Abstract
Image steganography is the process of hiding information, which can be text, image, or video inside a cover image. Recent steganography literature hasn’t addressed the problem of loss of secret information during extraction and reliability. Hence, to reduce information loss and provide reliability between in the basic criteria, Herein, we proposed a hybrid method that utilizes the least significant bit (LSB) substitution, transppsition, magic matrix, key and Advance Encrytion Standard (AES) algorithm. The LSB method decreases embedding errors by implementing a new value difference algorithm. In addition, to improves the reliability between the basic criterion for image steganography we used transposition, magic matrix, key and AES. The proposed method ensures a high-quality image format in the RGB color model to conceal the hidden message within the cover image which is jpeg. The proposed hybrid method performed several experiments and these are mainly based on quality assessment metrics such as PSNR, SSIM, RMSE, NCC, etc. which showed better results. The proposed method also analyzed with different perspectives in terms of different dimensions of images and different sizes of message text which showed better results. In addition, the performance of the proposed method showed better results based on (regular and singular) steganalysis, noise, and cropping attacks. The security analyses such as key space, differential, and statistical attacks show that the proposed scheme is secure and robust against channel noise and JPEG compression.
Similar content being viewed by others
Introduction
With the rapid growth in modern technology, millions or even billions of data are transferred over the internet within seconds. From this aspect, ensuring data protection from unauthorized access becomes a crucial issue. Different techniques are used to tackle these issues, and each has their own pros and cons but Steganography plays a vital role in secure communication, which means “secret writing” or “covered writing”. It is the art and modern science of hiding sensitive information from unauthorized and third parties that no naked eye can detect. The steganography seeks to conceal data that no naked eye can suspect, the information that needs to be kept hidden is embedded in a carrier, such as an image, audio file, video, or text, to establish covert communication. Both cryptography and steganography terms are closely related, but they serve different purposes. During the literature review, we found that cryptography, watermarking, and steganography techniques are used to secure data transmission. However, the balance between the basic criteria used for image steganography is essential. Up to now many methods developed to tackle secure communication between end users. So, some are try to cover security and some struggle to get capacity or another criteria, but for image steganography it is essential to developed a reliable method in term of basic criteria which are robustness, captaincy, temper protection, transparency etc.1.So, image steganography play a vital role and we proposed hybrid method that give the reliability between the criterion of steganography. In addition, also used Cryptography which shuffles messages to prevent deciphering, while steganography conceals the communication so that it remains undetected2,3,4,5,6. Before going to further discussion let explain some existing concepts which vital for the proposed method that make clear statement. So, in the spatial domain, the researcher’s primary focus is to cover the image. This cannot have detected by the naked eye even if information is embedded in the image. In the spatial domain, bits from the original image’s pixels are dispersed. The LSB (least significant bit) is one of the popular strategies used in the spatial domain7. This technique involves embedding a hidden message by manipulating the least significant bit (LSB) of each pixel in the cover image. Each pixel has 8 bits and is assigned a binary value10. The most significant bit (MSB) determines the shape of the object in the image. If the MSB is altered significantly, the resulting image will differ greatly from the original. The LSB modification does not alter the shape of the object in a notable way up to 4 LSB8. Recently, the data transmission on the internet is a challenging task for both the sender and the receiver. Therefore, in steganography, the calculation of the image is very important for embedding a secret message into the image to meet the criteria of steganography. Because the resulting image must resist different attacks. However, reliability in Image steganography, the format of the image, and the dimension of the image remain a challenging task. Because the complexity of the Image (different dimensions, formats, etc.) can’t give us a way to make the reliability in information security. That’s why the proposed method used AES, key, magic matric, LSB, and some transposition comments are used to address secure communication issues up to some acceptable limits. However, several methods such as adaptive are10, modified lsb modification technique11, hybrid is method12, hybrid using lsb13, text security14, chaos-based cryptography17, Ransomware Hiding Model25, Hybrid data security26, and Hybrid EMI Edge29 proposed but have differernt issues; for instance; balanced and tradeoffs, etc. These techniques are superior to LSB but do not satisfy the essential measures of steganography; limit/payload, robustness, perceptional frankness, temper insurance, calculation, etc. In addition, these techniques have high payloads and separate different models and some have accomplished two boundaries but not get the others. Our research aims to develop and design a very effective and efficient data hiding method using the steganography technique with encryption algorithms to ensure confidentiality and integrity and to increase the security of the stego image by a method that does not show any difference in the image using visual attack tools. Also, the proposed method is designed to generate a stego image with the lowest quality changes to avoid any visual attacks that can lead to a hidden message. The proposed method also has an encryption solution using AES to the hidden message to protect the content of the secret message. This research mainly addresses the problem of detecting an attacker’s alteration of a concealed confidential message. It also addresses the issue of improving the unauthorized individual’s steganography of a personal protection technique by attaching an unauthorized individual to verify integrity. Our proposed steganography method fulfills the need for security and covers these issues by combining AES, Magic matrix, transposition, MLEA, and LSB. Its purpose is to defeat steganography as well as to assess and enhance the security of steganographic systems using some concepts such as MLEA, AES cryptography, MM, Different perspectives, and steganalysis, etc.11.
The key contributions of our research are given below.
-
This research proposes a method that combines steganography and encryption algorithms to ensure the confidentiality and integrity of the transmitted data. It works systematically by enabling the embedding procedure to enhance the security level.
-
We propose an improved hybrid image steganography method using the AES algorithm supporting different operations such as magic matrix, and transposition for securing data or information.
-
To ensure the security and quality of the stego image, we combined AES encrypts for sensitive data, and XOR operation before embedding the carrier image pixels.
-
To show the efficiency of the proposed method, we compared our method with some of the state-of-the-art methods and also analyzed different perspectives in terms of different dimensions of RGB images, different sizes of secret messages, etc.
-
We performed critical analysis using QAM’and RS, Histogram, and PDH of the proposed method which indicates better results.
The paper is organized into several sections. Section “Literature review” provides an overview and critical analysis of related works. Section “Proposed methodology” presents the proposed work, which includes the use of the LSB, AES algorithm, Magic Matrix, Embedding Algorithm, and Extraction Algorithm. Experimental results and image quality assessment measurements are presented in Section “Simulation results and discussion”, while Section “Discussion” analyzes security performance. Finally, Section “Conclusions” concludes the paper conclusion and future work.
Literature review
Due to the rapid use and researcher attention, people used image Steganographic techniques to hide messages for secure communication. For instance, in ancient Greece, messengers used to tattoo messages into their shaved heads and let their hair grow out to cover them. Similarly, during World War II, invisible ink was used to write information on seemingly blank paper. The paper had to be heated to reveal the message, and the ink would turn visible. Fruit juices, milk, and vinegar were used to make the ink, as they all turned dark when heated, making the message visible to the human eye12. Recently, different cover objects have been used to embed secret messages, such as images, audio, video, etc. Still, the concept and uses of digital images and their formats, types, and channels get attention for steganography. Because RGB images can be stored with 24 depth per pixel of 8 bits for each RGB color channel. A 24-bit image provides more space for hiding information using the least significant bit (LSB) shown in Fig. 1. So, LSB steganography is a type of image steganography that involves concealing messages inside an image by replacing the message’s secret bits with the LSB of each pixel shown in Fig. 1.
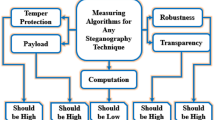
However, LSB steganography is the most common technique for hiding data by converting the message’s values to decimal and then binary using the ASCII table. Once the pixel values are converted to binary, we replace every least significant bit in a sequence with the message bits13. We just used the reverse operation to extract the secret message. However, the LSB encoding is highly vulnerable to filtration or alteration of the stego image, one of its major drawbacks14,15,16. Any attack on the stego-image is likely to destroy the message. That’s why we used the AES algorithm to tackle this issue. Before analyzing previous work, it is necessary to elaborate on some basic parameters used for any steganographic method. When developing any steganography method, it is important to consider objectives such as security, payload, robustness, imperceptibility, tamper protection, calculation complexity, and perceptual transparency. So, Payload refers to the concealed capacity of the hidden message inside the image, which is calculated in bits per pixel (bpp)17,18,19,20. It is important to ensure that the stego and cover images match transparency or visual quality, with no distortion or noise allowed. Perception requires identical cover and stego images, with no visible differences to the naked eye20,21. Considering these objectives is crucial to develop an effective and secure steganography method22,23. Temper Protection: It is difficult to modify the secret message in an implanted object after it has been protected. Calculation Complexity: How expensive is it computationally to embed & extract a covered message?24. Toughness: This describes the ability of the implanting and decrypting system to function, although the stego-image is deformed by a third party utilizing image processing techniques such as rotation, scaling, resizing, etc. Imperceptibility: Since concealing the hidden data in the digital image in a manner that retard it from being understood by the human eye is the primary characteristic and power of any Steganographic system or statistical algorithms, imperceptibility is the most top priority criterion for any data implanting25,26,27. Security: Security in a Steganographic system refers, in an oblique sense, to "un-noticeability" or "un-detectability “. As a result, any steganography method is considered safe if the concealed information cannot be found using statistical methods28,29,30,31. Below, Tables 1 and 2 below present a critical analysis of previous techniques developed for image steganography.
To sum up this section first we explored the basic idea of LSB, RGB, and its importance in this research field. After that, we elaborate on the basic criterion (payload, robustness, temper, computation, perception) of image steganography for reliability. These parameters are used in Tables 1 and 2 for critical analysis of some existing methods. Therefore, Tables 1 and 2 elaborate on the advantages and disadvantages of various image steganography techniques, including their uses, cover objects, and embedding procedures, and also analyze the basic criteria of steganography achieved. The key issue in image steganography is that the cover object is visible for some time, making it crucial to maintain reliability between the fundamental parameters to ensure security. It is important to consider factors such as message size, image dimensions, cover object selection, image type, embedding techniques, and procedures to ensure successful steganography. Our proposed method aims to establish a dependable mechanism to meet the security requirements up to an acceptable standard which is discussed in the next section in detail.
Proposed methodology
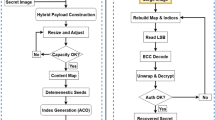
In this section, first, we briefly defined various mathematical notations and other concept terms used for proposed method. Finally, we explain the essential steps of embedding and extraction of proposed method concisely. The AES embedding algorithm used just after the stego image generated. first, we take a cover image and apply transposition function then divided into three channels and blue channels is further divided into four equals blocks. After that shuffled the bits of Blue chancel using magic matrix and apply xor. After that w rearranged the shuffled block and combine three channels once the stego image generated then AES algorithm performed. Equations 1–6 are used for the proposed method embedding parameters such as Ci denote cover image, Ti transpose image, Re, Gr, Bl respectively Red, Green, and Blue channel of the RGB image. While Mdv1 represents message bits, Mg Message, and Si show Stego image. So, extraction process is the reverse process of the embedding procedure and these parameters are set in Eqs. 7–12.
Figure 2 elaborates the whole procedure of the proposed method. Firstly, taking secret data and cover images for embedding the data using LSB. Once the coded image was generated then we applied the AES and key to get the encrypted stego image. For in decrypted side first, we take the resulting stego encrypted image and apply AES and key to generate a decrypted stego image after that applying LSB the secret data extracted. Figure 2 elaborates the whole proposed method. It explains the steps handling from cover image to stego image and AES. Similarly, Fig. 3 explains the LSB procedure from cover image to stego image before AES operation means the process is just ready to apply AES operation. Figure 4 shows the graphical representation Lsb data embedding. It is the transformed version of Fig. 3. Figure 5 presents the whole AES encrypted and decrypted operations. Finally, Fig. 6 elaborated on the way of encrypted bits such as the Transformation of Sub bytes, (b) Transformation of Shift Rows, (c) Transformation of Mix Column, (d) Transformation of Add Round Key.
Mathematical foundation for LSB data embedding and extraction
The hidden message is represented by Mg in the cover image (Ci). \(Ti\) shows the transposed Image. Re denotes the red, Gr the green, and Bl the blue channels, whereas Si denotes the encrypted image. Six functions named \(\varepsilon , \pi , \omega , \mu , \eta , and \upsilon\) are used in the proposed method as a part of embedding in Eqs. (1)–(6) as stated.
The 1st function (\(\varepsilon\)) takes \(i\) as input & gets back (Ti\()\) which is the transposed image. 2nd function \((\pi )\) splits \(Ti\) into three channels that are red, green, and blue, where (Bl) is utilized for inserting the secret message. For providing more security \(XOR\) operation is applied on encrypted bits, which return (\(Mdv{\prime}\)). Before inserting the secret message into blue channel \((Bl)\) it is shuffled utilizing magic matrix (Matlab function), then utilizing the 5th function \((\eta )\) which provides \(\left({Bl}^{{{\prime}}}\right)\) mean shuffled image of blue channel. Lastly, the stego image (Si) is generated utilizing the 6th function \((\upsilon )\) by inserting secret message bits \((M dv{\prime})\) in the shuffled blue channel (B\(l^{{\prime}}\)) utilizing LSB after that once the stego image generated then performed AES algorithm. On the receiver side, the reverse operation has to be applied to extract the original message. The original message can be extracted by utilizing the following six procedures in Eqs. (7), (8), (9), (10), (11), and (12), as described below.
In extraction side, we first apply the AES extraction procedure, then we apply LSB-based extraction on stego image. In the extraction process, function (\({\varepsilon }^{-1}\)) put on to the encrypted image (Si) & returns a transposed image (Ti). Equation (8) divides (Ti) into three channels of RGB. function (\({\omega }^{-1}\)), will give the shuffled blue channel (Bl) randomized to produce the blue channel. after that applying XOR operation (M dv′) and extracted the secret message from (\({Bl}^{{{\prime}}}\)) by utilizing Eq. (10). To obtain the plaintext (Mdv), function (\({\upeta }^{-1}\)) is utilized. Lastly, the original message (Mg) is attained by utilizing Eq. (12).
,4 and 5 describe the LSB data embedding. First, we take a cover image and apply the transport function to get a transpose image, then divide it into red, green, and blue channels. The blue channel is further divided into four equal blocks and shuffled using the magic matrix function. So after that the secret message converted bits embedded using XOR operation into blue channel sub-blocks. Once the process is completed and get the stego image then we apply AES algorithm, the whole procedure is shown in below Figs. 5 and 6.
Shuffling by magic matrix (MM)
An MM is a Matlab function called “magic matrix” that produces a matrix of a specified size with the characteristic that there are no duplicate numbers in the magic matrix. It is a magic matrix that the numbers cannot be larger than the sum of its rows and columns or diagonally. The results are the same by adding rows, columns, and diagonally. Considering the traits above, the pixels of a cover image can be easily rearranged in the right sequence after we shuffle them. A simple precedent is used to explain this rearranging method further. Imagine a 3 × 3 inch cover image (Ic), i.e., Ic = {95,25,10,36,21,48,88,33,62} to reposition. For this reason, we must create an enchantment framework (Mm) that is equivalent to the cover image dimensions and set (Is) as the repositioned image31,32.
The enchantment framework shows us where moving values of pixels, i.e., the first-pixel value 95 shifted to the 1 of mm (col 2, ro1), the second, 25 to (col 2, row 2), the third, 10 to (column 3, row 2), the fourth, 36 to (column 3, row 3), the fifth, 65 to (column 2, row 2), and so on. The MM Matlab function used in the proposed method on blue channel for shuffling the bits to gets more security and resistance to attackers.
Advanced encryption standard (AES)
AES is a symmetric encryption method and is considered an industry standard for keeping confidential data used in proposed method and applied once the stego image generated after LSB process. So, AES offers three different key sizes: a 128-bit key is used for 10 rounds, a 192-bit key is required for 12 rounds, and a 256-bit key is used for 14 rounds. The method resists various cryptographic attacks due to its use of multiple rounds of substitution, permutation, and mixing operations33,34. Below are the main steps in the AES encryption process, as shown in Figs. 6 and 7a.
-
Step 1: Key Expansion: Each round of the method uses a different set of round keys created by expanding the original encryption key.
-
Step 2. Initial Key: The input data blocks, typically 128 bits each, are created. In the first round, each block byte and the matching byte of the round key are concatenated using a bitwise XOR operation.
-
Step 3. Rounds: The key size affects the number of rounds AES uses, which is fixed. During each round, the data block is subjected to many modifications. These changes to the bytes’ structure include substitution, permutation, and mixing.
-
Step 4. Final Round: The mixing operation is absent from the final round, comparable to the earlier rounds. This ensures that the encryption procedure can be uncompleted.
The Advanced Encryption Standard (AES) is a highly secure encryption algorithm thoroughly researched by cryptographers globally. It resists known attacks when correctly implemented with a sufficiently long and random key. AES is widely used to protect network communication, data storage, cryptographic systems, and various applications and protocols. Figures 5 and 6 elaborate both LSB and AES process used for embedded message bits in the proposed method.
AES decryption process
Decoding is the reverse of encoding and includes returning the code image to the decrypted image using a key. There is a backward substitute byte, a reverse blend section, an opposite shift column, and a converse box. Inverse Sub Byte Transformation: Acquiring the new framework, each byte from the frame is supplanted with the opposite s-box table. Inverse Shift Rows Transformation: The frame’s column has been circularly correctly moved. Inverse Add Round Key Transformation: Capability is opposite to that of blend segment change. Opposite34,35,36,37. Add Round Key Change: The subsequent grid is XORed with the lengthy key from the earliest key shown in Fig. 7a–d.
Simulation results and discussion
In this section, we present the experimental setup, analysis, and discussion in detail. The proposed method enables information to be concealed without causing noticeable visual alterations because the least significant bit has a minimal impact on the image up to 4 LSBs. The proposed method used MATLAB for experiments, a well-known programming, numerical, and technical computing language. It offers a convenient setting for working with images and putting the essential algorithms for concealing and obtaining sensitive information into practice. The experimental results are conducted based on different perspectives (to measure the method with different dimensions for getting better image type, dimensions, format, etc.) and also critically analyzed on some QAM and security analysis to show the importance of the research work. However, the overall analysis and discussion of the proposed method are discussed respectively, which are given below:
-
Perspective 1: Same-size images and different-size text
-
Perspective 2: Different dimensions’ images with same text.
-
Perspective 3: Analysis using QAM and Security Analysis
Image quality assessment measurements (QAMs)
To assess the effectiveness of image steganography, various methods are utilized. All of these methods evaluate a different angle of the Steganographic method31,32. A few renowned approaches include Mean Square Error (MSE), Peak Signal Noise Ratio (PSNR), Structured Similarity Index Measure (SSIM), Normalized Cross Correlation (NCC), and Root Mean Square Error (RMSE). Peak Signal Noise Ratio (PSNR) are used. So, the Peak signal–noise ratio is a fundamental metric used to determine whether the resulted image is identical to the original image. PSNR is used to calculate the robustness of the suggested technique. Where C represents the cover media.
Mean Square Error: The mean square determines the distinction between the original and the resulted image. It highlights the variations between the original and stego images. Where S denotes the stego media & \(C\) denotes the cover medium. The median dimensions are \(M\) and \(N.x \& y\) are then the loop counters. MSE formula is:
Structural Similarity Index Measurement: Structural Similarity index measurement is utilized to compute the brightness, contrast, & structure of the original & stego mediums were calculated using this measurement.
SSIM assesses the decline in quality induced by certain activities. Where \(x\) and \(y\) are the mean values for \({\mu }_{x}\) & \({\upmu }_{\text{y}}\), the variances for \(x\) and \(y\) are \({{\sigma }_{x}}^{2}\) & \({{\sigma }_{y}}^{2}\), respectively, while the covariance for \(x\) and y is \({\sigma }_{xy}\).
Normalized Cross Correlation: Normalized Cross Correlation is the approach for calculating the original medium & stego medium quality. \(M\) & \(N\) denote the medium dimensions, \(C\) the cover medium & \(S\) the stego medium.
Root Mean Square Error: RMSE calculates the variation among the stego & the original medium.
Mean Absolute Error: Mean Absolute Error is a criterion to assess how well a system resists assaults. Where \(C(x, y) \& S(x, y)\) are the pixel’s grey levels, \(M\) is the cypher medium, & \(N\) is the plain medium26.
Correlation Coefficient: it is also used for linearity analysis of two random variables. Both variables are said to be equal if the value is 1 otherwise not equal if 0. Eq. 19 represent the formula of CC.
Image Fidelity: it is also used for checking the image quality of both stego and the cover image. Equation 20 shows IF where P and S are both stego and cover images. While i and j represent upper and lower bonds.
To begin, a text of eight KB is inserted in color images of various formats with a size of 256 × 256 utilizing Perspective 1; On 50 images, this experiment is conducted. Second, in Perspective 2, conceal four different text sizes (i.e.:2 KB, 4 KB, 6 KB, 8 KB) in separate images of the equal size (256 × 256). This investigation is focused on four standard shading images. In Perspective 3, we employ comparable images to those in Perspective 2 with varying resolutions (128 × 128, 256 × 256, 512 × 512, and 1024 × 1024) with an inserting hidden text size of 8 KB.
We used image datasets from SIPI as shown in Fig. 8. For perspective 1 based on PSNR, the same text size (8 KB) is inserted in several images with the same dimensions (256 × 256). The average PSNR value over one hundred pictures (100) demonstrates the performance of this research work, shown in Figures and Tables 3, 4 and 5 below.
Table 3 and Fig. 9 represents the performing exploration of the proposed method based on some quality assessment metrics that shows better results.
Different message text sizes (2-8 KBs) are inserted into three usual edgy & flat images (Peppers, Home, Lake, and Splash) of the same size (256x256) from the dataset, according to perspective 2. The average PSNR of the identical stego image with various text sizes is shown in Figs. 10 and 11.
In light of perspective 3, 8 KB text is inserted in images of various sizes (128 × 128, 256 × 256, 512 × 512, and 1024 × 1024), as shown in Fig. 10. The data demonstrated improved presentation. Table 4's results using some QAM present the performance of the proposed method. Table 5 shows the results of the comparative analysis of the proposed method with some existing methods. The performance of proposed method can be clearly seen over the existing methods.
However, performance analysis of the proposed method with different perspectives shows the better performance and reasonable results of this research work, highlighted in Figs. 8, 9, 10, 11 and 12, and Tables 3 and 4. After performance analysis of the proposed method, safety or critical breakdown analysis was also conducted, which shows the performance of the proposed method, which is elaborated in the given sub-sections. In Table 6, the bits per pixel is calculated using the standard formula, which is; bpp (bits per pixel) = total embedded bits/number of pixels (image width and Height, i.e., W × H). So, in Table 6, 512 × 512 images with different hiding capacities, the bpp is shown in detail.
Discussion
In this section, we explain a critical analysis of the proposed results and performance, examining how it can resist some attacks using RS Steganalysis. The proposed method was analyzed using security RS analysis, noise, and cropping attacks. The proposed method also analyzed up to 4 LSB’s to check the tranparencey of the images, either the cover image and resulted image is identical or not and the bits how much effected. The proposed method also analyzed with historgram analysis. However, after performing this analysis, attacks on the proposed method with some standard images show better results and can resist any attacks. The RS analysis explains modifications in singular & regular groups via collective volume from a small inserting (5%) to the highest inserting of 50%. An encrypted picture can effectively shield against the RS attack under the condition that Rm Equivalents R − m and Sm Equivalents S − m. The RS examination finds no restricted information if Rm ≈ R − m > Sm≈ S − m. Table 6. displays the outcomes of the suggested method’s RS-steganalysis for the stego-images at varied embedding rates. The statement Rm ≈ R − m > Sm = S-m is accurate. In other words, even when the embedding capacity is increased to 50%, the distinction between Rm, Rm & Sm, and Sm remains the same. Hence, the probability of finding hidden data inserted within cover images is very weak. Differences in the RS detection values for the suggested approach are reported at K = 4. Moreover, there is a maximum embedding capacity Between Rm and R-m on one side and between Sm and S-m on the other. The outcome demonstrates that the suggested method keeps relatively few average discrepancies between the singular group and the regular group, as shown in Table 7. It also shows that very few objects can be found. It demonstrates the suggested method’s capacity to withstand RS-steganalysis by preventing contact with the attack and achieving the necessary level of security.
Figures 13 and 14, show the experimental results of the proposed method using 2 testing images. In each figure, the first line shows the cover and encoded image; the second line shows the stage image encrypted by AES, and the third line shows the Decoded and reconstructed stego image. We conducted both objective and subjective analysis for our proposed method, and it can be seen that the QAM values are from the 50–90 range, which is acceptable and shows the quality of images. It can be strongly supported using histogram analysis of the proposed method by the following Histogram analysis of both cover and stego images shown in Figs. 15, 16, and 17.
We have experimented with the proposed method that analyzes the embedding LSB from 1 to 4 LSBs. It can be seen in Table 8 and Figs. 17, 18, 19, 20, 21 and 22, the impact of the 1st LSB to 4th LSB embedding. In Fig. 20, it is seen that we exceeded the embedding bits into more than 4th Lsb, and then the image quality degraded. So the feasible LSB for embedding message bits is up to the 4th LSB. Figure 22 shows the result of the cropping attack (ca) analysis.
Several standard images were analyzed using noise attacks with salt and pepper noise values of 0.01, 0.1, and 0.5. The results showed that 0.1 salt and pepper noise is still detectable. To protect against Cropping Attacks (CA), a good cryptosystem should be able to resist both transmission and storage-based data. To evaluate its resistance to cropping attacks, sections of size 64 × 64, 64 × 128, 128 × 128, and 128 × 256 were removed from the “Lake” image embedded in Fig. 23. The resulting images are displayed in Fig. 16 they are still recognizable. This demonstrates that our algorithm is capable of resisting data manipulation attacks. In this way, our proposed method shows has great durability and can capably go against upheaval attacks. This is demonstrated in Figs. 15, 16, 17, 18, 19, 20, 21, 22.
The proposed algorithm has felt empirical testing from diverse perspectives using assessment metrics, showing improvement, efficiency, and effectiveness. Our method upgrades the payload, undeniable level of security, and temper assurance, and works on the visual nature of pictures21. The limitations in our method regarding format, color model, and some compression attacks. If attackers attempt to use techniques such as LSB or steganalysis to extract the contents of the secret message, they will not be able to succeed due to the use of AES, MLE, key, and Magic matrix. Even if they partially succeed, the extracted contents are useless without using AES, MLE, and other techniques to retrieve the actual message.
In order to test the strength of the proposed approach, the security analysis was performed in detail to determine the possible ambiguities and the measures adopted to address the ambiguities. The system is highly resistant to the attacks based on statistics because the xor process of embedding effectively randomizes the pixel intensity distributions with the help of group of bits’ substitution and key permutation and reduces the statistical differences that can be detected. When compared to brute-force key attacks, there is an important complexity contribution of both a large key space and multi-level permutation, which makes exhaustive key search unfeasible. Moreover, the technique proves to be very resistant to steganalysis-based detection because the pixel level randomness brought about obscures embedding patterns and lowers the possibilities of detecting hidden data. The comparative analysis against the current methods reveals that the given scheme has a better confidentiality, imperceptibility, and resistance to different attacks. These findings reaffirm that the bit-group substitution coupled with the key-controlled pixel permutation operation is effective in enhancing the overall backlash in the security of the entire steganographic process. So the proposed method is embedded the secret message in a such a way that fulfill the need of image steganography and make a reliable method in terms of basics criteria. That’s why we used a hybrid concept to achieve some criteria using cryptography and some are steganpragphy based and such a way that can easily achieve a better image steganography method. so we also tried to embeds the message in such a way that cover the need of steganography and the proposed method also analyzed using different statistically attacks (singular and regular groups, cropping and checking up to 4 LSB’s (because according to literature and our experiment it can be clearly seen that we can embed a secret message up to 4 LSB)) to checks the resistance against attackers. The Proposed method also analyzed using different quality assessment metrics to shows the strengthen of the method. After a detail analysis and experiment on different perspectives of the proposed method, it is found that Jpeg format is best format and dimensions is 512 × 512 for image steganography and the cropping analysis clearly shows the performance of the method but still need some compression i.e. Huffman etc. technique to more strengthen the steganography. Because image steganography needs reliability between the criterion and in the best of my knowledge they can only achievable only a hybrid model of both cryptography and steganography.
Conclusions
This research work presented an enhaced image steganography on LSB, AES, and Magix matrix, transposition and key based method to make a reliable method in term of basic criterion such as robustness, tranparecney, temper protection and computation etc. in spaital domian. So, to cover reilablity, we used hybrid different concepts to fullfill the need of image steganography. First way make a embedding procedure based on LSB’s in such a way to improves visual quality and embedding efficencey compared to exsiting methods while mainting great resistance against common attacks on steganpgraphy. Once the stego image generated, then applied AES algorithm to stego images to improve the security layers of secret data. The propoded research work also tested on different perspectives in terms of different dimensions images, and different sizes of message text which shows the performance of the method. The proposed work also tested based on quality assesment matrices, and it can be seen that the values of PSNR, MSE, RMSE, MAE, NCC, and SSIM shows better results fulfill the need for image steganography. After a details experiment it is identified that: JPG format, 512 × 512 dimenion, and 64 kb message size is best and recemended for future uses. In addition, we also assessed the proposed method’s based on tamper resistance, robustness, and resistance against known attacks through Histogram and PDH analysis, etc. which generates high-quality images and increases level the security level when embedding up to the first 4 LSB in the ratio of 5.035 embedding capacity. It technical merits, the proposed method has meangfull effects on data secuirty healthcare and others sensitive domians where security and privacy are critical. In the future, the proposed method can be extended for mulimedia formats, noise, frequencey domian, differernt image formats, others attacks models, lossey compression and uses of deep learning for optimal cover steganography and smooth embedding processes. In our analysis, we found that our proposed method is best supported using JPG Images, but we observed that repeated compression of JPEG images loses the quality. Thus, to address these issues by adopting advanced compression procedures, for instance; Huffman coding or other deep learning optimization for better embedding process that make a secure communication in healthcare and data management.
Data availability
Data is provided within the manuscript.
References
Laishram & Tuithung, D. T. A survey on digital image steganography: Current trends and challenges. In 3rd International Conference on Internet of Things and Connected Technologies, 1–17.
Doshi, R., Jain, P. & Gupta, L. Steganography and its applications in security. Int. J. Mod. Eng. Res. (IJMER) 2(6), 4634–4638 (2012).
Ye, J. Advancements in spatial domain image steganography: Techniques, applications, and future outlook. Appl. Comput. Eng. 94, 6–19 (2024).
Shamsi, Z. et al. Visually meaningful cipher data concealment. Digital Signal Process. 155, 104717 (2024).
Sahu, A. K. & Sahu, M. Digital image steganography and steganalysis: A journey of the past three decades. Open Comput. Sci. 10(1), 296–342 (2020).
Anfal, S. A. & Saeed, M. J. A deep dive into deep learning-powered steganography for enhanced security. Int. Res. J. Innov. Eng. Technol. 8(3), 79 (2024).
Borse, G., Anand, V. & Patel, K. (2013). Steganography: Exploring an ancient art of hiding information from past to the future. Int. J. Eng. Innov. Technol. (IJEIT) 192–194
Majumder, S., Tanu, M. D., Faisal, S. M., Sristy, M. R., & Paul, R. Enhanced and secured hybrid steganography model for hiding large data. Doctoral dissertation, Brac University (2023).
Chanu, Y. B. J., Tuithung, T. & Singh, K. M. A short survey on image steganography and steganalysis techniques. In 3rd National Conference on Emerging Trends and Applications in Computer Science, 52–55 (IEEE, 2012).
Por, L.Y. & Delina, B. Information hiding: A new approach in text steganography. In Proceedings of the International Conference on Applied Computer and Applied Computational Science, 689–695 (World Scientific and Engineering Academy and Society (WSEAS 2008) (2008).
Kadhim, I. J., Premaratne, P. & Vial, P. J. High capacity adaptive image steganography with cover region selection using dual-tree complex wavelet transform. Cogn. Syst. Res. 60, 20–32 (2020).
Shah, P. D. & Bichkar, R. S. Secret data modification based image steganography technique using genetic algorithm having a flexible chromosome structure. Eng. Sci. Technol. Int. J. 24(3), 782–794 (2021).
Sahu, A. K. A logistic map based blind and fragile watermarking for tamper detection and localization in images. J. Ambient. Intell. Humaniz. Comput. 13(8), 3869–3881 (2022).
Roy, S. & Islam, M. M. A hybrid secured approach combining LSB steganography and AES using mosaic images for ensuring data security. SN Comput. Sci. 3(2), 153 (2022).
Alanzy, M., Alomrani, R., Alqarni, B. & Almutairi, S. Image steganography using LSB and hybrid encryption algorithms. Appl. Sci. 13(21), 11771 (2023).
Bima, A., Irawan, C., Krismawan, A. D. & Isinkaye, F. O. A text security evaluation based on advanced encryption standard algorithm. J. Soft Comput. Explor. 4(4), 250–261 (2023).
Karim, S. M. M., Rahman, Md. S., & Hossain, Md. I. A new approach for LSB based image steganography using secret key. In Proceedings of 14th International Conference on Computer and Information Technology (ICCIT 2011), 286–291 (2011).
Akhtar, N., Johri, P. & Khan, S. Enhancing the security and quality of LSB based image steganography. In International Conference on Computational Intelligence and Communication Networks, 385–390 (2013).
Aiswarya, S. & Gomathi, R. Chaos based cryptography and rectangular shape based steganography technique using Lsb. Malays. J. Comput. Sci. 36(4), 368–380 (2023).
Ahmed, A. & Ahmed, A. A secure image steganography using LSB and double XOR operations. IJCSNS Int. J. Comput. Sci. Netw. Secur. 20(5), 139–144 (2020).
Ali, U. A. M. E., Sohrawordi, M. & Uddin, M. P. A robust and secured image steganography using LSB and random bit substitution. Am. J. Eng. Res. (AJER) 8(1), 39–44 (2019).
Rahman, S. et al. A novel approach of image steganography for secure communication based on LSB substitution technique. Comput. Mater. Continua 64(1), 31–36 (2020).
Pabbi, A., Malhotra, R. & Manikandan, K. Implementation of least significant bit image steganography advanced encryption standard. In International Conference on Emerging Smart Computing and Informatics (ESCI), 363–366. (AISSMS Institute of Information Technology, 2021).
Yamni, M., Daoui, A. & Abd El-Latif, A. A. Efficient colour image steganography based on a new adapted chaotic dynamical system with discrete orthogonal moment transforms. Math. Comput. Simul. (2024).
Awadh, W. A., Alasady, A. S. & Hamoud, A. K. Hybrid information security system via a combination of compression, cryptography, and image steganography. Int. J. Electr. Comput. Eng. 12(6), 6574–6584 (2022).
Abunadi, I. et al. Optimal multikey homomorphic encryption with steganography approach for multimedia security in Internet of Everything environment. Appl. Sci. 12(8), 4026 (2022).
Muhammad, K., Sajjad, M., Mehmood, I., Rho, S. & Baik, S. W. A novel magic LSB substitution method (M-LSB-SM) using multi-level encryption and achromatic component of an image, 1–27 (2016)
Almomani, I., AlKhayer, A. & El-Shafai, W. Novel ransomware hiding model using HEVC steganography approach. Comput. Mater. Continua 70(1), 1209–1228 (2022).
Islam, M. R., Siddiqa, A., Uddin, M. P., Mandal, A. K. & Hossain, M. D. An efficient filtering based approach improving LSB image steganography using status bit along with AES cryptography. In 3rd International Conference on Informatics, Electronics & Vision 2014, 1–6 (2014).
Ghrare, S. E., Abouras, M. A. & Akermi, I. A. Development of hybrid data security system using LSB steganography and AES cryptography. Afr. J. Adv. Pure Appl. Sci. (AJAPAS) 3, 86–95 (2024).
Islam, M. R., Tanni, T. R., Parvin, S., Sultana, M. J. & Siddiqa, A. A modified LSB image steganography method using filtering algorithm and stream of password. Inf. Secur. J. A Global Perspective 30, 359–370 (2021).
Sharma, D. & Prabha, C. Hybrid security of EMI using edge-based steganography and three-layered cryptography. In Applied Data Science and Smart Systems, 278–290. (CRC Press, 2024).
Rahman, S. et al. Multi perspectives steganography algorithm for color images on multiple-formats. Sustainability 15(5), 4252 (2023).
Rahman, S., Masood, F., Khan, W. U., Salam, A. & Ullah, S. I. Investigation of LSB-based image steganographictechniquesin spatial domainfor secure communication. Sukkur IBA J. Emerg. Technol. 02(01), 1–12 (2019).
Kadhim, I. J., Premaratnea, P., Vial, P. J. & Hallorana, B. Comprehensive survey of image steganography: Techniques, evaluations, and trends in future research. Neurocomputing 335, 299–326 (2019).
Bandekar, P. P. & Suguna, G. C. LSB based text and image steganography using AES algorithm. In Proceedings of the International Conference on Communication and Electronics Systems (ICCES 2018), 782–788 (2018).
Alyousuf, F. Q. A., Din, R. & Qasim, A. J. Analysis review on spatial and transform domain technique in digital steganography. Bull. Electr. Eng. Inform. 9(02), 573–581 (2020).
Acknowledgements
This research is funded by the European University of Atlantic.
Author information
Authors and Affiliations
Contributions
Syeda Zahra Banoori.Wajidullah Khan. Farhan Amin and Shahid Rahman. wrote the main manuscript text and Fahad Masood.Abdu Salam. Isabel de la Torre. Mónica Gracia Villar. Helena Garay. Gyu Sang Choi prepared Figs. 1–3. All authors reviewed the manuscript.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Banoori, S.Z., Khan, W., Rahman, S. et al. An improved hybrid image steganography method using AES algorithm. Sci Rep 15, 44515 (2025). https://doi.org/10.1038/s41598-025-28140-0
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-28140-0