglement distance R. (a) Entanglement swapping circuit. It generates a Bell state of two qubits indexed by q1 and q2 with certainty, but it is not fault-tolerant under noise, such as i.i.d. measurement error. (b) Our protocol. Each repeater has m qubits. The gates \({\mathsf{H}}\) and \({\mathsf{CZ}}\) are tensor products of Hadamard gates and controlled-Z gates, respectively, on certain subsets of qubits clarified in Result.
Here, we may replace the preshared Bell pairs in this protocol with the computational basis state followed by a Hadamard gate and a CNOT gate, and we can also replace Bell measurements with entangling gates followed by the computational basis measurements. Then the protocol can be written as an adaptive quantum circuit of constant depth, where two-qubit gates act on neighboring sites only. Since the depth is constant, the latency of the protocol without the correction remains constant even if R increases, thus giving us property (d).
However, entanglement swapping is not fault-tolerantly scalable in the presence of noise. Suppose we have i.i.d. noise on the measurement results, i.e., there is a non-zero constant p such that each measurement result is flipped with probability p, independently. Then, the probability that the resulting state is Φ exponentially converges to 1/4 as the communication distance increases. This motivates us to introduce more qubits per site to make protocols fault-tolerant; see the initial state of the protocol in Fig. 2(b).
The protocol we propose here uses quantum error correction, and is a close relative of the protocols discussed in ref. 19. Indeed, one interpretation of the corresponding architecture is that it encodes logical information into a surface code at each repeater. We emphasize, however, that this only motivates the scheme in a similar way, e.g., cluster-state measurement-based quantum computation is related to braiding surface code anyons. For example, the scheme does not involve intermediate encoding/recovery operations associated with these surface codes.
Results
Our work builds on the fault-tolerance properties of the 3D cluster state. In seminal work ref. 36, Raussendorf, Bravyi and Harrington proved that for temperatures below some threshold, the thermal state of the cluster state Hamiltonian on a simple 3D cubic lattice has localizable entanglement: applying single-qubit Pauli measurements to each “bulk” qubit results – up to Pauli corrections determined by the measurement outcomes – in an encoded Bell state of 2D surface codes lying on two opposing faces of the cube. Since the initial thermal state is the cluster state with independent and identically distributed Pauli-Z-errors on each qubit, and the cluster state can be created in constant depth with local operations, this provides a scheme for long-range (encoded) entanglement generation by a constant-depth circuit with local gates. While the assumed (physically motivated) noise model is somewhat restricted, the authors of ref. 36 also point out that more general errors on the initial cluster state such as independent single-qubit depolarizing noise can be tolerated when using ideal (non-faulty) operations at the two surfaces.
The scheme of ref. 36 produces a surface-code encoded Bell pair, i.e., the resulting entanglement lives in a logical 2-qubit subspace of a many-qubit system. In applications such as the one considered in ref. 37, this is a desirable feature: the encoded information can be operated on without decoding, thus preserving fault-tolerance properties. In a communication scenario, however, it may be more desirable to establish entanglement between two physical qubits instead. A scheme for achieving this kind of localization of the entanglement was proposed in ref. 38 by modifying the approach of ref. 36: Here a different single-qubit measurement pattern is used at the two (“surface code”) boundaries. This results in entanglement between two distinguished qubits in each surface. For the problem of establishing a constant-fidelity Bell pair in a cube of size R × R × R, the work ref. 38 provides analytical and numerical threshold estimates in the case of i.i.d. Pauli-X and Pauli-Z errors in the cluster state. (It was argued in ref. 38 that this error model captures a situation where initially, independent noisy Bell states are shared along each edge of the cubic lattice, and all subsequent (single-qubit) operations are ideal, i.e., noise-free.) In particular, it is shown that there is a threshold error rate such that constant-fidelity two-qubit entanglement (i.e., independent of R) is established for any error rate below that threshold.
To achieve a longer communication distance, one can use cluster states on lattices of the form d × d × R with R ≫ d, i.e., lattices that are elongated in the direction where quantum information is to be transferred. This idea has been explored numerically in the case of i.i.d. Pauli-Z noise in ref. 36. In a similar vein, the results of ref. 38 are stated for cubes (i.e., lattices of the form R × R × R), but the author suggests using lattices of the form d × d × R with \(d=\Theta (\log R)\).
The protocol based on the 3D cluster state satisfies the low-latency requirement (iv) and uses only geometrically local operations (cf. (ii)) by its construction. However, the achievable communication distance as a function of the number of qubits (see (i)) and the resilience to local stochastic noise (see (iii)) have not been addressed by the prior work36,38. Here we extend the result of refs. 36,38 and prove that the protocol based on the cluster state of the lattice of the form d × d × R is fault-tolerant under circuit-level local stochastic noise of strength below a constant threshold, even with d ≫ R. Our result shows that the protocol based on the 3D cluster state additionally satisfies properties (i) and (iii).
In the remainder of this section, we present our construction and the associated analysis. First, we describe the cluster-state-based protocol38 in detail, highlighting its low latency and the fact that it only uses geometrically local operations in 3D. Next, we establish rigorous bounds on the fault-tolerance threshold for the scenario where the protocol is run with R ≫ d under general circuit-level noise. We will show that a large distance R is achievable (cf. (a) and prove a fault-tolerance threshold result (cf. (c)). Subsequently, we discuss a fundamental limit to entanglement distribution protocols on a line under the low latency constraint: It takes the form of a lower bound on the number of qubits that each repeater must control. Next, we discuss an upper bound on the communication distance achievable with our 3D cluster state-based protocol, and compare it with general entanglement distribution protocols with low latency. Finally, we provide a modular way of understanding the protocol by introducing the protocol which fault-tolerantly transfers surface-code encoded information onto a single physical qubit.
Low-latency long-range entanglement generation using a 3D cluster state
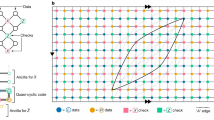
We present a protocol for generating a long-range entangled two-qubit Bell state in a fault-tolerant manner in the presence of local stochastic noise. We note that it is essentially identical to the protocol introduced in ref. 38, but we work with longer communication distance R ≫ d. Consider a lattice \({\mathcal{C}}={\mathcal{C}}[d\times d\times R]\) which is a subgraph of the 3D grid graph of size (2d − 1) × (2d − 1) × R (see Fig. 3). Edges of \({\mathcal{C}}\) are collected so that two vertices in \({\mathcal{C}}\) are adjacent if their Manhattan distance is equal to 1. Each vertex of the lattice \({\mathcal{C}}\) is occupied with one qubit which is initialized as \(\left\vert 0\right\rangle ={{1}\choose{0}}\in {{\mathbb{C}}}^{2}\).
Each sphere represents a qubit. Also indicated is the measurement pattern used in our protocol, consisting of single-qubit Pauli-X and Pauli-Z measurements. Entanglement is established between the qubits q1 and q2. The set of qubits is partitioned into three subsets, namely \({\mathcal{X}}\), \({\mathcal{Z}}\) and {q1, q2}. In the course of the protocol, the qubits in the subsets \({\mathcal{X}}\) and \({\mathcal{Z}}\) are measured in the Hadamard- and computational basis, respectively.
The goal of the protocol is to prepare a Bell pair \(\left\vert \Phi \right\rangle\) on the qubits q1 and q2 which are located at two opposite corners of the lattice \({\mathcal{C}}\) (see Fig. 3). Each slice of size (2d − 1) × (2d − 1) is considered a node or a repeater. With this interpretation, the protocol describes a procedure of entanglement sharing between the two end nodes in a 1D network. Considering the slice of the lattice \({\mathcal{C}}\) containing the qubit q1 as the first slice (associated with repeater \({{\mathcal{R}}}_{1}\)), we call the j-th slice the repeater \({{\mathcal{R}}}_{j}\).
Let n = Θ(d2R) be the number of vertices of the lattice \({\mathcal{C}}\). The protocol starts by preparing the 3D cluster state \(W{\left\vert 0\right\rangle }^{\otimes n}\) of the lattice \({\mathcal{C}}\), where
is a product of Hadamard gates and controlled-Z gates
and the product of controlled-Z gates CZu,v is taken over all edges {u, v} of the lattice \({\mathcal{C}}\).
We first observe that the product ∏{u, v}CZu,v of controlled-Z gates in Eq. (1) can be written as a depth-6 quantum circuit as described in Figs. 4 and 5. Here the operations in Fig. 4 are “local” for each repeater, and are applied within each repeater \({{\mathcal{R}}}_{j}\) in parallel for j = 1, …, R. The operations illustrated in Fig. 5 couple neighboring odd-even pairs \(({{\mathcal{R}}}_{2k-1},{{\mathcal{R}}}_{2k})\), k = 1, …, ⌊R/2⌋ of repeaters, and even-odd pairs \(({{\mathcal{R}}}_{2k},{{\mathcal{R}}}_{2k+1})\), \(k=1,\ldots ,\lfloor R\rfloor /2\rfloor\) of repeaters in two rounds.
The first step consists of two-qubit CZ operations between repeater \({{\mathcal{R}}}_{2j-1}\) and repeater \({{\mathcal{R}}}_{2j}\) (solid lines) for all j = 1, …, ⌊R/2⌋. The second step is of two-qubit CZ operations between repeater \({{\mathcal{R}}}_{2j}\) and repeater \({{\mathcal{R}}}_{2j+1}\) (dashed lines) for all j = 1, …, ⌊R/2⌋.
In more detail, the first four layers consist of CZ gates on the edges connecting two qubits in the same node. The fifth layer consists of CZ gates acting on (2j − 1)-th and 2j-th repeaters for j = 1, …, ⌊R/2⌋ (see solid lines in Fig. 5), and the sixth layer consists of CZ gates acting on 2j-th and (2j + 1)-th repeaters for j = 1, …, ⌊R/2⌋ (see dashed lines in Fig. 5). In summary, we can write W as
where all \({U}_{j}^{{\prime} }\) for j = 2, …, 5 together with \({U}_{1}^{{\prime} }\) and \({U}_{6}^{{\prime} }\) consist of CZ gates. Note that this depth-8 circuit is also illustrated in Fig. 2(b).
We can further merge the layers H⊗n and \({U}_{1}^{{\prime} }\) into one layer \({U}_{1}={U}_{1}^{{\prime} }{H}^{\otimes n}\), which is a product of two-qubit gates CZu,vHu acting on different qubits. Analogously, we define the unitary \({U}_{6}={H}^{\otimes n}{U}_{6}^{{\prime} }\) as the layer obtained by merging two layers \({U}_{6}^{{\prime} }\) and H⊗n. Finally, we can write W as a depth-6 Clifford circuit
where each Uj for j = 1, …, 6 consists of CZu,v, HuCZu,v and CZu,vHu gates acting on pairwise disjoint qubits {u, v}.
To describe the remaining steps of the protocol, we consider the partition \({\mathcal{X}}\cup {\mathcal{Z}}\cup \{{q}_{1},{q}_{2}\}\) of these n qubits which is represented in Fig. 3. With the cluster state \(W{\left\vert 0\right\rangle }^{\otimes n}\), we perform single-qubit measurements on the qubits except for two qubits q1 and q2. Here, each qubit in \({\mathcal{X}}\) and \({\mathcal{Z}}\) is measured in the Hadamard- and computational basis, respectively.
We can construct functions \(\alpha ,\beta :{\{0,1\}}^{{\mathcal{X}}\cup {\mathcal{Z}}}\to \{0,1\}\) such that given the measurement results \(s\in {\{0,1\}}^{{\mathcal{X}}\cup {\mathcal{Z}}}\), the post-measurement state on q1 and q2 is \({Z}_{{q}_{2}}^{\alpha (s)}{X}_{{q}_{2}}^{\beta (s)}{\left\vert \Phi \right\rangle }_{{q}_{1},{q}_{2}}\), if all operations are perfect. Therefore, given the two bits α(s) and β(s), one can apply the Pauli “correction” operator Zα(s)Xβ(s) to qubit q2 to obtain the desired state \({\left\vert \Phi \right\rangle }_{{q}_{1},{q}_{2}}\). Note that for many applications which can be written as Clifford circuits, it is sufficient to compute the two bits α(s) and β(s) to correct the Pauli operator in “software”, i.e., one can commute the Pauli correction Zα(s)Xβ(s) through a stabilizer circuit without the need for physically applying a correction.
Before we move on to the precise description of the components of the protocol, we observe that the protocol satisfies the low-latency and geometric locality requirements discussed in the Introduction: The whole process can be written in a constant-depth quantum circuit with Pauli gates controlled by classical bits obtained by computing the bits α(s) and β(s) (see Fig. 2(b)). Moreover, the involved qubits are arranged in a slab-like 3D lattice, as shown in Fig. 3, and operations are between neighboring qubits only. A precise description of the lattice \({\mathcal{C}}[d\times d\times R]\) as well as the validity of the protocol is deferred to Sections 4 and 5 of the Supplementary Information.
Here we state the definition of α and β and discuss when the protocol fails to output the correct Bell basis state in the scenario where the protocol runs with the noisy cluster state \(EW{\left\vert 0\right\rangle }^{\otimes n}\) corrupted by some n-qubit random Pauli E and all measurements are perfect. (We also discuss more general circuit-level noise below.)
First, note that since all qubits in \({\mathcal{X}}\) and \({\mathcal{Z}}\) are measured in Hadamard basis and computational basis, respectively, we may assume that the random Pauli E is of the form
where \({E}_{{q}_{1},{q}_{2}}\) is a random Pauli supported on the qubits q1 and q2, \({E}_{{\mathcal{X}}}\) is an X-type random Pauli supported on \({\mathcal{X}}\), and \({E}_{{\mathcal{Z}}}\) is a Z-type random Pauli supported on \({\mathcal{Z}}\). In particular, from now on, we think of \({E}_{{\mathcal{X}}}\) and \({E}_{{\mathcal{Z}}}\) respectively as a (random) subset of \({\mathcal{X}}\) and \({\mathcal{Z}}\).
The main subroutine contained in the (algorithmic) definition of α and β is solving minimum matching problems39 on the (primal) and dual decoding graphs
illustrated in Fig. 6. The full definitions of the decoding graphs are deferred to Section 4 of the Supplementary Information, but here we state all properties of these graphs to give the definition of α and β.
External vertices (black spheres) and internal vertices (white spheres) are illustrated. The external vertices incident to the edges in \({{\mathcal{L}}}_{{\rm{cl}},X}\) and \({{\mathcal{L}}}_{{\rm{cl}},Z}^{* }\) form the membranes M1 and \({M}_{{1}^{* }}\). Labels on the external vertices are used in Supplementary Information for the analysis on the failure probability of the protocol.
-
1.
Each qubit in \({\mathcal{X}}\cup {\mathcal{Z}}\) corresponds to one of the edges of \({{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}\) or \({{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}\). With this correspondence, the subset \({E}_{{\mathcal{X}}}\cup {E}_{{\mathcal{Z}}}\subseteq {\mathcal{X}}\cup {\mathcal{Z}}\) can be represented as a subset of the edges of the decoding graphs. Let us denote these subsets of the edges by
$$\begin{array}{rcl}{E}_{{\rm{dec}}}&=&({E}_{{\mathcal{X}}}\cup {E}_{{\mathcal{Z}}})\cap {{\mathsf{E}}}_{{\rm{cl}},{\rm{dec}}}\\ {E}_{{{\rm{dec}}}^{* }}&=&({E}_{{\mathcal{X}}}\cup {E}_{{\mathcal{Z}}})\cap {{\mathsf{E}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}.\end{array}$$ -
2.
Each vertex of the decoding graphs is either internal or external. The set of external vertices of a decoding graph \({{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}\) is partitioned into two “membranes” M1 and M2. We collect all edges connecting the vertices in M1 with internal vertices and let \({{\mathcal{L}}}_{{\rm{cl}},X}\) denote the set of these edges. We analogously define the membranes \({M}_{{1}^{* }}\) and \({M}_{{2}^{* }}\) of the other decoding graph \({{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}\) and the set of edges \({{\mathcal{L}}}_{{\rm{cl}},Z}^{* }\).
Given the measurement result \(s\in {\{0,1\}}^{{\mathcal{X}}\cup {\mathcal{Z}}}\), the bits α(s) and β(s) are computed as follows:
-
1.
Considering s as a subset of the set of edges \({{\mathsf{E}}}_{{\rm{cl}},{\rm{dec}}}\cup {{\mathsf{E}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}\), partition s into two subsets
$$s={s}_{{\rm{dec}}}\cup {s}_{{{\rm{dec}}}^{* }}\quad \,\text{where}\,\quad {s}_{{\rm{dec}}}=s\cap {{\mathsf{E}}}_{{\rm{cl}},{\rm{dec}}}\quad \,\text{and}\,\quad {s}_{{{\rm{dec}}}^{* }}=s\cap {{\mathsf{E}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}.$$ -
2.
Compute the boundaries \({\partial }_{{{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}}({s}_{{\rm{dec}}})\) and \({\partial }_{{{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}}({s}_{{\rm{dec}}})\) of sdec and \({s}_{{{\rm{dec}}}^{* }}\) in the decoding graphs \({{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}\) and \({{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}\). Here, the boundary \({\partial }_{{\mathsf{T}}}({{\mathsf{E}}}^{{\prime} })\) of a subset \({{\mathsf{E}}}^{{\prime} }\subseteq {\mathsf{E}}\) of edges in a decoding graph \({\mathsf{T}}\) is defined as the set of internal vertices of \({{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}\) incident to odd number of edges in \({{\mathsf{E}}}^{{\prime} }\).
-
3.
Compute minimal matchings
$$\begin{array}{rcl}m&=&{{\mathsf{MinMatch}}}_{{{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}}({\partial }_{{{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}}({s}_{{\rm{dec}}}))\\ {m}^{* }&=&{{\mathsf{MinMatch}}}_{{{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}}({\partial }_{{{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}}({s}_{{{\rm{dec}}}^{* }}))\end{array}$$of the internal vertices \({\partial }_{{{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}}({s}_{{\rm{dec}}})\) and \({\partial }_{{{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}}({s}_{{\rm{dec}}}^{* })\). Here, a minimal matching \({{\mathsf{MinMatch}}}_{{\mathsf{T}}}({{\mathsf{V}}}^{{\prime} })\) of a subset \({{\mathsf{V}}}^{{\prime} }\) of internal vertices in a decoding graph \({\mathsf{T}}\) is a minimal subset of edges of \({\mathsf{T}}\) whose boundary is \({{\mathsf{V}}}^{{\prime} }\).
-
4.
Finally, compute the bits
$$\begin{array}{rcl}\alpha (s)&=&\left\langle \left\langle {s}_{{\rm{dec}}}\oplus m,{{\mathcal{L}}}_{{\rm{cl}},X}\right\rangle \right\rangle \\ \beta (s)&=&\left\langle \left\langle {s}_{{{\rm{dec}}}^{* }}\oplus {m}^{* },{{\mathcal{L}}}_{{\rm{cl}},Z}^{* }\right\rangle \right\rangle .\end{array}$$Here, for two sets A and B, we denote A ⊕ B the symmetric difference of A and B, or equivalently the bit-wise summation over modulo 2 if all sets are considered as bitstrings. The notation \(\left\langle \left\langle A,B\right\rangle \right\rangle\) denotes the parity of the number of elements in the intersection A ∩ B, or equivalently the usual inner product on the bitstring defined as the parity of the sum of the bits obtained by bit-wise multiplication of A and B which are considered as bitstrings.
A key fact here is that the two subsets sdec and Edec have the same boundaries in the decoding graph \({{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}\), i.e.,
Analogously, we have
for the subsets \({s}_{{{\rm{dec}}}^{* }}\) and \({E}_{{{\rm{dec}}}^{* }}\) of the edges of the decoding graph \({{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}\) In particular, the boundaries of the errors Edec and \({E}_{{{\rm{dec}}}^{* }}\) can be computed from the measurement outcome s. The main role of the function α is finding the estimate
of Edec with the information about its boundary in the decoding graph by solving a minimum matching problem39 on the decoding graph \({{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}\). Analogously, a subroutine of β computes a minimal matching
of the boundary of \({E}_{{{\rm{dec}}}^{* }}\) associated with the dual decoding graph \({{\mathsf{T}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}\). With Edmond’s algorithm39,40,41,42, if the repeater R, which contains q2, receives all measurement results from all other R − 1 repeaters, then it can evaluate the estimates \({\hat{E}}_{{\rm{dec}}}(s)\) and \({\hat{E}}_{{{\rm{dec}}}^{* }}(s)\) in a time O(d6 ⋅ R3). (The “flow” of the classical information, which is the measurement results, is illustrated as double line segments in Fig. 2).
A necessary condition for the failure of the protocol, i.e., the case where the output state is not the desired Bell state \(\left\vert \Phi \right\rangle\), is that the Pauli \({E}_{{q}_{1},{q}_{2}}\) on the qubits q1 and q2 is non-trivial. Geometrically, this implies that at least one of the subsets \({E}_{{\rm{dec}}}\oplus {\hat{E}}_{{\rm{dec}}}(s)\subseteq {{\mathsf{E}}}_{{\rm{cl}},{\rm{dec}}}\) or \({E}_{{{\rm{dec}}}^{* }}\oplus {\hat{E}}_{{{\rm{dec}}}^{* }}(s)\subseteq {{\mathsf{E}}}_{{\rm{cl}},{{\rm{dec}}}^{* }}\) of the edges connects two membranes M1 and M2 or \({M}_{{1}^{* }}\) and \({M}_{{2}^{* }}\) of the decoding graphs at the opposite sides, consisting of external vertices, see Fig. 7. The proof of the necessity of this condition for failure of the protocol is deferred to Section 4 of the Supplementary Information.
A threshold theorem for low-latency long-range entanglement generation
We prove that the entanglement generation protocol using a 3D cluster state is robust under local stochastic noise of strength below a threshold, even with a communication distance R ≫ d. The formal definition of local stochastic errors is as follows.
Definition 1
(Local stochastic errors). Let [n]: = {1, …, n} denote the set of n qubits. A random n-qubit Pauli E is local stochastic with strength p ∈ [0, 1] if
where supp(E) is the set of all qubits where E acts non-trivially. We write \(E \sim {\mathcal{N}}(p)\) if E is local stochastic with strength p.
We first state our result on fault-tolerance of the protocolin the case where the protocol runs with the noisy cluster state \(EW{\left\vert 0\right\rangle }^{\otimes n}\) where \(E \sim {\mathcal{N}}(p)\) is a random Pauli which is local stochastic with strength p, and there is no other source of error.
Theorem 2
(Long-range entanglement generation). Consider a cluster state \(W{\left\vert 0\right\rangle }^{\otimes n}\) associated with the lattice \({\mathcal{C}}[d\times d\times R]\) where d ≥ 3 is arbitrary. Suppose the measurement pattern in Fig. 3 is applied to a corrupted cluster state \(EW{\left\vert 0\right\rangle }^{\otimes n}\), where \(E \sim {\mathcal{N}}(p)\) is a local stochastic error. Then there are two efficiently computable functions α, β taking the collection s of measurement outcomes to bits such that the post-measurement state on qubits q1, q2 is the state \({Z}_{{q}_{2}}^{\alpha (s)}{X}_{{q}_{2}}^{\beta (s)}\Phi\) with probability at least 1 − 5006p, for any
Here, we only give a sketch of the proof of Theorem 2 presented in Section 5 of the Supplementary Information. In the proof of Theorem 2, we show that for a random Pauli \(E \sim {\mathcal{N}}(p)\), the subset \({E}_{{\rm{dec}}}\oplus {\hat{E}}_{{\rm{dec}}}(s)\) of the edges contains a path connecting the two membranes of the decoding graph \({{\mathsf{T}}}_{{\rm{cl}},{\rm{dec}}}\) at the opposite sides with probability at most O(p). We also show a similar result for the subset \({E}_{{{\rm{dec}}}^{* }}\oplus {\hat{E}}_{{{\rm{dec}}}^{* }}(s)\) of \({{\mathsf{E}}}_{{\rm{cl}},{\rm{dec}}}\). The upper bound on the failure probability is obtained by applying the union bound to these events.
We also show that fault-tolerance of the protocol with this simplified noise model (with noise only on the cluster state \(W{\left\vert 0\right\rangle }^{\otimes n}\), i.e., Theorem 2 implies that the protocol is robust under circuit-level local stochastic noise of strength below some constant threshold where Pauli error occurs before and after every layer of the state preparation, unitary operation, and single-qubit measurements, see the Methods section.
Optimality: A converse to the threshold theorem
Considering each (2d − 1) × (2d − 1)-slice of the lattice \({\mathcal{C}}[d\times d\times R]\) as a repeater, we have m = O(d2) qubits per repeater. Theorem 2 thus implies that below the threshold error strength p0,
qubits per repeater are sufficient to establish constant-fidelity over distance R. Thus, the cluster-state-based protocol satisfies the properties discussed in the introduction.
In this subsection, we study to which extent the protocol provided by Theorem 2 is optimal among protocols with low latency. Specifically, we ask if the relationship between the number m of qubits at each site and the communication distance R can be better than polylogarithmic (cf. (2)). We find that this is not the case, i.e., the scaling of our protocol is essentially optimal.
Theorem 3
(Converse for low latency schemes). Let π be an entanglement generation of low-latency over communication distance R which uses m qubits per repeater. If its output state achieves fidelity at least \(\frac{1}{2}(1+{e}^{-1})\approx 0.684\) under arbitrary local stochastic noise of strength p below a constant threshold p0 > 0, then we must have \(m=\Omega (\log R)\).
The proof of Theorem 3 replaces the analysis of a low-latency protocol π by that of an entanglement-assisted protocol \({\pi }^{{\prime} }\), and follows from the fact that for any p ∈ (0, 1), the qubit depolarizing channel \({{\mathcal{E}}}_{p}(\rho )=(1-p)\rho +p{\rm{tr}}(\rho )\frac{I}{2}\) is a convex combination of an entanglement-breaking channel43 and the identity channel (see Supplementary Information Section 6 for details). It implies that local stochastic noise with any constant noise strength prevents entanglement generation over distances greater than exponential in the number of qubits at each site. Comparing the lower bound from the converse theorem with the number of qubits per site from our protocol (2), we conclude that the polylogarithmic scaling on the number m of Theorem 2 can at best be improved to a logarithmic scaling in R.
Closing the log-factor gap between the converse Theorem 3 and achievability Theorem 2 appears to require a new approach, however: We can show that the analysis of Theorem 2 leading to the scaling (2) is tight. In fact, the scaling is necessary for any procedure which is based on the cluster state and uses the same syndrome information using functions α and β as in our protocol: We show the lower bound
for any such protocol. This result is obtained by a detailed analysis of the associated decoding problem, see Supplementary Information Section 6. It applies, in particular, to natural variants of our scheme that are obtained, e.g., by replacing Edmond’s minimal matching algorithm by other procedures, including heuristic algorithms. This indicates that improving over our protocol will require a different resource state or measurement pattern.
Understanding the protocol with surface code single-shot decoding
We give a modular way of understanding the protocol, giving a high-level overview focused on the two main building blocks:
-
(I)
Generating a surface-code-encoded Bell pair: The generation of a cluster state on an elongated lattice \({\mathcal{C}}[d\times d\times R]\) and subsequent single-qubit measurement of “bulk” qubits not belonging to the two boundaries with third coordinate equal to u3 = 1 and u3 = R, respectively. Up to local unitaries, this part of the procedure is identical to the original scheme of36. This generates a surface-code encoded Bell pair up to a (computable) Pauli correction and residual local stochastic noise [37, Result 3].
-
(II)
Single-shot decoding of the surface code: A single-shot decoding procedure for transferring surface-code encoded quantum information onto a single physical qubit. We note that the same idea was used in44 for logical T-basis measurement. We show that this procedure is resilient to local stochastic noise: There is a threshold \({p}_{0}^{{\rm{dec}}}\) such that if the initial encoded state \(\overline{\Psi }\) is corrupted by a local stochastic noise with strength \(p\le {p}_{0}^{{\rm{dec}}}\), then the fidelity of the resulting single-qubit state with the logical state \(\overline{\Psi }\) is linearly close to 1 as a function of the noise strength p. We refer to Supplementary Information Section 1 and 3 for details.
From a conceptual point of view, it is clear that combining (I) with (II) results in a procedure for generating long-range entanglement. However, our analysis of the resulting fidelity is not simply a combination of the analytical results stated above for each building block (I) and (II). This is because a threshold result derived in this way does not yield parameters of practical relevance. Instead, we establish a significantly tighter threshold estimate by a direct analysis of the achieved fidelity for the entire (combined) process.
Discussion
In this work, we give a complete analysis of the robustness of the distance-R entanglement generating protocol based on the 3D cluster state of size (2d − 1) × (2d − 1) × R with \(d=O(\log R)\) under circuit-level local stochastic noise. Our main result is a fault-tolerance threshold theorem giving a bound on the tolerable noise strength.
We also show that our protocol based on the 3D cluster state gives rise to a low-latency protocol for long-range entanglement generation by a set of R equidistant repeaters on a line. We prove that fault-tolerant generation of one Bell pair between two end nodes by any low-latency protocol requires at least \(m=\Omega (\log R)\) qubits per node. Our construction uses \(m=O({\log }^{2}R)\) quibts at each repeater, which we show is optimal for the 3D cluster-state approach. We note that it is still an open problem whether there exists a low-latency protocol which saturates the lower bound \(m=\Omega (\log R)\).
Methods
In this section, we explain how to reduce the problem of showing fault-tolerance of low-latency protocols with circuit-level noise to the setting of a noisy cluster state \(EW{\left\vert 0\right\rangle }^{\otimes n}\) (and noise-free operations otherwise). We note that this reduction is same as that of ref. 37, and it is ubiquitous in the error correction literature, see e.g., refs. 15,45.
Recall that the protocol we proposed (without the correction operator) is essentially preparing the state \(W{\left\vert 0\right\rangle }^{\otimes n}\) followed by the single-qubit measurements, where W is a Clifford unitary
of depth Δ = 6, where each Uj is a tensor product of single- or two-qubit Clifford unitaries whose supports are disjoint.
A noisy implementation of the whole protocol with noise strength p ∈ [0, 1] can be described as the protocol performing the perfect single-qubit measurements on a noisy input state
with Δ = 6. Here, all \({E}_{j} \sim {\mathcal{N}}(p)\) are local stochastic errors of strength p on all qubits. In particular, E0 denotes the Pauli error caused by noisy state preparation, and EΔ+1 denotes the Pauli error which is introduced to describe the measurement error.
Proving the robustness of the protocol with a noisy state of the form (3) seems to be complicated. However, we can sidestep this problem with the following observation: Since all Uj are Clifford unitaries, we can “commute” all Pauli errors Ej to the left. For example, there exists a Pauli \({E}_{0}^{{\prime} }\) such that \({E}_{0}^{{\prime} }{U}_{1}={U}_{1}{E}_{0}\), i.e., \({E}_{0}^{{\prime} }={U}_{1}{E}_{0}{U}_{1}^{\dagger }\) is obtained by conjugating E0 with the Clifford unitary U1. Then, consider the Pauli \({E}_{1}{E}_{0}^{{\prime} }\) and apply the similar technique with the Clifford unitary E2. By repeating this procedure, we end up with some Pauli E such that the noisy state (3) is equal to
More importantly, \(E \sim {\mathcal{N}}({p}^{{\prime} })\) is also a local stochastic error of strength \({p}^{{\prime} }\) with \({p}^{{\prime} }=4{p}^{{4}^{-(\Delta +1)}}\). This fact follows from [37, Lemma 12]: The main idea here is using the commuting technique described above with the following update rules of the noise strength: If \(E \sim {\mathcal{N}}(p)\) and \({E}^{{\prime} } \sim {\mathcal{N}}(q)\) are Paulis and U is a depth-1 Clifford unitary consisting of one- and two-qubit gates, then \(E\cdot {E}^{{\prime} } \sim {\mathcal{N}}(2\max \{\sqrt{p},\sqrt{q}\})\) and \(UE{U}^{\dagger } \sim {\mathcal{N}}(\sqrt{2p})\), see also [37,Lemma 11] for the proof of the update rules. Therefore, if we show that the the protocol is robust for a noisy initial cluster state \(EW{\left\vert 0\right\rangle }^{\otimes n}\) (see Eq. (4)), where the only error during the whole process is the random Pauli \(E \sim {\mathcal{N}}({p}^{{\prime} })\) with \({p}^{{\prime} }\le {p}_{0}^{{\prime} }\), then we can say that the protocol is robust with the circuit-level noise model with random Paulis \({E}_{j} \sim {\mathcal{N}}(p)\) in Eq. (3) for all p ≤ p0 with some constant threshold p0 > 0.
Data availability
Data sharing is not applicable to this article as no datasets were generated or analysed during the current study.
References
DiVincenzo, D. P. The physical implementation of quantum computation. Fortschritte der Physik 48, 771–783 (2000).
Preskill, J. Quantum computing: pro and con. Proceedings of the Royal Society of London. Series A: Mathematical, Physical and Engineering Sciences 454, 469–486 (1998).
Gisin, N. & Thew, R. Quantum communication. Nature Photonics 1, 1749–4893 (2007).
Kimble, H. The quantum internet. Nature 453, 1476–4687 (2008).
Wehner, S., Elkouss, D. & Hanson, R. Quantum internet: A vision for the road ahead. Science 362, eaam9288 (2018).
Bennett, C. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore 175–179 (1984).
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145–195 (2002).
Cirac, J. I., Ekert, A. K., Huelga, S. F. & Macchiavello, C. Distributed quantum computation over noisy channels. Phys. Rev. A 59, 4249–4254 (1999).
Meter, R. V., Munro, W. J., Nemoto, K. & Itoh, K. M. Arithmetic on a distributed-memory quantum multicomputer. J. Emerg. Technol. Comput. Syst.3 (2008).
Robert, B. et al. Efficient distributed quantum computing. Proc. R. Soc. A.469 (2013).
Kómár, P. et al. A quantum network of clocks. Nature Physics 10, 582–587 (2014).
Eldredge, Z., Foss-Feig, M., Gross, J. A., Rolston, S. L. & Gorshkov, A. V. Optimal and secure measurement protocols for quantum sensor networks. Phys. Rev. A 97, 042337 (2018).
Baspin, N. & Krishna, A. Connectivity constrains quantum codes. Quantum 6, 711 (2022).
Brennen, G. K., Song, D. & Williams, C. J. Quantum-computer architecture using nonlocal interactions. Phys. Rev. A 67, 050302 (2003).
Gottesman, D. Fault-tolerant quantum computation with constant overhead (2013). https://arxiv.org/abs/1310.2984.
Panteleev, P. & Kalachev, G. Asymptotically good quantum and locally testable classical ldpc codes. In Proceedings of the 54th Annual ACM SIGACT Symposium on Theory of Computing, STOC 2022, 375–388 (Association for Computing Machinery, New York, NY, USA, 2022). https://doi.org/10.1145/3519935.3520017
Fowler, A. G. et al. Surface code quantum communication. Phys. Rev. Lett. 104, 180503 (2010).
Muralidharan, S., Kim, J., Lütkenhaus, N., Lukin, M. D. & Jiang, L. Ultrafast and fault-tolerant quantum communication across long distances. Phys. Rev. Lett. 112, 250501 (2014).
Muralidharan, S. et al. Optimal architectures for long distance quantum communication. Scientific Reports6 (2016).
Muralidharan, S., Zou, C.-L., Li, L., Wen, J. & Jiang, L. Overcoming erasure errors with multilevel systems. New Journal of Physics 19, 013026 (2017).
Munro, W., Stephens, A., Devitt, S., Harrison, K. & Nemoto, K. Quantum communication without the necessity of quantum memories. Nature Photonics6 (2013).
Zwerger, M., Pirker, A., Dunjko, V., Briegel, H. J. & Dür, W. Long-range big quantum-data transmission. Physical Review Letters 120, 030503 (2018).
Dai, W., Peng, T. & Win, M. Z. Optimal Remote Entanglement Distribution. IEEE Journal on Selected Areas in Communications 38, 540–556 (2020).
Sinclair, N. et al. Spectral multiplexing for scalable quantum photonics using an atomic frequency comb quantum memory and feed-forward control. Phys. Rev. Lett. 113, 053603 (2014).
Guha, S. et al. Rate-loss analysis of an efficient quantum repeater architecture. Phys. Rev. A 92, 022357 (2015).
Liu, X., Zhou, Z.-Q., Hua, Y.-L., Li, C.-F. & Guo, G.-C. Semihierarchical quantum repeaters based on moderate lifetime quantum memories. Phys. Rev. A 95, 012319 (2017).
Briegel, H.-J., Dür, W., Cirac, J. I. & Zoller, P. Quantum repeaters: The role of imperfect local operations in quantum communication. Phys. Rev. Lett. 81, 5932–5935 (1998).
Duan, L.-M., Lukin, M. D., Cirac, J. I. & Zoller, P. Long-distance quantum communication with atomic ensembles and linear optics. Nature 414, 413–418 (2001).
Collins, O. A., Jenkins, S. D., Kuzmich, A. & Kennedy, T. A. B. Multiplexed Memory-Insensitive Quantum Repeaters. Physical Review Letters 98, 060502 (2007).
Sangouard, N. et al. Long-distance entanglement distribution with single-photon sources. Physical Review A 76, 050301 (2007).
Chen, Z.-B., Zhao, B., Chen, Y.-A., Schmiedmayer, J. & Pan, J.-W. Fault-tolerant quantum repeater with atomic ensembles and linear optics. Physical Review A 76, 022329 (2007).
Sangouard, N., Simon, C., De Riedmatten, H. & Gisin, N. Quantum repeaters based on atomic ensembles and linear optics. Reviews of Modern Physics 83, 33–80 (2011).
Shchukin, E., Schmidt, F. & Van Loock, P. Waiting time in quantum repeaters with probabilistic entanglement swapping. Physical Review A 100, 032322 (2019).
Jiang, L., Taylor, J. M., Khaneja, N. & Lukin, M. D. Optimal approach to quantum communication using dynamic programming. Proceedings of the National Academy of Sciences 104, 17291–17296 (2007).
Bernardes, N. K., Praxmeyer, L. & van Loock, P. Rate analysis for a hybrid quantum repeater. Physical Review A 83, 012323 (2011).
Raussendorf, R., Bravyi, S. & Harrington, J. Long-range quantum entanglement in noisy cluster states. Physical Review A 71, 062313 (2005).
Bravyi, S., Gosset, D., Koenig, R. & Tomamichel, M. Quantum advantage with noisy shallow circuits in 3D. Nature Physics 16, 1040–1045 (2020).
Perseguers, S. Fidelity threshold for long-range entanglement in quantum networks. Physical Review A 81, 012310 (2010).
Edmonds, J. Maximum matching and a polyhedron with 0, 1 vertices. J. of Res. the Nat. Bureau of Standards 69 B, 125–130 (1965).
Lawler, E.Combinatorial Optimization: Networks and Matroids. Dover Books on Mathematics Series (Dover Publications, 2001).
Gabow, H. N. An Efficient Implementation of Edmonds’ Algorithm for Maximum Matching on Graphs. Journal of the ACM 23, 221–234 (1976).
Wang, D. S., Fowler, A. G., Stephens, A. M. & Hollenberg, L. C. L. Threshold error rates for the toric and surface codes (2009). 0905.0531.
Horodecki, M., Shor, P. W. & Ruskai, M. B. Entanglement breaking channels. Reviews in Mathematical Physics 15, 629–641 (2003).
Litinski, D. Magic State Distillation: Not as Costly as You Think. Quantum 3, 205 (2019).
Fawzi, O., Grospellier, A. & Leverrier, A. Constant overhead quantum fault-tolerance with quantum expander codes. In 2018 IEEE 59th Annual Symposium on Foundations of Computer Science (FOCS), 743–754 (2018).
Momma, K. & Izumi, F. Vesta 3 for three-dimensional visualization of crystal, volumetric and morphology data. Journal of Applied Crystallography 44 (2011).
Acknowledgements
SC and RK gratefully acknowledge support by the European Research Council under grant agreement no. 101001976 (project EQUIPTNT). Figures were produced using VESTA46. RK thanks Isaac Kim for discussions on surface codes.
Funding
Open Access funding enabled and organized by Projekt DEAL.
Author information
Authors and Affiliations
Contributions
SC and RK both siginificantly contributed to this work.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Choe, S.H., König, R. Long-range data transmission in a fault-tolerant quantum bus architecture. npj Quantum Inf 10, 132 (2024). https://doi.org/10.1038/s41534-024-00928-4
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41534-024-00928-4