Abstract
MANET is a hot research subject. Its qualities, including no infrastructure, fast network setup, and no centralized management, have led to its popularity and widespread use in numerous sectors. A major part of the network is security. Intrusion Discovery Scheme (IDS) is a network security strategy. In this paper, we implemented effective intrusion detection and efficient clustering with cluster head selection. For these two stages of implementation, we are not integrating any logic combinations to make decisions. Machine learning models are filled up that place of work in the proposed optimal MANET design. At first, the IDS is performed in the network using Adaptive Ensemble Tree Learning (AETL) based classification of typical nodes and malicious intrusions. Once the attacker nodes are identified, the nodes will be recovered to mold the network for the next sequence process of clustering. In the disemboweled network, the proposed model of second stage Hybrid Dual Optimization of Machine Learning Model (HDOMLM) is applied to elect the leading agent node in the formed clusters. Particle Swarm Optimization (PSO) is defined for the initial clustering of nodes and immediately the O-MLM is performed to detect the leading agent nodes in each cluster with the selection features of node degree, node mobility, energy, distance and delay. Experiment validations are accomplished to analyze the results of the proposed method using the MATLAB simulation tool and quantitative evaluations done for different Key Performance Indices (KPI) of network lifetime, residual energy, packet delivery and transmission delay with earlier works of the same. From the simulation performances, our proposed AETL with HDOMLM attained the peak results than other algorithms with the metrics of 71% of energy saving and 50.12% enlarging the network lifetime.
Similar content being viewed by others
Introduction
Mobile Ad Hoc Network (MANET) remain the next-generation way to conduct communication systems. MANETs are autonomous networks that operate without any pre-existing infrastructure for communication. These networks can also employ existing immovable infrastructure networks, if they are available, to establish communication with additional devices1. The proliferation of MANETs has been driven by the cost-effective wireless networking technology and the ability to provide mobility anytime and anywhere. This has mostly contributed to the development of mobile ad-hoc networks. A Mobile Ad hoc Network (MANET) consists of a specific number of nodes that are interconnected by wireless means. The nodes in the network establish communication with each other if they are located within the range of coverage. A mobile computer device is capable of moving in any direction within the coverage area of radio connections without relying on a permanent infrastructure2. Due to the innovations in low range wireless technology of mobile computing, it is now possible to develop applications over Mobile Ad hoc Networks (MANETs). MANET programs perform wireless network operations and have seen a significant rise in adoption due to their capacity to adapt and configure themselves3.
Mobile nodes are categorized by their memory savage, power, and weight. Wireless networks possess a greater number of security susceptibilities compared to wired networks due to the absence of centralized supervision over the network4,5. Due to the scattered nature, security risks are more widespread, encompassing routing, configuration, and the absence of an intrusion approach6. MANETs are more susceptible to security threats compared to wired networks due to their dynamic nature, potential vulnerabilities arising from compromised nodes, inadequate encryption methods, unpredictable network topology, scalability issues, and nonexistence of centralized control7,8.
An intrusion detection technique (IDS)9 is a defensive tactic used in MANETs to examine and evaluate unusual events by utilizing various methods to detect abnormalities or deviations in behavior or behavior patterns. To properly utilize MANET and make the most of its versatile and adaptive characteristics, it is imperative to implement highly reliable and robust security protocols. Preventing an intrusion serves as a strong initial measure to fend off subsequent attempts, however it does not ensure absolute security. Enhancing intrusion detection in MANET can be achieved by implementing a secondary layer of defense that relies on classification algorithms capable of distinguishing between normal network behavior and malicious intrusion attempts10. As the user base of the network expands, the expenses associated with network service infrastructure escalate significantly. Consequently, an efficient algorithm is essential for detecting attackers, which relies on cost-effectiveness and low latency in network services11. and these factors must be considered during the design of an Intrusion Detection System (IDS). To achieve the goal of electing the most cost-efficient nodes as leaders in the presence of selfish and malicious nodes, efficient learning-based model should be structured.
Deep learning models for security analysis with LSTM architecture process sequences as input, yielding excellent prediction accuracy with little computing complexity. The deep learning-based approach can yield near-optimal outcomes in brief time intervals, provided the DNN is adequately trained12. The effective training of various scenarios in MANETs utilizing deep learning necessitates greater information storage compared to machine learning. Recent Federated UnLearning to address the “right to be forgotten”, and ignore the server’s right to remove local models from the global model, particularly when clients are trained with low-quality data. SIFU proposed in13, a category-based method for quantifying low-quality data for each client and filter out clients containing such data which is used to minimize any bias introduced. Using only FL lags while the participation of data source is limited. This problem overcome by model value transfer incentive (MVTI)14 to enable adapted model creation. Even though it faces the issue of data integrity.
Consequently, we have resolved to apply a machine learning approach to reduce the complexity with higher prediction rate. In15, utilizing the Full Mesh Aggregation (FMA) topology, the identified abstracted pathways link the source and destination of the Service Function Chain (SFC) request, therefore mitigating superfluous forwarding during the SFC partitioning process. The data on the accessible resources of each domain will be presented as a weight for the partitioning of a Service Function Chain (SFC). The SFC mapping issue is NP-hard, making the acquisition of the optimal solution challenging and time-consuming. The use of various security methods alongside an intrusion detection system can substantially elevate the complexity of a system, complicating management and troubleshooting efforts. Security techniques such as encryption may occasionally impose significant performance overhead, hence impeding system operations, particularly on legacy hardware16. Consequently, we concentrated on intrusion detection with machine learning, employing security-preserving metrics as features gathered from the network nodes.
The inherent openness of Mobile Ad hoc Networks (MANETs) and the lack of centralized control heighten their vulnerability to security risks, since attackers can effortlessly penetrate and compromise the network. Administration of a distributed network lacking a centralized infrastructure adds complexity to the implementation of security protocols and allocation of resources. Through deliberate neglect of the routing protocols requirements, malicious routing attacks can target the identification or upkeep of routing. Nevertheless, most systems, which rely on the aforementioned methods, face challenges in terms of high rates of false negative and false positive detection. Additionally, they lack continuous adaptation to evolving malevolent behaviors.
We provide a generic clustering approach that, regardless of the routes, can continuously detect intrusions and operates on top of any kind of routing protocol using machine learning models with the constraints of mobility of nodes. Regardless of the network’s paths, connected as traffic types, or nodes’ mobility, the suggested reduced clustering technique of AETL integrated with HDOMLM was able to identify intrusions with significant detection rates and little processing and memory cost. To sum up, this study presents a strategy for Leading Agent node (LAn) selection and MANET IDS that aims to achieve the following:
-
1.
The full potential of Mobile Ad hoc Networks (MANETs) can be achieved by the mitigation of the hazards linked to their operational dynamics.
-
2.
The HDOMLM Protocol is designed to handle different node characteristics, including processing power, transmission range, and energy resources, while identifying the top agent nodes in different topology setups.
-
3.
Applying the ensemble model of Adaptive Ensemble Tree Learning (AETL) to implement the dependence on intermediate nodes for data forwarding, so providing end-to-end security and reliability.
-
4.
In order to accommodate bandwidth-intensive applications and adhere to the processing and storage limitations of mobile devices, we have developed the HDOMLM based relay node prediction system. This system aims to maintain an energy and throughput aware decision mechanism in MANET.
We provide a new AETL with HDOMLM machine learning models that include these two parts to accomplish these goals:
-
AETL based Intrusion Detection: In this module, based on the network acquired features of consumed energy, packet delivery ratio and routing overhead of certain processing rounds, the malicious nodes are identified with structured learning model of AETL. In AETL, adaptive learner of bagging tree and boosting tree selection is performed which improves the classification accuracy with less complexity.
-
HDOMLM based Leading Agent Node (LAn) assortment: The clustering is accomplished by PSO based objective design. For this completed clustering nodes, important selection metrics of delta difference, average distance, related mobility, related energy and delay terms are estimated to evaluate the O-MLM based LAn selection.
The enduring paper is prearranged as section II discuss about the earlier works of intrusion detection in MANET. Our suggested method and system model for implementation are detailed in Section III. The findings and analysis of the metrics are presented in Section IV. The paper’s conclusion may be found in section V.
Related works
The underlying vulnerabilities of Mobile Ad-hoc Networks can result in significant implications17, with Black hole attacks being especially difficult to detect due to their covert nature. In18, the researcher presents a new method that employs advanced computer algorithms to analyze network data and accurately identify breaches in mobile ad-hoc networks, thereby enhancing their security. Machine learning and deep learning are effective methods for identifying black hole attacks in mobile ad-hoc networks. Machine learning algorithms can be utilized to acquire knowledge about the typical patterns of network behavior and then identify any deviations from those patterns as possible assaults. Deep learning algorithms possess the ability to acquire intricate patterns within the data, which enhances their efficacy in identifying black hole attacks.
The researcher19 proposes a technique for detecting and measuring intrusions in Mobile Ad hoc Networks \(\:\left(MANET\right)\) using a model called “Whale Optimization based DNN”. The reference19 describes the detection of intrusions in \(\:MANET\) services. The dataset dimensionality is reduced using Principal Component Analysis \(\:\left(PCA\right)\) and extraneous data is eliminated using the “WhaleOA” technique. The DNN Classifier improves model classification accuracy. Comparisons of the proposed method’s effectiveness to previous approaches demonstrate higher classification accuracy, attack detection rate, and F-Measure. The suggested technique demonstrates a superior attack detection rate of \(\:2.043\%\) compared to the “HybridCSTuningSDeepNN“20 model, and an \(\:13.201\%\) improvement over\(\:\:GOA-SVM\). The proposed technique has a classification accuracy of 99.1%. The proposed WOA-DNN model achieves a classification accuracy of \(\:99.1\%.\) the precision \(\:\left(\%\right)\) for the target and normal classes which is also superior in compared to other approaches. The many algorithms of implementation for intrusion detection in MANET21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43 are listed out in Table 1. In44, Adaptive Marine Predator Optimization Algorithm (AMOA) and Deep Supervised Learning Classification (DSLC) are developed. AMOA used to select the features from the normalized dataset and DSLC algorithm is used to accurately calculate the type of intrusion based on the preferred features. Two-Pronged Intrusion Detection System (TP-IDS) designed for MANET in45 to focus on the multi attacks prediction with SMOTE class imbalance behavior.
To adapt numerical computations for deep learning, most researchers convert semantic attributes into numerical values with embedding technology. The randomization and obfuscation in network attacks cause their carriers to exhibit polymorphism. The issue of unbalanced datasets, characterized by a predominance of benign traffic over malicious operations, frequently results in biases during model training favoring the majority class. The issue is exacerbated by the necessity for meticulous selection of observation time frames for learner models, which substantially influences the accuracy and reliability of attack detection methods. For imbalanced dataset, in46, the author addressed these issues and developed HIDIM for intrusion detection using deep learning. Secure transmission in relay networks and multihop ad-hoc networks utilizing physical layer security has garnered significant interest. To tackle the eavesdropping problem posed by randomly located passive attackers in a large-scale ad hoc network, secure transmission in wireless ad hoc networks is formulated in47 utilizing a secrecy connection probability model, which ensures that transmissions are safeguarded against intrusion in MANET.
Federated Learning is attracting model in detecting the attackers and integrated with the local predictor model which is used in48 with improved variance reduction. The discovery highlights the capability of federated learning (FL) to improve security protocols in mobile ad hoc networks (MANETs) without requiring centralized supervision, which is frequently unfeasible in these networks owing to communication and power limitations. Support Vector Machines (SVMs) are usually employed for binary classification tasks, but they may also be leveraged efficiently for anomaly detection in specific settings. In49, the ImSVM based attack detection with imbalanced dataset is discussed. ImSVM allocates distinct weights to each positive support vector within the decision function, transforming it into an unconstrained optimization problem.
Recent studies indicate that most existing works might benefit from dependable strategies for maintaining cyber-security; nonetheless, they employ sophisticated models to get a higher attack detection rate. Consequently, we intend to design a low-complexity IDS system.
Proposed intrusion detection and leading agent node assortment in MANET using AETL and HDOMLM algorithms
Preliminaries of the system model
An example of a communications connection that may be constructed in a Mobile Ad-hoc network is the symbol for T = (S, R), where the collection of nodes is denoted by S and the linkages that relate to them are assigned to R.
The connection between the beginning of the node a and the terminating point node z is denoted by the symbol (a, z), which means that a, z belongs to the set S. When node a and node z are located in close proximity to one another, they are able to interact with one another in a linear fashion. One of the responsibilities of a network regulator in a centralized grid is to ensure that the specifics of the network architecture are correctly maintained. For the purpose of maintaining the topology of the network, a regionalized grid requires the node and its surrounding nodes to communicate information. The proposed routing approach is intended for use in regionalized MANETs, in which whole mobile nodes (MN) perform the functions of both mediators and routers in order to set up the network architecture for other nodes. When the primary process of path forecasting and communication is being carried out, the interaction between each node in the network is taken into consideration. This is accomplished by exchanging the configuration of the nodes.
Because of the perpetual mobility of nodes, the topology of the MANET is subject to changes that are neither predicted nor anticipated at all. When relay nodes are not in a direct link for transmission, the means of routing are utilized by the nodes in order to facilitate transmission. For the only purpose of propagating the data, relay nodes are accountable. Before starting the real transmission in the network, intrusion detection is performed using the proposed Adaptive Ensemble Tree Learning (AETL). To avoid the untrusted nodes-based clustering, we performed the intrusion detection before the clustering. The features to decide the node belongs to attack and features to decide the node belongs to leader node are different. So, to circumvent prediction degradation we implemented separate detection for these two stages.
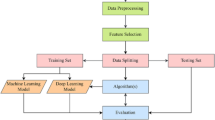
After the detection and recovery of intrusion nodes in the network, Leading Agent Node prediction is implemented using Hybrid Dual Optimization of Machine Learning Model (HDOMLM). The overall proposed work flow is depicted in Fig. 1.
Energy and mobility of nodes in MANET
Electricity from batteries is supposedly a scarce resource, and it frequently influences the way nodes in a network communicate with one another. Direct connections or multi-hop links are used for communication50. The primary difficulty is the node’s lifespan since mobile nodes have limited battery energy. Reducing energy usage for data packet transmission and increasing network lifetime are both achieved through control of transmission power. Using data collected locally, nodes optimize transmission power for least power usage. Residual energy is the amount of energy that remains in a battery after its initial capacity has been depleted. The time and energy needed to process each transmission in a MANET are independent variables. Initial energy is of each node is denoted as \(\:{E}_{\alpha\:}^{i}\left(t\right)\) at time slot of t and residual energy, consumption energy, transmission energy, receiving energy and operating energy are additionally represented with time t and duration \(\:\:\tau\:\) of i-th node as \(\:{E}_{\beta\:}^{i}\left(t+\tau\:\right)\), \(\:{E}_{\gamma\:}^{i}\left(t+\tau\:\right)\), \(\:{E}_{\delta\:}^{i}\left(t+\tau\:\right)\), \(\:{E}_{\mu\:}^{i}\left(t+\tau\:\right)\), \(\:{E}_{\rho\:}^{i}\left(t+\tau\:\right)\) respectively. The residual energy is given by,
The recommended strategy calculates energy usage by considering the power consumption of the circuitry P, time taken at each mode and the transmitted data packets of N.
whereas \(\:{P}_{\delta\:}^{i}\left(t+\tau\:\right)\) and \(\:{P}_{\mu\:}^{i}\left(t+\tau\:\right)\:\)denotes the transmitting power feasting for broadcasting \(\:n\) information packets and communicating the data to the next forwarding node with duration of \(\:\tau\:\) and power feasting of m packets from the TX nodes and sending it to the next relay node of Receiver. The power is measured in W/s. We need to modulate the network before we can test and simulate how well the ad hoc network solutions operate. Considering the characteristics of MANET networks, the mobility of the nodes plays a crucial role in the design of the network model. Various mobility models have been put out in the literature to accomplish this. The Random Way Point (RWP) model is the most applicable of the most well-known models51. Every node in the simulated region moves at a uniformly distributed random speed toward an unknown destination in this model. Once a node reaches its target, it will wait for an arbitrary amount of time that is evenly distributed before continuing its progress.
Attacks of MANET
Active attacks and passive assaults are the two primary categories that may be used to classify the kind of attacks that might occur in MANET. An example of a passive assault is the interchange of data inside a network without causing any disruption to the activities of communication. On the other hand, an example of an active attack is the interruption of communication and information, as well as manufacture and modification, which can disrupt the regular functioning of a MANET52. Examples of passive assaults include eavesdropping, traffic monitoring, and traffic analysis. Another example is traffic monitoring. One further way to separate the attacks is by separating them into internal and external attacks. The various types of attacks in MANET with different layers are shown in Fig. 2.
Black hole attack
Attacks in MANET may be categorized into two primary types: active attacks and passive attacks. A passive attack involves the interchange of data inside a network without causing any disruption to communication activities. On the other hand, active assaults involve interrupting communication and information flow, as well as manipulating and modifying data, which can disrupt the regular functioning of a Mobile Ad hoc Network (MANET)53. Passive assaults include traffic analysis, eavesdropping, and traffic monitoring. The assaults may also be classified based on whether they originate from within the system (internal) or from outside the system (external).
Cooperative black hole attack
The intercepted packets are dropped by the attacker node without being forwarded. This attack can also take a more covert form in which a node acting as the attacker suppresses or alters packets coming from specific nodes while keeping other nodes’ data packets intact. Other nodes find it more challenging to identify the rogue node as a result.
Gray hole attack
Grey hole attacks are a subset of black hole attacks54.The technique is similar to the classic black hole assault, however it drops packets selectively instead of all of them. A gray hole attack allows the attacker to forward all data packets while ignoring packets from a specific source or IP address or range of addresses. Within the grey hole, every node keeps track of its own activities in the routing table and keeps track of all the neighboring nodes that can be used to send data packets to the desired destination. Whenever a node wants to send a packet to another node, it checks the routing table to see if the desired route is already there. If not, route discovery is employed.
Wormhole attack
The wormhole threat is one of the most serious security issues with MANET. Using a secure connection known as a tunnel, at least two malevolent nodes may identify a wormhole assault. The next step is for the wormhole tunnel to begin collecting data packets and sending them on to another destination55. On one end of the tunnel, a control packet lands at the malicious node’s doorstep. Retransmitting the packet locally, it moves on to another intriguing node over a private channel at the opposite end. Because of better metrics, such fewer hops or less time than packets delivered over other channels normally, the private channel is chosen as the means for communication between the source and destination. Wormhole nodes may intentionally disclose, modify, or delete data for their own malevolent ends. It is possible to bring down the whole MANET routing network with a wormhole assault.
Sybil attack
The MANET network is more susceptible to many attacks since there is no centralized authority or control for its preservation. A malevolent node launches a Sybil attack when it unlawfully uses the identities of several phonies to deceive and bring down the network52. While authentication methods can thwart Sybil and other external attacks on a network, they are powerless against attacks launched from inside the network itself. The authentication process guarantees that there should be a mapping between the network’s entities and individuals so that every node may prove its authenticity.
Jelly fish attacks
The closed-loop flows are the targets of jellyfish assaults. A jellyfish attack occurs when an attacker node follows all protocol rules to the letter. This kind of attack is stealthy and hard to spot. One way that jellyfish nodes work is by discarding packets, which reduces the good put.
Intrusion detection using proposed AETL
In our proposed intrusion detection, method, we are using a novel machine learning algorithm of Adaptive Ensemble Tree Learning (AETL) method for classification of nodes into two category of normal node or malicious node. The proposed block diagram is shown in the Fig. 3. The proposed system detects attacks in mobile ad hoc networks by monitoring the inequitable utilization of the transmission channel. Common behaviors exhibited by attackers include Active Time Deviation (where a node is compelled to deplete its battery), Malicious Flooding (where an excessive volume of control packets is transmitted to the entire network or specific target nodes), and Ignoring the MAC protocol (where a misbehaving node generates RTS/CTS at an unacceptable frequency, disregarding the back off mechanism, thereby preventing competing neighbors from obtaining a fair share of the transmission channel). These three principal aspects of multiple attacks, as outlined in the previous section, result in elevated energy consumption due to Active Time Deviation, increased routing overhead due to malicious flooding, and a diminished packet delivery ratio due to the Ignoring of the MAC protocol.
From the network acquisition stage, we can evaluate the main three attributes of consumed energy, routing overhead and packet delivery ratio of each node. The AETL algorithm is used to classify the nodes category with application of these features as input vector for training and the corresponding class of nodes as target labels. In AETL, we are integrating bagging and boosting algorithm with decision tree classifier. We employ “Averaging” to discover ensemble prediction in Ensemble Learning, which generates an ensemble of all well-chosen strong and diversified models. To give you a rough idea, ensemble learning relies on the premise that merging several models into one stronger model, which is supported by the results of various machine learning contests56.
The first step in establishing an ensemble learning approach is to decide which base models will be aggregated. In most cases, including popular bagging and boosting techniques, just one fundamental learning algorithm is utilized, resulting in weak learners that are educated in many ways and are homogenous. The resulting ensemble model is referred regarded be “homogeneous” after this. Some approaches, however, employ a variety of base learning algorithms; for example, a “heterogeneous ensembles model” can consist of a number of weak learners from diverse backgrounds as shown in Fig. 4. It is critical that the methods we use to aggregate these models be consistent with the weak learners we select57. It is recommended to use an aggregating approach that lowers variance when selecting base models having minimal bias but a large variance, and the opposite is true when selecting base models having minimal variance but high bias: an accumulating method that reduces bias should be used.
The error of a learning algorithm has three components as given below
The bias is the systematic error that the learning algorithm is expected to make due to, e.g., architectural choices or to insufficient/unrepresentative training data. The variance measures the sensitivity of the algorithm to the specific training set and/or hyper-parameters used. Both the terms can be reducible and noise is irreducible error.
\(\:X,Y,\:\widehat{Y}\) are random variables describing the distribution of values for instances x, and their ground truth and predicted values f(x) and h(x).
ℎ(X) is an estimator (hypothesis) of the true(unknown) function f(X), which is generated by some model M as given by,
Bagging ensemble tree
A model with a high variance is undesirable as it indicates that its performance is highly influenced by the training data. Therefore, despite the provision of additional training data, the model may still exhibit subpar performance. Furthermore, there is no guarantee that this will decrease the variability of our model. To address this issue, the technique of bagging is utilized. Bootstrapping and Aggregating is named as bagging. Bagging works by training many separate weak learners f((x), fi(x),…fN(x) on B separate bootstrapped training sets with replacement, and then averaging these to output the learning result in the usual way:
Boosting tree ensemble
The primary concept of boosting is to gradually include models into the overall ensemble. During each iteration, a novel model is generated and the new base-learner model is compelled to focus on the mistakes made by the prior learners. Regarding bagging, the method generates numerous weak models, and their outputs are ultimately aggregated to obtain an overall forecast. The ultimate result of the boosting process is the aggregated value obtained by taking the weighted average of the predictions made by the feeble learners:
where \(\:{\alpha\:}_{t}\) is the weight calculated by considering the last iteration’s error. Like the random forest, since these methods are tree-based regressions, they allow for much greater implementation of the spatial co-ordinates. Many boosting methods often allow for an even larger number of trees, with minimal increase in complexity. The difference of bagging and boosting is simply shown in Fig. 5 below.
Adaptive ensemble tree learning (AETL)
Adaptive Ensemble Tree learning stands a ranked classifier characterized by a complete binary tree structure. In severely instable classification issues, there is a significant disparity in the number of positive and negative samples. The ensemble tree scheme employs the technique of initial screening, resulting in a minimal overall classification cost. In order to classify a positive sample, it is necessary to have a full path from the root node to the leaf node. However, for a negative sample, the classifier’s accessibility is less crucial and the cost is inferior.
If ensemble method is optimized as boosting, The AdaBoost classifier is utilized, while bagging refers to the usage of the random forest classifier58. Assume that the cost of classification for a classifier with n features is,
Presume the entire binary tree having\(\:\:L\:layers\), the \(\:{l}^{th}\)layer’s \(\:{k}^{th}\) classifier model data value represents by using\(\:{\:M}_{l,k}\), in \(\:{l}^{th}\)layer the \(\:{k}^{th}\)classifier .features are represented by using the parameter \(\:{f}_{l,k}\),the \(\:{l}^{th}\)layers total number of nodes can be calculated by using the variable \(\:{G}_{l}\), Given that classifiers employ an equal number of features in every layer of the tree structure,\(\:\:{f}_{l,k}={f}_{l}\). Let \(\:\psi\:(l\:-\:1;\:f)\) represent the likelihood of misclassification by layer\(\:\:1\:to\:l-1\), and let\(\:\:\psi\:(0;\:f)=1\). Next, the cost of classifying a sample is calculated,
When comparing the cost of positive and negative samples, we assume that the cost of classifying positive samples is quite little. The overall cost of the ensemble tree classifiers primarily takes into account the cost of classifying negative samples. Regarding negative samples, if a negative sample object is identified in the \(\:{l}^{th}\) layer, its likelihood of being executed is equal to the likelihood of the sample being mistakenly classified as “positive” by the classifier in layers \(\:1\:to\:l-1\)\(\:\left(false\:positive\:rate\right),\:\)hence, the cost of classifying the ensemble tree classifier is represented by Eq. (13):
The complete ensemble tree classifier’s false positive rate is equal to the cumulative false positive rates of each individual classifier in the\(\:\:{L}^{th}\:layer\), denoted as \(\:{G}_{l}\:\psi\:(L;f).\) In order to achieve the best possible enactment of the exemplary when dealing with an imbalanced classification problem, it is necessary to reduce the classification cost. The aforementioned cost can be transformed into a problem of least possible reduction,
The symbol \(\:\mu\:\) denotes the highest possible value for the number of false positive rates, while \(\:{F}_{l}\) signifies the maximum number of features that may be utilized by the \(\:{l}^{th}\:layer\) of a single classifier. The functional relationship in the middle of\(\:\:\psi\:(l-1;f),\:l\), and \(\:n\:\)can be supplementary resulting based on the marginal and conditional likelihoods. Assuming that,
where \(\:{\beta\:}_{1},{\beta\:}_{2},\:\dots\:\dots\:.,\:{\beta\:}_{l}\) are given that the variables are constants, the minimization issue in Eq. (15) can be reformulated as follows:
The overall algorithm of AETL is described in algorithm 1 below.
Recovery of compromised nodes
The recovery procedure will be started if the database does not satisfy the security standards. The program-loaded recovery method is employed when a limited number of nodes (fewer than 10–15%) have been compromised. In this instance, we reinstall the software on each hacked node. The objective is to restore compromised nodes expeditiously. We analyze the old block picture against the current image and refresh the discrepancies. A FetchCheckpoint Message is initiated when the AETL identifies a failure and starts the restoration of the state prior to the failure. A FetchCheckpointReply encompasses the most recent checkpoint of the database59. The disk and database under AETL monitoring will revert to the most recent image stored at the base station. Any faulty or tainted data may be discarded during this procedure.
Proposed HDOMLM algorithm based LAn assortment
In this cluster head selection algorithm, we are make sequential optimization of cluster formation and LAn selection using PSO and O-MLM respectively. The overall flow is shown in Fig. 6. The weight of each node is used to decide whether or not to become a cluster head for the current round. The weight is the significant feature of input to the proposed leaning based LA prediction of HDOMLM. Each node in the cluster consumes more energy, due to the long distance between the sensors and the base station, which lowers the life expectancy of the network. The increase in lifetime of the network is possible with high energy preservation, low delay and lowest distance, the presence of more alive nodes and so on. To save resources of each node and increase the optimal performance of HDOMLM, it is modelled with mobility, energy, distance and delay. The optimization in prediction of LA node attained by achieving all these metrics in the feature learning and detection using HDOMLM.
PSO based cluster formation
The optimization protocol of \(\:PSO\) that relies on a population of particles. The system initializes the random solutions with a population and searches for optimal solutions in every single generation60. The cluster is created by the use of a base station or sink, employing a centralized clustering approach.
The individual node fitness can be evaluated after generating the initial population. For best results, the cluster members in each cluster should able to communicate to each other. Hence the fitness function is defined based on the distance of nodes. The major parameter used in the fitness evaluation is network nodes-BS distance. Based on the distance of each nodes the number of selected clusters are formed using PSO iteration and convergence. The process can be summarized in the following steps:
Step 1: The problem is transformed into the PSO space, where the PSO particle is represented by two dimensions: particle position and velocity.
Step 2: Calculation of the fitness value by the utilization of a fitness function. The fitness function we propose for clustering based on Particle Swarm Optimization (PSO) aims to optimize the average distance between the member nodes. The particle’s fitness value is determined by calculation,
Step 3: Production of novel particles from the initial solution. The process of creating a new particle from an existing one is referred to as particle creation.
Step 3.1: The estimation of the new velocity involves determining the rate at which the position of a given particle is changing. The calculation for the new velocity is as follows.
where ω is inertia weight and w1 and w2 are basic PSO tuning parameters.
Step 3.2: Estimation of new position of the particle is as follows.
Step 4: Computation of the fitness value for newly generated particles. The fitness value of the new particles is determined by applying the fitness function in Step 2 to the updated velocity and position.
Step 5: Fitness value of old particle and new particle is compared and the best one is selected for the next iteration:

Step 6: During each iteration, a single optimal solution is chosen as the local best solution. The particle with the highest fitness value in the current iteration is chosen as the solution.
Step 7: The local best solutions from all iterations of the particle in which has maximum among all solutions are selected as a global best solution. The final solutions are decoded into clusters.
O-MLM based CH node selection from the clusters of PSO
Derivation of selection metrics as features for machine learning model is the primary part of this Optimized Machine Learning Model (O-MLM). Delta difference, Average Distance, Related Energy, Related Mobility and Average transmission Delay are features taken for the learning model.
After the cluster formation using PSO, the Leading node selection is performed for all the cluster members in each cluster. The features are extracted for these cluster members as selection metrics of Delta difference, Average Distance, Related Energy, Related Mobility and Average transmission Delay as described below. Once these features are extracted from the nodes gathered information, we use the O-MLM model to predict the particular feature set belongs to normal node or leading node. O-MLM model is trained with prelabelled features. The formation of O-MLM model is described in the following section.
The delta difference is employed as a criterion for load balancing. While it is possible for all clusters to have an equal number of nodes in some instances, achieving this in real-world scenarios is challenging owing to factors like as the changing positions of sensor nodes and other external impacts. Delta difference \(\:{\varDelta\:}_{d}\) is represented as,
where \(\:{I}_{\theta\:}\) is ideal degree of the nodes in MANET set as 45o and \(\:{N}_{\theta\:}\) is individual nodes’s mobility degree from RWP model. Average distance is evaluated between the corresponding neighboring nodes and LAn61and it is given by,
where, M is the aggregate count of neighboring nodes inside the respective cluster and \(\:{D}_{m}\:\)is distance in the middle of neighbor node and LAn of the same cluster. Related energy is computed by the ratio of energy utilization between member nodes of cluster and LAn to the energy between sequent nodes.
K represents the number of clusters in the network, whereas M represents the number of cluster members in each cluster, \(\:{E}_{i}\) is energy of i-th member node in the j-th cluster and \(\:{E}_{C,j}\) is energy of LAn in the j-th cluster.
This paper proposes that the clustering process must include the mobility of individual nodes in relation to their nearby nodes called as related mobility. A node should not be designated as a cluster leader if it exhibits significant mobility compared to its neighbors, as this increases the possibility of cluster fragmentation and requires re-clustering. We should endeavor to choose a node that exhibits less mobility in comparison to its neighbors for the position of leading agent. Consequently, LA should have the lowest relative mobility and the largest residual battery power to ensure enhanced stability inside the clusters. Related mobility is ratio of sum of mobility distance between and nodes to LAn and LAn to BS to the mobility of nodes in the same cluster which is represented as,
The variable \(\:DL{A}_{j,i}\) represents the distance between the i-th member node and the j-th leading agent and LA\(\:{B}_{j}\) is the distance in the middle of j-th leading agent node to BS. \(\:{d}_{i,j}\) is the distance between to member nodes in each cluster. Average delay of each node is computed by averaging the time consumption in each slot for each node.
where \(\:{\tau\:}_{i,j}\) is the maximum delay of all i-th member nodes in the j-th cluster.
This study introduces a novel approach in the clustering process of Mobile Ad hoc Networks (MANETs) by utilizing machine learning (ML) to classify nodes as either regular nodes or Leading Agent nodes (LAns). The classification is based on chosen metrics that are used as features.
By utilizing machine learning methods such as Support Vector Machines (SVM), decision trees, neural networks, ensemble learning, K-Nearest Neighbors (KNN), and naïve Bayes, we may attain high classification accuracy. We are now deploying the optimized Machine Learning model (O-MLM). In this approach, the ML model may be selected by optimizing the hyperparameters to achieve the best classification accuracy and minimize the loss simultaneously.
This O-MLM algorithm chooses the most optimal machine learning model together with their respective hyperparameters for the training process, based on the available ML models with task scheduling62. The system use Bayesian optimization to choose models and their corresponding hyperparameter values. It then calculates the cross-validation classification error for each model. Once the optimization process is finished, O-MLM provides the model that has been trained on the full data set and is anticipated to accurately categorize fresh data.
To train its Gaussian process model of the objective function, Bayesian optimization uses objective function evaluations. A new feature of Bayesian optimization is the acquisition function, which determines the next point to assess.
The acquisition function can balance sampling at low-modeled objective functions with investigating unmodeled areas. O-MLM’s Bayesian optimization maintains a multi-Tree Bagger objective function model. This means the objective function model splits by learner type and becomes a Tree Bagger ensemble for regression for each learner.
The objective of hyperparameter optimization in machine learning is to identify the hyperparameters of a specific machine learning algorithm that yield the optimal performance, as evaluated on a validation set. Bayesian methods, as opposed to random or grid search, maintain a record of previous evaluation outcomes. They utilize this information to construct a probabilistic model that links hyperparameters to the likelihood of achieving a certain score on the objective function.
We used Expected improvement for acquisition function. Typically, acquisition functions rely on past observations and the hyperparameters of the Gaussian Process (GP). We represent this reliance as\(\:\:a\left(x;\left\{{x}_{n},{y}_{n}\right\},\theta\:\right)\). There are multiple widely favored options for the acquisition function. In the context of the Gaussian process prior, these functions are exclusively dependent on the model by means of its predictive mean function \(\:\mu\:\left(x;\left\{{x}_{n},{y}_{n}\right\},\theta\:\right)\) and predictive variance function\(\:{\:{\upsigma\:}}^{2}\left(x;\left\{{x}_{n},{y}_{n}\right\},\theta\:\right)\). As we move forward, we will represent the best current value as \(\:{x}_{best}=\underset{{x}_{n}}{argmin}\:\left\{f\left({x}_{n}\right)\right\}\), and the cumulative distribution function of the standard normal will be denoted as\(\:\:{\Phi\:}\left(.\right)\). Specifically, the Expected Improvement function is utilized in the job that we are doing. An evaluation of the expected amount of progress in the objective function is performed by the ‘expected-improvement’ family of acquisition functions. This family of functions disregards values that result in an increase in the objective. To put it another way, the location of the lowest posterior mean is what we mean when we talk about\(\:{\:x}_{best}\). The lowest value of the posterior mean is denoted by the symbol\(\:\:\mu\:Q\left({x}_{best}\right)\). Consequently, the anticipated enhancement is provided by,
Results and discussion
The proposed intrusion detection and cluster head selection using AETL and HDOMLM is experimentally evaluated and compared with earlier implementations in this section. MATLAB 2020a version simulation tool is used to implement the software development of the proposed algorithm of MANET. 200 m length squared area is configured for the network space. Within this area coverage range of 50 m of 50 sensor nodes with single sink node is considered. The RWP mobility access the velocity of 20 ms− 1. The delay of each transmission between the nodes takes 0.01s. From the 50 nodes of sensor nodes, 5 nodes i.e. 0.1% is for Leading Agent nodes. the energy model of our is followed the same from the radio propagation model. 20% of nodes are taken as malicious nodes in the network i.e. 10 nodes out of 50 nodes. the optimization configuration is listed in Table 2.
For training in the optimized machine learning model of AETL and HDOMLM, we considered randomly generated network topology of 100 different to create the database. For the database of AETL, 100 scenarios and 50 nodes, 10 nodes will be malicious nodes and it is labelled as type 2 and simultaneously for type 1 is normal nodes. for classification of AETL model, three features of energy, PDR and routing overhead are configured for input features of training. Finally, 5000 × 3 is the dimension of AETL learning input data. In the database of HDOMLM, for each scenario, we are considering the 50 nodes in the network. Each node has 5 selection metrics to classify that as normal node or cluster head node. The training input information for single node is 5. Total of 100 scenarios and 50 nodes has 5000 × 5 dimensioned database for training and 5000 × 1 for training label with classes of either 1 or 2. The class 1 denotes that the node belongs to normal and class 2 considered as LA nodes. The performance analysis of the proposed work is segregated for two contents of intrusion detection and the graphical view is shown in Fig. 7. The attacker node characteristics are included in the simulation level as highest overhead, less transmission of packet (dropping the received packets) and energy consumption for each transmission will be high.
The training data formation is modelled with dynamic MANET environment. As the environment changes, expending the configuration details, simulation methodology will mathematically derive the metrics of decision to form the training information sets. Based on the current environment of MANET, the label of nodes in detection can be assigned by pre-labelled data comparison. For example, when we considered initial energy as 0.1, the consumed energy leads to high of 0.05 i.e. 50% of initial energy at first round itself, then we labelled the corresponding node as Attack in the training. Suppose if the initial energy is changed for network configuration, it automatically labelled with high consumption of energy as > 50% of initial energy. Like this for other decision metrics of overhead and PDR. Based on the mathematical calculation from the current MANET configuration, the training data can be revised to adapt multiple environments.
Qualitative analysis of the network, intrusion detection and clustering
Figure 8 depicts the network topology of 50 nodes. the nodes position is generated by random manner. Figure 9 for the malicious nodes detection using proposed AETL. After this intrusion detection and recovery, PSO based clustering is performed as to produce the cluster output of Fig. 10 for cluster formation and initial cluster head selected based on cluster centroid is shown in Fig. 11. The formation and initial cluster head selected based on cluster centroid is shown in Fig. 11.
Quantitative analysis of proposed
In this implementation, for performance analysis number of metrics are evaluated such as Network Residual Energy, Energy Tax, Network Energy Utilization, Total Packets Received, Packet Delivery Ratio, Packet Loss Ratio, Throughput, Alive Nodes, Dead Nodes, Average Delay, Total time consumption, Jitter. The mathematical representation of these metrics are given below.
-
1.
Network Residual Energy
$$\:Network\:Residual\:Energy=\:\frac{\sum\:_{i=1}^{N}\left|{E}_{i}-{E}_{c}\right|}{N}\:\:\:$$(34) -
2.
Energy Tax
$$\:Energy\:Tax=\frac{Residual\:Energy}{Transmitted\:Packets*N}\:\:\:\:\:$$(35) -
3.
Network Energy Utilization
$$\:Network\:Energy\:Utilization=\:\sum\:_{j=1}^{K}\left[C{H}_{E}\left(j\right)+\sum\:_{{m}_{j}=1}^{M}{S}_{E}\left({m}_{j}\right)\right]\:\:\:\:$$(36)where N is number of nodes, K is number of cluster heads and M is number of member nodes in each cluster.
-
4.
Packet Delivery ratio
$$\:PDR=\frac{\sum\:_{i=1}^{N}Pa{c}_{R}^{i}}{\sum\:_{i=1}^{N}Pa{c}_{T}^{i}}\:$$(37)where \(\:Pa{c}_{R}^{i}\) is the number of packets received by the i-th node and \(\:Pa{c}_{T}^{i}\) is the number of packets transmitted by the i-th node in the network.
-
5.
Packet Loss Ratio
$$\:PLR=\frac{\sum\:_{i=1}^{N}\left(Pa{c}_{T}^{i}-Pa{c}_{R}^{i}\right)}{N}\:\:$$(38) -
6.
Throughput
$$\:Throughput=\frac{\sum\:_{i=1}^{N}Pa{c}_{T}^{i}}{Time\:Taken}\:$$(39) -
7.
Jitter
$$\:Jitter=\sqrt{\frac{1}{{N}_{p}}*\sum\:_{p=1}^{{N}_{p}}{({D}_{p}-D)}^{2}}$$(40)where \(\:{N}_{p}\) is the number of packets received, \(\:{D}_{p}\) is the delay of current p-packet receiving, \(\:D\) is the average delay of all the packets.
Figure 12 depicts the residual energy of the nodes in the network for increasing number of rounds. In this we are comparing the performance with existing methods of CCCH63 and ANFIS-EESC64. Our proposed model HDOMLM is compared like with malicious and without malicious and application of AETL with malicious scenario. ANFIS-EESC and CCCH methods are live upto 500 and 700 rounds respectively which is 400 and 200 rounds earlier than HDOMLM proposed method even with malicious. Without malicious means HDOMLM doesn’t lose the life even at 1000 iteration as shown in Fig. 9 and the residual energy is increased at AETLID with HDOMLM of 0.00485.
As number of nodes increases, the residual energy will automatically increase due to highest number of nodes individual energy cumulating as shown in Fig. 13.
Figure 14 illustrates the energy tax metric for number of increasing rounds of process. Energy tax is the ratio of residual energy to the product of transmitting packets and number of nodes. When the energy tax is less, the network energy saving is increased. Hence as shown in Fig. 11, the HDOLML + AETLID is providing very low energy tax of 0.413. Figure 15 depicts the performance of the same energy tax vs. different number of nodes. Even at 400 nodes, the energy tax of proposed model is 1.4256 which is 50% less than ANFIS-EESC method.
In Table 3, we enumerated the sample features of training considered for the intrusion detection using AETL method. Three features and the corresponding target labels are shown as malicious or normal node. In Table 4, we shown the sample training features and target labels of LA node or member nodes of each case of network node.
From Figs. 16, 17, 18 and 19, we shown the performance of network lifetime in terms of alive nodes in Figs. 16 and 17 and dead nodes in Figs. 18 and 19 respectively. As number of rounds increasing the alive nodes are getting reduced from the number of nodes as shown in Fig. 16. But, at the round of 1000 also, the proposed HDOMLM + AETLID is still alive with nodes of 20 out of 50 which is 4 times higher than only HDOMLM without malicious. For ANFIS and CCCH case, it reaches zero even before the 1000 rounds.
In Fig. 17, the alive nodes vs. number of nodes is depicted. As nodes increasing alive nodes will increase. Even at 400 nodes 378 nodes are still alive in HDOMLM + AETLID which increasing network lifetime. Figures 18 and 19 represents the dead nodes as increasing processing round and increasing number of nodes in MANET respectively. These are the graphical curves of inverse view of alive nodes in the network. As efficient system, HDOMLM + AETL getting lowest dead nodes than others.
Figure 20 shows the packet delivery ratio of proposed and existing methods as increasing number of rounds. As rounds increasing the PDR reached to one for proposed in the ascend order of HDOMLM + AETL with malicious, HDOMLM without malicious and HDOLML with malicious.
HDOMLM providing best results in the case of without malicious and it degrades when intrusion introduced. This case performance is improved by HDOMLM + AETL as shown in Fig. 21 of total packets delivery at CH nodes. At round 1000, our method attains 6500 which is 500, 1100, 1400, 2320 packets higher than HDOMLM without malicious, HDOMLM with malicious, CCCH and ANFIS-EESC methods respectively.
Figure 22 is illustration of average delay of transmission increasing as increasing rounds. Figure 23 shows the overall time taken for each round to IDS and LAn assortment and Transmission slots. By comparing both the figures, time taken of HDOMLM + AETL is slightly higher than only HDOMLM due to additional process of IDS and for delay of transmission HDOMLM + AETL attains the low delay due to combination of IDS and LAn prediction.
Table 5 is the intrusion detection performance of proposed AETL algorithm for different metrics and different number of nodes. As nodes increasing the performance of IDS getting increased. Figure 24 depicts the confusion matrix of AETL, in which the overall accuracy is reached to 99.3%. Green marked boxes denote the correctly classified samples and blue boxes are misclassified. The testing case samples of 1250 are used to compute the confusion matrix. Out of this 1250 samples are 995 are correctly classified as normal nodes and 246 are correctly classified as malicious nodes. 5 nodes and 4 nodes misclassified nodes of normal and malicious respectively. Hence the error percentage is 0.7.
Computation complexity analysis of proposed work
Energy efficiency
Instead of using multiple nested decision for multiple metrics to make the system with acceptable accuracy of detection, here we used learning for both cases of detection individually. The computational complexity of AETL and O-MLM is given in the Table 6. To reduce the delay of decision and energy consumption in selection of leading agent, we implemented the learning based prediction especially for resource constrained MANET nodes. Because once the trained model is loaded into the nodes, the delay and energy consumption to predict the intrusion nodes and leading agent nodes is too low for proposed method than conventional deciding protocol loops. Hence the overall energy efficiency improved in our proposed ML models.
The parameters in the computation of complexity are w (number of samples in the database), L ( Dictionary length), T (number of trees in RF), m (number of features), d (depth of RF), \(\:{I}_{i}\) (number of iterations), \(\:{A}_{t}\) (Average execution time), h (number of hypothesis for selecting ML method) and N (Number of classifiers).
Scalability
As number of nodes increasing in the large networks, it increases overhead to perform clustering in BS. As the nodes increasing in network, the number of clusters will be increased by the BS. Hence the PSO form the highest number of clusters based on the best distance from the nodes in large networks which makes the convergence as early as possible compared with earlier implementations of clustering. In Fig. 19, we shown the evaluations of scalability by increasing the number of nodes in the network from 50 to 400. It depicts the proof of the our proposed method attains the best network lifetime than other methods. Evaluating network scalability is a crucial process in confirming that a network can accommodate growth efficiently. This procedure often entails simulating heightened network traffic with increased number of nodes to assess the network’s performance under duress. Critical metrics including Latency, Jitter, Throughput, QoS, and Packet loss are evaluated to determine the network’s capacity to uphold performance standards during heightened demand.
Figure 25 illustrated the jitter performance for increasing number of nodes in the network. The network nodes range from 50 to 400. As the number of nodes increasing, the jitter increasing. In this Fig. 25, we shown the jitter results in milliseconds. Compared with existing methods, the proposed HDOMLM + AETLID reached to low value of 0.212 s. This is 0.3 s less than the CCCH and ANFIS-EESC methods.
When the number of nodes increased in the network, the traffic congestion makes the communication to be error. This will increases the PLR as nodes increases. In Fig. 26, we shown the Path loss for the scalability measure. At the nodes count of 50, path loss for proposed method is 0.001 and at 400 nodes, PLR is 0.01. Compared with existing methods, proposed HDOMLM + AETLID model is highly efficient as shown in Fig. 0.02 and 0.019 less PLR achieved in proposed method than ANFIS-EESC and CCCH respectively.
The energy utilization characteristics to show the scalability of network Fig. 27 depicts. As the energy utilization is less, the network lifetime getting increased. Figure 27 illustrated that our proposed method has the low energy utilization of 0.0007 J at 50 nodes and the same criteria of 0.014 J attained at 400 nodes scenario also. This energy utilization is very less than ANFIS-EESC, CCCH as 0.092 J and 0.063 J respectively at 50 nodes.
Figure 28 depicts the throughput measurement for different number nodes configured network. The packet loss ratio is less in our proposed method which automatically increases the throughput. As number of nodes increases, the packets received with error is increased. Thus it reduces the throughput also as shown in Fig. 28. The proposed method HDOMLM + AETLID is achieved a highest throughput of 1000Mbps at node 50 and 875Mbps at node 400. This results proven that our proposed method provide the high throughput than other existing methods.
Figure 29 illustrated the latency performance for different number of nodes. The latency is low in terms of proposed HDOMLM + AETLID due to the time required for the computation of delivery probability as well as the iterations of PSO clustering approach.
The proposed approach also improved the network latency, especially for larger node structures. For 50 nodes, the average latency was noted to be 0.8 s, and for 400 nodes, it was reduced to 1.22 s only through proposed method of HDOMLM + AETLID, indicating that it can handle a greater number of nodes without a high delay as shown Fig. 29.
Reliability
To show the efficiency of our proposed in terms of reliability, we shown the QoS performance for different scenario of different mobility, different attacker rate and different nodes densities in Table 7.
In Table 7, for different node density we considered two cases of small network of nodes 50 and large network of nodes 500. For smaller network, the QoS value of proposed method HDOMLM + AETLID is 0.9141. This QoS value is 11.35% higher than the existing method of ANFIS-EESC. The difference of QoS between larger network and smaller network is 0.0377 which is 4.2% only in our proposed HDOMLM + AETLID. This clearly shows that our proposed algorithm attains the effective scalability. As increasing the node’s mobility from low speed to high speed, the QoS values will be decreased for all the methods. Proposed HDOMLM + AETLID obtained the QoS values of 0.8917 and 0.7083 with low speed of mobility(20 m/s) and high speed of mobility(200 m/s) respectively. As the speed increasing 10 times than low speed of 20 m/s, the 0.1834 of QoS difference achieved which shows our proposed methods reliability. For different attacker rate, the QoS is evaluated for proposed and existing methods. For low attacking rate, here we considered number of attacker nodes is less the 15% of number of nodes in the network and the same manner of greater than 15% and less than 50% for high attacker rate. The proposed method’s QoS value at low attacker rate is 0.8849 and it is 14.03% & 20% higher than existing methods of CCCH and ANFIS-EESC respectively. Even at the high rate of attackers in the network, the proposed method HDOMLM + AETLID lags of 0.2337 of QoS than low attacking rate scenario.
Discussion
The HDOMLM-based blustering outperforms both regular clustering and non-clustering methods. Consequently, the throughput reached the optimal condition, while the delay and packet loss rates diminished. Furthermore, the packet delivery rate has been enhanced. This results from the HDOMLM approach used in our clustering strategy, which may modify the network’s dynamic behavior and judiciously select ideal nodes for grouping based on their content popularity distribution and mobility patterns. Clustering nodes with like features can decrease competition for channel access and packet collisions, hence enhancing network performance.
This study’s results highlight the importance of considering clustering and node density in the design and optimization of MANETs. The suggested clustering approach utilizing the HDOMLM can enhance throughput latency and packet delivery ratio. This is a crucial component, particularly in applications requiring the transmission of real-time data. The findings indicate that the suggested model outperforms the alternatives. The performance study include energy usage, throughput, packet delivery, jitter, network longevity, and related metrics.
Based on the clustering applications, the requirement of fault tolerance will differ. In the resource constrained Leading agent selection in MANET nodes, implementing fault tolerance often requires additional steps like selecting backup nodes, monitoring node health, and re-assigning data in case of failure, which can significantly increase the algorithm’s complexity and make it harder to understand and maintain. In our work, recovery of nodes is already implemented. Hence adding fault tolerance might not be necessary which further increase the complexity. So, it is not included in this work.
The proposed algorithm is adaptively predicting the clusters based on the current node’s position which decides the cluster size in clustering. Mostly the selection of CH nodes maintains the equal coverage and parallel maintenance of all nodes in the network which mostly reduces the Re-clustering in the network. Re-clustering will be taken place due to the network having the cluster size is too big or too small. This is considered and overcome with our proposed equalized and adaptive clustering method.
It enhances clustering by extending node lifespan inside the network, minimizing the number of clusters, lowering re-affiliation frequency, boosting cluster stability, and assuring effective resource management. The lack of a centralized authority renders the mobile ad hoc network vulnerable to numerous security attacks, as the wireless link is accessible to all users. In this performance investigation, when the attacker rate escalates, the HDOMLM + AETLID achieves superior QoS values compared to previous techniques.
Conclusion
We suggested a new, simple machine learning model that combines AETL and HDOMLM to build intelligent and efficient processing for intrusion detection and leading agent node assortment in MANET. In this research, we show how to use the Adaptive Ensemble Tree Learning (AETL) Model to detect and measure MANET incursions. Intrusion detection in MANET services is the purpose of the proposed technique. The optimality of LAn selection is guaranteed by the Hybrid Dual Optimization of Machine Learning Model (HDOMLM). To add insult to injury, in order to keep energy consumption low, the function of centrally and optimally decide on LAn is not evolved in distant BS but is instead limited to the local mobile wireless network. The performance of the suggested system is compared to that of ANFIS-EESC and CCCH through the use of simulated assessments. The proposed HDOMLM + AETL has an energy tax of 0.4, which is 71% less than the ANFIS-EESC. When compared to the combined effects of AETL and HDOMLM, the network lifespan of HDOMLM alone is 50.12% shorter. Regardless, only HDOMLM outlives CCCH by 18.64% and ANFIS-EESC by 29.35% on average. When compared to alternative methodologies, the metrics used to evaluate the performance of the proposed method classification accuracy, attack detection rate, and F-Measure are greater, according to the AETL based IDS findings. In this present work, we focused on the typical intrusions of network layer level in MANET. For future implementations, we include the analysis for other layer attacks and different types of attacks in each layer with recent update like zero-day exploits. The recovering of nodes after the intrusion detection is performed in this work to avoid the interruption in the network communication for immediate recovery nodes by reinitialize the compromised nodes. The efficient attack level recovery mechanism will be designed to maintain the network performance in balanced with the energy efficiency and delay drop with multi-level attack recovery mechanisms based on compromised nodes. Together with intrusion detection systems and critical infrastructure security, we may build a fault tolerant trustworthy multi-path routing architecture for MANET in the future work, which will define efficient MANET communication.
Data availability
The Datasets used and /or analysed during the current study available from the corresponding author on reasonable request.
References
P, R. P. & Shankar, S. Secure intrusion detection system routing protocol for mobile ad-hoc network. Glob. Transitions Proc. 3(2), 399–411. (2022).
Veeraiah, N. et al. Trust aware secure energy efficient hybrid protocol for MANET. IEEE Access. 9, 120996–121005 (2021).
Srilakshmi, U., Alghamdi, S., Ankalu, V. V., Veeraiah, N. & Alotaibi, Y. A secure optimization routing algorithm for mobile ad hoc networks. IEEE Access. 10, 14260–14269 (2022).
Rajabi, S., Jamali, S. & Javidan, J. An intrusion detection system in computer networks using the firefly algorithm and the fast learning network. Int. J. Wine Res. 3(1), 50–56 (2020).
Ghori, M. R., Wan, T. C. & Sodhy, G. C. Bluetooth low energy mesh networks: survey of communication and security protocols. Sensors 20(12), 3590 (2020).
Fahmy, H. M. A. Wireless sensor networks essentials, in: Wireless Sensor Networks, Springer, Cham, 3–39. (2020).
Sugi, S. S. S. & Ratna, S. R. Investigation of machine learning techniques in intrusion detection system for IoT network. In 2020 3rd International Conference on Intelligent Sustainable Systems (ICISS), 1164–1167 (IEEE, 2020).
Zhang, H., Lin, K. Y., Chen, W. & Genyuan, L. Using machine learning techniques to improve intrusion detection accuracy. In 2019 IEEE 2nd International Conference on Knowledge Innovation and Invention (ICKII), 308–310 (IEEE, 2019).
Alavizadeh, H., Alavizadeh, H. & Jang-Jaccard, J. Deep Q-learning based reinforcement learning approach for network intrusion detection. Computers 11(3), 1–19 (2022).
Singh, S. et al. Wireless body area routing protocols impact analysis on entity mobility models with static sink node. Appl. Sci. 12(11), 5655 (2022).
Sun, G. et al. Cost-efficient service function chain orchestration for low-latency applications in NFV networks. IEEE Syst. J. 13(4), 3877–3888 (2018).
Zhang, M., Zhang, Y., Cen, Q. & Wu, S. Deep learning-based resource allocation for secure transmission in a non-orthogonal multiple access network. Int. J. Distrib. Sens. Netw. 18(6), 155013292211043 (2022).
Wang, P. et al. Server-initiated federated unlearning to eliminate impacts of low-quality data. IEEE Trans. Serv. Comput. 17(3), 1196–1211 (2024).
Xu, G. et al. A model value transfer incentive mechanism for federated learning with smart contracts in AIoT. IEEE Internet Things J., 1. (2024).
Sun, G., Li, Y., Liao, D. & Chang, V. Service function chain orchestration across multiple domains: a full mesh aggregation approach. IEEE Trans. Netw. Serv. Manage. 15(3), 1175–1191 (2018).
Bi, B., Huang, D., Mi, B., Deng, Z. & Pan, H. Efficient LBS security-preserving based on NTRU oblivious transfer. Wireless Pers. Commun. 108(4), 2663–2674 (2019).
Kancharakuntla, D. & El-Ocla, H. EBR: routing protocol to detect blackhole attacks in mobile ad hoc networks. Electronics 11(21), 3480. https://doi.org/10.3390/electronics11213480 (2022).
Alazab, M. & Hobbs, M. Machine learning approaches for intrusion detection in MANETs. J. Netw. Comput. Appl. 70, 102–120 (2023).
Singh, C. E. & Vigila, S. M. C. WOA-DNN for intelligent intrusion detection and classification in MANET services. Intell. Autom. Soft Computing/Intelligent Autom. Soft Comput. 35(2), 1737–1751 (2023).
Boualouache, A. & Engel, T. A survey on machine learning-based misbehavior detection systems systems for 5G and beyond vehicular networks. IEEE Commun. Surv. Tutorials/IEEE Commun. Surv. Tutorials. 25(2), 1128–1172 (2023).
Cheng, H., Shojafar, M., Alazab, M., Tafazolli, R. & Liu, Y. PPVF: privacy-preserving protocol for vehicle feedback in cloud-assisted VANET. IEEE Trans. Intell. Transp. Syst. 1–13 (2021).
Prasad, M., Tripathi, S. & Dahal, K. Wormhole attack detection in ad hoc network using machine learning technique. In In 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), 1–7 (IEEE, 2019).
Jhanjhi, N. Z., Brohi, S. N., Malik, N. A. & Humayun, M. Proposing a hybrid RPL protocol for rank and wormhole attack mitigation using machine learning. In In 2020 2nd International Conference on Computer and Information Sciences (ICCIS), 1–6 (IEEE, 2020).
Wang, T. et al. A weighted corrective fuzzy reasoning spiking neural P system for fault diagnosis in power systems with variable topologies. Eng. Appl. Artif. Intell. 92, 103680 (2020).
Singh, M. M., Dutta, N., Singh, T. R. & Nandi, U. A technique to detect wormhole attack in wireless sensor network using artificial neural network. In Evolutionary Computing and Mobile Sustainable Networks, 297–307 (Springer, 2020).
Srilakshmi, R. & Muthukuru, J. Intrusion detection in mobile ad-hoc network using hybrid reactive search and bat algorithm. Int. J. Intell. Unmanned Syst. vol. ahead-of-print, no. ahead-of-print, (2021).
Goyal, N., Sandhu, J. K. & Verma, L. CDMA-based security against wormhole attack in underwater wireless sensor networks. In Advances in Communication and Computational Technology, 829–835 (Springer, 2021).
Wang, S. et al. Service composition in cyber-physical-social systems. IEEE Trans. Emerg. Top. Comput. 8(1), 82–91 (2020).
Ni, T. et al. Architecture of cobweb-based redundant TSV for clustered faults. IEEE Trans. Very Large Scale Integr. VLSI Syst. 28(7), 1736–1739 (2020).
Amutha, J., Sharma, S. & Sharma, S. K. Strategies based on various aspects of clustering in wireless sensor networks using classical, optimization and machine learning techniques: review, taxonomy, research findings, challenges and future directions. Comput. Sci. Rev. 40(40), 100376 (2021).
Jiang, Y. & Li, X. Broadband cancellation method in an adaptive co-site interference cancellation system. Int. J. Electron. 1–21 (2021).
Ahmadi, M. et al. DQRESCnet: a novel hybrid approach for selecting users in federated learning with deep-q-reinforcement learning based on spectral clustering. J. King Saud Univ.-Comput. Inf. Sci. (2021).
Tama, B. A. & Lim, S. Ensemble learning for intrusion detection systems: a systematic mapping study and cross- benchmark evaluation. Comput. Sci. Rev. 39(39), 100357 (2021).
Chen, J., Liu, Y., Xiang, Y. & Sood, K. RPPTD: robust privacy-preserving truth discovery scheme. IEEE Syst. J. 1–8 (2021).
Sultana, T., Mohammad, A. A. & Gupta, N. Importance of the considering bottleneck intermediate node during the intrusion detection in MANET. In Research in Intelligent and Computing in Engineering, 205–213 (Springer, 2021).
Sultanuddin & Hussain, M. A. Intrusion detection in manet through machine learning approach. Int. J. Innovative Technol. Exploring Eng. 11(3), 1–6 (2022).
Ali, M. H. Network Intrusion Detection in MANET Using Improved Whale Optimization Algorithm-SVM, vol. 13 (Tikrit University, 2022).
Jayakanth, J. J. & Madhumati, G. L. A novel approach for intrusion detection system using equalized multi-routing protocol in MANET. Int. J. Intell. Syst. Appl. Engineering(IJISAE). 11(6s), 86–95 (2023).
Singh, C. E. & Vigila, S. M. C. Fuzzy based intrusion detection system in MANET. Meas. Sens. 26, 100578 (2023d).
Sultan, M. T., Sayed, H. E. & Khan, M. A. An intrusion detection mechanism for MANETS based on Deep Learning Artificial neural networks (ANNS). Int. J. Comput. Networks Commun. 15(01), 01–15 (2023).
Gupta, M., Vashishth, T. K. & Verma, P. K. Machine learning and deep learning based intrusion detection for blackhole attacks in mobile ad-hoc networks. Multidisciplinary Sci. J. 6(11), 2024209 (2024).
Mohammadi, S., Balador, A., Sinaei, S. & Flammini, F. Balancing privacy and performance in federated learning: a systematic literature review on methods and metrics. J. Parallel Distrib. Comput. 192, 104918 (2024).
Hassan, S. M., Mohamad, M. M. & Muchtar, F. B. Advanced intrusion detection in MANETs: a survey of machine learning and optimization techniques for mitigating black/gray hole attacks. IEEE Access. 1 (2024).
Sheela, M. S. et al. Adaptive marine predator optimization algorithm (AOMA)-deep supervised learning classification (DSLC) based IDS framework for MANET security. Intell. Converged Networks. 5(1), 1–18 (2024).
Rajan, N., Kiran, M. V., K, V., Jaiswal, S. & Nithya, B. Two-pronged intrusion detection system for MANET. In 2024 International Conference on Emerging Technologies in Computer Science for Interdisciplinary Applications (ICETCS), Bengaluru, India, 1–6 (2024).
Zhou, W. et al. HIDIM: a novel framework of network intrusion detection for hierarchical dependency and class imbalance. Comput. Security 104155 (2024).
Bai, L., Han, P., Wang, J. & Wang, J. Throughput maximization for Multipath Secure Transmission in Wireless Ad-Hoc Networks. IEEE Trans. Commun. 72(11), 6810–6821 (2024).
Li, C. et al. RFL-APIA: a Comprehensive Framework for mitigating poisoning attacks and promoting model aggregation in IIoT Federated Learning. IEEE Trans. Industr. Inf. 20(11), 12935–12944 (2024).
Wang, G., Yang, J. & Li, R. Imbalanced SVM-based anomaly detection algorithm for imbalanced training datasets. ETRI J. 39(5), 621–631 (2017).
Krishnamoorthy, V. K. et al. Energy saving optimization technique-based routing protocol in mobile ad-hoc network with IoT environment. Energies 16, 138 (2023).
Sirmollo, C. Z. & Bitew, M. A. Mobility-aware routing algorithm for mobile ad hoc networks. Wirel. Commun. Mob. Comput. 2021, 1–12 (2021).
Popli, R., Sethi, M., Kansal, I., Garg, A. & Goyal, N. Machine learning based security solutions in MANETs: state of the art approaches. J. Phys. Conf. Ser. 1950(1), 012070 (2021).
Malik, A., Khan, M. Z., Faisal, M., Khan, F. & Seo, J. T. An efficient dynamic solution for the detection and prevention of black hole attack in VANETs. Sensors 22(5), 1897 (2022).
Rani, P., Kavita, N., Verma, S. & Nguyen, G. N. Mitigation of black hole and gray hole attack using swarm inspired algorithm with artificial neural network. IEEE Access. 8, 121755–121764 (2020).
Rubi & Popli, R. A worm hole attack detection in mobile AD-HOC network using GA and SVM. Int. J. Eng. Appl. Sci. Technol. 5(3), 582–588 (2020).
Zhai, A. Guohua Fan, Regression Tree Ensemble Rainfall–Runoff Forecasting Model and Its Application to Xiangxi River, China, MDPI (2022).
McMackin, L. Regression Tree Ensembles For Irish Property Valuation, (2018).
Peibei, S. H. I. & Zhong, W. A. N. G. An ensemble Tree Classifier for highly imbalanced data classification. J. Syst. Sci. Complex. (2021).
Suganyadevi, K., Nandhalal, V., Palanisamy, S. & Dhanasekaran, S. Data security and safety services using modified timed efficient stream loss-tolerant authentication in diverse models of VANET. In 2022 International Conference on Edge Computing and Applications (ICECAA), 417–422 (2022).
Gamal, M., Mekky, N. E., Soliman, H. H. & Hikal, N. A. Enhancing the lifetime of wireless sensor networks using fuzzy logic LEACH technique-based particle swarm optimization. IEEE Access. 10, 36935–36948 (2022).
Dhanasekaran, S., Ramalingam, S., Baskaran, K. & Vivek Karthick, P. Efficient distance and connectivity based traffic density stable routing protocol for vehicular ad hoc networks. IETE J. Res. (2023).
Suganyadevi, K., Nandhalal, V., Thiyagarajan, N., Dhanasekaran, S. & Multicore, A. ECU-based automotive software domain combining runnable sequencing and task scheduling. In 2022 International Conference on Automation, Computing and Renewable Systems (ICACRS), Pudukkottai, India, 34–38 (2022).
L, R. & K, R. S. An advancement in energy efficient clustering algorithm using cluster coordinator-based CH election mechanism (CCCH). Meas. Sens. 25, 100623 (2023).
Rajeswari, A. R., Lai, W. C., Kavitha, C., Balasubramanian, P. K. & Srividhya, S. R. A trust-based secure neuro fuzzy clustering technique for mobile ad hoc networks. Electronics 12(2), 274 (2023).
Author information
Authors and Affiliations
Contributions
Nirmala Bai K.S wrote the main manuscript text and M.V.Subramanyam prepared Figs. 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, 26, 27, 28 and 29. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Consent to publish
All authors gave permission to consent to publish.
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Nirmala Bai, K.S., Subramanyam, D.M. Integrated intrusion detection design with discretion of leading agent using machine learning for efficient MANET system. Sci Rep 15, 30849 (2025). https://doi.org/10.1038/s41598-025-89221-8
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-89221-8