Abstract
This paper describes a novel 4-D hyperchaotic system with a high level of complexity. It can produce chaotic, hyperchaotic, periodic, and quasi-periodic behaviors by adjusting its parameters. The study showed that the new system experienced the famous dynamical property of multistability. It can exhibit different coexisting attractors for the same parameter values. Furthermore, by using Lyapunov exponents, bifurcation diagram, equilibrium points’ stability, dissipativity, and phase plots, the study was able to investigate the dynamical features of the proposed system. The mathematical model’s feasibility is proved by applying the corresponding electronic circuit using Multisim software. The study also reveals an interesting and special feature of the system’s offset boosting control. Therefore, the new 4D system is very desirable to use in Chaos-based applications due to its hyperchaotic behavior, multistability, offset boosting property, and easily implementable electronic circuit. Then, the study presents a voice encryption scheme that employs the characteristics of the proposed hyperchaotic system to encrypt a voice signal. The new encryption system is implemented on MATLAB (R2023) to simulate the research findings. Numerous tests are used to measure the efficiency of the developed encryption system against attacks, such as histogram analysis, percent residual deviation (PRD), signal-to-noise ratio (SNR), correlation coefficient (cc), key sensitivity, and NIST randomness test. The simulation findings show how effective our proposed encryption system is and how resilient it is to different cryptographic assaults.
Similar content being viewed by others
Introduction
After the seminal work of Lorenz, the construction of models and implementation of circuits for chaotic systems have emerged as an intriguing area of research, driven by the significant potential of chaotic systems in various engineering applications, particularly in secure communications. In terms of Lyapunov exponents, high-dimensional 4D hyperchaos dynamical systems with two positive Lyapunov exponents can produce more unpredictable and complex random signals than 3D chaotic systems, which improves the security of chaos-based communication systems. Consequently, the literature has reported numerous 4-D hyperchaos systems with two positive Lyapunov exponents1,2.
In addition, the existence of multistability phenomenon in certain chaotic systems is very interesting. Multistability or the presence of different coexisting attractors for a given set of system parameters allows the system to behave with a high degree of flexibility and this has recently become a fundamental research topic explored by various researchers. For instance, studies by3,4 recently investigated some chaotic systems with multistability. Furthermore, a chaotic system that allows for free offset boosting control is attractive for engineering and industrial applications. A prospective chaotic system’s offset boosting control is a crucial component that makes converting a bipolar signal to a unipolar signal or vice versa very helpful. Many studies have been conducted recently on chaotic systems with offset boosting control5,6. Therefore, developing a new system with multiple positive Lyapunov exponents, multistability and offset boosting is a challenging, interesting, and very demanding task. Chaotic systems are known for their intricate and unpredictable behavior, making them suitable for generating cryptographic keys and enhancing encryption algorithms7,8. Therefore, chaotic systems have been used intensively to improve the security of different information formations, images, voices, and videos. Integrating a chaotic system with encryption systems increases the complexity and makes it more difficult for attackers to decrypt data9,10,11,12,13.
Numerous studies delve into hyperchaotic systems, such as the work by Xu et al.14, who by featuring torus attractors was able to introduce a novel 4D hyperchaotic system and further demonstrated the presence of the maximum of two positive Lyapunov exponents. In a related vein, Hui et al.15 proposed an intricate four-dimensional hyperchaotic system exhibiting a larger key space and more complex dynamic behaviors. Their application extended to image encryption via the hyperchaotic sequence and Secure Hash Algorithm-512 (SHA-512) functions. Fu et al.16 developed a 4D hyperchaotic system derived from a 3D Lü chaotic system’s foundation. This system found application in audio encryption employing a cross-XOR algorithm, implemented on the platform of STM32 embedded hardware. Li et al.17 introduced a 4D hyperchaotic system incorporating certain exponential term. They explored synchronization issues using an adaptive control law having two inputs. Yang et al.18 presented a sequential architecture that converts 3D quadratic system into a basic 6D hyperchaotic system with complex dynamics using linear control. Notably, when the system had a single equilibrium line, they found that at least seven distinct attractors coexisted. Jiang et al.19 put forth a brand-new TDCS that exhibits hyperchaotic behavior over the whole parameter range. Their method involved fusing SVD, BP, and the recently created TDCS to create an image cryptosystem with aesthetic significance. Meanwhile, Gu et al.20 introduced a novel conservative hyperchaotic system that is non-Hamiltonian in four dimensions. They compared the time sequences produced by the system with previously published works using a complexity analysis of the study. Kong et al.21 introduced a novel 5D FOD memristive HNN (FOMHNN) framework aimed at simulating a neuron’s autapse and clarifying electromagnetic induction resulting from electromagnetic radiation. Additionally, they developed a secure image encryption scheme that reduces memory overhead and simplifies hardware implementation significantly. On the other hand, Yu et al.22 designed three distinct memristive HNNs, including a 4D memristive synapse weight HNN, and designed an image encryption circuit to allow FPGA to directly encrypt images and transmit them to the IO device.
The main contribution and novelty of this paper is proposing a new 4D dynamical system with two positive Lyapunov exponents, multistability and offset boosting. Dynamical properties of the proposed scheme are studied using LEs, bifurcation diagrams, phase plots, and stability analysis. Different coexisting attractors are displayed. An equivalent electrical circuit is designed using Multisim to validate the proposed system’s feasibility. Finally, offset boosting control is achieved and shown using numerical plots. Moreover, it demonstrates the effectiveness of the properties of the proposed system, which is helpful for chaos-based applications. The paper introduces a novel voice encryption system using the new hyperchaotic system for encrypting voice signals. Then, various tests were applied to determine how effectively the encryption system responded against attacks, including histogram analysis, percent residual deviation (PRD), signal-to-noise ratio (SNR), correlation coefficient (CC), key sensitivity, and NIST randomness test.
A new 4D hyperchaotic system
The new 4D hyperchaotic system is defined by the algebraic equations that follows:
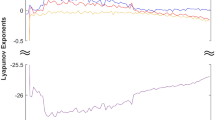
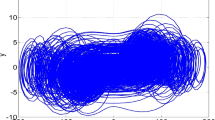
where the parameters a, b, c, d denotes positive constant and x, y, z, w, define the state variables. This study aim to establish that system (1) is hyperchaotic by taking the initial state as [10,1,10,1]T and parameters as a = 8, b = 40, c = 15, d = − 0.1. In Fig. 1, we generate the hyperchaotic attractors of system (1) using the MATLAB ode45 function.
By choosing system (1)’s previous parameter values, the corresponding Lyapunov exponents are calculated using Wolf’s algorithm23 incorporated in MATLAB as:
From (2), System (1) has: LE1,2 > 0, LE3 = 0, LE4 < 0 as depicted in Fig. 1 implying that the system exhibits a hyperchaotic behaviour with two positive Lyapunov exponents, one zero Lyapunov exponents, and one negative Lyapunov exponent. Also, we note that the sum of the Lyapunov exponents is negative, confirming that the proposed 4D system (1) is dissipative.
According to the chaos theory, a high value of Kaplan–Yorke dimension directly corresponds to high complexity of system dynamics. The corresponding Kaplan-Yorke dimension for the suggested system (1) is computed as follows:
The fractional nature of the Kaplan-Yorke dimension is seen from Eq. (3). Thus, the new 4D system (1) produces intricate hyperchaotic attractors. This section will examine the effects of the parameters and initial conditions on the complexity and features of system (1).
System (1) has two equilibrium points; they are obtained as the following:
By examining the eigenvalues of the Jacobian matrix \({J}_{{E}_{i}}\), the study was able to investigate the stability of the new system (1) at the two equilibrium positions. All equilibrium points are unstable, as Table 1 demonstrates. Therefore, it follows that the 4D system is a member of the self-excited family.
Dynamical analysis of the new 4D hyperchaotic system
Bifurcation analysis
This section examines the dynamic characteristics of the 4D hyperchaotic system (1) versus the control parameter c using phase graphs, bifurcation diagrams, and Lyapunov exponents spectra. Figures 2a and b show the Lyapunov exponents spectrum and the bifurcation diagram of the new system, respectively, when the parameters a, b, and d are fixed at a = 8, b = 40, and d = − 0.1, while the control parameter c is adjusted in the range7,15.
When 7 < c < 8, system (1) has no positive Lyapunov exponent implying that the system exhibits periodic behaviour as shown in Fig. 3a for c = 7. The corresponding LEs are: LE1 = 0, LE2 = − 0.078, LE3 =− 2.202, LE4 = − 36.719.
When 8 < c < 9, system (1) has exhibits quasi-periodic behaviour as demonstrated in Fig. 3b for c = 8.4. The corresponding LEs are: LE1 = 0, LE2 = 0, LE3 = -0.484, LE4 = − 39.916.
When 9 < c < 10, system (1) exhibits chaotic behaviour with one positive LE as depicted in Fig. 3c for c = 9.4. The corresponding LEs are: LE1 = 0.847, LE2 = 0, LE3 = -0.073, LE4 = − 42.171.
When 10 < c < 15, system (1) has two positive Lyapunov exponents implying that the system exhibits hyperchaotic behavior as presented in Fig. 3d for c = 14. The corresponding LEs are: LE1 = 2.818, LE2 = 0.012, LE3 = 0, LE4 = − 48.810.
Coexisting attractors
For varying parameter values, the 4D system (1) exhibits the coexistence of one periodic attractor and one chaotic attractor, the coexistence of two hyperchaotic attractors, or the coexistence of two chaotic attractors, as demonstrated by the coexisting bifurcation diagram, basin of attraction, and phase plots. Assume that Y01 = (1, 1, 1, 1) and Y02 = (10, 1, 10, 1) are two distinct starting points for the new 4D system (1). We will use blue for the state orbit associated with Y01 and red for the state orbit associated with Y02. Figure 4a illustrates the bifurcation diagram of system (1) versus parameters c, calculated and plotted starting from Y01 and Y02, showing that the new system can generate coexisting attractors. Additionally, Fig. 4b illustrates the basin of attraction for system (1) plotted in the x(0)-z(0) plane, highlighting regions associated with distinct behaviors. The blue region represents the basin of attraction for periodic behavior, where trajectories converge to periodic orbits, while the red regions denote areas where chaotic dynamics emerge.
Graphical presentation of system (1): (a) coexisting bifurcation diagram for 7 < c < 15, (b) basin of attraction in x(0)—z(0) plane with y(0) = w(0) = 1 and c = 7, (c) coexistence of one chaotic attractor and one periodic attractor, (d) coexisting of two chaotic attractors, (e) coexisting of two hyperchaotic attractors.
Adjusting the values of a = 8, b = 40, c = 7, and d = − 0.1, as seen in Fig. 4c, the 4D system (1) exhibits the coexistence of one chaotic attractor and one periodic attractor. Setting a = 8, b = 40, c = 9.4, and d = − 0.1 as the parameters, as shown in Fig. 4d, the 4D system (1) exhibits two coexisting chaotic attractors. Further adjusting the values to a = 8, b = 40, c = 10, and d = − 0.1, as depicted in Fig. 4e, the 4D system (1) exhibits two coexisting hyperchaotic attractors.
Offset boosting control
Since the fourth variable of system (1), \(w\) appears just in the first equation, the proposed 4-D scheme is a variable-boosting hyperchaotic system with controlled \(w.\) As a result, \(w\) can be boosted by replacing \(w\) with \((w + k)\). System (1)’s first differential equation can be rewritten as follows:
where \(k\) is a controller for offset boosting. Figure 5 depicts several positions of hyperchaotic attractors boosted on different \(k\) in the x–y plane. For a positive value of \(k,\) the attractors are boosted in the negative direction while for a negative value of \(k,\) the attractors are boosted in the positive direction. This special property has a numerous application in chaos-based cryptography and other engineering domains24,25,26,27
Circuit design
Multisim software is used to implement the analog circuit of the proposed 4D hyperchaotic system (1). Figure 6 displays the circuit schematic of the 4D hyperchaotic system. The circuit used in this study includes linear resistors, capacitors, an operational amplifier (TL082CD), and a multiplier (AD633). A power supply of ± 15 V is used. Circuit functions including addition, subtraction, and integration are performed by the operational amplifier. In the meantime, the multiplier unifies the four state variables into a coherent whole while capturing the nonlinearity of the system.
The following corresponding circuital equations of proposed scheme (1) is derived by applying Kirchhoff’s laws to the circuit in Fig. 6, where:
The agreement between the outcomes derived from numerical simulation software Matlab (See Fig. 1) and the electronic circuit simulation software Multisim (See Fig. 7) establishes strong validation for both hyperchaotic attractors of the novel hyperchaotic systems.
Voice encryption algorithm
The block diagrams of voice encryption\decryption using the new hyperchaotic process are demonstrated in Fig. 8 and Fig. 9 respectively.
As displayed in Fig. 8, the encryption process contains two levels: scrambling level and masking level, where both levels depend on the sequence generated by the proposed scheme. Chaotic scrambling is the process of transforming the original voice signal based on a particular algorithm28,29,30. This transformation can be achieved through various techniques, including mathematical transformations, encryption algorithms, or chaotic systems. In our system, the voice signal is scrambled using the x, y, z, and w sequences generated by the new hyperchaotic system according to the following equation:
The scrambling equation introduces a more sophisticated algorithm by integrating chaos and nonlinearity into the scrambling process. Where Vs is the scrambled voice signal, v(t) is the original voice signal s1, s2, s3, and s4 represent coefficients, and p1, p2, p3, and p4, represent the power terms associated with each state variable w(t), z(t), y(t), and x(t). The power terms add an element of nonlinearity to the scrambling process, making it more complex and potentially enhancing the algorithm’s security. Adjusting the power terms allows for fine-tuning the scrambling strength and the degree of nonlinearity introduced into the signal. Where the scrambling strength is set to 0.9, and the values of p1 = p2 = p3 = p4 = 1. The secret keys used in the encryption process are s1 = s2 = s3 = s4 = 1.
Then, to add a complexity to the encrypted signal, the resulted scrambled signal Vs(t) is further masked using the state variables generated from the new scheme producing the encrypted voice signal Ve(t) as follows:
In masking level, the complete state variables are used for masking the signal to increase the security level of the proposed system.
Decryption process
The decryption procedure is the vice versa of the encryption procedure, it involves generating an unmask signal by subtracting the same state variables from the encrypted signal producing the signal Vd(t) as follows:
The produced signal is then unscrambled according to the following equation:
The resulting signal Vr(t), represents the recovered voice signal. Assuming that the hyperchaotic systems in both the encryption and decryption systems are identical, have the same initial condition, and synchronized. The recovered signal Vr(t) is like the original voice signal v(t). In our system the values of coefficients terms are 0.1 for s1, s2, and s3, and 1 for s4. While the values of the power terms are 1 for p1, p2, p3, and p4, and 0.5 for the scrambling strength term.
Numerical simulation and security analysis
MATLAB program was used to acquire the simulation results. The suggested system’s effectiveness and security were evaluated using various tests, including waveform analysis, PRD, SNR, and correlation measurements. The voice signals use eight quantization bits at 8000 Hz.
The waveforms obtained from the proposed encryption system are illustrated in Fig. 10, the recovered, encrypted, and original voice signals, where the original voice transmission is entirely altered by the encrypted signal. Meanwhile, the recovered and original signals are identical.
Figure 11 depicts the histograms of the encrypted, original, and recovered voice signals. The distributed histogram indicates the randomness of the encrypted voice signal, a stark contrast to the histogram of the original and recovered voice signals, which exhibits a normal distribution, rendering it susceptible to attacks. The analysis reveals that our proposed algorithm provides robust security against various statistical attacks, affirming its efficacy in safeguarding voice communication.
Statistical tests
The Percentage Residual Deviation (PRD), Signal Noise Ratio (SNR), and Correlation Coefficient (CC) are employed to analyse the proposed scheme’s immunity against statistical intruders31,32,33. Table 2 displays the values that were computed for various voice signals. The (PRD) is a statistical tool used to measure the deviation between encrypted and original audio signals. Low PRD values suggest a similarity between encrypted and original signals, indicating high fidelity and minimal distortion. Conversely, high PRD values imply significant differences, potentially indicating a decline in signal integrity and increased distortion. Table 2 provides the computed percent residual deviation values for a range of original and encrypted voice signals.
One of the widely considered objective metrics for assessing the strength of the original audio signal is the signal–noise ratio (SNR). The measurements of the SNR in Table 2 are highly negative, indicating an enormous quality of the encrypted speech signals. The correlation coefficient is a numerical correlation measure between -1 and 1. Table 2 provides the calculation for various speech signals. The small value of the (CC) obtained demonstrates how severely jumbled the encrypted signal is in comparison to the original voice signal. The higher PRD values suggest a significant deviation between the encrypted and original signals. The large negative SNR value indicates that the noise power is higher than the signal power, which makes it difficult to detect. On the other hand, near-zero correlation values imply a reduced similarity between the encrypted and original signals.
Key sensitivity
A key sensitivity analysis has been conducted to assess the responsiveness of the new encryption scheme to slight variations in the key values. A small change in one key, for example, the initial value of the x state variable is changed by 0.000000000000001, will entirely deviate the decrypted signal, as shown in Fig. 12, which reflects the immunity of the proposed encryption system against attacks.
NIST statistical randomness tests
Utilizing the NIST 800–22 test package, which is provided by the US National Institute of Standards and Technology, we examined the randomness of the encrypted speech signal in this test. This research primarily aims to test the randomness of encrypted and original voice signals. As indicated in Table 3, the tests were used to investigate the degree of randomness of each signal. The bit-stream of the original speech signal passed only 2 of the NIST tests. The results also suggest that the encrypted voice signal performs favorably in several statistical tests, meeting the criteria for randomness and passing certain NIST assessments.
Conclusion
This article presents a novel 4-D hyperchaotic system characterized by a high level of complexity, capable of exhibiting periodic, quasi-periodic, chaotic, and hyperchaotic behaviors through parameter adjustments. The system demonstrates the well-known dynamical property of multistability, showcasing various coexisting attractors for identical parameter values. The dynamical characteristics of the proposed system are explored via bifurcation diagrams, Lyapunov exponents, stability analysis of equilibrium points, dissipativity, and phase plots. To validate the mathematical model, Multisim software is used to implement an electronic circuit. The system’s offset boosting control capability is highlighted as an attractive and unique feature. Consequently, the new found 4D system proves to be highly advantageous for applications relying on chaos, given its hyperchaotic behavior, multistability, offset boosting property, and the ease with which its electronic circuit can be implemented. We conducted comprehensive tests, including histogram analysis, PRD, SNR, CC, key sensitivity, and NIST randomness, to evaluate its effectiveness against attacks. Our findings demonstrate robust performance, highlighting the system’s capability to safeguard voice signals effectively. This work advances cryptography through innovative encryption methods tailored for voice communication security. In future research, we will make enhancements to the voice encryption system to bolster its resilience against various attacks. This could involve investigating advanced encryption algorithms, incorporating additional layers of security, or exploring techniques from other domains.
Data availability
The data that support the findings of this study are available from the corresponding author on reasonable request.
References
Nestor, T. et al. A new 4D hyperchaotic system with dynamics analysis, synchronization, and application to image encryption. Symmetry 14(2), 424 (2022).
Leutcho, G. D. et al. Dynamics of a new multistable 4D hyperchaotic Lorenz system and its applications. Int. J. Bifurc. Chaos 32(01), 2250001 (2022).
Dong, C. & Wang, J. Hidden and coexisting attractors in a novel 4D hyperchaotic system with no equilibrium point. Fractal Fract. 6(6), 306 (2022).
Lai, Q., Wang, Z. & Kuate, P. D. K. Dynamical analysis, FPGA implementation and synchronization for secure communication of new chaotic system with hidden and coexisting attractors. Mod. Phys. Lett. B 36(01), 2150538 (2022).
Lai, Q. & Lai, C. Design and implementation of a new memristive chaotic system with coexisting attractors and offset boosting behaviors. Indian J. Phys. https://doi.org/10.1007/s12648-022-02344-w (2022).
Ma, C. et al. Dynamical analysis of a new chaotic system: Asymmetric multistability, offset boosting control and circuit realization. Nonlinear Dyn. 103(3), 2867–2880 (2021).
Wen, H. & Lin, Y. Cryptanalysis of an image encryption algorithm using quantum chaotic map and DNA coding. Expert Syst. Appl. 237, 121514 (2024).
Wen, H., Lin, Y., Xie, Z. & Liu, T. Chaos-based block permutation and dynamic sequence multiplexing for video encryption. Sci. Rep. 13(1), 14721 (2023).
Bonny, T. Chaotic or hyper-chaotic oscillator? Numerical solution, circuit design, MATLAB HDL-coder implementation, VHDL code, security analysis, and FPGA realization. Circuits Syst. Signal Process. 40(3), 1061–1088 (2021).
Bonny, T., Al Debsi, R., Majzoub, S. & Elwakil, A. S. Hardware optimized FPGA implementations of high-speed true random bit generators based on switching-type chaotic oscillators. Circuits Syst. Signal Process. 38, 1342–1359 (2019).
Wen, H., Huang, Y. & Lin, Y. High-quality color image compression-encryption using chaos and block permutation. J. King Saud Univ.-Comput. Inf. Sci. 35(8), 101660 (2023).
Bonny, T., Nassan, W. A., Vaidyanathan, S. & Sambas, A. Highly-secured chaos-based communication system using cascaded masking technique and adaptive synchronization. Multimed. Tools Appl. 82(22), 34229–34258 (2023).
Bonny, T., Nassan, W. A. & Baba, A. Voice encryption using a unified hyper-chaotic system. Multimed. Tools Appl. 82(1), 1067–1085 (2023).
Xu, C., Liu, Z., Pang, Y., Saifullah, S. & Khan, J. Torus and fixed-point attractors of a new hyperchaotic 4D system. J. Comput. Sci. 67, 101974 (2023).
Hui, Y., Liu, H. & Fang, P. A DNA image encryption based on a new hyperchaotic system. Multimed. Tools Appl. 82(14), 21983–22007 (2023).
Fu, S., Cheng, X. & Liu, J. Dynamics, circuit design, feedback control of a new hyperchaotic system and its application in audio encryption. Sci. Rep. 13(1), 19385 (2023).
Li, S., Wu, Y. & Zhang, X. Analysis and synchronization of a new hyperchaotic system with exponential term. Mathematics 9(24), 3281 (2021).
Yang, L., Yang, Q. & Chen, G. Hidden attractors, singularly degenerate heteroclinic orbits, multistability and physical realization of a new 6D hyperchaotic system. Commun. Nonlinear Sci. Numer. Simul. 90, 105362 (2020).
Jiang, D., Liu, L., Wang, X. & Rong, X. Image encryption algorithm for crowd data based on a new hyperchaotic system and Bernstein polynomial. IET Image Process. 15(14), 3698–3717 (2021).
Gu, S., Du, B. & Wan, Y. A new four-dimensional non-Hamiltonian conservative hyperchaotic system. Int. J. Bifurc. Chaos 30(16), 2050242 (2020).
Yu, F. et al. Dynamics analysis, synchronization and FPGA implementation of multiscroll Hopfield neural networks with non-polynomial memristor. Chaos Solitons Fractals 179, 114440 (2024).
Kong, X. et al. Memristor-induced hyperchaos, multiscroll and extreme multistability in fractional-order HNN: Image encryption and FPGA implementation. Neural Netw. 171, 85–103 (2024).
Wolf, A., Swift, J. B., Swinney, H. L. & Vastano, J. A. Determining Lyapunov exponents from a time series. Phys. D Nonlinear Phenom. 16(3), 285–317 (1985).
Sambas, A. et al. A New Hyperjerk system with a half line equilibrium: Multistability, Period doubling reversals, antimonotonocity, electronic circuit, FPGA design and an application to image encryption. IEEE Access 12, 9177–9194 (2024).
Benkouider, K. et al. A new 5-D multistable hyperchaotic system with three positive Lyapunov exponents: Bifurcation analysis, circuit design, FPGA realization and image encryption. IEEE Access 10, 90111–90132 (2022).
Flores-Carapia, R., Silva-García, V. M. & Cardona-López, M. A. A Dynamic hybrid cryptosystem using chaos and Diffie-hellman protocol: An image encryption application. Appl. Sci. 13(12), 7168 (2023).
Luis, M., Daniel, L., Isabel, A. & Deicy, A. A new multimedia cryptosystem using chaos, quaternion theory and modular arithmetic. Multimed. Tools Appl. 82(23), 35149–35181 (2023).
Chen, X., Mou, J., Cao, Y. & Banerjee, S. Chaotic multiple-image encryption algorithm based on block scrambling and dynamic DNA coding. Int. J. Bifurc. Chaos 33(16), 2350190 (2023).
Zhou, T., Guo, A., Xu, S., Chen, X. & Swingle, B. Hydrodynamic theory of scrambling in chaotic long-range interacting systems. Phys. Rev. B 107(1), 014201 (2023).
Tang, J. et al. An image layered scrambling encryption algorithm based on a novel discrete chaotic map. IET Image Process. 17(2), 518–532 (2023).
Al-Mhadawi, M. M., Albahrani, E. A. & Lafta, S. H. Efficient and secure chaotic PRNG for color image encryption. Microprocess. Microsyst. 101, 104911 (2023).
Alexan, W., Elkandoz, M., Mashaly, M., Azab, E. & Aboshousha, A. Color image encryption through chaos and kaa map. IEEE Access 11, 11541–11554 (2023).
Gupta, M., Singh, V. P., Gupta, K. K. & Shukla, P. K. An efficient image encryption technique based on two-level security for internet of things. Multimed. Tools Appl. 82(4), 5091–5111 (2023).
Author information
Authors and Affiliations
Contributions
Conceptualization, A.S. and K.B; methodology, T.B and W.A.N; software, K.B, W.A.N and T.B; formal analysis, I.M.S, and I.A.R.M.; investigation, B.A.H, M.M and T.B; Methodology, I.M.S, B.A.H and M.M; Funding, I.A.R.M and I.M.S; writing—original draft preparation, A.S, K.B and W.A.N; writing—review and editing, I.A.R.M, B.A.H and M.M.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Benkouider, K., Sambas, A., Bonny, T. et al. A comprehensive study of the novel 4D hyperchaotic system with self-exited multistability and application in the voice encryption. Sci Rep 14, 12993 (2024). https://doi.org/10.1038/s41598-024-63779-1
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-024-63779-1
Keywords
This article is cited by
-
Image encryption scheme based on thorp shuffle and pseudo dequeue
Scientific Reports (2025)
-
Chaos-enhanced manganese electrolysis: nodule suppression and improved efficiency using controllable chaotic electrical signals
Scientific Reports (2025)
-
Design of grid multi-scroll attractors in memristive Hopfield neural networks and its secure communication scheme
Nonlinear Dynamics (2025)
-
Mechanical Analysis and Synchronization of Chaotic System
International Journal of Applied and Computational Mathematics (2025)
-
A novel (predefined-)time-synchronized fast sliding mode for synchronizing chaotic systems with different dimensions
Nonlinear Dynamics (2025)