Abstract
Some of the potential advancements in information and communication technology (ICT), like artificial intelligence (AI) with federated learning (FL), which are particularly used in the transformation of industrial environments, are driven by digital technologies and can increase the efficiency and dependability of systems. The world has recently become more interconnected as a result of digital technology adoption but with some significant drawbacks. One of the major problems that arises as a malevolent possibility is cybercrime, which poses a threat to governments, corporations, and societies—most significantly, civil society. It is now feasible to work with more than two people to integrate Advanced Digital Technology (ADT) and move the foundation in the direction of a strong hierarchy, but in a complicated way, which has turned into a playground for cybercriminals. The idea of zero trust offers some sweetness in demand for threat detection by autonomously based FL, ML, and DL to address such difficult elements. This paper’s main objective, however, is to offer an investigative report based on cyber vulnerability detection using AI, ML, and DL in order to shield the ecosystem from malevolent attacks before they happen. Examining machine learning-enabled classifiers and ensembles for network intrusions and autonomous malicious detection is the secondary objective. Therefore, it explains how we can combine the two models to analyze the context of attacks more effectively and efficiently and how to respond by implementing network security and Internet of Things (IoT) security strategies, such as the stop-and-listen method. When developing and implementing an integrated AI-enabled zero-trust intrusion detection architecture into the present industrial IoT ecosystem, there is a significant discussion about difficult issues and potential solutions. Given the notable outcomes of the simulations we obtained, it is evident at the conclusion of this research that the proposed solution is a strong contender for implementation in the real-time industrial setting.
Similar content being viewed by others
Introduction
The Internet of Things (IoT) has gained popularity due to its association found in every aspect of daily life, like its involvement in smart medical systems, intelligent industrial environments, smart cities, and IoT transportation for traveling autonomously1,2. In order to provide neutral connectivity to the devices, a significantly large number of data that is interoperable from one to another, which includes personal information such as data of authentication, geolocation, GPS connectivity and sharing resources, and coupling with the sensitive data from the interoperable environment within the same ecosystem. Undoubtedly, managing real-time data is a challenging problem, especially in the Industrial Environment (IE), which is only possible while proposing a standardized hierarchy of data organization, for example, captured, shared, examined, analyzed, presented, and preserved dynamically3,4. In short, it is clear that the IoT derives, and related ecosystems need to be more protected, which is often a complex task because of enforcing rigorous physical security measures. In addition, there are other reasons, like open and closing and dispersed registration of a huge number of participants, which create a compound limitation, such as financial implications. Furthermore, the architecture of IoT systems is critical in terms of managing device diversity from different developing environments while integrating distinct protocols and their operations. It is worth noting that the existing IoT devices have potentially a huge ground for the occurrence of malicious attacks3,4,5. In IE, the technological experts, along with the enterprises prefer privacy protection and security promotions in order to achieve the cost of resource reduction, which is directly proportional to the competitive benefits. Such type of practices affects the technological privacy protection and security of their products.
However, the compound limitations are derived from the computational, network, and preservation-related problems in the device environment, where a discussion of conventional privacy protection is raised5,6. Thus, algorithms of conventional privacy and security of IoT devices are unreliable to be integrated and deployed in the domain of small medium-sized enterprises (SMEs) due to constraints of cost management of IoT systems. As per the recent report, the rate of IoT devices can robust drastically in a number of utilizations worldwide up from 10 billion to 28.8 billion approximately in between 2023 and 20305,6,7. More than that, it is evaluated that the current IoT systems rely on the non-standard lifecycle, hierarchy, and protocols, which leads to environmental vulnerabilities that transform into malicious threats. The availability of different third-party open-source software plays a critical role in the adverse impact on the entire Industrial IoT (IIoT) ecosystem. All such prospects have the same security weakness that raises infection exploitation, systems threats and malware, personal information leakage, and authentication. In addition, network scans, buffer overflow, and injection-like command-based are also critical popped up throughout the investigation. Resultant separates a list of advanced attacks evolved in the IoT environment. More than that, the evaluation of IoT vulnerability indicates the weakness in the process of response techniques that are actively adopted in the current scenario8,9.
In general, there are different classical approaches proposed and adopted in software vulnerability analysis, mainly for IoT-enabled equipment for privacy protection and security-related active threat detection using Artificial Intelligence (AI), especially Machine Learning (ML)7,8,9. Most of these AI-based algorithms are increasingly utilized to examine the patterns of attacks being trained in the system for fast intrusion detection and related vulnerabilities9,10. Some of the AI algorithms use cluster functions for more specifically evaluate the occurrence of intrusions throughout. Due to the low availability of computational power, processing, and energy in consumption of training the systems7,9; in order to these metrics, ML plays a significant role in implementing a sufficient large amount of anomaly detection, which means such ML-based proposals consume low cost of memory with respect to execution time. Throughout this process, the overall cloud network and communication environment can be investigated while evaluating before transmission8,10. Undoubtedly, we must say that the ML techniques are more supportable and reliable compared to the traditional method of intrusion detection in the IoT environment. Unfortunately, the restriction from the IoT connectivity and networking while node-to-node interoperability environment, there are still challenging prospects counted based on the recent infrastructure of ML integrates with IoT for active intrusion detection and vulnerabilities.
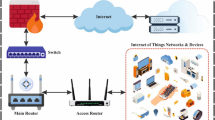
Traditionally, software-enabled intrusion detection is examined and detected on high-performance centralized server-based architectures due to the effectiveness of the ecosystem11,12,13,14. On the other side, the lightweight nature of IoT devices makes it difficult to such software in terms of scheduling high-intensive detection and response tasks12,14. Nowadays, different types of research have been conducted that mainly adopt the techniques of ML in IoT for achieving better results. However, the insufficiency of IoT resource constraints, especially for the industrial environment needs to be considered, which is required to make a realistic attack performance prospect that cannot be conducted previously. To provide a solution for addressing a new paradigm for an efficient and reliable process of intrusion detection, along with the integration of optimization by training data size to detect system intrusion effectively and robustly while managing loss function. The ratio of data sampling in the collected dataset and training the AI-enabled ML techniques in the IoT in accordance with the optimal point finders, which are between performance and size of data. In addition, the concept of zero-trust intrusion detection in the industrial IoT diverts the dynamics in terms of defining a set of cybersecurity principles that can be used to make an approach for moving network defense from malicious attacks, the perimeter of a wide area, static network management that mainly focusing on systems, users, and ecosystem, along with a personal or small group of resources, as shown in Fig. 1. In this manner, the adaptation of an AI-enabled zero-trust intrusion detection strategy can be counted successfully, especially for industrial things management and organization, as shown in Fig. 1.
Research motivation and contributions
A recent industrial environment is categorized into three subunits (i) manufacturing, (ii) production, and (iii) industrial things management. In these divisions, the role of wireless sensor networks and IoT devices is crucial throughout the development cycle of industrial products and manufacturing. Due to this scenario, the infrastructural security and privacy protection of IoT devices require different paradigms to tackle their integrity while transmissions, in which physical to man-in-the-middle attacks, like botnet, false data injection, and distributed-denial of service (DDoS) need to be evaluated before. To achieve such prospects, the metrics of intrusion detection software can be adjusted in terms of complexity, code reusability, functional parameters, and detection methods using one of the strategies, like an abstract syntax tree. But in this paper, an AI-enabled zero-trust intrusion detection strategy applies to IoT networks to support the industrial environment to get better results (defending from advanced attacks, like DDoS), including efficiency, effectiveness, robustness, and reliable manner. This paper majorly focuses on the practical detection of ML-based intrusion that occurs in industrial transmission and delivery, but it should evaluate performance from consecutive accuracy, complex architectural management, computational limitations, memory consumption, and latency. Substantially, we need a standardized design that alleviates the trade-off of both the devices and performance. By analyzing such critical problems, this paper addresses some of the major research questions as follows:
-
Question 1: What AI-enabled ML techniques are suitable for adopting to implement an efficient and effective zero-trust intrusion detection strategy for industrial things?
-
Question 2: How the current architectures integrate with the autonomous penetration testing and support?
-
Question 3: What type of penetration testing identifies security issues of IoT in the industrial and manufacturing environment?
-
Question 4: Which criteria can be considered for creating or selecting a standardized way to proposed zero-trust intrusion detection architecture for IoT systems?
The main contributions and objectives of this paper is defined as follows:
-
This paper addresses via presenting the infrastructural weakness of the existing IoT systems through evaluating the recent published (more than fourth (40) that are most cited) state-of-the-art research publication. In the process of examination, various impactful privacy protection and security related problems highlights, which can be considered in this proposed work while designing the architecture.
-
A standardized process of AI-enabled zero trust intrusion detection software implementation for IoT systems, is proposed.
-
In this paper, we propose a novel architecture that define a pathway to create AI-enabled ML connectivity with zero trust strategy for real-time identification of intrusions in the industrial environment.
-
The result of this proposal is based on the updates of such parameters as follows:
-
The open research gaps are highlighted that involved in the process of implementation, along with system’s deployment. And so, in this manner, we propose some of the possible solutions of each prospect in the end of this research.
Structure of this paper
The section and subsections of this paper are aligned as follows: In Sect. 2, a detailed argument of investigation on the topic of AI-based zero-trust intrusion detection in an industrial environment and related hierarchy. And so, the role of IoT networks in cyberspace is listed. The preliminaries and fundamental knowledge of the current problem examination are discussed, along with the description of integrated technologies that are associated with the creation of the proposed architecture of intrusion detection using AI-enabled zero trust strategy for industrial things in Sect. 3. Through the simulations, this paper presents unique results that are generated via deploying the proposed strategy of zero trust and compared with state-of-the-art schemes in Sect. 4. In Sect. 5, a list of open research problems that still require expert consideration is mentioned with possible solution descriptions. Finally, this work concluded with the statement of conclusions and future research directions in Sect. 6.
Background and related work
This section identifies that IoT security is mainly a complex and achievable manner due to their broad range of distinct underlying IoT components, along with the connectivity of wireless sensors network15,16. The current architecture of IoT technology is categorized into three subunits such as (i) embedded devices connectivity, (ii) radio communications, and (iii) software integrations. The embedded devices connectivity is mainly designed for equipping sensors association to capture and examine data from the environments on different devices with different data formats by using radio-frequency identification, such as wireless sensors network and GPS. On the other side, radio communication enables the interconnectivity between devices for efficient intercommunication like sharing and exchange. The common communication protocols are the cellular network, LoRa-WAN, Wi-Fi, Wave, etc. Whereas the software integration makes everything on one page, the focusing factor of this subunit is the firmware that bridges both environments, like mobile and web, in order to run the system effectively. However, device interface management is one of the critical prospects that is resolved by setting up the cloud components connected to the devices and others. for instance, these subdivisions in the architecture of IoT make this technology weak; due to this, security and privacy protection are the fundamental concerns involved in this environment and become one of the discussion factors in every domain of investigation. The major investigation of this study is divided into two different sections, including AI-based zero-trust intrusion detection in industrial environments and the role of IoT networks in cyberspace as follows:
AI-based zero-trust intrusion detection in industrial environment
AI-enabled zero trust strategy is considered an architectural module of security that mandates, which is granted before, by maintaining data accessibility and applications15,16,17. However, users either work in the environment of organizations or outside, which requires different channels for networks to intercommunicate, such as implicit and explicit requests. For instance, there are authentication, authorization, and security protocols for undergoing/ongoing connectivity, and their posture validation maintenance requires additional technological integration for autonomous decision-making. In this manner, the revolution of AI in cybersecurity creates new paradigms, like proactive threat detection, predictive insights, automated response, user behavior monitoring, threat hunting, adaptive access control, and intrusion identification14,15. Network intrusion detection is another key area that is covered by AI in cybersecurity, where an Intrusion Detection System (IDS) can be capable of examining the patterns of network traffic and redundancies. It can help to note the point of unusual impacts that occur in the network and evaluate the point of breach and the point of assault15,16. By proposing such developments from the side of cybersecurity experts16,17, a fast and reliable evaluation of the large volume of network data takes place using AI techniques that reduce the effect along with speeding up the identification and restriction process to attacks.
Table 1 presents the analysis report of the current adoptive AI-based zero-trust strategy for intrusion identification and its detection and vice versa in the real-time environment, where the examination metrics are defined as follows: (i) major research objectives, (ii) as used with the methods, models, or techniques, (iii) benefits of this proposed work, (iv) comparative analysis and opportunities, and (v) references of each state-of-the-art publication.
The role of internet of things (IoT) network in cyberspace
As per the evaluation of state-of-the-art publications24,25,26,27,28,29, it is clear that IoT technology is becoming more closely integrated into everyday lifestyles, most importantly in the enterprise environment, which is a great need for cybersecurity. The major role of cybersecurity is to encompass the technological activities employed to secure and protect in terms to safeguard devices and the platforms that are associated with the networks from malicious threats. From an industrial perspective, operations like manufacturing and product delivery, the IoT units have extremely sensitive information and handling. The critical aspects of IoT device compromises, weak network points, and connectivity of vulnerable devices raise the malicious attackers, most probably the physical deranges and the ability to retrieve intelligence without requiring any kind of authentication24,25,26. While shifting the IoT to interconnectedness, the technology has raised critical drawbacks, such as managing potential financial and privacy protection damages and risk mitigation. In addition, the emergence of device utilization impacts drastically by increasing network consumption, which directly affects privacy protection and security-related prospects in terms of increasing the opportunities for cybercriminals entrance into the systems and access data27,28. Furthermore, cost-effective convenience from the business point of view creates consequences of the biggest cybersecurity problems due to neglect of the integration of different IoT components, which are lightweight in nature, and also because of unsecure growing network interconnectivity. To tackle such challenging issues involved in the IoT environment, the experts of24,25,26,27,28,29 discussed the crucial aspects that need to be adopted before designing, developing, and deploying the architecture as follows:
-
Building infrastructure.
-
Association with industrial infrastructure.
-
Communication infrastructure integration and testing.
Preliminaries
Recently, AI-enabled Deep Learning (DL) models (including Artificial Neural Networks (ANNs), Convolutional Neural Networks (CNN), Recurrent Neural Networks (RNNs)) have gained a lot of attention, especially in the cybersecurity domain, most importantly in network intrusion detection purpose24,25. Due to this, we can achieve availability to adopt such methods for getting different format of data form different datasets, which directly impacts the performance enhancement. On the other side, the resource management of these methods is yet to be the complex prospects-critical domain where data management, organization, and optimization is important. In this manner, most of the research directions shifted towards the side of ML, where the experimental study elaborates that the three different machine learning methods perform drastically better, such as supervised learning, unsupervised learning, and semi-supervised learning. And so, the designed models-based on these mentioned methods that are listed as one of the topmost adoptive strategies for intrusion detection and evaluate network vulnerabilities26,27,28,29: (i) random forest, (ii) logistic regression, (iii) gradient boosting machine learning, and (iv) AL-enabled adoptive deep learning approach. The detail of these models is discussed as follows:
-
Random Forest: It is a partitioning algorithm, which is recursive in nature. It allows to create various decision trees that average the predictive results at the end, which reduces the load of computational resources.
-
Logistic Regression: One of the generalized linear algorithms that is mostly used for the context of binary classification and analytics based on prediction.
-
Gradient Boosting Machine: It does not create different trees for decision making-create an average outcome which operates in a sequential manner. The model specifically boosts the weak learner prospects by correcting the error in each step of passing.
-
Advanced Deep Learning-Adoptive Learning: A pre-trained model that can collaborate with fusion process to build a more powerful learner. It is overall scenario, three things need to be associated with, such as big data, computational processing units (like GPU), and strategy of optimization (for example, metaheuristic-enabled optimization).
Whereas the algorithms are setup in accordance with the following manner:
-
1.
For feature scaling of intrusion throughout the process of identification:
$$\:a=a-\text{min}\left(a\right)/\text{m}\text{a}\text{x}\left(a\right)-\text{m}\text{i}\text{n}\left(x\right)$$(1) -
2.
Hyperparameter for data capturing and optimization:
$$\:\text{a}\left(\text{b}\text{e}\text{s}\text{t}\:\text{c}\text{a}\text{s}\text{e}\right)=average\:\left(\text{min}\left(f\left(a\right)\right)\right)\to\:a\:belongs\:to\:inside\:liited\:domain\:A$$(2) -
3.
Parameter for overall accuracy measures:
$$\:Xi+Xn\:/Xi+Xn\:+Frequency\:of\left(Fi\right)+\:Frequency\:of\left(Fn\right)$$(3) -
4.
Parameter for overall precision:
$$\:Xi\:/Xi+Fi\:\:\:\:\:\:$$(4) -
5.
Parameter for overall recall:
$$\:Xi\:/Xi+Fn\:\:\:\:\:\:\:$$(5) -
6.
Parameter for overall F1-score:
$$\:F1-score=2*(precision*recall\:/\:precision+recall)$$(6) -
7.
False Positive and True Positive Calculation:
$$\:Fi\:/Fi+Xn$$(7)
In this paper, a standardized process of training the proposed AI-enabled zero-trust architecture is presented, where the mentioned ML and DL models are getting used to train a real-time intrusion identification and detection for industrial environment (such as industrial, manufacturing, and products point of view) is defined as follows (as shown in Fig. 2):
-
Step#1: set the surface for protection (for each industrial units);
-
Step#2: data flow plan (like industrial, manufacturing, and production related);
-
Step#3: design architecture (the proposed AI-enabled zero-trust architecture, as shown in Fig. 3);
-
Step#4: create regulatory (industrial verified protocols); and.
-
Step#5: manage the designed industrial network.
Problem description, formulation, and the proposed working hierarchy
An endless increment in the usage of IoT devices has initiated a seamless bridge between digital and physical environments. The IoT is performed in a wide area of internet management concept, where internet-based systems that are seamlessly connected can share and exchange data because of the design of interoperability. Due to this, technology is a primary factor that enables cyber-physical systems, the industrial metaverse, and digital twins. However, the intersecting nature of IoT technologies; includes different components to fulfil the requirement of technological deployment or maintain the ecosystem, and such prospect creates critical security challenges. For instance, IoT security comes up with the achievable of wireless security, mobile device security, and network security. In order to tackle this in the industrial environment, this paper proposed a novel architecture using an AI-enabled zero-trust strategy to create privacy protection and security in industrial, manufacturing, and production units, as shown in Fig. 3. This proposed architecture is split into three different sub folds, such as the interconnection of industrial units, the perimeter of zero trust strategy (which is integrated with AI), and the internet. In industrial unit interconnection, all manufacturing, industrial, and production units of the industry are interconnected in such a way that they can intercommunicated with the dedicated channels of explicit and implicit, respectively, as shown in Fig. 3. On the other side, the Internet connects all such units and zero-trust architecture with the centralized network connection. In the third fold of this proposed architecture, we design a perimeter that is integrated with the AI-enabled ML/DL-based zero-trust architecture that can derive a model for industrial unit security, where we design, create, and deploy secure VPN (for remote users’ connection) and internet tunnel (for explicit delivery of industrial, manufacturing, and product units). In addition, with the association of AI, we can able to maintain some of the highlighted prospects: such as (i) creating and deploying a secure access service edge-enabling system that helps in unifying software development wireless access network and network security protocols into a centralized cloud native-services, (ii) schedule micro-segments, (iii) integrates multi-factor authentication, (iv) associate the principle of least privilege, (v) end-point validation, (vi) operationalized zero-trust, as shown in Fig. 3.
Datasets description and formulation
The discussion of datasets is initiated in this section, where different types of datasets are used with different range of applicational scenarios integrated for efficient, fast, reliable, and effective network intrusion detection purposes, including network intrusion identification, malware detection in industrial units, IoT vulnerabilities, and involved other cyber threats. The name of the benchmark dataset that is used in this paper is addressed as follows:
-
1.
Dataset #1: Canadian Institute of Cybersecurity—IDS Dataset
-
a.
Observations: 25k + observations are registered.
-
b.
Flagged as attacks: network attacks, IDS, IoT device vulnerabilities.
-
c.
Normal traffic: 1200+.
-
d.
Traffic behaviors: Normal.
-
e.
Full form encompasses observations: 29k full encompasses observations.
-
f.
Spin of original dataset: 20%.
-
a.
-
2.
Dataset #2: Vizsec—UGR’16
-
a.
Observations: 21k + observations are registered.
-
b.
Flagged as attacks: network attacks, IDS, IoT device vulnerabilities.
-
c.
Normal traffic: 1700+.
-
d.
Traffic behaviors: Normal.
-
e.
Full form encompasses observations: 28k full encompasses observations.
-
f.
Spin of original dataset: 25%.
-
a.
-
3.
Dataset #3: Kaggle—Network Security
-
a.
Observations: 19k + observations are registered.
-
b.
Flagged as attacks: network attacks, IDS, IoT device vulnerabilities.
-
c.
Normal traffic: 1100+.
-
d.
Traffic behaviors: Normal.
-
e.
Full form encompasses observations: 24k full encompasses observations.
-
f.
Spin of original dataset: 22%.
-
a.
Results and discussion
Before initiate the discussion of simulation results, some of key assumptions are highlighted due to implement and deployment of the proposed AI-enabled zero-trust architecture for industrial environments. The list of features are as follows:
-
Processor: Intel core i7 vPro Processor with 3.2 GHz clock speed is required;
-
Memory: Minimum of 16 GB RAM up to 32 GB RAM;
-
Solid State Drive: Minimum of 256 GB is required;
-
Network: Minimum of 4–6 Mbps to 1 Gbps support is required;
-
Wireless communication sensors connectivity is required;
-
Two intercommunication channels are required for implicit and explicit industrial transactions.
However, Figs. 5 and 6, and 7 illustrate the working hierarchy of the proposed AI-enabled (majorly ML adaptive learning model) with zero-trust architecture for real-time network intrusion detection, whose metrics are the rate of intrusion identified with respect to time(s). In this test, we receive a prominent result, which is completely unique, where the rate of intrusion is identified = 273 in 563 s, as shown in Fig. 5. On the other side, DL performs almost the same as ML; in this evaluation, we receive a fluctuation in between the rate of intrusion identified = 261 in 1955 s, as shown in Fig. 6. In test 3 (zero-trust with clustering features), we receive a fluctuation in between the rate of intrusion is identified = 273 in 821 s, as shown in Fig. 7.
Figures 8 and 9 present the True Positive Test (1) and False Positive Test (1) for both the models that are based on AI-enabled (majorly ML adaptive learning model and DL model, as mentioned in Sect. 3) with zero-trust architecture for real-time network intrusion detection and IoT vulnerabilities, whose metrics are the rate of intrusion identifies on the IoT network with respect of time(s). In both these tests (1) (2), we receive a good result with uniqueness, where the rate of intrusion is identified = 266 in 541 s, as shown in Fig. 8. On the other side, DL performs almost the same as ML; in this evaluation, we receive a fluctuation in between the rate of intrusion is identified = 233 in 821 s, as shown in Fig. 9. However, the overall result we received in the proposed simulations and results, where the cost of computation used by ML algorithms is 13.1% (reduction) and maintains 97.4% efficiency. On the other side, DL consumes 17.3% of computational resources due to the management of complex layers but maintains an efficiency of up to 98.7%.
The results of the proposed AI-enabled zero-trust architecture is compared with the list of state-of-the-art methods as follows30,31,32,33,34,35,36,37:
-
B. Sharma et al., Explainable artificial intelligence for intrusion detection in IoT networks: A deep learning based approach.
-
A. Alalmaie et al., Zero Trust Network Intrusion Detection System (NIDS) using Auto Encoder for Attention-based CNN-BiLSTM.
-
X. Chen et al., Zero trust architecture for 6G security.
-
C. Zanasi et al., Flexible zero trust architecture for the cybersecurity of industrial IoT infrastructures.
-
F. Naeem et al., Federated-learning-empowered semi-supervised active learning framework for intrusion detection in ZSM.
-
X. Larriva-Novo et al., Leveraging Explainable Artificial Intelligence in Real-Time Cyberattack Identification: Intrusion Detection System Approach.
-
A. Singh et al., Transfer Fuzzy Learning Enabled Streebog Cryptographic Substitution Permutation Based Zero Trust Security in IIOT.
-
S. Shen et al., Deep Q-network-based heuristic intrusion detection against edge-based SIoT zero-day attacks.
Tables 3 and 4 present the report of comparative analysis (both the tests (1)(2)), which is done between the proposed architecture with other state-of-the-art methods30,31,32,33,34,35,36,37, where the metrics of compression are as follows: (i) context of comparison, (ii) zero-trust architecture, (iii) collaborative technique for distributed access control architecture and management, (iv) classical access control, and (vi) overall impacts.
Open research problems
In this context, we highlight and discuss the open research gaps that are involved in the process of implementation, along with the deployment of AI-enabled zero-trust-based real-time intrusion identification and prevention as follows:
Technological integration and the role of AI
As the revolution occurs in the industrial and manufactural environment day-to-day, AI plays a significant role in terms of allowing security experts to make an informed decision to secure information effectively and live within the less human resources in the server rooms38,39,40,41. By applying AI in the dynamic monitoring domain for productional analysis, AI performs far better compared to the classical methods due to eliminating repetitive work like humans do in real-time, including video surveillance shift-to-shift monitoring and routine server checks for malicious prevention38,40. While at the same time, enhancing real-time monitoring efficiency and accuracy is a critical task for humans, AI employs threat recognition on overall industrial monitoring setups at machine time with speed. However, existing security professionals often struggle to identify the dynamic protocols by means of time to detect new threats. Furthermore, most of the industrial units still use a classical method for hunting treats which is often enough because it consumes more computational resources and time due to execution cycle completion. Altering fatigue is another perspective of this angle too. On the other side, AI security mainly replaces the classical method in some of the giant’s industrial units by helping to save time in hunting threats, which promptly detects and stops malicious intrusions, along with the reduced set of interventions required. However, the complex architecture of AI-enabled ML techniques requires computational processing and programming-related efforts to handle multi-layer networks, especially Artificial Neural Networks (ANNs). Resultant, a standardized hierarchy is required to lighten the complexity of ML algorithms in both perspectives, like efficient resource management and performance.
Hierarchy of applying zero trust in industrial environment
The hierarchy of applying AI-enabled zero-trust strategy for intrusion detection in the industrial domain is mentioned as follows42,43,44,45,46,47: (i) create and deploy secure access service edge-enabling system that helps in unifying software development wireless access network and network security protocols into a centralized cloud native-services, (ii) schedule micro-segments, (iii) integrates multi-factor authentication, (iv) associate the principle of least privilege, (v) end-point validation, (vi) operationalized zero-trust (like ease of development, scalability, security, visibility, and service & support). However, implementing a zero-trust model in a giant enterprise demand buy-in from participating users to ensure training effectiveness, design and plan, and development. For instance, the implementation of a zero-trust strategy impacts every department in the industrial domain, so the managers of all sectors need to participate and agree on the applicational approach and related protocols. These mentioned critical prospects need to be addressed while deploying an AI-enabled zero-trust strategy in the industrial environment.
Intrusion detection and countermeasures
The discussion of intrusion investigation is based on physical geotechnical examination that integrates with the role of cyberpunk literature that ensures privacy protection and security programs, which means secure computerized information from being accessed by malicious persons, such as it can be malicious insiders or malicious attackers41,42,43. In the real-time environment of industry, firewalls and their related software components need to be classified for the significance of manufacturing and product delivery electronically. In order to make this possible, there is a requirement to create a strong connection between the cyberpunk literature and the cybercrime investigation process.
Modern technology and the criteria of vulnerabilities investigation
In the advanced digital technological environment, it is clarified that the criteria of vulnerability investigation, which are designed for the proper, efficient, and reliable evaluations, are discussed as follows40,43:
-
i.
obtain the identified data,
-
ii.
obtained the identified data on the systems’ of affected industrial units41,43,
-
iii.
examine the known particular component of the intrusion using zero-trust strategy,
-
iv.
determine the systems are in secured mode,
-
v.
check if not, then sent alert,
-
vi.
address the category of intrusion, and.
-
vii.
document.
Conclusion and future work
This study examines the adaptive advantages of a zero-trust approach powered by AI for real-time intrusion detection on industrial IoT networks. Furthermore, ML’s function in autonomous detection is emphasized, wherein intrusions are classified using a list of learnt datasets. To improve privacy protection and security-related measures, particularly in the industrial setting, the zero-trust architecture idea offers a means of designing “never trust—always verify” infrastructure. The current investigation examined all of these possibilities and proposed a new architecture that establishes a framework for implementing a zero-trust strategy based on AI-enabled machine learning for real-time intrusion detection and identification, and it limits them for security reasons in the industrial sectors. This architecture is supported by a standardized procedure for implementing AI-enabled zero-trust intrusion detection software for Internet of Things systems. Significantly, this work is unique because it uses the most recent iteration of zero-trust intrusion detection parameters, including (i) logistic regression, (ii) recursive partitioning, (iii) gradient boosting, and (iv) DL-AI for fine-tuning Deep Neural Networks (DNNs). Through the simulations, we receive results of the proposed AI-enabled zero trust intrusion detection architecture, which is far better compared to other state-of-the-art methods. The fluctuation in-between false-positive and true-positive from both perspectives of ML and DL is presented, where the cost of computation used by ML algorithms is 13.1% (reduction) and maintains 97.4% efficiency. On the other side, DL consumes 17.3% of computational resources due to the management of complex layers but maintains efficiency up to 98.7%. The application of this proposed architecture in real-time industrial units can be considered one of the candidates due to it provides integrity, effectiveness, efficiency, and reliability.
Data availability
Data Availability Statement: All data generated or analyzed during this study are included in this published article.
Abbreviations
- ADT:
-
Advanced digital technology
- IoT:
-
Internet of things
- AI:
-
Artificial Intelligence
- FL:
-
Federated learning
- ML:
-
Machine learning
- DL:
-
Deep learning
- ICT:
-
Information and communication technology
- IE:
-
Industrial environment
- SMEs:
-
Small-medium size enterprises
- GPS:
-
Global positioning system
References
Luo, H., Zhang, Q., Sun, G., Yu, H. & Niyato, D. Symbiotic blockchain consensus: cognitive backscatter Communications-Enabled wireless blockchain consensus. IEEE/ACM Trans. Networking. 32 (6), 5372–5387. https://doi.org/10.1109/TNET.2024.3462539 (2024).
Luo, H., Sun, G., Chi, C., Yu, H. & Guizani, M. Convergence of symbiotic communications and blockchain for sustainable and trustworthy 6G wireless networks. IEEE Wirel. Commun. 32 (2), 18–25. https://doi.org/10.1109/MWC.001.2400245 (2025).
Wang, Q. et al. Elevator fault diagnosis based on digital twin and PINNs-e-RGCN. Sci. Rep. 14 (1), 30713. https://doi.org/10.1038/s41598-024-78784-7 (2024).
Khan, A. A. et al. GAN-IoTVS: A Novel Internet of Multimedia Things-enabled Video Streaming Compression Model Using GAN and Fuzzy Logic (IEEE Sensors Journal, 2023).
Zhang, Y. et al. A Multi-Layer information dissemination model and interference optimization strategy for communication networks in disaster areas. IEEE Trans. Veh. Technol. 73 (1), 1239–1252. https://doi.org/10.1109/TVT.2023.3304707 (2024).
Khan, A. A. et al. A lightweight scalable hybrid authentication framework for Internet of Medical Things (IoMT) using blockchain hyperledger consortium network with edge computing. Sci. Rep. 15(1), 1–20 (2025).
Khan, A. A. et al. Data Security in Healthcare Industrial Internet of Things with Blockchain (IEEE Sensors Journal, 2023).
Saheed, Y. K., Misra, S. & Chockalingam, S. Autoencoder via DCNN and LSTM models for intrusion detection in industrial control systems of critical infrastructures. In 2023 IEEE/ACM 4th International Workshop on Engineering and Cybersecurity of Critical Systems (EnCyCriS) (pp. 9–16). IEEE. (2023), May.
Siganos, M. et al. Explainable AI-based Intrusion Detection in the Internet of Things. In Proceedings of the 18th International Conference on Availability, Reliability and Security (pp. 1–10). (2023), August.
Saheed, Y. K. & Chukwuere, J. E. CPS-IIoT-P2Attention: Explainable Privacy-Preserving with Scaled Dot-Product Attention in Cyber Physical System-Industrial IoT Network (IEEE Access, 2025).
Khan, A. A. et al. Artificial intelligence and blockchain technology for secure smart grid and power distribution automation: A State-of-the-Art review. Sustain. Energy Technol. Assess. 57, 103282 (2023).
Xu, F., Yang, H. & Alouini, M. Energy Consumption Minimization for Data Collection From Wirelessly-Powered IoT Sensors: Session-Specific Optimal Design With DRL. IEEE Sens. J., 22(20), 19886–19896. doi: https://doi.org/10.1109/JSEN.2022.3205017. (2022).
Jie, W. et al. A novel extended multimodal AI framework towards vulnerability detection in smart contracts. Inf. Sci. 636, 118907 (2023).
Khan, A. A. et al. A drone-based data management and optimization using metaheuristic algorithms and blockchain smart contracts in a secure fog environment. Comput. Electr. Eng. 102, 108234 (2022).
Meziane, H. & Ouerdi, N. A survey on performance evaluation of artificial intelligence algorithms for improving IoT security systems. Sci. Rep. 13 (1), 21255 (2023).
Rangaraju, S. Secure by intelligence: enhancing products with AI-Driven security measures. EPH-International J. Sci. Eng. 9 (3), 36–41 (2023).
Hernandez-Jaimes, M. L., Martinez-Cruz, A., Ramírez-Gutiérrez, K. A. & Feregrino-Uribe, C. Artificial intelligence for IoMT security: A review of intrusion detection systems, attacks, datasets and Cloud–Fog–Edge architectures. Int. Thing. 23, 100887 (2023).
Sedjelmaci, H. & Ansari, N. Zero Trust Architecture Empowered Attack Detection Framework To Secure 6G Edge Computing (IEEE Network, 2023).
Abuhasel, K. A. A Zero-Trust Network-Based Access Control Scheme for Sustainable and Resilient Industry 5.0 (IEEE Access, 2023).
Kang, H., Liu, G., Wang, Q., Meng, L. & Liu, J. Theory and application of zero trust security: A brief survey. Entropy 25 (12), 1595 (2023).
Khan, M. J. Zero trust architecture: redefining network security paradigms in the digital age. World J. Adv. Res. Reviews. 19 (3), 105–116 (2023).
Fernandez, E. B. & Brazhuk, A. A Critical Analysis of Zero Trust Architecture (ZTA)103832 (Computer Standards & Interfaces, 2024).
Sivamohan, S., Sridhar, S. S. & Krishnaveni, S. TEA-EKHO-IDS: an intrusion detection system for industrial CPS with trustworthy explainable AI and enhanced Krill herd optimization. Peer-to-Peer Netw. Appl. 16 (4), 1993–2021 (2023).
Beg, O. A., Khan, A. A., Rehman, W. U. & Hassan, A. A review of AI-Based Cyber-Attack detection and mitigation in microgrids. Energies 16 (22), 7644 (2023).
Muna, R. K. et al. Demystifying machine learning models of massive IoT attack detection with explainable AI for sustainable and secure future smart cities. Internet Things. 24, 100919 (2023).
Chakraborty, C., Nagarajan, S. M., Devarajan, G. G., Ramana, T. V. & Mohanty, R. Intelligent AI-based Healthcare Cyber Security System Using Multi-Source Transfer Learning Method (ACM Transactions on Sensor Networks, 2023).
Jia, Y. et al. Artificial intelligence enabled cyber security defense for smart cities: A novel attack detection framework based on the MDATA model. Knowl. Based Syst. 276, 110781 (2023).
Chohan, M. N. et al. Detection of cyber attacks using machine learning based intrusion detection system for IoT based smart cities. EAI Endorsed Trans. Smart Cities. 7 (2), e4–e4 (2023).
Yang, J. et al. Improving commute experience for private Car users via Blockchain-Enabled multitask learning. IEEE Internet Things J. 10 (24), 21656–21669. https://doi.org/10.1109/JIOT.2023.3317639 (2023).
Qiao, Y. et al. A multihead attention Self-Supervised representation model for industrial sensors anomaly detection. IEEE Trans. Industr. Inf. 20 (2), 2190–2199. https://doi.org/10.1109/TII.2023.3280337 (2024).
Shi, G. et al. One for all: A unified generative framework for image emotion classification. IEEE Trans. Circuits Syst. Video Technol. 34 (8), 7057–7068. https://doi.org/10.1109/TCSVT.2023.3341840 (2024).
Shi, H., Dao, S. D. & Cai, J. LLMFormer: large Language model for Open-Vocabulary semantic segmentation. Int. J. Comput. Vision. 133 (2), 742–759. https://doi.org/10.1007/s11263-024-02171-y (2025).
Jiang, H., Ji, P., Zhang, T., Cao, H. & Liu, D. Two-Factor authentication for keyless entry system via Finger-Induced vibrations. IEEE Trans. Mob. Comput. 23 (10), 9708–9720. https://doi.org/10.1109/TMC.2024.3368331 (2024).
Xu, Y., Ding, L., He, P., Lu, Z. & Zhang, J. Meta: A Memory-Efficient Tri-Stage polynomial multiplication accelerator using 2D Coupled-BFUs. IEEE Trans. Circuits Syst. I Regul. Pap. 72 (2), 647–660. https://doi.org/10.1109/TCSI.2024.3461736 (2025).
Gowdhaman, V. & Dhanapal, R. Hybrid deep learning-based intrusion detection system for wireless sensor network. Int. J. Veh. Inf. Commun. Syst. 9 (3), 239–255. https://doi.org/10.1504/IJVICS.2024.139627 (2024).
Fu, C., Liu, G., Yuan, K. & Wu, J. Nowhere to H2IDE: fraud detection from Multi-Relation graphs via disentangled homophily and heterophily identification. IEEE Trans. Knowl. Data Eng. 37 (3), 1380–1393. https://doi.org/10.1109/TKDE.2024.3523107 (2025).
Hu, J. et al. WiShield: privacy against Wi-Fi human tracking. IEEE J. Sel. Areas Commun. 42 (10), 2970–2984. https://doi.org/10.1109/JSAC.2024.3414597 (2024).
Chen, S. et al. Echoes of fingertip: unveiling POS terminal passwords through Wi-Fi beamforming feedback. IEEE Trans. Mob. Comput. 24 (2), 662–676. https://doi.org/10.1109/TMC.2024.3465564 (2025).
Jiang, X. et al. Advancing industrial data augmentation in AIGC era: from foundations to frontier applications. IEEE Trans. Instrum. Meas. https://doi.org/10.1109/TIM.2025.3572162 (2025).
Wu, X. et al. Dynamic security computing framework with zero trust based on privacy domain prevention and control theory. IEEE J. Sel. Areas Commun. 43 (6), 2266–2278. https://doi.org/10.1109/JSAC.2025.3560036 (2025).
Khan, A. A., Laghari, A. A., Shaikh, Z. A., Dacko-Pikiewicz, Z. & Kot, S. Internet of Things (IoT) Security with Blockchain Technology: A state-of-the-art Review (IEEE Access, 2022).
Qiu, R., Yin, Y., Su, Q. & Guan, T. Func-Bagging: an ensemble learning strategy for improving the performance of heterogeneous anomaly detection models. Appl. Sci. 15 (2), 905. https://doi.org/10.3390/app15020905 (2025).
Zhang, J. et al. GrabPhisher: phishing scams detection in Ethereum via temporally evolving GNNs. IEEE Trans. Serv. Comput. 17 (6), 3727–3741. https://doi.org/10.1109/TSC.2024.3411449 (2024).
Zheng, W., Liu, C., Deng, P., Chen, X. & Wu, X. Enhancing concurrency vulnerability detection through AST-based static fuzz mutation. J. Syst. Softw. 222, 112352. https://doi.org/10.1016/j.jss.2025.112352 (2025).
Zenggang, X. et al. NDLSC: A new deep Learning-based approach to smart contract vulnerability detection. J. Signal. Process. Syst. 97 (1), 49–68. https://doi.org/10.1007/s11265-025-01954-x (2025).
Luo, J., Zhao, C., Chen, Q. & Li, G. Using deep belief network to construct the agricultural information system based on internet of things. J. Supercomputing. 78 (1), 379–405. https://doi.org/10.1007/s11227-021-03898-y (2022).
Khan, A. A., Laghari, A. A., Li, P., Dootio, M. A. & Karim, S. The collaborative role of blockchain, artificial intelligence, and industrial internet of things in digitalization of small and medium-size enterprises. Sci. Rep. 13 (1), 1656 (2023).
Acknowledgements
The authors extend their appreciation to Prof. Dr Natalia Kryvinska (Comenius University Bratislava, Odbojárov 10, 82005 Bratislava 25, Slovakia), for supporting this work.
Funding
This study was funded by Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2025R759), Princess Nourah bint Abdulrahman University.
Author information
Authors and Affiliations
Contributions
Author Contributions: Abdullah Ayub Khan, perform the Original Writing Part, Software, and Methodology; Asif Ali Laghari, Abdullah Ayub Khan, Amel Ksibi, Fahima Hajjej, Natalia Kryvinska, Ahmad Almadhor, Mohamad Afendee Mohamed, and Shtwai Alsubai performs Rewriting, investigation, design Methodology, and Conceptualization; Asif Ali Laghari, Abdullah Ayub Khan, Amel Ksibi, Fahima Hajjej, Natalia Kryvinska, Ahmad Almadhor, Mohamad Afendee Mohamed, and Shtwai Alsubai performs related work part and manage results and discussions; Asif Ali Laghari, Abdullah Ayub Khan, Amel Ksibi, Fahima Hajjej, Natalia Kryvinska, Ahmad Almadhor, Mohamad Afendee Mohamed, and Shtwai Alsubai performs related work part and manage results and discussion; Abdullah Ayub Khan performs Rewriting, design Methodology, and Visualization. The author accepts the online/published version of this manuscript.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Laghari, A.A., Khan, A.A., Ksibi, A. et al. A novel and secure artificial intelligence enabled zero trust intrusion detection in industrial internet of things architecture. Sci Rep 15, 26843 (2025). https://doi.org/10.1038/s41598-025-11738-9
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-11738-9
Keywords
This article is cited by
-
Securing industry 4.0: a systematic review of AI-driven intrusion detection approaches and emerging trends
Journal of Reliable Intelligent Environments (2026)
-
Innovative Hybrid Machine Learning Methods for Breast Cancer Predictive Optimization
International Journal of Computational Intelligence Systems (2026)