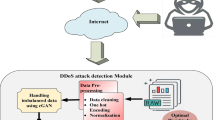
Abstract
The integration of advanced technologies into the infrastructure of modern smart grids has revolutionized the efficiency and reliability of energy distribution systems. However, the increasing reliance on interconnected digital systems exposes smart grids to various cyber threats, with distributed denial-of-service (DDoS) attacks posing a significant risk. This paper presents an effective method for identifying smart grid DDoS attacks by introducing the use of the deep neural network VGG19 combined with the Harris Hawks Optimization Algorithm (HHO). The suggested approach uses the robust feature extraction capability of VGG19-DNN for network traffic pattern analysis to detect abnormal traffic flows indicative of DDoS attacks. These features are then optimized using the HHO to enhance accuracy and efficiency. The approach also utilizes a distributed architecture for real-time monitoring and response, enabling timely mitigating of DDoS threats without compromising smart grid performance. The efficacy of the proposed framework is evaluated through extensive simulations and experiments using real-world smart grid datasets. Results demonstrated that the proposed approach outperforms existing methods in terms of detection accuracy and computational efficiency. Moreover, the robustness of the proposed solution against different attack scenarios is analyzed, and its scalability for large-scale deployments is validated. A comprehensive framework for protecting smart grids from DDoS attacks is developed, enabling more robust resilience and security of critical energy infrastructures against increasingly sophisticated cyber threats.
Similar content being viewed by others
Introduction
The security of the Internet of Things (IoT) is a critical topic and a key global issue1. Without IoT security, the capabilities of this network are reduced, and the confidentiality of information is compromised2. One of the most important issues in IoT security is countering network attacks, especially those targeting network infrastructure3. Today, most IoT services are provided as service-based offerings4.Application services are mostly hosted in the cloud computing layer and deliver a variety of functionalities to users. However, one of the major challenges associated with these services is the risk DDoS attacks and CrossFire attacks5. Cybersecurity involves protecting digital systems, networks, and data from unauthorized access, damage, or cyber-attacks6,7. A Distributed Denial-of-Service (DDoS) attack is a type of cyber threat in which multiple compromised systems generate excessive traffic to overwhelm a network or service, making it unavailable to legitimate users8,9. These attacks can disrupt smart grid operations by flooding communication channels or servers with fake requests10.
In the first type, the server is attacked with a large number of malware-infected nodes, and in the second type, the server’s communication links are attacked. Identifying and classifying offensive traffic from normal traffic is the focus of this research. Specifically, the problem involves categorizing network traffic into normal and abnormal classes, which can be solved with deep learning (DL) and data mining methods.
Current methods for detecting DDoS attacks often face challenges such as high false alarm rates, limited adaptability to emerging attack patterns, and inefficiencies in processing high-dimensional network traffic. To address these limitations, this study proposes a novel model that integrates deep feature extraction using the VGG19 architecture with optimization based on the HHO Algorithm. This combined approach significantly improves detection accuracy while reducing computational overhead.
Classification tools are essential for detecting attacks such as DDoS or CrossFire on the IoT. Machine learning-based classification methods need to select the optimal feature to analyze network traffic with minimal time and error. In this research, the Long Short-Term Memory (LSTM) deep learning network is utilized for attribute identification, and the important features of network traffic are to multiple classification techniques instead of relying on a single one. In the proposed method, several learning algorithms, such as SVM, ANN, and DT are used to classify network traffic. A majority voting mechanism is then applied to the results from these three methods to determine whether the traffic is normal or abnormal.
This research has several objectives, which are listed below:
-
Feature selection within DL to identify important features associated with attacks.
-
Increase IoT security.
-
Deal with botnets and nodes infected with malware.
-
Combining the learning mechanism of machine learning methods to reduce classification error.
Attacks such as DDoS or CrossFire cause significant damage to the network and their infrastructure. In attacks such as DDoS, application services are targeted, rendering them unable to provide services to users. Network attacks have devastating effects on smart cities, such as disruptions to electricity, subway systems, and transportation networks. These IoT attacks significantly undermine users’ trust in security services, Thus, it is essential to deliver effective and accurate Security breach detection systems.
Conventional detection techniques typically rely on fixed rule sets, manual feature extraction, and limited learning capabilities. As a result, they struggle to recognize emerging attack patterns, adapt to evolving threat landscapes, and efficiently process large-scale datasets. Furthermore, their limited ability to reduce false positives hampers real-time detection and degrades overall system performance.
The most important advantage of this research lies in the development of a security system that combines multiple machine learning (ML) methods using a majority voting mechanism11,12. This approach allows any ML technique prone to errors to reduce its impact by contributing to the majority vote. Another benefit of the suggested approach is the integration of DL for feature selection, which reduces the dimensionally of network traffic during the feature selection phase. The main challenge of this method, like other machine learning and DL methods, is the time spent on training13.
The primary contribution of this thesis is the development of a computational fog-based detection system14. This system operates within the computational fog layer and this system is implemented across distributed computational fog nodes15, where each node functions as an independent network intrusion detection system equipped with a majority voting mechanism16.The core contribution of this research is the identification of attacks in the lower layer of the computing cloud with group learning in fog nodes17,18,19,20,21. Conventional intrusion detection systems (IDS) in smart grids are often unable to effectively detect and respond to increasingly sophisticated and dynamic DDoS attacks in real time. This underscores the urgent need for an intelligent, scalable, and accurate IDS that can handle complex traffic patterns without relying solely on manually engineered features.
Research objectives:
-
To develop a hybrid framework for DDoS detection by integrating the VGG19 deep learning model with the Harris Hawks Optimization Algorithm (HHOA).
-
To enhance the effectiveness of feature selection and optimize model hyperparameters for improved performance.
-
To validate the proposed approach using benchmark smart grid datasets, ensuring its effectiveness under real-time operational conditions.
Literature review
A crucial asset in safeguarding smart grids against malicious activities is an intrusion detection system, adept at pinpointing potential attacks by scrutinizing network traffic for irregularities. Various techniques, including blocklist approaches22, , heuristic methods23, and advanced ML approaches are employed to detect and counteract threats24.
While blocklist approaches maintain a repository of known attack patterns, they often required substantial memory resources and may fail to detect novel attacks. Heuristic methods rely on evidence and exploration functions to identify attack patterns but are hindered by notable error rates. In contrast, deep learning (DL) and ML methods excel in detecting previously unseen or “zero-day” attacks, making them pivotal components in the development of robust intrusion detection systems for smart grids. This part provides a comprehensive review and analysis of pertinent research endeavors focused on enhancing attack detection capabilities within smart grid environments.
In a recent study25, a DL technique combined with a feature section was introduced for detecting cyber intrusions with smart grid systems. The studies suggested an innovative Bayesian method integrated with convolutional neural networks (CNNs) to enhance attack detection accuracy. Their approach utilizes CNN layers for real-time feature extraction from industrial control system datasets, achieving complete accuracy in attack detection when utilizing LSTM and recurrent neural networks (RNNs). reference26 explores identifying attacks on smart grids through federated learning, framing anomaly detection as a classification challenge. By employing various ML techniques, including logistic regression and 1D-CNN, the study aimed to differentiate between normal and irregular network traffic, with the 1D-CNN approach proving superior in detecting attacks.
Research27 suggests adversarial generative networks, including XGBoost CGAN, with WCGAN and gradient enforcement to improve the stability of attack detection models. Evaluation of intrusion detection datasets like UNSW-NB15, NSL-KDD, and BoT-IoT demonstrates superior effectiveness compared to traditional methods such as Random Forest (RF), Decision Tree (DT), and Support Vector Machine (SVM) and surpassing the DGM approach in terms of accuracy.
The study28 introduced a DDoS detection technique that employs the physical and cyber systems of SDN networks. Utilizing information entropy and unsupervised anomaly detection methods, this strategy identifies suspicious elements and detects DDoS attacks. With an average precision rate of 99.13% for recognizing DDoS attacks, their methodology significantly reduces the false positive rate by 35–59% as evaluated with similar approaches.
In paper29, a blockchain platform was introduced to mitigate attacks on intelligent networks. Experimental results demonstrate that in the presence of significant attacks, this strategy shows a strong capability to detect such intrusions.
In reference30, an approach was developed employing an enhanced firefly algorithm (FA) alongside a CNN to detect DDoS attacks within an SDN-IoT setting. The FA is integrated into the research to augment the CNN’s capacity for identifying DDoS attacks. Evaluations demonstrated a 98% accuracy rate in detecting these attacks.
Prior studies31 introduce an ML-driven intrusion detection system for smart grids, utilizing Arduino, Zigbee, and Raspberry Pi sensors, Assessments revealed that the Gaussian SVM demonstrates superior precision in detecting attacks.
A recent study32 introduces a novel intrusion detection method for smart grids, integrating SMOTE and Extremely Randomized Trees (ERT) techniques to enhance cybersecurity. The ET-SMOTE approach, which categorizes five types of network traffic, demonstrates notable precision in detecting intrusions when tested on the NSL-KDD dataset.
Additionally, in a separate investigation33, researchers introduce an advanced intrusion detection system tailored for smart grids, utilizing five distinct ML methodologies. Their system exhibits impressive performance metrics, boasting a precision rate of 98.4%, minimal attack detection delay of approximately 5 microseconds, a low false positives rate of 0.28%, and a modest false negative rate of 1.32%.
In reference34, a hybrid DT approach is introduced for detecting intrusions within smart grids. This innovative method integrates three DTs to effectively detect intrusions. Experimental evaluations conducted with the NSL-KDD dataset reveal that their approach outperforms traditional techniques, such as SVM, nearest neighbor, and singular DT in accurately identifying attacks.
Another study35 introduces an intrusion detection network for SDN-based intelligent networks that uses a CNN to identify uncommon network activity from two-dimensional data. An assessment conducted on the UNSW_NB15 and KDDCup 99 datasets demonstrates its superior performance in detecting attacks compared to LSTM. Furthermore, in a subsequent study36, an improved feature selection technique utilizing the PSO algorithm is proposed to enhance attack detection on benchmark datasets NSL-KDD and UNSW-NB15 through the application of a DL-based anomaly detection approach incorporating autoencoders, resulting in F1 scores of 92.09% and 92.90%, respectively.
In study37, a novel ML approach is introduced for detecting intrusions in smart grids, combining ML with signature recognition methods to effectively identify attacks on intelligent energy Networks. This integrated approach demonstrates significant efficiency in detecting intrusions on the smart grid framework. Table 1 provides a comprehensive overview of relevant methodologies for detecting attacks in smart grids, detailing the methods, benefits, limitations, and datasets employed for comparison.
Material and method
Dataset collection and preprocessing
The suggested intrusion detection system is implemented and assessed using the NSL-KDD dataset. Of the 42 features in the KDD-NSL dataset, 41 are input features and 42 are output features. Of the 23 traffic types in the NSL-KDD dataset, 22 are attacks, and just one is typical traffic34,38. The CGAN approach is used to balance the attack samples in the NSL-KDD dataset since there are more normal examples than attack samples, making the dataset unbalanced.
While the paper introduces the use of CGANs to balance the NSL-KDD dataset, a more detailed explanation of the CGAN architecture is needed. The CGAN employed in this study consists of two components: a generator and a discriminator, both structured as multilayer perceptrons. The generator is conditioned on class labels (such as normal or attack traffic types) to generate synthetic feature vectors that match these classes. The discriminator, on the other hand, receives both real and synthetic samples along with their corresponding labels, enabling it to distinguish between authentic and generated data. Before training, the dataset is preprocessed using normalization and PCA-based dimensionality reduction. This approach ensures the generation of high-quality synthetic data that closely aligns with real data distributions, thereby enhancing the training process for subsequent classifiers.
These datasets include comprehensive information about network traffic patterns, including packet headers, source and destination IP addresses, timestamps, communication protocols, other any relevant metadata. The raw dataset has been preprocessed to improve its quality and suitability for training the deep neural network (DNN) model and optimization algorithm. Steps include:
-
Data Cleaning: Remove any corrupt or incomplete data entries to maintain data integrity.
-
Feature Extraction: Extract relevant features from the dataset, such as packet size, communication frequency, and network topology information.
-
Normalization: scale the features to a standardized range to ensure uniformity and facilitate convergence during training.
-
Dimensionality Reduction: Employ techniques like principal component analysis (PCA) or feature choice to decrease the dimensionality of the dataset while protecting significant data.
VGG19 deep neural network architecture
VGG19 is a deep convolutional neural network that is well-suited for capturing hierarchical feature representations, making it particularly effective for analyzing complex network traffic patterns.
-
Model architecture: implement the VGG19 architecture, a well-established CNN model known for its deep architecture and excellent feature extraction capabilities.
-
Pre-training: Initialize the VGG19 model with weights pre-trained on large-scale image datasets (e.g., ImageNet) to use the learned features for initial pattern recognition.
-
Fine-tuning: fine-tune the pre-trained VGG19 model using transfer learning techniques on the smart grid dataset. This process involves updating weights and biases of the network layers to adapt them to the specific characteristics of network traffic data.
Harris Hawks optimization algorithm (HHO)
HHO is inspired by the cooperative hunting strategies of hawks, offering an optimal balance between exploration and exploitation. Collective intelligence utilizes cooperation and daily interactions within the population to solve optimization challenges, mimicking the collaborative hunting strategies tactics found in diverse animal species such as insects, arthropods, and mammals. This process, evident in metaheuristic approaches, entails individuals within the population near lure or presents the best solution, jointly exploring their environment for advantageous prospects. An example of this concept is the HHO technique, introduced in 201939 which mirrors the cooperative hunting conduct of hawks, usually operating in groups of no more than six members. This behavior is demonstrated in Fig. 1.
The hunting process of collective insight in the HHO algorithm39.
Hawks’ ability to hunt collectively is attributed to the lack of bait in their arid region habitat. Initially, a small group begins the hunt, with more members joining for cooperation. During this process, all hawks converge around the bait or optimal solution pursued by a single bird. The algorithm identifies, encircles, and attacks the bait, with each hawk representing a solution. To help readers understand the process, each mathematical step in the HHO algorithm demonstrates how hawks adjust their positions (candidate solutions) while searching for the optimal solution (minimal error). The equations describe the hawks’ exploration and exploitation behaviors within their environment. This equation represents the random search pattern of hawks as they seek potential solutions39. This equation represents the random search pattern of hawks as they seek potential solutions:
Equation (2) updates the positions of hawks or solutions from the current iteration \(X\left(t\right)\) to the subsequent one \(X(t+1)\). \({X}_{rabbit}\left(t\right)\) represents the optimal solution’s position, while \({X}_{rand}\left(t\right)\) indicates an arbitrary location in the challenge domain. \({X}_{M}\left(t\right)\)signifies the focal point of the hawk population, with \({r}_{1}\), \({r}_{2}\), \({r}_{3}\), and \({r}_{4}\) denoting random numbers from 0 to 1, and \(LB\) and \(UB\) representing the bottom and top ends of the solutions. This equation updates each hawk’s position by considering both the global best position and randomness:
Equation (3) in the HHO model describes the transformation of hawk behavior as the energy coefficient (E) decreases from an initial value (like 2) to zero, guiding the transition from exploration to pursuit. The equation involves variables such as \({X}_{i}\left(t\right)\)for solution positions and \({X}_{M}\left(t\right)\)for the population’s center of gravity. Figure 2 visualizes the fluctuation of E throughout iterations, indicating this behavioral transition, with \({E}_{0}\) representing the primary power and T denoting the algorithm’s maximum repetition limit. This equation represents energy loss over time, transitioning the behavior from search to attack.
Within the HHO approach, a sequence of behaviors guides problem-solving and population management. Specifically, “soft siege” in the HHO algorithm entails hawks gradually approaching bait and conducting a thorough search around it. This behavior is characterized by utilization of Eqs. (4) and (5) to update the positions of hawks. Also, Eqs. (4–9) govern both soft and hard siege strategies, depending on the prey’s energy and the hawks’ positions.
Equations (6) and (7) in HHO algorithm govern the dynamic hawks and rabbits, with J representing a stochastic parameter defining rabbit movement. Equation (7) encapsulates the direct approach of hawks towards rabbits, facilitating their hunting behavior. Additionally, Eqs. (8) and (9) model the gradual convergence of hawks towards bait, employing soft siege and quick dive mechanisms, respectively. These behaviors are illustrated in Fig. 3.
Equation (9) delineates Y and Z as indicators of a situation influenced by gentle encirclement and swift descent maneuvers, correspondingly, while LF(D) represents a levy flight model governing dimensional changes. Figure 3 visually depicts the concept underlying these behaviors.
Figure 3 demonstrates how hawks execute soft encirclement (gradually surrounding their prey) and rapid dives (sudden attacks). This mimics real-world hunting behaviors, enabling the algorithm to alternate between slow and fast search strategies. Utilizing the gentle encirclement and swift descent principles within the HHO technique, two fresh situations emerge, necessitating a comparison against the current one. Given the objective of minimizing, a new situation is chosen only if it represents a lesser lowest compared to its counterparts, as prescribed by Eq. (10). This formulation compares the current and new solutions, accepting only the better ones.
Within the HHO strategies, each hawk possesses the capability to assess the congregation point of fellow hawks and ascertain their collective focal point. This movement is orchestrated utilizing Eq. (11)39. This formulation updates the hawks’ positions based on the group’s average location:
Figure 4 illustrates this phenomenon as hawks navigate toward the bait via the mean position of the population and the ideal location:
The HHO algorithm is susceptible to premature convergence, often becoming trapped in local optima when navigating complex search spaces. To address this limitation, the proposed study introduces adaptive exploration and exploitation strategies within the algorithm’s framework. The enhanced HHO dynamically alternates between soft siege and hard siege phases, governed by the energy coefficient (E), to balance diversification and intensification. This adaptive switching mechanism, as detailed in Eq. (3) to (11), improves the algorithm’s ability to explore the search space effectively and reduce the risk of stagnation. Additionally, the integration of the VGG19 deep learning model ensures robust feature space representations, further complementing HHO’s adaptive optimization and leading to more accurate and efficient search performance. Figure 4 shows how hawks approach the prey (optimal solution) by utilizing the center of the group’s positions, ensuring convergence within the search space. In each iteration of the HHO technique, both hawk and rabbit (or current optimal solution) positions undergo iterative updates. Ultimately, the bait situation is derived as the final solution in the last repetition. Extensive testing and evaluation have demonstrated that their suggested method surpasses GA, PSO, FA, bat algorithms, biogeography-based optimization (BBO), cuckoo searches, and differential evolution algorithms in terms of precision. Algorithm Implementation: Develop the HHOA using a programming language such as Python. HHOA is a population-based optimization algorithm inspired by the hunting behavior of Harris hawks, renowned for its efficiency in solving complex optimization problems. Objective Function Definition: Define an objective function that quantifies the performance metrics of the VGG19 model, including accuracy, precision, recall, and F1-score. This objective function serves as the fitness function for the HHO optimization process.
Parameter Optimization: Utilize HHO to optimize the hyperparameters of the VGG19 model, including learning rates, batch sizes, dropout rates, and other architectural settings. Through iterative updates, the algorithm seeks to improve the performance of the model on the validation dataset. In this context, it is employed to optimize the hyperparameters of VGG19 and select the most pertinent features to enhance both accuracy and efficiency. These two elements work together: VGG19 manages complex data representation, while HHOA guarantees optimal performance.
Training and evaluation
-
Dataset Splitting: Split the preprocessed dataset into training, validation, and testing sets using appropriate ratios (e.g., 70% for training, 15% for validation, and 15% for testing).
-
Model Training: Train the VGG19 learning model and monitor its effectiveness on the validation set to mitigate excessive fitting. Employ techniques like early stopping to halt training when the performance on the validation set starts deteriorating.
-
Optimization: Apply the HHOA optimization algorithm to fine-tune the hyperparameters of the VGG19 model based on the validation set performance.
-
Model Evaluation: Analyze the trained model on the testing set to measure its ability to accurately detect DDoS attacks in smart networks. Contrast the effectiveness of the suggested approach with baseline methods using appropriate evaluation metrics.
Implementation and deployment
System Implementation: Implement the trained model and the HHOA optimization process in a distributed computing environment suitable for immediate monitoring and response in modern electrical frameworks.
Integration: Integrate the proposed solution into existing smart grid infrastructure for continuous monitoring of network traffic and detection of DDoS attacks. Ensure compatibility with industry-standard protocols and communication interfaces.
Incorporating the proposed detection system into the current smart grid infrastructure may introduce compatibility challenges due to differences in protocols, hardware interfaces, and legacy systems. To address these issues, the proposed model is designed to operate within a distributed fog computing environment that adheres to industry-standard protocols. This design facilitates the seamless deployment of the intrusion detection system across various smart grid components without requiring significant changes to existing systems. Furthermore, the modular architecture and protocol-agnostic preprocessing steps enhance interoperability and simplify the integration process.
Validation: Validate the scalability and robustness of the deployed solution through extensive simulations and experiments under various network conditions and attack scenarios. Figure 5 depicts the flow chart of the suggested approach.
Figure 5 presents a method for attack detection, which is divided into three key stages:
-
Initialize random feature vectors (representing hawk positions).
-
Assess the error of each vector using an objective function.
-
Apply HHO equations to adjust the vectors, directing them toward improved solutions.
-
Continue this process until the error reaches an acceptable level.
-
Select the optimal feature set and use it to fine-tune the parameters of the VGG19 model.
In conclusion, the flowchart illustrates an integrated approach encompassing data preprocessing, feature selection, model optimization, and final attack detection. The iterative nature of the HHO algorithm ensures model optimization while minimizing detection error.
In order to use the data in subsequent steps, we first read it and store it in the designated variable. Next, we build an extensive LSTM that will be utilized throughout the training system. Once constructed, the LSTM networks are trained for approximately 100 epochs to minimize loss that is used to estimate the weights in the network. We use the assessment outcomes approach to estimate the training and test data for the following day as soon as the training process is completed. The data is analyzed, and conclusions are generated using sensitivity and specificity findings, along with Accuracy, Precision, and F1 Scores.
Assessment indicators, including precision, sensitivity, and accuracy, are designed to evaluate the proposed approach, as outlined by Eqs. (12) to (16).
Results and discussion
Results
The suggested approach utilizing VGG19 DNN and HHOA achieved significant improvements.
In discovering DDoS attacks on smart grids. The accuracy of DDoS attacks detection was measured using various evaluation metrics, including precision, F1-score, and area under the receiver operating characteristic curve (AUC-ROC).
Comparative evaluations were conducted against baseline methods, including traditional ML and other DL architectures, to assess the superiority of the proposed approach. The results demonstrated that our method outperformed existing techniques in terms of both accuracy and efficiency.
The robustness of proposed solution was evaluated under different attack scenarios and network conditions, including varying intensities of DDoS attacks, network congestion, and noise in the data.
The results showed that our approach maintained high detection accuracy across diverse conditions, highlighting its resilience to adversarial challenges. The computational efficiency of the proposed solution was evaluated in terms of training time and inference time. Despite the complexity of the VGG19 DNN architecture, the optimization process facilitated by the HHOA improved convergence speed and reduced training time, enabling real-time monitoring and response in smart grid environments.
To address the issue of class imbalance in DDoS datasets, the proposed solution employs data balancing techniques, particularly through the integration of CGANs during the preprocessing stage. This method mitigates the imbalance by generating synthetic samples to better represent both benign and attack-related traffic, which is crucial for enhancing the model’s ability to detect DDoS attacks accurately. The results demonstrate that this approach significantly improves detection accuracy, precision, and sensitivity.
In the experimental setup, the dataset is divided into training, validation, and testing sets using an appropriate ratio (such as 70% for training, 15% for validation, and 15% for testing). The model also incorporates the VGG19 deep learning architecture, optimized with the HHO algorithm for both feature selection and parameter tuning. This combination ensures balanced performance across key metrics, such as accuracy and F1-score, while also addressing the class imbalance by applying CGAN-based data regularization, which improves the model’s generalization ability.
By using CGAN to tackle class imbalance, the proposed method outperforms traditional machine learning models and existing DL techniques, achieving superior accuracy, precision, and sensitivity in various comparative evaluations. The model’s robustness and scalability are further validated through experiments conducted under different attack scenarios, network conditions, and dataset sizes, consistently demonstrating that the proposed method maintains high detection performance.
The proposed approach effectively addresses the class imbalance problem in DDoS detection by using advanced data balancing techniques, ensuring that the model remains both accurate and efficient across diverse scenarios.
Analysis of resource utilization, including CPU and memory usage, indicated that the proposed approach consumed reasonable computational resources, making it suitable for deployment in resource-constrained smart grids systems without compromising performance.
The scalability of the proposed solution was tested through experiments conducted on datasets of varying sizes, ranging from small-scale simulations to large-scale real-time datasets. The results demonstrated that our approach exhibited linear scalability, maintaining high detection accuracy even with increasing data volume.
Assessment outcomes
Various circumstances were explored to assess the effectiveness of the suggested approach. Initially, the security monitoring system operates without VGG optimization. In the second scenario, VGG is integrated with the HHO variable selection method. Subsequently, VGG undergoes optimization with the HHO method in the third case. Finally, the HHO approach both determines characteristics and adjusts VGG factors in the fourth scenario. These study conditions are denoted as S1, S2, S3, and S4, correspondingly. Figure 6 presents the accuracy, sensitivity, and precision indices of the suggested approach in the two VGG scenarios, with and without the HHO approach, demonstrating their comparative performance.
The proposed intrusion detection system achieves high accuracy in attack detection, especially when a specific optimization algorithm is used for both feature selection and parameter optimization. The system’s performance is further improved when a data regularization technique is implemented. Figure 7 confirms CGAN-based data regularization achieves similar results to GAN, indicating that both techniques are effective for intrusion detection.
This section explores the impact of GAN balancing on the suggested intrusion detection system through the evaluation of four different scenarios. Research indicates that substituting GAN with CGAN in dataset balancing enhances the suggested system’s ability to detect attacks, improving accuracy, sensitivity, and precision. The high accuracy and low latency of the proposed method are crucial for real-time threat detection within smart grids. This enables faster mitigation of threats, such as preventing power outages, which in turn enhances the operational reliability of smart cities, utility providers, and critical infrastructures. Table 2 illustrates a comparative evaluation of the proposed intrusion detection system’s performance when utilizing two distinct data balancing methods: Generative Adversarial Network (GAN) and Conditional GAN (CGAN). Both techniques are employed to mitigate class imbalance within the NSL-KDD dataset by synthesizing artificial samples to equalize the representation of normal and attack-related traffic.
The findings indicate that the model integrated with CGAN (HHO + VGG19 + CGAN) surpasses its counterpart in all major evaluation metrics. Specifically, the accuracy increases from 98.62 to 99.82%, precision rises from 98.25 to 99.76%, and sensitivity improves from 98.23 to 99.69%.
These performance gains—1.2% in accuracy, 1.46% in precision, and 1.51% in sensitivity—underscore CGAN’s superior capability in generating more representative and informative synthetic data. Consequently, the model exhibits improved generalization and a lower false negative rate in identifying DDoS attacks.
Incorporating CGAN during the data preprocessing phase significantly enhances the overall effectiveness and dependability of the detection framework, particularly in real-time smart grid environments. Achieving high accuracy and sensitivity is essential to minimizing undetected threats and ensuring the uninterrupted operation of vital infrastructure systems, such as energy distribution networks.
Table 3 presents a comparative analysis of the proposed approach against several conventional machine learning (ML) algorithms, including Hybrid Decision Tree (HDT), Decision Tree (DT), k-Nearest Neighbors (KNN), and Support Vector Machine (SVM). The evaluation metrics—sensitivity, precision, and accuracy—demonstrate the superior performance of the proposed method.
As shown, the proposed framework achieves the highest scores across all evaluation criteria, attaining 99.76% sensitivity, 99.69% precision, and 99.82% accuracy. These results significantly outperform those of traditional ML techniques, with HDT and DT showing moderate performance, and KNN and SVM exhibiting comparatively lower accuracy and sensitivity. Notably, SVM records the lowest accuracy among the tested methods, highlighting its limitations in effectively detecting DDoS attacks in this context.
The substantial improvement in sensitivity emphasizes the model’s enhanced ability to accurately identify malicious traffic—a critical requirement for effective intrusion detection systems. These findings reinforce the efficacy of the proposed VGG19-HHOA-based detection system, offering a more robust and accurate solution compared to classical ML algorithms. Figure 8 illustrates this comparison across various accuracy, sensitivity, and precision metrics.
In40, networked hierarchical learning is employed for detecting attacks on smart grids. The results demonstrate that the suggested approach surpasses federated learning in terms of accuracy for detecting attacks in smart grids. Table 4 presents a comparative evaluation of the proposed intrusion detection system against various advanced federated learning models, with accuracy as the primary performance metric. The evaluated techniques include Fed-DNN-3, Fed-GRU + MLP, Fed-DNN-16, and Fed-Transformer-IDM.
Among all methods, the proposed approach achieves the highest accuracy of 99.82%, surpassing the best-performing federated model, Fed-Transformer-IDM, which records 99.49%. This notable improvement highlights the superior generalization capability and learning efficiency of the proposed VGG19-HHOA-based framework.
Although DL methods in federated settings demonstrate competitive performance, the results clearly show that the proposed method offers enhanced detection accuracy. This performance advantage underscores the potential of integrating deep convolutional neural networks with nature-inspired optimization techniques for effective and scalable intrusion detection in smart grid environments41. Figure 9 visually compares the accuracy of the proposed intrusion detection system with different federated learning models. The x-axis represents the different evaluated methods (Fed-DNN-3, Fed-GRU + MLP, Fed-DNN-16, Fed-Transformer-IDM, and the proposed method), and the y-axis represents their respective accuracy in percentage. The graph clearly shows that the proposed method achieves the highest accuracy of 99.82%, outperforming all the federated models.
Table 5 presents a comparative assessment of the proposed method against several advanced learning techniques, including GA-ELM, ELM, CNN, ICNN, and AE-LightGBM, with accuracy as the primary evaluation metric.
The results demonstrate that the proposed VGG19 model optimized with HHOA achieves the highest accuracy of 99.82%, outperforming all benchmark models. Notably, while AE-LightGBM performs competitively with an accuracy of 99.7%, the proposed method still achieves superior results, underscoring its robustness and precision in detecting attacks within smart grid environments.
This performance highlights the effectiveness of combining deep convolutional neural networks with metaheuristic optimization for enhancing detection accuracy. The comparative analysis confirms the proposed framework’s capability to outperform even state-of-the-art deep learning methods in identifying complex and dynamic intrusion patterns.
Figure 10 presents a 3D bar chart that provides a comparative analysis of the accuracy of several learning techniques. The methods being evaluated are displayed along the x-axis, which includes GA-ELM, ELM, CNN, ICNN, AE-LightGBM, and the proposed method.
The chart clearly shows that the bar representing the “Proposed Method” is the tallest, indicating its superior accuracy compared to all the other techniques. Additionally, the figure highlights that the proposed method, a VGG19 model optimized with HHOA, outperforms all other models, including AE-LightGBM, in terms of accuracy.
Table 6 presents a comparison of detection times for the proposed method and several baseline techniques, as reported in42. The values, measured in seconds, provide insights into the computational efficiency of each approach within real-time DDoS detection scenarios.
The analysis reveals that although the DT method exhibits the lowest detection time among traditional techniques (0.2013s), it significantly underperforms in terms of accuracy when compared to the proposed framework. Notably, the proposed method achieves the shortest detection time overall (0.1602s) while maintaining superior detection performance. It also outperforms other contemporary approaches, such as LR, RF, CNN–GRU, and CNN–GRU–FL, in both speed and accuracy.
These results underscore the efficiency of the proposed approach, which integrates the VGG19 DNN with the HHO Algorithm (. This integration facilitates automated feature extraction and optimized parameter tuning, enabling fast and reliable identification of sophisticated cyber threats.
Advantages of the Proposed Method: The synergy between VGG19 and HHOA yields a highly adaptive and accurate intrusion detection system. VGG19 ensures comprehensive deep feature learning, while HHOA fine-tunes critical model parameters, enhancing both responsiveness and precision.
Practical Implications: The findings affirm the proposed method’s suitability for deployment in real-time smart grid environments, where both detection speed and accuracy are essential. By leveraging advanced deep learning and metaheuristic optimization techniques, utility providers and grid operators can significantly reinforce their cybersecurity defenses and mitigate the impact of DDoS attacks on critical infrastructure.
Figure 11 shows the comparison of detection times (measured in seconds) for different DDoS detection methods, including DT, LR, NB, RF, CNN-GRU, CNN-GRU-FL, and the proposed method. The results show that the proposed method achieves the shortest detection time (0.1602 s), while maintaining competitive accuracy. Among the traditional techniques, DT has the shortest detection time (0.2013s), but lags behind in accuracy. Notably, the proposed method integrates advanced deep learning techniques with meta-heuristic optimization, ensuring high efficiency and reliability in detecting cyber threats.
Future directions
-
Extending the model to detect other cyber-attacks like malware or insider threats.
-
Enhancing computational efficiency for real-time, low-resource environments.
-
Exploring hybrid optimization methods by combining HHO with techniques like PSO or GA.
-
Adapting the model for evolving threats through continuous learning mechanisms.
While the proposed model demonstrates high accuracy, the complexity of the VGG19 deep neural network may present challenges for deployment in environments with limited computational resources, such as edge devices. To mitigate this, alternative classifiers like Random Forest (RF) could be considered, especially in cases where computational efficiency is paramount. RF offers strong performance with significantly faster training and inference times, though it may come with a slight trade-off in accuracy. Future work could explore a hybrid approach, where Random Forest is used for initial filtering, followed by VGG19-HHO-based verification to ensure high-confidence decision-making.
Limitations
Despite strong performance, the model’s deep architecture may increase training time in resource-constrained environments. Real-time deployment on edge devices may require lightweight adaptations. Future research should explore model compression or hybrid frameworks for faster inference in large-scale networks.
Conclusion
This study presents a novel DDoS detection system for smart grids, combining the VGG19 deep neural network (DNN) with the Harris Hawks Optimization Algorithm (HHO). The proposed method demonstrates enhanced detection accuracy, real-time response capabilities, and optimized resource utilization. These improvements significantly strengthen the security and resilience of smart grid systems against cyber threats, ensuring the protection of critical infrastructure. The practical implications of this research are substantial, providing a robust solution to the growing cybersecurity challenges faced by utilities and grid operators. Future research should focus on further optimization, exploration of ensemble learning techniques, and adaptation to emerging cyber threats, while fostering collaboration across academia, industry, and regulatory bodies to bolster smart grid cybersecurity strategies.
Data availability
The dataset was obtained from: https://www.kaggle.com/datasets/hassan06/nslkdd.
References
Rekha, S., Thirupathi, L., Renikunta, S. & Gangula, R. Study of security issues and solutions in Internet of Things (IoT), Mater. Today Proc., vol. 80, pp. 3554–3559, (2023).
Lone, A. N., Mustajab, S. & Alam, M. A comprehensive study on cybersecurity challenges and opportunities in the IoT world. Secur. Priv. 6 (6), e318 (2023).
Vetrivel, S. C., Maheswari, R. & Saravanan, T. P. Industrial IOT: security threats and counter measures, in Communication Technologies and Security Challenges in IoT: Present and Future, Springer, 403–425. (2024).
Toorajipour, R. The Progression of Iot Business Model Types: Implications for Supply Chain Management, in The 58th Hawaii International Conference on System Sciences. HICSS 2025, pp. 4139–4148. (2025).
Kumar, S., Dwivedi, M., Kumar, M. & Gill, S. S. A comprehensive review of vulnerabilities and AI-enabled defense against DDoS attacks for Securing cloud services. Comput. Sci. Rev. 53, 100661 (2024).
Yaghoubi, E., Yaghoubi, E., Yusupov, Z. & Maghami, M. R. A Real-Time and online dynamic reconfiguration against Cyber-Attacks to enhance security and Cost-Efficiency in smart power microgrids using deep learning. Technologies 12 (10), 197 (2024).
Amachree, T., Sam-Leeloo, T. A. & Nwisagbo, A. E. Cyber Security Operation and Management of Post-Basic Education and Career Development (PBECD) in Nigeria.
Gupta, S. & Singla, J. Deluge of disruption: an introduction to DDoS attacks, in Vulnerabilities Assessment and Risk Management in Cyber Security, IGI Global Scientific Publishing, 99–112. (2025).
Boukraa, L. et al. Enhancing DDoS attack detection in software-defined networking: a comparative study of machine learning algorithms using benchmark datasets. EDPACS, pp. 1–20, (2025).
Ali, O., Nguyen, T. L. & Mohammed, O. A. Assessment of cyber-physical inverter-based microgrid control performance under communication delay and cyber-attacks. Appl. Sci. 14 (3), 997 (2024).
Venkatesan, K. & Rahayu, S. B. Blockchain security enhancement: an approach towards hybrid consensus algorithms and machine learning techniques. Sci. Rep. 14 (1), 1149 (2024).
Yaghoubi, E., Yaghoubi, E., Khamees, A. & Vakili, A. H. A systematic review and meta-analysis of artificial neural network, machine learning, deep learning, and ensemble learning approaches in field of geotechnical engineering. Neural Comput. Appl, pp. 1–45, (2024).
Thakkar, A. & Lohiya, R. A survey on intrusion detection system: feature selection, model, performance measures, application perspective, challenges, and future research directions. Artif. Intell. Rev. 55 (1), 453–563 (2022).
Hoseinpur, F. Towards security and resource efficiency in fog computing networks, (2022).
Huaranga-Junco, E., González-Gerpe, S., Castillo-Cara, M., Cimmino, A. & García-Castro, R. From cloud and fog computing to federated-fog computing: A comparative analysis of computational resources in real-time IoT applications based on semantic interoperability. Futur Gener Comput. Syst. 159, 134–150 (2024).
Chen, Y. et al. Intrusion detection using multi-objective evolutionary convolutional neural network for internet of things in fog computing. Knowledge-based Syst. 244, 108505 (2022).
Norvig, P. & Russell, S. Artificial intelligence: a modern approach, Global Edition, Pearson, Harlow, vol. 1, pp. 1239–1269, (2021).
Abiodun, O. I. et al. State-of-the-art in artificial neural network applications: A survey. Heliyon, 4, 11, (2018).
Babaei Goushlavandani, A., Bayat, P. & Ekbatanifard, G. Detecting attacks on the internet of things network in the computing fog layer with an embedded learning approach based on clustering and blockchain. Cluster Comput. 28 (4), 226 (2025).
Sarker, I. H. Deep cybersecurity: a comprehensive overview from neural network and deep learning perspective. SN Comput. Sci. 2 (3), 154 (2021).
Naseer, S., Faizan Ali, R., Dominic, P. D. D. & Saleem, Y. Learning representations of network traffic using deep neural networks for network anomaly detection: A perspective towards oil and gas IT infrastructures. Symmetry (Basel). 12 (11), 1882 (2020).
Liu, Q., Hagenmeyer, V. & Keller, H. B. A Review of Rule Learning Based Intrusion Detection Systems and Their Prospects in Smart Grids. IEEE Access 9 57542–57564. 2021. (2021).
Sakhnini, J., Karimipour, H. & Dehghantanha, A. Smart grid cyber attacks detection using supervised learning and heuristic feature selection, in IEEE 7th international conference on smart energy grid engineering (SEGE), pp. 108–112. (2019).
Nafees, M. N., Saxena, N., Cardenas, A., Grijalva, S. & Burnap, P. Smart grid cyber-physical situational awareness of complex operational technology attacks: A review. ACM Comput. Surv. 55 (10), 1–36 (2023).
Kaur, D. et al. A bayesian deep learning approach with convolutional feature engineering to discriminate cyber-physical intrusions in smart grid systems. IEEE Access. 11, 18910–18920 (2023).
Jithish, J., Alangot, B., Mahalingam, N. & Yeo, K. S. Distributed anomaly detection in smart grids: a federated learning-based approach. IEEE Access. 11, 7157–7179 (2023).
Kumar, V. & Sinha, D. Synthetic attack data generation model applying generative adversarial network for intrusion detection. Comput. Secur. 125, 103054 (2023).
Cai, T., Jia, T., Adepu, S., Li, Y. & Yang, Z. ADAM: an adaptive DDoS attack mitigation scheme in software-defined cyber-physical system. IEEE Trans. Ind. Inf. 19 (6), 7802–7813 (2023).
Neupane, R. L., Bhandari, P., Calyam, P. & Mitra, R. SGChain: Blockchain Platform for Availability Attack Mitigation in Smart Grid Environments, in International Conference on Computing, Networking and Communications (ICNC), pp. 324–330. (2023).
Sivanesan, N. & Archana, K. S. Detecting distributed denial of service (DDoS) in SD-IoT environment with enhanced firefly algorithm and Convolution neural network. Opt. Quantum Electron. 55 (5), 393 (2023).
Sriranjani, R., Saleem, M. D., Hemavathi, N. & Parvathy, A. Machine learning based intrusion detection scheme to detect replay attacks in smart grid, in IEEE International Students’ Conference on Electrical, Electronics and Computer Science (SCEECS), pp. 1–5. (2023).
Massaoudi, M., Refaat, S. S. & Abu-Rub, H. Intrusion detection method based on smote transformation for smart grid cybersecurity, in 3rd International Conference on Smart Grid and Renewable Energy (SGRE), pp. 1–6. (2022).
Abdelkhalek, M., Ravikumar, G. & Govindarasu, M. Ml-based anomaly detection system for der communication in smart grid, in IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), pp. 1–5. (2022).
Taghavinejad, S. M., Taghavinejad, M., Shahmiri, L., Zavvar, M. & Zavvar, M. H. Intrusion detection in IoT-based smart grid using hybrid decision tree, in 6th International Conference on Web Research (ICWR), pp. 152–156. (2020).
Ding, P., Li, J., Wang, L., Wen, M. & Guan, Y. HYBRID-CNN: An efficient scheme for abnormal flow detection in the SDN-Based Smart Grid, Secur. Commun. networks, vol. pp. 1–20, 2020. (2020).
Chohra, A., Shirani, P., Karbab, E. B. & Debbabi, M. Chameleon: optimized feature selection using particle swarm optimization and ensemble methods for network anomaly detection. Comput. Secur. 117, 102684 (2022).
Yadav, N., Truong, L., Troja, E. & Aliasgari, M. Machine learning architecture for signature-based IoT intrusion detection in smart energy grids, in IEEE 21st Mediterranean Electrotechnical Conference (MELECON), pp. 671–676. (2022).
Umukoro, I. I., Eke, B. O. & Edward, O. An efficient intrusion detection technique for traffic pattern learning. Sci. Africana. 23 (2), 26–41 (2024).
Heidari, A. A. et al. Harris Hawks optimization: algorithm and applications. Futur Gener Comput. Syst. 97, 849–872 (2019).
Sun, X. et al. A hierarchical federated learning-based intrusion detection system for 5 g smart grids. Electronics 11 (16), 2627 (2022).
Yao, R. et al. Intrusion detection system in the smart distribution network: A feature engineering based AE-LightGBM approach. Energy Rep. 7, 353–361 (2021).
Zhai, F., Yang, T., Chen, H., He, B. & Li, S. Intrusion detection method based on CNN–GRU–FL in a smart grid environment. Electronics 12 (5), 1164 (2023).
Acknowledgements
Thanks in advance.
Funding
The authors declare that there was no funding for this work.
Author information
Authors and Affiliations
Contributions
Abdurahim and Selçuk wrote the main manuscript text and Javad prepared matlab programming and results. Raheleh analysed the results. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interest
The authors declare no competing interests.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Alhashmi, A., Idwaib, H., Avci, S.A. et al. Distributed denial-of-service (DDoS) on the smart grids based on VGG19 deep neural network and Harris Hawks optimization algorithm. Sci Rep 15, 18243 (2025). https://doi.org/10.1038/s41598-025-03354-4
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-03354-4