Abstract
In the era of big data, medical imaging systems create millions of medical images daily. Securing these images during their transmission and storage is a challenging task. Encryption is a practical approach for securing medical images, as it ensures the security of these images while preserving their sensitive contents. Multiple-image encryption is preferable to single-image encryption, in which patches of medical images are encrypted simultaneously. A novel multi-medical image encryption algorithm based on stack representation and block division is proposed. During preprocessing, the medical images are stacked into a 3D cube to prepare for the encryption process. The cube experiences a block division phase, followed by individual confusion and diffusion phases for each block. These phases utilize different keys generated from a Baker chaotic map, incorporating swapping and XOR operations, which result in a fully encrypted cube. The scalability and effectiveness of the proposed algorithm are tested through experiments, revealing its promise as a secure approach for encrypting color and grayscale medical images. The proposed MIE algorithm is robust against various attacks, exhibiting superior performance in terms of speed and security compared to similar methods.
Similar content being viewed by others
Introduction
Advancements in data transmission and multimedia processing techniques add significant risks to the security and privacy of medical data. As a vital data type, images are essential in various fields, including electronic healthcare1. These images typically contain sensitive information2, and unauthorized access to this data could result in significant problems. Developing an efficient and safe image encryption algorithm has become a considerable concern in image processing3. Researchers have suggested several encryption techniques, including chaos-based4,5,6, DNA-based7,8,9, compressive sensing10,11, transform domain12, and AI-based13,14 approaches, among others. Hosny et al.15 presented an elegant and extensive survey for securing multimedia content using various encryption approaches.
Many researchers are focusing on studying MIE algorithms to secure the large number of medical images transmitted16. MIE enhances security by combining multiple images into a single encrypted format, increasing complexity and making unauthorized decryption more challenging. This approach provides cohesive protection that mitigates the effects of breaches, surpassing the individual safeguarding of single images in complexity. Additionally, it reduces computational expenses compared to processing each image independently.
In recent years, several notable MIE algorithms have been proposed, including17,18. In the first paper, Chen et al. used DNA, and the gyrator transformed with the XOR operation to design an algorithm for MIE. In the second paper, Zhang et al. used DCT, Lorenz, and logistic maps to encrypt multiple images. Zhang & Gao19. proposed a MIE technique based on using a scrambling-diffusion structure, bit planes, Zigzag transformation, and exclusive OR operation. Wu et al.20 proposed an MIE algorithm based on DNA encoding and the SHA-256 hashing algorithm. Song et al.21 proposed a parallel image encryption scheme using intra-bitplane scrambling and multithreaded diffusion to accelerate the encryption process. While the method targets single images, its parallel architecture and efficiency improvements are highly relevant to MIE scenarios, where speed and scalability are critical.
Perez et al.22 proposed an MIE algorithm based on the JTC architecture, GT, and the JGPD. Zhang & Liu23 developed an MIE algorithm for encrypting multiple grayscale images using SZT, the Henon chaotic map, and the 2D ZT. Kumar & Dua24 utilized the ESC map and DNA to develop an MIE algorithm for RGB color images. Liu et al.25 proposed a semantically enhanced selective image encryption scheme based on salient object detection and parallel chaos-based encryption. Although it focuses on single images, its strategy of encrypting only sensitive regions and improving efficiency via parallel processing is relevant to MIE scenarios, where both speed and intelligent resource usage are essential.
Song et al.26 introduced a batch image encryption scheme that utilizes cross-image permutation and bidirectional diffusion, enabling the encryption of multiple images of varying sizes without requiring preprocessing. Du et al.27 proposed an MIE technique, which the study implemented into face images. The study began with a face detection process to capture the desired facial information from multiple plain images that were input.
Stack Image Representation (SIR) employs a stacking approach, where images are arranged in layers along the vertical dimension, resulting in a 3D array28. This representation is beneficial for enhancing the security of image encryption and enabling simultaneous processing of multiple images, preserving their unique characteristics while improving efficiency and maintaining data integrity, making it a valuable strategy for robust multidimensional image handling.
Despite their efficiency, existing MIE schemes have certain limitations. Certain methods are limited to encrypting a specific number of images simultaneously rather than accommodating an arbitrary number. Most algorithms are primarily tested on standard grayscale images, with very few explicitly tailored for medical image encryption. Others work with either grayscale or color images only. This paper, therefore, introduces an encryption scheme designed explicitly for multiple medical images. This paper’s primary contributions are delineated as follows:
-
1.
The proposed MIE algorithm encrypts a massive number of medical images simultaneously and is designed to effectively encrypt grayscale and color images, showcasing its adaptability and broad applicability.
-
2.
It creates interconnected cipher images within the same stack, where if one cipher image is lost, the remaining cipher images in the stack can help recover partial information from the lost image.
-
3.
MIE is implemented using multilayer encryption to enhance security, including subdivision, 3D transformation, block segmentation, confusion, and diffusion processes. Subdivide the images and apply 3D transformations to increase the complexity of the decryption process.
-
4.
Applying block segmentation-based encryption to disrupt the intra-correlation between adjacent pixels and utilize different keys generated from a Baker chaotic map, incorporating swapping and XOR operations to apply confusion and diffusion processes for each block.
This multi-stage approach provides high security and complexity, making unauthorized decryption attempts for multiple medical images challenging. It integrates stacking randomization, confusion, and diffusion, supported by chaotic maps and stacking representation.
The paper is organized as follows: the proposed MIE algorithm is presented in Sect. 2. The validity and the effectiveness of the proposed method are presented in Sect. 3. Experiments, results, and the discussion are included in Sect. 4. Finally, the conclusion is given in Sect. 5.
Proposed method
Encryption scheme for color images
The encryption process for multiple images involves several sequential steps, each contributing to the security of the images. The entire process can be broken down into the following stages, as illustrated in the diagram below.
Crop process
For each original image \(\:I\:\)with dimension \(\:W\times\:H\times\:D\:\)and desired crop size \(\:{w}_{c}\:and\:{h}_{c}\):
-
1.
Split each image into RGB channels \(\:{I}_{r},{I}_{g},\:{I}_{b}\), each of which has a size of \(\:W\times\:H\).
-
2.
Determine the number of crops in both the width and height directions.
$$\:{N}_{x}=\left[\:\frac{W}{{w}_{c}}\:\right],\:{N}_{y}=\left[\:\frac{H}{{\:h}_{c}}\:\right]\:$$(1)
Where \(\:{N}_{x}\) represents the number of crops along the horizontal direction, and \(\:{N}_{y}\:\)represents the number of crops along the vertical direction.
-
3
For each crop \(\:(i,j)\) operation:
-
a.
Determine the coordinates of each crop.
Where,
Where \(\:i\) denotes the horizontal index and \(\:j\:\)denotes the vertical index. \(\:{x}_{s},\:\:{x}_{e}\:\)are the start and end coordinates along the horizontal direction, and \(\:{y}_{s},\:\:{y}_{e}\:\)along the vertical direction.
-
4.
Use the calculated coordinates to extract crops for each channel:
Stacking process
After cropping all input images into smaller crops, the stacking process proceeds as follows:
-
1.
Determine the total number of 2D crops.
Where \(\:n\) is the total number of input images.
-
2.
Initialize \(\:cube\) of size \(\:N\times\:{w}_{c}\times\:{h}_{c}\), and stack the crops \(\:{C}_{l}\) onto it.
where:
3. Repeat steps 1 and 2 for each channel.
Block division
-
1.
Let the block size be \(\:{b}_{x},{b}_{y},\:and\:{b}_{z}\). Determine the number of blocks that fit along all dimensions:
-
2.
Iterate \(\:{N}_{b}\) over the \(\:cube\) to extract blocks by slicing them. For each iteration, extract a block as follows:
where:
-
3.
Repeat steps 1 and 2 for each channel.
Permutation and substitution
In this process, pixels in each block are permuted and substituted using different keys according to the following steps.
-
1.
Generate two keys for each block using \(\:\alpha\:\:and\:\beta\:\) parameters, which are calculated as follows:
-
2.
Insert \(\:\alpha\:\:and\:\beta\:\) parameters into the Baker map defined by29 to generate the keys \(\:({X}_{p},\:{Y}_{s})\).
-
3.
Apply the permutation process for each block. In this phase, the pixel positions across the block are permuted to achieve a more complex data mixing. In this step \(\:block\) cube is scrambled by using a sequence \(\:{X}_{p}\) as follows:
-
i.
Flattening block cube into a 1D vector \(\:v\), as follows:
where \(\:r\) is a linear index in the 1D vector, and let \(\:{v}_{n}=\:{b}_{x}\times\:{b}_{y}\times\:{b}_{z}\).
ii. Swapping values in the vector as follows:
-
4.
Apply the substitution process for each block. In this phase, the pixel values are adjusted to obscure their original content using \(\:{Y}_{s}\), where the values of the vector \(\:v\) is changed as follows:
-
i.
The bitwise XOR operation is performed as follows.
-
i.
ii. Reshaping of vector \(\:v\) is performed to obtain a final encrypted \(\:block\) cube, as follows.
-
5.
Repeat steps from 1 to 4 are applied to each block separately, obtaining a total \(\:{N}_{b}\) encrypted blocks.
-
6.
Reconstruct the stack from the encrypted blocks to obtain the encrypted stack cube.
-
7.
Repeat steps 1 to 6 for each channel, resulting in three RGB-encrypted stacked cubes.
-
8.
Merge the RGB encrypted stacked cubes to produce the final cipher stacked image.
The entire encryption process is shown in Fig. 1.
Illustrative example for one channel
We use 64 images from the Multi-Cancer Dataset—8 Types of Cancer Images dataset. This dataset contains images of various cancer types, compiled for research and analysis purposes. It encompasses 8 main cancer classes and 26 subclasses, offering a comprehensive resource for medical image classification and machine learning applications. Given that the number of input images is \(\:n=64\), where the size of each image is \(\:W=512,\:H=512\) and crop size \(\:{w}_{c}=256,\:{h}_{c}=256\). Determine the number of crops along the width \(\:{N}_{x}\) and along the height \(\:{N}_{y}\):
The grid consists of a \(\:2\times\:2\) matrix of crops, with each crop defined by its coordinates \(\:{x}_{s},{y}_{s},{x}_{e},{y}_{e}\), Which results in Table 1:
Figure 2 illustrates the crop process for the illustrative example of one image. The previous steps applied to all input images resulted in a total number of crops \(\:N:\)
The total of 256 crops is stacked together, resulting in a 3D cube of size \(\:256\times\:256\times\:256\). Figure 3 shows the result of the stack process of the illustrative example. In the block segmentation process, let the block size be \(\:\left(128,\:128,\:128\right)\) then, the number of blocks that fit along each dimension is:
The result of the stacking process. The authors created the 3D visualization by using Python 3.9.12 and Plotly v6.2.0 (https://plotly.com/python/).
The result of the block segmentation, permutation, and substitution processes for the R-channel. The authors created the 3D visualization by using Python 3.9.12 and Plotly v6.2.0 (https://plotly.com/python/).
Figure 4 shows the result of the block segmentation process of the illustrative example, as well as the result of the permutation and substitution processes.
Table 2 is the representation for visualizing the block extraction for a total of 8 blocks:
Examples of plain images from the mentioned dataset and their corresponding encrypted images are shown in Fig. 5.
Decryption process
The encrypted images are divided into sub-images and stacked into a 3D cube in the decryption process. Block segmentation is then performed to prepare the images for reversing the encryption process. Figure 6 illustrates the entire decryption procedure.
Performance analysis
Three experiments were conducted to evaluate the proposed scheme’s performance. Table 3 provides details of the images, cubes, and blocks used in these experiments.
Key space
A valid image cryptosystem requires a key space large enough to render standard attacks, such as brute-force, infeasible. The key space represents the complete set of possible keys available for encryption/decryption. The secret key mainly consists of the initial values (\(\:u,t)\:\)and the control parameter \(\:\left(\rho\:\right)\:\)and the keys parameter \(\:(\alpha\:,\beta\:)\). Suppose the control parameter initial values and key parameter precision are\(\:{10}^{-15}\). Thus, the corresponding key space value is \(\:{\left({10}^{15}\right)}^{5\times\:{N}_{b}}\:\)where the minimum \(\:{N}_{b}\) value is equal to 2. So, the minimum key space value for the scheme is approximately \(\:{\left({10}^{15}\right)}^{5\times\:2}={10}^{150}\approx\:\:{2}^{498.29}\) which is greater than \(\:{2}^{128}\). Hence, the scheme has a highly adequate key space, therefore being resilient toward brute-force attacks. Table 4 lists the key spaces of the three experiments used.
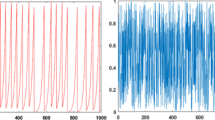
Key sensitivity
The secret key should be completely different when generated using different initial conditions, especially when the difference between these initial conditions is minimal. To carry out the key sensitivity analysis, there are two primary steps. The first one, \(\:{Key}_{1}\), is generated with the initial conditions \(\:{x}_{0},\:{y}_{0}\:\)and used to encrypt the plain image, resulting in a cipher image \(\:{c}_{1}\). In the second step, we change the initial conditions to \(\:{x}_{0}+{10}^{-10},\:{y}_{0}+{10}^{-10}\), then generate \(\:{Key}_{2}\) and use it to encrypt the same plain image, resulting in a cipher image \(\:{c}_{2}\). Finally, we decrypt the two encrypted images with the original \(\:{Key}_{1}\). Figure 7 illustrates the results of these processes.
Entropy
Entropy, as defined by30, quantifies an image’s level of randomness or unpredictability. It is a metric to assess how much information is hidden or concealed within the image. The entropy of the encrypted image was calculated and compared to that of the original image. The encrypted images showed a significant increase in entropy, indicating a high level of randomness and, thus, enhanced security. The amount of entropy \(\:H\) of an image is determined by utilizing the following formula:
Where \(\:N\) is the number of possible pixel values and \(\:{p}_{i}\), is the probability of occurrence of the \(\:i-th\) pixel value in the image. Ideally, the information entropy for a grayscale image is 8. Table 5 provides an entropy of the three implemented experiments after encryption. An entropy value of \(\:7.9999\) bits per pixel in the encrypted image is close to the theoretical ideal value. The high entropy of the encrypted image suggests that the pixel values are spread roughly uniformly. Such high entropy demonstrates that the encryption process has been highly effective in randomizing pixel values and concealing the original image content.
Histogram analysis
The histograms of the original and encrypted images were compared to assess the effectiveness of the encryption in terms of pixel value distribution. The encrypted images exhibited uniform histograms, indicating that pixel values were effectively scrambled and that the encryption successfully masked the original image data. Figure 8 displays the histograms of the cipher cubes of the three experiments.
Time analysis
The efficiency of the designed scheme is directly reflected in the speed of the encryption process. To evaluate this, three image sets with dimensions of \(\:128\times\:128\), \(\:256\times\:256\), and \(\:512\times\:512\) were used. The average encryption times for these operations are presented in Table 6. The experiments were conducted on a system with an Intel Core i5-9300 H CPU (2.40 GHz, 4 cores, 8 threads) and Windows 11 OS. The average encryption time per image and channel demonstrates the method’s efficiency, with reasonable execution times across test cases. These results suggest that the proposed scheme is computationally feasible for practical applications; however, further optimization, such as parallel processing, could enhance its performance.
Time complexity
The proposed MIE algorithm consists of four main stages: cropping, 3D stacking, block division, and block-wise encryption. The cropping and stacking steps are linear concerning the number of input images \(\:n\), resulting in a complexity of \(\:O\left(n\right)\). During encryption, each block of fixed size\(\:\:b\times\:b\times\:b\) undergoes permutation and substitution, with complexity \(\:O\left({b}^{3}\right)\) per block. Since the block size \(\:b\) is small and constant in practice, the overall time complexity becomes \(\:O(n\cdot\:{b}^{3})\), which effectively behaves as \(\:O\left(n\right)\). This demonstrates the method’s scalability and computational efficiency in real-world implementations.
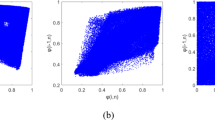
Correlation analysis
An effective encryption technique should eliminate the correlation between diagonal, horizontal, and vertical pixels, ensuring that the pixel relationships in the plain images are completely obscured, thereby enhancing the security of the encrypted images and preventing statistical attacks. The correlation \(\:{r}_{i,j}\) of 10,000 randomly selected adjacent pixel pairs \(\:(i,j)\) from both the plain and cipher images was estimated using the following equations:
Where:
In Experiment 2, Figs. 9 and 10 present the distributions of pixels of the RGB channels of the color plain and corresponding cipher images along three orientations. Table 7 identifies the correlation coefficients of the RGB channels of the plain and corresponding cipher color images neighboring pixel values in three orientations. All the results of the cipher RGB channels are approaching 0, exhibiting reduced inter- and intra-channel correlation, and the pixels became highly dissimilar to each other.
Differential attack analysis
Metrics include the Unified Average Changing Intensity (UACI) and the Number of Pixels Change Rate (NPCR), which are used to quantify the resistance to different attacks. These metrics measure the differences between two encrypted images obtained by slightly altering the original image. Consequently, even minor pixel alterations in the original image substantially impact the encrypted image31. The following are the definitions of UACI and NPCR:
Where \(\:{C}_{1},\:\text{a}\text{n}\text{d}\:{C}_{2\:}\), are two cipher images derived from a plain image with a single random pixel variation, while \(\:\left(w,h\right),\:\)denotes the number of rows and columns. Table 8 shows NPCR and UACI values. Suppose the resulting cubes from encrypting two virtually similar cubes show an NPCR close to 100% and a UACI larger than 33%32. In this case, the encryption method can be considered strong since a minor change in the algorithm’s input results in a drastically different output. The results indicate that our method exhibits resilience against differential attacks.
MSE and PSNR
For a cipher image to be deemed effective, it must show a substantial deviation from its plain form, ensuring that the encrypted image bears no resemblance to the plain image. The MSE measures the total squared difference between the original and cipher images using the following formula:
where \(\:P\left(i,j\right)\) represents the pixel value of the plain image while \(\:E(i,j)\) denotes the corresponding encrypted pixel value at the position \(\:(i,j)\) in the cipher image. The MSE value serves as a criterion for assessing the encryption level of a cryptosystem, where the encryption security level increases with a larger MSE scale. PSNR analysis determines the quality level of encryption; a higher score indicates that the encrypted image closely resembles the original image. Therefore, a smaller PSNR value indicates stronger encryption for a cryptosystem. It can be described as follows:
The values of the MSE and PSNR reported in Table 9 highlight the difficulties of recovering the plain image content from the cipher image without knowing the secret decryption key.
Data loss and data noise
Images experience data loss during transmission or storage. In the case of a cipher cube, some data is lost, and the remaining information is recovered through the decryption process. The experiments partially destroy the cipher cube and then implement the decryption process to get the original images. Images are also affected by noise during transmission or storage, in addition to data loss. To simulate a noise attack, noise was added to the cipher cube at varying intensities of salt and pepper before decrypting the cube. After applying block data loss of 10% and 20%, and under salt-and-pepper noise with densities of 5% and 10%, the proposed algorithm maintained PSNR values ranging from 21.5 dB to 30.2 dB. Corresponding SSIM scores were 0.72 and 0.81, indicating acceptable visual quality and structural preservation despite noise corruption.
The results are displayed in Fig. 11. The results reveal that the most authentic features of the images have remained intact after decryption, suggesting that the proposed technique can resist these attacks.
Grayscale images
Although this study focuses on color image encryption, the proposed method can also be used for a single grayscale channel. Some analyses are performed to evaluate the scheme for grayscale images. Figures 12 and 13 illustrate the encryption and decryption methodology for grayscale images, and Fig. 14 shows examples of plain grayscale medical images and their corresponding encrypted images.
Figures 15 and 16 show the histogram and correlation analysis results for a 256 × 256 image, demonstrating a uniform distribution. The histogram confirms that pixel intensity values are evenly spread, ensuring the encryption process effectively conceals patterns. Additionally, the reduced correlation between adjacent pixels highlights the proposed method’s strong diffusion and confusion properties, making it resistant to statistical attacks.
Other analyses are shown in Table 10, where the entropy, NPCR, UACI, PSNR, MSE, and execution time demonstrate favorable values. The high entropy value indicates a high level of randomness in cipher images. In contrast, NPCR and UACI values confirm the method’s sensitivity to small changes in plaintext images, ensuring a strong avalanche effect. The PSNR and MSE values also highlight the significant difference between the original and cipher images, reinforcing the encryption strength. Moreover, the execution time further demonstrates the efficiency of the proposed approach, making it suitable for real-time applications.
Discussion
This study presents a multiple medical image encryption scheme for both color and grayscale images. The proposed approach integrates a chaotic map, 3D transformation, and block segmentation to enhance security and efficiency. Chaotic maps ensure high sensitivity, 3D transformations strengthen confusions and diffusions, and block segmentation optimizes processing speed. Following the trends of hybrid encryption techniques, this scheme effectively balances security and computational performance. Notably, it achieves a 0.1-second encryption time for a 256 × 256-channels image, demonstrating its efficiency for real-time applications. The result highlights the potential of combining chaotic maps with 3D transformation for robust and fast encryptions. The proposed multiple medical image encryption scheme demonstrates superior performance across key security and efficiency metrics.
The algorithm was compared with several recent chaotic-based MIE techniques. Singh et al.33 encrypt multiple grayscale images by merging them into an RGB image and applying chaotic permutation and diffusion. The method proposed by Gao et al.34 combines three grayscale images into a single image and performs encryption on a single channel using a chaotic system. The algorithm by Zhang and Zhang35 encrypts multiple images using chaotic scrambling and gene fusion based on DNA operations. These algorithms were selected for comparison as they represent MIE approaches built entirely on chaotic principles.
Additionally, the scheme was evaluated against MIE algorithms that employ alternative strategies. Xu et al.36 introduced an approach that encrypts multiple medical images by scrambling the region of interest (ROI) and applying diffusion using odd-even interleaved points. It represents a domain-specific MIE method that focuses on protecting sensitive content. Xu37 proposed a multiple-image encryption algorithm based on orthogonal arrays with strength 3, incorporating chaotic operations to perform spatial permutation and substitution across images. Ye and Guo38 presented an MIE algorithm that embeds encrypted images into a carrier image using 3D-DCT and a 3D chaotic map, producing a visually meaningful encrypted result with combined encryption and hiding. These works were selected for comparison as they present recent MIE techniques with varied strategies.
Further comparison was made with hybrid techniques that integrate chaotic systems with classical cryptographic or transformation elements. Zhang and Liu23 introduced a stereo Zigzag transformation to expand 2D scrambling into 3D, combined with hash-based chaotic diffusion. Alexan et al.39 developed an MIE algorithm using SVD, modified RC5, and a hyperchaotic Hill cipher for satellite imagery. Xu et al.40 proposed an approach based on a novel chaotic system and odd-even interleaving strategy for encrypting medical images. These methods were chosen for comparison because they represent recent hybrid MIE approaches that target enhanced robustness and domain-specific performance.
As shown in Table 11, the proposed algorithm achieves faster execution times than most recent MIE methods. The encryption time of 0.1 s for a 256 × 256-channel image makes it more efficient than both chaotic-only and transform-based approaches.
Security analysis reveals that the scheme maintains high entropy, ensuring a uniform distribution of ciphertexts. It provides a large key space, making brute-force attacks infeasible. The encryption process effectively reduces pixel correlation, enhancing security against statistical attacks. Table 12 presents the different MIE experiment key space and entropy results obtained using our scheme and recent algorithms, as well as various experimental correlation results.
Additionally, the scheme achieves high NPCR (~ 99%) and UACI (~ 33%), indicating strong sensitivity to small changes in plain data. Image quality metrics further validate the scheme’s effectiveness. A high MSE and low PSNR confirm strong encryption, ensuring encrypted images appear noise-like and unreadable. These improvements make the proposed approach well-suited for secure and efficient multiple medical image encryption. The values of UACI, NPCR, MSE, and PSNR for different algorithms are listed in Table 13.
The proposed encryption algorithm is based on chaotic systems and block-wise permutation–diffusion operations rather than number-theoretic or algebraic primitives. As a result, it is not directly susceptible to well-known quantum algorithms such as Shor’s algorithm, which targets RSA and ECC, or Grover’s algorithm, which speeds up key search in symmetric cryptosystems. Since the chaotic sequences used for scrambling and diffusion are dynamically generated per block and do not rely on fixed key scheduling or algebraic structure, the algorithm provides an inherent level of resistance to existing quantum attack models.
However, a formal quantum cryptanalysis of chaos-based image encryption schemes remains an open area of research. At present, there are no known quantum algorithms that can efficiently break such systems. Nevertheless, evaluating their security under quantum computing assumptions is essential in the context of post-quantum cryptography and will be addressed in future work.
Conclusion
A multiple-image encryption algorithm for medical images is proposed based on stack representation and block segmentation. In the preprocessing phase, multiple medical grayscale images are cropped into sub-images and stacked into a 3D cube to prepare for encryption. The cube then undergoes block segmentation, where each block is individually subjected to confusion and diffusion processes. These processes leverage keys generated from a Baker chaotic map, employing swapping and XOR operations to produce a fully encrypted cube. The proposed algorithm’s effectiveness is evaluated through comprehensive experiments, demonstrating its potential as a secure solution for encrypting medical grayscale images. By integrating image transformation, sub-image stacking, block segmentation, and the confusion and diffusion phases, the algorithm achieves high encryption strength and robustness against attacks. Performance analyses further reveal excellent encryption speed and strong security characteristics, making it a promising approach for medical image encryption.
Data availability
The data supporting this study’s findings are available from the corresponding author upon request.
Abbreviations
- MIE:
-
Multiple Image Encryption
- DNA:
-
Deoxyribonucleic acid
- AI:
-
Artificial Intelligence
- DCT:
-
Discrete Cosine Transform
- NJTC:
-
Nonlinear Joint Transform Correlator
- GT:
-
Gyrator Transform
- JGPD:
-
Joint Gyrator Power Distribution
- SZT:
-
Stereo Zigzag Transformation
- ZT:
-
Zigzag Transformation
- ESC map:
-
Exponent Sine-Cosine map
- RGB:
-
Red, Green, Blue
- SIR:
-
Stack Image Representation
- 2D:
-
Two Dimensional
- 3D:
-
Three Dimensional
- OS:
-
Operating System
- UACI:
-
Unified Average Changing Intensity
- NPCR:
-
Number of Pixels Change Rate
- MSE:
-
Mean Square Error
- PSNR:
-
Peak-to-nose ratio
References
Abouelmehdi, K., Beni-Hessane, A. & Khaloufi, H. Big healthcare data: preserving security and privacy. J. Big Data. 5 (1), 1–18 (2018).
Wang, X., Liu, C. & Jiang, D. A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing, and 3D DCT. Inf. Sci. 574, 505–527 (2021).
Hosny, K. M. et al. New Method of Color Image Encryption Using Triple Chaotic Maps. IET Image Processing, Volume 18, Issue 12, Pages 3262–3276. (2024).
Mansouri, A. & Wang, X. A novel one-dimensional sine-powered chaotic map and its application in a new image encryption scheme. Inf. Sci. 520, 46–62 (2020).
Mohamed, H. I., Alhammad, S. M., Khafaga, D. S. & Hosny, K. M. A new image encryption scheme based on the hybridization of Lorenz chaotic map and fibonacci Qmatrix. IEEE Access. 12, 14764–14775 (2024).
Liu, X., Sun, K. & Wang, H. A novel image encryption scheme based on 2D SILM and improved permutation-confusion-diffusion operations. Multimedia Tools Appl. 82 (15), 23179–23205 (2023).
Wen, W., Wei, K., Zhang, Y., Fang, Y. & Li, M. Colour light field image encryption based on DNA sequences and chaotic systems. Nonlinear Dyn. 99, 1587–1600 (2020).
Wang, X. & Zhao, M. An image encryption algorithm based on a hyperchaotic system and DNA coding. Opt. Laser Technol. 143, 107316 (2021).
Qobbi, Y., Jarjar, A., Essaid, M. & Benazzi, A. Image encryption algorithm based on genetic operations and chaotic DNA encoding. Soft. Comput. 26 (12), 5823–5832 (2022).
Gong, L., Qiu, K., Deng, C. & Zhou, N. An image compression and encryption algorithm based on chaotic system and compressive sensing. Opt. Laser Technol. 115, 257–267 (2019).
Liu, J., Zhang, M., Tong, X. & Wang, Z. Image compression and encryption algorithm based on 2D compressive sensing and hyperchaotic system. Multimedia Syst. 28 (2), 595–610 (2022).
Joshi, A. B., Kumar, D., Mishra, D. C. & Guleria, V. Colour-image encryption based on 2D discrete wavelet transform and 3D logistic chaotic map. J. Mod. Opt. 67 (10), 933–949 (2020).
Qi, K. Advancing hospital healthcare: achieving IoT-based secure health monitoring through multilayer machine learning. J. Big Data. 12 (1), 1 (2025).
Naresh, V. S. & Reddi, S. Exploring the future of privacy-preserving heart disease prediction: a fully homomorphic encryption-driven logistic regression approach—Journal. Big Data. 12 (1), 52 (2025).
Hosny, K. M., Zaki, M. A., Lashin, N. A., Fouda, M. M. & Hamza, H. M. Multimedia security using encryption: A survey. IEEE Access. 11, 63027–63056 (2023).
Hosny, K. M., Elnabawy, Y. M., Salama, R. A. & Elshewey, A. M. Multiple image encryption algorithm using channel randomization and multiple chaotic maps. Sci. Rep. 14 (1), 30597 (2024).
Chen, H., Liu, Z., Tanougast, C., Liu, F. & Blondel, W. A novel chaos-based optical cryptosystem for multiple images using DNA-blend and gyrator transform. Opt. Lasers Eng. 138, 106448 (2021).
Zhang, Y., He, Y., Zhang, J. & Liu, X. Multiple digital image encryption algorithm based on chaos algorithm. Mob. Networks Appl. 27 (4), 1349–1358 (2022).
Zhang, X. & Gao, T. Multiple-image encryption algorithm based on the bit plane and superpixel. Multimedia Tools Appl. 82 (13), 19969–19991 (2023).
Wu, J., Zhang, J., Liu, D. & Wang, X. A multiple-medical-image encryption method based on SHA-256 and DNA encoding. Entropy 25 (6), 898 (2023).
Song, W. et al. A parallel image encryption algorithm using intra bitplane scrambling. Math. Comput. Simul. 204, 71–88 (2023).
Perez, R. A., Vilardy, J. M., Pérez-Cabré, E., Millán, M. S. & Torres, C. O. Nonlinear encryption for multiple images based on a joint transform correlator and the gyrator transform. Sensors 23 (3), 1679 (2023).
Zhang, X. & Liu, M. Multiple-image encryption algorithm based on the stereo zigzag transformation. Multimedia Tools Appl. 83 (8), 22701–22726 (2024).
Kumar, A. & Dua, M. A novel exponent–sine–cosine chaos map-based multiple image encryption technique. Multimedia Syst. 30 (3), 141 (2024).
Liu, B. et al. Semantically enhanced selective image encryption scheme with parallel computing. Expert Syst. Appl. 279, 127404 (2025).
Song, W. et al. Batch image encryption using cross image permutation and diffusion. J. Inform. Secur. Appl. 80, 103686 (2024).
Du, L., Teng, L., Liu, H. & Lu, H. Multiple face images encryption based on a new non-adjacent dynamic coupled mapping lattice. Expert Syst. Appl. 238, 121728 (2024).
Eltoukhy, M. M., Alsubaei, F. S., Elnabawy, Y. M. & Hosny, K. M. Multiple image encryption techniques: strategies, challenges, and potential future directions. Alexandria Eng. J. 125, 367–387 (2025).
Liu, L. & Miao, S. An image encryption algorithm based on a Baker map with varying parameters. Multimedia Tools Appl. 76, 16511–16527 (2017).
Ramakrishnan, B., Nkandeu, Y. P. K., Tamba, V. K., Tchamda, A. R. & Rajagopal, K. Image encryption based on S-box generation constructed by using a chaotic autonomous snap system with only one equilibrium point. Multimedia Tools Appl. 83 (8), 23509–23532 (2024).
Young, L. S. Mathematical theory of Lyapunov exponents. J. Phys. A: Math. Theor. 46 (25), 254001 (2013).
Zhang, F. & Wang, X. Color image encryption based on LSS-Type coupled mapped lattice. IEEE Access. 12, 41413–41420 (2024).
Laiphrakpam, D. S., Thingbaijam, R., Singh, K. M., Awida, A. & M Encrypting multiple images with an enhanced chaotic map. IEEE Access. 10, 87844–87859 (2022).
Gao, X. et al. A fast and efficient multiple images encryption based on single-channel encryption and chaotic system. Nonlinear Dyn. 108 (1), 613–636 (2022).
Zhang, X. & Zhang, L. Multiple-image encryption algorithm based on chaos and gene fusion. Multimedia Tools Appl. 81 (14), 20021–20042 (2022).
Wang, X. & Wang, Y. Multiple medical image encryption algorithm based on scrambling of region of interest and diffusion of odd-even interleaved points. Expert Syst. Appl. 213, 118924 (2023).
Xu, M. A multiple-image encryption algorithm based on orthogonal arrays with strength 3. Opt. Laser Technol. 167, 109746 (2023).
Ye, G., & Guo, L. A visual meaningful encryption and hiding algorithm for multiple images. Nonlinear Dynamics 112(16), 14593–14616 (2024).
Alexan, W. et al. A new multiple image encryption algorithm using hyperchaotic systems, SVD, and modified RC5. Sci. Rep. 15 (1), 9775 (2025).
Xu, C., Shang, Y., Yang, Y. & Zou, C. An encryption algorithm for multiple medical images based on a novel chaotic system and an odd-even separation strategy. Sci. Rep. 15 (1), 2863 (2025).
Acknowledgements
This work was funded by the University of Jeddah, Jeddah, Saudi Arabia, under grant No. (UJ-24-DR-xxx). Therefore, the authors thank the University of Jeddah for its technical and financial support. The authors extend their appreciation to the Deputyship for Research & Innovation, Ministry of Education in Saudi Arabia for funding this research work through the project number MoE-IF-UJ-R2-22-0379-1.
Author information
Authors and Affiliations
Contributions
Yousef S. Alsahafi: Formal analysis, Project administration, Funding acquisition, ValidationAkram Y. Sarhan: Resources, Data curation, VisualizationYasmin M. Elnabawy: Conceptualization, software, methodology, Visualization, writing—original draft preparationKhalid M. Hosny: Conceptualization, methodology, Formal analysis, Validation, writing—review and editing.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Alsahafi, Y.S., Sarhan, A.Y., Elnabawy, Y.M. et al. A new algorithm for multiple medical image encryption based on stacked representation and block division. Sci Rep 15, 35263 (2025). https://doi.org/10.1038/s41598-025-16146-7
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-16146-7