Abstract
Digital images have become an important way of transmitting information, and the risk of attacks during transmission is increasing. Image watermarking is an important technical means of protecting image information security and plays an important role in the field of information security. In the field of image watermarking technology, achieving a balance between imperceptibility, robustness, and embedding capacity is a key issue. To address this issue, this paper proposes a high-capacity color image adaptive watermarking scheme based on discrete wavelet transform (DWT), Heisenberg decomposition (HD), and singular value decomposition (SVD). In order to enhance the security of the watermark, Logistic chaotic mapping was used to encrypt the watermark image. By adaptively calculating the embedding factor through the entropy of the cover image, and then combining it with Alpha blending technology, the watermark image is embedded into the Y component of the YCbCr color space to enhance the imperceptibility of the algorithm. In addition, the robustness of the algorithm was further improved through singular value correction methods. The experimental results show that the average PSNR and SSIM of the watermarking scheme are 45.3437dB and 0.9987, respectively. When facing various attacks, the average NCC of the extracted watermark reaches above 0.95, indicating good robustness. The embedding capacity of this scheme is 0.6667bpp, which is higher than other watermarking schemes, and the average running time is 1.1136 seconds, which is better than most schemes.
Similar content being viewed by others
Introduction
Digital images have become an important way of transmitting information, and the risk of being attacked during transmission is increasing1. The ease of copying and tampering of digital images brings great challenges to information security. Therefore, the confidentiality and security of sensitive information when transmitted through public channels has become an important issue2. Especially in the medical field, the rapid development of Internet technology has increased the use of digital images, resulting in the production and storage of a large number of medical information every day, and the protection of image information security is particularly important3. Image watermarking is an important technical means to protect image information security and plays an important role in the field of information security. The methods of image watermarking are divided into different categories, and according to the embedding process of watermarking, watermarking can be divided into spatial domain4 and frequency domain5. Spatial domain watermarking mainly embeds the watermark by slightly changing the image pixels of the medium, which has the advantages of low computational complexity and high operational efficiency. Frequency domain watermarking is mainly realized by some common image transformations that transform pixels into frequency coefficients and then embed the watermark information. Compared to spatial domain watermarking algorithms, frequency domain algorithms greatly improve the reliability, but the computational complexity is usually higher and the operation time is longer. Discrete Wavelet Transform, Discrete Cosine Transform and Singular Value Decomposition are commonly used frequency domain watermarking schemes6. In order to ensure that the embedded watermark has high security, the watermark image is usually properly encrypted before embedding. The main concerns in the design of schemes for image watermarking are the selection of the embedding domain and embedding location, as well as the design of the embedding and extraction algorithms7. In recent decades, various researchers have advocated the use of two or more transformations to create new watermarking methods, and multiple transformations can be used to improve system performance8.
Robustness, imperceptibility, embedding capacity and security are the four evaluation indexes of image watermarking algorithms, there is a trade-off between these evaluation indexes, that is, these indexes cannot reach a better state at the same time, Alpha hybrid technology can be used to solve this trade-off9, by adjusting the embedding strength, it can make these four evaluation indexes reach a relatively balanced state. Watermark embedding can be either adaptive or non-adaptive. The adaptive watermarking scheme determines the embedding parameters based on the statistics of the host image or the image features after embedding the watermark. Its purpose is to realize the adaptive embedding of the embedding strength and embedding position of the watermark with the different characteristics of each part of the cover image, in order to solve the problem of balancing the imperceptibility and robustness of digital watermarking, and to realize as much as possible the lower complexity of the algorithm, and to enhance the practicality of the algorithm. In watermarking schemes, the choice of embedding factor plays a vital role in balancing the imperceptibility and robustness of the watermark. Most of the schemes use a single fixed embedding factor which is applicable only for fixed images but if the input image is altered then it will not provide valid results. By calculating the embedding factor adaptively, it ensures that the watermark image is robust and non-adaptive embedding strength makes the watermark image fragile, so adaptive calculation is more beneficial to get better results10.
Wavelet transform based watermarking is difficult to resist geometric attacks11. The limitations of wavelet transform based watermarking algorithms are addressed by utilizing matrix decomposition to extract geometric features of an image. Therefore, wavelet transform and matrix decomposition methods are commonly used for watermarking images to avoid image manipulation and geometric attacks. Heisenberg Decomposition (HD) has lower complexity, which results in more accurate cover image components and improves the robustness of the embedded watermark. Many existing digital watermarking systems based on Singular Value Decomposition suffer from the False Positive Problem (FPP)12, which specifies the ability to extract non-embedded or illegal watermarks from cover images. A single transform cannot guarantee all the features of watermarking at the same time, so mixed domain watermarking is needed to fulfill these watermarking requirements. Watermarking performed in two or more transform domains is known as hybrid domain watermarking, which was developed mainly to improve robustness against image processing attacks13. In addition, the color space plays an important role in image watermarking. The YCbCr color space separates the luminance information (Y component) from the chrominance information (Cb and Cr components). Luminance information represents the lightness and darkness of the image, while chrominance information represents the color information of the image. Watermarks are more likely to be hidden in the luminance information of an image, and the separation allows for more targeted embedding of watermarks, reducing the impact on the overall quality of the image14.
Literature review
Kang et al.15 proposed a secure and robust watermarking scheme for color images, which uses Frobenius paradigm and majority voting in the DWT-SVD domain in order to create zero watermarks. Experimental results show that the scheme is less robust to geometric attacks. Pandey et al.16 proposed a stable, lossless, and reliable hybrid color watermarking technique called lifting method and GWO, which uses Arnold transform to scramble the watermark, improving security and robustness. However, compared with other color image watermarking schemes, this scheme has poorer robustness. Koley17 proposed a watermarking of color images in LWT domain using \(\alpha \)-\(\beta \) mixing. The method embeds factors \(\alpha \) and \(\beta \) according to the PC feature map by varying the diagonal information coefficients of the cover image. The experimental results show that the technique is less robust to JPEG compression attacks.
Zhang, L et al.18 proposed a two-stage encryption algorithm based on Invariant Integer Wavelet (IIW) by transforming the main image to frequency domain using Redistributed Invariant Integer Wavelet Transform (RIIWT) and calculating the singular values of the image matrix by using QR Decomposition and Singular Value Decomposition to hide the watermarks in the low and high frequencies of the cover image, which is a rotationally stable scheme with low computational cost. Pandey et al.19 proposed a non-blind color image watermarking scheme based on SWT and SVD, watermarking in YCbCr color space, embedding the watermark through different embedding factors, and the results show that the imperceptibility of the watermarked image decreases as the embedding factor increases. Vaidya P et al.20 proposed an adaptive color watermarking using multiple decomposition. To embed the watermark, the embedding factor is computed adaptively using the kurtosis and entropy of the color image. The experimental results show that this scheme is less imperceptible for color images. Roy et al.21 proposed a color image watermarking scheme based on DWT-SVD. The watermark is inserted into the Y component of the YCbCr color space. Experimental results show that the method is not robust to image processing attacks.
Abdulrahman et al.22 proposed a color image watermarking scheme based on DCT-DWT domain. After performing global DCT for each color component, one level of DWT is applied to the DCT coefficients of the color components. The result shows that the method is poorly robust to noise addition attacks. Prabha K et al.23 proposed a watermarking method for color images based on Triangular Vertex Transform (TVT) and WHT. To obtain the U, V and W coefficients, the technique transforms the RGB image with TVT. Experimental results show that the scheme is less robust to histogram equalization and JPEG compression attacks.
Zhang et al.24 proposed a color image watermarking scheme using correlation of RGB color channels for copyright protection. The Tucker decomposition is utilized to generate the first feature of the image, which contains most of the energy of the image and the correlation between the three channels. The first feature of the image is then segmented into non-overlapping blocks, and the blocks are decomposed using singular value decomposition to embed the watermark in the left singular matrix. The results show that the robustness and imperceptibility of this scheme are poor. Al-maweri et al.25 proposed an adaptive digital image watermarking robust scheme based on DCT-DWT. Firstly, the image is converted to DCT and then wavelet transform is applied to the image, the algorithm selects the best embedding factor by self-training, but the algorithm is weakly robust to noise addition attacks.
Kang X et al.26 proposed a watermarking scheme based on DWT-DCT-SVD, which uses a two-level DWT transformation of the cover image to generate LH2 and HL2 sub-bands, and applies DCT to these sub-bands. The watermark image to be inserted is encrypted using chaotic logic mapping. And an optimized particle swarm optimization algorithm was proposed, which selects the most suitable DCT sub-band through multidimensional optimization and estimates the watermark embedding factor by considering the imperceptibility and robustness of the watermark scheme. This algorithm can better meet the watermark requirements, but its robustness to some geometric attacks is not strong. Zhang H et al.27 proposed a hybrid domain watermarking scheme for QWT and QSVD. The watermark is embedded into the Y component of the YCbCr color space. For the security of the watermark, the watermark is encrypted with a 2D Chebyshev logistic map and then embedded. Experimental results show that the scheme is not robust. Wang et al.28 proposed a color image watermarking method using multilevel DWT-SVD and chaotic encryption. To embed the watermark, both the cover image and the watermarked image are converted to NTSC color space. Experimental results show that the scheme is less robust to image processing attacks.
Sourabh Sharma et al.29 proposed a new robust adaptive watermarking scheme, where the host image is decomposed into four subbands of the same dimensions by Redundant Discrete Wavelet Transform (RDWT), and then Singular Value Decomposition (SVD) is performed on the approximate subbands to obtain the principal components (PCs). Then adaptive multiscale factor optimized by artificial bee colony is used to insert the disrupted watermark directly into the principal components of the disrupted host image, which overcomes the trade-off between imperceptibility and robustness of the watermarked image. Meanwhile, the scheme overcomes the security problem of false positive error (FPE), which is common in existing watermarking schemes based on singular value decomposition. Sourabh Sharma et al.30 proposed a hybrid DCT-NNMF domain based color image watermarking. The scheme utilizes Multi-Objective Artificial Bee Colony (MOABC) to generate optimal multiple embedding factors to achieve the elimination of the imbalance between imperceptibility and robustness.To improve the security of the watermark, a key is created from the watermarked image, which is required to successfully extract the correct watermark.The experimental results show that the scheme has better visual quality and robustness. Sourabh Sharma et al.31 proposed an adaptive color image blind watermarking method based on boosted wavelet transform and discrete cosine transform, which balances the visual quality and robustness of the watermark by optimizing the algorithm of Artificial Bee Colony (ABC) to optimize the optimal embedding factor, and the experimental results show that the scheme has better imperceptibility and robustness to resist image processing and manipulation attacks.
Singh, O.P. et al.32 proposed an optimization based robust watermarking algorithm for color medical image copyright protection. The algorithm decomposes the host image using the enhanced wavelet transform (LWT), decomposes the transformed coefficients using the discrete cosine transform, and embeds multiple watermarks into the transformed host image using a hybrid optimization algorithm. The experimental results show that the algorithm has good invisibility, watermark payload, and robustness against image processing attacks. Priyanka et al.33 proposed a medical image data hiding method in the context of invisibility, robustness, security, and low time cost. Firstly, use a local binary pattern based on adjacent pixels to calculate the optimal value for embedding two markers. Secondly, the host medical images are labeled using enhanced wavelet transform, LU decomposition, singular value decomposition, and embedding factors. Finally, 3D chaos is used to encrypt the labeled image. The experimental results and performance analysis indicate that the proposed scheme has better robustness, imperceptibility, and security, and reduces the time cost compared to other traditional encryption techniques. Singh, Om Prakash et al.34 proposed a medical image watermarking scheme based on integer wavelet transform (IWT) and least significant bit (LSB). This technology first converts the cover image into three channels, and then uses IWT to convert each channel. With the help of LSB scheme, multiple markers are hidden in the overlay medium. At the same time, lossless soft methods are used to compress image labels before embedding, thereby reducing storage and transmission overhead and improving the embedding ability of labeled color images. The experimental results show that this scheme has good performance in terms of perceived quality, robustness, and capacity.
It is obvious from the literature review that the balance between perceptibility, robustness and embedding capacity is crucial in the field of image watermarking and the hybrid domain watermarking scheme helps to balance the imperceptibility and robustness of the watermarking algorithms, so in this paper we propose a color image watermarking scheme based on DWT-HD-SVD.
Motivation and contribution
In recent years, image watermarking technology has been widely used in the fields of information hiding as well as copyright protection, and mixed-domain watermarking has important advantages in improving the imperceptibility and robustness of watermarking algorithms. Both DWT and SVD are lossless transforms, which do not significantly degrade the quality of the image during the whole process of watermark embedding and extraction, and both Heisenberg decomposition and SVD have good stability, which can effectively improve the robustness of the watermarking algorithm in the face of attacks. One of the key issues in watermarking techniques based on singular value decomposition is FPP and when the image embedded in the watermark is attacked, the singular value of the image tends to become larger and it needs to be corrected appropriately. Therefore, in this paper, we propose a robust watermarking scheme based on DWT-HD-SVD that can resist various types of attacks such as noise attacks, filtering attacks, etc.
The innovation of this paper is to propose a robust watermarking scheme based on DWT-HD-SVD, which balances the robustness and imperceptibility of watermarking by adaptively computing the embedding factor using the entropy of the cover image in YCbCr color space. The main contributions of this work are:
-
1.
This paper proposes a color image watermarking scheme based on DWT-HD-SVD, which calculates the embedding factor by the visual entropy and edge entropy of the image, and balances the imperceptibility and robustness of the watermark.
-
2.
In order to solve the FPP problem and the problem that the singular value becomes large after the watermark is attacked, a singular value correction method is proposed to enhance the anti-attack ability of the algorithm.
-
3.
Balance the imperceptibility and robustness of the watermarking scheme by improving the Alpha hybrid algorithm.
The experimental results show that the algorithm has better imperceptibility as well as larger embedding capacity than existing algorithms, exhibits excellent robustness in the face of common attacks, and strikes a good balance between robustness and imperceptibility.
The rest of the paper is structured as follows. Section 2 describes some of the techniques used in this paper, Section 3 describes the watermarking scheme proposed in this paper, Section 4 shows the experimental results of this scheme, Section 5 summarizes the work of this paper.
Background
Logistic chaos mapping
Chaos occurs in systems with nonlinear processes that are sensitive to the starting and control points, and are random and unpredictable in chaotic orbits, and this security system is characterized by randomness, mixing, and reliability35. Therefore, the most common method is to use chaotic systems for encryption. In this paper, Logistic mapping is used to encrypt the watermark image thereby meeting the security requirements of the watermarking system. The essence of Logistic mapping is to change the correlation between neighboring pixel points in the original watermark image without changing the gray value and histogram of the original image. The equation for one-dimensional Logistic mapping is:
where \(x_k\in (0,1)\) is the kth value produced by the iteration and \(\mu \in [0,4]\) is the parameter of the logistic mapping, and the resulting sequence satisfies the chaotic property only when \(3.5699456<\mu \le 4\). Thus the generated chaotic sequence can be controlled by a reasonable choice of the initial value \(x_0\) and the parameter \(\mu \). Figure 1 shows the encryption of a 256\(\times \)256 grayscale image using Logistic chaotic mapping with \(x_0=0.5\) and \(\mu =4\).
As can be seen from Fig. 1, the histogram of the encrypted image has no similarity with the histogram of the original image, it looks like two different maps and the images before encryption and after decryption are the same, so it is said that the image encryption of Logistic chaotic mapping is reliable and effective to improve the security of the watermarking algorithm.
Discrete wavelet transform
Discrete Wavelet Transform is an important signal analysis method, which is often used for time-frequency analysis and processing of signals36. It is widely used in image processing due to its good multi decomposition capability, DWT can decompose the image layer by layer through filters, so it is called image microscope. Doing two-dimensional discrete wavelet transform on the image will get four sub-bands, LL, LH, HL, HH, and the vast majority of the energy of the original image is concentrated in the LL sub-band, which has strong anti-jamming and stability, while the horizontal low-frequency component and vertical high-frequency component (LH sub-band), the horizontal high-frequency component and vertical low-frequency component (HL sub-band), and the horizontal and vertical high-frequency components (HH sub-bands) show the characteristics of the original image such as the edges, contours, and textural details, which are then more prone to be attacked; therefore, LL sub-bands, which retain the details, were chosen to be embedded in the watermark. A further decomposition of the LL sub-bands can be performed, called the secondary DWT decomposition. Figure 2 shows an example of discrete wavelet transform performed on an image.
Heisenberg decomposition
Heisenberg decomposition37 is a matrix decomposition method with low time complexity for square matrix decomposition. More accurate host image components can be obtained using Heisenberg decomposition to improve the robustness of embedded watermarked images. The HD decomposition of a matrix A is:
where P is a unitary matrix and H is the upper Heisenberg matrix, if h(i, j) denotes the element of the H matrix, we have \(h(i,j)=0\) when \(i>j+1\).
Singular value decomposition
Singular value decomposition is one of the very important matrix decomposition tools in the field of linear algebra, providing a method of diagonalizing matrices based on orthogonal equivalent transformations36. There exists a matrix \(A\in R^{m\times n}\) that can represent an image and the matrix has dimensions \(m\times n\):
Make it:
where \(V\in R^{m\times n}\) and \(U\in R^{m\times n}\), both of which are orthogonal matrices, and \(\Sigma \in R^{m\times n}\) denotes a diagonal matrix whose values on the off-diagonal are all 0, and whose values on the diagonal are satisfied:
where r denotes the rank of A whose size is the number of non-zero real numbers on the diagonal, and \(\sigma _{i}(i=1,2,\cdots ,m)\) is the singular value of the matrix.
Analyzed from the perspective of image processing, the singular values of the image matrix are correlated with the intrinsic features of the image and have a strong stability, so that when the image suffers from a small attack, its singular values do not change significantly. Moreover, the singular values of the image are invariant to geometric distortions (e.g. rotation, scaling, translation, etc.). Therefore, applying singular value decomposition to digital image watermarking can effectively improve the robustness of the algorithm.
Proposed watermarking technique
Singular value correction
The singular values of an image have good stability, and when a small perturbation is applied to the image, the singular values of the image are not greatly affected. However, there is no correspondence between the image and the singular values, so the singular values of different images can be the same, thus creating the problem of false positives. And when attacking an image, the attacker may modify the pixel values of the image or introduce noise, which can cause the singular values of the image matrix to become larger. In order to solve the FPP as well as to reduce the singular values of the image and to reduce the sensitivity of the attacked image matrix, a correction factor \(\beta \) is added and a \(\beta \) power operation is performed on the singular value matrix S.
After an image is attacked, the singular value obtained by the traditional singular value decomposition method fluctuates greatly, especially under geometric attacks. However, the stability of singular values determines the stability of watermark extraction. Therefore, its impact must be minimized before extracting the watermark. When the original image is attacked, a correction factor \(\beta \) is added to the singular value to eliminate the effect, and \(\beta \) takes the value of 0.95 in this paper.
Adaptive embedding factors
The watermark embedding factor is a trade-off problem that needs to be adjusted according to specific application requirements and image characteristics. In practical applications, several tests and adjustments may be required to find the most suitable embedding strength to achieve good watermark effect and image quality. Entropy is an index that describes the spatial correlation of neighboring pixels, and the visual entropy and edge entropy of the cover image38 are used to calculate the embedding factor of the scheme with the following equation:
Where \(E_e\) is the edge entropy of the cover image, \(E_v\) is the visual entropy of the cover image and \(\lambda \) is the parameter to be adjusted. The visual entropy and edge entropy of the image are calculated as follows:
Where L is the maximum value of pixels desirable in the gray scale image, e is a natural constant and pi is the probability of pixel value i, \(i\in \{1,2,\cdots ,L\}\).
Watermark embedding
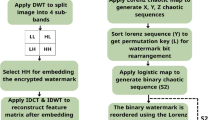
In this article, the cover image used is a color image, while the watermark image is a grayscale image. To enhance the security of the watermark algorithm, we use Logistic chaotic mapping to encrypt the watermark image, generate a chaotic sequence through chaotic mapping, use it as a key, and XOR encrypt it with the watermark image. Subsequently, singular value decomposition operation is performed on the encrypted image. To enhance the imperceptibility of the watermarking algorithm, we convert the cover image to YCbCr color space and select the Y component of it for discrete wavelet decomposition. The YCbCr color space is chosen to improve the visual transparency of the watermarking algorithm, and the Y component is chosen because it is more robust in embedding the watermark compared to the Cb and Cr components. Next, we perform a discrete wavelet decomposition of the Y component and a Heisenberg decomposition of the resulting LL sub-band to obtain the upper matrix H. Subsequently, we perform a singular value decomposition of the H matrix. The embedding factor is calculated from the visual entropy and edge entropy of the cover image in order to perform Alpha blending technique to embed the watermark. The steps of watermark embedding are shown in Fig. 3.
Step 1: Read the grayscale watermark image and encrypt it with Logistic chaotic mapping with the encryption parameters \(x_0=0.5\) and \(\mu =4\);
Step 2: Using singular value decomposition, the image \(W_{E}\) is decomposed into 3 matrices \(U_w\) , \(S_w\) and \(V_w\);
Step 3: Read the color cover image and convert it to YCbCr color space, then select the Y component;
Step 4: Adaptive computation of embedding factor \(\alpha \). The embedding factor is computed by the visual entropy, edge entropy, and scaling factor of the cover image using Eq. (8);
Step 5: A one-level Haar wavelet decomposition of the Y component (\(H_Y\)) of the cover image is performed to decompose it into four sub-bands, LL, HL, LH, and HH;
Step 6: Perform the Heisenberg matrix decomposition on the LL sub-band to obtain the upper matrix H;
Step 7: Apply the singular value decomposition to the matrix H to obtain three matrices \(U_H\), \(S_H\) and \(V_H\);
Step 8: The \(S_w\) obtained from the singular value decomposition in Step 3 and the \(S_H\) obtained from the singular value decomposition in Step 7 are embedded by the Alpha blending method;
Step 9: Reconstruct the matrix H using inverse singular value decomposition based on the matrices \(U_H\) , \(S_{H}^{\prime }\) and \(V_H\);
Step 10: Reconstruct the \(LL'\) sub-band according to the matrices P and \(H^{\prime }\), using the inverse Heisenberg decomposition;
Step 11: According to the four sub-bands \(LL'\), HL, LH, and HH, inverse discrete wavelet transform processing is performed to obtain the Y-channel image \(Y'\) with embedded watermark;
Step 12: Perform RGB reconstruction of the image to obtain the image \(H_{RGB}^{\prime }\) after embedding the watermark.
Watermark extraction
In the watermark extraction process, the image embedded with the watermark is first converted to YCbCr color space, then discrete wavelet decomposition is applied to the Y component, and the LL sub-bands are selected for Heisenberg matrix decomposition to obtain the upper matrix H. The singular value decomposition of H is applied. On this basis, singular value decomposition is applied to obtain the singular value matrix and correct it, and the singular value matrix of the watermark is extracted by inverse Alpha mixing. Finally, the encrypted watermark image is obtained by inverse singular value decomposition and then the watermarked image is restored by the decryption process. The steps of watermark extraction are shown in Fig. 4.
Step 1: Read the color image with the embedded watermark and convert it to YCbCr color space, then select the Y component;
Step 2: Select the Y component and perform one level Haar wavelet decomposition on it;
Step 3: Perform the Heisenberg matrix decomposition on the \(LL_WM\) sub-bands to obtain the upper matrix \(H_WM\);
Step 4: Perform singular value decomposition of the upper matrix \(H_WM\) into 3 matrices \(U_WM\), \(S_WM\) and \(V_WM\);
Step 5: Correct the singular values according to Eq. (7);
Step 6: The singular value matrix of the encrypted watermark can be obtained by the embedding factor \(\alpha \) and the singular value matrix \(S_H\);
Step 7: Recover the encrypted watermark by performing inverse singular value decomposition of the matrices \(U_w\), \(s_{w}^{\prime }\) and \(V_w\);
Step 8: Decrypt the image using Logistic chaotic mapping and finally get the watermark image.
Experimental results and analysis
In this section, six color cover images of size 512\(\times \)512 and one grayscale watermark of size 256\(\times \)256 are used to verify the performance of the proposed scheme. Figure 5 shows the cover images and watermark images used in this paper. All image data used in this article are from the public dataset USC-SIPI: Signal and Image Processing Institute University of Southern California https://sipi.usc.edu/database/. The experiments were performed in MATLAB (R2020b) environment on Intel(R) Core (TM) i5-12400F CPU 2.50 GHz, 16.0 GB RAM computer. Peak signal-to-noise ratio (PSNR) and structural similarity (SSIM) metrics are used to measure the imperceptibility of the proposed scheme, while normalized correlation coefficient (NCC) and bit error rate (BER) metrics are used to measure the robustness of the proposed scheme. The embedding factor is calculated using Eq. (8) and in this paper the value of \(\lambda \) is taken as 0.04. The embedding factor for each cover image is shown in Table 1.
Imperceptibility
Imperceptibility refers to the ability of the embedded watermark to remain consistent with the original cover image, and the change in the image cannot be detected through the human eye. In this paper, the imperceptibility of the method is tested on six different cover images, PSNR and SSIM metrics to evaluate the imperceptibility of the proposed scheme. PSNR is used to show the perceived transparency of the watermarked image with respect to the original cover image and SSIM describes the contrast, luminance and structural attributes of the image and is used for similarity measurements, when the PSNR measurement is greater than 30 dB, it is considered to have an acceptable visual quality and similarity to the original image, watermarked images with SSIM close to 1 have a high level of perceptual quality39. Figure 6 shows the embedded watermarked cover image and the extracted watermark image.
The PSNR, MSE and SSIM of this paper’s scheme for different cover images are shown in Table 2. The average PSNR and SSIM of the scheme are 45.3437 dB and 0.9987, respectively, which shows that the scheme has good imperceptibility.
Similar to PSNR, image histogram can be considered as a widely valid tool for evaluating the visual effects caused by image watermarks on cover images. An image histogram shows the frequency of each intensity value in an image, presenting the characteristics of the image in a more visual way. By comparing the histograms of two images, their similarity can be determined. The image histogram provides a more reliable way to compare the similarity which shows that the watermarking method cannot significantly alter the cover image. Figure 7 shows the original cover image and the histogram of the cover image with the embedded watermark, as can be seen from the figure, there is no significant difference in the histogram before and after embedding the watermark, so the imperceptibility of this scheme is better.
Table 3 compares the PSNR and SSIM metrics of our proposed scheme with the invisibility metrics of other watermarking schemes. From Table 3, it can be seen that our proposed scheme has an average PSNR of 45.6135dB and an average SSIM of 0.9984, indicating good invisibility. Except for references22,40, and41, invisibility is superior to other schemes.
Robustness analysis
In this section, NCC and BER metrics are used to evaluate the robustness of the proposed scheme against various attacks. A high value of NCC indicates high resistance to attacks. And lower BER indicates less watermarking distortion. The robustness of any watermarking scheme is tested by various attacks which can be broadly categorized as noise attack, enhancement technique attack, geometric transformation attack and compression attack. Figure 8 shows the attacked cover images, and Fig. 9 shows the watermark images extracted from these attacked images, where [a-l] represent: no attack, pretzel noise (v=0.05), Gaussian noise (m=0, v=0.05), speckle noise (v=0.05), sharpening, Gaussian filtering, mean filtering, rotate by 10\(^\circ \), flip vertically, crop by 20%, JPEG compression (QF=90), JPEG 2000 compression (QF=90) and Gamma correction (gama=0.8), respectively. As can be seen from Fig. 9, except for the rotation attack and the shear attack, this scheme is able to effectively deal with other attacks, and the extracted watermark image has only a small amount of distortion, with good robustness.
Table 4 describes the NCC of watermark images extracted from different attacks, and Table 5 describes the BER of watermark images extracted from different attacks. Under no attack conditions, the average NCC of this method is 1 and the average bit error rate is 0. And under various attacks, the average NCC and average BER can maintain a good level. Except for the NCC of around 0.85 in the face of rotation attacks, the NCC values reach above 0.95 in the face of other attacks, indicating that this scheme has good robustness. Table 6 describes the robustness comparison results with other watermarking schemes. Taking the Peppers cover image as an example, it can be seen from Table 5 that our watermarking scheme has better robustness.
Embedded capacity analysis
Embedding capacity is a metric that describes the number of bits of information that can be inserted into the cover image15. This scheme uses a color cover image of size 512 \(\times \) 512 and a grayscale watermark image of 256 \(\times \) 256. Therefore, the embedding capacity of this scheme is (256 \(\times \) 256 \(\times \) 8)/(512 \(\times \) 512 \(\times \) 3) = 0.6667bpp, which has a high embedding capacity.
Security analysis
Watermark security protection is an important prerequisite to ensure the effective embedding of the watermarking scheme. In this paper, we use Logistic Chaos Mapping encryption to protect the watermark, even if the attacker extracts the watermark, but what he gets is only the encrypted image, Logistic Chaos Mapping should exhibit good chaotic properties, including sensitivity dependent on the initial conditions, unpredictability over a long period of time, etc., and these properties ensure that the generated chaotic sequences have a high degree of randomness and improve the strength of watermark encryption. And this scheme has good robustness, which can fully extract the watermark image in the face of some attacks, greatly improving the security of the watermark.
Complexity analysis
In this paper, the size of the cover image is M \(\times \) M and the size of the watermark is m \(\times \) m, where m < M. Therefore, the time complexity of the watermarking algorithm based on DWT-HD-SVD proposed in this paper is calculated as follows.
The time complexity of DWT is: \(O(M^2)\) , the time complexity of HD is: \(O(M^3)\), the time complexity of SVD is: \(O(M^3)\), and the time complexity of Logistic Chaotic Mapping Encryption is: \(O(M^2)\), so the overall time complexity of this scheme is: \(T(M)=O(M^2)+O(M^3)+O(M^3)+O(M^2)=O(M^3)\).
Runtime analysis
The efficacy of any mathematical algorithm depends on the computational complexity, we compared several similar schemes and Table 7 depicts the comparative analysis of the presented work with other works in terms of execution time. From the comparative analysis, it can be seen that the total execution time of the proposed work is almost similar to Ref.31 and Ref.47. Meanwhile, the execution time in Ref.42 and Ref.43 is longer and the execution time in Ref.40 is shorter compared to the proposed method.
Other comparative analysis
Table 8 compares the characteristics of our proposed method with the latest existing methods and analyzes various aspects of different schemes, including the methods used, the size and color of the cover image, the size and color of the watermark image, PSNR, SSIM, advantages and disadvantages, security techniques used, and embedding capacity. From Table 8, it can be seen that the watermark image used in this article has a larger size, larger embedding capacity, and higher robustness and security. Overall, compared to similar watermark schemes, this article is relatively better.
Conclusion
Image watermarking technology has a crucial role in the fields of copyright protection as well as identity authentication, however, there is always a trade-off between the imperceptibility, robustness, and embedding capacity of watermarking schemes. To solve this problem, this paper proposes an adaptive color image watermarking scheme based on DWT-HD-SVD. The embedding factor is calculated by the visual entropy as well as the edge entropy of the cover image, and a singular value correction method is proposed to correct the singular value when the watermarked image is attacked, which improves the robustness of the algorithm. In order to improve the security of the watermark, Logistic chaotic mapping is used to encrypt the watermark image. The experimental results show that the average PSNR and SSIM of this watermarking scheme are 45.3437 dB and 0.9987, respectively.The embedding capacity of this scheme is 0.6667bpp, which is higher than the other watermarking schemes, and the average running time is 1.1136 seconds, which is better than the other schemes. The experimental results show that this scheme realizes the trade-off between imperceptibility, robustness, and embedding capacity. Compared with other hybrid watermarking schemes, our proposed scheme is able to effectively resist multiple attacks with high robustness, although the scheme has better overall robustness, its robustness to rotation and cropping attacks is relatively poor.
Data availability
The datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request.
References
Walia, S., Kumar, K., Kumar, M. & Gao, X.-Z. Fusion of handcrafted and deep features for forgery detection in digital images. IEEE Access 9, 99742–99755 (2021).
Abdulla, A. A. Exploiting similarities between secret and cover images for improved embedding efficiency and security in digital steganography. Ph.D. thesis, University of Buckingham (2015).
Singh, K. N., Baranwal, N., Singh, O. P. & Singh, A. K. Deepenc: Deep learning-based roi selection for encryption of medical images through key generation with multimodal information fusion. IEEE Trans. Consumer Electron. (2024).
Kahlessenane, F., Khaldi, A., Kafi, M. R. & Euschi, S. A color value differentiation scheme for blind digital image watermarking. Multimed. Tools Appl. 80, 19827–19844 (2021).
Singh, K. U. et al. Secure watermarking scheme for color dicom images in telemedicine applications. Comput. Mater. Continua 70, 2525–2542 (2021).
Ernawan, F. & Kabir, M. N. A block-based rdwt-svd image watermarking method using human visual system characteristics. Vis. Comput. 36, 19–37 (2020).
Chopra, A., Gupta, S. & Dhall, S. Analysis of frequency domain watermarking techniques in presence of geometric and simple attacks. Multimed. Tools Appl. 79, 501–554 (2020).
Wan, W. et al. A comprehensive survey on robust image watermarking. Neurocomputing 488, 226–247 (2022).
Fragoso-Navarro, E., Cedillo-Hernandez, M., Nakano-Miyatake, M., Cedillo-Hernandez, A. & Pérez-Meana, H. M. Visible watermarking assessment metrics based on just noticeable distortion. IEEE Access 6, 75767–75788 (2018).
CM PVSSR. Adaptive, robust and blind digital watermarking using bhattacharyya distance and bit manipulation. Multimed. Tools Appl. 77, 5609–5635 (2018).
Liu, J. et al. An optimized image watermarking method based on hd and svd in dwt domain. Multimed. Tools Appl. 7, 80849–80860 (2019).
Makbol, N. M., Khoo, B. E. & Rassem, T. H. Security analyses of false positive problem for the svd-based hybrid digital image watermarking techniques in the wavelet transform domain. Multimed. Tools Appl. 77, 26845–26879 (2018).
Begum, M. & Uddin, M. S. Analysis of digital image watermarking techniques through hybrid methods. Adv. Multimed. 2020, 1–12 (2020).
Kumar, S. & Singh, B. K. Dwt based color image watermarking using maximum entropy. Multimed. Tools Appl. 80, 15487–15510 (2021).
Kang, X.-B. et al. Robust and secure zero-watermarking algorithm for color images based on majority voting pattern and hyper-chaotic encryption. Multimed. Tools Appl. 79, 1169–1202 (2020).
Pandey, M. K., Parmar, G., Gupta, R. & Sikander, A. Lossless robust color image watermarking using lifting scheme and gwo. Int. J. Syst. Assur. Eng. Manag. 11, 320–331 (2020).
Koley, S. A feature adaptive image watermarking framework based on phase congruency and symmetric key cryptography. J. King Saud Univ. Comput. Inf. Sci. 34, 636–645 (2022).
Zhang, L. & Wei, D. Image watermarking based on matrix decomposition and gyrator transform in invariant integer wavelet domain. Signal Process. 169, 107421 (2020).
Pandey, M. K., Parmar, G., Gupta, R. & Sikander, A. Non-blind Arnold scrambled hybrid image watermarking in ycbcr color space. Microsyst. Technol. 25, 3071–3081 (2019).
CM PVSSR. A robust semi-blind watermarking for color images based on multiple decompositions. Multimed. Tools Appl. 76, 25623–25656 (2017).
Roy, S. & Pal, A. K. A hybrid domain color image watermarking based on dwt-svd. Iran. J. Sci. Technol. Trans. Electr. Eng. 43, 201–217 (2019).
Abdulrahman, A. K. & Ozturk, S. A novel hybrid dct and dwt based robust watermarking algorithm for color images. Multimed. Tools Appl. 78, 17027–17049 (2019).
Prabha, K. & Sam, I. S. A novel blind color image watermarking based on walsh hadamard transform. Multimed. Tools Appl. 79, 6845–6869 (2020).
Zhang, F. et al. A novel robust color image watermarking method using rgb correlations. Multimed. Tools Appl. 78, 20133–20155 (2019).
Al-maweri, N. A. A. S. et al. A hybrid digital image watermarking algorithm based on dct-dwt and auto-thresholding. Secur. Commun. Netw. 8, 4373–4395 (2015).
Kang, X., Chen, Y., Zhao, F. & Lin, G. Multi-dimensional particle swarm optimization for robust blind image watermarking using intertwining logistic map and hybrid domain. Soft Comput. 24, 10561–10584 (2020).
Zhang, H., Li, Z., Liu, X., Wang, C. & Wang, X. Robust image watermarking algorithm based on qwt and qsvd using 2d chebyshev-logistic map. J. Franklin Inst. 359, 1755–1781 (2022).
Wang, K., Gao, T., You, D., Wu, X. & Kan, H. A secure dual-color image watermarking scheme based 2d dwt, svd and chaotic map. Multimed. Tools Appl. 81, 6159–6190 (2022).
Sharma, S., Sharma, H. & Sharma, J. B. An adaptive color image watermarking using rdwt-svd and artificial bee colony based quality metric strength factor optimization. Appl. Soft Comput. 84, 105696 (2019).
Sharma, S., Sharma, H. & Sharma, J. B. A new optimization based color image watermarking using non-negative matrix factorization in discrete cosine transform domain. Journal of Ambient Intelligence and Humanized Computing 1–23 (2022).
Sharma, S., Sharma, H. & Sharma, J. B. Artificial bee colony based perceptually tuned blind color image watermarking in hybrid lwt-dct domain. Multimed. Tools Appl. 80, 18753–18785 (2021).
Singh, O. P., Singh, K. N., Singh, A. K., Agrawal, A. K. & Zhou, H. An improved robust algorithm for optimisation-based colour medical image watermarking. Comput. Electr. Eng. 117, 109278 (2024).
Priyanka, Baranwal, N., Singh, K., Singh, O. P. & Singh, A. Hidden: Robust data hiding for medical images with encryption and local binary pattern. Circuits Syst. Signal Process. 1–21 (2024).
Singh, O. P. et al. Hidemarks: hiding multiple marks for robust medical data sharing using iwt-lsb. Multimed. Tools Appl. 83, 24919–24937 (2024).
Kang, X.-B., Zhao, F., Lin, G.-F. & Chen, Y.-J. A novel hybrid of dct and svd in dwt domain for robust and invisible blind image watermarking with optimal embedding strength. Multimed. Tools Appl. 77, 13197–13224 (2018).
Singh, A. K., Dave, M. & Mohan, A. Hybrid technique for robust and imperceptible image watermarking in dwt-dct-svd domain. Natl. Acad. Sci. Lett. 37, 351–358 (2014).
Su, Q. & Chen, B. A novel blind color image watermarking using upper Hessenberg matrix. AEU-Int. J. Electron. Commun. 78, 64–71 (2017).
Kumar, S. & Singh, B. K. An improved watermarking scheme for color image using alpha blending. Multimed. Tools Appl. 80, 13975–13999 (2021).
Wang, Z., Bovik, A. C., Sheikh, H. R. & Simoncelli, E. P. Image quality assessment: from error visibility to structural similarity. IEEE Trans. Image Process. 13, 600–612 (2004).
Su, Q., Liu, Y., Liu, D., Yuan, Z. & Ning, H. A new watermarking scheme for colour image using qr decomposition and ternary coding. Multimed. Tools Appl. 78, 8113–8132 (2019).
Kumar, S. & Singh, B. K. Dwt based color image watermarking using maximum entropy. Multimed. Tools Appl. 80, 15487–15510 (2021).
Hsu, L.-Y. & Hu, H.-T. Blind watermarking for color images using emmq based on qdft. Expert Syst. Appl. 149, 113225 (2020).
Huynh-The, T. et al. Selective bit embedding scheme for robust blind color image watermarking. Inf. Sci. 426, 1–18 (2018).
Kumar, S. et al. Entropy based adaptive color image watermarking technique in yc b c r color space. Multimed. Tools Appl. 83, 13725–13751 (2024).
Sangeetha, N. & Anita, X. Entropy based texture watermarking using discrete wavelet transform. Optik 160, 380–388 (2018).
Roy, S. & Pal, A. K. An svd based location specific robust color image watermarking scheme using rdwt and Arnold scrambling. Wirel. Pers. Commun. 98, 2223–2250 (2018).
Su, Q. Novel blind colour image watermarking technique using Hessenberg decomposition. IET Image Process 10(11), 817–829 (2016).
Acknowledgements
This work was supported by National Natural Science Foundation of China (No.61772295), Key Projects of Chongqing Natural Science Foundation Innovation Development Joint Fund (CSTB2023NSCQ-LZX0139), Open Fund of Advanced Cryptography and System Security Key Laboratory of Sichuan Province (Grant No. SKLACSS–202208) and Technology Research Program of Chongqing Municipal Education Commission (Grant no. KJZD-M202000501).
Author information
Authors and Affiliations
Contributions
Y.D. Provided fund support, R.Y. Conceptualize experiments and write manuscripts, C.Y. Performed verification. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Dong, Y., Yan, R. & Yin, C. An adaptive robust watermarking scheme based on chaotic mapping. Sci Rep 14, 24735 (2024). https://doi.org/10.1038/s41598-024-76101-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-024-76101-w
This article is cited by
-
A hybrid steganography framework using DCT and GAN for secure data communication in the big data era
Scientific Reports (2025)