Abstract
VANETs exchange data in highly dynamic open wireless access environments which are prone to security and privacy attacks. In order to safeguard the transmitted data, group key agreement authentication (GKAA) technique is used. Utilization of group key allows entities to corroborate a group key for secure VANET communication in an unsecure wireless communication channels. The traditional GKAA consumes a considerable amount of resources, verification delay is very high. Since the group key is computed and administered solely by TTA, it leads to central tendency. Additionally the communication delay soars high. To alleviate the problems of computational cost, communication cost, security, conditional privacy, central tendency, a Dickson polynomial based conditional privacy preservation authentication based on group key authentication (GKA) for VANETs has been proposed. The proposed work involves the use of Dickson polynomial to improve the security strength of TTA while authentication vehicles. Since it is based on chaotic mapping algorithm, wherein the chaotic map provides a one-way hash function; Dickson polynomial is used to corroborate a publicly distributed group key; it alleviates the complex modular or scalar multiplication performed using Elliptic curves. The group key gets computed in a distributed fashion by using the Chinese Remainder Theorem (CRT) and gets updated dynamically without the aid of TTA. Conditional Privacy has been ensured by the tracing back the pseudonyms in case of any illicit behavior exhibited by the vehicles. The proposed scheme is lightweight and lowers the communication, computation cost involved during authentication and verification. Performance analysis has been carried out by using BAN logic and ROR model thereby ensuring the security and efficiency. Thus the proposed authentication technique outperforms the traditional certificate-less and group key authentication schemes in terms of improvement in computation cost of 39%, communication cost of 672 bits for a single message with a less verification delay.
Similar content being viewed by others
Introduction
Conventional transportation systems (CTSs) suffer from problems such as traffic congestion, traffic delays, traffic accidents, economical loss, infrastructure damage and deaths1. To cater these problems of traffic, ITS emerged as a solution to mitigate the traffic problems encountered by the traditional transportation2. VANETs act as a core functioning entity of ITS3. Vehicles, especially cars have now been equipped with sensors and information computing facilities along with the information and communication technologies (ICT) opened a new arena of applications revolutionizing the modern transportation systems4. VANETs are applied in a wide variety of applications relating to advanced cruise control, vehicle collision avoidance, cooperative and autonomous driving5. Vehicles are capable of forming a network on-the-go referred to as VANETs. They are highly dynamic and self-organized in nature6. The major advantage of the VANETs is to provide the safety, efficiency and comfort to the commuters7.
Data transmissions in VANETs are highly subjugated by different kinds of security and privacy concerns8. Since the data gets exchanged through a wide open wireless communication channel, it is highly susceptible to message modification, tampering, impersonation, signature forgery, and side channel attacks9. Thus it provokes a hasty concern to protect the data that has been exchanged through the vehicles on the roads to enable a secure and a sustainable ITS. Traffic information being trapped or hijacked by an intruder may manipulate, modify or de-route the commuter leading to unforeseen consequences. The leakage of the sensitive data during the transit may also be viable which questions the integrity and the legality of the data being transmitted. Hence anonymity of data has to be ensured10. In case of medical emergencies, patient information on roads falling into the hands of intruder may tend to critical situations of life loss, delay in treatment or even medical errors11. Similarly, an invader having access to the personal travelling preference may have the possibility to exploit in any possible way. It is essential to preserve the privacy by means of pseudonyms. Usage of pseudonyms helps the signature verifier for tracking the original identification of the vehicles that involve in adverse illegal activities12. There is an exclusive need to process the large amount of messages being generated which may lead high computation delay or processing delays. Processing large amounts of messages by the RSUs may be cumbersome, overloading resulting in attrition, exposed, physical side-channel attacks, replication attacks, DoS attacks and TPD attacks in the network13. This consequence will lead to the decline in the performance of the network. In order to achieve security and privacy several authentication schemes relating to public key-based14, identity-based15, pseudonym-based16, certificate-less cryptography17,18 have been proposed. Most of these cryptographic schemes utilize either bilinear pairing or elliptic curves in order to ensure the security of the data being generated and transferred. Though ECC is 20 times faster than the bilinear pairing operation, it still suffers from lengthy signatures which degrade the computation efficiency and storage overhead19.
To alleviate these problems, it is desired to design a lightweight distributed authentication scheme by using Dickson polynomials has been proposed20. The proposed scheme utilizes lightweight mechanisms such as XOR operations and chaotic maps21 to ensure security and high connectivity among the vehicles in the network. The authentication is lightweight and employs Chinese Remainder Theorem for the dynamic distribution of group keys. Our method involves the following advantages. First, it effectively distinct security objectives and resists message modification, replay, impersonation and so on. Second, it reduces the computational overhead incurred with the cryptographic methods based on ECC or bilinear pairing which means that it performs distributed authentication.
Research gaps
Existing authentication schemes in VANETs suffers from problems such as central point of failure, traceability and privacy preservation. In addition, when the pseudonyms are stored inside the TPDs of the OBUs, there is a high possibility of TPD attack. TTA faces high computational burden when it performs message signature verification and revocation in a centralized manner. Chebyshev polynomial based conditional privacy preservation authentication scheme though it alleviates the aforementioned problems it suffers Bergamo et al.22 attack. These challenges provide a motivation to design a conditional privacy preservation authentication scheme that would be distributed, traceable, revocation and thereby achieving conditional privacy preservation in VANETs.
Major contributions
The major contributions of the proposed authentication scheme are outlined as follows:
-
A new distributed group key agreement authentication scheme has been proposed to ensure conditional privacy preservation implemented using Dickson polynomial in lieu of ECC or Bilinear Pairing with reduced computation and communication overheads.
-
The proposed scheme is lightweight, distributed and performs dynamic distribution of group keys using Chinese Remainder Theorem (CRT) where the vehicles are managed efficiently while stepping in or out of a group thereby achieving V2V and V2I communications
-
The proposed scheme achieves location, user, conditional privacy, traceability and resists replay, message modification and impersonation attacks, TPD and Bergamo et al.22 attacks being encountered.
-
The proposed scheme utilizes group key authentication to reduce the computational burden incurred by the TTA while performing verification by making it distributed. This alleviates the central dependency problem associated with the conventional authentication schemes.
-
A formal security analysis has been carried out by using both BAN logic and ROR model to demonstrate the security of the proposed scheme. Performance analysis has also been carried out by using performance metrics such as computation, communication, storage costs and verification delay.
Organization of the article
The manuscript has been structured as follows: “Introduction” Section encompasses the introductory segment, while “Related Works” Section delves into the comprehensive examination of the research endeavors pertaining to group key authentication techniques. “Preliminaries” Section introduces the foundational elements, system design, and security objectives that serve as the foundation for the proposed distributed authentication scheme. “Proposed Methodology” Section elaborates on the methodology of the authentication scheme. “Security Analysis” Section presents both the formal and informal security analysis. “Experimental Setup and Performance Metrics” Section offers a performance evaluation of the proposed authentication scheme, including benchmarks. Finally, “Results Discussion and Analysis” Section concludes the paper. Table 1 presents a compilation of abbreviations employed in the present study.
Related works
Various Authors have proposed numerous mechanisms to counter the issues related to security and privacy by designing numerous authentication schemes. To achieve security, conditional privacy and to improve the efficiency schemes such as certificate-based, identity-based, pseudonym-based, certificate-less are proposed. This section provides a brief understanding of some of the related works pertaining to authentication schemes.
Conditional privacy preserving authentication schemes (CPPAs)
CPPA ensures security, anonymity and traceability in the network. Upon any malfunctioning, CPPA provides efficient tracing back of vehicles with the help of pseudonyms stored inside the TPDs of the vehicles. Several schemes based on conditional privacy preservation have been proposed by various academicians around the globe. Among them, Liang et al.23 proposed an authentication scheme to address the problem of ESL from the storage devices by utilizing PUFs. Their system model also addressed the problem of computational overhead soars due to frequent contact with the vehicles in motion. Their proposed authentication scheme utilized PUFs to achieve conditional privacy authenticated key agreement for VANETs. The proposed PUF based mutual authentication between the vehicles and RSUs does not require the participation of TA. Utilization of pseudonym and conditional privacy provides anonymity and traceability in case of malevolent vehicles. The proposed protocol is resilient against cloning, physical, vehicle-RSU impersonation, MiTM, replay, ESL and known session key attacks. However, the computation and communication cost soars high which needs to be reduced. Yang et al.24 has come up with a secure, pairing-free, energy-efficient CLAS scheme which ensures CPPA for VANETs. Their proposed scheme addresses the problem of coalition attacks from malicious RSUs and public-key replacement attacks from malicious vehicles. Their proposed scheme involves ECC based authentication scheme which provides anonymity of vehicle identity and traceability of malevolent vehicles. Their methodology is secure against public key replacement, forgery, and tampering, malicious KGC, coalition attacks and lowers the computation and communication costs efficiently. Roy et al.25 has come up with a novel multiple TA model for fog-enables VANETs to address the problems of centralized trusted authority, single-point-of-failure, service unavailability due to increased traffic load. Their proposed model involves multiple TAs where the traffic processing load has been distributed across many sub-TAs. Their model also incorporates a fog node which takes care of the managing the RSUs centrally eliminating the need to perform individual authentication of RSUs. Their proposed protocol involves CPPA ensuring security and privacy it suffers from high computation and communication costs. Additionally utilized TA may behave as malevolent which weakens the security strength of the proposed scheme. Zhu et al.26 proposed a CLAS based authentication scheme based on ECC. Their proposed system utilized ECC based multiplication, one-way hash functions, XoR operation and dynamic pseudonyms in order to guarantee security and privacy. However the proposed protocol suffers from high computational overhead. TA incurs additional overhead in maintaining subsequent updation of pseudonyms. Zhang et al.27 proposed a novel authentication scheme based on HSMs to address the problem of certificate storage. In order to lower the computation costs, forward secrecy, a lightweight authentication scheme that ensures CPPA has been proposed. Their scheme involves SSK updation which involves identity-based batch multi-signature algorithm which ensures traceability and revocation. Though the proposed work reduces the computational complexity to a considerable extent, it still suffers from communication overhead due to frequent secret session key updates. Wang et al.28 has come up with a CPPA ensure anonymity and conditional privacy. The proposed authentication scheme has been designed without pseudonyms and is resilient to linkage attacks. Their proposed scheme is efficient and achieves anonymity, unlinkability, non-repudiation, message integrity, traceability and revocation. Though their proposed scheme is computationally efficient it is suitable only for V2V communications. Roy et al.29 has come up with an authentication protocol which has backed up by the elimination of TA ensuring zero-trust mechanism for VCS. Their scheme addressed the problem of communication delay, central tendency and DoS with the help of 5G connectivity. Their system has utilized ECC and Secret sharing scheme to ensure the security against vehicles and RSUs and provides support for both V2V and V2I communications. However the authentication delay is still high which needs to get reduced. Kumar et al.30 proposed a (2,n) threshold secret sharing scheme in combination with ECC to provide solution to the problem of computational overhead, authentication delay and re-authentication. Their proposed scheme eliminated the use of TA and subsequently reduces the communication overhead. The major novelty is that atleast two of n registered vehicles cooperation is required to compute a shared secret key which is highly not possible for an attacker to counter. Though the proposed scheme ensures security and privacy, the computation and the communication cost is higher in case of V2I communications. Moni et al.31 proposed a pseudonym-based privacy preservation scheme to address the problem of traceability incurred in processing the certificate revocation lists. Though it reduces the overhead it suffers from storage cost in maintaining the cuckoo filter and is not suited for V2I communications. Samra et al.32 has come up with a CPPA scheme based on ECC and ring signatures. Though the scheme achieves traceability it suffers from computation overhead and non-repudiation. Wang et al.33 proposed a certificate-less conditional privacy preservation scheme based on Bilinear pairing. Their work has achieved full aggregation and reduced the communication cost, it suffers from high computation cost due to pairing operation. Wang et al.34 has come up with a certificate-less CPPA to ensure unlinkability, anonymity and to lower the computational and computational overhead incurred in VANETs. Their proposed scheme involves the use of Bilinear pairing technique and ensured traceability, anonymity. Though it is resilient against reply, impersonation, message modifications and MiTM attacks it has to be tested and validated for real-time implementations. Xiong et al.35 proposed a mutual authentication protocol to ensure conditional privacy, anonymity and traceability in VANETs to address the problem of forward and backward secrecy. Their proposed protocol utilized bilinear maps and puncturable authentication along with parallel key insulation technique which eliminates the computational overhead incurred when authentication involves RSUs. However the authentication delay is very high.
Group key agreement authentication schemes (GKAs)
Group key Agreement authentication schemes have been proposed to reduce the computational overhead incurred by the TTA thereby eliminating the central point of failure. To ensure security and conditional privacy several GKAA schemes have been proposed. Among them, Ali et al.36 has proposed group shared key authentication scheme based on ECC and a combiner for hash function to provide security in case of IIoTs. Their proposed scheme utilized group secret keys between the industrial objects. Digital signatures are utilized and the scheme is highly resilient against attacks such as brute force, stolen verifier table, device capture, MiTM, Cipher-text, key attacks. However their protocol needs to be verified for computational and communication overheads. Zhan et al.37 proposed a secure group authentication scheme where the GKA are updated based on condition matching to ensure conditional privacy in VANETs. Their proposed authentication scheme involves the use of ECC and fog-computing for VANETs in order to reduce the problem of computational overhead and key management burdens. The scheme achieves cross-domain authentication, anonymity, traceability, key-escrow freeness, perfect forward secrecy and is resistant to attacks such as replay, impersonation and modification attacks. However, their schemes incur high computation and communication costs which need to get reduced. Li et al.38 has come up with a MAC based group key authentication scheme to achieve anonymity and conditional privacy. The scheme lags in key update mechanism and is vulnerable to security attacks. It cannot achieve forward and backward security. Islam et al.39 proposed a secure password based GKAA scheme to achieve conditional privacy. Though their work has reduced the computational cost to a greater extent it still suffers from communication overhead since it involves repeated communication with the transport authority. Cui et al.40 addressed the problem of security and privacy by proposing a novel dynamic GKA scheme to prevent forgery and session specific key attacks. Though the protocol extremely supports C-V2X application is suffers from high communication overhead which needs to be reduced. paliwal et al.41 has come up with a novel multi-party GKA scheme to ensure conditional privacy, and to overcome the data breach during data transmission. Their proposed protocol incurs authentication and communication delay which involve high transmission cost. Xu et al.42 addressed the problem of forward secrecy and malicious attacks by proposing a continuous GKA for IoVs. Their main aim is to design a GKA which provide efficiency against collusion attacks. The proposed protocol utilizes treeKEM architecture for group key authentication and management along with threshold secret sharing scheme for encryption. Though their protocol reduces the computation cost it still suffers from communication overhead during the communication and key updation phase. Cui et al.43 proposed a conditional privacy preserving GKA using chaotic maps for VANETs. Though their proposed protocol efficiently lowers the computation overhead it is high susceptible to Bergamo et al.22 attacks and suffers from high communication cost. Lai et al.44 has come up with a three party key agreement authentication scheme utilizing Chebyshev chaotic maps for VANETs. Their scheme suffers from the disadvantage such as bilinear pairing which incurs high computation overhead and is suitable only for V2I communications. Similarly, Lee et al.45 utilized Chebyshev chaotic maps based on diffie-hellman assumption. The major advantage is that it reduces the computational complexity incurred in signing and verification. Yang et al.46 proposed a Chebyshev polynomial based GKAA scheme to achieve conditional privacy and traceability. However, the proposed scheme is suitable only for V2V communications. The major drawback of the scheme is that it cannot resist Bergamo et al.22 attack where the security assumption is based on real numbers and is sensitive to initial value47,48. Table 2 provides the comparative analysis of various authentication schemes. From the literary related works, it is apparent that most of the CPPAs either use bilinear pairing or ECC to counter the TPD attacks and non-repudiation. However, these schemes suffer from computational complexity and increased length of signatures. Similarly, the GKAs suffer from high communication cost, forward and backward security. Hence in order to counter these issues, our scheme aims to counter by utilizing pseudonym to achieve non-repudiation, forward and backward security and CRT for key management. Additionally, it is necessary to reduce the computational complexity of the TTA; the scheme is distributed where the computational burden gets reduced. In addition, the key operations and values are also reduced subsequently. This results in the design of a new authentication scheme to achieve conditional privacy preservation and traceability using the Dickson polynomial in VANETs.
Preliminaries
This chapter provides an overview of the context, concept and system design employed in the development of the proposed distributed authentication technique for vehicular ad hoc networks.
Dickson polynomial
Due to the irreducible property, polynomials find its applications in security and authentication49. Polynomial cryptography exhibits two different properties namely semi-group and irreducibility50. Utilization of Dickson polynomial offers security against TPD and ephemeral key attacks it finds application in key agreement schemes. Due to the irresistive nature of Chebyshev polynomial towards MiTM and Bergamo et al. attack Dickson polynomial has been adopted51,52,53,54,55. Dickson polynomials are defined over the finite field recursively which depends upon the parameter \(n\) and \(a\) mapping the elements bijectively which makes it highly suitable for low resource-constrained environment like VANETs56
Dickson Polynomial and its properties: Dickson Polynomial20 for a variable \({\text{a}} \in {\text{F}}_{{\text{q}}}\) defined by an integer n; then the Dickson Polynomial \({\text{D}}_{{\text{n}}} \left( {{\text{x}},{\text{ a}}} \right)\) over any finite field \({\text{F}}_{{\text{q}}}\) can be defined as
where \(\frac{n}{2}\) is the largest integer \(\ge \frac{n}{2}\). The Dickson Polynomials gets gratified by the continuous relation such that \(D_{n} \left( {x,\alpha } \right) = x D_{n - 1} \left( {x,\alpha } \right) - \alpha D_{n - 2} \left( {x,\alpha } \right); n{ \succcurlyeq }2.\) Under the initial condition \({\text{D}}_{0} ({\text{x}},{\upalpha }\)) = 2 and \({\text{D}}_{1} ({\text{x}},{\upalpha }\)) = x and some of the other polynomials are computed by using the Eqs. (2–5) as follows:
The most important characteristic property of the Dickson polynomial is that is satisfies commutativity under composition when \(\alpha\) = 0 or 1.
Definition 1: Semi-group Property: Dickson polynomials exhibit semi-group property under composition which can be defined as follows:where p is a prime number. Hence
The semi-group property exhibited by the Dickson polynomials is an essential property and finds a wide variety of cryptographic applications which is given by the Eq. (6).
Definition 2: Chaotic-Map based Dickson Diffie-Hellman Problem (CMDDHP): For any given value of x; where \(x \in \left( { - \infty ,\user2{ } + \infty } \right)\); \(D_{u} \left( x \right)mod p, D_{v} \left( x \right)mod p\) for a large prime p. It is intransigent to compute \(D_{uv} \left( x \right)mod p\)47.
Chaotic map based hash function
Due to the properties of variable-dependency and abstract correlation; chaotic maps are utilized to build the hash functions. One notable benefit of utilizing chaotic hash is its ability to streamline normal procedures. Chaotic Hash function57,58 used along with Dickson-based sequences alleviates the problem of computational overhead and storage complexity. This results in increase in the performance of the OBUs. The algorithm works according to46 which consist of both the input and the output as follows:
Input: A discrete length of a string of bits which is of length y.
Output: Chaotic Hash Value of 128 bits.
Chinese remainder theorem (CRT)
CRT asserts that, under the condition that the divisors are pairwise co-prime, it is feasible to determine the remainder of an integer divided by its product in a unique manner, provided that the remainders resulting from the Euclidean division of n by multiple integers are known23.
CRT can be stated as follows:
Let \(\left\{ {l_{1} , l_{2} ,l_{3} , \ldots , l_{n} } \right\}\) be the set of positive integers which are relatively prime to one another;
Let \(\left\{ {b_{1} ,b_{2} ,b_{3} , \ldots ,b_{n} } \right\}\) be the set of positive integers. Therefore the pair of congruences given by the chinese remainder theorem can be defined as.
{\(Z \equiv b_{1} mod l_{1}\); \(Z \equiv b_{2} mod l_{2} , \ldots ,Z \equiv b_{n} mod l_{n}\)} gives an individual solution defined by \(mod \partial_{h} = \mathop \prod \limits_{i = 1}^{n} \left( {l_{i} } \right)\). The trusted transport authority finds the solution based on the Eq. (7)
where \(\theta_{i} = \frac{{\partial_{h} }}{{l_{i} }}\) and \(\theta_{i} \vartheta_{i} \equiv 1 mod l_{i}\).
System design
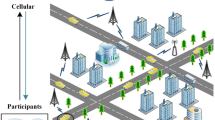
The typical architecture of a conventional VANET comprises of essential components namely the trusted transport authority (TTA), which includes the Key Generation Center (KGC) and the Authentication Server (AS), as well as the Road-Side Units (RSUs) and the On-Board Units (OBUs). The logical description of these components is achieved through the utilization of three levels, specifically referred to as the upper layer, the middle layer, and the bottom layer. The uppermost tier of the architecture comprises of the TTA, the KGC, and the AS while the intermediate layers comprises of RSUs. The lowest layer is comprised of the vehicles. The exchange of information among these three constituents is enabled by an IEEE standard, namely IEEE 802.11p, which is commonly referred to as DSRC. RSUs serve as an intermediary entity that facilitates communication and coordination between the TTA, KGC, and OBUs. The architectural structure adheres to a hierarchical design in which data transmission is authenticated through the utilization of two private keys generated by both the key generation center and the trusted transport authority. The concatenation of these partial private keys serves as a shield against forging, replay, impersonation, and various other forms of attacks. To compromise a specific message, an intruder must possess two partial private keys and one secret key of the vehicle, hence rendering it highly resistant to key ephemeral assaults. The distributed nature of the VANET model employed in our proposed system is illustrated in Fig. 1. Figure 2 depicts the operational framework of the proposed system.
Trusted transport authority (TTA)
TTA is mainly responsible for the initialization, functioning and generation of the public parameters required for the system. TTA is highly trustworthy and it cannot be compromised. The communication between the TTA and the AS can be accommodated wirelessly by means of EAP59,60,61. This protocol takes the responsibility of the vehicle registration, RSUs and AS. Furthermore, legal measures are implemented to address the issue of vehicle impersonation or masquerading, with the capability to trace the true identity of the vehicle in question during any legal procedures. This guarantees the retention of conditional privacy within the system.
Key generation center (KGC)
KGC is a separate entity which exhibits functionality such as generation of partial private key for secure message communications. KGC possess enough storage and processing capabilities which administers the role of managing and storing the keys. KGC is fully trusted and cannot be compromised37.
Authentication server (AS)
AS performs the verification of messages received from the vehicle or the RSUs. Both KGC and AS shares the same database that contains keys. AS stores all the traffic information in the form of database records and performs analytics very often. It is fully trusted and cannot be compromised39.
Road-side units (RSUs)
RSUs are mainly responsible for the communication between the OBUs and the Upper layered components. RSUs are installed for every 500 m and they are responsible for the message signature verification. RSUs are partially-trusted and are authenticated during the installation of the system by the TTA. RSUs are equipped with sensor device, servicing platform and a V2I communication platform. Utilization of RSUs makes it possible to achieve both V2V and V2I communications.
On-board units (OBUs)
OBUs are the vehicles which are registered with the TTA in an offline manner. After registration, each vehicle gets installed with the public parameters by taking the private aspects of each vehicle. Each vehicle is fitted with a TPD called as OBUs. Vehicles communicate with each other with the help of these on-board units. Each vehicle is fitted with communication systems called GPS and sensors for navigation which is responsible for the transmission and record-keeping of highly crucial information like messages and private keys.
Adversary model
The adversarial model for the proposed authentication scheme is simulated in the form of a game between an adversary \(\zeta_{1}\) and the rival \(\eta_{1}\). The adversarial model of existential unforgeability against chosen-message attacks (EUF-CMA) can be defined as follows:
Initialization: The system initialization algorithm is executed by the rival \(\eta_{1}\) in order to generate the system public parameters \(pms.\) The public parameters are then sent to the adversary \(\zeta_{1}\) and the rival \(\eta_{1}\) in a secret way thereby seizing the master secret key \(o\).
Queries: The adversary \(\zeta_{1}\) attempts to query on messages selected by the adversary in an adaptive way. In order to execute a signature query on the message \(M_{i}\), then the rival performs the execution of the message signature generation algorithm in order to compute the message signature \(\sigma_{i}\) and dispatches it to the adversary \(\zeta_{1}\).
Forgery: The adversary \(\zeta_{1}\) returns a signature which is forged \(\sigma_{i}^{\prime }\) on a particular message \(M_{i}^{\prime }\) and succeeds in the game iff.
-
\(\sigma_{i}^{\prime }\) is the legitimate signature pertaining to the message \(M_{i}^{\prime }\)
-
During the querying phase, queries are not performed for the message signature \(\sigma_{i}^{\prime }\)
The major benefit \({\Im }\) in succeeding the game indicates the generation of a valid forged signature. When \({\Im }\) is trivial for any polynomial adversary \(\zeta_{1}\) then the proposed authentication scheme is secure.
Security goals
Data transmission in VANETs has to be secured. In the proposed work, the group key agreement authentication scheme should satisfy the security properties such as message authentication, data integrity, perfect forward secrecy, perfect backward secrecy, conditional privacy preservation, traceability, unlinkability, anonymity.
Data integrity and message authentication
The received data should not be tampered, modified but preventing the data loss and leaks, errors and unauthorized access. The vehicle must be authenticated before it acquires the group key for message transmission.
Perfect forward secrecy
Upon any attack, even if the current session key gets compromised, the attacker should not gain any access to the previous session key utilized for Vehicular communications.
Perfect backward secrecy
Ensuring that the attackers cannot gain access to future session keys even if the current session key gets compromised during vehicular communications.
Conditional privacy preservation
The attacker should not be able to access or break into the original identity of the vehicle involved in communication. In case of legal proceeding TTA or AS performs revocation.
Traceability
Upon any illegal activity, it is necessary to trace and revoke back the original identity of the vehicle by the TTA or AS.
Unlinkability
Only TTA possess the capability to performs the linking of messages sent from the same vehicle.
Anonymity
The original identity of the entities such as \(V_{{ID_{i} }}\) and \(RSU_{{ID_{i} }}\) cannot disclose their original identity thereby ensuring the anonymity with the help of the pseudonyms.
Non-repudiation
The sender cannot deny the sending of the message.
Mutual authentication
All the entities involved inside the communication should verify the legitimacy of each other during the mutual authentication and group key agreement (GKA) phase.
Resistance to attacks
The proposed scheme must be resistant to attacks such as replay, message modification, impersonation, coalition, Man-in-the-Middle, Key Exposure, DoS and ESL attacks.
Proposed methodology
The proposed distributed authentication scheme’s primary objective is to provide conditional privacy preservation in VANET communications by facilitating efficient group key agreement authentication. It is composed mainly of eight phases namely 1. System Initialization Phase 2. Offline Registration Phase 3. Group Key Computation Phase 4. Group Key Distribution Phase 5. Mutual Authentication Phase 6. Message Signing and Verification Phase 7. Group Key Updation Phase and 8. Pseudonym Updation Phase. The first module to be created is called "System Initialization," and its primary job is to generate crucial parameters necessary for the system’s initial operation. Additionally the group key is computed during this phase. In the second phase, known as offline registration, vehicles and RSUs are added to the system and given public and private keys for use in further communications. The group key distribution section is the third component. Here, the TTA must produce the group key that will be used later in the process to authenticate and verify messages.
The fourth phase, known as Group Key distribution phase is responsible for concealing the true identities of vehicles and roadside units behind fictitious names, or pseudonyms. The mutual authentication process is the fifth and the sixth module. The vehicles now have the group key and can reliably communicate with each other while still within range of the roadside equipment. The sixth stage is the group key updation phase. In this step, the group key is updated anytime a vehicle joins or departs the group. The seventh section deals with the generation and signature of messages. In this step, vehicles collect data on the road’s state and construct a time stamped message that must be sent to other nearby vehicles or roadside equipment. The eighth modules consist of the pseudonym updation phase. Table 3 provides the description of the symbols utilized in our proposed scheme.
System initialization phase
TTA initiates the system initialization phase. TTA computes the field of prime numbers over the galois field by selecting an odd prime number and a random positive integer. Additionally, TTA chooses a system secret key for the whole system from the multiplicative field. To compute a Dickson polynomial, KGC selects a random number from the Galois field of a selected prime number. Following the selection of a random number, KGC selects a secret key for each car and RSU that will be given out at the time of vehicle registration and forwards it to the TTA. Algorithm 1 provides the steps involved in the system initialization phase.
Offline registration phase
Offline vehicle registration phase
Each vehicle and RSU is securely registered offline with the TTA before to the particular system’s operation. The personal credentials such as name, address, phone number, email address, car number, type, and Iris biometric data are all submitted by each owner of a vehicle. Following TTA registration, KGC generates a special secret Dickson group key for every car and sends it to that vehicle. The procedures to be taken during the offline registration phase are listed in Algorithm 2. A duplicate of the same is then kept in the AS’s tracking database. The third step illustrates how the identification and secret key of the matching vehicle are kept in the tracking database.
Offline RSU registration phase
The RSUs are registered with the TTA prior to the RSUs being installed. The first step illustrates how the location and identity of the RSUs are obtained during registration. Following verification, KGC computes the Dickson polynomial and the Dickson secret key, which serve as the corresponding RSU’s public key and are represented in step 4. Algorithm 3 provides the steps necessary for offline RSU registration phase. Next, KGC selects the RSU secret key that has been transmitted to it. A duplicate of the secret key will be kept in the KGC database, as indicated by equation in the final step.
Dickson’s group key computation phase
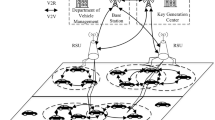
Users or vehicles in the same communication RSU range must first go through an authorization process before they can receive a group key for message creation and authentication. A vehicle notifies the KGC of its approach to the RSU’s coverage region by sending an authentication request. The step 1 shows how the KGC and AS choose a new group key in response to the request. It then broadcasts the private key to all of the RSUs and cars in group G, as shown in step 2 and step 3 after calculating the private key for the vehicle that approaches the RSU coverage range. The step 4 shows how the vehicle can access a new domain key that was calculated using the CRT after it has been authorized. The list of steps needed to calculate the Dickson’s group key computation is given in Algorithm 4. The figure illustrates the group key computation and distribution phase in Fig. 3.
Group key distribution phase
In this phase, a pseudonym is given to every single vehicle before any communication is initiated. To produce the pseudonym for a vehicle, the Dickson polynomial must be calculated, as indicated using the step 1.Every vehicle communicates with the TTA using an authentication request message. Following receipt of the request, it directs the KGC to create a pseudo-identity allowing vehicle in order to enable communication, as indicated by the step 2. Every vehicle receives an authorized public key that may be used to describe the message using the step 3. Vehicles near an RSU need to be validated during this phase in order to ensure the group key’s authenticity. It comprises the generation of messages for authentication as well as their verification. Figure 5 describes how the vehicles are authenticated. Algorithm.5 has provided a description of the group key distribution. Prior to being sent from the car to the RSU, all messages are encrypted using the step 4, the Dickson polynomial, and the Dickson secret key.
Mutual authentication phase
Only after the AS computes the vehicle’s original identity using the matching Dickson polynomial and verifies the vehicles timestamp to get vehicle authorized. The original identification that has been decrypted is confirmed against the tracking database that is shared with the KGC and AS. Step 3 indicates that a vehicle is authentic if the matching vehicle identity is found in the database. Algorithm.6 has outlined the procedures that must be followed during the mutual authentication phase. Figure 4 provides the steps required for vehicle authentication.
Group key updation phase
The group key updating phase initiates when a vehicle leaves the RSU’s communication range, as shown by step 1 and step 4. Tree based logical key hierarchy rekeying procedure is followed where the group keys are updated dynamically62. The procedures to be followed during the group key updating phase are given in Algorithm 7.
Message signature generation and verification phase
Message signature generation phase
According to Step 1 and 2, traffic information is transmitted by selecting a new pseudo-identity and a current timestamp, which is then sent to the vehicle or RSU for verification because the communication entities are authenticated using the Dickson secret key and the Dickson polynomial. The procedures to be followed during the message signing phase are given in Algorithm 8.
Message signature verification phase
When the message signature is received, the vehicle or the AS verifies it by utilizing step 1 and step 2 to compare the message signatures received. The step 2 is used to verify the correctness proof. The procedure for the single message verification is provided in Algorithm 9. Figure 5 provides the message authentication among the vehicles.
Pseudonym updation phase
Every time the vehicle enters an urban region, it frequently changes its pseudonym to protect location privacy. Each vehicle produces a Dickson group polynomial from the pseudo-identity production phase, as indicated using the Eq. (33) as follows:
Security analysis
This section provides the security analysis for the proposed authentication scheme in terms of formal security proofs and informal security proofs to validate its security strengths and its resilience to security attacks. Formal security analysis has been carried out by using BAN logic and ROR model. Since both of them serve for distinct purpose wherein BAN logic ascertain the logical correctness of the authentication proofs while ROR model verifies the security strengths of the authentication scheme.
Formal security analysis based on BAN logic
This section provides an analysis based on BAN logic63 to validate the security features of the proposed distributed group key authentication scheme. The most important rules of the BAN logic are as follows:
-
Axiom 1: Information-Definition Rule: \(\frac{{R| \equiv R \leftrightarrow S, R \triangleleft Y_{k} }}{{R\left| { \equiv S} \right| \sim Y}}\)
-
Axiom 2: Time-Stamp Verification Rule: \(\frac{{R| \equiv \# \left( Y \right), R\left| { \equiv S} \right| \sim Y}}{{R\left| { \equiv S} \right| \equiv Y}}\)
-
Axiom 3: Authority Rule: \(\frac{{R\left| { \equiv S \Rightarrow Y, R} \right| \equiv S| \equiv Y}}{R| \equiv Y}\)
-
Axiom 4: Aliveness-Concurrence Rule: \(\frac{R| \equiv \# \left( Y \right)}{{R| \equiv \# \left( {Y,Z} \right)}}\)
-
Axiom 5: Access Key Rule: \(\frac{{R\left| { \equiv \# Y,R} \right| \equiv S| \equiv Y}}{{R| \equiv R\mathop \leftrightarrow \limits^{k} S}}\)
There are four objectives which are supposed to be achieved and are as follows:
-
Obj 1: \(TTA\left| { \equiv KGC} \right| \equiv RSU_{{ID_{i} }} ,~TTS_{{RSU_{i} }} ,~M_{{V_{i} }} ,~\Delta T_{i} ^{\prime }\)
-
Obj 2: \(RSU_{i} | \equiv PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( y \right),\Delta T_{i}\)
-
Obj 3: \(V_{i} | \equiv t_{i}\)
-
Obj 4: \(V_{j} \left| { \equiv V_{i} } \right| \equiv PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,{\mathcal{L}}_{i}\)
In order to carry out the formal security analysis, the messages are exchanged between the TTA, KGC, AS, RSUs and OBUs are formulated as follows:
-
Msg1:\(V_{i} \to RSU_{j} :\left\{ {PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( y \right),\Delta T_{i} } \right\}\)
-
Msg2: \(RSU_{j} \to KGC:\left\{ {RSU_{{ID_{i} }} ,~TTS_{{RSU_{i} }} ,~M_{{V_{i} }} ,~\Delta T_{i} ^{\prime } } \right\}\)
-
Msg3: \(KGC \to V_{i} :g_{i}\)
-
Msg4: \(V_{i} \to V_{j} :\left\{ {PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,{\mathcal{L}}_{i} } \right\}\)
The rudimentary formulations required for the formal verification proofs are as follows:
-
P1: \(RSU_{j} | \equiv RSU_{j} \mathop \leftrightarrow \limits^{{(m_{i } , D_{{n_{i} }} \left( {m_{i} } \right))}} V_{i}\)
-
P2: \(RSU_{j} | \equiv \# \Delta T_{i}\)
-
P3: \(RSU_{j} | \equiv V_{i} \Rightarrow PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( Y \right),\Delta T_{i}\)
-
P4: \(KGC| \equiv \# \Delta T_{i}^{\prime }\)
-
P5: \(KGC| \equiv RSU_{j} \Rightarrow \left( {RSU_{{ID_{i} }} ,S_{{RSU_{i} }} } \right)\)
-
P6: \(V_{i} | \equiv V_{i} \mathop \leftrightarrow \limits^{{DSK_{i} }} TTA\)
-
P7: \(V_{i} | \equiv \# \Delta T_{i}\)
-
P8: \(V_{i} \left| { \equiv TTA} \right| \equiv DSK_{i}\)
-
P9: \(V_{j} | \equiv V_{j} \mathop \leftrightarrow \limits^{{t_{i} }} V_{i}\)
-
P10: \(V_{j} | \equiv \# TS_{{V_{i} }}\)
According to the formulated hypothesis and rational premises of BAN logic, the formal proof verification of the proposed authentication scheme is as follows:
By using the message 1, the following statements are obtained:
-
Q1: \(RSU_{j} \triangleleft \left\{ {PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( y \right),\Delta T_{i} } \right\}_{{\left( {(m_{i } , D_{{n_{i} }} \left( {m_{i} } \right))} \right)}}\)
According to Q1, P1 and Axiom 1, it is obvious that:
-
Q2: \(RSU_{j} \left| { \equiv V_{i} } \right| \sim PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( y \right),\Delta T_{i}\)
According to Q2, P2, Axiom 2 and Axiom 4, it is obvious that:
-
Q3: \(RSU_{j} \left| { \equiv V_{i} } \right| \equiv PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( y \right),\Delta T_{i}\).
According to Q3, P3 and Axiom 3, it is obvious that:
-
Q4: \(RSU_{j} | \equiv PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( y \right),\Delta T_{i} \quad \left( {\text{Obj 2}} \right)\)
By using the message 2, the following statements are obtained:
-
Q5: \(KGC\left| { \equiv RSU_{j} } \right| \sim RSU_{{ID_{i} }} ,~TTS_{{RSU_{i} }} ,~M_{{V_{i} }} ,~\Delta T_{i} ^{\prime }\)
According to Q5, P4, Axiom 2 and Axiom 4, it is obvious that:
-
Q6:\(~KGC\left| { \equiv RSU_{j} } \right| \equiv RSU_{{ID_{i} }} ,~TTS_{{RSU_{i} }} ,~M_{{V_{i} }} ,~\Delta T_{i} ^{\prime }\)
According to Q6, P5 and Axiom 3, it is obvious that:
-
Q7: \(KGC| \equiv RSU_{{ID_{i} }} ,~TTS_{{RSU_{i} }} ,~M_{{V_{i} }} ,~\Delta T_{i} ^{\prime } \quad \left( {{\text{Obj 1}}} \right)\)
By using the message 3, the following statements are obtained:
-
Q8:\(V_{i} \triangleleft t_{i} x {\complement }\)
According to Q8, P6 and Axiom 1, it is obvious that:
-
Q9:\(V_{i} \left| { \equiv KGC} \right|\sim t_{i} x {\complement }\)
According to Q9, P7, Axiom 2 and Axiom 4, it is obvious that:
-
Q10: \(V_{i} \left| { \equiv KGC} \right| \equiv t_{i} x {\complement }\)
According to Q10, P8 and Axiom 3, it is obvious that:
-
Q11: \(V_{i} | \equiv g_{i} \quad \left( {\text{Obj 3}} \right)\)
By using the message 4, the following statements are obtained:
-
Q12:\(V_{j} \triangleleft PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,{\mathcal{L}}_{i}\)
According to Q12, P9 and Axiom 1, it is obvious that:
-
Q13: \(V_{j} \left| { \equiv V_{i} } \right| \sim PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,{\mathcal{L}}_{i}\)
According to Q13, P10, Axiom 2 and Axiom 4, it is obvious that:
-
Q14: \(V_{j} \left| { \equiv V_{i} } \right| \equiv PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,{\mathcal{L}}_{i} \quad \left( {\text{Obj 4}} \right)\)
It is obvious that the proposed authentication scheme through the security analysis made using BAN logic has achieved all the formulated objectives and thereby provides an assurance of mutual authentication between the vehicles. It is also apparent that vehicles receive correct group key after the mutual authentication which makes vehicles to have a communication with the same group key within the range of road-side units. From these results obtained, it is obvious that our proposed authentication scheme according to the definition (1 and 2) it is not possible to crack due to the CMDDHP.
Formal security analysis based on ROR model
In VANETs, the communication proceeds between the road-side units and the vehicles through a wide open wireless communication channel, it is obvious that the network is susceptible to hackers and malevolent users which are unavoidable. Analysis using ROR has been adopted from Vallant et al.64. To prove that our proposed authentication mechanism is safe from adaptive selected message attacks, the following proofs are presented.
Definition:
It is not possible for an invader to gain access to an entity \(\left( {t, \beth , p} \right)\) to perform an adaptive chosen message attack under a signature authentication scheme. P denotes the number of \(H_{2}\) hash queries in the random oracle.
Theorem 1:
The ROR states that any invader A with a probabilistic polynomial time executes the game (Definition 4) and succeeds with probability which cannot be left out in the corresponding polynomial time, then the simulator with the probabilistic polynomial time can solve CMDDHP problem not less than within a span of \(\beth^{\prime} = \frac{\beth }{p}\) in that polynomial time.
Proof:
Let us assume that an invader \(\chi\) can be able to gain access and generate the message as \(\left\{ {PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,{\mathcal{L}}_{i} } \right\}\). Let \(\psi\) be an imposter that has been built on \(\chi\), so \(\psi\) describes the capability to provide solution to the CMDDHP problem executed by \(\chi\) with a ruled out probability. With an instance sample \(\left\{ {Z, q,y,f\left( y \right),p = q^{o} } \right\}\) of the CMDDHP problem, \(\psi\) imposter oracles which are challenged by \(\chi\) as follows:
Setup: The Imposter \(\psi\) fix \(p = q^{o}\) and chooses an abstract integer \(\lambda_{i} \epsilon Z\) which is utilized to establish an anonymous set \({\text{PSID}}_{{v_{n} }} = \left\{ {PSID_{{v_{1} }} ,PSID_{{v_{2} }} , \ldots ,PSID_{{v_{n} }} } \right\}\) where \(i \epsilon \left\{ {1,2, \ldots ,n} \right\}\).
Imposter \(\psi\) selects an abstract integer \(t_{i} \epsilon Z\) and computes the public group key as \(g_{i} = \gamma_{i} x {\complement }\). Then the imposter \(\psi\) sends these parameters as \(pms = \left\{ {Z, P,t_{i} {\complement }, H_{1} ,H_{2} } \right\}\) and the anonymous set \(K_{{ID_{{i,n}} }}\) to the invader \(\chi\).
H2 Hash Query: If the invader \(\chi\) makes an \(H_{2}\) query by having a pseudo-identity \(PSID_{{v_{i,n} }}\), the imposter \(\psi\) examines whether the tuple \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,\tau _{{H_{2} }} } \right\rangle\) is present in the hash list \(L_{{H_{2} }}\) or not. Iff the tuple presents in the list, then the imposter \(\left\langle {\tau _{{H_{2} }} = H_{2} {\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} } \right\rangle\) dispatch to \(\chi\). Else \(\psi\) selects an abstract \(\tau_{{H_{2} }} \in Z\) and then appends \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,\tau _{{H_{2} }} } \right\rangle\) it to the hash list \(L_{{H_{2} }}\). At the end, \(\psi\) gives \(\left\langle {\tau _{{H_{2} }} = H_{2} {\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} } \right\rangle\) to \(\chi\).
H3 Hash Query: When an invader \(\chi\) makes an \(H_{3}\) query with the message \(\left\langle {PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,\tau_{{H_{2} }} } \right\rangle\), the imposter \(\psi\) examines iff the tuple \(\left\langle {PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} } \right\rangle\) is already present in the list \(L_{{H_{3} }}\) or not. Iff the tuple presents in the list, then the imposter \(\tau _{{H_{3} }} = H_{3} \left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,M_{i} } \right\rangle\) dispatch to \(\chi\). Else \(\psi\) selects an abstract \({\tau }_{{H}_{3}}\in Z\) and then appends \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,M_{i} ,\tau _{{H_{2} }} } \right\rangle\) it to the hash list \(L_{{H_{2} }}\). At the end, \(\psi\) gives \(\tau _{{H_{3} }} = H_{3} \left\langle {{\text{PSID}}_{{ID_{i} }} ,M_{i} ,TS_{{V_{i} }} } \right\rangle\) to \(\chi\).
Sign Query: If the invader \(\chi\) generates a signing inquiry on the message \(M_{i}\) and the pseudo-identity \({\text{PSID}}_{{ID_{i} }}\), then the imposter \(\psi\) examines the tuple value \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,\tau _{{H_{2} }} } \right\rangle\) from the hash list \(L_{{H_{2} }} .\) Then the imposter \(\psi\) picks up \(\tau_{{H_{2} }}\) from the tuple \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,\tau _{{H_{2} }} } \right\rangle\).
If \(i = i^{*}\); then the imposter \(\psi\) selects three abstract integers \(\phi_{i} ,\varphi_{i} ,{\Psi }_{i} \epsilon Z\), a random point \({\text{PSID}}_{{ID_{i} }}\); and computes \(V_{{ID_{i} }} =\) \(PSID_{{V_{i,n} }} D_{{n{ }\vartheta_{i,n} { }}} \left( {Y^{ - 1} } \right){ }mod{ }\left( {f\left( y \right)} \right)\). Then the imposter \(\psi\) appends \(\tau _{{H_{2} }} = H_{2} \left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} } \right\rangle ~and~\tau _{{H_{3} }} = \left\langle {H_{3} {\text{PSID}}_{{ID_{i} }} ,M_{i} ,TS_{{V_{i} }} } \right\rangle\) to the hash list \(L_{{H_{3} }}\); then dispatches \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,M_{i} ,\tau _{{H_{2} }} } \right\rangle\) to \(\chi\). According to the formulations specified, all the reply sent to the sign query becomes valid because \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,M_{i} ,\tau _{{H_{2} }} } \right\rangle\) has been answered in the game thereby satisfying:
Else \(i \ne i^{*}\); then the imposter \(\psi\) gets verified that it has obtained a valid signature and publishes it.
Output: The invader communicates \(\chi\) with the imposter \(\psi\) until \(\chi\) comprehend that the work has been completed. Therefore, the invader provides the message \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,M_{i} ,{\mathcal{L}}_{i} } \right\rangle\) as its output. The imposter checks whether the equation holds true or not.
If not the imposter \(\psi\) will end the process. By using the forgery axiom54, the invader may produce another legal valid message with \(\left\langle {{\text{PSID}}_{{ID_{i} }} ,TS_{{V_{i} }} ,M_{i} ,{\mathcal{L}}_{i} ^{*} } \right\rangle\) within a polynomial time, if it selects another \(H_{2}\) where \(V_{{ID_{i} }} \ne V_{{ID_{i} }}^{*}\). Hence we obtain:
From the Eqs. 36 and 37, it is deduced that
Now the imposter \(\psi\) produces the solution \(\left( {V_{{ID_{i} }} - V_{{ID_{i} }}^{*} } \right)^{ - 1} (\sigma_{i}^{*} - \sigma_{i} )\) for the proposed instance of the CMDDHP problem. Else the imposition will be ceased.
The correct solutions for the proposed instance of the CMDDHP problem can be assured based on the co-occurrence of the events as follows:
-
Event \(E_{1}\): The invader \(\chi\) produces and outputs a legal signature forgery.
-
Event \(E_{2}\): The invader \(\chi\) can forfeit a pseudo-identity \(PSID_{{v_{i} }} \ne PSID_{{v_{i} }}^{*}\)
Due to Prob \(\left[ {E_{1} } \right] = \beth\), Prob \(\left[ {E_{2} } \right] = \frac{1}{p}\); we get.
Prob \(\left[ {E_{1} E_{2} } \right]\) = Prob \(\left[ {E_{1} } \right]\) Prob \(\left[ {E_{2} } \right]\) = \(\beth x \frac{1}{p} = \frac{\beth }{p}\).
It is obvious that the imposter \(\psi\) can solve the instance of the CMDDHP problem with the advantage \(adv_{\psi } = = \frac{\beth }{p}\). Thus, the imposter \(\psi\) calculates y within a polynomial time with an waste probability with the advantage of \(\frac{\beth }{p}\) namely the solution to the CMDDHP problem which implies that the theorem 1 can be satisfied. However it is difficult to solve the CMDDHP within a minimum span of time. Hence, it proved that our proposed authentication scheme is secure against forgery under the adaptive chosen message attacks.
Formal security analysis using coq tool65
Coq is a formal security verification system that offers tools for the interactive creation of machine-checked proofs along with a programming language and logic for expressing mathematical prepositions, algorithms, and theorems. Coq has been extensively utilized in several fields, such as security verification for protocols based on polynomials cryptography, quantum communication66. Coq offers a high degree of assurance in the security of cryptographic protocols by enabling logical reasoning about their characteristics and behavior. The ability to formally reason about the behavior and characteristics of the protocol is one advantage of utilizing Coq for security verification of cryptographic protocols. This aids in locating possible weaknesses in the protocol and offers a means of demonstrating that it satisfies security standards.
Informal security analysis
In order to evaluate the safety measures used in our suggested authentication technique, informal security analysis has been presented below.
Message integrity and authentication
Since the authentication scheme utilizes group key based authentication strategy; it is necessary for vehicle to be verified as legitimate if it wants to join a group and connect with others. The Hash value created by the sender can be affirmed by using the formula \({\mathcal{L}}_{i} = H_{{t_{i} }} \left( {PSID_{{v_{i,n} }} \left\| {M_{i} } \right\|TS_{{V_{i} }} } \right)\). In order to verify the integrity of the message received, the receiver verifies the legitimacy of the hash value generated by using the group key as \({\mathcal{L}}_{i} = = {\mathcal{L}}_{i}^{*}\). If it holds then the message will be accepted.
Perfect backward secrecy
An intruder can compromise a group’s security by intercepting the freshly produced group key \(t_{i}\) and using it to unlock the private key \(DSK_{i} ;\) of one of the group vehicles. A large collection of positive integers related to the multiplicative field Z is also required for the random number generator used to produce the private keys. This feature makes it so the enemy can’t break into any other cars’ safes. Since the adversary cannot access the communication that had place before their entry into the group, the proposed solution satisfies the backward secrecy condition.
Perfect forward secrecy
It is obvious that any invader cannot find out the current group key \(t_{i}\) when leaving the group as formulated earlier in the backward secrecy technique. When a vehicle leaves its group, KGC removes it by subtraction which is the culmination of \(y_{i}\) and \(x_{i}\) and extracts \(\delta_{i}\) from \({\complement }\) to produce \({\complement }^{\prime }\). The newly generated domain key value \(g_{i}\) is formed by the culmination of the rekeying message \({\complement }^{\prime }\) and \(\gamma_{i}^{\prime }\). Without any requirement of the vehicle’s secret key it is possibly to get access to the new group key being generated even after leaving the group. These left vehicles from the group with its key information can be able to gain access to the new group key \(\gamma_{i}\), which is impractical to be sent as a broadcast message from the KGC. This means that the vehicle has to culminate its secret key with the integers from 1 to p, where p is the maximum group value. On a certain situation, the vehicle generates \({\mathfrak{H}} =\)ϰ′ (i.e., \(DSK_{i} x a = {\mathfrak{H}}\)). After the reception of the \(a\), a particular vehicle \(V_{i}\) obtains a series of integers n, which will divide the number \(a\). The set of integers can be defined as \(\left\{ {a mod 1,a mod 2, \ldots .,a mod a} \right\} = = 0\) each represents the value of n. From this obtained sequence of integers, the integer \(t_{i} \epsilon n\) is also involved in the generation of the new group key. Due to this fact, it is assumed that the size of \(\gamma_{i}\) is a bits, then the invader has to perform the modulo operation of \(2^{a}\). Hence, it is evident deducing the value of \(\gamma_{i}\) by selecting a large \(DSK_{i}\) value for a vehicle’s secret key is highly expensive and incurs high computational overhead. Let us assume that the size of \(DSK_{i}\) is fixed as 1024 bits which was previously set to 128, 256 and 512 bits. The attacker (after leaving the domain) can conduct a subsequent brute force attack to acquire the new domain key by selecting exploitable values from the set n that divides the integer a. If this effort takes 1 \(\mu\) s, then the total time taken will be \(2^{n - 1} \mu\) s would elapse. Our suggested technique meets the forward secrecy requirement since an attacker cannot gain the domain key to access the present communication.
Conditional privacy preservation
I. Identity Privacy Preservation: In order to retrieve the original identity the invader has to compute \(V_{{ID_{i} }} =\) \(PSID_{{V_{i,n} }} D_{{n{ }\vartheta_{i,n} { }}} \left( {Y^{ - 1} } \right){ }mod{ }\left( {f\left( y \right)} \right)\). However, \(\gamma_{i}\) is stored in the TTA, and \(t\) being a random number the invader cannot be able to gain access to the original identity. Because, it not possible to compute the CDHP. Therefore, the adversary will not be able to learn the user’s true identity even if the pseudo identity \(PSID_{{V_{i,n} }}\) is leaked. ii. Location Privacy Preservation: The proposed authentication scheme engulfs pseudonym updation mechanism, which means that the vehicles changes it pseudonyms constantly when it reaches the urban scenario thereby ensuring the location privacy.
Traceability
On any legal proceedings, KGC will trace back the original identity of the vehicle that has involved in any malfunction. It traces from its tracking database based upon the command from the trusted transport authority. Since KGC issues the pseudonyms required for the vehicle, it is impossible for any invader to guess the pseudo-identity since it was encrypted by using Dickson polynomial. KGC uses the original ID of the vehicle and the master secret n and computes \(V_{{ID_{i} }} =\) \(PSID_{{V_{i,n} }} D_{{n{ }\vartheta_{i,n} { }}} \left( {Y^{ - 1} } \right){ }mod{ }\left( {f\left( y \right)} \right)\). Our proposed authentication scheme uses Iris biometric for the vehicle identity verification, which provides an accurate way of tracing back the user’s identity by using its iris biometric. Iris biometric based recognition provides an efficient way to track back in case of any illegitimate signature sent by any vehicle.
Unlinkability
In our proposed authentication scheme, the message signature is generated by using a pseudo-identity \(PSID_{{V_{i,n} }}\). Since each pseudo-identity utilized for generating the message signature is significantly distinct and the random number utilized to verify the identities is never reused. Therefore, no opponent could link multiple signatures from the same vehicle thereby ensuring unlinkability.
Anonymity
Utilization of pseudonym provides the protection of the vehicle’s original identity which makes difficult for an adversary to compute the original identity of the vehicle except TTA.
Mutual authentication
In the proposed protocol the authenticity of the vehicles and RSUs are verified by using Dickson polynomial by AS. AS first checks and verifies for the timestamp \(\Delta T_{i}^{\prime }\) from the received message \(\{ RSU_{{ID_{i} }} , TTS_{{V_{i} }} , M_{{V_{i} }} , \Delta T_{i}^{\prime } \}\) where \(\Delta T_{i} = \Delta T_{i}^{\prime }\). If both are same, then the road-side unit is a legal identity which sends or relays the message. When the verification of the timestamp remains successful, then AS computes \(V_{{ID_{i} }} =\) \(PSID_{{V_{i,n} }} D_{{n{ }\vartheta_{i,n} { }}} \left( {Y^{ - 1} } \right){ }mod{ }\left( {f\left( y \right)} \right),{ }TTS_{{V_{i} }}^{\prime } = H\left( {V_{{ID_{i} }} \left\| {\Delta T_{i} } \right.} \right)\). Iff \(TTS_{{V_{i} }}^{\prime } = TTS_{{V_{i} }}\), then it checks the identity of the vehicle in the tracking database which is shared between the trusted transport authority and the key generation center. f the vehicle ID is present in the database then it is an authenticated vehicle. It then sends the command verified to the KGC to compute the group key \(DSK_{i}\). Hence mutual authentication is achieved.
Non-repudiation
The sender cannot be able to deny the message being sent since the message contains the pseudo-identity which is generated based on the Dickson polynomial. Since the original identity of the vehicle is encapsulated with the help of variable and timestamps, it is not possible for a vehicle user or RSU to deny the message being sent during vehicular communications. Thus our proposed scheme achieves Non-Repudiation.
Resistance to attacks
Impersonation attack
An invader willing to impersonate a vehicle to other vehicles or RSUs must have to generate a message \(\left\{ {PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,{\mathcal{L}}_{i}^{*} } \right\}\) thereby satisfying the equation \(\sigma_{i} .P = V_{{ID_{i} }} D_{{n \vartheta_{i,n} }} + M_{i} + H_{{\gamma_{i} }}\). According to theorem 1, it is impossible for a polynomial adversary to copy a genuine message signature is self-evident. Hence, our proposed authentication scheme is able to resist impersonation attack.
Message modification attack
It is possible for an opponent to alter a message and then rebroadcast it. Since the messages are authenticated using the chaotic hash function H, it is challenging to produce a genuine hash without the group key \(g_{i}\). When the message \(\{ PSID_{{v_{i,n} }} ,M_{i} ,TS_{{V_{i} }} ,{\mathcal{L}}_{i}^{*} \}\) gets modified, it cause \({\mathcal{L}}_{i} \ne H_{{t_{i} }} \left( {PSID_{{v_{i,n} }} \left\| {M_{i} } \right\|TS_{{V_{i} }} } \right)\) which means that the message will not be verified and accepted. Hence, it is evident that our proposed scheme can be able to resist message modification attack.
Replay attack
Normally, a replay attack involves bad actors sending out the repeated copies of previous messages. In our proposed scheme, since timestamp is included in every message generated the recipients can verify the life of the timestamp of the authenticated messages by checking the condition \(TS_{{V_{i} }}^{\prime } - TS_{{V_{i} }} \le \Delta T\) holds. Hence our proposed scheme is resilient towards replay attacks.
Coalition attack
It happen when several hackers or invaders collide together or attack together to get access to the private key. In the proposed authentication scheme, when the invaders attempts to compute the newly generated group key when the vehicles leave the group. Since it is obvious that the value of \(\delta_{i}\) is subtracted from \({\complement }\), some of the vehicles cannot collide to get access to the newly generated group key \(\gamma_{i}\) because the utilized pairwise relative prime number is expensively huge. Let us speculate that there are two invaders Invader \(I_{1}\) has gain access to the key values \(DSK_{1}\), \(\gamma_{i}\) and the invader \(I_{2}\) has gain access to the values \(DSK_{3}\), \(\gamma_{i}\) at time \(\left( {t - 2} \right)\). When the time is \(\left( {t - 1} \right)\), the invader probably may leave the group with its access privileges \(DSK_{1} and\) \(t_{i}\). When the time becomes \(t\), the invader \(I_{2}\) obtains the rekeying information \(r_{g}\) from KGC and computes \(\gamma_{i}\).When the time becomes \(\left( {t + 1} \right)\), the invader \(I_{2}\) left the group with its access privileges and both the invaders may exchange their access keys. However, it is not possible to gain access to the newly updated group key \(\gamma_{i}\) broadcasted at time \(\left( {t + 2} \right)\), because \(\delta_{1}\) and \(\delta_{3}\) are excluded from \({\complement }\). Hence, it is evident that our proposed authentication scheme can be able to resist coalition attacks.
MitM attack
Let’s pretend an enemy is lurking between any pair of cars, or RSUs. Since each communication happens by means of an authenticated group key which are directly involved by the Dickson polynomial, it is not possible to counterfeit the message signature which has been proved by using the theorem 1. Hence our proposed authentication scheme can be able to resist man-in-the-middle attacks.
Key exposure attack
There might be a possibility to gain access to the pseudo-identity while during the communication between any two entities involved. However it is not possible to guess the random number and the Dickson polynomial utilized to generate the pseudo-identity. Even if the key gets exposed, it is not possible for the invader to gain access to the original identity since it involves an expensive CDHP. Intruders cannot obtain or compute the distributed computed group key from both the KGC and AS without spending a lot of time and money. Therefore, our proposed method is secure against key-exposure attacks.
DoS attack
In the proposed authentication scheme follows the segregation of duties in producing the necessary keys, pseudo-identities, message signatures and verification which reduces the computation time when compared with its counterparts. In the proposed scheme, since we followed distributed approach for signature verification which has been employed to segregate to the AS following the process of verification. Hence the overhead at each component has been reduced which increases the computation speed to a greater extent. This implies that the entities present inside the network cannot deny its work even if it encounters multiple vehicles at the same time. Thus the proposed scheme is resilient to DoS attacks.
ESL attack
For each vehicle the pseudonym is generated by using the random number as defined as \(PSID_{{V_{i,n} }} = V_{{ID_{i} }} D_{{n \vartheta_{i,n} }} \left( y \right) mod \left( {f\left( y \right)} \right)\). The timestamp value for each vehicle is computed by using the chaotic hash function as \(TTS_{{V_{i} }} = H\left( {V_{{ID_{i} }} \left\| {\Delta T_{i} } \right.} \right)\). Each Vehicle \(V_{i}\) obtains the authenticated public key \(\left\{ {m_{i } , D_{{n_{i} }} \left( {m_{i} } \right)} \right\}\) where the message can be represented by the Eq. (23) as \(M_{{V_{i} }} = \left\{ {PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( y \right),\Delta T_{i} } \right\}\). The group key of the vehicle gets computed by choosing a random number \(o \in Z;o \ne 0,1\) and it computes \(D_{o} \left( {m_{i} } \right) where D_{{o n_{i} }} \left( {m_{i} } \right) = D_{o} \left( {D_{{n_{i} }} \left( {m_{i} } \right)} \right)\) and sends the encrypted text to the RSUs through an open wireless communication channel which can be depicted as \(Enc_{i} = \left\{ {D_{o} \left( {m_{i} } \right), M_{{V_{i} }} \oplus D_{{o n_{i} }} \left( {m_{i} } \right)mod f\left( y \right)} \right\}\) When the adversary tries to attack to retrieve the group key it is not possible to guess the random number. Additionally during the message generation the original identity is encapsulated with Dickson polynomial based on semi-group and irreducible property along with time stamp it not possible to compute \(D_{{o n_{i} }} \left( {m_{i} } \right)\) due to CMDDHP. From the Eq. (23) the group key gets computed with a random value which hidden and random adding an additional layer of flexibility is making it more secure and adaptable for key generation and encryption. Hence the proposed scheme is resistant towards ESL attack.
Side-channel/TPD attacks
Existing authentication schemes attempts to load /install the master secret key into the TPD of the vehicle where no attacker can compromise it. However, this information can be hijacked by the adversary by means of side-channel attack. In our proposed scheme, since the pseudonym gets updated periodically (“Pseudonym Updation Phase” Section) using \(PSID_{{V_{i,n} }} = V_{{ID_{i} }} D_{{n \vartheta_{i,n} }} \left( y \right) mod \left( {f\left( y \right)} \right)\). Thus our proposed scheme is resistant to Side-channel attacks.
Comparison of security properties
This section provides a comparative analysis of the proposed authentication scheme in terms of the security characteristics to that of the existing CPPA-GKA schemes23,25,26,27,29,30,35,37,40,42,48. From the Table 4 conditional privacy is guaranteed by23,25,35,40,42,48, ours; while identity privacy and location privacy is guaranteed by two schemes48, ours; Key escrow freeness is ensured by23,25, ours. Authentication schemes which are resilient to ESL attacks are23,25,35, ours. The proposed scheme is resilient against coalition attack, DoS attack and key exposure attacks.
Experimental setup and performance metrics
The experimental setup of the proposed distributed GKA scheme has been carried out by using the NS3 and SUMO traffic simulator. To prototype the vehicular communications, OMNET++ must first expose and design the performance of vehicles in SUMO. The work has been implemented by using Ubuntu 18.04 LTS on \({\text{Intel\textregistered Core}}^{TM}\) i7- i7-10610U processor and 4.90 GHz and 8 GB RAM. The simulation parameters have been depicted by using the Table 5 as follows:
Performance metrics
The performance aspects of the proposed distributed GKA scheme can be measured by using the performance metrics such as computation cost, communication cost and storage costs.
Computation cost (CMPC)
The work carried out on authentication scheme32 has employed the bilinear pairing operation which assumes a security parameter \({\text{\rm T}}\) of 180 bits which can be depicted as \(\widehat{e}: G_{1 } x G_{1 } \to G_{T }\). In the proposed authentication scheme utilized Dickson polynomial based cryptography where \(G_{1 }\) is an additive group of order \(\hat{p}\) and the generator \(\hat{q}\) which is a point on a on a multiplicative field Z where \(E:D_{n} \left( x \right) \equiv \left( {2xD_{n - 1} \left( x \right) - D_{n - 2} \left( x \right)} \right) mod p;\) with an embedding degree of order 2. It is obvious to choose that the length of p be 160 solinas prime number and q be 512 bits. The authentication scheme utilized MIRACL cryptographic library software in order to perform the necessary cryptographic operation on a 64-bit Ubuntu 16.04 Operating system and an i4-Gen CPU. Table 6 provides the basic assumptions of various cryptographic operations. Table 7 summarizes the notations and run-time efficiency of various cryptographic operations has been adopted from46,55,56. Performance analysis has been evaluated by comparing the proposed authentication scheme along with the existing schemes such as23,25,27,29,30.
The symbols utilized in the Table 4 are described as follows: \(T_{emul}\) defines the run-time efficiency of elliptic curve multiplication operation; \(T_{ea}\) defines the run-time efficiency of elliptic curve point addition operation; \(T_{esm}\) defines the run-time efficiency of the elliptic curve scalar multiplication operation; \(T_{ddp}\) defines the run-time efficiency of one scalar multiplication on Dickson polynomial; \(T_{DH}\) defines the run-time efficiency of dickson encryption; \(T_{h}\) defines the run-time efficiency of one hash function operation using secured chaotic hash algorithm; \(T_{DH}\) defines the run-time efficiency of dickson encryption; \(T_{GHKEY}\) defines the run-time efficiency of one keyed hash function operation chaotic maps; \(T_{pm}\) denotes the run-time efficiency of point multiplication operation; \(T_{pa}\) defines the run-time efficiency of point addition operation; \(T_{C/d}\) defines the run-time efficiency of symmetric encryption/decryption; \(T_{r}\) define the run-time efficiency of random number generation; \(T_{f}\) defines the run-time efficiency of fuzzy extractor; and \(T_{PR}\) defines the run-time efficiency of the pseudo-random function.
The total computation cost can be calculated by using the formula given in the Eq. (39).
Communication cost (CMMC)
For the computation of the communication cost, it is assumed that \(G_{1}\) and \(G\) are 128 bytes and 40 bytes. In case of addition the result of the hash function operation and the size of the timestamp can be calculated as 20 bytes and 4 bytes. It is also identified since our scheme utilizes finite field \(Z_{p}^{*}\) which involves the message size of 20 bytes. Communication cost can be calculated by using the Eq. (40) which is depicted as follows:
Storage cost (SC)
Storage cost can be defined as the number of bits required to perform authentication where the parameters are necessary to be stored. Storage cost is evaluated in terms of bits. The formula to compute the storage cost has been defined using the Eq. (41) as follows:
Results discussion and analysis
The distributed group key authentication scheme’s performance is analyzed here, taking into account factors like computation cost. The performance evaluation was completed using the aforementioned techniques as references depicted in Table 8. A comparative analysis of existing systems using characteristics such as fundamental hard problem, nature of security, grouping type, and presence/absence of bilinear pairing procedures has been provided in the table.
Computation cost
The cost of computation can be defined as the cost involved in performing all the cryptographic operations by the communicating entities inside the network. The proposed authentication scheme involves the entities such as vehicle, RSUs and TTA/KGC/AS. Therefore the computation cost incurred by the proposed authentication scheme with the vehicle can be defined as 4TDH + 2Th + Tr + Tmul + TGHKEY + Tkey + Tsign = 4 * 0.00207 + 2 * 0.0045 + 0.0106 + 0.2463 + 0.172 + 0.4420 = 0.00828 + 0090 + 0.0106 + 0.2463 + 0.172+ 0.4420 + 1.536 = 2.42418 ms. Similarly, the computation cost pertaining to RSUs is computed as 4Tddp + 4TDH + 2Th + TGHKEY + Tsign + Tverify = 4 * 0.172 + 4 * 0.00207 + 2 * 0.0045 + 0.172 + 1.536 + 6.044 = 8.28114 ms. Similarly in case of TTA/KGC/AS the computation cost can be defined as 6Tr + 3TGHKEY + 4Tkey + Tddp + 2TDH + 5Th + Tverify = 6 * 0.0106 + 3 * 0.172 + 4 * 2 .5597 + 2 * 0.00207 + 0.172 + 5 * 0.0045 + 6.044 = 0.0636 + 0.516 + 10.2388 + 0.00414 + 0.172 + 0.0225 + 6.044 = 17.0569 ms. Therefor the total computation cost incurred by the proposed protocol = 17.2474 ms. In a similar manner, for other existing schemes23,25,27,29,30, the computation cost is estimated and a comparative analysis has been presented using the Table 9 and Fig. 6. Table 9 provides the performance comparison in terms of computation costs.
From the Table 9 it is obvious that the proposed authentication scheme incurs lower computation overhead at the vehicle side and RSUs while at TTA/KGC/AS the computation cost is bit higher. However, the overall computational cost for the entire message transmission is very less due to the use of less computation based on Dickson polynomial whose security strength is extremely good than the existing counterparts. Since distributed key generation based mutual authentication is performed the proposed work incurs less computation costs.
Communication cost
Figure 7 provides the comparative analysis on the communication cost for the proposed authentication scheme to that of the existing schemes. Table 10 provides the computation and the comparison of the communication cost. The authentication delay is greatly reduced due to the use of chaotic hash function of 256 bits. The proposed Dickson polynomial provides an encrypted message length of 3456 bits. The communication cost for the proposed protocol at the vehicle side can be computed as \(M_{{V_{i} }} = \left\{ {PSID_{{V_{i,n} }} , TTS_{{V_{i} }} ,D_{{\vartheta_{i,n} }} \left( y \right),\Delta T_{i} } \right\}\) and \(D_{{o n_{i} }} \left( {m_{i} } \right) = D_{o} \left( {D_{{n_{i} }} \left( {m_{i} } \right)} \right)\) is defined as 800 bits. While at RSUs, the communication cost can be computed as \({\mathcal{L}}_{i}^{\prime } = H_{{\gamma_{i} }} \left\{ {PSID_{{V_{i,n} }} \left\| {M_{i} } \right\|TS_{{V_{i} }} } \right\}\) and \(\sigma_{i} .P = \left\{ {PSID_{{v_{i,n} }} \left\| {M_{i} } \right\|\left. {TS_{{V_{i} }} } \right\|{\mathcal{L}}_{i} } \right\} \cdot P\) which involves 1536 bits and at the TTA/KGC/AS side the cost of communication is 1120 bits. The overall cost of communication for a message transmission can be 3456 bits. The authentication scheme proposed incurs lower communication cost when compared with that of its counterparts. In a similar way, the communication cost for the other existing schemes23,25,27,29,30 are computed and compared which is depicted in the Table 10 and Fig. 7.
Storage cost
The overall storage cost can be computed by the number of bits needed by the entities inside the network. It is presumed that the cost of system parameters initialized during the system setup and vehicle registration are considered to be zero. The proposed authentication scheme involves the storage cost at the vehicle side is defined by \(\left\{ {{\text{D}}_{{\text{n}}} \left( {\text{y}} \right),{\text{ y}},{\text{ f}}\left( {\text{y}} \right),{\text{ H}}} \right\};{\text{ASID}}_{{\text{i}}} = { }\left\{ {{\text{V}}_{{{\text{ID}}_{{\text{i}}} }} ,{\text{DSK}}_{{\text{i}}} } \right\}; D_{o} \left( {D_{{n_{i} }} \left( {m_{i} } \right)} \right)\) which can be computed as 704 bits; at the RSU side is defined by \(\left\{ {{\text{RSU}}_{{{\text{ID}}_{{\text{i}}} }} ,{\text{S}}_{{{\text{RSU}}_{{\text{i}}} }} { }} \right\};\) \(\left\{ {{\text{m}}_{{\text{i }}} ,{\text{ D}}_{{{\text{n}}_{{\text{i}}} }} \left( {{\text{m}}_{{\text{i}}} } \right)} \right\}\) as 256 bits and at the TTA/KGC/AS side is defined by \(\left\{ {{\text{g}}_{{\text{i}}} ,{\text{kpvk}}_{{\text{i}}} ,{\text{DS}}_{{{\text{kpvk}}_{{\text{i}}} }} \left( {{\text{g}}_{{\text{i}}} ||\Delta {\text{T}}_{{\text{i}}} } \right)} \right\}\); \(PSID_{{V_{i,n} }} = V_{{ID_{i} }} D_{{n \vartheta_{i,n} }} \left( y \right) mod \left( {f\left( y \right)} \right)\) is 384 bits. In a similar way, the storage cost is computed for the other existing schemes23,25,27,29,30. Table 11 provides the performance comparison in terms of Storage costs to the proposed Vs existing authentication schemes. Figure 8 provides the comparative analysis of storage costs of the proposed authentication scheme.
From the comparative analysis, it is evident that the proposed protocol incurs less computation overhead, communication and storage costs. In some cases due to higher number of cryptographic operations computation and communication costs is relatively high. This is mainly due to the increase in the number of bits for message transmission. A small compromise is needed in order to achieve more security requirements.
Conclusion and future work
In this paper, we propose a conditional privacy preserving authentication and group key agreement authentication scheme for VANETs has been proposed. The proposed approach addressed the problem of computational burden in low-constrained resources of VANETs by using Dickson polynomial thereby optimizing the computing efficiency. By exploiting distributed approach, the scheme distributes the centralized role of TTA among KGC and AS thereby enhancing the robustness and countering the realistic demands of VANETs. Since the scheme employs distributed approach, the computational burden incurred by the TTA gets reduced thereby enabling group key agreement mutual authentication. The group key gets computed by the use of CRT which facilitates dynamic distribution and updation easily. Conditional privacy preservation can be achieved by the use of pseudonyms thereby assuring traceability and revocability. Since the group key is computed by means of distributed group key computation it provides enough security which is resilient towards TPD, ESL and Side-channel attacks. The scheme achieves traceability with the help of pseudonyms. The security strengths are proved using BAN, ROR model and Coq formal security verification tools and proofs are provided thereby demonstrating the resilience of the authentication scheme. Additionally a comparative analysis on security parameters, performance metrics has been analyzed with the existing schemes and is proven to be efficient than their counterparts. Finally the proposed protocol accomplishes the security and privacy properties with relatively low computation, communication and storage costs than the existing counterparts.
In the future work, distributed learning can be included where the scheme can be designed for data poisoning and free-rider attacks. Lattice and post quantum cryptographic approaches can be utilized to address the problems of security and privacy that benefits the low-resource constrained environment like VANETs.
Data availability
All data generated or analyzed during this study are included in this published article.
References
Sripathi Venkata Naga, S. K., Yesuraj, R., Munuswamy, S. & Arputharaj, K. A comprehensive survey on certificate-less authentication schemes for vehicular ad hoc networks in intelligent transportation systems. Sensors 23(5), 2682. https://doi.org/10.3390/s23052682 (2023).
Bagloee, S. A., Tavana, M., Asadi, M. & Oliver, T. Autonomous vehicles: Challenges, opportunities, and future implications for transportation policies. J. Mod. Transp. 24, 284–303 (2016).
Sharma, S. & Kaul, A. VANETs cloud: Architecture, applications, challenges, and issues. Arch. Comput. Methods Eng. 28, 2081–2102 (2021).
Javed, A. R. et al. Future smart cities: Requirements, emerging technologies, applications, challenges, and future aspects. Cities 129, 103794 (2022).
He, D., Zeadally, S., Xu, B. & Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forens. Secur. 10(12), 2681–2690 (2015).
Silva, L. et al. Computing paradigms in emerging vehicular environments: A review. IEEE/CAA J. Autom. Sinica 8(3), 491–511 (2021).
Commission, F.C. et al. Amendment of the commission’ rules regarding dedicated short-range communication service in the 5.850–5.925 ghz band. FCC, Washington, DC, USA, Tech. Rep. FCC pp. 02–302 (2002).
Wang, Y., Zhong, H., Xu, Y., Cui, J. & Wu, G. Enhanced security identity-based privacy-preserving authentication scheme supporting revocation for VANETs. IEEE Syst. J. 14(4), 5373–5383 (2020).
Cheng, L., Wen, Q., Jin, Z., Zhang, H. & Zhou, L. Cryptanalysis and improvement of a certi_cateless aggregate signature scheme. Inf. Sci. 295, 337–346 (2015).
Zhang, Y. et al. Efficient public verification of data integrity for cloud storage systems from indistinguishability obfuscation. IEEE Trans. Inf. Forens. Secur. 12(3), 676–688 (2017).
Rajasoundaran, S. et al. Machine learning based volatile block chain construction for secure routing in decentralized military sensor networks. Wirel. Netw. 27(7), 4513–4534. https://doi.org/10.1007/s11276-021-02748-2 (2021).
Wei, L., Cui, J., Xu, Y., Cheng, J. & Zhong, H. Secure and lightweight conditional privacy-preserving authentication for securing traffic emergency messages in VANETs. IEEE Trans. Inf. Forens. Secur. 16, 1681–1695 (2021).
Muthumeenakshi, R., Reshmi, T. R. & Murugan, K. Extended 3PAKE authentication scheme for value-added services in VANETs. Comput. Electr. Eng. 59, 27–38. https://doi.org/10.1016/j.compeleceng.2017.03.011 (2017).
Raya, M., Papadimitratos, P. & Hubaux, J. P. Securing vehicular communications. IEEE Wirel. Commun. 13(5), 8–15 (2006).
Shamir, A. Identity-based cryptosystems and signature schemes. in Proceedings of Advances in cryptology-CRYPTO 47–53 (1984).
Zhang, C., Lu, R., Lin, X., Ho, P. H. & Shen, X. An efficient identity based batch verification scheme for vehicular sensor networks. in Proceedings of IEEE INFOCOM 246–250 (2008).
Tan, H., Gui, Z. & Chung, I. A secure and efficient certificateless authentication scheme with unsupervised anomaly detection in VANETs. IEEE Access 6, 74260–74276 (2018).
Li, J., Yuan, H. & Zhang, Y. Cryptanalysis and improvement of certificateless ag-gregate signature with conditional privacy-preserving for vehicular sensor net-works. Networks 317, 48–66 (2015).
He, D., Chen, J. & Zhang, R. An efficient and provably-secure certificateless signature scheme without bilinear pairings. Int. J. Commun. Syst. 25(11), 1432–1442 (2012).
Paul, K., Singh, M. M., & Goswami, P. A new public key encryption using Dickson polynomials over finite field with 2 m. in Nonlinear Dynamics and Applications: Proceedings of the ICNDA 2022, 555–563. (Springer International Publishing, 2022)
Kocarev, L. Chaos-based cryptography: A brief overview. IEEE Circuits Syst. Mag. 1(3), 6–21 (2001).
Bergamo, P., D’Arco, P., De Santis, A. & Kocarev, L. Security of public-key cryptosystems based on Chebyshev polynomials. IEEE Trans. Circuits Syst-I 7(52), 1382–1393 (2005).
Liang, Y., Luo, E. & Liu, Y. Physically secure and conditional-privacy authenticated key agreement for VANETs. IEEE Trans. Veh. Technol. 72(6), 7914–7925 (2023).
Yang, X., Li, S., Yang, L., Du, X. & Wang, C. Efficient and security-enhanced certificateless aggregate signature-based authentication scheme with conditional privacy preservation for VANETs. IEEE Trans. Intell. Transp. Syst. 25(9), 12256–12268. https://doi.org/10.1109/TITS.2024.3367925 (2024).
Kumar, P. & Om, H. Multi-TA model-based conditional privacy-preserving authentication protocol for fog-enabled VANET. Veh. Commun. 47, 100785 (2024).
Zhu, D. & Guan, Y. Secure and lightweight conditional privacy-preserving identity authentication scheme for VANET. IEEE Sens. J. 24(21), 35743–35756. https://doi.org/10.1109/JSEN.2024.3431557 (2024).
Zhang, Z., Li, J., Li, Y., Cao, C. & Cao, Z. Hardware secure module based lightweight conditional privacy-preserving authentication for VANETs. IEEE Trans. Inf. Forens. Secur. https://doi.org/10.1109/TIFS.2024.3412418 (2024).
Wang, Q., Li, Y., Tan, Z., Fan, N. & Yao, G. Conditional privacy-preserving authentication scheme for V2V communication without pseudonyms. J. Inf. Secur. Appl. 78, 103616 (2023).
Roy, P. K., Kumar, P. & Bhattacharya, A. ZeroVCS: An efficient authentication protocol without trusted authority for zero-trust vehicular communication systems. Fut. Generat. Comput. Syst. 163, 107520 (2025).
Kumar, P. & Om, H. NextGenV2V: Authenticated V2V communication for next generation vehicular network using (2, n)-threshold scheme. Comput. Commun. 213, 296–308 (2024).
Moni, S. S., & Manivannan, D. A lightweight privacy-preserving V2I mutual authentication scheme using cuckoo filter in VANETs. in 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), 815–820 (IEEE, 2022).
Samra, B. & Fouzi, S. New efficient certificateless scheme-based conditional privacy preservation authentication for applications in VANET. Veh. Commun. 34, 100414 (2022).
Wang, H., Wang, L., Zhang, K., Li, J. & Luo, Y. A conditional privacy-preserving certificateless aggregate signature scheme in the standard model for VANETs. IEEE Access 10, 15605–15618 (2022).
Wang, Y., Liu, Y. & Tian, Y. ISC-CPPA: Improved-security certificate-less conditional privacy-preserving authentication scheme with revocation. IEEE Trans. Veh. Technol. 71(11), 12304–12314 (2022).
Xiong, H., Yao, T., Zhao, Y., Gong, L. & Yeh, K.-H. A conditional privacy-preserving mutual authentication protocol with fine-grained forward and backward security in IoV. IEEE Trans. Intell. Transp. Syst. 25(11), 15493–15511. https://doi.org/10.1109/TITS.2024.3465242 (2024).
Ali, W. & Ahmed, A. A. An authenticated group shared key mechanism based on a combiner for hash functions over the industrial internet of things. Processes 11, 1558. https://doi.org/10.3390/pr11051558 (2023).
Zhan, Y., Xie, W., Shi, R., Huang, Y. & Zheng, X. Dynamic privacy-preserving anonymous authentication scheme for condition-matching in fog-cloud-based VANETs. Sensors 24, 1773. https://doi.org/10.3390/s24061773 (2024).
Li, X., Liu, Y. & Yin, X. An anonymous conditional privacy preserving authentication scheme for vanets. in 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), 1763–1770 (IEEE, 2019).
Islam, S. H. et al. A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs. Fut. Generat. Comput. Syst. 84, 216–227 (2018).
Cui, B., He, W. & Cui, Y. A dynamic C-V2X anonymous authentication and group key agreement protocol. Int. J. Inf. Secur. https://doi.org/10.1007/s10207-024-00876-2 (2024).
Paliwal, S. & Chandrakar, A. (2019). A conditional privacy preserving authentication and multi party group key establishment scheme for real-time application in VANETs. Cryptology ePrint Archive.
Xu, G., Yin, X. & Li, X. ER-CGKA: Efficient and robust continuous group key agreement scheme with post-compromise forward security for IoV. PloS One 19(8), e0307867 (2024).
Cui, J., Wang, Y., Zhang, J., Xu, Y. & Zhong, H. Full session key agreement scheme based on chaotic map in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 69(8), 8914–8924 (2020).
Lai, H. et al. Provably secure three-party key agreement protocol using chebyshev chaotic maps in the standard model. Nonlinear Dyn. 77(4), 1427–1439 (2014).
Lee, T. F. Efficient three-party authenticated key agreements based on chebyshev chaotic map-based Diffie–Hellman assumption. Nonlinear Dyn. 81(4), 2071–2078 (2015).
Yang, J., Deng, J., Xiang, T. & Tang, Bo. A Chebyshev polynomial-based conditional privacy-preserving authentication and group-key agreement scheme for VANET. Nonlinear Dyn. 106, 2655–2666 (2021).
Wei, P., Liao, X. & Wong, K.-W. Key exchange based on Dickson polynomials over finite field with 2m. J. Comput. 6(12), 2546–2551 (2011).
Rivest, R. L. Permutation polynomial modulo 2ω. Finite Fields Their Appl. 7, 287–292 (2001).
Muratović-Ribić, A. & Pasalic, E. A note on complete polynomials over finite fields and their applications in cryptography. Finite Fields Appl. 25, 306–315 (2014).
Lima, J. B., Panario, D. & de Souza, R. C. Public-key encryption based on Chebyshev polynomials over GF (q). Inf. Process. Lett. 111(2), 51–56 (2010).
Xiao, D., Liao, X. & Deng, S. A novel key agreement protocol based on chaotic maps. Inf. Sci. 177(4), 1136–1142 (2007).
Kocarev, L. & Tasev, Z. Public-key encryption based on Chebyshev maps. in Proceedings of the 2003 International Symposium on Circuits and Systems, 2003. ISCAS’03, Vol. 3, III–III (IEEE, 2003).
Xiao, D., Liao, X. & Wong, K. W. An efficient entire chaos-based scheme for deniable authentication. Chaos Solit. Fract. 23(4), 1327–1331 (2005).
Han, S. Security of a key agreement protocol based on chaotic maps. Chaos Solit. Fract. 38(3), 764–768 (2008).
Xiang, T., Wong, K. W. & Liao, X. On the security of a novel key agreement protocol based on chaotic maps. Chaos Solit. Fract. 40(2), 672–675 (2009).
Paul, K., Singh, M. M. & Goswami, P. A new public key encryption using Dickson polynomials over finite field with 2 m. in Nonlinear Dynamics and Applications: Proceedings of the ICNDA 2022, 555–563. (Springer International Publishing, 2022).
Raya, M. & Hubaux, J. P. Securing vehicular ad hoc networks. J. Comput. Secur. 15(1), 39–68 (2007).
Zheng, Y. et al. Design and analysis of a security-enhanced three-party authenticated key agreement protocol based on chaotic maps. IEEE Access 8(2020), 66150–66162 (2020).
Ye, G., Jiao, K. & Huang, X. Quantum logistic image encryption algorithm based on sha-3 and rsa. Nonlinear Dyn. https://doi.org/10.1007/s11071-021-06422-2 (2021).
Rajkumar, Y. & Santhosh Kumar, S. V. N. An elliptic curve cryptography based certificate-less signature aggregation scheme for efficient authentication in vehicular ad hoc networks. Wirel. Netw. https://doi.org/10.1007/s11276-023-03473-8 (2023).
Rajkumar, Y. & Kumar, S. V. N. S. A lightweight privacy preserving distributed certificate-less aggregate based mutual authentication scheme for vehicular adhoc networks. Peer-to-Peer Netw. Appl. 17, 1442–1466. https://doi.org/10.1007/s12083-024-01636-8 (2024).
Inoue, D. & Kuroda, M. FDLKH: Fully decentralized key management scheme on logical key hierarchy. in Applied Cryptography and Network Security: Second International Conference, ACNS 2004, Yellow Mountain, China, June 8-11, 2004. Proceedings 2, 339–354 (Springer, 2004).
Burrows, M., et Abad, M. & Needham, R. A logic of authentication. Proc. R. Soc. Lond. A. Math. Phys. Sci. 426, 233–271 (1989).
Vallent, T. F., Hanyurwimfura, D. & Mikeka, C. Efficient certificate-less aggregate signature scheme with conditional privacy–preservation for vehicular ad hoc networks enhanced smart grid system. Sensors 21, 2900. https://doi.org/10.3390/s21092900 (2021).
Abate, C., Haselwarter, P. G., Rivas, E., Van Muylder, A., Winterhalter, T., Hriţcu, C., Maillard, K. & Spitters, B. Ssprove: A foundational framework for modular cryptographic proofs in coq. in 2021 IEEE 34th Computer Security Foundations Symposium (CSF), 1–15 (IEEE, 2021).
Haselwarter, P. G. et al. SSProve: A foundational framework for modular cryptographic proofs in Coq. ACM Trans. Program. Lang. Syst. 45(3), 1–61 (2023).
Funding
Open access funding provided by Vellore Institute of Technology.
Author information
Authors and Affiliations
Contributions
All the authors have contributed in a equal manner.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Ethics approval
Authors provide the ethical approval for the given manuscript.
Consent to publish
All the authors gave permission for consent to publish.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Rajkumar, Y., Santhosh Kumar, S.V.N. A Dickson polynomial based group key agreement authentication scheme for ensuring conditional privacy preservation and traceability in VANETs. Sci Rep 15, 6211 (2025). https://doi.org/10.1038/s41598-025-89208-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-025-89208-5
Keywords
This article is cited by
-
Lightweight identity authentication and key agreement scheme for VANETs based on SSL-PUF
Scientific Reports (2025)