Abstract
Autonomous Vehicles (AVs) rely on secure neighbors and proactive infrastructures for robust communications. The heterogeneous communication scenario exploits concealed media for secure information exchange. Concealed communications assist precise navigation, information exchange, object detection, etc. In this process, the end-to-end computations are complex in converting a vehicle communication stream to an encrypted stream. This article introduces a Secure Module for Concealed Navigation Communication (SM-CNC) in AV environments. The information identified is transmitted by attaching volatile authentication that disintegrates if a communication source (vehicle or access point, etc.) is intercepted. Contrarily, the information is dropped in the communication medium if adverse or unauthorized vehicles intercept. This process is monitored during the relaying and end-to-end validation processes. The proposed secure module relies on quantum computing and recurrent learning for multiple recommendations from the information relay points. The information points are modeled as qubits for low-complex processing to administer security and ensure reliable communication. This prevents security breaches in the concealed medium through authentication failures and unauthorized access detection based on vehicle information allocated to individual qubits. The learning paradigm analyzes the qubits for their availability for secure information exchange throughout the navigation. The performance of the proposed module is verified using the metrics of communication failure, complexity, and authentication rate. The proposed secure module improves the authentication rate by 9.29% and reduces the communication failure and computation complexity by 11.87% and 12.13% respectively, for the maximum communication requests/ interval.
Similar content being viewed by others
Introduction
Context
Communication in vehicle fleets must be maintained in a secure environment to preserve communication continuity with each vehicle, known as concealed information communication. It uses encrypted communication channels that disguise the information in the transmission1. The unauthorized vehicles cannot collect visible transmission information. Concealed information communications support essential vehicle functions such as coordinated routes, as well as hazard communications2. The secret communication layers allow the vehicles to communicate without revealing vehicle-identifying data. There is no direct connection to the broadcasting emissions, so intrusion seems highly unlikely3. Vehicles can communicate while steering their routing to maximize the effectiveness of their encryption processes while minimizing the prospects of message latency4. Concealed information communication is significant in uses such as relaying messages in an urban network with multiple vehicles. Electronic messages are sent to several vehicles without exposing any data about the sender5. The type of environment supports situational awareness, while also keeping the identified data sealed from exposure. Encoding mechanisms are mapped to vehicular protocols and allow assessments at the fleet level. The secure concealment provides the basis for communication privacy to support large-scale autonomous deployments6,7.
Vehicle-to-vehicle exchanges should not only involve basic encryption but, more importantly, sensitive and context-aware authentication routines and responsive route guidance protocols8. Navigation services are even more reliant on secure data streams that prevent data hijacking and injection of false commands. Compromised channel communications from threats such as spoofing and packet manipulation are avoided through the use of ephemeral authentication keys that dissolve as soon as they’ve been compromised9. Authentication solutions that are protocol-based in-vehicle modules can respond instantly to the detection of anomalous sources. Communication protocols containing rejection logic prevent sending packets that are derived from unauthorized sources10. Media communication will provide linkages only to authentic sources, further reducing the ability for misinformation to cascade during transit. Potential hijacking or unintended interference in traffic patterns will forecast a revised trajectory based on the degree of access validation to the proximate infrastructure11,12. Vehicles will then alter their behavior dynamically based on threat mitigation. The dynamic and layered defense processes employed for route accuracy and data integrity across an enterprise fleet are likewise effective for security vulnerabilities that have yet to be discovered. The security framework supports autonomous coordination between vehicles and shared services while providing real-time adaptive validation methods for mobile-enabled networks13,14.
Deep learning (DL) models can shield vulnerable aspects of autonomous vehicles by utilizing feedback loops that change the flow of information and anticipate vulnerabilities. Recurrent structures can observe the movements of traffic and discover unusual behavior in information exchanges15. Models can also assess vehicle-to-vehicle communication streams and provide recommendations for messaging relaying intervals and the frequency of adaptive key-renewing mechanisms. Packet information is tagged through observance of behaviors and behavior-driven identity scores from learning patterns16. While qubit-based encoding methods for performance help reduce processing time, they also work with a quantum-aware deep network operating system. Such an approach also allows and manages fast encryption and low-latency responses as the mobility of the vehicle changes17,18. Neural networks that have been trained with data from past integrity attacks will now use that data to determine if there are future intrusion attempts. The added layer of intelligence ensures that vehicle communications remain secure without interrupting autonomous processes. DL models provide a barrier or a bubble around the data exchanges accumulated with connected vehicles in their ecosystem19,20.
Key contributions
The contributions of the article are:
-
To design and develop a novel concealed navigation communication module for autonomous vehicle platoons with volatile authentication and security validation features.
-
To integrate quantum computing and recurrent learning paradigms to ensure less complex security validations, to improve breach detection, and to ensure reliable vehicle-to-vehicle/vehicle-to-infrastructure communications.
-
To assess the performance of the proposed module using communication failure, computation complexity, authentication rate, sharing delay, and breach detection metrics.
-
To verify the proposed module’s performance using the above metrics with the existing RL4V2X, GSM, PSLAP, and IWOAFS-XAIAD methods.
Related works
Current research
Yang, X et al.21 proposed a decentralized approach to vehicle platoon formation that emphasizes security and reliability. The technique employs zero-knowledge succinct non-interactive arguments of knowledge and permissioned blockchain technology to conceal vehicle credentials from the service. The approach provides an adaptive defense against distributed denial-of-service and impersonation attacks during the formation process. The approach enhances the formation process better than the statistical barrier.
Zhang et al.22 developed a tamper-resistant broadcasting scheme (TRBS) for securing communications in the Internet of Autonomous Vehicles. An identity-based broadcast signcryption scheme was developed to ensure secure and authenticated one-to-many dissemination of messages. The TRBS protects against message tampering and forgery between autonomous vehicles. The TRBS was proven secure using formal security proofs and a practical implementation of the TRBS to be deployable in real life.
Xu et al.23 developed a secure system using XOR operations to protect communication between drones and vehicles. The method combines lightweight cryptographic techniques to ensure privacy and resist physical capture attacks. It is designed to use minimal resources for efficiency. Testing showed the method has low overhead and strong security.
Jin et al.24 proposed a provably secure lightweight privacy-preserving authentication method for autonomous vehicles in IoT settings. The idea utilized cryptographic primitives, such as XOR operations and elliptic curve cryptography, to allow secure communication within intelligent transportation systems. Informal assessment and real-or-random (ROR) modeling confirmed the privacy preservation. The suggested system demonstrated much higher computational and communications efficiency than existing methods.
To improve detection and classification, Zuo et al.25 proposed a privacy-preserving vehicle-to-infrastructure communication and secure authentication scheme. The proposed method used local differential privacy along with physical unclonable functions for authentication and operated without a third party. The IOTA distributed ledger is proposed to allow secure, scalable, and quantum-resistant vehicle-to-vehicle and vehicle-to-infrastructure interactions. The experimental analysis confirmed that the scheme had little overhead and preserved the utility-privacy balance.
Zhang et al.26 introduced an innovative reinforcement learning method (RL4V2X) for autonomous driving under interrupted vehicle-to-everything communications. The method uses convolutional neural networks, gated recurrent units, and gate networks to extract spatiotemporal features in the case of V2X disruption. The method contributes to improving decision-making and motion planning for autonomous vehicles navigating uncertain environments. The simulation results demonstrated improved working safety and efficiency in traversing the environment.
Zhu et al.27 proposed a two-layer optimization algorithm and a convolutional Bi-LSTM approach for flexible anomaly detection in autonomous vehicles. The methodology improves platoon formation security by establishing zk-SNARK signal encryption optimization and verifying it in real time on a permissioned blockchain. The approach serves as a powerful mechanism for anomaly identification and attack defense. The method improves security in autonomous vehicle networks.
Chen et al.28 proposed a Multilevel Electronic Control Unit Re-Encryption Scheme for autonomous vehicles. The method uses proxy re-encryption to provide backup electronic control units the ability to decrypt messages securely without disclosing their network keys. It ensures secure communications between multiple vehicle networks so that adversaries cannot send spoofed messages. The method is backed by formal proofs of security and simulations to demonstrate strong resiliency against known attacks.
To enable detection and classification, Chen et al.29 suggested a Privacy-Preserving Group Authentication Scheme for connected autonomous vehicles. The method allows for multi-user authentication at once using group-based authentication. It allows for privacy by changing group member identifiers frequently, so it cannot be tracked. The method defends against replay, identity, and spoofing attacks while making it cheaper and more practical than other methods.
Chen et al.30 created a method using contracts and the Arrowhead Framework to ensure safe vehicle communication. The technique employs agreements to officially outline security needs. It combines these agreements with a safety system to verify and permit communications between cars. The approach supports trustworthy and secure inter-vehicle communication.
Zhou et al.31 examined simple security measures designed for self-driving cars. The approach emphasizes flexible rules for personal devices in self-driving cars. It enhances fixed Internet of Things safety measures by tailoring them to car-specific requirements. The guidelines guarantee robust protection without affecting the efficiency of the system.
Zhou et al.32 created PDSM-FC, a method for sharing data among self-driving vehicle groups while keeping it private. The technique permits a safe, encrypted message transformation to facilitate interaction among various vehicle convoy clusters. It ensures the privacy and honesty of the information while organizing and altering the platoon. Security tests show the method resists attacks and uses minimal storage and computing power.
Liu et al.33 created a data-driven event-triggered sliding mode secure control scheme for autonomous vehicles under actuator attacks. The approach combines data-driven model decomposition with sliding mode control to stabilize vehicle lateral control during attacks. It reduces communication load by using event-triggered transmissions. Case studies show the method effectively counters malicious actuator interference.
Gao et al.34 implemented a detailed permission system for self-driving cars. The technique uses encryption based on characteristics with remote processing to protect messaging in vehicles with limited resources. It aids in confidentiality, streamlined key handling, and defense against numerous assaults. Tests showed the method is practical for real use.
Wang et al.35 suggested a visual safety framework with indicators for self-driving car systems. The technique constructs assault diagrams and hierarchies from network information to discover assault routes and evaluate protections. The indicators spontaneously evaluate protection and safety across various network strata. Applying the method improved security analysis in autonomous vehicle networks.
Gao et al.36 created SEFAV, a security testing platform for self-driving cars. The technique offers a virtual setting to examine privacy breaches involving movement patterns. It aids scientists in assessing and enhancing car safety. The framework is compatible with both Windows and Linux.
Chen et al.37 created a safe online system for self-driving cars with blockchain and smart agreements. The technique establishes a secure data exchange framework among self-driving car network points that is resistant to tampering. Smart agreements ensure data exchange guidelines, enhancing security and dependability. The method was executed using Solidity and blockchain technologies to show real-world applications.
Gao et al.38 introduced an Information-Centric Networking (ICN)-based cooperative caching framework for 5G communication systems that significantly improves cache hit ratio and latency reduction for AVs. This approach supports efficient data delivery under high mobility, contributing to reduced communication delays in autonomous fleets.
Balamurali et al.39 proposed an intelligent optimized route-discovery model for IoT-based VANETs using the Java macaque algorithm. This method ensures loop-free and efficient route establishment between AVs, enhancing energy-efficient and delay-tolerant communication.
Cui et al.40 presented a comprehensive study on 6G security, emphasizing physical and service-layer protocols including AI and quantum cryptography. Their work outlines how future AV networks must integrate post-quantum authentication and scalable access control mechanisms.
Karabulut-Kurt et al.41 developed a reinforcement learning-based peer-to-peer energy optimization model within a V2X framework, demonstrating how decentralized learning can efficiently manage AV energy exchange while supporting secure vehicle interactions.
Heterogeneous communication is exploited in the AV infrastructure for secure information exchange and navigation assistance between vehicles. End-to-end communication is used to share secure information with the vehicle. The volatile authentication is attached to the shared information to mitigate breaches. Here, both authentication and authorization are used to estimate the communication in a heterogeneous platform. The security breaches are used to ensure reliable communication for the AVs.
Research gap
Despite significant advancements in secure communication for autonomous vehicle (AV) systems, several critical challenges remain unresolved, particularly in the context of large-scale AV platoons operating in heterogeneous and dynamic environments. Existing solutions such as RL4V2X26, GSM30, PSLAP24, and IWOAFS-XAIAD27 have contributed notable frameworks for authentication, anomaly detection, and resilient communication. However, a closer examination reveals the following gaps:
-
Limited concealment and volatility mechanisms: Most existing models emphasize encryption and static key-based authentication but lack dynamic concealment strategies and volatile authentication protocols that adapt based on real-time threat detection. This limitation reduces their effectiveness in mitigating sophisticated interception or spoofing attacks during vehicle-to-vehicle (V2V) or vehicle-to-infrastructure (V2I) communications.
-
High computational complexity: Approaches involving traditional cryptographic primitives or reinforcement learning with deep networks often introduce substantial processing overhead. This computational cost limits their scalability in real-time AV platoon navigation, where rapid authentication and communication response are critical.
-
Underutilization of quantum-aware computing: While post-quantum cryptographic research is gaining momentum, few works have integrated quantum computing paradigms, such as qubit-based information modeling, with recurrent learning mechanisms to enable secure, low-complexity validation processes in AV networks. This integration remains largely underexplored.
-
Insufficient multi-metric evaluation: Many studies evaluate security models using narrow metrics, often limited to accuracy or authentication success rate. There is a need for a more holistic evaluation framework that simultaneously considers communication failure, computation complexity, authentication rate, sharing delay, and breach detection—metrics that collectively determine the viability of AV communication modules in operational environments.
-
Lack of end-to-end validation in AV platoons: Existing solutions often target isolated vehicle interactions or assume ideal communication channels. Real-world AV environments require continuous end-to-end validation with multi-point recommendations and secure relaying mechanisms to account for fluctuating trust levels and infrastructure heterogeneity.
In light of these gaps, this article proposes a novel Secure Module for Concealed Navigation Communication (SM-CNC) that leverages qubit-based computation and recurrent learning for dynamic, low-complexity authentication and breach detection. The module is rigorously validated using a multi-metric evaluation framework and benchmarked against leading approaches to demonstrate its superiority in AV platoon communication scenarios.
Proposed secure module for concealed information exchange
The concealed information exchange module proposed in this article targets secure communications between autonomous vehicles. Due to decentralized instruction feed and environmental sensing, adversary breaches are common in these networks. In an AV platoon, an interruption (breach) in a single communication line hinders/topples the entire AV collection. Besides, the coordinated vehicle movements are distributed, making them independent with different control executions. In a real-time scenario, the anonymous control of such vehicles results in accidents/pedestrian harm, etc., of severities. To handle the fundamental problem of AV breaches, this article introduces a novel module by assimilating quantum computing and recurrent learning paradigms. The role of qubits is to ensure low-complexity computations across security and communication. The learning paradigm validates the availability of qubits for AV breach assessment. Based on the above, the process flow of the proposed module is illustrated in Fig. 1.
In Fig. 1, the process flow of the proposed module is illustrated. The information sharing between the AV platoon and the infrastructure/access points is validated by the qubits for complexity. This complexity measure under volatile authentication and end-to-end validation is reduced by reusing qubits for any number of platoons. This qubit replacement/discarding results in the identification of breaches, and the validation is incomplete. The qubits for validation are recurrently analyzed using learning to ensure less complex assessments. For better understanding, the symbols used in the article are introduced in Table 1.
Information sharing model
The reliable neighboring vehicle is identified in the AV environment and detects the authentication and authorization for the vehicles. The authentication failure and unauthorized access are based on the initial registration and authentication. The mapping factor is generated for every step of processing that deploys secure information sharing between the vehicles. Here, the information loss and misdetection ratio are decreased, whereas information sharing is improved. This is addressed by developing the SM-CNC method between heterogeneous vehicles. Finally, the analysis is done for vehicle communication in the AV environment.
Vehicle communication is established to find a heterogeneous medium to exchange information with the end vehicle. Here, the end-to-end process is carried out by performing the communication securely. The volatile authentication is done for the information that detects the intercepts of the neighboring vehicles. The volatile authentication is attached to the vehicle and disintegrates if the authentication neighbor is intercepted. Finally, the validation is done for the relaying and end-to-end process, and the validation is carried out for the security breaches. Thus, the mapping factor is maintained for the security breaches for the vehicles in the AV environment. The information handling is done for the reliable vehicle and exploits the concealed medium for secure exchange between the heterogeneous platforms. The communication is established for the initial and the neighboring vehicle and performs the recommendation to ensure the mapping factor that deploys the end-to-end sharing. For information sharing, multiple recommendations are made, and sharing is examined for\(\:\:{h}_{n}\). The analysis for the communication is denoted as\(\:\:S\), and the vehicle and the vehicles in the AV are represented as\(\:{\:h}_{0}\text{a}\text{n}\text{d}\:{h}_{n}\). The neighboring vehicle at its initial position is denoted as\(\:\:h{\prime\:}\), and the information sharing in the secure medium is termed as\(\:{\:n}_{f}\).
The information is shared securely using a reliable medium and is represented as\(\:\:x{\prime\:}\); the communication in the heterogeneous infrastructure is denoted as\(\:\:{m}_{0}\). The request and response for the vehicle are used to forward the information appropriately, and it is defined as\(\:{\:q}^{{\prime\:}}\text{a}\text{n}\text{d}\:{p}_{s}\), the volatile information is attached to identify unauthenticated vehicles, and it is represented as\(\:\:l{\prime\:}\). The identical information is retrieved from the individual vehicles in the fleet. It ensures security, and it is termed as\(\:\:L\), the time of processing the data is denoted as\(\:\:m{\prime\:}\), and the previous state of information is denoted as\(\:\:d{\prime\:}\). The state is either a successful validation with a delivered state or a failure, and the validation is incomplete. Therefore,\(\:\:{d}^{{\prime\:}}=0\) for incomplete validation, else 1 for a\(\:\:{p}_{s}\) satisfied validation. Thus, the analysis for communication is established efficiently. The equation below is used to identify the information sharing for the neighboring and initial vehicles.
The identification is done before sharing to ensure the communication is concealed. Here, information exchange is done from the initial to the neighboring vehicle and examines the volatile authentication. The information is attached with the volatile authentication and provides the complex conversion of information. Here, the identification of information is derived by determining the request and response based on the mapping factor. The recommendation system is generated for reliable information sharing with the neighboring vehicles. Finally, the communication in a heterogeneous platform is used to estimate the authentication and authorization that addresses the intercepts. The authentication for the reliable processing is denoted as\(\:\:T\), the information exchange is done reliably, and it is termed as\(\:{\:c}_{h}\), the recommendation is carried out for reliable communication, and it is represented as\(\:{\:e}_{d}\). The request and response are handled for the authentication process, and it is formulated as\(\:\:\left({x}^{{\prime\:}}+\frac{{q}^{{\prime\:}}}{T+{l}^{{\prime\:}}}\right)\). The communication analysis is used to share the information with the neighboring vehicles, and the identification is carried out for the complex vehicle communication, which is termed as\(\:\:I\). The information sharing is evaluated for the identification of identical sharing. This adverse and unauthorized vehicle is examined in the section below as follows.
Adverse vehicle identification
The adverse and unauthorized vehicle is identified by matching the information from the previous history. Through this processing, the adverse is detected and the unauthorized vehicle is prevented from sharing information between the vehicles/ infrastructures. Here, the recommendation system is developed along with the mapping factor. The examination is carried out by utilizing the volatile information for\(\:\:{h}_{n}\) to decide on further information sharing. The authentication and authorization are evaluated for the security maintenance of the heterogeneous communication for the vehicle. The following equation is used to detect the adverse (breach) and unauthorized vehicle.
In the above Eq. (3), the existing information maps the pursuing data and provides a reliable result. The vehicle that forwards the essential information to the neighboring vehicle on AVs is used to evaluate the identification and validation. The neighboring vehicle is used to examine the volatile information that performs authentication. The authentication and authorization are maintained for the vehicles, and the evaluation of the recommendation process. The recommendation is provided along with the mapping factor to balance the security of the information exchange. The information is exchanged and completes the communication in the heterogeneous platform, and the validation is performed.
The examination \(\:E\:\)is done by mapping with the previous state and avoids further sharing that leads to information loss. Here, the examination is used to ensure end-to-end communication for the information relaying and multiple recommendation processes. In this process, vehicle communication is used to identify the volatile authentication for the end-to-end computation. The information exchange is done for the recommendation system, and it is computed as\(\:\:\left(\raisebox{1ex}{${e}_{d}$}\!\left/\:\!\raisebox{-1ex}{$\frac{{h}_{n}}{{c}_{h}}$}\right.\right)\). Here, authentication and identification of an adverse and unauthorized vehicle are detected in AV navigation to avoid information failure. The information sharing between the adverse vehicles is computed in the equation below.
The information sharing is derived from the above equation, which requires the active\(\:\:{h}_{n}\) to perform the communication securely. Here, the recommendation is given for the analysis of vehicles for heterogeneous communication. The volatile authentication is used to address the intercepts and adversarial threats in the network. Here, security is maintained for better communication for the vehicles, indicating authentication and authorization. This sharing is performed for the neighboring vehicle and resolves the conflicts and adversities in the network. Finally, authentication is used to derive the encrypted data and deploy the heterogeneous vehicles’ communication.
In this category, security validation is performed, and the examination for the sharing is computed as\(\:\:\left[E+\left(\raisebox{1ex}{${m}_{0}$}\!\left/\:\!\raisebox{-1ex}{$x{\prime\:}$}\right.\right)\right]\). The request and response are handled from the initial vehicle to the neighboring vehicle to ensure security, and it is represented as\(\:{\:u}_{r}\). The relaying information is forwarded to the appropriate vehicle in an end-to-end computation. In this, converting the vehicle communication stream to an encrypted stream is complex. This issue is addressed by introducing recurrent learning, which prevents security breaches in AV.
Qubit-based computation and recurrent learning
The proposed Secure Module employs a recurrent learning process that involves training qubits to assess and confirm the exchange of information between autonomous vehicles. By utilizing the previous information state, it enhances authentication and decision-making for future processes. The learning model sets up qubits for each vehicle and checks the conditions for information exchange. If these conditions are met, the existing qubit is reused, ensuring efficient mapping without extra computation. In the event of a detected breach, the current qubit is stopped, and a new state is assigned. The learning network is designed to manage qubit replacement and pending generation at various intervals. This approach facilitates ongoing validation and updating of the authentication sequence, thereby reducing complexity and enhancing security in vehicle-to-vehicle communication. The proposed module utilizes qubits as carriers of information. These qubits are allocated to various data or information produced during communication periods and form the foundation for simple computations in security and communication tasks. In this scenario, the quantum model pertains to employing quantum computing principles, especially qubit-based calculations, to boost security and effectiveness in communications among autonomous vehicles (AVs). Although the quantum-based concealed medium is not explicitly defined, it can be understood as the secure communication channel established by exploiting the quantum characteristics of qubits for information transfer. This method enables the discreet exchange of information between vehicles, with qubit states being employed to verify authentications and identify breaches within the AV network. The qubits are assigned to the different data/information generated at any communication interval. This is represented as\(\:\:{g}^{{\prime\:}}\) that satisfies the requirements through\(\:\:{n}_{f}\) based distribution. The qubits and learning concepts are assimilated as a single entity for validation. The learning is trained using these qubits for analyzing\(\:\:{d}^{{\prime\:}}\) considering its previous state (history). The mapping factor introduced estimates the maximum relationship between the authentication validation and maximum sharing. In the authentication validation, its completeness in\(\:\:{m}^{{\prime\:}}\:\forall\:\:{m}_{o}\) is expected as\(\:\:\frac{{p}_{s}}{{q}^{{\prime\:}}}=1\) (maximum) and qubits availability (active) until\(\:\:T\in\:{n}_{f}\). This mapping factor is reliable to maximize the decision on state change or to modify the state changes across various\(\:\:{h}_{o}\in\:{h}_{n}\) communications. Recurrent learning is used to train the information from the AV and to ensure decentralized and low-complexity sharing between the vehicles. The information is distributed to the identical vehicle that carries the request by mapping with the previous history of qubits. The scope of this recurrent learning is used to train the qubits and improve the information sharing without failure. If the vehicle requests the information in a heterogeneous platform, the qubit history is verified, and sharing is pursued. In this aspect, the training qubits are used for learning and mapping the consistency between validation (complete) and sharing. This is used to update the state of the qubits, wherein the changes are used to identify the breaches. The following equation is used to define the qubits training for the secure validations.
The qubits are trained as defined above in Eq. (5); in this, information analysis is done to verify their state to authenticate or validate the sharing. The decision outcome results in the secure sharing of information to the requested vehicle in the response. Here, the existing qubits are used to retrieve the related information and forward it to the appropriate vehicle. The authenticated qubit representing information secures the sharing from breaches and is denoted as\(\:\:r{\prime\:}\). The qubits are trained in this recurrent learning to provide reliable communication between the heterogeneous vehicle, and it is represented as\(\:{\:i}_{0}\).
In this evaluation step, identical information is retrieved and shared using active qubits. The volatile authentication information is extracted and forwarded to the appropriate vehicle. The response is optimal for extracting similar information from the pursuing vehicle. Thus, the qubit is trained concerning the breach data handled in the previous state, if any. This improves the upcoming processing by distributing the information to the secure vehicle, referred to as\(\:\:g{\prime\:}\). This information is trained using active qubits, and the mapping is evaluated for the identical distribution as
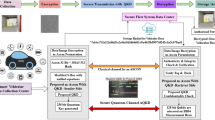
This equation establishes a method for mapping qubits to ensure the consistent distribution of secure information across the network. The qubit mapping is performed from the previous and the following states to decide on sharing or validation. The data is shared with identical qubit mapping to validate the current distribution for selective (request-demanding) vehicles. The distribution is continued for the remaining requests, and response satisfaction is achieved by the qubit validation and mapping. Here, mapping determines the consolidation of complete authentication and successful communication (without failure), providing a state\(\:\:{d}^{{\prime\:}}=1\). The verification consolidated information is shared with the appropriate vehicle by the identification process, represented as\(\:\:\left(\frac{\prod\:_{{n}_{f}}\left(I+{m}_{0}\right)}{{d}^{{\prime\:}}-{u}^{{\prime\:}}}\right)\). In this process, the training qubits are used to extract the related information from the\(\:\:{d}^{{\prime\:}}\) and\(\:\:{i}_{0}\left({n}_{f}\right)\) recurrently. The recurrent learning process is depicted in Fig. 2 for the end-to-end validation process.
The learning model for security validation is represented in Fig. 2 above. The process starts with the initialization between two states, S(t) and S(t + 1), which operate independently for each vehicle. The diagram then follows a sequence of conditional evaluations and actions. If specific conditions are fulfilled, the process either maintains the current state, continues using the existing qubit (Q(t)), or identifies a security breach. Upon detecting a breach, the current qubit is stopped, and a new state S(t + 1) is established. If the initial conditions are unmet, the process involves substituting qubits and generating pending operations to proceed through various intervals. The learning network is trained under these circumstances to manage security and ensure dependable communication in autonomous vehicle settings. This learning performs an initialization between\(\:\:{q}_{n}^{{\prime\:}}\) and\(\:\:{r}_{n}^{{\prime\:}}\) that is independent for each vehicle. The information sharing is relevant based on\(\:\:{g}^{{\prime\:}}={i}_{o}\) satisfying condition. If this is true, then\(\:\:{T}_{n}\:\forall\:\:{I}_{n}\) is the consecutive verification\(\:\:C\left(E\right)={n}_{f}\:\forall\:\:{r}_{n}^{{\prime\:}}\) is the state retention (i.e.)\(\:\:{d}^{{\prime\:}}=1\) condition. If the above two conditions are satisfied, then, \(\:{r}_{n}^{{\prime\:}}\) is reused, ensuring the mapping is high with no additional computation. The failure in the second condition results in a breach (i.e.)\(\:\:{h}_{o}\in\:{h}_{n}\) detection. If this is true,\(\:\:{I}_{n}\) is halted\(\:\:\forall\:\:{m}^{{\prime\:}}\) and\(\:\:{d}^{{\prime\:}}=0\) is the current state. The first condition failure results in the replacement of the qubits, as their task of consolidated mapping is incomplete. Therefore, the authentication associated with the data is revoked until a new \(\:{r}_{n}^{{\prime\:}}\) is assigned. The learning network is trained under replacement\(\:\:{r}_{n}\) and pending \(\:{q}_{n}^{{\prime\:}}\) generation to continue\(\:\:{n}_{f}\) across various\(\:\:{l}^{{\prime\:}}\) to administer\(\:\:L\). The response is forwarded to the appropriate vehicle by examining the mapped qubit-associated information for the active requests. In this step, the distribution is verified by\(\:\:{d}^{{\prime\:}}\) throughout\(\:\:T\),\(\:\:{m}_{0}\). and\(\:\:E\). The following qubit in this recurrent learning indicates the request from the vehicle, and it is termed as\(\:\:u{\prime\:}\). The active qubit is used to determine the information handled by the vehicle, and here, training is used for security improvement, referred to as\(\:{\:d}_{s}\). The mapping is done concerning the previous and pursuing qubit states for this validation. The qubit mapping is repeated for the vehicle information requests, and it is represented as\(\:\:C\). In this mapping process, detection is also feasible in any recurrent learning iteration. This is used to secure the information and reduce communication failure, and it is equated in Eq. (7).
The decision for concealed sharing is verified based on the above equation to ensure the information sharing and post-to-state changes in vehicle communication. In a concealed sharing process, vehicle authentication is recommended for secure data sharing to restrict maximum state changes due to breaches. The volatile authentication is introduced to address the intercepted and adverse. Here, communication is established to avoid security breaches in the network and ensure mapped validations in the qubit training phases.
The decision post to the mapping process from the information sharing state history is used to complete the validations. In this validation step, the mapping with authentication is carried out, and the information is shared with the appropriate vehicle. Here, the relaying and the recommendation are used to enhance the security. The decision in this recurrent learning is used to define the sharing using training data, and it is denoted as\(\:\:O\). The request and response for the vehicle are used to define the authentication for the complex information. Finally, the computation is completed for secure sharing in the end-to-end process. Thus, the decision is made for the vehicles, and from this recommendation, a design is developed. It is used for the information relaying points performed by the recurrent learning; the following equation is used for the recommendation process.
The recommendation is carried out for the vehicles and administers the authentication by exchanging reliable information. The security level is maintained by detecting and intercepting in the network. The security is balanced for reliable communication between the vehicles, and it evaluates the volatile information exchange. The validation is performed to identify secure information and share it with the neighboring vehicle. Recurrent learning is used to decide the upcoming information in the network and determine an end-to-end computation. Here, the analysis is carried out for reliable sharing between the vehicles. Secure sharing is pursued by identifying the better recommendation and deploying the mapping factor.
The mapping factor is used to determine the better decision for\(\:\:{h}_{n}\) and continue the vehicles’ information sharing. The relaying and multiple recommendations are done, and the matching is done with the previous history. The secure sharing is forwarded to the security vehicle, which performs the matching on time, and it is represented as\(\:\:{x}^{{\prime\:}}\left({u}_{r}+\left({m}_{0}-{m}^{{\prime\:}}\right)\right)\). The training data is used to evaluate the identical data matching. Multiple recommendations are made by deriving volatile authentication to resolve the adverse and intercepts. The mapping factor is used to define the consolidation of authentication completeness and failure-free information sharing. The mapping factor is defined in the equation below (9).
The mapping factor is defined in the above equation and is used for the authentication of\(\:\:{h}_{n}\). The communication is carried out for the relaying vehicles, and it is represented as\(\:\:y{\prime\:}\). The matching is done with the previous state and provides a result that indicates the recommendation. The security is carried out, following the conversion of the complex information to an encrypted stream, and evaluates the request and response, and it is formulated as\(\:\:\left(\frac{\raisebox{1ex}{$r{\prime\:}\left({n}_{f}\right)$}\!\left/\:\!\raisebox{-1ex}{$q{\prime\:}$}\right.}{{x}^{{\prime\:}}+y{\prime\:}}\right)\). The existing information is used to decide the upcoming information and evaluate the sharing to perform the communication. The mapping process for qubit validation is depicted in Fig. 3.
The qubit validation mapping process describes two scenarios based on the mapping factor. When the factor = 1, the graph shows a consolidation of authentication completeness and response sharing, indicating high authentication success and effective information sharing. Conversely, when the factor < 1, there is no consolidation between these elements, suggesting incomplete authentication or less effective information sharing. This visual representation helps illustrate the impact of the mapping factor on authentication and communication processes within the proposed secure module for concealed navigation communication (SM-CNC) in autonomous systems. The mapping is performed to differentiate communication failure and high response categories. The authentication, interval, and response between two/more\(\:\:{h}_{o}\) in\(\:\:{h}_{n}\) follows the mapping factor verification. The\(\:\:S\left(O\right)\) (or)\(\:\:\frac{{p}_{s}}{q}\) (or) both have to be consolidated for a minimum\(\:\:{e}_{d}\:\forall\:\) communication. There are two cases of\(\:\:{e}_{d}\) as presented in the above Fig. 3. The first case is the\(\:\:S\left({S}_{a}\right)=1\) and the second is\(\:\:S\left({S}_{a}\right)=0\) where consolidation and no-consolidation of authentication completeness and response sharing are satisfied. For the satisfied\(\:\:{m}^{{\prime\:}}\) intervals, the\(\:\:{y}^{{\prime\:}}\) is monotonous using\(\:\:{r}_{n}\) such that the reuse is defined as\(\:\:\left({g}^{{\prime\:}}+{I}_{n}\right)\) for the consecutive interval. In this case, a final validation of\(\:\:S\left({S}_{a}\right)\) is updated for the next interval using the same\(\:\:{r}_{n}\). Therefore, the successful update for the new\(\:\:{e}_{d}\) is the key to optimal information sharing and\(\:\:{q}_{s}\) achievement.
Volatile authentication
The volatile authentication follows a two-way key-based security for ensuring maximum data integrity. This authentication is short-lived based on the communication interval and neighbors, after which the key and authentication are modified. Replicated authentication sequences or keys are not used in this model to prevent breach guessing. A notable feature of this authentication is the revocation of the active security if\(\:\:S\left({S}_{a}\right)=0\) (or)\(\:\:S\left({S}_{a}\right)<1\) to ensure computations are less. The identification of information is utilized in this authentication performed for the vehicle-to-vehicle communication for navigation. The reliable communication is carried out by performing matching, which is examined by the training data. Recurrent learning performs the mapping decisions using qubit validations with volatile authentication. Here, the complex information is derived from identifying the qubits between the communication vehicles. The recommendation is provided for information-sharing processes using high mapping factor-based authentication. Here, the distribution is carried out for identical information. The mapping factor is used to modify the previous decisions and security based on the state, and it is denoted as\(\:{\:s}_{a}\). If a state change occurs from\(\:\:{d}^{{\prime\:}}=1\) to\(\:\:{d}^{{\prime\:}}=0,\) then authentication failure is true and the validation is incomplete. The equation below is used to define the authentication and its variants for success and failure.
The examination of authentication failure is used to analyze the vehicle communications and provide secure sharing. Recurrent learning is used to train the previous state of information and improve authentication. The authentication and authorization of the vehicle are used to evaluate a better recommendation for the relaying. The recommendation is performed for the active requests from the vehicle and determines the mapping factor. The security level is maintained for the vehicle and evaluates the sharing with the authenticated vehicle. The identification information is shared with the neighboring vehicles, and it is represented as\(\:\:\left(I+\frac{{x}^{{\prime\:}}}{{h}_{n}}\right)\).
The authentication is improved by deriving the above Eq. (10); here, the relaying is used to perform the heterogeneous communication, denoted as\(\:\:T\). The complex conversion is addressed in this authentication process and deploys the matching with the history of processing. In this analysis, the decision is finalized after the training phase, and it detects the information request from the vehicles. The sharing of appropriate information with the vehicle is used to examine reliable communication, and it is denoted as\(\:{\:b}_{e}\). Thus, volatile authentication is attached to disintegrate if authentication and neighbor interception appear in the network. The identification of a secure neighbor is evaluated in the equation below.
The secure neighbor is identified to share the information without any failure or interception. The authentication and authorization are used to determine the validation process that is performed on end-to-end vehicles. Here, the recommendation is made to improve the computation time and information sharing. The appropriate information is shared with the secure vehicle, and by examining this information, the security breach is detected. This provides multiple recommendations at the time of initial registration. This mapping factor is used to validate the heterogeneous communication for the secure information exchange. Here, the identical distribution of information is forwarded to the neighboring vehicles. The neighboring vehicle security is detected by evaluating the state decision and training qubits in active learning. The detection of security breaches is evaluated in the equation below.
The security breaches are detected to avoid interception and failure; the information is shared with the requested vehicle on time during this processing. The mapping factor is generated for the vehicle, and after this processing, mapping is done with the previous history of data. The volatile authentication is attached for the security breach detection in AV platoons, and it is formulated as\(\:\:\prod\:{l}^{{\prime\:}}\left(T\right)+\left[{x}^{{\prime\:}}\text{*}\left(O+{i}_{0}\right)\right]-m{\prime\:}\). The evaluation is carried out promptly, and mapping consolidation is verified for secure information exchange. The authentication process sequence is diagrammatically presented in Fig. 4.
Initially, the sharing request is fulfilled by thoroughly validating the verification. Depending on the results, the key usage and deployment proceed. If the same key is employed for deployment and information sharing, the process continues. The figure indicates that a true validation case for the vehicle across all intervals ensures maximum sharing. However, any disruption in the sharing prevents the authentication sequence, leading to a false outcome for the subsequent sequence. The diagram also illustrates that significant modifications in any interval necessitate multiple key generations, which aids in preventing breaches. Furthermore, it shows that computations are not carried forward in an interrupted sequence where validation is unnecessary, thereby reducing complexity. The volatile authentication between two vehicles is sequentially represented in Fig. 4. The sharing request is satisfied by providing maximum validation of\(\:\:S\left(O\right)\) and\(\:\:S\left({S}_{a}\right)\) for\(\:\:\left\{E\left(T\right),{b}_{e},\:\text{a}\text{n}\text{d}\:{n}_{f}\right\}\) verification. Based on the\(\:\:{C}_{h}\:\forall\:\:T\), the key usage, and deployment are continuous. If the same\(\:\:{r}_{n}\) is used for deployment and information sharing, the\(\:\:I\left({h}^{{\prime\:}}\right)\) is pursued. Therefore, the true case of\(\:\:E\left(T\right)\) for all\(\:\:S\left({S}_{a}\right)=1\) is the validation case to ensure maximum sharing. The interruption in\(\:\:S\left({S}_{a}\right)\) and\(\:\:E\left(T\right)\:\forall\:\:{m}^{{\prime\:}}\) defaces the authentication sequence such that\(\:\:{r}_{n}\:\forall\:\:{x}^{{\prime\:}}\) is\(\:\:{e}_{d}\) for the consecutive sequence. The maximum modification in any interval updates the need for multiple\(\:\:{r}_{n}\) generation, preventing breaches. Besides, the computations are not carried forward in an interrupted\(\:\:{m}^{{\prime\:}}\) for which validation is not required, reducing the complexity. The relaying and multiple recommendations are made to convert the vehicle communication to an encrypted stream. In AV platoons, authentication and authorization are improved, and security breaches and intercepts are reduced. Here, detection is carried out for the \(\:l{\prime\:}\left(T\right)\) and ensures the neighbor security for the sharing, and it is termed as\(\:\:K\); in this equation, the misdetection ratio is decreased. Furthermore, the authentication is improved by updating the sequence for active qubits using the following Eq. (13).
The authentication is enhanced for the active\(\:\:{h}_{0}\in\:{h}_{n}\) and evaluates the better recommendation and adverse detection in the network. The detection is carried out for the relaying and multiple recommendations to ensure secure information exchange. Here, the mapping factor is dynamically modified for communication by distributing identical qubit-related information to the neighboring vehicles. Recurrent learning and secure information exchange are used to mitigate adversaries to ensure secure navigation. Here, the concealed sharing in\(\:\:{m}_{0}\) is used to finalize the state and qubits mapping for further\(\:\:{n}_{f}\). With this information, the communication failure is decreased, ensuring secure AV communication and navigation.
Hyperparameter study
In the hyperparameter study,\(\:\:S\left({S}_{a}\right)\) and\(\:\:K\) are the communication-impacting factors considered for analysis. The\(\:\:S\left({S}_{a}\right)\) for complete authentication and response, it has no additional computations. Similarly, the\(\:\:K\) detection increases the chances of successful communication with low failure rates. Therefore, the computation complexity and authentication types are detailed with graphical representations in this section. The complexity analysis is presented in Fig. 5, followed by the response analysis in Fig. 6.
The complexity analysis for the three variants\(\:\:S\left({S}_{a}\right),\:\:K,\) and\(\:\:{m}^{{\prime\:}}\) is presented in Fig. 5 above. The\(\:\:{n}_{f}\) ad\(\:\:{C}_{h}\) variants do not disclose the same outcomes as the qubits are different for\(\:\:\left({q}_{n}\to\:{r}_{n}\right)\) and\(\:\:S\left({S}_{a}\right)\) updated. If the recurrent learning process is based on\(\:\:{T}_{n}=0\), then complexity is saturated for\(\:\:K,\) whereas for the alternating update of\(\:\:{q}_{n}^{{\prime\:}}\), the\(\:\:S\left({S}_{a}\right)\) saturates the complexity for new updates based on\(\:\:{e}_{d}\). For the varying times of\(\:\:{m}^{{\prime\:}}\) the complexity varies based on\(\:\:{n}_{f}\) and\(\:\:{C}_{h}\). These two variants are decided by the\(\:\:K\) detected and\(\:\:S\left({S}_{a}\right)\) based on the qubits used. Therefore, the qubits’ usage in a monotonous manner confines the revocation without\(\:\:I\left({h}^{{\prime\:}}\right)\). This is further validated using\(\:\:E\left(T\right)\) and\(\:\:{i}_{o}\left({n}_{f}\right)\) to reduce the complexity. Besides, the computations are not complicated for the\(\:\:E\left(T\right)\) failed intervals, reducing the authentication need until a new\(\:\:{r}_{n}\) is generated. In Fig. 6, the response analysis for requests and authentication types is presented.
The authentication types considered in this analysis are complete and discontinued, referenced by\(\:\:T\) and\(\:\:I\) processes. The\(\:\:C\left(E\right)\) requires\(\:\:T\) more than\(\:\:I\) to retain high\(\:\:{p}_{s}\) such that the recurrent learning validates the chances of\(\:\:S\left(O\right)\) and \(\:\frac{{p}_{s}}{q}\) conditions. The target is the consolidation of the above to retain\(\:\:S\left({S}_{a}\right)\) at a high rate provided\(\:\:\left({g}^{{\prime\:}}={i}_{o}\right)\) is satisfied at any\(\:\:{m}^{{\prime\:}}\). The consecutive validation of\(\:\:C\left(E\right)={n}_{f}\:\forall\:\:{h}_{o}\in\:{h}_{n}\) improves the detection (breaches) to maximize the\(\:\:{T}_{n}\). For all the\(\:\:{T}_{n}\) activated, the qubits validation based on\(\:\:C\left(E\right)\) ensures flow loss communication reduces the failures. Therefore, the change in\(\:\:C\left(E\right)\) requires to update\(\:\:{d}^{{\prime\:}}\) and the consecutive sharing requires\(\:\:T\) over\(\:\:{q}^{{\prime\:}},\:C\left(E\right),\) and\(\:\:S\left({S}_{a}\right)\) is presented in the above Fig. 6 for the authentication variants\(\:\:T\) and\(\:\:I\).
Experimental setup
The experimental setup is described in this section using the network model illustrated in Fig. 7. The network model is implemented in VanSim to verify the proposed module’s efficiency. Following the network model, the experimental parameters are defined.
The network comprises 120 AVs, and the maximum information sharing distance is 200 m. The network contains vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communications at 200 m and 500 m coverage ranges. A highway road map covering 4 km with 11 intersections from the source42 is considered for this experimental setup. The communication is performed for 3 different applications, such as instant messaging, radio, and navigation. The number of requests handled by an AV from the neighbor and its infrastructure is 30/interval. This interval varies from 10s to 180s depending on the application demand43. The information sharing and adversary models are previously disclosed. The authentication follows a 256-bit DES encryption process in two ways between AVs44.
Comparative study
In the comparative study, the communication failure, computation complexity, authentication rate, sharing delay, and breach detection metrics are analyzed. These metrics are studied under two variants: number of AVs (10 to 120) and communication requests/ interval (2 to 30)45. The proposed module is compared with RL4V2X26, GSM30, PSLAP24, and IWOAFS-XAIAD27 methods discussed in the related works section.
Communication failure
Communication failure in AV networks indicates a breakdown in data transmission between neighboring vehicles and the control server that occurs due to data interception or packet loss during communication. A single communication breakdown can lead to incorrect navigation and create desynchronization between vehicles. In the proposed SM-CNC method, each communication channel is mapped with quantum-allocated qubits to verify the complex state of correlation. The learning-based selection of available qubits avoids compromised paths with fewer failures than existing methods. This \(\:E={\prod\:}_{{h}_{n}}^{S}\left({d}^{{\prime\:}}+{q}^{{\prime\:}}\right)\text{*}\left(\raisebox{1ex}{${e}_{d}$}\!\left/\:\!\raisebox{-1ex}{$\frac{{h}_{n}}{{c}_{h}}$}\right.\right)+\left({l}^{{\prime\:}}\text{*}I\right)+\sum\:\left({x}^{{\prime\:}}+{h}^{{\prime\:}}\right)-m{\prime\:}\) verifies the adversaries and unauthorized vehicles to eliminate them from the communication process. It is essential to maintain uninterrupted communication throughout the entire AV navigation process to minimize communication failures. This concealed communication, done by qubit validation, ensures that only authenticated and verified data packets are transmitted (Fig. 8).
Computation complexity
In AV environments, concealed communication prevents excessive computational overhead during data sharing within the communication sessions. Conventional encryption or authentication methods contain heavy processing layers, which lead to high computational complexity with minimal accuracy. The proposed SM-CNC method uses authentication based on quantum to verify qubit signatures to replace heavy cryptographic communication between vehicles. The computational complexity is minimized by \(\:S\left(O\right)=\left[\left({u}_{r}+{c}_{h}\right)\text{*}\left({m}_{0}+{h}_{n}\right)\right]+\left({n}_{f}\text{*}{x}^{{\prime\:}}\right)-m{\prime\:}\left(C\right)\) using recurrent learning to match the vehicle request during detection. Lower computation complexity results in faster data processing with better energy efficiency in vehicle fleets to communicate in a secure environment. It limits computation by selecting only valid and trust-labeled qubits for the secure session through adaptive quantum state analysis. This minimizes the need for continuous re-authentication that causes a computational burden on the heterogeneous vehicle (Fig. 9).
Authentication rate
Authentication rate measures how quickly the system verifies the identity and integrity of a message or communication source from the vehicle during its request. In the SM-CNC method, a high authentication rate is achieved by connecting each vehicle’s request to a specific quantum state management. The computation of \(\:{e}_{d}=\sum\:_{u{\prime\:}}{u}_{r}\text{*}{l}^{{\prime\:}}\left({n}_{f}\right)+\left(\frac{\raisebox{1ex}{$I\left({n}_{f}\right)$}\!\left/\:\!\raisebox{-1ex}{${p}_{s}$}\right.}{C}\right)\text{*}{x}^{{\prime\:}}\left({u}_{r}+\left({m}_{0}-{m}^{{\prime\:}}\right)\right)+L\) ensures that messages can only be authenticated if the state is untampered and derives the authentication by exchanging reliable information. The messages from verified sources prevent spoofing and man-in-the-middle attacks. A high authentication rate leads to secure decision-making and trusted communication in the fleet. The utilization of quantum entanglement verification allows paired qubit states to exchange data. This enables instant authentication based on the quantum correlation to confirm the integrity of communication between vehicles (Fig. 10).
Sharing delay
Sharing delay in AV monitors the time taken by the vehicle to transmit communication between fleet vehicles or with base stations. Some existing methods with encrypted models lead to higher buffering and delays during data transmission. The proposed SM-CNC method conceals information directly and exchanges it through verified quantum links with multi-phase authentication. The incorporation of qubits with pre-established identity reduces the communication delay within the system. The sharing of appropriate information about the vehicle is evaluated by \(\:{b}_{e}={u}_{r}\left({h}_{0}\right)+{x}^{{\prime\:}}\text{*}g\) prevents delays during communication within the vehicles. This helps the system minimize sharing delay without obstacles and synchronize the data among AVs. A minimal delay in sharing ensures that all vehicles in the fleet operate with up-to-date information to improve performance (Fig. 11).
Breach detection
The ability of the system to detect unauthorized access attempts or anomalous vehicle behavior in data sharing is defined as breach detection. The proposed SM-CNC method tracks the quantum state between vehicles without any deviation in expected qubit patterns that trigger breach alerts. Traditional methods often fail to detect all the breaches due to their poor security mechanism. The proposed system learns the expected behavior of qubit communication paths and uses quantum error detection patterns to detect abnormalities. The AV networks are vulnerable to attacks that aim to manipulate route instructions with poor fleet behavior. Early and precise detection of breaches as \(\:K=\left[\left({n}_{f}+{c}_{h}\right)\text{*}\left({g}^{{\prime\:}}+{e}_{d}\left(L\right)\right)\right]\text{*}\prod\:{l}^{{\prime\:}}\left(T\right)+\left[{x}^{{\prime\:}}\text{*}\left(O+{i}_{0}\right)\right]-m{\prime\:}\) maintain integrity in data transmission during communication. High breach detection accuracy improves threat mitigation without affecting the rest of the fleet and makes it harder for attackers to hack legitimate patterns (Fig. 12). The comparative study results are given in Tables 2 and 3 for the maximum AVs and the communication requests/ interval.
The proposed secure module improves the authentication rate and breach detection by 9.06% and 11.45% respectively. This module reduces the communication failure, computation complexity, and sharing delay by 11.68%, 11.94%, and 11.23% respectively.
The proposed secure module improves the authentication rate and breach detection by 9.29% and 11.71% respectively. This module reduces the communication failure, computation complexity, and sharing delay by 11.87%, 12.13%, and 11.49% respectively.
Conclusion
Recapitulation
This article introduced a novel concealed navigation communication module (SM-CNC) to ensure secure information sharing among AVs operating in platoons. The module integrates quantum computing and recurrent learning paradigms to perform low-complexity validation and authentication. In this approach, qubits serve as information carriers, and their state history is used to perform authentication completeness and verify response mapping over multiple sharing intervals. The mapping factor consolidates authentication results and communication responses to distinguish valid from incomplete or breached states. Recurrent learning updates qubit states dynamically, enhancing breach detection accuracy and minimizing redundant processing.
Experimental evaluation demonstrated that the proposed SM-CNC module improved breach detection by 11.45%, reduced computational complexity by 11.94%, and lowered sharing delay by 11.23%, compared to benchmark methods such as RL4V2X, GSM, PSLAP, and IWOAFS-XAIAD. These results validate the effectiveness of SM-CNC in managing secure, efficient communication across heterogeneous AV fleets.
Future work
While the SM-CNC module effectively addresses dynamic authentication and secure relaying in AV platoons, certain limitations remain. Notably, the system does not explicitly account for anomalous object data or navigation susceptibility, which may affect AV decision-making and pose privacy risks. Future research will focus on incorporating privacy-preserving mechanisms and access-gain control schemes using quantum-enhanced modeling to detect and manage such anomalies.
In addition, efforts will be directed toward expanding the functional scope of qubits beyond authentication, enabling them to support context-aware privacy enforcement and fine-grained access control. This will ensure robust defense mechanisms without increasing the system’s computational burden, maintaining the module’s core advantage of low complexity.
Data availability
All data generated or analyzed during this study are included in this published article.
References
Fan, Z. & Zhao, L. Autonomous integrity of multi-source information resilient fusion navigation system: state-of-the-art and open challenges. IEEE Transact. Instrument. Measur.. (2024).
Ali, A., Jianjun, H. & Jabbar, A. Recent advances in federated learning for connected autonomous vehicles: addressing privacy, performance, and scalability challenges. IEEE Access (2025).
Xu, C., Wang, Z., Li, Z. & Zhu, K. Secure observer-based collision-free control for autonomous vehicles under Non-Gaussian noises. IEEE Trans. Industr. Inf. 21, 2184–2193. https://doi.org/10.1109/TII.2024.3495763 (2025).
Nawaz, M. W., Zhang, W., Flynn, D., Zhang, L., Swash, R., Abbasi, Q. H.,Popoola,O. (2024). 6G edge-networks and multi-UAV knowledge fusion for urban autonomous vehicles.Phys. Commun. 67, 102479.
Balamurugan, G. et al. Improving the traffic prediction process efficiency using novel cohesive model. Comput. Electr. Eng. 123, 110082 (2025).
Kabir, M. M., Jim, J. R. & Istenes, Z. Terrain detection and segmentation for autonomous vehicle navigation: A state-of-the-art systematic review. Inform. Fusion. 113, 102644 (2025).
Chen, R. et al. Autonomous fleet management system in smart ports: practical design and analytical considerations. Multimodal Transp. 4 (3), 100211 (2025).
Park, S. H. et al. Identification of operational limitations of an autonomous vehicle based on dynamic simulation. J. Mech. Sci. Technol. 38 (12), 6519–6528 (2024).
Shankar, A. et al. A study on analyzing the security and privacy implications of existing and emerging sensors in autonomous electric vehicles. Tsinghua Sci. Technol. 30 (4), 1401–1420 (2025).
Ullah, N. et al. Solutions to cybersecurity challenges in secure vehicle-to-vehicle communications: A multivocal literature review. Inform. Softw. Technol. 107639. (2024).
Xu, D. et al. Post-quantum authentication against cyber-physical attacks in v2x-based autonomous vehicle platoon. IEEE Trans. Intell. Transp. Syst. 25 (6), 5034–5044 (2023).
Hardaway, K., Teran, O. & Cai, H. Silent emissions: the cyber-infrastructure environmental impacts of autonomous vehicles. Appl. Energy. 392, 125949 (2025).
Taghavifar, H., Hu, C., Wei, C., Mohammadzadeh, A. & Zhang, C. Behaviorally-aware Multi-Agent RL with dynamic optimization for autonomous driving. IEEE Trans. Autom. Sci. Eng. 22, 10672–10683. https://doi.org/10.1109/TASE.2025.3527327 (2025).
Cunha, L. et al. Security First, safety next: the Next-Generation embedded sensors for autonomous vehicles. Electronics 14 (11), 2172 (2025).
Zhao, F. et al. A blockchain-based efficient cross-domain authentication scheme for internet of vehicles. Comput. Mater. & Continua, 80(1). (2024).
Sadaf, M. et al. A novel framework for detection and prevention of denial of service attacks on autonomous vehicles using fuzzy logic. Veh. Commun. 46, 100741 (2024).
Sun, G., Xu, Z., Yu, H. & Chang, V. Dynamic network function provisioning to enable network in box for industrial applications. IEEE Trans. Industr. Inf. 17 (10), 7155–7164. https://doi.org/10.1109/TII.2020.3042872 (2021).
Sun, G., Zhang, Y., Yu, H., Du, X. & Guizani, M. Intersection Fog-Based distributed routing for V2V communication in urban vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 21 (6), 2409–2426. https://doi.org/10.1109/TITS.2019.2918255 (2020).
Luo, H., Sun, G., Chi, C., Yu, H. & Guizani, M. Convergence of symbiotic communications and blockchain for sustainable and trustworthy 6G wireless networks. IEEE Wirel. Commun. 32 (2), 18–25. https://doi.org/10.1109/MWC.001.2400245 (2025).
Yang, X., Zhuang, Y., Shi, M., Sun, X., Cao, X., Zhou, B. (2024). RatioVLP: Ambient light noise evaluation and suppression in the visible light positioning system. IEEE Transact. Mobile Comput. 23 (5), 5755–5769. https://doi.org/10.1109/TMC.2023.3312550.
Yang, X., Zhang, H., Zhuang, Y., Wang, Y., Shi, M.,Xu, Y. (2025). uLiDR: An inertial-assisted unmodulated visible light positioning system for smartphone-based pedestrian navigation.Inform. Fusion 113, 102579. https://doi.org/10.1016/j.inffus.2024.102579.
Zhang, Y., Hong, Y., Guizani, M., Wu, S., Zhang, P.,… Liu, R. (2024). A multi-layer information dissemination model and interference optimization strategy for communication networks in disaster areas. IEEE Transact. Vehicular Technol., 73 (1), 1239–1252. https://doi.org/10.1109/TVT.2023.3304707.
Xu, F., Yang, H. & Alouini, M. Energy Consumption Minimization for Data Collection From Wirelessly-Powered IoT Sensors: Session-Specific Optimal Design With DRL. IEEE Sens. J., 22(20), 19886–19896. doi: https://doi.org/10.1109/JSEN.2022.3205017 (2022).
Jin, S., Wang, X. & Meng, Q. Spatial memory-augmented visual navigation based on hierarchical deep reinforcement learning in unknown environments. Knowl. Based Syst. 285, 111358. https://doi.org/10.1016/j.knosys.2023.111358 (2024).
Zuo, C., Zhang, X., Zhao, G. & Yan, L. PCR: A parallel Convolution residual network for traffic flow prediction. IEEE Trans. Emerg. Top. Comput. Intell. 9 (4), 3072–3083. https://doi.org/10.1109/TETCI.2025.3525656 (2025).
Zhang, Y., Gang, Y., Wu, P., Fan, G., Xu, W., Ai, B., Wu, Q. (2025). Integrated sensing,communication, and computation in SAGIN: joint beamforming and resource allocation.IEEE Transact. Cognitive Commun. Netw.. https://doi.org/10.1109/TCCN.2025.3577377.
Zhu, B., Tang, R., Zhao, J., Zhang, P., Li, W., Cao, X.,… Li, S. (2025). Critical scenarios adversarial generation method for intelligent vehicles testing based on hierarchical reinforcement architecture. Accident Analysis & Prevention, 215, 108013. https://doi.org/10.1016/j.aap.2025.108013.
Chen, J., Ye, H., Ying, Z., Sun, Y. & Xu, W. Dynamic trend fusion module for traffic flow prediction. Appl. Soft Comput. 174, 112979. https://doi.org/10.1016/j.asoc.2025.112979 (2025).
Chen, J., Pan, S., Peng, W. & Xu, W. Bilinear Spatiotemporal fusion network: an efficient approach for traffic flow prediction. Neural Netw. 187, 107382. https://doi.org/10.1016/j.neunet.2025.107382 (2025).
Chen, J., Zhang, S. & Xu, W. Scalable prediction of heterogeneous traffic flow with enhanced non-periodic feature modeling. Expert Syst. Appl. 294, 128847. https://doi.org/10.1016/j.eswa.2025.128847 (2025).
Zhou, Z., Wang, Y., Zhou, G., Liu, X., Wu, M.,… Dai, K. (2024). Vehicle lateral dynamics-inspired hybrid model using neural network for parameter identification and error characterization.IEEE Transact. Vehicular Technol., 73 (11), 16173–16186. https://doi.org/10.1109/TVT.2024.3416317.
Zhou, Z., Wang, Y., Liu, R., Wei, C., Du, H. Yin, C. (2022). Short-term lateral behavior reasoning for target vehicles considering driver preview characteristic.IEEE Transact. Intell. Transport. Syst., 23 (8), 11801–11810. https://doi.org/10.1109/TITS.2021.3107310
Liu, X., Wang, Y., Zhou, Z., Nam, K., Wei, C.,… Yin, C. (2021). Trajectory prediction of preceding target vehicles based on lane crossing and final points generation model considering driving styles. IEEE Transact. Vehicular Technol. 70 (9), 8720–8730. https://doi.org/10.1109/TVT.2021.3098429.
Gao, M., Xu, G., Song, Z., Zhang, Q. & Zhang, W. Performance analysis of LEO Satellite-assisted deep space communication systems. IEEE Trans. Aerosp. Electron. Syst. 1–19. https://doi.org/10.1109/TAES.2025.3573275 (2025).
Wang, F., Zhang, S., Hong, E. & Quek, T. Q. S. Constellation as a service: tailored connectivity management in Direct-Satellite-to-Device networks. IEEE Commun. Mag. 1–7. https://doi.org/10.1109/MCOM.001.2500138 (2025).
Gao, N., Liu, Y., Zhang, Q., Li, X. & Jin, S. Let RFF do the talking: large Language model enabled lightweight RFFI for 6G edge intelligence. Sci. China Inform. Sci. 68 (7), 170308. https://doi.org/10.1007/s11432-024-4463-0 (2025).
Chen, Y., Liang, X., Zhou, H., Yang, X., Wu, L., Lv, G. (2025). GENDN: A geospatially enhanced NDN framework for location-related Pub/Sub services in NTN-enabled IoT. IEEE Internet Things J. 12 (7), https://doi.org/10.1109/JIOT.2024.35075338381–8393.
Gao, H., Xin, R., Chen, P., Li, X., Lu, N. You, P. (2025). Memory-augment graph transformer based unsupervised detection model for identifying performance anomalies in highly-dynamic cloud environments. J. Cloud Comput. 14, 40https://doi.org/10.1186/s13677-025-00766-5.
Balamurali, S. et al. Redefining IoT networks for improving energy and memory efficiency through compressive sensing paradigm. Sci. Rep. 15, 27180. https://doi.org/10.1038/s41598-025-12278-y (2025).
Cui, J., Shen, Y., Zhong, H., Zhang, J. & Liu, L. A multilevel electronic control unit re-encryption scheme for autonomous vehicles. IEEE Trans. Intell. Transp. Syst. 25 (1), 104–119 (2023).
Karabulut-Kurt, G., Nari-Baykal, K. & Ozdemir, E. Privacy-preserving authentication scheme for connected autonomous vehicles. IEEE Trans. Intell. Transp. Syst. 25 (6), 4998–5010 (2023).
Plosz, S. et al. A Methodology for the design of safety-compliant and secure communication of autonomous vehicles.
Ali, H. et al. Navigating the challenges and opportunities of Securing internet of autonomous vehicles with lightweight authentication. IEEE Access (2025).
S, B. & Palanisamy, M. K. A novel Hadamard matrix based hybrid compressive sensing technique for enhancing energy efficiency and network longevity. Sci. Rep. 15, 5937. https://doi.org/10.1038/s41598-025-88712-y (2025).
Xue, X. et al. A hybrid cross layer with Harris-Hawk-Optimization-Based efficient routing for wireless sensor networks. Symmetry 15, 438. https://doi.org/10.3390/sym15020438 (2023).
Acknowledgements
Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2025R97), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Funding
This research was supported by Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2025R97), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Author information
Authors and Affiliations
Contributions
Venkatesh T: Writing – original draft, Visualization, Project administration, SatheeshKumar Palanisamy-Conceptualization, Formal analysis, Writing – original draft, N. Sathishkumar:-Conceptualization, Writing – original draft, Maha Abdelhaq: Visualization, Project administration.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
T, V., Palanisamy, S., Abdelhaq, M. et al. 6G -enabled qubit-based concealed communication with AI-driven breach detection in autonomous fleets. Sci Rep 15, 43194 (2025). https://doi.org/10.1038/s41598-025-26667-w
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-26667-w