Abstract
The advent of smart healthcare technology has provided various benefits, including remote patient monitoring, personalized treatments, and early disease detection. However, transmitting sensitive patient data through IoMT devices raises significant security and privacy concerns. To protect patients’ data and smart medical devices, authentication is required. We uncovered security flaws in the current healthcare architecture, including impersonation, stolen verifiers, and man-in-the-middle attacks. This encouraged us to propose a security architecture that protects patients’ data from attacks and guarantees the security of sensitive healthcare information. Our proposed security scheme, ฿-ED-CRY (Bi Encryption Decryption Crypto), is based on Elliptic Curve Cryptography (ECC). It protects patients’ sensitive healthcare information by enhancing privacy-preserving mechanisms and validates the effectiveness of our scheme. We implemented the proposed scheme using GCC 4.9.5 and the pairing-based cryptography (PBC) library. The results demonstrate that our scheme performs better than the existing security schemes in terms of privacy and computational efficiency. The computation cost is around 13.3640 percentage lower than other related schemes. This research explores the revolutionary effects of integrated healthcare systems, with an emphasis on the convergence of digital health technologies and patient treatment in real-world IoMT scenarios.
Similar content being viewed by others
Introduction
The IoMT enables smart healthcare through interconnected medical devices, facilitating remote patient monitoring, real-time data exchange, and automated diagnostics. However, the security and privacy of patient data remain critical concerns due to various types of attacks. Traditional authentication mechanisms often impose high computational and communication overhead, making them unsuitable for resource-constrained IoMT devices. Therefore, there is a need for a lightweight and secure authentication and privacy protection scheme that ensures data confidentiality, integrity, and efficient access control while minimizing system overhead1.
The rapid development of electronic devices and connected gadgets has a considerable impact on the speed at which healthcare applications emerge. Because wearables and smartphones have a range of sensors capable of measuring blood pressure, respiration, and heart rate, continuous remote monitoring is feasible at a cheap cost, allowing healthcare workers to treat patients more efficiently. Cloud computing is a remote data storage and management service. Users can gain access to the service via a network, usually the Internet. It enables the user to save files online, making them accessible from anywhere over the internet. The service provider keeps the uploaded files on an external server, making them available to users online2,3.
The proliferation of IoMT devices in our digital ecology raises new concerns. These issues involve device authentication while conserving bandwidth and storage. Using identity-based cryptography can solve these problems. The Media Access Control (MAC) address of an Internet of Things (IoT) device is used as the public key in identity-based cryptography. It’s necessary to perform resource-intensive cryptographic operations. This approach simplifies and scales IoMT authentication, improving efficiency and scalability. Gateway access control policies and MAC address authentication ensure that only allowed devices can connect to the network and communicate safely with cloud services. The Internet of Things ecosystem’s growth enhances security and resource use. At its most basic, identity-based cryptography can solve Internet of Things device authentication challenges. The technique allows safe and efficient communication while managing limited resources4,5.
The number of individuals who are elderly, people who have chronic diseases, and people who have disabilities has greatly increased, which places a huge burden on the existing healthcare system. This is the case despite the rapid improvement of technology that detects and treats diseases. A great number of countries are experiencing difficulties due to a deficiency of medical resources, particularly in light of the COVID-19 epidemic. Many of the patients have been left alone at home because they have not received proper care. As a consequence of all of these problems, there is an immediate need for a healthcare system that is more efficient and adequate in meeting the medical needs of people who live in distant areas. The IoMT is one possible solution to this problem6.
The combination of radio frequency identification technology, wireless networks, and medical devices equipped with sensors is used to develop remote healthcare monitoring systems. Medical devices collect the health information of patients who are hospitalized for an extended period of time, persons who have disabilities, and the elderly, and then report it to medical professionals, carers, or healthcare facilities in order to provide fundamental medical services. This results in costs being reduced, medical resources being conserved, and accessibility being improved. In most cases, the capabilities of IoMT end devices are not sufficient to handle the categorization, analysis, transmission, and storage of sensor data. This is because the collection of sensor data requires these activities. As a consequence of this, the Internet of Medical Things design usually makes use of cloud data centres in order to offload resource-intensive computing, networking, and storage tasks from healthcare devices. Cloud computing, on the other hand, has limitations in applications that are extremely mobile or delay-sensitive because of the distance that exists between cloud servers and end devices. Furthermore, the raw data that sensors have gathered must be analyzed to identify only the abnormal health data that has to be detected and then transmitted to cloud servers7.
Motivation
Ensuring the privacy and security of patient health-related information is a significant concern for remote healthcare systems. Wireless communication technologies frequently transmit sensitive patient information in IoMT. This enables attackers to intercept the communication channel and acquire sensitive information about patients. Furthermore, the rapid adoption of IoMT in the healthcare ecosystem makes it substantially more difficult to establish security measures during pandemics, such as the spread of the COVID-19 virus. F-Secure’s analysis reveals that hackers exploited 82 percent of Internet of Things devices in the first half of 20198. The existing schemes are vulnerable to attacks and take more computational cost. This motivates us to design a lightweight security scheme that protects IoMT applications from any attacks and takes less computational cost.
Research objective
The objective of this research is to enhance the security and efficiency of smart healthcare systems while ensuring the protection of patients’ health information and the effective functioning of medical devices at various points, such as:
-
Enhance Security and Privacy Address and mitigate security flaws in the current smart healthcare system.
-
Secure Authentication Implement an ECC-based lightweight signature scheme for robust authentication.
-
Efficient Implementation Develop a practical application for the secure and efficient tracking of health status in real time.
-
Performance Benchmarking Validate the scheme’s superior performance in comparison to existing solutions.
Research contributions
-
Our proposed scheme and security model are based on an identity-based access control system that protects from new attacks in smart healthcare.
-
The Bi-Encryption Decryption scheme secures the patients’ information from various attacks, and the scheme ensures patient privacy by employing Schnorr signatures upon registration of medical devices with the hospital.
-
Our lightweight scheme is more effective for authentication, boasting strong authenticity and preventing unauthorized IoMT devices from cloud environments.
-
The security protocol enables recognizing and destroying any adversarial gateway and IoMT appliances from IoMT healthcare environments.
-
Conducted a security analysis of the proposed scheme and compared the results obtained by the proposed scheme with existing schemes.
Paper roadmap
The rest of the paper is structured as follows: We describe some related work and preliminary concepts used in this research in Sect. 2. In Sect. 3, discuss the workings of the proposed methodology. In Sect. 4, the security performance of the proposed scheme. Section 5 calculates the performance results of the proposed scheme as well as security comparisons with related existing schemes. Finally, we conclude the paper and provide future direction for this research in Sect. 6.
Related work
In this section, we examined the working methods, applications, and research limits of current schemes. As a result of the advent of the digital age, numerous industries have been presented with an abundance of opportunities and innovations, which have been characterized by an ever-increasing dependence on technology. However, these improvements also carry with them several challenges, particularly in the realm of cybersecurity9. Insider threats, also known as damaging activities that originate from within an organization, have emerged as a significant worry in recent years, despite the fact that outside threats have traditionally been the primary focus of security measures10.
The use of a trustworthy server that saves the data is a common feature of the methods now in use. Access control relies on software checks to ensure that a person can access a piece of data only if authorized. From a security perspective, this arrangement is not very desirable. We then encrypt the data using the public key of the intended set and classify it according to the hierarchy. There are some drawbacks to these techniques. If a user of a set needs to provide access to a third party to access data for that set, the user must either provide the third party with their private decryption key so that it may access all entries or act as an intermediary and decode all relevant entries11.
In contrast to conventional PKI, identity-based public key cryptography (ID-PKC) addresses the issue of key authenticity through various procedures. An entity’s public key in ID-PKC is directly obtained from distinct characteristics of its identity, such as an IP address that belongs to a network host or an email address that is connected to a user. The public key generator (PKG) constructs private keys for entities. Before launching an attack, the adversary in a typical PKI must issue a new certificate and persuade entities to accept the new public keys. These factors suggest that applications with low-security requirements or small, closed groups could be the only ones permitted the user ID-PKC12.
The authors present a brand-new public key cryptography paradigm, referring to it as certificateless public key cryptography (CL-PKC)13. The search for public key schemes without requirements for certificates and without ID-PKC’s built-in key escrow capability provided developers with the idea of CL-PKC. One of the most important issues with public key infrastructures (PKIs) has always been the efficient revocation of public key certificates. In RSA-type cryptosystems, Boneh presented a technique for getting instantaneous revocation of a user’s public key privileges14.
According to the description, the system known as mediated RSA (mRSA) uses threshold RSA, in which both parties share the private key. The encryption and verification processes in the SEM architecture are identical to those in traditional RSA, making it transparent to both the sender and the verifier of a signature. Additionally, adopting SEM design eliminates the requirement to check a public key’s status before using it. Users don’t need to worry about any certificate’s validity before using another user’s key to encrypt a message.
Identity-based cryptosystems are another way to streamline key management. This idea was first presented by Shamir in 1984, with the goal of removing as many public key certificates as feasible by enabling a public key to be uniquely generated from the user’s identifying data like email address, phone number, and social security number15.
Additionally, it makes key management simpler because there’s no need to maintain a huge database with a list of public keys and their owners. COVID-19 had a significant impact on the healthcare industry, which was the global pandemic problem. The COVID-19 outbreak resulted in an exponential increase in demand for IoMT devices, which then impacted the global market. The IoMT dramatically reduces patient costs, easing the financial strain on individuals and governments. According to a report published by Fortune Business Insights on August 26, 2024, the IoMT market was estimated to be worth USD 47.32 billion in 2023. During the projection period, the market is expected to increase from USD 60.03 billion in 2024 to USD 814.28 billion in 2032, with a CAGR of 38.5 %16.
The authors present a sensor cloud architecture that uses virtualized physical sensors and dynamic sensor placement based on patient movement and health to continuously monitor high-risk patients17. The research uses a threat model to address wearable payment security. For near-field communication pairs of devices, ECC encrypts messages, and biometrics authenticates safe payments18.
The authors present an identity-based signature system without key escrow that issues private keys without a secure connection. It employs binding–blinding to avoid key escrow and eliminate the need for a secure connection during private issuance19. To ensure the confidentiality of patient information while it is shared and integrated across healthcare providers, they offer a system based on knowledge graphs20. Fog computing with private blockchain offers a trustworthy method of storing and transferring patient data while simultaneously improving the identification of security risks and bolstering the privacy and security of medical data21.
The MD5 hash technique securely stores user passwords for use in authentication procedures. Integrating an MD5 checksum into the original patient record file presents an additional barrier to security and verification22. To create a cryptographic method that satisfies the essential requirements of contemporary smart healthcare cyber-physical systems, the research uses ECC, hash functions, and digital signatures23.
An authentication strategy for IoMT devices is proposed to enhance the security and performance of existing authentication schemes. Through the development of an offline authentication model that directly checks identities, the suggested authentication system successfully authenticates users and IoMT devices within the local area network24. A scalable and adaptable distributed group key agreement protocol is used to reduce CPU overhead by running elliptic curve Diffie-Hellman using multiplications instead of exponential calculations to secure data transmissions in WSN25.
The prospect of IoMT-related attacks poses the most severe threat to the security and privacy of patient medical records. The suggested approach protects the secrecy of IoMT devices linked to the patient’s body while communicating. The XOR operator, hash function, and concatenation were used to save processing power26. An authenticated key agreement protocol for the IoMT using elliptic curve encryption and zero-knowledge proof methods is used to preserve the privacy of patient’s critical information27.
In order to secure the transfer of medical records, a research uses signcryption with an identity-based authentication system based on elliptic curve cryptography. Based on bilinear pairing, the suggested protocol covers a number of security characteristics, such as data confidentiality and authentication with efficient key management28.
iSecureHealth, a lightweight and reliable key exchange mechanism, addresses security, authentication, and privacy issues. To secure communication between IoMT sensors and the gateway node, it adds a security control node. The system uses ECDH for key exchange and HMAC-SHA256-based JSON Web Token for session key creation29.
Our goal in writing this paper is to add to the increasing quantity of information on insider threat detection by providing theoretical understanding and useful solutions to one of the most important cybersecurity problems of our day. The relation between various existing security models, threat models, and their limitations is discussed in Table 1.
Health monitoring with body sensors
Wireless Sensor Networks are also utilized for in-home patient monitoring. A system for distributed telemonitoring was proposed. It employs the Services Layers over the Physical Devices paradigm. The architecture model is service-oriented. The distribution of resources among several WSNs is the primary goal. This concept can also link several networks with different wireless technologies. The device was placed within the patient’s home and gathered motion data and several feature values, such as activity, mobility, and non-response levels. To distinguish between normal and pathological behaviors, the Support Vector Data Description method was applied. An algorithm for categorizing behavior patterns was employed to group the patterns in this instance. There is no evidence to support the expectation that these methods will work in a home setting30,31.
A Body Sensor Network with several body sensors is developed for the best possible resource allocation. This solution effectively addressed the two main issues facing health monitoring systems: a sustainable power source and quality of service. A survey was conducted on wearable sensor-based health monitoring systems. Evaluation aspects led to the evaluation of several systems32,33.
The Wireless Patient Portable Unit, which is likewise affixed to the patient’s body, received data relating to cardiac monitoring that was continuously recorded in the home module. The Wireless Access Point Unit was then used to transfer it via the Internet to the hospital. If the doctor notices any irregularities in the signals the patient got while in the hospital, they can get in touch with them, offer some guidance, or, in an emergency, send an ambulance to the patient’s home. This technology does not provide security or surveillance of the outer environment.
Health monitoring using smart phones
Wearable sensors served as the foundation for the sensor network. The sensors obtained the patient’s vital signs, which were then sent to the patient’s mobile phone. The data is safely received, stored, and sent to reliable medical specialists by the mobile device. Only the data’s accessibility to outside parties is under the patient’s control. No PC was utilized in this process; instead, all tasks were completed via mobile device. The handheld gadget transfers only the relevant data after data mining techniques were applied to filter out extraneous data sequences. The expert’s equipment and the patient’s mobile phone communicated over Bluetooth or WLAN 802.11. When an emergency occurs, the patient’s device generates an emergency call, which is then routed to the caregiver’s device.
A brand-new Wearable Mobility Monitoring System was unveiled. It recognized a state change and utilized a smartphone to take pictures. A solution for on-demand tracking and placement was suggested. It was designed for vast spaces and was based on devices with Global Positioning enabled. The first communication between the two terminals was done via a smartphone.
First communication takes place during the synchronization phase. In this case, the requested terminal T1 sends the desired terminal T2 a synchronization Short Message Service (SMS). T2 completes the operation if it rejects the message. If not, the terminal’s position is sent in one of the following formats: multimedia (MMS) or text (SMS). The graphic that shows the position map of the terminal was present in the multimedia format, but the text format just contained the coordinate values of the terminal. A straightforward Peer-to-peer (P2P) protocol is used to facilitate communication between two terminals.
Health monitoring with security
For health monitoring, various security and privacy protocols were applied34. The patient’s vital signs were transmitted, stored, and received via a smartphone. A multimedia format was provided between sensors and the central hub encryption scheme, which depicts the location map of the terminal. Peer-to-peer (P2P) protocol is a straightforward means of communication between two terminals.
Cipher text Policy Attribute Based Encryption (CP-ABE) with security enhancement techniques was presented. The two main issues in CPABE were the user revocation and the key escrow problem. In CP-ABE, a set of user attributes is applied to KGC’s master secret keys, allowing KGC to produce the users’ private keys. Because KGC may decrypt user ciphertext to obtain the original data, it was not considered trustworthy. It is called the “key escrow problem.” Users may periodically alter their properties or certain secret keys may be hacked. Regular updates are required for every characteristic to keep the system secure. We refer to this as user revocation. Both of these issues were resolved35.
Threat model
This subsection covered privacy and security breaches involving patient data. The threat model primarily targets the cybersecurity domains of application-level security, communication-level security, and device-level security. We will discuss the following points related to threat model:
-
We analyze a robust adversary model, assuming that, except for the certificate authority, we cannot fully trust any of the entities. Though strange, the hospital and payment gateway are regarded as trustworthy.
-
External adversaries could listen in on the conversation and deduce private information about patients as the records are being transmitted.
-
To fraudulently accuse lawful patients of overspending, attackers may initiate collision assaults.
-
While paying a doctor’s charge or ordering medicine online, an eavesdropper may attack the system by providing false information or by pretending to be another real patient, utilizing their hospital account.
-
Multiple system attacks may compromise employee privacy when client-server communication stores and forwards private information to several external parties. Via network vulnerabilities or the acquisition of the access point identifier, the attacker, for instance, can seize the patients and examine the network traffic.
-
Problems with data communication arise when sensitive data is sent and processed between different detachments participating in the transmission security and privacy problems arise.
-
Problems with digital devices and Internet of Things devices, as well as the outcomes for patients using these devices.
-
The stakeholders that are considered in the framework are the entities that are a part of this entire procedure (e.g., hospital servers, employees, and patients).
-
Digital electronic devices that are incorporated with advanced cryptography tools preserve patient data.
The prevalence of attacks came from the communication and application levels, which we addressed and stopped. The adversary may launch significant assaults and seriously harm financial institutions and other protocol participants if they discover any gaps or vulnerabilities in these areas. We are using the lightweight cryptography techniques provided by ECDSA to create and validate signatures. Similar to this, we have employed the elliptic curve integrated encryption scheme (ECIES) as an asymmetric method of encryption and decryption while employing an encryption/decryption algorithm for symmetric purposes36.
Secure network model
This subsection discusses the various security models used in data security in the cloud-based system. The The security model provides two-channel digital device connectivity to hospitals, merchants, application providers, and doctors. The main duty of the hospital server, which is a reputable third-party server, is to gather and transmit patients, employees, and doctors’ information to merchants. Put differently, this organization determines the information in the patient’s database and responds to the hospital employee with an acceptance or rejection of the patient’s queries37,38. Figure 1 represents the IoMT-based secure netwok model. The information flow in the framework is as follows:
-
The hospital receives requests from patients to provide information digitally.
-
The staff member’s request is sent to the smartphone. Through a wireless connection, the smartphone and the digital devices establish a secure connection.
-
Once a link has been made, the application uses password and biometric authentication to verify patients’ requests for authentication.
-
After the patient’s authentication is successful, information is sent from the wireless device to the employee’s smartphone through hospital applications that have been loaded.
-
Patients initiate and submit requests, such as information portal requests, to any institution.
-
The staff member chooses any patient data and submits the request to the appropriate server, like the staff member’s server, which manages patient communications records.
-
An employee of the hospital verifies the information in their database, validates the patient data, and redirects the exchange of data to the patient’s devices.
-
The hospital database server uses a secure network to confirm patient information and send data to physicians related to specific medical conditions.
-
After completing all verification, the patient’s account is credited with the amount of the payment order.
-
The server will notify the appropriate entities of the patient’s initiator and service provider upon successful validation by the hospital.
Addressing the drawbacks in17 could considerably improve the effectiveness and security in healthcare architecture. The18 refers to a lack of research into advanced or emerging security protocols that could improve protection against new types of cyber threats, whereas the11,13 improves understanding and effectiveness of revocation mechanisms in certificateless public key cryptography, resulting in more robust and practical cryptographic systems. Next,19 aims to improve the creation and use of identity-based signature schemes, resulting in more secure and practical cryptography solutions based on cloud technologies in healthcare settings.
Proposed methodologies
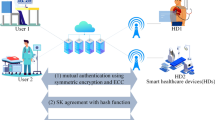
In this work, we proposed a security scheme ฿-ED-CRY with an identity-based cryptography. Schnorr signature is a digital signature scheme known for its simplicity, efficiency, and ability to generate short signatures. We prove our construction of an encryption-decryption scheme satisfies security by using a signature that shows the identification protocol for an honest verifier zero-knowledge protocol. The next subsections present it with an architecture and encryption-decryption scheme based on elliptic curve cryptography. An elliptic curve generates the secure points, and Fig. 2 depicts the operations.
Our proposed security architecture
This subsection presents the system architecture of an access control system that utilizes identity-based methods and is based on the Internet of Medical Things. The key generation center serves as the trusted authority responsible for issuing user keys that match their public identities. The system utilizes authentication servers to authenticate legitimate users who are trying to access important resources. Similar to traditional public key infrastructure, the system operates under the assumption that a safe and trusted third party exists. The identity-based access system offers a robust authentication mechanism while maintaining low operational overhead needs.
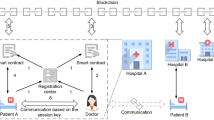
Our proposed IoMT architecture consists of three main components: patients, hospitals, and cloud servers. This design describes the components and procedures that comprise an Internet of Medical Things model. This architecture focuses on interactions between patients, hospitals, and cloud servers, as seen in Fig. 3. Patients use IoMT devices to communicate about their present health status. These health records are acquired by hospitals, who process and store them in their own databases. Cloud servers make it easier for medical practitioners and hospital workers to communicate with one another while monitoring and diagnosing patients.
-
Utilization of IoMT Devices Patients are able to communicate their medical information through the usage of IoMT devices. Wearables, sensors, and other components of medical monitoring devices could be included in this category of gadgets.
-
Wireless Media It is possible to establish connections between devices connected to the Internet of Things and the web server through the utilization of wireless media. Consequently, there is no longer a requirement for physical connections, which makes it possible for medical information to be transferred smoothly.
-
Validation and Authentication In order to ensure that the database of the hospital is up to date with the patient’s current health condition, it is essential to perform validation on the message that has been received. The integrity of the data as well as its reliability are safeguarded from this perspective. The next step is to authenticate the message using a Digital Signature Algorithm (DSA), which confirms its authenticity. This step comes after the message has been validated.
-
Data Storage All of the health information that has been verified and encrypted is kept in a safe place within the database of the hospital. Only authorized workers will be able to access important patient information, which will be safeguarded from unauthorized access.
-
Cloud Server Communication Hospital workers and medical professionals can connect and work together on patient care through the use of the cloud server. According to the information that is provided, they can access patient health data that is recorded in the database of the hospital, which enables remote monitoring and diagnosis.
So, IoMT devices enable patients to transmit their health data to hospitals via wireless connections. The data undergoes validation, authentication, and encryption before being stored in the hospital’s database. Cloud servers facilitate communication and collaboration among hospital personnel and doctors for monitoring patient health and making informed diagnoses.
Mathematical preliminaries of ECC
In this section, we will discuss the main mathematical calculations used in elliptic curve cryptography. These include the Elliptic Curve Discrete Logarithm Problem (ECDLP), as well as how signatures are generated and verified. All the acronyms and notations used in this paper are represented in Table 2.
Process of ECC
In this subsection, elliptic curve cryptography (ECC), particularly ECDSA (Elliptic Curve Digital Signature Algorithm), is indeed a pivotal aspect of modern cryptographic systems. Understanding its fundamental operations is crucial for anyone interested in cryptography and cybersecurity. Here’s a brief overview of what you’ll typically encounter when delving into ECDSA:
Key pair generation of ECC
Key pair generation in elliptic curve cryptography involves creating a public-private key pair that can be used for cryptographic operations such as digital signatures and encryption. Here’s an overview of the key pair generation process:
Choose an Elliptic Curve: The first step is to choose an elliptic curve over a finite field. Elliptic curves are typically defined by the equation \(y^{2}=x^{3}+ax+b\), where a and b are constants specific to the curve, and the operations are performed modulo a prime p. Commonly used curves include the NIST curves such as P-256, P-384, and P-521.
Choose one of the generator points, as every elliptic curve has a special point that is referred to as the generator point, which is sometimes represented by the letter G. The number of points on the curve that can be formed by continually adding the generator point to itself is denoted by order n, which is a specific order that this point possesses. When it comes to prime numbers, the order n is often rather large.
The Key Pair Storage of the private key must be securely stored and protected from unauthorized access. The public key can be shared freely with other parties. The key pair usage to generate key pair can now be used for cryptographic operations such as digital signatures, encryption, and decryption.
Schnorr digital signature
Claus-Peter Schnorr invented the Schnorr signature scheme, a well-known digital signature algorithm known for its simplicity, potency, and security assurance it offers. Its implementation takes advantage of the difficulties presented by the discrete logarithm problem (DLP) within finite fields or groups. When adopting ECC for this purpose, while the fundamental principles persist, there is a fundamental shift in the underlying mathematical framework from finite fields to elliptic curves. Here’s a high-level summary of how the ECC-based Schnorr signature scheme operates.
The Schnorr signature scheme’s security depends on the computational difficulty of solving the DLP, which is a difficult problem even with advances in computing power. The approach preserves the simplicity and effectiveness of the original Schnorr method while leveraging elliptic curves’ intrinsic security features.
The basis of Schnorr signature techniques is the ability to digitally sign a message that is verifiable by everyone possessing the signer’s public key. This is an interpretation of how its functions work, which are as follows:
Schnorr Signature Scheme
Let the User sign a message by using different parameters as
-
Select random value r from the \(0< r < q\) and compute x = a.r mod p.
-
Concatenate message with x and hash result to compute \(e = H(M \parallel x)\).
-
Compute \(y = ( r + Sec_{A}. e )\) mod q.
-
Signature is pair \(\sigma\) = (e, y)
So, any other users can verify the \(\sigma\) as follows:
-
Compute \(x^{'} = a. y. v.e\) mod p.
-
Verify that \(e = H(M \parallel x^{'} )\)
So, the signature proof that \(x^{'} = a^{y}. Pub_{A}\) mod p
=\(a^{(r+ Sec_{A} e + Z_{1}q)}\) \(a^{(Sec_{A}+ Z_{2} p )^{e}}\) mod p
=\(a^(r + Z_{3} q)\) mod p
= \(a^{r}\) mod p
= x
Firstly, the message to be signed (m) is hashed using a cryptographic hash function such as SHA-256 to obtain a fixed-size digest: z=Hash(m).
Encryption-decryption
This subsection discusses the encryption and decryption mechanism of our security scheme, ฿-ED-CRY to maintain the privacy of patient-related information.
Key Generation
-
Let the public key as \(PK_{key}\)
so \(PK_{key}\) =(BS, RL)
-
The message M with length L = \(\vert M \vert\), where \(\vert M \vert\) represents the length of the source message M.
-
Convert the Message to Decimal:
For each character \(M_{i}\) in the source message M
\(D_{i}\) = ASCII(\(M_{i}\))
Encryption of Message
-
Convert Message to Binary
For each character \(M_{i}\) in the source message M:
\(B_{i}\)=ASCII(\(M_{i}\))binary
-
Convert MBM to BS
MBM = \(\Re\) (MBM, BS, Col)
-
Rotate Each Column RL Times: For each column \(C_{i}\) in the reshaped matrix as: Rotated \(Col_{i}\) = RL(\(C_{i}\), RL)
-
compute the shape Resulting Matrix to 8 Columns Matrix:
FM = \(\Re\)(RM,8 col)
-
Compute the Result to Decimal:
For every number N in the final matrix D = BinaryTo Decimal(N)
-
Compute Decimal to Binary Number as characters
for every decimal number
E= (\(M_{i}\)) = ASCII (D)
Decryption of Message
-
Convert Message to Binary (MBM):
For each character \(B_{i}\) in the source message M:
\(B_{i}\)=ASCII()binary \(M_{i}\)
-
Reshape MBM to BS Columns:
-
Reshaped MBM = \(\Re\)(MBM,BS col)
-
Compute as a first rotation as Each Column BS-ROTL Times: For each col \(C_{i}\) in the reshaped matrix:
-
Next, Rotated Col = RL(\(C_{i}\), BS-RL)
-
Reshape Resulting Matrix to 8 Columns Matrix: FM = \(\Re\)(RM,8 col)
-
Convert Result to Decimal:
-
For each number N in the final matrix:
D = BT o D(N)
-
Convert Decimal Results to Characters:
For each decimal number D:
D=(\(M_{i}\)) =ASCII(E)


We represent the message as M and convert it into the ASCII values for each input value. We then convert these values into binary form, creating a message binary matrix (MBM) for the message. Next, we manipulate the values of the MBM by using the base shift values and randomly select a point from an elliptic curve as a security parameter. These values serve as the user’s private keys for encryption. The user then chooses these values and performs the 8-bit rotation. After these computations, we find the final matrix in matrix D. We store the converted values in E as characters using the ASCII value. For the decryption of the secret message, the algorithm uses the private key of the receiver and follow the steps in as shown in an algorithm.
Figure 3 provides our proposed hospital management system flow of information for the health care protocol using a cloud-based device. Some Initial assumptions and prerequisites used for this proposed secure scheme are as:
-
1.
Using a cloud-based device, the patient requested a health examination and payment. The numerous pieces of technology should be paired or connected with the gadget and smartphone.
-
2.
To access transaction information via a mobile device and pay fees using a digital payment system, the registered patient (hospital and patient) must maintain a current database and account with their respective hospitals.
-
3.
To conduct secure conversations, each patient uses their signed certificates from a certification authority (CA), a reliable third party.
-
4.
Each patient is provisioned with a unique “Wireless Public Key Infrastructure” certificate that is preserved in a Secure Element (SE) within the communication devices.
-
5.
Each party to the suggested protocol owns their digital certificates and public keys.
-
6.
The hospital offers and customizes digital and mobile devices for payment and communication applications through cloud-based technology.
As illustrated in Fig. 4, the client manager and patient data reader are merged to form the data owner. Outdoor environment monitoring was not supported in some of the systems that were already in place. In that instance, it becomes challenging to keep an eye on a patient when they relocate away from their home. However, the GPS-enabled smartphone in the suggested work also allows for outdoor monitoring. Since the patient constantly carries a mobile phone, it continuously gathers bodily parameters even when the patient is not at home. Bluetooth short-range communication is used to communicate between sensors and mobile phones.
The acquired body parameters from the sensors are saved on a personal computer in the majority of current systems. There are several issues that can arise when using a computer. A GPS-enabled mobile phone replaces the requirement for a PC in the proposed task. Data Storing Centre (DSC) and Client Key Manager (KGC) make up the data server. The creation of keys for the safe transfer of medical data falls under the purview of KGC and DSC. The user refers to medical personnel at the hospital side, whereas the data owner represents the patient.
Figure 5 represents the flowchart to visualize the working of the proposed IoMT model. Using IoMT devices, patients can communicate their current health status to hospitals when seeking treatment from remote locations. To avoid wasting time on fraudulent users, we first verify whether the message is valid or not. If the message is valid, we then perform parameter validation to verify the patient ID and health condition. After parameter validation, we add the patient to the hospital’s patient list. The message is then authenticated using a digital signature algorithm, which confirms its authenticity. All verified and encrypted health information is securely stored in the hospital’s database. Only authorized personnel can access this important patient health information, ensuring it is protected from unauthorized access. Any incomplete or invalid messages received are temporarily stored without encryption in the hospital database and deleted after a specified period.
Phases of secure communication
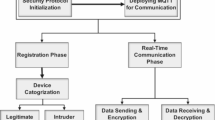
This section discusses all the phases for secure communication in a step-by-step manner, as represented in Fig. 6. This figure analyzed stepwise communication between IoMT devices, the cloud gateway, and the cloud server.
Step-1. System Setup In this step, the cloud server provides the server storage and various network resources. The cloud server manages every user and hospital’s devices in a centralized. The medical devices are configured with unique identifiers and cryptographic keys. After that secure database is created in the cloud to store device information, user credentials, and cryptographic keys.
Step-2. Device Registration In this phase, the IoMT device sends a registration request to the cloud gateway, including its unique identifier, and forwards the registration request to the cloud server. The server verifies the device identification ID with shared credentials. After that generate the public and private key and pair the devices with updates to the key in the server.
Step-3. Authentication The device sends an authentication request to the cloud gateway including its unique identifier and a digitally signed message. The cloud gateway forwards the authentication request to the cloud server. The cloud server retrieves the device’s public key from the database and verifies the digital signature. The cloud server generates a session key for secure communication if the signature is valid.
Step-4. Key Agreement According to Diffie-Hellman and ECC, the cloud server and the IoMT device use a secure key exchange protocol to agree on a shared secret key. All data transmitted between the device and the cloud is encrypted using the shared secret key.
Step-5. Secure communication Any communication network’s dependability primarily rests on its ability to flow continuously and securely. The network’s autonomous phases, which may function independently to provide a seamless connection, have made this possible.
Step-6. Parameter Update The cloud server sends a parameter update request (e.g., firmware update, configuration changes) to the IoMT. The device decrypts the request, applies the updates, and sends an acknowledgment back to the cloud server. The cloud server updates the device’s profile in the database to reflect the new parameters.
Security analysis of the proposed scheme
This section discusses the security analysis of the proposed scheme, including its ability to maintain patients’ data confidentiality, integrity, and authentication. We also discuss various potential attacks and provide a security analysis that demonstrates the proposed scheme is resistant to man-in-the-middle (MITM) attacks, based on the Canetti and Krawczyk security model.
Man-in-the-Middle (MITM) Attack This attack is not possible with our framework since it provides robust anonymous authentication. It prevents an attacker from carrying out such an attack. The key values are based on global patient identification. It means that if there is a new wireless sensor network (WSN) visit, an attacker who pretends to be a valid scheme will not be able to guess the key values. In addition, when the same WSN is present in the vicinity, the attacker will not be able to decrypt multiple messages since the cloud server has already encoded them using a session key.
Replay Attack An attacker is capable of replaying previous messages sent and received via the key exchange protocol. Nonetheless, because fresh random numbers are created to ensure the freshness of each session, the provisioning server recognizes the invalidity of the message.
Session Key Disclosure Attack This attack takes place when an adversary is able to intercept and retrieve the session key that is utilized for the purpose of encrypting communication between IoMT devices. In the proposed scheme, session keys are dynamically generated using identity-based cryptography and are never transmitted in plaintext.
Eavesdropping Attack In this, an attacker secretly listens to communication channels to steal sensitive patient data. Our scheme employs a robust encryption technique to ensure all transmitted patient data is encrypted using the session key.
Gateway Impersonation Attack This attack happens when an attacker masquerades as a legitimate gateway to deceive IoMT devices into revealing sensitive data. The proposed scheme uses identity-based authentication and a secure handshake process where both the gateway and devices validate each other’s credentials.
Off-line User Identity Predicting Attack This attack involves an adversary attempting to guess a user’s identity through offline analysis. The proposed scheme safeguards against this by incorporating identity-based cryptographic techniques where user identities are never exposed in plaintext.
Security Analysis Against MITM Attacks
Security analysis against a man-in-the-middle (MITM) attack based on Canetti and Krawczyk model is represented in Fig. 7.
The Schnorr signature scheme is effective in preventing MITM attacks primarily because of its reliance on the cryptographic hash function and the discrete logarithm problem. This signature scheme involves three main algorithms: key generation, signing, and verification. The scheme uses the discrete logarithm problem in a finite cyclic group for its security.
Theorem: The Schnorr signature scheme is secure against MITM attacks, assuming the hardness of the discrete logarithm problem and the security of the hash function.
-
1.
Non-interactive Signature Generation
-
There is no communication with any other party during the signing procedure. Sender A can sign any communication on their own without communicating with user B after they have generated their key pair.
-
-
2.
Signature Unforgeability
-
Assumption The features of the hash function H and the difficulty of the discrete logarithm problem determine the security of Schnorr signatures.
-
Reduction to Discrete Logarithm Problem An adversary must either solve the discrete logarithm problem or compromise the security of the hash function to forge a signature (r,s) for a message m without knowing the private key a. It is impossible to forge a signature due to the difficulty of these issues.
-
-
3.
Authenticity
-
Hash Function The hash function H ensures the reliance of the signature on the message m and random integer r. Therefore, an authentic signature used in one message cannot be used in another.
-
No Key Substitution The signature verification equation \(g^{s} = r \cdot y^{e} \; mod \; p\) involves the public key y and the hash H, which includes the message. Thus, an attacker cannot substitute User A’s public key with their own without failing the verification check.
-
Because of these features, an attacker can’t make a valid signature without the private key or by breaking cryptographic assumptions, even if they are able to read and change messages. Schnorr signatures therefore offer robust defense against Man-in-the-Middle attacks.
Results and simulation
In this section, we have discussed the computational performance of the proposed scheme.We have incorporated patients’ sensitive health information in both the encryption and decryption processes. Additionally, we have implemented an authentication mechanism for patients and hospital staff through a digital signing and verification process.
Simulation setup
The proposed security technique is used in a programming language to create the architecture of the suggested in-home patient monitoring system. Every task is completed on a PC running the Linux 18.04 Ubuntu operating system, which calls for a Core i5 processor clocked at 3.4 GHz, 8 GB of RAM, and GCC 4.9.5. C++ is used to code the pairing-based cryptography (PBC) library. In the simulation, we perform 20 iterations in a simulation of the proposed methods to get the desired result.
The relation between various security schemes and their features is presented in Table 3.This table shows different types of security features, such as a digital certificate, key escrow-free (so only the user knows their own private key), denial-of-service, trusted authority (so only a trusted authority can issue a digital certificate), fast revocation (which solves the issue of adding more users), and cryptographic workflow (sender and receiver share encrypted plaintext by a key). In this table, (\(\checkmark\)) represents that security features are found, and (\(\times\)) represents that security features are not found. From this table, we conclude that our proposed scheme provides all security features, while previous schemes lack some features.
Computational comparison
The computational cost is the term used to describe the time needed to execute cryptographic procedures. The primary cryptographic procedures used in this study include pairing, hashing, one-point addition, multiplication, and the exclusive-or (XOR) operation. The time taken for encryption, decryption, signing process, and verification process are shown in Figs. 8 and 9. We find that our proposed scheme takes less time as compared to other related schemes, as shown in Table 4. That means our schemes perform better than other existing schemes.
Conclusion and future research
Protecting patient privacy is an important issue that requires attention in light of recent developments in the Internet of Medical Things. The proposed scheme, ฿-ED-CRY would solve concerns and offer a different perspective on secure communication in the IoMT. The system includes a portable application that securely monitors patients’ medical conditions at all times from a remote location. This scheme protects personal information by performing more effective encryption and decryption operations and preserving user identity. We have demonstrated the robustness of the proposed scheme against man-in-the-middle attacks. The results of performance analysis indicate that the proposed scheme provides enhanced security and takes lower computational cost as compared to other related existing schemes.
Even while the proposed scheme works well for existing IoMT configurations, more research is necessary to fully understand its effects on security and performance in large-scale deployments.
Future research might investigate computationally less-intensive, lightweight-based security techniques and add the concept to make the scheme more scalable in the field of smart healthcare.
Data Availability
The datasets used and/or analyzed during the current study are available from the corresponding author on reasonable request.
References
Guo, P., Liang, W. & Xu, S. A privacy preserving four-factor authentication protocol for internet of medical things. Computers & Security 137, 103632 (2024).
Gupta, C. & Varshney, G. A lightweight and secure puf-based authentication and key-exchange protocol for iot devices. arXiv preprint arXiv:2311.04078 (2023).
Mondal, A., Chatterjee, P. S. & Ray, N. K. An optimal novel approach for dynamic energy-efficient task offloading in mobile edge-cloud computing networks. SN Comput Sci 5(5), 655 (2024).
Gaur, R. et al. A secure and efficient scheme based on unlinkability and anonymous traceable protocol for cloud-assisted iot environment. J Circuits, Syst Comput 32(18), 2350316 (2023).
Khajehzadeh, L., Barati, H. & Barati, A. A lightweight authentication and authorization method in iot-based medical care. Multimedia Tools and Applications, 1–40 (2024)
Yu, S. et al. Efficient ECC-based conditional privacy-preserving aggregation signature scheme in v2v. IEEE Trans Veh Technol 72(11), 15028–15039 (2023).
Mondal, A. & Chatterjee, P. S. Cloudsec: a lightweight and agile approach to secure medical image transmission in the cloud computing environment. SN Comput Sci 5(2), 237 (2024).
Kumar, S., Abhishek, K., Jhaveri, R., Alabdulatif, A. & Gaur, R. An efficient dual encryption of iomt data using lightweight security scheme for cloud based iot environment. In: Proceedings of the 38th ACM/SIGAPP symposium on applied computing, pp. 1782–1788 (2023).
Echenim, K.U. & Joshi, K.P. Iot-reg: A comprehensive knowledge graph for real-time iot data privacy compliance. In: 2023 IEEE International conference on big data (BigData), pp. 2897–2906 (2023). IEEE.
Pooranian, Z., Shojafar, M., Taheri, R. & Tafazolli, R. Pascoinfog/pasfog: Privacy-preserving data deduplication algorithms for fog storage systems. IEEE Consumer Electronics Magazine (2023).
Bissessar, D. & Adams, C. Construction and implementation of a privacy-preserving identity-based encryption architecture. J. Inf. Secur. 14(4), 304–329 (2023).
Das, M. L. A key escrow-free identity-based signature scheme without using secure channel. Cryptologia 35(1), 58–72 (2010).
Liu, X., Sun, Y. & Dong, H. A pairing-free certificateless searchable public key encryption scheme for iomt. J. Syst. Architect. 139, 102885 (2023).
Boneh, D., Ding, X., Tsudik, G. & Wong, C.M. A method for fast revocation of public key certificates and security capabilities. In: 10th USENIX Security Symposium (USENIX Security 01) (2001).
Shamir, A. Identity-based cryptosystems and signature schemes. Adv Cryptol: Proc CRYPTO 84(4), 47–53 (1985) (Springer).
Methodology - Internet of Medical Things (IoMT) Market | Fortune Business Insights — fortunebusinessinsights.com. https://www.fortunebusinessinsights.com/industry-reports/methodology/internet-of-medical-things-iomt-market-101844. [Accessed 12-09-2024]
Guezguez, M. J., Rekhis, S. & Boudriga, N. A sensor cloud for the provision of secure and qos-aware healthcare services. Arab. J. Sci. Eng. 43(12), 7059–7082 (2018).
Bojjagani, S. et al. The use of iot-based wearable devices to ensure secure lightweight payments in fintech applications. J King Saud Univ-Comput Inf Sci 35(9), 101785 (2023).
Sahana, S. C., Das, M. L. & Bhuyan, B. A provable secure key-escrow-free identity-based signature scheme without using secure channel at the phase of private key issuance. Sādhanā 44, 1–9 (2019).
Walid, R., Joshi, K.P., Elluri, L., et al. Secure and privacy-compliant data sharing: An essential framework for healthcare organizations. In: 10th International conference on mathematics and computing ICMC 2024 (2024).
Al-Zubaidie, M.H. & Razzaq, R.H. Maintaining security of patient data by employing private blockchain and fog computing technologies based on internet of medical things. Informatica48(12) (2024).
Patil, A., Ashwini, D., TP, R.R. & Srinivas, T. A mobile cloud based approach for secure medical data management. International Journal of Computer Applications119(5) (2015).
Kumar, M. & Chand, S. A provable secure and lightweight smart healthcare cyber-physical system with public verifiability. IEEE Syst. J. 16(4), 5501–5508 (2021).
Maarouf, A., Sakr, R., & Elmougy, S. An offline direct authentication scheme for the internet of medical things based on elliptic curve cryptography. IEEe Access (2024).
Lin, H. Y. Integrate the hierarchical cluster elliptic curve key agreement with multiple secure data transfer modes into wireless sensor networks. Connect. Sci. 34(1), 274–300 (2022).
Samal, K., Sunanda, S. K., Jena, D. & Patnaik, S. A lightweight privacy preservation authentication protocol for iomt using ECC based blind signature. Int J Eng Bus Manag 17, 18479790251318536 (2025).
Misra, G., Hazela, B., & Chaurasia, B.K. A user-adaptive privacy-preserving authentication of iomt using zero knowledge proofs with ecc. Multimedia Tools and Applications, 1–32 (2025).
Patil, R. Y., Karati, A. & Patil, Y. H. A signcryption with identity-based authentication for secure EHR sharing in iomt utilizing ECC. Int. J. Inf. Technol. 16(8), 5133–5148 (2024).
Dhar, C. K. & Majumder, A. isecurehealth: an efficient and secure technique to exchange health data using iomt devices. Smart Health 33, 100504 (2024).
Cano, C.A.G., Castillo, V.S., Castillo-Gonzalez, W., Vitón-Castillo, A.A., & Gonzalez-Argote, J. Internet of things and wearable devices: a mixed literature review. EAI Endorsed Transactions on Internet of Things9(4) (2023).
Chen, C.-M., Liu, S., Li, X., Islam, S. H. & Das, A. K. A provably-secure authenticated key agreement protocol for remote patient monitoring iomt. J. Syst. Architect. 136, 102831 (2023).
Ouiazzane, S., Addou, M. & Barramou, F. A zero-trust model for intrusion detection in drone networks. Int. J. Adv. Comput. Sci. Appl14(11) (2023).
Liu, S., Wang, Z., Kumari, S., Lv, J. & Chen, C.-M. Provably secure anti-phishing scheme for medical information in smart healthcare. IEEE Internet of Things Journal (2024).
Gaur, R. & Prakash, S. Privacy prevention and nodes optimization, detection of iout based on artificial intelligence. Wirel Personal Commun 138(1), 67–97 (2024).
Li, X., Wang, H., Ma, S., Xiao, M. & Huang, Q. Revocable and verifiable weighted attribute-based encryption with collaborative access for electronic health record in cloud. Cybersecurity 7(1), 1–19 (2024).
Gaur, R. et al. A machine-learning-blockchain-based authentication using smart contracts for an ioht system. Sensors 22(23), 9074 (2022).
Khan, N. et al. An ECC-based mutual data access control protocol for next-generation public cloud. J Cloud Comput 12(1), 101 (2023).
Mondal, A. & Chatterjee, P.S. A systematic literature survey on data security techniques in a cloud environment. In: 2022 OITS International conference on information technology (OCIT), pp. 451–456 (2022). IEEE.
Author information
Authors and Affiliations
Contributions
Mr. Sanjay Kumar designed the idea of framework of the research. He created and tested the proposed algorithm. Sanjay also prepared the first draft of the manuscript. Kumar Abhishek played a role in the final model’s development, testing, and verification. Throughout the duration of the endeavor, Sitharth Selvrajan provided guidance and supervision. Managed all correspondence with the journal and served as the corresponding author, overseeing the submission process.
Corresponding author
Ethics declarations
Competing Interest
No
Dual Publication
No
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Kumar, S., Abhishek, K. & Selvarajan, S. A lightweight and secure authentication and privacy protection scheme for internet of medical things. Sci Rep 15, 23876 (2025). https://doi.org/10.1038/s41598-025-05910-4
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-05910-4
Keywords
This article is cited by
-
Schnorr approval-based secure and privacy-preserving data aggregation with dynamic clustering and fault tolerance for wireless body area networks
Journal of King Saud University Computer and Information Sciences (2025)