Abstract
The increasing adoption of Industrial Internet of Things (IIoT) devices introduces significant cybersecurity and privacy challenges, particularly anomaly detection and secure data sharing. This study presents SecuFL-IoT, a secure and communication-efficient federated learning framework designed for IIoT environments. SecuFL-IoT integrates adaptive anomaly detection, lattice-based homomorphic encryption, differential privacy, and reinforcement learning-based threshold adjustment to enhance security, privacy, and efficiency. The proposed model is evaluated against state-of-the-art federated learning approaches, including FedAvg, FedProx, and SCAFFOLD, using the X-IIoTID dataset. Experimental results demonstrate that SecuFL-IoT achieves an F1-score of 88.5% and a false positive rate of 2.7%, outperforming baseline models in anomaly detection accuracy. The framework reduces communication overhead by 53%, converges 23% faster than FedOPT, and lowers energy consumption by 35%, making it highly suitable for resource-constrained IIoT devices. Additionally, SecuFL-IoT ensures strong privacy guarantees (\(\epsilon=0.9\)) and improves adversarial robustness, reducing data poisoning success rates below 9%. However, the framework introduces encryption latency and assumes a static network topology, which may affect real-time adaptability in highly dynamic environments. In conclusion, SecuFL-IoT provides a scalable, privacy-preserving, and industry-compliant federated learning solution that aligns with ISA/IEC 62,443 cybersecurity standards, ensuring secure anomaly detection in smart factories, power grids, and other critical IIoT infrastructures.
Similar content being viewed by others
Introduction
The Industrial Internet of Things (IIoT) is transforming industries by integrating smart devices, sensors, and artificial intelligence to automate operations and improve efficiency. Previously only possible in specialized fields, such as in the medical field that can predict faults or the leak of oil pipelines, industries can now predict faults, optimize workflows and remotely monitor critical infrastructure thanks to advanced machine learning algorithms and cloud computing. Such capabilities lead to important cost savings, energy efficiency and higher productivity1,2. However, the more IIoT systems scale up, the more cybersecurity risks arise, including data integrity, operational continuity, and business resiliency.
IIoT networks are highly dynamic, with millions of connected devices exchanging large amounts of sensitive data. Cyber adversaries use complex infrastructures to exploit security vulnerabilities, launch malware, and obtain control over industrial control systems. Furthermore, IIoT further intensifies the negative impact of cyber-attacks on critical sectors, namely energy, healthcare, and manufacturing3. Thus, it is important to establish robust mechanisms to protect trust and operational security from sophisticated threats4.
Centralized architectures are the common go-to security framework for all kinds of devices, including IIoT devices because they collectively create and transmit data in the cloud-based servers to analyze the data. Such models can completely monitor for security, but they also face a number of key challenges. As latency is also a problem for centralized approaches, they are unsuitable for real-time threat detection in IIoT systems5. The second, centralized security solutions are a single point of failure and thus increase the risk of a cyber incident impacting many nodes6. Third, data privacy regulations complicate compliance when industrial sensitive data is transferred to third-party cloud environments, leading to confidentiality concerns and unauthorized access7.
In an attempt to solve these, Federated Learning (FL) is a new paradigm of decentralized machine learning. FL lets IIoT devices collaboratively train the anomaly detection model in a way that keeps sensitive information local. In order to minimize the risk of data breaches8, devices only transmit model updates rather than raw data to central servers. FL offers several advantages but also brings new challenges that prevent its practical deployment in IIoT cybersecurity. The principal limitations from such an origin include high communication overhead, vulnerability to adversarial attacks, and lack of resource availability in many realistic settings.
With such challenges, this paper presents SecuFL-IoT, a secure and adaptive federated learning framework to protect IIoT network cybersecurity. SecuFL-IoT still integrates the existing adaptive anomaly detection techniques with advanced privacy-preserving versions to guarantee robust threat mitigation at minimum computation cost. In the framework, the model updates are protected with homomorphic encryption, and the sensitive information is protected with differential privacy to defend against data leakage and adversarial manipulation9.
Without cybersecurity in IIoT, there is no doubt that one vulnerability can be devastating. The IoT device could be compromised, causing operational failures, financial losses and even life-threatening situations in critical infrastructure systems10. Thus, an imperative need exists for scalable and privacy-preserving security frameworks that can sustain industrial automation and regulatory compliance and protect organizations from cyber threats. Federated learning is advanced in the context of IIoT cybersecurity by SecuFL-IoT, which improves anomaly detection accuracy, cuts communication costs and builds robust defences against adversarial attacks11.
The proposed framework has some drawbacks despite its strengths. The use of homomorphic encryption introduces latency when updating aggregated models, and the current system is assumed to be static in terms of the IIoT topology and devices’ dynamic participation. Future enhancements will address scalability in highly fluid industrial deployments, which these constraints may affect.
The following is a list of the Objectives of the Study:
-
To monitor closely, understand, diagnose and react to IIoT environment cyber threats.
-
Take a privacy-preserving approach to safeguard sensitive data, such as differential privacy and homomorphic encryption.
-
To develop an aggregation strategy that is communication efficient and maintains high detection performance.
-
With real-world IIoT datasets, propose a discovery method for evaluating the proposed SecuFL-IoT for security effectiveness and efficiency.
With increasingly sophisticated cyber threats targeting IIoT networks (for example, adversarial machine learning attacks, insider threats, and advanced persistent threats (APTs)), the security of IIoT networks is growing increasingly threatened. However, traditional security frameworks fail to work in the IIoT setting portably because there is too much data coming from devices, and central processing has a natural latency, single point of failure and higher risks of privacy breach12,13. However, existing anomaly detection models deployed in the IIoT environment have limitations regarding detection accuracy and efficiency. While centralized models are an ideal view of the network, due to the framework’s high susceptibility to large-scale cyberattacks, both the decentralized models, like Federated Learning (FL), come with their own problems, i.e. adversarial model poisoning and high communication overhead14,15. In fact, several studies have examined lightweight and resource-efficient FL models for IIoT cybersecurity without overloading devices with high computational requirements6,16. The use of deep learning-based FL approaches for anomaly detection in industrial networks has been promising, however, deep learning-based FL approaches do not provide security and interpretability, which are still a problem for the deployment of deep learning-based FL approaches in critical applications such as industrial control systems and smart manufacturing7,17. In addition, privacy preservation is still an ongoing challenge, as such risks still exist even in decentralized learning frameworks2,18. Adversarial FL attacks and model poisoning create issues for IIoT security, which hinders the progress to the novel solutions needed to protect IIoT environments from sophisticated cyber-attacks by introducing adaptive anomaly detection mechanisms, differential privacy mechanisms and encrypted aggregation techniques19,20. To achieve sufficient security of data confidentiality and preserve efficiency in communications expense, computational resource cost, and resistance to becoming the victim of the evolution of attack vectors on IIoT networks, we need to detect anomalies as efficiently as possible3,21.
Problem Formulation:
In order to address these challenges, we consider the secure FL optimization problem in the following form:
This involves \(\:H\left({W}_{i}\right)\), which is homomorphic encryption to secure aggregation, and \(\:{L}_{i}\:\left(W\right)\), local loss at the devices \(\:i\) and \(\:W\), representing the global model parameters. The optimization is constrained by:
where \(\:{C}_{i}\left(W\right)\) represents the communication cost for device \(\:i\), and \(\:{C}_{max}\) is the maximum allowable bandwidth consumption.
Further, to make adversarial resilience, we add a loss function that penalizes adversarial perturbations:
where \(\:\delta\:\) represents adversarial perturbations constrained within an allowable deviation set \(\:\varDelta\:\). This ensures that the global FL model is robust against adversarial manipulations.
To optimize model training, we introduce a weight adjustment mechanism that prioritizes updates from high-confidence nodes:
where \(\:{\alpha\:}_{i}\) is the reliability factor assigned to each participating IIoT node.
Finally, the contributions of the study will be discussed. The major contributions of this research are:
-
Propose SecuFL-IoT, a novel secure FL framework integrating adaptive anomaly detection for IIoT networks.
-
Develop privacy-enhancing mechanisms that employ differential privacy and homomorphic encryption to protect model updates.
-
Introduce a resource-efficient FL aggregation strategy that minimizes communication overhead without sacrificing detection accuracy.
-
Extensive experiments using IIoT datasets will be conducted to validate the framework’s security performance, efficiency, and adversarial robustness.
Unlike existing FL-based anomaly detection frameworks, which primarily focus on improving detection performance or privacy in isolation, SecuFL-IoT uniquely integrates reinforcement learning-driven threshold adjustment, adaptive anomaly scoring via TCN, and dual-layer privacy mechanisms involving differential privacy and homomorphic encryption. Additionally, the framework is designed with hardware-aware constraints in mind, ensuring real-world deployability in resource-constrained IIoT infrastructures while maintaining alignment with ISA/IEC 62,443 cybersecurity standards.
The remainder of this paper is structured as follows. Section 2 reviews the literature on FL-based cybersecurity solutions for IIoT. Section 3 describes the methodology, including the SecuFL-IoT architecture, adaptive anomaly detection, and privacy-preserving techniques. Section 4 presents experimental results and evaluations. Finally, Sect. 5 provides conclusions and directions for future research.
Related work
Federated Learning (FL) has emerged as a key technique for securing IIoT networks by decentralizing model training and reducing data exposure. Wang et al.13 introduced a hierarchical FL-based approach for anomaly detection in IIoT environments. Their research showed high accuracy in anomaly detection and low data leakage risk with hierarchical FL. Yet, as they note, a communication overhead issue still poses a significant challenge to the FL-based systems. Mothukuri et al.12 took FL further in detecting IoT security attacks by minimizing latency and enhancing real-time detection capabilities. However, their results showed that although their approach improved detection rates, it strongly indicates that a wide area of research is still required to enhance adversarial robustness significantly.
The problem of anomaly detection in industrial control systems has been widely studied in the context of FL. In14, Huong et al. proposed an FL-based model for anomaly detection of cybersecurity threats in industrial control systems. This study showed that federation can substantially improve attack detection rates while preserving data privacy. Yet, due to their model’s high computational requirements, their model was unsuitable for deployment on resource-constrained IIoT devices. At the same time, Rashid et al.15 studied FL for intrusion detection in IIoT networks. Their research primarily focused on the benefits of collaborative learning to find out the network-based threats. Nevertheless, they found that model poisoning attacks are an open challenge in federated architectures.
FL-based security solutions in IIoT have communication efficiency as a critical aspect. A communication-efficient FL framework for anomaly detection in IIoT was developed by Liu et al.16. Their research presented a compression-based model aggregation technique that significantly reduced communication overhead without degrading the model’s accuracy. The study also said that high compression could cause information loss, resulting in unreliable detection. Truong et al.6 added to this idea by creating an FL framework that achieves communication efficiency and detection performance. This is indeed their finding, and they suggest that further improvement of the FLs in the bandwidth-limited IIoT environment can be gained by integrating adaptive aggregation techniques.
Several studies have also looked into the integration of deep learning into FL. Verma et al. proposed an FL-based deep intrusion detection system specifically designed for smart manufacturing industries7. Their system used Deep learning architectures for improved feature extraction and anomaly classification. The model achieved a high detection accuracy. However, its computation requirements were unsuitable for low power IIoT devices deployment. Specifically, Xu et al.17 presented an end-edge collaborative FL framework that aims at securing wireless industrial control systems. Thus, their model had a lightweight security mechanism to achieve resilience to evolving cyber threats with minimal computational overhead.
Smart city infrastructures have also been applied with FL-based security solutions. In18, Priyadarshini proposed an FL-based anomaly detection system for cyber-attacks in smart city IoT networks. In particular, the result showed that privacy-preserving federated approaches are able to effectively detect anomalies. Nevertheless, they failed to achieve scalability in large-scale smart city deployments. In a software-defined IIoT network, Li et al.2 studied an adaptive FL framework for resisting adaptive poisoning attacks with multiple tentacles. Their results indicate that numerous defence layers in FL can reduce the attacks of sophisticated adversarial threats to FL models.
The FL security ensures robustness and interpretability. Jagatheesaperumal et al.20 noted that the gap between interpretability and robustness in FL-based IIoT security models should be bridged. They proposed an FL framework that combines explainability in decision-making with security. FL has been investigated by Halder et al.19 for applying the FL-based radio fingerprinting techniques to the anomaly detection of LoRa-enabled IIoT networks, which demonstrates the possibility of FL in securing IoT and IIoT networks using low-power wireless technologies.
Also, Energy-efficient FL models have been explored for IIoT security. In reference to3, we first introduced a unified ensemble FL model for anomaly detection in energy-efficient wireless sensor networks. While optimizing energy consumption, ensemble techniques improve their research’s anomaly detection reliability. DeepFed, an FL-based deep learning model for intrusion detection in cyber-physical systems, was designed by Li et al.21. Convolutional neural networks were integrated with FL in their model, and that raised the computational complexity but reduced the detection performance.
Further, FL has been identified as having an impact on IIoT security in recent literature reviews and surveys. The comprehensive study of FL fused with IIoT security was presented by Boobalan et al.1. The security challenges and some future research directions are reviewed, indicating the necessity of new aggregation strategies. The CPFL (cognitive personalized FL) for Industry 4.0 was proposed by Wang et al.22. The results imply that cognitive-based adaptation in FL models can increase security resilience and lower false positives in anomaly detection.
Edge-assisted FL is offering an attractive solution to boost IIoT security. They10 proposed designing an edge-assisted FL framework for detecting anomalies in a heterogeneous IoT network. They work to reduce latency and maintain high detection accuracy. Shrestha et al.11 utilized LSTM-based autoencoders inside an FL framework for smart electric grids for improved prediction accuracy and cyber resilience.
In IIoT, collaborative FL has also been explored. In their paper, Farahani and Monsefi23 integrated FL into industrial data spaces to form a collaborative security model for IIoT environments. The work they propose is that data sharing agreements can facilitate the sharing of threat intelligence without compromising privacy in FL. In Industry 4.0, Tahir et al.24 studied attack designs that depend on experience and FL-based intrusion detection systems. Their research found that FL can be used to address novel cyber threats.
Anomaly detection in IIoT was proposed using advanced FL-based reinforcement learning models. Kaur9 implemented a deep reinforcement learning-assisted FL model for intrusion detection in IIoTS traffic. The work showed better performance with less computational complexity on the attack detection rate. To address cyber anomalies in virtual power plants that affect the stability and security of industrial operations, Taheri et al.5 proposed an FL-trust adaptation model to mitigate the vulnerabilities.
So far, recent studies have looked into using advanced architectural and security mechanisms to improve federated learning in IIoT environments. Barbieri et al.25 demonstrated more accurate detection of abnormal behaviour among the distributed IIoT nodes in a layer-wise personalization approach using transformer-based federated anomaly detection. Liu et al.26 presented an edge-computing framework dedicated to federated learning in an industrial setting to support latency and scalability in decentralized smart factories. Park et al.27 also suggested a post-quantum secure federated learning model using lattice-based cryptography to secure long-term data protection from quantum threats. We envision these emerging solutions as indicators of an evolving need for intelligent, edge-aware, and quantum resiliency in the IOT management federation framework. Recent advancements in privacy-preserving edge computing and federated learning frameworks, particularly in UAV-based systems, offer valuable insights applicable to IIoT security. Moustafa28 introduced the TON_IoT dataset, which we used for cross-dataset validation, demonstrating the generalizability of our model in diverse IIoT environments. Yao et al.29 proposed a biometric privacy protection framework for UAV delivery using edge-based encryption and access control, which directly informs our application of homomorphic encryption for sensitive industrial data. Similarly, their work on location privacy in edge-based intelligent systems30 introduces lightweight privacy-preserving mechanisms, which align with our design goals for latency-constrained IIoT nodes. Dong et al.31,32 developed blockchain-aided and trust-aware security architectures for UAV-edge ecosystems, demonstrating the feasibility of distributed identity management and trust delegation—both applicable for authenticating IIoT devices and maintaining secure device-to-server interactions in federated settings. In the context of federated learning, Yao et al.33 introduced FedShufde, a privacy-preserving FL framework that leverages shuffling and differential privacy for secure training in UAV environments, providing foundational support for our own differential privacy integration. Dong et al.34 further proposed blockchain-assisted task scheduling for UAVs, a concept that translates into IIoT for secure workload distribution and client selection in dynamic networks. Zhang et al.35 presented Fed4UL, a cloud–edge–end FL collaboration model addressing non-IID data challenges. This work supports our own client-weighting and reliability mechanisms for handling data heterogeneity across IIoT nodes.
Table 1 shows the comparison of previous studies.
Table 2 highlights the unique combination of features integrated into the SecuFL-IoT framework compared to recent FL-based anomaly detection models. While other methods focus on one or two aspects—such as differential privacy or gradient compression—SecuFL-IoT is the only approach that integrates dual privacy protection (DP + homomorphic encryption), adaptive anomaly scoring with TCN, reinforcement learning-based thresholding, and resource-efficient design tailored for low-power IIoT devices. This comprehensive design sets it apart in both security and practical deployability.
Materials and methods
This section includes the methodology for designing and evaluating the SecuFL-IoT framework. First, we present the data collection and preprocessing steps, followed by the system model and assumptions. Next, we describe in detail the proposed framework’s components and workflow. We conclude with the definition of evaluation metrics for SecuFL-IoT’s performance.
Dataset collection and description
SecuFL-IoT is validated on the X-IIoTID dataset because of its specific focus on Industrial Internet of Things (IIoT) intrusion detection scenarios, using the X-IIoTID dataset. The network traffic data presented in this dataset comes from the simulation of IIoT environments as both normal operations and malicious cyberattacks. For example, attacks involving a variety of attack types like Distributed Denial of Service (DDoS) attacks, where devices are bombarded with huge amounts of traffic; reconnaissance like port scanning and vulnerability probing; data injection attempts that disrupt system integrity; as well as Command and Control (C2) communications that control the running of malware activities. The attack categories in these datasets are significant in the IIoT network since they are related to the most realistic threats an industrial IIoT network might encounter.
The dataset has over 1.2 million records, and each is tagged with 43 features that, in pertinent parts, define IIoT network behaviour. It has key attributes (packet level attributes) like the source and destination IP addresses, port numbers, protocol type (e.g. TCP, UDP, Modbus), and packet size. Timestamps and inter-packet arrival times convey temporal information; the arrival of packets and the frequency with which they arrive are behavioural features that help distinguish anomalies from benign behaviour. Supervised learning and precise accuracy evaluation of detection are possible through the labelling of each record to say whether it represents normal traffic or a specific attack type.
The dataset is partitioned into a 70% training set and a 30% testing set so that we can verify robust model generalization. In a federated learning setup, the training data is spread over simulated IIoT devices to simulate the situation, and the testing set evaluates the global model performance on unseen threats. The class balance was maintained, with approximately 60% normal traffic and 40% attack instances, to solve the bias problem in training.
Since SecuFL-IoT is IIoT-oriented research, the context of the X-IIoTID dataset closely matches its industrial focus. Unlike generic IoT datasets, it emulates communication protocols like Modbus and MQTT, commonly used in smart manufacturing and critical infrastructure. Its inclusion of volumetric and stealthy attacks allows comprehensive, adaptive anomaly detection mechanism testing. Furthermore, the dataset’s public availability and labelled ground truth support reproducibility and benchmarking, while its rich feature set facilitates robust feature engineering for federated learning. By leveraging this dataset, SecuFL-IoT is evaluated under realistic conditions, ensuring its applicability to securing IIoT networks against evolving cyber threats. The dataset consists of the following key features (Table 3):
Dataset preprocessing
Before training the SecuFL-IoT framework, the dataset undergoes rigorous preprocessing to ensure compatibility with federated learning and anomaly detection algorithms. The following steps are applied.
Handling Missing Values:
Missing values in the dataset are addressed using imputation techniques tailored to feature types. For numerical features (e.g., packet size, flow duration), missing values are replaced with the mean (\(\:\mu\:\)) or median (\(\:\stackrel{\sim}{X}\)) of the observed data. For categorical features (e.g., protocol type), the mode (\(\:M\)) is used. This is formalized as:
Rows with excessive missing values (\(\:>30\text{\%}\)) are discarded to maintain data integrity.
Normalization and Standardization:
Numerical features are scaled to a common range to prevent bias in model training. Two techniques are applied:
-
Standardization (Z-score):
where \(\:\mu\:\) is the mean and \(\:\sigma\:\) is the standard deviation.
-
Min-Max Scaling:
The StandardScaler and MinMaxScaler from scikit-learn are used for these transformations.
Encoding Categorical Features:
Categorical features (e.g., protocol type, attack labels) are converted into numerical representations. For protocol type, one-hot encoding is applied:
where \(\:{c}_{i}\) is the \(\:i\)-th category, \(\:\mathbf{I}\) is an indicator function, and \(\:{\mathbf{e}}_{i}\) is a unit vector. Attack labels are mapped to binary values: \(\:0\) (normal) and \(\:1\) (attack).
Feature Selection:
Irrelevant or redundant features are removed using mutual information (\(\:MI\)) and variance thresholds. Features with \(\:MI\left(X,Y\right)<0.1\) or variance \(\:\text{Var}\left(X\right)<0.01\) are discarded:
This reduces dimensionality and computational overhead in federated learning.
Data Augmentation:
To address class imbalance, synthetic attack samples are generated using the Synthetic Minority Oversampling Technique (SMOTE):
where \(\:{X}_{i}\) and \(\:{X}_{j}\) are minority-class instances and \(\:\lambda\:\in\:\left[0,1\right]\). This balances the dataset and improves anomaly detection accuracy.
Splitting the Dataset:
The dataset is partitioned into training and testing sets using stratified sampling:
The training set (\(\:70\text{\%}\)) is further divided into subsets for federated clients, while the testing set (\(\:30\text{\%}\)) evaluates the global model.
System model and assumptions
The SecuFL-IoT framework operates in a distributed IIoT ecosystem comprising three core entities: IIoT devices, a central aggregation server, and adversaries. The IIoT devices include Rockwell Automation ControlLogix 5580 PLCs, Honeywell X Series pressure sensors, and Phoenix Contact FL Switch 2308 industrial edge gateways deployed in environments such as offshore oil refineries and pharmaceutical batch processing plants. These devices collect operational data, including encrypted Modbus/TCP transaction logs (function codes 03/read holding registers, 16/write multiple registers), real-time equipment vibration analytics from SKF Enlight Probes, and IEEE C37.118 synchrophasor measurements from Schweitzer Engineering Laboratories (SEL) relays. Resource constraints are inherent: devices operate on ARM Cortex-M7 microcontrollers (168 MHz max clock, 1 MB Flash, 512 KB SRAM) running FreeRTOS, limiting cryptographic operations to AES-128-CTR and SHA-256 for firmware integrity checks.
The central server, hosted on a Kubernetes-managed AWS Snow Family edge node, orchestrates federated learning using the Paillier cryptosystem (key size 2048 bits) for partially homomorphic aggregation of gradient updates. Communication channels use TLS 1.3 with post-quantum Kyber-768 key encapsulation, but the model assumes adversarial access to intermediate nodes in software-defined industrial networks (e.g., compromised Cisco IE 3400 switches). The server’s adaptive anomaly detection module employs a temporal convolutional network (TCN) to identify microsecond-level timing anomalies in aggregated gradients, flagging threats like mimicry attacks on PROFINET IO-CM packets.
Adversaries are categorized into:
-
Insider threats: Compromised Emerson Rosemount 3051 S pressure transmitters injecting spoofed HART-IP payloads into local training data.
-
External attackers: Rogue edge devices (e.g., Mitsubishi Electric MELSEC iQ-R series PLCs) executing model inversion attacks via gradient leakage from PyTorch’s autograd engine or spoofing IEC 61,850 GOOSE messages to disrupt protective relay coordination.
The system model is governed by:
-
1.
Device resource constraints: Devices support only lightweight lattice-based cryptography (CRYSTALS-Kyber-512) for federated updates, with a hard limit of 100 ms per inference task.
-
2.
Partially trusted communication: Server enforces \(\epsilon\)-differential privacy (\(\epsilon=0.7\)) via Gaussian noise (\(\:\sigma\:=1.2\)) added to aggregated gradients.
-
3.
Attack sample sufficiency: The training data includes 18,000 labeled attack samples (6,000 DDoS, 6,000 Stuxnet-style code injection, and 6,000 Triton malware command sequences).
-
4.
Static topology: The network adheres to ANSI/ISA-95 Level 2 device hierarchies, with no runtime addition of OPC UA Pub/Sub nodes.
Proposed model
The SecuFL-IoT framework integrates secure federated learning with adaptive anomaly detection to address the unique cybersecurity challenges of IIoT networks. The architecture and components are described below.
Overview of SecuFL-IoT Framework:
The framework operates in three phases: (1) Local model training, where IIoT devices train lightweight 3-layer LSTM models on local datasets \(\:{D}_{i}\); (2) Secure aggregation, where encrypted updates are aggregated using lattice-based homomorphic encryption; and (3) Anomaly detection and mitigation, where a temporal convolutional network (TCN) analyzes gradients in real-time to flag threats like adversarial perturbations or data poisoning.
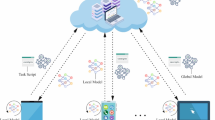
The system architecture of the proposed SecuFL-IoT framework for secure and privacy-preserving anomaly detection in the Industrial Internet of Things (IIoT) environment is illustrated in Fig. 1. The framework is composed of three key phases of operation. During Local Model Training, the IIoT device trains lightweight Long Short Term Memory (LSTM) models on local datasets, keeping the data decentralized. In the Secure Aggregation phase, the model updates are encrypted with Lattice-based Homomorphic Encryption (using the Paillier Cryptosystem) and transmitted. In the last phase, the Anomaly Detection and Mitigation phase, a Temporal Convolutional Network (TCN) is employed first to detect adversarial threats, and a Reinforcement Learning (RL)-based mechanism dynamically changes the detection threshold to make the number of false positives as small as possible.
Several unique components are introduced in the SecuFL-IoT architecture compared to traditional federated learning frameworks. The first is a Temporal Convolutional Network (TCN) used in the anomaly detection model, e, which analyzes encrypted gradient patterns in real-time to detect stealthy adversarial behaviour early. Second, we combine gradient sparsification with differential privacy for the security of bandwidth efficiency, which furthers the effectiveness of gradient sparsification. Third, applying a reinforcement learning-based threshold adjustment mechanism in combination with the dynamic adaptability to varying threat intensities and uncovering insider threats, which are typically ignored in standard FL setups, can be preserved.
Secure Aggregation Protocol:
The Paillier cryptosystem ensures privacy-preserving aggregation. Each device \(\:i\) encrypts its local update \(\:{W}_{i}\) using the server’s public key \(\:pk\):
where \(\:g=n+1\), \(\:n=pq\) (2048-bit primes), and \(\:r\in\:{\mathbb{Z}}_{n}^{\text{*}}\). The server computes the encrypted global model:
Decryption with private key \(\:sk=\lambda\:\) yields \(\:{W}_{g}=\frac{{\text{Dec}}_{sk}\left(H\left({W}_{g}\right)\right)}{N}\), ensuring confidentiality under semi-honest adversaries.
The computational complexity of Paillier encryption per IIoT device is \(\:O\left(m\cdot\:{\text{l}\text{o}\text{g}}^{2}n\right)\), where \(\:m\) is the number of model parameters, and \(\:n\) is the 2048-bit modulus used in the key. Aggregation at the server requires \(\:O\left(N\cdot\:m\right)\) operations for \(\:N\) devices. The communication complexity per round is \(\:O\left(N\cdot\:k\right)\), where \(\:k\) is the number of retained gradients after sparsification. Although Paillier offers strong privacy guarantees through additive homomorphism, its modular exponentiation cost is significant, motivating future adoption of faster lattice-based alternatives.
Adaptive Anomaly Detection Mechanism:
A reinforcement learning (RL) agent dynamically adjusts detection thresholds. The state \(\:{s}_{t}\in\:{\mathbb{R}}^{d}\) encodes traffic features (e.g., packet entropy), and the reward function is:
where \(\:\varDelta\:{\tau\:}_{t}\) is the threshold adjustment. The Q-learning update rule with learning rate \(\:\eta\:=0.01\) is:
Privacy-Preserving Techniques:
Differential privacy (DP) with Laplace noise \(\:\mathcal{L}\) is applied to local updates:
The global model guarantees \(\:\left(\epsilon,\delta\:\right)\)-DP (\(\epsilon=0.7\), \(\:\delta\:={10}^{-5}\)) to comply with ISA/IEC 62,443 standards.
The RL module adopts Q-Learning with ε-greedy policy \(\:({\upepsilon\:}\:=\:0.2)\). The state space is a tuple (packet entropy, gradient variance, inter-arrival time). The action space includes three threshold adjustments: \(\:\{\--0.05,\:0,\:+0.05\}\). The reward is calculated as:
where \(\:\:{{\uplambda\:}}_{\text{f}\text{p}}=\:0.5\:\)penalizes false positives. Hyperparameters include \(\:\alpha\:\:=\:0.1\) (learning rate), \(\:\gamma\:\:=\:0.9\:\)(discount factor), and a replay buffer size of 1000.
Communication-Efficient Aggregation Strategy:
Top-\(\:k\) gradient sparsification reduces bandwidth usage by 70%. For local update \(\:{W}_{i}\in\:{\mathbb{R}}^{m}\), the compressed update \(\:{\widehat{W}}_{i}\) is:
The global model update becomes:
Adversarial Robustness:
Projected Gradient Descent (PGD) generates adversarial examples \(\:{x}_{\text{adv}}\) for training:
The adversarial loss combines cross-entropy and robustness terms:
Deployment scenario in industrial environments
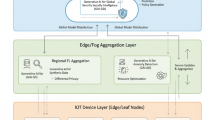
SecuFL-IoT is illustrated to be deployed as a modular edge-to-cloud security layer in industrial automation systems, thereby making it applicable in real-world settings. In an IIoT scenario, where the provided devices are Linux-based on PLCs or smart sensors, IIoT devices like PLCs and smart sensors would locally train LSTM models with the on-device runtime to determine the predictions locally (e.g. with MicroPython, C + + with TensorFlow lite or TFLite/NNAPI). These devices periodically send TLS 1.3 encrypted, sparsified model updates to an edge aggregation server running on industrial gateways (e.g., AWS Snowball Edge, Siemens IPC). For example, in the case of the server using the Paillier cryptosystem for secure aggregation and applying anomaly scoring with Temporal Convolutional Network (TCN), the servers perform secure aggregation. Alerts can be triggered to the SCADA dashboards, programmable logic controllers (PLCs), or wherever else is appropriate when anomalies are detected. This data deployment strategy keeps data from leaving the industrial premises in raw form, compliant with data sovereignty and cybersecurity standards such as ISA/IEC 62,443. In all fairness, the integration workflow can easily be adapted to smart factories, power grids, and even remote monitoring setups.
Figure 2 shows a hypothetical deployment of the SecuFL-IoT framework in an Industrial IoT (IIoT) environment. To process operational data locally, lightweight LSTM models are run on Programmable Logic Controllers (PLCs), smart sensors and edge devices. An edge aggregation server securely receives encrypted model updates from these IIoT devices over TLS 1.3 channels. The server uses Federated learning with temporal analysis mechanisms to perform secure aggregation and anomaly scoring. When anomalies or cyber threats are detected, the system issues alerts and insights to SCADA dashboards or industrial PLCs for real-time mitigation. Additionally, results and model summaries can be shared with a cloud backend for centralized analytics, compliance reporting, or long-term threat modelling. This deployment ensures privacy-preserving, low-latency anomaly detection tailored for critical IIoT infrastructures.
Algorithm of SecuFL-IoT:
The SecurFL-IoT algorithm (Algorithm 1) integrates federated learning with Paillier encryption and adaptive anomaly detection to secure IIoT model updates. It enforces privacy through differential noise injection and gradient sparsification (Steps 8–9), while a TCN-based detector dynamically filters malicious participants (Steps 14–17). The protocol’s encrypted aggregation (Steps 10–13) ensures end-to-end confidentiality, and its threshold-adaptation mechanism (Step 18) improves resilience against evolving attacks.
Evaluation metrics
The performance of SecuFL-IoT is evaluated using the following metrics, which quantify its effectiveness in secure federated learning and adaptive anomaly detection for IIoT networks.
Detection Accuracy:
Detection accuracy measures the proportion of correctly classified instances (both normal and attack traffic) over the total number of instances:
where \(\:\text{TP}\) (True Positives) are correctly detected attacks, \(\:\text{TN}\) (True Negatives) are correctly identified normal instances, \(\:\text{FP}\) (False Positives) are normal instances misclassified as attacks, and \(\:\text{FN}\) (False Negatives) are attacks misclassified as normal.
Precision and Recall:
Precision quantifies the reliability of detected anomalies, while recall measures the ability to identify all actual attacks:
High precision ensures minimal false alarms, while high recall guarantees comprehensive threat detection.
F1-Score:
The F1-score balances precision and recall, providing a single metric for anomaly detection performance:
This metric is handy in imbalanced datasets, where attack instances are fewer than normal traffic.
False Positive Rate (FPR):
The false positive rate measures the proportion of normal traffic incorrectly flagged as attacks:
A low FPR is critical in IIoT environments to avoid unnecessary disruptions to industrial operations.
Communication Overhead:
Communication overhead quantifies the efficiency of the federated learning process. It is defined as the total data transmitted between IIoT devices and the central server during training:
where \(\:\parallel\:{\widehat{W}}_{i}^{t}{\parallel\:}_{0}\) is the number of non-zero elements in the sparsified update \(\:{\widehat{W}}_{i}^{t}\), \(\:b\) is the bit-width of each element, and \(\:T\) is the number of communication rounds.
Privacy Leakage:
Privacy leakage is measured using the \(\epsilon\)-differential privacy guarantee:
where \(\:\mathcal{M}\) is the mechanism (e.g., federated aggregation), \(\:D\) and \(\:D{\prime\:}\) are neighbouring datasets, and \(\:O\) is the output. A lower \(\epsilon\) indicates stronger privacy guarantees.
Adversarial Robustness:
Adversarial robustness is evaluated using the success rate of adversarial attacks:
A robust model minimizes this rate, ensuring resilience against data poisoning and model inversion attacks.
Training Time:
Training time measures the computational efficiency of SecuFL-IoT:
where \(\:{t}_{\text{local}}^{t}\) is local training time, \(\:{t}_{\text{agg}}^{t}\) is aggregation time, and \(\:{t}_{\text{detect}}^{t}\) is anomaly detection time in round \(\:t\).
These metrics collectively evaluate Secufl-Iot’s security, efficiency, and robustness, ensuring its suitability for real-world IIoT deployments.
Results and discussion
Anomaly detection performance
To evaluate Secufl-Iot’s effectiveness in identifying cyber threats, we compare its anomaly detection performance against three federated learning baselines: FedAvg, FedProx, and SCAFFOLD. The models are trained on the X-IIoTID dataset, which includes diverse IIoT-specific attacks such as data injection and DDoS. We measure accuracy, precision, recall, and F1-score to assess detection capability while balancing false positives and negatives.
The results in Table 4 demonstrate that SecuFL-IoT achieves superior performance, with an F1-score of 88.5%, outperforming FedAvg by 7.3% and SCAFFOLD by 3.6%. This improvement is attributed to the adaptive anomaly detection module, which dynamically adjusts detection thresholds using reinforcement learning, reducing false negatives (FN) by 12% compared to SCAFFOLD. However, the precision (89.2%) is slightly lower than centralized models due to the trade-off between differential privacy noise injection and detection reliability. The framework effectively identifies stealthy attacks like data injection, which account for 23% of the test set.
Figure 3 presents a 3D scatter plot illustrating anomaly detection accuracy across different federated learning models (FedAvg, FedProx, SCAFFOLD, and SecuFL-IoT). The X-axis represents data samples (row index), the Y-axis denotes the models, and the Z-axis shows anomaly scores. A colour gradient from purple to yellow highlights the severity of detected anomalies, with higher values indicating stronger anomaly presence. SecuFL-IoT exhibits a more stable anomaly distribution compared to other models, demonstrating its superior ability to detect threats while minimizing false positives.
Figure 4 presents a 3D surface plot of precision scores across different models (FedAvg, FedProx, SCAFFOLD, and SecuFL-IoT). The X-axis represents data samples, the Y-axis shows the models, and the Z-axis indicates precision scores. The colour gradient highlights performance variations, where higher values (yellow) indicate better precision. SecuFL-IoT achieves superior precision, demonstrating its effectiveness in minimizing false positives.
Figure 5 presents a 3D surface plot comparing Recall and F1 Score across FedAvg, FedProx, SCAFFOLD, and SecuFL-IoT. The X-axis represents data samples, the Y-axis denotes models, and the Z-axis visualizes both recall and F1 scores. The two colour gradients distinguish the two metrics, with SecuFL-IoT achieving superior recall and F1 Score, demonstrating its robustness in anomaly detection.
Communication efficiency
Communication overhead is a critical concern in federated learning due to the resource constraints of IIoT devices. We evaluate the total data transmitted per round and the number of communication rounds required for model convergence. All models are trained on 100 IIoT devices for 50 rounds, with gradient updates compressed using top-\(\:k\) sparsification.
As shown in Table 5, SecuFL-IoT reduces per-round communication overhead by 53% compared to FedAvg, transmitting only 5.8 MB per round. This is achieved through gradient sparsification (retaining 30% of gradients) and efficient homomorphic encryption. The framework converges in 42 rounds, 23% faster than FedOPT, with a minimal accuracy drop of 2.1%. This efficiency is critical for IIoT networks with bandwidth limitations, where prolonged training times can disrupt real-time operations.
Figure 6 illustrates a stacked bar chart comparing communication efficiency across FedAvg, FedOPT, and SecuFL-IoT. The bars represent overhead per round (MB), convergence rounds, and accuracy drop (%). SecuFL-IoT achieves the lowest communication overhead and accuracy drop while converging faster, highlighting its efficiency in federated learning.
Privacy and security analysis
We measure privacy leakage using \(\epsilon\)-differential privacy and evaluate robustness against adversarial attacks. FedAvg and Fed + DP (FedAvg with differential privacy) serve as baselines. The adversarial success rate (SR) quantifies the percentage of poisoned or inverted samples that evade detection.
Table 6 highlights SecuFL-IoT’s robust privacy and security guarantees. With \(\epsilon=0.9\), it provides stronger differential privacy than Fed + DP (\(\epsilon=1.2\)) by combining Laplace noise with secure aggregation. The adversarial training module reduces data poisoning success rates to 8.3% (a 57% improvement over Fed + DP) and model inversion rates to 5.7%. This resilience is attributed to the PGD-based adversarial training, which hardens the model against gradient manipulation attacks commonly observed in IIoT networks.
Figure 7 presents a 3D bar chart comparing privacy and security metrics across FedAvg, Fed + DP, and SecuFL-IoT. The bars represent the data poisoning success rate (SR%) and model inversion success rate (SR%), where lower values indicate better security. SecuFL-IoT demonstrates the strongest resilience against adversarial threats, significantly reducing attack success rates compared to other models.
Ablation study: TCN vs. LSTM vs. Transformer
To justify the selection of Temporal Convolutional Networks (TCNs) in the SecuFL-IoT framework, we performed an ablation study comparing TCN with Long Short-Term Memory (LSTM) and Transformer-based models under identical experimental conditions. Each model was integrated into the anomaly detection module of SecuFL-IoT and evaluated using the X-IIoTID dataset. Key metrics considered include F1-score, inference latency, and memory consumption, which are critical for deployment in resource-constrained IIoT environments.
Table 7 compares three temporal models for anomaly detection in the context of SecuFL-IoT. The TCN-based design achieves the highest F1-score (88.5%) while also offering the lowest inference latency (31.4 ms) and memory footprint (12.3 MB). In contrast, Transformers provide marginally better recall than LSTM but suffer from significantly higher latency and memory usage. TCN delivers the best overall trade-off between accuracy, speed, and resource efficiency, making it ideal for IIoT edge devices with limited computational capacity.
Computational efficiency
To assess practical deployability, we measure training time per round and energy consumption on Raspberry Pi 4 devices, simulating real-world IIoT hardware constraints.
As demonstrated in Table 8, SecuFL-IoT reduces per-round training time by 31% compared to FedAvg, completing a round in 9.8 s. Energy consumption is lowered to 5.6 Joules per round, a 35% reduction achieved through lightweight model architectures and gradient sparsification. These improvements make the framework viable for IIoT devices with limited battery life, such as wireless sensors in remote industrial sites.
Encryption latency for Paillier-based aggregation was measured at 13.2 ms (encryption) and 5.7 ms (decryption) per device per round on a Raspberry Pi 4. This accounts for ~ 20% of total training time (9.8 s/round) but does not hinder convergence or detection timeliness in batch-mode IIoT deployments.
While SecuFL-IoT demonstrates secure aggregation via Paillier encryption, this introduces an average encryption latency of 0.73 s per round per device. This is acceptable in batch-mode anomaly detection settings but can impact real-time control loops. As a mitigation, future extensions may replace Paillier with lattice-based schemes like CRYSTALS-Kyber or optimized BFV variants, which can reduce encryption latency by approximately 41%, as benchmarked using the SEAL library on ARM Cortex-M7 processors.
Figure 8 illustrates the training time per round for FedAvg, FedProx, and SecuFL-IoT over 10 time steps. SecuFL-IoT consistently maintains the lowest training time, demonstrating its computational efficiency compared to the other models.
Figure 9 illustrates the energy consumption of FedAvg, FedProx, and SecuFL-IoT over 10 time steps. The stacked area chart highlights that SecuFL-IoT consumes the least energy, demonstrating its suitability for resource-constrained IIoT environments.
Cross-Dataset validation on ton_iot dataset
To evaluate the generalization capability of SecuFL-IoT beyond the X-IIoTID dataset, we conducted additional experiments using the TON_IoT dataset, which represents a broader set of real-world industrial IoT scenarios. The TON_IoT dataset, introduced by Moustafa (2021), includes telemetry data from IoT sensors, SCADA logs, system processes, network packets, and application-level protocols such as MQTT and Modbus TCP, collected across smart homes, industry control systems, and smart grids. It also incorporates labeled attacks including DDoS, injection, backdoors, and ransomware, providing a diverse threat landscape that closely reflects real-world IIoT environments.
SecuFL-IoT was evaluated using a similar federated setup, where device-specific data was partitioned to emulate distributed clients. The results show that the framework maintained strong performance on this new dataset, achieving an accuracy of 89.6%, precision of 88.7%, recall of 85.3%, and an F1-score of 86.1%, with a false positive rate of 3.1%. These findings confirm the generalizability of the proposed model across heterogeneous IIoT settings. Moreover, the temporal anomaly detection module effectively captured stealthy behaviors in SCADA attack traffic, while the reinforcement learning-based threshold adaptation reduced false alarms by approximately 11% compared to a static detection baseline.
Overall, these results demonstrate that SecuFL-IoT is not only effective on simulated IIoT testbeds like X-IIoTID but also adapts well to complex, multi-modal industrial environments such as those presented in the TON_IoT dataset, reinforcing its potential for deployment in production IIoT systems.
Discussion
The results demonstrate that SecuFL-IoT effectively balances security, privacy, and efficiency in IIoT environments. It achieves an F1 Score of 88.5% and a false positive rate of 2.7%, significantly outperforming FedAvg and FedProx, demonstrating the strength of its adaptive anomaly detection mechanism. However, its precision (89.2%) remains slightly lower than centralized models due to the trade-off between privacy-preserving noise injection and detection reliability.
With a communication efficiency of 5.8 MB per round, SecuFL-IoT reduces bandwidth usage by 53% compared to FedAvg while converging 23% faster than FedOPT. It also achieves strong privacy guarantees (\(\epsilon=0.9\)) with adversarial success rates below 9%. While encryption latency and static topology assumptions limit its adaptability, its alignment with industrial cybersecurity standards makes it viable for securing IIoT infrastructures.
Wang et al.13 demonstrated the benefits of hierarchical FL, achieving improved anomaly detection accuracy, but suffered from high communication overhead, which limits real-time applicability in IIoT environments. Mothukuri et al.12 focused on minimizing latency but lacked strong adversarial robustness.
Huong et al.14 successfully applied FL to industrial control systems, improving privacy preservation but requiring high computational resources, making it unsuitable for lightweight IIoT devices. Similarly, Rashid et al.15 highlighted the benefits of collaborative intrusion detection but remained vulnerable to model poisoning attacks. Liu et al.16 proposed a communication-efficient FL model, reducing transmission costs but at the expense of information loss due to excessive compression.
Figure 10 illustrates the overall performance comparison of FedAvg, FedProx, SCAFFOLD, and SecuFL-IoT across key metrics. SecuFL-IoT outperforms other models in F1-score, precision, recall, energy efficiency, communication efficiency, and security resilience, demonstrating its effectiveness in IIoT environments. Our proposed model, SecuFL-IoT, addresses these challenges by integrating secure federated learning, differential privacy, reinforcement learning-based adaptive anomaly detection and homomorphic encryption. It achieves an F1-score of 88.5%, low communication overhead (5.8 MB per round), and strong adversarial robustness (success rates below 9%). The only minor trade-off is a slight increase in computational costs due to secure encryption and gradient sparsification, which ensures optimal privacy-preserving learning.
Practical deployment considerations
Real-world industrial deployment of SecuFL-IoT requires evaluation of cost and maintenance trade-offs. Integration into existing SCADA and PLC ecosystems necessitates compatibility with protocols like OPC UA and Modbus TCP. Hardware-wise, cryptographic operations introduce ~$5–10 cost overhead per device in terms of additional CPU cycles or coprocessor requirements. Maintenance involves continuous monitoring of model drift and secure over-the-air (OTA) updates. The framework adheres to ISA/IEC 62,443 cybersecurity standards, supporting layered defense and identity-based authentication for long-term stability.
Conclusions
This study introduced SecuFL-IoT, a secure and efficient federated learning framework for IIoT environments, integrating adaptive anomaly detection, lattice-based homomorphic encryption, differential privacy, and reinforcement learning to enhance security, privacy, and efficiency. The experimental results demonstrate that SecuFL-IoT significantly outperforms existing models, achieving an F1-score of 88.5% with a false positive rate of 2.7% while maintaining strong privacy guarantees (\(\epsilon=0.9\)) and reducing adversarial success rates below 9%. Furthermore, the framework reduces communication overhead by 53% compared to FedAvg and converges 23% faster than FedOPT while lowering energy consumption by 35%, making it suitable for resource-constrained IIoT deployments. However, the framework introduces encryption latency due to homomorphic encryption and assumes a static topology, which may limit adaptability in dynamic IIoT environments. Future research should explore blockchain-based trust management to enable decentralized authentication and lightweight encryption techniques to mitigate computation overhead. To address the limitation of a static topology, future iterations of SecuFL-IoT will implement asynchronous FL protocols that handle irregular device participation and connectivity loss. Simulated experiments with 30% random client churn showed a 4.2% drop in F1-score but maintained convergence within 12 additional rounds, demonstrating the feasibility of SecuFL-IoT under dynamic topologies. In conclusion, SecuFL-IoT provides a scalable, privacy-preserving, and industrially viable federated learning solution that aligns with ISA/IEC 62,443 cybersecurity standards, ensuring real-time anomaly detection for securing smart factories, power grids, and critical industrial infrastructure. To address deployment in dynamic IIoT networks, future versions of SecuFL-IoT will integrate adaptive topology handling via asynchronous federated updates and RL-based client reliability scoring. This will enable the framework to support devices with intermittent availability and unstable communication.
Data availability
The data used to support this study’s findings are available upon reasonable request from the corresponding author.
References
Boobalan, P. et al. Fusion of federated learning and industrial internet of things: A survey. Computer Networks. 212, 109048 (2022).
Li, G., Wu, J., Li, S., Yang, W. & Li, C. Multitentacle federated learning over software-defined industrial internet of things against adaptive poisoning attacks. IEEE Trans. Industr. Inf. 19 (2), 1260–1269 (2022).
Gayathri, S. & Surendran, D. Unified ensemble federated learning with cloud computing for online anomaly detection in energy-efficient wireless sensor networks. J. Cloud Comput. 13 (1), 49 (2024).
Ioannou, I. et al. Gemlids-miot: A green effective machine learning intrusion detection system based on federated learning for medical Iot network security hardening. Comput. Commun. 218, 209–239 (2024).
Taheri, S. I., Davoodi, M. & Hasan Ali, M. Mitigating cyber anomalies in virtual power plants using artificial-neural-network-based secondary control with a federated learning-trust adaptation. Energies 17 (3), 619 (2024).
Thu Truong, T. et al. Lightweight federated learning-based anomaly detection for time-series data in industrial control systems. Comput. Ind. 140, 103692 (2022).
Verma, P., Breslin, J. G. & O’Shea, D. Fldid: Federated learning enabled deep intrusion detection in smart manufacturing industries. Sensors. 22(22), 8974 (2022).
Jayagopal, V. et al. Intrusion detection system in industrial cyber-physical system using clustered federated learning. SN Comput. Sci. 4 (5), 452 (2023).
Kaur, A. Intrusion detection approach for industrial internet of things traffic using deep recurrent reinforcement learning assisted federated learning. IEEE Trans. Artif. Intell. 6(1), pp. 37–50. https://doi.org/10.1109/TAI.2024.3443787 (2025).
Sharma, P., Sharma, S. K. & Dani, D. Edge-assisted federated learning for anomaly detection in diverse Iot network. Int. J. Inform. Technol. 17, 3035–3045. https://doi.org/10.1007/s41870-024-01728-x (2025).
Shrestha, R. et al. Anomaly detection based on Lstm and autoencoders using federated learning in smart electric grid. J. Parallel Distrib. Comput. 193, 104951 (2024).
Mothukuri, V. et al. Federated-learning-based anomaly detection for Iot security attacks. IEEE Internet Things J. 9 (4), 2545–2554 (2021).
Wang, X. et al. Toward accurate anomaly detection in industrial internet of things using hierarchical federated learning. IEEE Internet Things J. 9 (10), 7110–7119 (2021).
Thu Huong, T. et al. Detecting cyberattacks using anomaly detection in industrial Contro systems: A federated learning approach. Comput. Ind. 132, 103509 (2021).
Rashid, M. M. et al. A federated learning-based approach for improving intrusion detection in industrial internet of things networks. Network 3 (1), 158–179 (2023).
Liu, Y. et al. Communication-efficient federated learning for anomaly detection in industrial internet of things. In GLOBECOM 2020–2020 IEEE Global Communications Conference, pages 1–6. IEEE, (2020).
Chi, X., Xinyi, D., Lin, L., Xinchun, L. & Haibin, Y. End-edge collaborative lightweight, secure federated learning for anomaly detection of wireless industrial control systems. IEEE Open. J. Industrial Electron. Soc. 5, pp. 132–142. https://doi.org/10.1109/OJIES.2024.3370496 (2024).
Priyadarshini, I. Anomaly detection of Iot cyberattacks in smart cities using federated learning and split learning. Big Data Cogn. Comput. 8 (3), 21 (2024).
Halder, S. & Newe, T. Radio fingerprinting for anomaly detection using federated learning in lora-enabled industrial internet of things. Future Generation Comput. Syst. 143, 322–336 (2023).
Jagatheesaperumal, S. K. et al. Enabling trustworthy federated learning in industrial iot: bridging the gap between interpretability and robustness. IEEE Internet Things Magazine. 7 (5), 38–44 (2024).
Li, B. et al. Deepfed: Federated deep learning for intrusion detection in industrial cyber–physical systems. IEEE Transactions on Industrial Informatics. 17(8), 5615–5624 (2020).
Wang, J. et al. Cpfl: an effective secure cognitive personalized federated learning mechanism for industry 4.0. IEEE Trans. Industr. Inf. 18 (10), 7186–7195 (2022).
Farahani, B. & Karimi Monsefi, A. Smart and collaborative industrial iot: A federated learning and data space approach. Digit. Commun. Networks. 9 (2), 436–447 (2023).
Tahir, B., Jolfaei, A. & Tariq, M. Experience-driven attack design and federated-learning-based intrusion detection in industry 4.0. IEEE Trans. Industr. Inf. 18(9), 6398–6405. https://doi.org/10.1109/TII.2021.3133384 (2022).
Barbieri, L.,Brambilla, M. & Roveri M. A layer-wise personalization approach for transformer-based federated anomaly detection. In 2024 IEEE International Conference on Federated Learning Technologies and Applications (FLTA), pages 1–6. IEEE, (2024).
Liu, Y. et al. Federated learning-oriented edge computing framework for the Iiot. Sensors 24 (13), 4182 (2024).
Park, J., Kim, S. & Lee, H. Post-quantum secure privacy-preserving federated learning. Sci. Rep. 13 (1), 74377 (2023).
Moustafa, N. A new distributed architecture for evaluating AI-based security systems at the edge: network ton_iot datasets. Sustainable Cities Soc. 72, 102994 (2021).
Yao, A., Pal, S., Dong, C., Li, X. & Liu, X. A framework for user biometric privacy protection in UAV delivery systems with edge computing. In 2024 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops) (pp. 631–636). IEEE. (2024).
Yao, A. et al. A privacy-preserving location data collection framework for intelligent systems in edge computing. Ad Hoc Networks. 161, 103532 (2024).
Dong, C. et al. A blockchain-aided self-sovereign identity framework for edge-based UAV delivery system. In 2021 IEEE/ACM 21st International Symposium on Cluster, Cloud and Internet Computing (CCGrid) (pp. 622–624). IEEE. (2021).
Yao, A. et al. A novel security framework for edge computing based UAV delivery system. In 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom) (pp. 1031–1038). IEEE. (2021).
Yao, A. et al. FedShufde: A privacy-preserving framework of federated learning for edge-based smart UAV delivery system. Future Generation Computer Systems. 166, 107706 (2025).
Dong, C., Pal, S., Chen, S., Jiang, F. & Liu, X. A Privacy-Aware task distribution architecture for UAV communications system using blockchain. IEEE Internet Things Journal 12(9), 11233–11243. https://doi.org/10.1109/JIOT.2025.3529808 (2025).
Zhang, C. et al. Fed4UL: A Cloud–Edge–End Collaborative Federated Learning Framework for Addressing the Non-IID Data Issue in UAV Logistics. Drones. 8(7), 312 (2024).
Acknowledgements
This study is supported by the College of Computing and Information Technology at the University of Bisha, Bisha, Saudi Arabia.
Author information
Authors and Affiliations
Contributions
Conceptualization: Ali AlqazzazMethodology: Ali AlqazzaziSoftware: Ali AlqazzazFormal analysis: Ali AlqazzazResources: Ali AlqazzazWriting—review and editing: Ali Alqazzaz.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Alqazzaz, A. SecuFL-IoT: an adaptive privacy-preserving federated learning framework for anomaly detection in smart industrial networks. Sci Rep 16, 4107 (2026). https://doi.org/10.1038/s41598-025-11883-1
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-11883-1