Abstract
This study delves into the vulnerability of the smart grid to infiltration by hackers and proposes methods to safeguard it by leveraging blockchain and artificial intelligence (AI). A categorization and analysis of cyberattacks against smart grids will be conducted, focusing on those targeting their communication layers. The main goal of the work is to address the challenges in this area by implementing novel detection and defense strategies. The authors categorize attacks on smart grid networks based on the communication classes they want to compromise. They propose novel taxonomies specifically designed to detect and implement defense strategies. The study investigates artificial intelligence and blockchain techniques to identify cyber-attacks that employ deceptive data injection. The study indicates that cyberattacks against smart grids are increasing in frequency and complexity. The paper proposes innovative strategies for defense, such as enhancing cybersecurity with artificial intelligence and blockchain technology. The research further enumerates several challenges, such as counterfeit topological data, imprecise data identification, and combining big data with blockchain technology. Given the increasing risks, the study emphasizes the crucial need for robust cybersecurity safeguards in smart grids. This work contributes to the protection of smart grid infrastructures by categorizing attacks, suggesting novel defenses, and exploring solutions integrating artificial intelligence and blockchain technology. Research should prioritize enhancing technology to maximize security and counter emerging attack methods. The intended audience of our paper comprises graduate-level academics and independent researchers.
Similar content being viewed by others
Introduction
Context
The transformation of traditional electrical infrastructure into smart grids (SGs) has introduced significant advancements in energy efficiency, automation, and intelligent management. These grids leverage technologies such as Artificial Intelligence (AI), Blockchain, and the Internet of Things (IoT) to optimize energy distribution, enhance security, and improve communication among various grid components. The global industrial automation market is projected to reach USD 54.2 billion by 2026, reflecting the rapid adoption of these technologies1.
While SGs offer numerous advantages, they also introduce cybersecurity risks due to their interconnected nature. Cyberattacks targeting communication layers, data integrity, and control mechanisms pose severe threats, leading to financial losses and system failures. Given these vulnerabilities, this study investigates AI and blockchain-based security mechanisms to protect SG infrastructures from emerging cyber threats while ensuring optimal performance and reliability2. Figure 1 shows the main components of smart grids. Effective communication and collaboration between the grid, service providers, and users are crucial for the intelligent grid framework.
Each part of this system can communicate using a diverse array of protocols and channels. At the grid domain level, substantial amounts of electricity are generated, conveyed, and dispersed. Contemporary meters, sensors, and control equipment have been extensively deployed, enabling the practical examination of the advantages of the SG3. Figure 2 shows the characteristics of an SG. Advanced Metering Infrastructure (AMI) refers to the physical equipment that links individual residential units to the broader communication network. Cloud computing service providers may experience advantages from utilizing intelligent data to gain insights into problems such as energy usage and power outages4.
Propagation methods utilizing either wired or wireless networks have the potential to reach a wider audience. Cables are necessary for the transmission of data across the Internet Protocol Version 2 (Ethernet), power lines, and fiber optics. Optical free-space networks, cellular, ZigBee, Z-wave, and Wi-MAX are all parts of today’s communication infrastructure. All of the smart power grid’s many parts can talk to each other and share information5. Business owners are increasingly concerned about the security vulnerabilities of SG due to their attractiveness to hackers6.
Table 1 provides a comprehensive list of challenges related to SGs in different fields.
Key aspects and novel elements
This research proposes an innovative AI-Blockchain Hybrid Security Model, which integrates advanced machine learning (ML) techniques for intrusion detection with blockchain-based authentication and data integrity mechanisms. The proposed model enhances smart grid cybersecurity by leveraging AI-driven predictive analytics to detect anomalies in energy consumption patterns and network behavior, while blockchain ensures a tamper-proof, decentralized security framework for verifying transactions and securing data exchanges.
One of the central contributions of this study is the development of a novel taxonomy that categorizes cyberattacks based on their impact on different smart grid layers, providing a structured approach to understanding threat vectors and their countermeasures. The AI-enhanced Intrusion Detection Systems (IDS) proposed in this work utilize supervised and unsupervised learning techniques to detect cyber threats in real-time, significantly improving response time and accuracy. Furthermore, blockchain-based security mechanisms, including smart contracts and decentralized consensus algorithms, offer robust protection against data manipulation and unauthorized access.
This study also presents a comprehensive review of challenges and future directions in integrating AI and blockchain within SGs. Key challenges, such as scalability, interoperability, computational overhead, and latency, are critically analyzed to propose efficient solutions for seamless deployment in real-world smart grid environments. Additionally, we explore the implications of privacy-preserving AI techniques and secure multi-party computation to ensure enhanced security while maintaining system efficiency. Our findings contribute to building a more resilient cyber-physical security model, addressing both internal and external cybersecurity threats.
By addressing these challenges, this research provides a foundational security model that enhances resilience against cyber threats while maintaining the efficiency and adaptability of smart grids.
Structure of the article
5. The remainder of this paper is structured as follows. Sect “Literature review” explores the existing literature on smart grid security challenges, cyber threats, and defense mechanisms, offering an in-depth analysis of current methodologies and identifying research gaps. Sect “Methodology” outlines the research methodology, including the classification of cyberattacks, data collection strategies, and the security framework design. Sect “Results” presents our findings, detailing the proposed AI-Blockchain Hybrid Security Model, its implementation, and its impact on smart grid cybersecurity. Finally, Sect “Application of blockchain and Artificial intelligence” concludes the study by summarizing key insights and outlining potential future research directions, with an emphasis on enhancing security frameworks through technological advancements and interdisciplinary collaboration.
Literature review
Due to its dependence on computer networks and other networked technology, SG is vulnerable to cyberattacks, which can compromise the system’s dependability. Complementary operations related to the production, distribution, and use of energy encompass the industrial, agricultural, and healthcare sectors1. The subsequent examples illustrate several analogous actions: Feasibly catastrophic and costly assaults on the country’s power infrastructure would compel people to adjust their daily schedules. The impact of cyberattacks that exploit the inherent weaknesses of SG and the subsequent financial burdens of these attacks becomes evident when the total cost of these attacks is taken into account18. The reliability of SG may be compromised by insufficient security application software, defective software and hardware maintenance, and issues with its logical design. In terms of cybersecurity risk management, these security governance procedures may not meet the protocols for the detection, assessment, mitigation, and restoration of dangers, increasing the risks associated with industrial automation in SG environments19. These defects are identified and utilized to directly impact the extent of harm to any electrical system20. Malware software has become the preferred tool for exploiting SG vulnerabilities during attacks21. Only individuals with expertise in criminal software development inside the electrical industry have the skill to decipher this information. The penetration of a system by malware can occur through several means, such as unsolicited emails, hyperlinks to malicious websites, and system weaknesses.
The Internet of Things (IoT) is a fundamental component of the concept of “Industry 4.0,” which integrates embedded software with real-world sensors and cyber-physical technologies. By using ML and artificial intelligence at each phase of production, this approach promotes collaboration22. Industry sectors that could potentially gain advantages from the Internet of Things include medicine, home automation, the arts, business, classrooms, and universities23. IoT devices, however, introduce significant cybersecurity risks, necessitating the deployment of AI-driven detection and prevention mechanisms to mitigate potential network attacks24. If Smart Grid (SG) provides the capacity to remotely operate and monitor different devices, homeowners may obtain an enhanced feeling of security. Notwithstanding the exciting prospects of intelligent buildings, their widespread adoption is impeded by several obstacles. Emphasizing security should be the highest emphasis in all areas of SG management, design, and construction standards25. By leveraging AI-powered anomaly detection and intrusion prevention systems, SG infrastructures can significantly reduce cybersecurity vulnerabilities associated with IoT-enabled devices, improving both security and operational resilience24.
Through using the capabilities of the Internet of Things, SG can augment individuals’ perception of security and tranquility. Furthermore, other than enhancing corporate productivity, they can also reduce energy inefficiency. Enhancing energy consumption control may be achieved by incorporating additional IoT devices into smart grids (SGs)26. The implementation of IoT-based humidity, temperature, and air pressure monitoring has the potential to decrease energy consumption for SG. Intelligent grids employ digital sensors linked to the internet to regulate the lighting. The potential application of internet-connected gadgets in disaster relief and crisis management is under ongoing consideration. Understanding how safety systems work has been greatly simplified by the Internet of Things, which allows sensors to be connected and real-time data to be transmitted to people responsible and at risk27. However, these advancements also introduce novel attack vectors, requiring robust cybersecurity frameworks that integrate both AI-driven security solutions and blockchain-based authentication techniques19. This technology has the potential to simplify users’ lives and enhance the organization of intelligent applications. Incorporating artificial intelligence with Internet of Things-enabled components is crucial for enhancing the energy efficiency of silicon graphene. Table 2 enumerates the several problems associated with SGs and the corresponding fixes to address those challenges.
The authors discussed the essential “SG,” or intelligent electrical system, required to manage variability in energy requirements. In the field of electrical power distribution, the term “SG” refers to a system that efficiently handles energy generation, transmission, and consumption with low demands on computing resources. Due to their structural architecture, these networks distinguish themselves from others. Contemporary technology enables individuals to independently diagnose, communicate, regulate, and monitor themselves21. In regions without sufficient renewable energy sources, the complexity of electrical distribution networks increases. Some of the problems include insufficient service, not making enough use of green power, and misuse of resources1. Renewable forms of energy fill an important function in Central America and Mexico. Renewable sources, such as wind and solar, are projected to account for 50% of the electricity generated by major power plants by 203040.
Energy systems must be efficient, flexible, and intelligent for a country to prosper. About 50% of the electricity would come from conventional sources, while the other 50% would come from smaller, more dispersed sources like residential solar panels and wind farms. This benefits energy, the economy, the environment, and technology. Due to solid-state generators, the electric power sector is becoming more decentralized, accessible, and efficient, benefiting businesses, the environment, and the global economy41. Conducting tests, enhancing technology, educating customers, establishing standards and laws, and exchanging information among electrical workers are all crucial during the transition period for smart grids to become completely implemented42. Hierarchical, unsupervised feature extraction, and semi-supervised feature extraction can teach machines. Popular ML algorithms include SAM, DBN, DBM, RNN and CNN. Deep understanding uses convolutions and drop-out techniques to learn from massive datasets. ML needs more data than traditional training methods. ML methods that extract unsupervised or semi-supervised characteristics are efficient43. Energy cost management and emission reduction require accurate energy demand predictions. Vehicle autonomous vehicles (VAVs) may evaluate pressure, gas flow, and temperature sensors using a wavelet neural network. Noun neural networks (NNs) and wavelet transforms work like this. System expenses and battery charge times can be optimized via time-series analysis. This strategy is now easier to deploy thanks to microgrid dependency prediction32. Both improve accuracy when used together. Time series prediction is vital, and ML should invest heavily in it. Dimensionality of the time series dataset may be an issue. Multiple methods can reduce data dimensionality when graphically showing time series data44. These methods include data-adaptive, model-based, and non-data-adaptive representation. The authors of reference45 developed a time series analysis method for social groups (SGs) to uncover periodic patterns from human and machine behavior data. Universal harmonic search, Fuzzy time series, and support vector machines were used to generate an unfailing electric load model46. This study analyzed occupant count-based building energy consumption calculations. Statistical support vector machines are supervised learning. An expectation survey can help a facility meet future management, resident satisfaction, and safety and security needs47. Support vector machine algorithms locate the hyperplane with the biggest difference between two data sets to partition the data into two groups48.
Upon the eventual implementation of IIoT, numerous organizations will have the opportunity to adopt novel business models. As referenced49, market-enhancing technologies including intelligent data, pervasive connectivity, decision-support systems, and predictive analytics will be used. Nevertheless, potential issues related to centralization, privacy, integrity, and trust may emerge due to the susceptibility of traditional Internet of Things architectures to various security vulnerabilities and network attacks31. This research attempts to provide a simple blockchain security architecture that uses AI to protect IIoT device data. Industrial Internet of Things (IIoT) systems that use cloud computing may face security and privacy issues while processing data in the cloud or on devices, innovation was used to solve certain problems. This study49 introduces a novel approach to enhance and simplify security operations by combining the advantages of lightweight boundary conditions with artificial intelligence techniques based on highly tuned sprinting neural networks. The implementation of a genuine intrinsic analysis paradigm that encodes characteristics enables the mitigation of damage caused by strikes50. A comprehensive evaluation of this approach is presently underway using a diverse range of attack datasets to verify its effectiveness. In addition, we assess and analyze the effectiveness of privacy-safeguarding approaches and artificial intelligence methodologies by considering several parameters.
Methodology
Research questions
This Systematic Literature Review (SLR) uses blockchain and AI to discover, appraise, and compress empirical data on secure governance (SG) security. This assessment focuses on Singapore’s blockchain implementation. Supply chain management difficulties and blockchain/AI solutions are examined. SG’s benefits and structure are also examined. Blockchain and AI methods boost SG security51. To achieve this objective, the review will be directed by the research questions and their underlying motives. The flow of the study is shown in Fig. 3, while the research questions are presented in Table 3.
Select data sources
The research papers were obtained from recognized digital libraries, including IEEE Xplore, ScienceDirect, ACM Digital Library, Springer, and Wiley52. A comprehensive search was conducted on full texts, abstracts, and keywords to retrieve prior studies relevant to the research questions. The chosen data repositories and the total number of studies resulting from search queries are presented in Table 4; Fig. 4.
Search string formulation
To refine the search process, a systematic keyword selection approach was used, based on the research questions (Table 3)52. Boolean operators (‘AND’ and ‘OR’) were employed to construct a precise search string. The search string formulation process is illustrated in Fig. 5 and the selected keywords are presented in Table 5.
Inclusion and exclusion criteria
The selection of research articles was based on well-defined inclusion and exclusion criteria to ensure relevance and quality53.
Inclusion criteria
-
Academic publications written in English from 2007 to 2024.
-
Studies focusing on blockchain applications in Sustainable Growth and Smart Grid security.
-
Research including empirical evaluations through supervised experiments or simulations.
-
Publications covering AI and blockchain architectures, applications, and components.
-
Studies discussing blockchain and AI integration for security enhancement in software governance.
-
Only peer-reviewed journal articles, conference papers, or book chapters were considered.
Exclusion criteria
-
Studies published before 2007.
-
Research focusing on blockchain applications outside cybersecurity or smart grid security.
-
Papers lacking empirical validation or theoretical relevance to AI-blockchain integration.
-
Studies that do not evaluate the impact of AI and blockchain on cybersecurity challenges.
For the inclusion of 2024 publications.
-
The selected studies from 2024 were sourced from preprint repositories and early-access journal articles from IEEE Xplore, ScienceDirect, ACM Digital Library, and Springer53.
-
These sources were vetted to ensure credibility and alignment with the systematic review methodology.
Define quality assessment criteria
The following quality assessment framework is synthesized from previous systematic reviews54, and adapted to match our research questions. Table 6 lists the evaluation criteria applied to each selected study.
Primary study selections
Primary studies were chosen based on their alignment with the research questions and quality assessment criteria. Using a multi-stage systematic selection methodology, 211 primary sources were selected for analysis. Figure 6; Table 7 present the distribution of selected papers by year, and Fig. 7 provides a PRISMA diagram summarizing the selection process.
Results
Sect “Results” presents both synthesized insights from prior literature and our novel contributions. Specifically, the attack taxonomies and mitigation strategies in Tables 8, 9, 10, 11, 12, 13, 14, 15 are based on an in-depth analysis of existing literature, whereas our proposed AI-Blockchain security model, its layered architecture, and the hybrid detection and authentication techniques represent our original contributions.
Vulnerabilities of SG
The vulnerabilities described in this section are based on synthesized findings from the literature and form the foundation for our proposed layered defense framework.
Demand response (DR) refers to the adaptation of customers’ power consumption patterns in reaction to fluctuations in prices. Consequently, the peak load consumption decreases and the service dependability of the system increases. Numerous years ago, enterprises and industries initiated the use of demand response (DR) as a means to enhance and maintain stability in the electricity grid1,54. According to the most recent Science and Technology report, the Demand Response can greatly influence the residential electricity industry. The incorporation of intelligence and bidirectional communication capabilities into the Smart Grid has the potential to enable utilities to provide customers with up-to-date price information. To optimize the power supply-to-load demand ratio, the Smart Grid (SG) utilizes demand response (DR) methodologies and incentives. This impacts utilities, businesses, and homes regardless of the system’s scale55. DR’s emphasis on client engagement and responsiveness can substantially improve system expansion, functionality, and market effectiveness. There are three distinct methods by which customers can modify their power use during Demand Response (DR)56. One classification of demand response programs (DRPs)57 is based on the approach they use to commence demand reduction. There are three types of programs: rate-based (price-based), incentive-based (event-based), and demand reduction bids. The implementation of a more secure system would benefit both players and clients by providing a wider range of choices, reducing costs, and enhancing market performance. A system is classified as vulnerable in the Common Vulnerabilities and Exposures (C.V.E.) database if it is susceptible to being readily targeted and attacked. A computer security vulnerability refers to a defect in the logical structure of software or hardware that, if taken advantage of, has the potential to undermine the security of the system. This issue has the potential to jeopardize security.
Typically, in such a situation, the process of addressing vulnerabilities entails the updating of the code. However, it is also feasible that the specification may require modification or total abandonment.
Interoperability and data management vulnerabilities
Interoperability refers to the extent to which various systems and technologies can interchange data and programs with each other. To entirely achieve the possibility of SG technology, it is essential to integrate different intelligent devices and architectures that utilize both software and hardware components1,58. An essential objective of the Internet of Things is to enable objects and systems to establish efficient communication among themselves. Facilitating the integration of new smart products with existing infrastructures and enabling communication between smart goods from different manufacturers is of utmost importance. To optimize the utilization of resources, plug-in hybrid electric vehicles (PHEVs)59 —a vital element of the future smart grid—mandate thorough testing. The challenges encompass the development of intelligent systems for energy management, power distribution from batteries, and optimizing power usage60. Compatibility testing of the intricate power electronics is necessary at every stage of small-scale fabrication. Before they can be implemented, it is necessary to resolve concerns regarding the intricacy and potential disruption they may bring to the system61. Inefficiencies in SG data management include the areas of data aggregation quality, data security, compliance control, common scope, and management technique effectiveness. Considerable amounts of data are generated and exchanged among multiple organizations. By utilizing reliable data streams, operators can effectively monitor and manage the grid system. Encompassed within these data streams are commercial records, meteorological predictions, and grid operational records. Furthermore, adding to the complexity is the challenge of fulfilling the legal need for the timely reporting of precise data. It presents a challenge. The sophisticated systems implemented for data gathering, analysis, processing, maintenance, and security in the era of digital technology do possess inherent weaknesses. Many Supervision Groups lack the means to ensure the confidentiality and security of their data62.
Vulnerabilities in scalability and energy storage
Distribution grid platforms, distributed energy resource management, and complex wealth management can all be built with the help of data collected from both information technology and operational technology. This makes it easier to turn raw data into actionable intelligence. In particular, sustainable energy facilities in industry have demonstrated a plethora of useful applications63. It takes a long time and a lot of effort to use established consensus mechanisms like Proof of Work (PoW) and Proof of Stake (PoS) to create a block or complete a transaction. The procedure also required a lot of power, which became increasingly problematic as the workforce expanded. The result is an increase in the number of nodes, also known as consumers, in the Sub-Grid Energy System (SGES)1,64. In order for the system to support an ever-growing user base, it needs to meet specific requirements. In fact, this situation has the potential to impact the SGES’s scalability65. By concentrating mining power in the hands of a few companies, the current BCN architecture prevents miners from other regions from getting involved and allows the covert consolidation and growth of the SGES activities. Another obstacle that limits the large growth of SGES is the current state of the BCN-enabled system’s interoperability and heterogeneity capabilities. Our goal is to improve scalability by making changes to the current design of the BCN network. Energy Storage Systems (ESSs) are chosen based on certain criteria. Utilizing flywheel technology, an ESS may store energy in the form of kinetic energy66 This device is designed for stationary applications and has a lifespan of 10,000 cycles. Its energy density is around 20 Wh/me, and it is commonly used in conjunction with electric machines that use permanent magnets or induction machines. These features—dynamic reaction speed, self-discharge rate, power density, ruggedness, and excellent energy conversion efficiency—define this gadget. For basic regulatory reasons, flywheel technology—which boasts an efficiency of almost 99.99%—is the ideal large-scale ESS40. This Energy Storage System’s (ESS) fuel cell uses a reversible electrochemical mechanism to produce energy. The hydrogen fuel cell has a lifespan of 20,000 cycles and produces no pollutants because water is the only byproduct. In addition, its storage capacity is enhanced, its efficiency is around 50%, and its dynamic reactivity is excellent. Electricity generation is transformed into thermal energy by thermal energy storage systems (ESS), which then store this thermal energy for usage during times of lower demand. An air-handling device, a heating/cooling setup, and a heat exchanger used for storage make up the system. Effective load transmission is made possible by this storage device, which may be charged either locally or centrally67. The huge store capacity, quick response time, and frequency regulation capabilities of this Energy Store System (ESS) are its most notable advantages. Consequently, these load requirements can be satisfied by taking into account a wide range of functional, technological, and financial factors. Due to their high price tag, energy storage systems (ESS) have been slow to incorporate supercapacitors, magnetic coils, and superconductors.
Cost, availability and complex SG vulnerabilities
Presently, sophisticated equipment and sophisticated systems are operated by large mining corporations. An increasingly complex consensus method can help overcome the difficulty of mining validity, which requires a sophisticated hardware system to compete with current BCN technology68. Because there is a third party involved and a large power usage, an additional medium of exchange is needed. SGES is a more economical option since these problems can be resolved by including new or enhanced features such as the inter-SC algorithm and IBSM into the current BCN technology69. “Availability” in this context refers to the guarantee of timely data access and the maintenance of reliable information. If unavailable, grid management and the delivery of energy could be interrupted. An increase in contact information within an SGES arrangement can slow down data transfer and prevent authorized users from accessing the system70. Thus, keeping high availability requires providing good security. The substantial third-party participation in the existing BCN makes it necessary to update the modeling of the current BCN since it causes the data retrieval process in SGES to be slow, complicated, and inaccurate. As SG improves and grows, more intelligent electronic devices (IEDs) and parts are added. These IEDs and their components connect to many network systems, enabling more applications and services and streamlining communication with crucial infrastructures1,71.
Authentication heterogeneity, interoperability, and security vulnerability
Advanced SGES are made up of several different intelligent parts and the majority of these devices and systems are electrical and electronic. Exact device and owner identification are necessary for efficient system control, monitoring, and maintenance72. Reliable device authentication makes it possible to identify instances of illegal access to the system’s resources. Only authorized nodes or users with the most recent BCN-enabled SGES authentication should be permitted access. During the authentication procedure, an attacker may obtain access to the user’s data and damage the network protocol73. This problem can be resolved by requiring users to carry out authentication processes, such as encryption processes1. SGES’s BCN technology does not sufficiently enable heterogeneity and interoperability. Inter-chain communications need a person to rely on and have trust in the authority of a third party. To improve interoperability and cross-chain activities, there isn’t yet a way to execute smart contracts across various chains. To resolve these problems and make the functions available, the current BCN in the SGES designation must be modified. One major problem is the scalability of the BCN-enabled SEGS. The upcoming version of BCN technology may include the introduction of PoL an enhanced consensus mechanism74. This consensus process enables BCN networks to process transactions using less energy. The efficiency of transaction validation has increased, and it won’t experience any new issues despite the number of nodes It is also possible to remove the concentrated mining authority and the system’s posed centralization. There will be incentives for miners from different locations to take part in the mining process. As a result, more transactions will be made possible by SGES communications75.
Attacks and countermeasures on smart gird
False data injection attack
By manipulating meter readings and surreptitiously influencing state estimation calculations, FDIAs jeopardize the security of the SG1,76. FDIAs may also evade SG BDDs, which identify erroneous data. Over the past decade, FDIAs’ effects on SG networks have been extensively studied77. FDIAs, who hack grids and manipulate data, benefit and suffer from cyber-physical system proliferation. Bus voltage and phase angle were estimated by state using SCADA to examine transmission stability and load shedding78. Installing an energy management system in the control center guarantees the SG operates as designed79. SG reliability and efficacy depend on state estimation precision. To operate and manage SGs effectively, conditions must be accurately assessed. Cyber-physical risk assessment of manipulated data is difficult. FDIAs manipulate network topology, deceive the control center, and disrupt the energy market to profit from power grid applications like the SCADA system and phasor measuring unit. Many research has examined FDIAs’ long-term effects on SGs80. The authors examined whether FDIAs may cause several branch outages at once. Further research was done on FDIAs’ data-dependent outage detection method, P.M.U81. Switchgear generators (SGs) frequency excursions can cause blackouts and electrical equipment damage. Reference25 details these phenomena. FDIAs have become better at hiding their activities and evading detection. Table 8 lists DL, Kullback-Leibler distance, sparse optimization, colored Gaussian noise, spatiotemporal correlations, Kalman filter, and Bayesian clustering (BC) technology as countermeasures. These are simply a few of the methods described in82.
Denial-of-service attack
The cyber defenses of the SG protect its data, power, and communication networks from potentially damaging attacks. Storage group access and power are impacted by denial-of-service attacks. Service disruptions can occur as a result of distributed denial of service attacks. Denial-of-service attacks use system weaknesses or inundate a specific channel or device with an excessive amount of data. Utilizing botnets is a method of launching DDoS attacks. Electrical service dependability is guaranteed by a Substation Generator. Disseminated denial of service attacks target the data, computer, energy, and communication infrastructure of the intelligent grid. A power outage would impact a substantial number of Standard Grid consumers, amounting to millions83. Distributed denial of service (DDoS) attacks significantly decrease network throughput and incur costs amounting to billions of dollars. The networking issues and power disruptions experienced by the SG are caused by denial-of-service attacks. Systems utilized by smart grids include data aggregators, smart meters, RTUs, IEDs, P.M.U.s, and P.L.C.s. A complete representation of data denial-of-service attack is depicted in Fig. 81,84.
Due to their use of Internet-sponsored protocols, these devices are vulnerable to denial-of-service attacks. In general, security is fraught with risk. P.M.U. networks may not be acknowledged by many utility companies as crucial cyber assets, thereby posing challenges in the defense against denial-of-service attacks. Denial-of-service attacks, ranging from minor to major, pose a threat to the availability and integrity of services. Subsequently, there are deficits and losses84. It is feasible to detect DoS assaults utilizing honeypots, ML, SDN, DL, and BC. The strategies to mitigate denial-of-service attacks are presented in Table 9. Refer to Table 9 for strategies to mitigate denial-of-service attacks.
MITM attack
Man-in-the-Middle (MITM) attacks pose a significant threat to SG security, particularly in Modbus TCP/IP-based SCADA (Supervisory Control and Data Acquisition) networks. These attacks allow adversaries to intercept, manipulate, or disrupt communication between smart grid components, leading to potential data breaches, operational failures, and unauthorized control over critical infrastructure1. MITM attacks can secretly intercept smart meter data, alter energy consumption measurements, and even manipulate control commands in SG systems85. An attacker can compromise 95% of HTTPS servers by impersonating trusted sources and exploiting certificate vulnerabilities, making smart grids particularly susceptible to spoofing-based MITM attacks.
The SG network, particularly in SCADA-based industrial control systems, is a primary target for MITM attacks. Energy providers, as well as water, gas, oil, and power producers, rely on IEC 60870-5-104 SCADA connections, which have been shown to be vulnerable to MITM interception and control manipulation. Researchers have identified MITM vulnerabilities in SCADA networks, with Address Resolution Protocol (ARP) poisoning being a commonly exploited technique to reroute traffic to malicious nodes86. Advanced Metering Infrastructure (AMI), responsible for monitoring electricity usage and energy distribution, is particularly vulnerable to MITM attacks. Modbus TCP/IP, a widely used protocol in smart grids, is often the entry point for MITM exploits, allowing attackers to modify metering data and disrupt grid operations87.
Social engineering plays a significant role in facilitating MITM attacks. Attackers use phishing, spear-phishing, and perception manipulation to exploit human vulnerabilities, enabling unauthorized access to smart grid resources and IT infrastructure. Phishing techniques are often the first stage of a MITM attack, where adversaries deceive users into sharing authentication credentials or security tokens, allowing persistent access to SG control systems. A study on serious game-based awareness training demonstrated that educating grid operators about phishing, impersonation attacks, and over-sharing of personal information significantly improves resilience against MITM intrusions88.
Detection and mitigation strategies for MITM attacks include IDS and ML, which play a critical role in identifying anomalies in SG networks. Physical Unclonable Function (PUF) authentication mechanisms enhance smart meter security by generating unique, tamper-resistant cryptographic keys, reducing the risk of MITM-based authentication bypasses. Table 8 provides a detailed overview of various techniques and approaches used to detect and mitigate MITM attacks, including ML-based anomaly detection, IDS monitoring, and cryptographic security measures89. The table illustrates how different methods leverage AI-driven network traffic analysis, pattern recognition, and authentication mechanisms to counter MITM threats effectively. It highlights the comparative advantages of each approach, particularly in terms of response time, accuracy, and integration feasibility in real-world SG environments.
Load altering attack
Large-scale automatic controllers (L.A.A.s) regulate the energy consumption of certain loads to prevent the power system from becoming excessively burdened. There are two alternatives for Local Authorities (L.A.A.s): direct and indirect load compromising. A demand-side management system provides clients with inaccurate pricing information. An excessive amount of electricity cannot be supplied to a circuit unless loads are properly regulated and protected. The LAAs encompass both SLAAs and DLAAs. By employing a closed-loop attack load, the authors demonstrated that DLAAs had a substantial impact on load fluctuations to the peak degree. In SLAAs, the attacker maintains a constant observation of the load’s direction while alternating it. The disadvantage of a DLAA over an SLAA lies in the need for the attacker to monitor the power frequency and adjust the load according to the signal’s reliability. Spectrum generators (SGs) offer frequency detection instruments available for online purchase93. These devices are used to monitor sensitive frequency loads. Large-scale anomalies (L.A.A.s) cause the grid to undergo more abrupt and unforeseen fluctuations. This results in the SG incurring substantial operational expenses and costly frequency deviations. With the assistance of UFLS, SG effectively handles significant power interruptions. It is feasible to implement load shedding and partition the electrical system using Load Allocation Areas (L.A.A.s)94. Table 9 provides a comprehensive list of several approaches for identifying Local Area Areas (L.A.A.s), including observers and model-free defensive frameworks.
Load redistribution attack
The authors of this article devised a method known as load redistribution, which has a resemblance to state estimation-false data injection. While attacks on L.R. do not alter the total power demand, they do impact the electrical flow and load bus measurements. A reallocation of resources is necessitated by the heightened demand on the network caused by the attack. The potential consequences of L.R. include not only financial damages but also bodily injuries, such as stumbling over electrical wires or experiencing violent attacks. Utilizing hacking techniques could be a viable solution for L.R. to prevent power disruptions and resolve the SCED problem97. Furthermore, there are two specific types of attacks associated with load-shedding: one that exploits the immediate operating expenses of load-shedding, and another that exploits the Systemic Control of Electrical Devices (SCED) to activate the solution by tripping lines, which is then postponed98. Table 10 provides a comprehensive list of several methods, including support vector models, closest neighbor identification techniques, and ML-based approaches, for identifying Local Registers (L.R.A.s).
Replay attack
Intercepting wireless data, assuming the identity of an authorized sender, and combining the intercepted data with the first dispatched data comprise a replay attack. This sort of assault relies on cognitive awareness, making it harder for the supervisor to spot. This disrupts electrical energy transmission, delaying alternating frequencies owing to the attack. A replay attacker may interrupt the system and prevent it from performing its operational functions101. Replay attacks with Stux Net were used to access the centrifuge SCADA system. This caused the centrifuge control system to corrupt, rendering 1000 centrifuges inoperable102.
The research implies that deliberately adding noise to the control input may prevent reflected replay assaults. This strategy failed. Game theory provided a dynamic control input that synchronized noise production in another investigation. Table 11 details R.A. identification processes. The methods include the support vector model, ML, and radar antenna nearest neighbor identification103.
Cybersecurity solutions for SG
This section explores potential approaches to safeguard satellites from cyberattacks by utilizing blockchain technology and artificial intelligence technologies such as ML and DL. The selection of these techniques was based on their remarkable capacity to independently identify intricate patterns. Each of these methods is enumerated below.
BC techniques in SGs based on cybersecurity
Smart energy systems may manage contracts and transactions with blockchain technology to prevent hacks and boost self-regulation. In traditional power systems, a successful attack compromises the meter record, data packets, fraudulent energy trading payments, and control center. BC protects SG from cyberattacks108. By identifying Blockchain-based attacks, Table 14 highlights published research on cybersecurity in Smart Grids (SGs) by objective, kind, solution, consensus methodologies, Smart Contract deployment, and performance evaluation criteria109.
In SGs, ArMor uses Bayesian calculation to discover the negative impacts of A.M.I. and S.M. System aimed to discover integrity issues caused by smart meter failure and FDI attacks. This paper proposes a decentralized Ethereum Blockchain solution to DDoS and SPoF. The authors presented a blockchain-based smart grid energy transaction confidentiality solution. Blockchain-based SG used PBFT consensus. The decentralized technique presented by authors110 effectively identified replay problems while simultaneously safeguarding the privacy of local data. To enhance the security of SG systems against cyberattacks, they advocated for a consensus-based approach.
In a similar vein, the developers of secure Smart Grid components leverage Blockchain technology. Miners utilize their computational capabilities to authenticate transactions. Throughout every energy transfer transaction, the rights of the consumer are upheld. The realistic threat model created by111 sought to deter a compromised secure gateway from detecting foreign direct investment (FDI) activities and encourage the submission of accurate data by penalizing users who provided inaccurate or missing information.
Blockchain-based security solutions improve smart grid protection by leveraging decentralized authentication, distributed consensus, and smart contract deployment. These mechanisms ensure enhanced resilience against cyber threats by eliminating single points of failure and providing tamper-resistant records of transactions. However, blockchain implementation in smart grids introduces certain trade-offs in terms of computational costs and transaction processing time. Unlike traditional security mechanisms, such as centralized access controls, encryption-based authentication, and rule-based fraud detection, blockchain solutions incur higher latency due to consensus verification processes but offer improved security guarantees. Additionally, while blockchain-based security frameworks provide enhanced scalability in decentralized architectures, the cost of implementation and maintenance can be higher compared to conventional security methods. Table 12 illustrates the comparison between blockchain-based solutions and traditional security approaches in terms of latency, cost, and scalability, providing insights into their respective advantages and challenges in smart grid environments.
Blockchain application in smart grid
Blockchain technology gained popularity due to Bitcoin, which is now widely accepted by researchers from many fields. The various BC systems were built after the blockchain for bitcoin was created. Blockchain that are federated, private, and public are among the numerous BC platforms. There are a few technical differences between these three kinds of BC119. Public blockchain that are frequently observed these days include Ethereum and Bitcoin. Any user can participate on any node with any publicly available BC type. As a result, everyone using the public blockchain will be able to see every transaction120.
The second kind, private BC, limits participants’ access to transaction information. A node on a private blockchain cannot engage in a transaction or access pertinent data until it is given access privileges. Thirdly, both public and private BC characteristics are present in federated BC. SG’s introduction made several uses in the energy industry possible121. A participant in the Energy Service Network (ESN) or Smart Grid (SG) can conduct peer-to-peer energy trade, such as selling electricity, and create invoices through the use of smart contracts based on blockchain technology. An ESN platform’s ability to store transactions is essential to the peer-to-peer model. Peers include prosumers, consumers, regulators, and those involved in power transfers. Although the centralized architecture has proven to be dependable, as trading volume increases and data interchange volume increases, it may become vulnerable to attacks, resulting in inefficiencies and a single point of failure. The BC servers are essential to the decentralized power grid because they maintain trust and log every transaction. A key principle of BC is the trust mechanism, which blocks the spread of corrupted data. A permission-less or public blockchain, which is a system without access restrictions, requires resources like fuel and processing power, therefore one must take those into account when adding new data22.
In the consensus proof-of-work (PoW) process, nodes solve the hash code and verify one another with one another. In the Proof of Work (PoW) consensus, adding more data (the following block) raises processing costs. A decentralized computer system provided by a blockchain allows for peer-to-peer communication in the absence of a central authority. In order to offer accuracy, effectiveness, and security without the need for middlemen, BC-based systems continue to rely on predetermined rules. Researchers continue to face a number of unresolved issues on the BC platform, despite constant advances and problem-solving efforts. The number of automated decision support systems122 has increased dramatically in the past several years. In this case, a blockchain can be helpful in keeping track of decisions and actions by completing the proof-of-work required to add a validated block to the chain. These tools can also be used to establish a mining approach’s proof-of-work. By using ML algorithms, unusual or malicious activity on the BC can be quickly detected. There will be a number of immersive applications and synergies between blockchain (BC) and ML. When it comes to data mining and safety procedures, the two systems can collaborate. By using Big Data-driven AI solutions through BC, an accurate and thorough decision database may be created for continuous system performance assessment. Decision-making may be tracked at various stages when a process is included into a business continuity paradigm, and artificial intelligence (AI) systems may use sensor data for analysis123. The security and accuracy of data in British Columbia might be greatly increased by implementing big data technology. Proponents of the BC paradigm contend that both are essential. By ensuring privacy and uniqueness, BC implementation should increase the efficiency and reach of data transfer. By independently carrying out the common transaction procedures, an “intelligent contract” eliminates the need for a middleman. Creating autonomous smart contracts that let the buyer and seller manage the sale and payment procedures securely and independently could be one way to implement smart energy systems. Blockchain technology in smart grids may benefit our current and future energy systems in several ways. Due to its tight relationship to the features and workings of the blockchain, the electrical system contributes significantly to the benefits of the decentralized trade network. Less red tape and improved computing power are two of blockchain’s main advantages when it comes to Enterprise Social Network (ESN) features and principles of operation. Moreover, it encourages decentralization, greater security, robustness, openness, and scalability.
AI techniques in SG based on cybersecurity
The implementation of artificial intelligence techniques has the potential to enhance the reliability and resilience of intelligent grid systems. This paper presents the authors’ comprehensive approach to safeguarding against SG attacks using DL and ML techniques.
Cybersecurity techniques in SGs based on DL
When traditional methods are unable to extract useful features, DL models employ more sophisticated training techniques. The phenomenon known as the dimensionality curse presents significant challenges in the successful elimination of essential characteristics. Ultimately, several DL methods successfully addressed the task of safeguarding sensor-gated networks124. This architecture incorporates a concealed fully convolutional layer, as well as two pooling layers, an output layer, and two convolutional layers. Previous studies have utilized several DL approaches, including recurrent neural networks (R.N.N.s), artificial neural networks (ANNs), and deep neural networks (D.N.N.s), to investigate SG attacks. By employing a Recurrent Neural Network (RNN) and the Kalman filter, the authors of the paper developed a technique for identifying FDIA.
To detect an FDI attack, the dynamic threshold was continuously monitored. A technique for determining the FDIA (Focal Design Index) for gas-fired producing and power-to-gas facilities is provided in reference53. The proposed approach utilized the IN and OUT signals supplied by the facility scheduler. To enhance the detection of FDIA, a hybrid neural network was employed47. In this specific case, the training data lacked any labels. Presented in Table 15 are the accuracy and DL models employed in cyberattacks. Furthermore, the authors identified vulnerabilities in the IEC 61,850 communication standards by using DL techniques. We developed a framework for detecting energy theft, a Convolutional Neural Network (CNN) approach to ensure energy privacy in Software-Defined Generators, and a Paillier algorithm.
DL models face computational constraints when deployed in real-time smart grid applications. The latency introduced by high-dimensional data processing, the need for significant computational power, and the limitations of traditional infrastructure create challenges in implementing DL-based cybersecurity solutions. Real-time IDS in edge and fog computing environments require lightweight yet efficient models that can process large-scale network traffic without introducing excessive delays. To mitigate these issues, recent studies have explored lightweight AI models such as MobileNet, XGBoost, and federated learning-based approaches, which optimize security detection while reducing computational overhead. These approaches allow for distributed learning while preserving data privacy and minimizing bandwidth consumption.
In this paper, an IEEE 1815.1-based Intrusion Detection System (IDS) for a power system is described. A DL system utilizing a bidirectional recurrent neural network (R.N.N.) was used to detect outliers, evaluate their importance, and provide a grade to the suggested approach. The GAN architecture successfully identified several threat categories, including as malware, foreign direct investment (FDI), and attacks that impede reassembly. To identify foreign direct investment (FDI) attacks that cause congestion in transmission lines in Singapore and evade state estimate, the researchers employed a DL-based neural network model125. The researchers implemented ensemble-based DL to identify false positives. The measurements obtained during the adjustment of the window were utilized to train multiple DL models. An ensemble-based detector utilized the ideal model to detect erroneous readings. To facilitate the detection of energy theft by SGs, researchers developed a classification method utilizing D.N.N. The employment of a Bayesian optimizer to selectively enhance and refine the hyper parameters significantly facilitated the detection of instances of energy theft126. The methodologies for DL-based cyberattack detection in smart grids are outlined in Table 13.
ML-based cybersecurity techniques in SGs
The detection and investigation of potential cybersecurity vulnerabilities by SGs are accomplished through the utilization of ML methodologies. The authors investigated the feasibility of employing ML to identify breaches on smart meters, perhaps resulting in a rise in energy bill costs. In their study, the authors of reference132 did not employ ML to forecast future electricity costs. Following the cleaning and arrangement of the data, many methods such as joint mutual information maximization, kernel principal component analysis, and principal component analysis were employed to extract features133. Following the extraction and selection of features, the model underwent training using ML techniques.
The training ML model was responsible for the produced results. A ML-based approach was proposed to identify foreign direct investment (FDI) hacking in state budget estimates. Ensemble learning implements both supervised and unsupervised classifiers as a means to address the challenges associated with dimensionality reduction. To underscore the differences between a physical grid and a data update, the authors conducted a comparison between the two. To produce historical data and assess it for idea drift resulting from changes in data distribution, the initial coefficient analysis was employed. Furthermore, the K-NN approach was employed to showcase the system’s value, achieving the maximum achievable level of accuracy134. One potential strategy for detecting covert attacks is to combine kernel principal component analysis with the technique of the highly randomized tree. The authors utilized SVMLDT to identify anomalies in the SG. Following an assault, remedial actions were taken, and a technique known as adaptive load rejection was used to mitigate the effects of denial-of-service attacks135. The data integrity attacks that were analyzed included pulse, ramp, replay-trip, and replay. The effectiveness and ML techniques employed for the detection of cyberattacks are presented in Table 14.
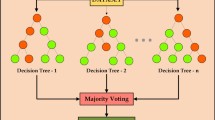
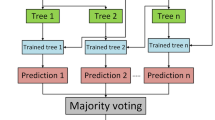
A novel abnormality detection and mitigation paradigm was provided. ML algorithms K.N.N. and D.T. classified assaults with 96.5% accuracy. This study introduces a cyber-physical anomaly detection system for communication and data integrity threats. This classification model uses D.T. ML with variation mode decomposition. CPADS was tested using the IEEE 39 bus design, the standard. The authors investigated foreign direct investment fraud detection using ensemble and extreme ML. The authors used a FLGB ensemble classifier to automatically recognize FDIA behavior using optimal parameters144. Extreme ML began with Gaussian weight selection. Foreign direct investment and denial of service assaults were classified using hierarchical clustering, hindering the state estimation approach. The authors used the D.T. algorithm with Kalman filters to create an accurate, efficient, and risk-reducing strategy. Foreign direct investment risks were identified using ML methods like data visualization, categorization, and aggregation145.
SGs use ML to find cybersecurity flaws. The authors studied using ML to identify smart meter breaches, which could raise energy bills. The author of the89 did not use ML to predict electricity bills. SG components are shown in Fig. 9.
Following the cleaning and arrangement of the data, many methods such as joint mutual information maximization, kernel principal component analysis, and principal component analysis were employed to extract features90. Following the extraction and selection of features, the model underwent training using ML techniques. The training ML model was responsible for the produced results.
A ML-based approach was proposed to identify foreign direct investment (FDI) hacking in state budget estimates. Ensemble learning implements both supervised and un-supervised classifiers as a means to address the challenges associated with dimensionality reduction. To underscore the differences between a physical grid and a data update, the authors conducted a comparison between the two. To produce historical data and assess it for idea drift resulting from changes in data distribution, the initial coefficient analysis was employed. Furthermore, the K-NN approach was employed to showcase the system’s value, achieving the maximum achievable level of accuracy91. One potential strategy for detecting covert attacks is to combine kernel principal component analysis with the technique of the highly randomized tree. The authors utilized SVMLDT to identify anomalies in the SG. Following an assault, remedial actions were taken, and a technique known as adaptive load rejection was used to mitigate the effects of denial-of-service attacks91. The data integrity attacks that were analyzed included pulse, ramp, replay-trip, and replay.
A unique paradigm for the detection and mitigation of abnormalities was also presented. K.N.N. and D.T., two ML algorithms, achieved a degree of accuracy of 96.5% in classifying attacks. This paper introduces a cyber-physical anomaly detection system designed to identify threats targeting communication and data integrity. This classification model was constructed using the D.T. ML approach with variation mode decomposition. An assessment was conducted to determine the effectiveness of CPADS utilizing the IEEE 39 bus design, which forms the standard. By employing ensemble and extreme ML techniques, the authors also explored the feasibility of detecting foreign direct investment fraud. By employing a FLGB ensemble classifier, the scientists automatically detected FDIA behavior using an optimal set of characteristics92. A first stage in extreme ML involved the random selection of weights from a Gaussian distribution. Hierarchical clustering was used to classify foreign direct investment and denial of service attacks, which significantly hindered the state estimate approach. The authors employed the D.T. algorithm and Kalman filters to develop an approach that achieved both accuracy and efficiency, while simultaneously reducing potential exposure to risk. The authors utilized ML techniques such as data visualization, categorization, and aggregation to identify foreign direct investment risks93. Table 15 presents the efficacy of various ML algorithms in detecting cyberattacks.
It is important to note that this study does not involve experiments with human subjects or any form of personal data collection. Furthermore, although our proposed AI-Blockchain hybrid framework is supported by extensive theoretical and empirical literature, it has not yet been deployed or validated in a real-world smart grid environment. These aspects remain open challenges and are part of our future research agenda.
Application of blockchain and artificial intelligence
Blockchain adaptation in the real-time energy sector
Utility and energy firms have recently started several projects utilizing BCN technology. Energy trading that is safe and transparent is the main use case for the BCN platform. Peer-to-peer transactions using strong encryption and distributed consensus are covered by this. It can be useful for grid maintenance, tracking carbon emissions, renewable energy certificates, tokenization techniques, and IoT integration, among other applications149. Although the objectives remain accessible, current programs have yet to develop to the point where they can fully support them. Significant modeling and testing continue to ensure project reliability, stability, and feasibility. Below, we examine some of these initiatives and explicitly connect them to AI and blockchain techniques discussed earlier in the manuscript.
Tennet
TenneT established a transmission system operator (TSO) in 2017 to manage electricity throughout Europe. The initial members were the Netherlands and Germany. In collaboration with IBM and Venderbron, TenneT developed a blockchain-based system to manage the electrical networks between these two countries. The system allows distributed energy sources to provide grid balancing services, ensuring that renewable energy sources are integrated efficiently. By leveraging blockchain’s decentralized ledger, this system enhances real-time data verification and energy transaction transparency, aligning with the blockchain-based smart grid security techniques discussed in Sect “Results”150.
LO3 energy
The Brooklyn Microgrid (BMGD) project, run by LO3 Energy in partnership with Centrica, Consensys, and Siemens, enables peer-to-peer energy trading using blockchain. This private blockchain network utilizes the PBFT consensus mechanism, built on Ethereum’s smart contract functionality, to facilitate secure transactions between consumers and prosumers151. AI algorithms integrated into the system predict energy demand patterns, optimize energy distribution, and ensure real-time transaction validation. Exergy, an extension of the LO3 project, employs AI-powered grid cloud management to reduce energy loss, detect anomalies, and automate overload responses, demonstrating the synergy between AI and blockchain in smart grid applications152,153,154.
Alliander and spectra
Alliander, a Dutch energy network operator, has implemented a peer-to-peer energy-sharing platform called Juliette, developed in collaboration with Spectral Energy. The project, deployed at De Ceuvel in Amsterdam, enables real-time energy transactions using blockchain tokens. The system relies on distributed AI algorithms to analyze grid congestion patterns, optimize trading strategies, and enhance security through automated fraud detection mechanisms155,156,157. By integrating blockchain for secure transactions and AI for data-driven optimization, this initiative highlights real-world implementations of the techniques proposed in Sect “Results”.
Motion Wrek
The German startup MotionWerk launched the Share & Charge project, utilizing blockchain for decentralized electric vehicle (EV) charging management. This system enables secure transactions between EV owners and charging station providers, facilitating transparent billing and decentralized roaming services158. MotionWerk’s AI-driven predictive analytics model optimizes charging station availability, energy pricing, and load balancing159, reducing grid strain while ensuring fair energy distribution. This use case demonstrates the practical integration of AI for real-time grid management and blockchain for secure transaction processing, reinforcing the methodologies outlined in Sects “Results” and “Algorithms used in smart grid”.
Artificial intelligence application
The advanced metering infrastructure (AMI) of smart grids generates significant volumes of data, which AI techniques can leverage to improve situational awareness, predict grid failures, and optimize energy efficiency. AI is particularly useful for small and medium-sized prosumers who have limited control system budgets but still require automated decision-making capabilities to efficiently manage their energy consumption and production160.
Game theory
AI-driven game-theoretic models improve decision-making in energy markets, enabling dynamic pricing, optimal resource allocation, and enhanced grid stability. Stackelberg and Cournot models, discussed in Sect. 4, have been successfully applied to optimize energy bidding strategies, reduce market manipulation risks, and ensure fair pricing161,162. These techniques support peer-to-peer energy trading platforms, such as those used by LO3 Energy and TenneT, by automating contract negotiations and minimizing transaction disputes.
Optimization approaches
AI-driven heuristic algorithms, such as genetic algorithms (GA), particle swarm optimization (PSO), and artificial immune systems (AIS), optimize energy distribution, fraud detection, and network resilience163,164,165. These methods enhance the real-time efficiency of blockchain-based energy trading platforms by ensuring that grid operations remain balanced, responsive, and secure. For example, Alliander’s AI-enhanced blockchain platform benefits from real-time optimization techniques to improve energy distribution accuracy and prevent grid congestion issues166.
Power generation forecast of renewable energy
Given the intermittent nature of renewable energy sources, AI-based long short-term memory (LSTM) networks and DL models improve energy generation forecasts, ensuring better integration of renewables into the grid. TenneT’s blockchain-based grid management system, for instance, incorporates AI-driven energy forecasting models to predict supply-demand fluctuations, reducing energy curtailment and enhancing system resilience167,168.
Research and implementations
Recent studies have applied game-theoretic optimization models and multi-objective evolutionary algorithms to enhance grid reliability, reduce carbon emissions, and maximize financial incentives for prosumers169,170. The application of these AI models to blockchain-secured smart grids has demonstrated tangible benefits, including improved transaction transparency, reduced operational costs, and increased energy trading efficiency. Real-world implementations, such as LO3 Energy’s Exergy platform and MotionWerk’s Share & Charge network, showcase how these AI-driven models facilitate practical energy management solutions171.
Lessons learned and performance outcomes
The integration of AI and blockchain in energy systems has demonstrated significant improvements in efficiency, security, and transparency. AI-driven models have proven to be invaluable for predicting energy demand, detecting anomalies, and preventing fraud. These applications enhance the accuracy and responsiveness of decentralized energy trading systems, ensuring fair and optimized market conditions.
Blockchain technology ensures secure, tamper-proof transactions, protecting against fraud and unauthorized access. However, while blockchain enhances transaction security and transparency, its computational requirements introduce latency and scalability challenges. AI plays a crucial role in optimizing blockchain efficiency, reducing delays, and enhancing adaptability to dynamic grid conditions.
The combination of AI and blockchain, as demonstrated by projects like LO3 Energy and Alliander, improves decentralized grid management by ensuring data integrity, automation, and secure peer-to-peer transactions. These hybrid systems help balance security concerns with computational scalability, allowing for broader adoption in smart grid applications.
Despite these advancements, future research must focus on developing lightweight AI models that integrate seamlessly with blockchain consensus mechanisms. This will enable real-time decision-making, improve transaction speed, and enhance system efficiency without compromising security. Additionally, further empirical validation through pilot projects and controlled test environments will be essential to measure scalability, interoperability, and long-term economic benefits of these technologies.
Algorithms used in smart grid
Inter-chain SC algorithm
One use case exists for the majority of these technologies, and that is token technology. If a condition is present in another BCn, unfortunately, there is no method to apply a SC to one of them. In the case of non-SC transfer assets, such as Bitcoin, the amount paid is “frozen” on a SC to show who owns it. This means that another work chain can enforce a characteristic of a SC both inside and outside of it172. Put yourself in the shoes of a user who wishes to move data from Ethereum to Polygon. Polygon provides cheaper storage than Ethereum does per unit of space. Notices of SC are broadcast through the Polygon’s DSL whenever an Ethereum node crates. In order to confirm its legitimacy and the likelihood of condition completion, the DSL will invite a set number of miners173.
The result is then displayed to the customer. The transaction is completed, and the miner receives payment from the customer’s charge for validating the data. In this scenario, the penalty the false data source must pay will compensate the miner. To validate the effectiveness of the inter-chain SC algorithm, further research and simulation are required to assess key performance indicators such as transaction finality time, miner verification success rates, and fraud detection efficiency174. Future experimental setups should evaluate how smart contract enforcement across chains influences security and efficiency175.
The pseudo-code aims to outline the process for transferring data from Ethereum to Polygon, leveraging a smart contract to enforce conditions across blockchains. This process involves smart contract notifications, miner verification on the Polygon network, and compensation mechanisms for data validation.
This pseudo-code represents a high-level overview of the process. It begins with the definition of smart contracts on both Ethereum and Polygon networks, followed by a function `TransferData` that manages the data transfer process. This process includes posting the transfer request on Ethereum, notifying the Polygon network, selecting miners for verification, and handling the transaction’s completion based on the verification results. Miners are compensated for their verification efforts, with penalties applied to sources of false data as necessary.
This algorithmic representation is simplified and would require detailed implementation specifics, including handling communication between blockchains, defining DSL (Domain Specific Language) notifications, and setting up secure and effective compensation and penalty mechanisms. Further, actual implementation would require a deeper integration with the blockchain platforms’ APIs and security protocols.
Instant standardization algorithm
The traded prices are stable and unchanging since every network employs a unique procedure. The criteria will be used to determine the transaction fee and exchange rate. Finding a single coin to serve as the de facto standard will further centralize the network, as has happened with all previous monetary systems176. Everyone else will back the BCN in charge of the funds. A regulatory agency is also needed to keep an eye on the value of each currency within the BCn system’s dominant currency. Here, precise evaluation of the value of the money may prove challenging.
In order to solve this issue and make future interoperability easier, we implemented an algorithm to assess the privacy, speed, scalability, security, and inter-chain linkages of any two or more networks177. The proposed approach requires further empirical validation through controlled simulation environments to assess its ability to improve interoperability while avoiding centralization178. Key performance indicators such as transaction latency, exchange rate stability, and computational efficiency should be examined in future studies179.
The Instant Standardization Algorithm’s pseudo-code includes the framework for creating a universally accepted transaction fee and exchange rate for use in various blockchain networks. This ensures cross-blockchain transactions remain efficient without relying on third-party regulatory bodies.
This pseudo-code illustrates a high-level approach to determining and using a standard currency for transactions involving multiple blockchain networks. The process begins with evaluating each participating blockchain’s attributes to identify which one offers the best combination of security, speed, scalability, transparency, and privacy. The blockchain network (BCN) with the highest score is selected as the standard for that particular transaction. The transaction is then executed using the currency of the chosen standard BCN, applying an established exchange rate and transaction fee.
This method promotes competitive improvement among blockchains by incentivizing them to enhance their performance standards to become the standard currency for more transactions, thereby avoiding centralization and eliminating the need for third-party regulation. Actual implementation would require detailed mechanisms for evaluating blockchain attributes and integrating with various blockchain networks to conduct transactions seamlessly.
In-system bridge mechanism
This bridge allows nodes to transfer tokens and other data between chains and networks. It makes it possible for a token to interact with another chain. Tokens are a virtual representation of the assets generated on another BCN using different coins or money. Tokens reflecting one’s network currency can be freely exchanged in any other BCn network. Today, many BCNs communicate across chains using well-liked bridge solutions, such as Binance Bridge, xPollinate, Matic Bridge, and Multi-chain. However, as previously mentioned, they are primarily developed and run by several organizations or businesses69.
To evaluate the effectiveness of the in-system bridge mechanism, experimental analysis is necessary to examine transaction execution speed, bridge security, and miner efficiency180. Future testbed implementations should focus on assessing how this approach impacts transaction completion times and its ability to enhance security in decentralized cross-chain communication181.
For the In-system Bridge Mechanism here, the goal is to enable seamless token and data transfer across different blockchain networks (BCNs) without relying on centralized intermediaries. The mechanism relies on in-system miners as verification agents, ensuring decentralization and reducing dependency on third-party validators182.
This pseudo-code provides a framework for a decentralized, in-system bridge mechanism that facilitates token and data transfers across blockchain networks by utilizing a network of miners as intermediaries. This approach ensures security, privacy, and transaction validity by leveraging the blockchain’s decentralized nature and avoiding centralized control points.
The process begins by deploying the bridge based on the request, followed by the selection of intermediary miners from both the source and target blockchains. These miners are responsible for validating the transaction on both ends, ensuring the tokens or data are locked and then transferred securely across chains. The successful execution of the transaction rewards the intermediary miners, incentivizing their participation and ensuring the bridge mechanism remains decentralized and autonomous.
Issues in the smart grid
Scalability issues
Currently, available consensus techniques include PoW and PoS, both of which make it extremely difficult to complete a transaction or create a block. The workers utilized a great deal of power, and their numbers are continually increasing. As a result, the SGES gains additional nodes, or users169. To keep up with the increasing number of users, it will need to adhere to specific guidelines. In this case, the SGES might not be able to grow178. Furthermore, the current BCN approach hides centralization while allowing the SGES to grow. This is due to the possibility of concentrated mining power in the hands of one or a small number of companies, which prevents miners from other regions from joining. The lack of heterogeneity and interoperability features in the current BCN-enabled system is another factor impeding SGES’s quick expansion. In this scenario, it is imperative to modify the current BCN network’s design to achieve significantly greater scalability179.
Cost inefficiency
Big mining corporations already utilise quite advanced installations and regulate the systems. The existing BCN technology, which requires a very well configured hardware system for mining to function, can be competed with by using the advanced consensus approach. Because of the significant power consumed and the participation of a third party, there needs to be an additional method for exchanging money180. The inter SC algorithm and IBSM, two of the most advanced elements of BCN technology, can be used to address these. This makes SGES a less expensive alternative.
Availability issues
The term “availability” refers to the guarantee of having timely access to the data or information, as well as the preservation of reliable information. In the event that there is a lack of availability, it has the potential to disrupt both the management of the grids and the delivery of energy. Data transmission becomes difficult and authorised access to the system becomes difficult when the number of contacts in the SGES landscape increases181. This is because the information contained in the contacts increases. Therefore, it is essential to provide the necessary level of security in order to keep the maximum amount of availability. The data-accessing procedure in SGES is slower, more difficult, and less trustworthy due to the current BCN, which causes a high degree of engagement from third parties. As a result, the modelling of the existing BCN needs to be revised182.
Authentication issues
The SGES of today is made up of many different smart devices and systems. Most of these have to do with electricity and technological devices. However, for efficient system control, monitoring, and maintenance, accurate device and owner identification is required. The identification of unauthorized access to system resources is made possible via device authentication. It is essential to use the current BCN-enabled SGES authentication to limit access to authorized nodes or individuals. During the authentication procedure, an attacker might be able to obtain the user’s personal information and interfere with the network protocol183. Users have to go through authentication processes, including decoding cryptographic functions or encrypting data, among other things, to fix it. Moreover, it can be avoided by creating distinct encryption methods that are challenging to decipher or guess171.
Heterogeneity and interoperability issues
SGES that use BCN technology have limited support for interoperability and heterogeneity. Inter-chain communications need a person to rely on and have faith in the authority of a third party. Furthermore, exchanging energy above a certain threshold is inefficient. Smart contracts cannot currently be implemented across different blockchain networks, which would greatly improve interoperability and allow for a greater number of interchange transactions73. To solve these issues and improve functioning, the current BCN in the SGES nomenclature must be modified.
Security issues
The centralization and dependence on other parties are hidden by the processes of the current BCn technology used in SGES. This technique creates security issues within the SGES. Given the location’s high level of mining power, a 51% attack is very likely. Data manipulation, fraudulent transactions, and duplicate spending are more likely184. Due to the system’s dependence on third-party authority for tasks like cost standardization, smart contract execution, and inter-chain operations, the system is vulnerable to security breaches. Man-in-the-middle (MITM)185 attacks and other incidents with comparable risks could occur. Hackers or unapproved third parties take advantage of a security flaw in the system during operation to obtain access. It is vital to reduce these problems as a result.
Network communication issues
When it comes to the Internet of Things, interoperability is crucial. The ability of smart devices made by various manufacturers to communicate with one another and with pre-existing infrastructures is crucial. To maximize resources it has to guarantee that plug-in hybrid electric vehicles (PHEVs)59 a significant component of the future of SG, can communicate with one another. Smart energy management, power consumption, and battery sharing are a few issues that require attention186. The interoperability of the advanced power electronics required at every level of SG needs to be demonstrated. Before they are used, in particular, the issues they raise such as confusion and adding complexity to systems need to be resolved. Power could only go in one direction before the SG, hence interactions were extremely simple. However, it allows for multiparty communication and a two-way power flow that complies with the SG. Reliability and security issues with wired and wireless187 contact setups are now affecting the SG. Smart grid installations rely on the substation’s proper operation since it serves as the central point of contact for all electricity companies. The SG sub-domains and domains will use a wide range of different public and private wireless and wired networks to communicate with one another. Working in a variety of networking environments is crucial for comparing the fundamental operating requirements of various applications, users, and domains as well as for determining performance metrics. There are many applications for chromophores188 although not all of their advantages have been thoroughly studied. The amount of testing and discussion about how successfully they safeguard real-world systems has been lacking. Thus, researching these fields ought to be a primary focus. Energy must be stored by SG, either directly or indirectly. Developing affordable storage solutions is currently the biggest challenge facing electrical power systems. Many excellent storage solutions are available, however, they are not very economical or efficient. Because this technology is efficient in power flow and has the potential to spread, many academics are also interested in it. Numerous applications have been investigated for energy storage, such as maintaining frequency stability, lowering peak loads, promoting green energy, postponing transmission upgrades, and supporting voltage. The only power facilities that can manage production levels that are higher than anticipated are thermal and hydropower plants. Nuclear power facilities always produce the same amount of electricity, however, the production of renewable energy sources varies with the weather. Thus, effective storage techniques are critical to a stable electric power grid. Energy can be stored in a variety of ways, including batteries, flywheels, compressed air, pumped water, superconducting magnet energy storage (SMES)189 hydrogen storage, and other materials. Each and every one has advantages and disadvantages. Because of this, a similar process is used to select the storage system that is most effective for a certain activity.
Fictitious topological and information flawed issue
A location’s geography, such as the configuration of rivers, roads, and boundaries, may be incorrectly represented on fake maps or plans. In fictional illustrations, changing the positions or relationships of geographical features could cause misconceptions among people. Fictional depictions may be insufficient or incorrect because they fail to include important topological features like water features or roadways. There may be inconsistencies in the layout of fictional representations, such as mismatched road networks or boundary lines. In topological datasets, errors in boundary points or disconnected road segments are common examples of outliers or anomalies that might point to inaccurate data190. Topological anomalies brought on by inaccurate data could include features that are replicated or have overlapping shapes.Due to faulty or insufficient topological data, imperfect data may contain gaps or low-quality estimations. Determining the veracity of flawed data that lacks quality marks or metadata may be difficult191.
Integration of big data and blockchain issues
Big data and blockchain both handle enormous volumes of data. Additional increasing challenges could make things worse. Blockchain puts consistency and transparency first, which could compromise privacy, whereas big data involves gathering and assessing enormous amounts of private information192. Big data systems’ diverse platforms and technologies make it difficult for them to interact with blockchain networks. Accurate and consistent data is essential for blockchain applications and big data. However, combining the two might make it more challenging to keep data consistent.
Solution of limitation
Increased scalability
One major difficulty facing the BCN-enabled SEGS is scalability. The next iteration of BCN technology might include PoL, an enhanced consensus technique. The implementation of this consensus mechanism can lead to more energy-efficient transactions on BCN networks. As the number of nodes or consumers rises, the transaction validation process becomes more effective and quicker while also avoiding potential new issues51. Moreover, it is possible to completely remove the system’s hidden centralization and power mining consolidation. There will be rewards for workers from different locations to take part in the mining process. Consequently, more transactions will be possible because of SGES communications.
Cost minimization
Although the current BCN architecture is expensive, if mining and transaction processing rates grow and power-intensive hardware is reduced, the upcoming version may be less expensive. Additionally, in all circumstances there won’t be any involvement from third parties, and the fees will be deducted from the transaction expenses. As mentioned in51, the total cost of next-generation BCN will drop significantly with the use of SGES.
Advanced security and availability
With the upcoming release of an enhanced consensus algorithm in the BCN framework, it may be imperative to reduce the consolidation of processing power. Implementing this approach will effectively eradicate the possibility of data duplication or alteration, so significantly decreasing the probability of 51% of attacks. Implementing enhanced transaction authentication will bolster the security of BCN, therefore mitigating the risk of fraudulent transactions and duplication of expenditures. Therefore, the probability of a security breach affecting the system ledger and algorithm will be reduced in comparison to the current scenario. Previous research has addressed the vulnerability of SG to intrusions by hackers. Similarly, prior research have examined the security of SG and the related dangers. Hence, the attainment of security and privacy can be accomplished by employing several strategies while simultaneously constraining technical progress. Some have proposed that analyzing cyberattacks based on their methodology, the key elements of the attacks, and their level of dynamism can enhance safety requirements for distributed generation. The analysis has uncovered novel attack routes and weaknesses, which will enhance the resilience of sensor networks. The following part will address the development of highly secure SG systems and will also explore possible directions for further study.
Real-time price standardization
The next generation includes a process for instantaneous standardization. For every electrical transaction, BCN can provide instant price standardization. Including a third party in any transaction to fix the price is prohibited. By analyzing variables including electricity quality, data security, transaction speed, transparency, privacy, and grid management system, the technology will determine the price of any grid on its own. The more advanced these grid needs are, the more expensive they will be.
AI-based solution
This paper comprehensively examines several potential applications of distributed smart grids, including demand response management, energy storage system integration, home energy management, integration of renewable energy sources, and energy security. The implementation of these technologies is expected to enhance productivity and simplify the management of Supplier Groups. Potential constraints encompass issues related to scalability, user pleasure, algorithm efficiency, privacy, security, and stability during failures, intelligent tool comprehension by users and network operators, and several other factors. By using artificial intelligence and cloud computing to compute power consumption and generation, the security of super grids (SG) can be improved and disruptions managed. Upon modifications to the input variables employed by the distributed agents, the system gains fresh knowledge and operates correspondingly. Every individual node within the grid will prioritize cost-effectiveness, adaptability, environmental consciousness, and exceptional speed. Enhancing the intelligence of the grid can be achieved by using self-learning algorithms capable of adjusting system parameters in reaction to any input.
The availability of vast quantities of data that can be analyzed using ML algorithms will augment the self-learning capability of the energy system. Further progress will be achievable for SG with the successful implementation of network automation, encompassing power production, distribution, and grid service administration. At present, most power system activities are carried out either manually or subject to some degree of automation. Implementing a distributed automation system can enhance the management of reactive power, integration of Distributed Energy Resources (DERs), processing speed, cost efficiency, and initiation of preventive maintenance. Complete automation of the SG system necessitates advanced intelligence in many domains, including automated feed switching, real-time load balancing, fault detection and restoration, voltage management, remote device monitoring, and the eradication of non-technical losses. By utilizing real-time data, Supply Chain (SG) can alleviate the strain on utilities and consumers. The feasibility of this is facilitated by enabling technology, encompassing sensors and automated controls. Although the implementation of self-healing technology may decrease the occurrence and duration of outages, the process of recovery will still require a significant amount of time for people. Prospective challenges to investigate include the rapid identification and diagnosis of concealed defects, timely implementation of preventive measures, and enabling users to assess the operational condition of the grid online. The implementation of SG plug-and-play technology may provide customers with an incentive to distribute the energy they produce on-site to other intelligent consumers. The effective incorporation of distributed algorithms into distributed controllers, facilitated by plug-and-play operation, enables the cost-effective administration of power distribution grid assets.
It is imperative for security measures to incorporate information theory, ML, and novel techniques for knowledge detection. Proposed solutions encompass customizing current security protocols to suit the requirements of SG applications, developing self-healing/adaptive security solutions, and incorporating security standards for dispersed components.
Future power system operators will require a diverse range of scientific and technical knowledge to effectively navigate the ever evolving regulations and technologies of the SG. The topics addressed include protocols for communication among distributed systems, cybersecurity, regulatory policies, utility decision-making applications, and the integration of distributed energy resources (DER). Smart grids strive to establish a completely automated, self-sufficient, responsive, flexible, self-healing, and financially viable system4. Evolving smart grid systems will increasingly rely on the integration of artificial intelligence (AI) and cloud computing to construct a self-learning system capable of improving resilience, security, and outage mitigation.
Rather than transmitting unprocessed data to the cloud, fog computing aims to locally preprocess it. The supply of computing resources according to demand in fog computing provides several benefits, such as scalability, energy efficiency, and flexibility. Previous research has been undertaken on the subject of integrating smart grid in conjunction with fog computing158,159. Given the growing volume of data generated by the future smart grid, fog computing is expected to gain significant importance.
A significant obstacle in the development of smart grids is the lack of relevant label data. The utilization of transfer learning by researchers is motivated by its ability to address the issue of data scarcity by minimizing the training data need. The advancement of smart grid technology may heavily rely on the issues of deep transfer learning, which are attracting growing attention from scholars162. The increasing significance of regulatory user involvement in power systems from the demand side can be attributed to the widespread adoption of fog computing and the advancement of the 5G network. Consumers who possess knowledge on their own power use and behavioral tendencies might provide valuable support to demand response initiatives.
SG security with AI and 5G
Technical advancements have been made to allow smart grids to connect with state-of-the-art technologies such as artificial intelligence and 5G. Optimal real-time infrastructure monitoring in the Internet of Things necessitates high-speed and resilient connections. Technological advancements such as 5G and B5G (beyond 5G) could facilitate the achievement of this vision. Nevertheless, the advancement of this technology has given rise to new challenges. AI and ML algorithms can enable the fulfilment of Quality of Service (QoS) criteria. Given that the objective of the network’s intelligent operation is to attain dependability, effectiveness, and robustness, then this is highly encouraging. Constructing an artificial intelligence model for a surveillance drone necessitates access to reliable historical data. Noncompliance with this requirement could result in overfitting and a reduction in the accuracy of the model. Furthermore, it is crucial to supervise AI decision-making to guarantee adherence to the rigorous cybersecurity regulations implemented on power lines.
Fictitious topological and information flawed solution
Make sure the data on maps or diagrams is accurate by using dependable sources and applying strict validation techniques. Software for geographic information systems (GIS) can give topological aspects a more realistic depiction. Use strategies like map projection modifications to reduce distortion and preserve the relative topology of features. Furthermore, if labels and legends are provided clearly and understandably, customers may find it easier to comprehend the depiction. Make sure that thorough methods for gathering data are in place. To adequately describe the topography of the area, use satellite imaging, fieldwork, and surveys. Maintaining and updating databases regularly is one way to fill in the gaps in the data. Use statistical methods like clustering analysis and z-score computations to find outliers in the data. Verify ambiguous data points by visually inspecting them and comparing them to credible sources. To automatically find and fix discrepancies, use data validation rules and checks. To find and fix geometric flaws in the data, use the topology validation features of GIS software. Determine missing or insufficient topological characteristics using data completeness evaluations. Use data interpolation techniques or alternate data sources to fill up any gaps in the topology.
Integration of big data and blockchain solution
To reduce the load on individual nodes, use splitting techniques to distribute data across numerous nodes. To handle massive data collections, combine blockchain technology with outside-of-the-chain storage options, using the blockchain just for validation and verification193. When analyzing sensitive data, protect it with privacy-enhancing techniques like homomorphic encryption and zero-knowledge proofs. Permitted blockchains can be used to make sure that sensitive data is only accessible to and altered by authorized users194. Provide standardized protocols and APIs to link big data platforms with blockchain networks. Use middleware solutions to make data sharing and communication between many platforms and technologies easier. Use data validation techniques through smart contracts to make sure that only very high-quality data is added to the blockchain. Make use of cryptographic hashing techniques to confirm the accuracy of data recorded on the blockchain and identify any modifications or manipulation.
Comparative analysis
In this review article, we critically examine the advancements in smart grid cybersecurity, focusing on the integration of Distributed Energy Resources (DERs) and the role of emerging technologies like AI and blockchain. This comparative analysis draws upon the insights from existing literature, including the seminal work by194 to highlight the evolution of cybersecurity solutions in the context of smart grids.
Scope, scalability, and effectiveness
The author195 underscores the importance of AI, IoT, and blockchain in enhancing the cybersecurity posture of smart grids, particularly with DER integration. These technologies facilitate secure energy trading, improve data integrity, and ensure resilient grid operations. However, the rapidly changing cyber threat landscape and the growing complexity of smart grid networks call for solutions that not only address current challenges but are also scalable and effective against future threats.
In reviewing the literature, we find that while existing solutions lay a strong foundation for cybersecurity in smart grids, there is a pressing need for more adaptable and scalable approaches. This includes the development of AI models that can dynamically learn and evolve to detect and mitigate new cyber threats, and blockchain frameworks that can handle the increasing volume of peer-to-peer energy transactions without compromising security or efficiency.
Innovative aspects and gaps
The review highlights several innovative aspects of current research, such as the application of DL algorithms for anomaly detection and the use of blockchain for transparent and secure energy transactions. However, gaps remain in fully exploiting the potential of these technologies. For instance, there is a need for:
Enhanced AI Models: Developing more sophisticated AI algorithms that can proactively identify and neutralize cyber threats in real time, adapting to the evolving tactics of cyber adversaries.
Blockchain Scalability: Addressing scalability and latency issues in blockchain implementations to support widespread adoption in the energy sector, ensuring that security does not come at the expense of performance.
Comprehensive IoT Security: Expanding the focus on IoT device security within the smart grid to encompass advanced encryption, authentication, and integrity checks, beyond current standards.
Potential impact and future directions
The conclusions suggest that addressing these deficiencies could significantly impact the resilience, reliability, and lifespan of smart grids. Enhanced cybersecurity measures will protect critical infrastructure from emerging threats, facilitate seamless integration of renewable energy sources, and enhance the safety and efficiency of energy commerce.
Future studies should prioritize the development of adaptable cybersecurity frameworks that can effectively respond to the dynamic smart grid environment. To address the intricate challenges related to smart grid cybersecurity, it is imperative to explore state-of-the-art artificial intelligence (AI) and blockchain technologies, establish robust protocols for safeguarding the internet of things (IoT), and promote collaboration among diverse academic disciplines. Relevant information is provided in the subsequent section.
Discussion
Previous research has addressed the vulnerability of Social Networks to hackers. Similarly, prior studies have examined the security of SG and the related dangers. The attainment of privacy and security can be accomplished by employing a range of strategies while simultaneously constraining technological progress. A contention has been made that analyzing cyberattacks based on their dynamic characteristics, attack techniques, and key elements can enhance safety standards for smart grids. The present study has revealed novel attack channels and vulnerabilities, thereby enhancing the resilience of security groups. However, while research has largely focused on attack classification and risk assessment, fewer studies have proposed practical deployment strategies for integrating AI and blockchain into smart grids. This work aims to bridge that gap by evaluating the feasibility of implementation and addressing potential challenges.
It is crucial to prioritize higher-level data structures and algorithms to include more advanced security features. The current state estimation algorithms cannot utilize the intrinsic mechanisms of FDIAs for evaluating the accuracy of an input. Consequently, it is necessary to employ complex data structures and algorithms to guarantee security. For example, the security of SCADA systems can be enhanced by integrating supplementary security modules. The main function of these modules is to compute false positive rates by employing novel criteria, in conjunction with the current methods for detecting inaccurate data.
The emergence of CPS and the Internet of Things as fundamental components of SGI 4.0 has led to a simultaneous increase in both the complexity of the undertaking and our accumulated expertise. As a result, SGI 4.0 now possesses a significantly larger amount of data of superior quality. Web applications, transactional applications, interactive servers, RFID, controllers, sensors, actuators, and other data sources are included in the data repository provided by SGI 4.0 for smart grid applications. Numerous social networking applications will exploit the gathered data. The data has a diverse range of applications, encompassing demand and response, sophisticated monitoring and management, energy consumption, metering, power cost analysis, and utility bill auditing. The level of sophistication of the Cyber-Physical System (CPS) used for energy generation and distribution directly correlates with the amount of data gathered. Hence, advanced systems must incorporate all data sources to gather, merge, manipulate, store, analyze, and present vast amounts of data196.
In practical terms, AI-driven cybersecurity mechanisms have already been deployed in smart grids for intrusion detection and anomaly detection. Blockchain, while still emerging, has demonstrated success in decentralized energy trading and secure authentication processes. However, integration challenges remain, particularly regarding computational overhead, data latency, and interoperability with existing infrastructure. Our proposed hybrid AI-Blockchain security model mitigates these concerns by employing optimized consensus mechanisms (e.g., Proof-of-Stake) and federated learning-based AI approaches to enhance efficiency and scalability.
To maintain the privacy of smart grids, federated learning is the optimal approach. This form of learning integrates the fundamental mechanisms. Locally constructed models provide substantial privacy advantages in comparison to ML applications that transmit raw data to a central server. Data privacy, energy demand, and electric load forecasting are among the many functional layer uses for the SG. Federated learning has demonstrated efficacy in many fields including transportation, healthcare, smart cities, visual object recognition, finance, and next-word prediction197. To ensure the secure and efficient transmission of clients’ energy data over the satellite gateway, the developers employed F.L. Several experts have highlighted that the FL surface is susceptible to incursions and presents its unique challenges97. Before integrating FL into the SG, a thorough assessment of future security measures is necessary.
Conclusion
Recapitulation
This systematic literature review (SLR) has provided a comprehensive exploration of the cybersecurity landscape within smart grids (SGs), focusing on the pivotal roles of blockchain (BC) and AI in fortifying these critical infrastructures against cyber threats. Reflecting on the research questions that guided our study, we offer a conclusive analysis that underscores the interconnectedness between our findings and the initial queries.
Our investigation has unearthed a multifaceted array of vulnerabilities inherent to SGs, ranging from physical infrastructure weaknesses to software-level exploits. This aligns with our motivation to understand the breadth and depth of SG vulnerabilities, highlighting the necessity for robust security frameworks that can adapt to evolving threats.
We have catalogued a comprehensive spectrum of cyberattacks targeting SGs, alongside an assortment of countermeasures, including novel AI-driven solutions and BC-based strategies. This directly responds to our aim of elucidating the dynamic cyber threat landscape and the corresponding defensive mechanisms that safeguard SG operations.
Our review has showcased the diversity of BC techniques deployed in SG contexts, from decentralized energy trading to integrity verification of critical data. This addresses our motivation to explore BC’s utility in enhancing SG security, confirming its potential to revolutionize energy sector cybersecurity paradigms.
The study delves into various AI and ML methodologies, from predictive analytics to anomaly detection, reinforcing their critical role in preemptively identifying and neutralizing cyber threats. This fulfills our motivation to examine AI and ML’s capacity to bolster SG security, affirming their indispensable contribution to advanced cybersecurity strategies.
Finally, our analysis identifies several open issues and avenues for future research, including the need for standardized frameworks for AI and BC integration into SGs and the exploration of ethical considerations in automated cybersecurity solutions. This reflection on unresolved challenges and potential research paths is motivated by our desire to chart the course for future advancements in SG cybersecurity.
To recapitulate, our study directly addresses the research questions set forth at the outset, offering a thorough analysis of SG vulnerabilities, cyberattacks and countermeasures, and the transformative roles of BC and AI in shaping the future of SG cybersecurity. By explicitly linking our findings to these questions, we have not only provided answers to the posed inquiries but also highlighted the significant impact and innovative contributions of BC and AI technologies in advancing SG security. This conclusion reaffirms our commitment to enhancing SG cybersecurity through the adoption of cutting-edge technologies and sets a foundation for future research endeavours in this critical field.
Future directions
Future research should emphasize the deployment of real-world pilot projects to test the feasibility of AI-Blockchain cybersecurity frameworks in live smart grid environments. Addressing interoperability concerns between blockchain systems and existing power grid infrastructure will be crucial to ensuring seamless adoption.
Another key avenue involves the integration of federated learning (FL) with SG security architectures. FL offers significant privacy advantages by allowing decentralized model training without exposing raw data, making it a promising technique for smart grid anomaly detection, energy forecasting, and demand response optimization. However, future work must address FL’s security vulnerabilities, such as adversarial attacks and communication bottlenecks, to ensure its effectiveness in large-scale deployments.
Moreover, interoperability challenges between blockchain-based SG security solutions and existing infrastructure remain a crucial research area. Future studies should explore lightweight consensus mechanisms to mitigate blockchain’s computational overhead while maintaining its security benefits. Additionally, post-quantum cryptography techniques should be examined to safeguard blockchain-secured SGs against emerging cryptographic threats.
Future research should also focus on the empirical validation of the proposed AI-Blockchain Hybrid Security Model. Simulation-based testing using benchmark cybersecurity datasets (e.g., KDD’99, UNSW-NB15, or ICS cybersecurity datasets) can be employed to assess the accuracy and efficiency of AI-driven threat detection mechanisms. Additionally, blockchain performance testing using platforms such as Hyperledger Fabric or Ethereum test networks should be conducted to evaluate latency, throughput, and security resilience.
Real-world case studies and experimental implementations in smart grid environments will be critical for assessing the practical viability of AI-Blockchain integration. Collaborations with industry stakeholders or leveraging open smart grid cybersecurity datasets can help test the effectiveness of the proposed security framework in mitigating cyber threats. These validation efforts will bridge the gap between theoretical contributions and practical deployment, ensuring a robust and scalable cybersecurity solution for smart grids.
Finally, ethical considerations in AI-driven cybersecurity solutions should be further investigated. The deployment of automated decision-making systems in smart grids raises concerns regarding bias, transparency, and regulatory compliance. Establishing standardized frameworks for AI and BC integration will be essential in ensuring fair, accountable, and robust cybersecurity practices in SG environments.
By addressing these critical aspects, future research will contribute to building a resilient, adaptive, and secure smart grid ecosystem, capable of withstanding evolving cyber threats while ensuring efficiency and sustainability.
Data availability
The data used to support the findings of this study are available from the corresponding authors upon request.
Abbreviations
- ML:
-
Machine learning
- DL:
-
Deep learning
- SG:
-
Smart grid
- AI:
-
Artificial intelligence
- MIM:
-
Man in middle
- IoT:
-
Internet of things
- KNN:
-
K-nearest neighbors
- NN:
-
Neural network
- SVM:
-
Support vector machine
- BC:
-
Blockchain
- RNN:
-
Recurrent neural network
- UDP:
-
User datagram protocol
- DoS:
-
Denial of service
- DDoS:
-
Distributed denial of service
- IDS:
-
Intrusion detection system
- TCP:
-
Transmission control protocol
- CNN:
-
Conventional neural network
- ANN:
-
Artificial neural network
References
Ghadi, Y. Y. et al. Enhancing Smart Grid Cybersecurity: A Comprehensive Analysis of Attacks, Defenses, and Innovative AI-Blockchain Solutions. (2023).
Jha, A. V. et al. Reliability analysis of smart grid networks incorporating hardware failures and packet loss. Rev. Roum Sci. Tech. El. 65 (3), 245–252 (2021).
Mahmoud, M. A. et al. The current state of the Art in research on predictive maintenance in smart grid distribution network: fault’s types, causes, and prediction methods—A systematic review. Energies 14 (16), 5078 (2021).
Sharma, D. K. et al. A review on smart grid telecommunication system. Mater. Today Proc. 51, p470–474 (2022).
Ibrahim, C. et al. A review on the deployment of demand response programs with multiple aspects coexistence over smart grid platform. Renew. Sustain. Energy Rev. 162, 112446 (2022).
Krichen, M. et al. Blockchain for modern applications: A survey. Sensors 22 (14), 5274 (2022).
Cichy, C. & Rass, S. An overview of data quality frameworks. IEEE Access 7, 24634–24648 (2019).
Connor, P. et al. Sources of risk and uncertainty in UK smart grid deployment: an expert stakeholder analysis. Energy 161, 1–9 (2018).
Syed, D. et al. Smart grid big data analytics: survey of technologies, techniques, and applications. IEEE Access. 9, 59564–59585 (2020).
Dalipi, F. & Yayilgan, S. Y. Security and privacy considerations for iot application on smart grids: Survey and research challenges. In IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW) IEEE (2016).
Sui, Z. & de Meer, H. BAP: A batch and auditable privacy preservation scheme for demand response in smart grids. IEEE Trans. Ind. Inf. 16 (2), 842–853 (2019).
Matos, D. R. et al. Securing electronic health records in the cloud. In Proceedings of the 1st Workshop on Privacy by Design in Distributed Systems. (2018).
Chen, S. et al. Internet of things based smart grids supported by intelligent edge computing. IEEE Access. 7, 74089–74102 (2019).
Khan, M. W. et al. QoS-aware traffic scheduling framework in cognitive radio based smart grids using multi-objective optimization of latency and throughput. Ad Hoc Netw. 97, 102020 (2020).
Yen, S. W. et al. Effect of smart meter data collection frequency in an early detection of shorter-duration voltage anomalies in smart grids. Int. J. Electr. Power Energy Syst. 109, 1–8 (2019).
Xu, B. et al. A hybrid demand response mechanism based on real-time incentive and real-time pricing. Energy 231, 120940 (2021).
Liu, Q. et al. Optimal Robust Real-time Pricing Algorithm Based on Utility Maximization for Smart Grid. In 4th International Conference on Energy, Electrical and Power Engineering (CEEPE) IEEE (2021).
Sen, Ö. et al. On using contextual correlation to detect multi-stage cyber attacks in smart grids. Sustain. Energy Grids Netw. 32, 100821 (2022).
Asif, M. Industrial automation information analogy for smart grid security. Mater. Continua. 71, 3985–3999. https://doi.org/10.32604/cmc.2022.023010 (2022).
Saba, D. et al. Development of an intelligent solution for the optimization of hybrid energy systems. Appl. Sci. 12 (17), 8397 (2022).
Judge, M. A. et al. Overview of smart grid implementation: frameworks, impact, performance and challenges. J. Energy Stor. 49, 104056 (2022).
Mazhar, T. et al. Analysis of cyber security attacks and its solutions for the smart grid using machine learning and blockchain methods. Future Internet. 15 (2), 83 (2023).
Kishor, A. & Chakraborty, C. Artificial intelligence and internet of things based healthcare 4.0 monitoring system. Wirel. Pers. Commun. 127 (2), 1615–1631 (2022).
Shafiq, M. et al. The Rise of Internet of Things: Review and Open Research Issues Related To Detection and Prevention of IoT-Based Security Attacks. Wirel. Commun. Mob. Comput. https://doi.org/10.1155/2022/8669348 (2022).
Chander, B. et al. Artificial intelligence-based internet of things for industry 5.0. Artificial intelligence-based internet of things systems. 3–45 (2022).
Abdullah, A. M. et al. An Efficient Multidocument Blind Signcryption Scheme for Smart Grid-Enabled Industrial Internet of Things. Wirel. Commun. Mob. Comput. (2022).
Alavikia, Z. & Shabro, M. A Comprehensive Layered Approach for Implementing Internet of things-enabled Smart Grid: A Survey (Digital Communications and Networks, 2022).
Sun, C. C. et al. Intrusion detection for cybersecurity of smart meters. IEEE Trans. Smart Grid. 12 (1), 612–622 (2020).
Kim, Y., Hakak, S. & Ghorbani, A. Smart Grid Security: Attacks and Defence Techniques (IET Smart Grid, 2022).
Alam, H. & Tomai, E. Security Attacks And Countermeasures In Smart Homes. Int. J. Cybern. Inform. (IJCI) 12 (12), 109 (2023).
Mazhar, T. et al. Analysis of challenges and solutions of IoT in smart grids using AI and machine learning techniques: A review. Electronics 12 (1), 242 (2023).
Mazhar, T. et al. The role of ML, AI and 5G technology in smart energy and smart Building management. Electronics 11 (23), 3960 (2022).
Abbasinezhad-Mood, D. & Nikooghadam, M. Design and hardware implementation of a security-enhanced elliptic curve cryptography based lightweight authentication scheme for smart grid communications. Future Gener. Comput. Syst. 84, 47–57 (2018).
Ding, J. et al. Cyber threats to smart grids: review, taxonomy, potential solutions, and future directions. Energies 15 (18), 6799 (2022).
Kumari, D., Singh, K. & Manjul, M. Performance evaluation of Sybil attack in cyber physical system. Procedia Comput. Sci. 167, 1013–1027 (2020).
Qasaimeh, M., Turab, R. & Al-Qassas, R. S. Authentication techniques in smart grid: a systematic review. TELKOMNIKA (Telecommun. Comput. Electron. Control). 17 (3), 1584–1594 (2019).
Konstantinou, C. & Maniatakos, M. 15. Security Analysis of Smart Grid. (2017).
Liu, R. & Srivastava, A. Integrated Simulation To Analyze the Impact of cyber-attacks on the Power Grid. In 2015 Workshop on Modeling and Simulation of Cyber-Physical Energy Systems (MSCPES) (IEEE, 2015).
Mazhar, T. et al. Analysis of IoT security challenges and its solutions using artificial intelligence. Brain Sci. 13 (4), 683 (2023).
Dileep, G. A survey on smart grid technologies and applications. Renew. Energy. 146, 2589–2625 (2020).
Ghiasi, M. et al. A comprehensive review of cyber-attacks and defense mechanisms for improving security in smart grid energy systems: past, present and future. Electr. Power Syst. Res. 215, 108975 (2023).
Lamnatou, C., Chemisana, D. & Cristofari, C. Smart grids and smart technologies in relation to photovoltaics, storage systems, buildings and the environment. Renew. Energy. 185, 1376–1391 (2022).
Bitirgen, K. & Filik, Ü. B. A hybrid deep learning model for discrimination of physical disturbance and cyber-attack detection in smart grid. Int. J. Crit. Infrastruct. Prot. 40, 100582 (2023).
Hasan, M. N. et al. Electricity theft detection in smart grid systems: A CNN-LSTM based approach. Energies 12 (17), 3310 (2019).
Ullah, A. et al. CNN and GRU based deep neural network for electricity theft detection to secure smart grid. In 2020 International Wireless Communications and Mobile Computing (IWCMC). IEEE. (2020).
Silva, P. C. et al. Distributed evolutionary hyperparameter optimization for fuzzy time series. IEEE Trans. Netw. Serv. Manage. 17 (3), 1309–1321 (2020).
Sakhnini, J., Karimipour, H. & Dehghantanha, A. Smart grid cyber attacks detection using supervised learning and heuristic feature selection. In IEEE 7th international conference on smart energy grid engineering (SEGE) IEEE (2019).
Kotsiopoulos, T. et al. Machine learning and deep learning in smart manufacturing: the smart grid paradigm. Comput. Sci. Rev. 40, 100341 (2021).
Selvarajan, S. et al. An artificial intelligence lightweight blockchain security model for security and privacy in IIoT systems. J. Cloud Comput. 12 (1), 38 (2023).
Chafiq, T., Azmi, R. & Mohammed, O. Blockchain-based Electronic Voting Systems: A Case Study in Morocco. Int. J. Intell. Netw. (2024).
Mariano, D. C. et al. A guide to performing systematic literature reviews in bioinformatics. arXiv (2017).
Kitchenham, B. et al. Systematic literature reviews in software engineering–a systematic literature review. Inf. Softw. Technol. 51 (1), 7–15 (2009).
Keele, S. Guidelines for performing systematic literature reviews in software engineering. Tech. Rep. (2007).
Kazmi, S. et al. Towards optimization of metaheuristic algorithms for IoT enabled smart homes targeting balanced demand and supply of energy. IEEE Access. 7, 24267–24281 (2017).
Ida, T., Tanaka, M. & Ito, K. Smart Grid Economics: A Field Experimental Approach To Demand Response (Springer Nature, 2024).
Salkuti, S. R. Energy storage technologies for smart grid: a comprehensive review. Majlesi J. Electr. Eng. 14 (1), 39–48 (2020).
Pallonetto, F. et al. On the assessment and control optimisation of demand response programs in residential buildings. Renew. Sustain. Energy Rev. 127, 109861 (2020).
Salkuti, S. R. Study on the performance indicators for smart grids: a comprehensive review. TELKOMNIKA (Telecommun. Comput. Electron. Control). 17 (6), 2912–2918 (2019).
Martinez, C. M. et al. Energy management in plug-in hybrid electric vehicles: recent progress and a connected vehicles perspective. IEEE Trans. Veh. Technol. 66 (6), 4534–4549 (2016).
Ostadian, R. et al. Intelligent energy management systems for electrified vehicles: current status, challenges, and emerging trends. IEEE Open. J. Veh. Technol. 1, 279–295 (2020).
Salkuti, S. R. Challenges, issues and opportunities for the development of smart grid. Int. J. Electr. Comput. Eng. (IJECE). 10 (2), 1179–1186 (2020).
Chihoub, H. & Collet, C. A scalability comparison study of data management approaches for smart metering systems. In 45th International Conference on Parallel Processing (ICPP) IEEE. (2016).
Pali, B. S. & Vadhera, S. Renewable energy systems for generating electric power: A review. In IEEE 1st international conference on power electronics, intelligent control and energy systems (ICPEICES) IEEE (2016). IEEE. (2016).
Sarker, S. K. et al. Ancillary voltage control design for adaptive tracking performance of microgrid coupled with industrial loads. IEEE Access. 9, 143690–143706 (2021).
Alfandi, O., Otoum, S. & Jararweh, Y. Blockchain solution for iot-based critical infrastructures: Byzantine fault tolerance. In NOMS 2020–2020 IEEE/IFIP network operations and management symposium. IEEE. (2020).
Zhang, C. et al. Energy storage system: current studies on batteries and power condition system. Renew. Sustain. Energy Rev. 82, 3091–3106 (2018).
Abujubbeh, M., Al-Turjman, F. & Fahrioglu, M. Software-defined wireless sensor networks in smart grids: an overview. Sustain. Cities Soc. 51, 101754 (2019).
Banik, S. & Banik, T. Survey on Simulation and Vulnerability Testing in Smart Grid. (2024).
Uddin, S. S. et al. Next-generation blockchain enabled smart grid: conceptual framework, key technologies and industry practices review. Energy AI. 12, 100228 (2023).
Ciatto, G. et al. Blockchain-based coordination: assessing the expressive power of smart contracts. Information 11 (1), 52 (2020).
Salvadori, F. et al. Design and implementation of a flexible intelligent electronic device for smart grid applications. In 2017 IEEE Industry Applications Society Annual Meeting IEEE. (2017).
Chehri, A., Fofana, I. & Yang, X. Security risk modeling in smart grid critical infrastructures in the era of big data and artificial intelligence. Sustainability 13 (6), 3196 (2021).
Xiao, H. et al. Joint clustering and blockchain for real-time information security transmission at the crossroads in C-V2X networks. IEEE Internet Things J. 8 (18), 13926–13938 (2021).
Omol, E., Mburu, L. & Onyango, D. Anomaly Detection In IoT Sensor Data Using Machine Learning Techniques For Predictive Maintenance In Smart Grids. Int. J. Sci. Technol. Manag. 5 (1), 201–210 (2024).
Uddin, S. S. et al. Energy and AI.
Shitharth, S. et al. An enriched RPCO-BCNN mechanisms for attack detection and classification in SCADA systems. IEEE Access. 9, 156297–156312 (2021).
Pei, C. et al. A deviation-based detection method against false data injection attacks in smart grid. IEEE Access. 9, 15499–15509 (2021).
Khadidos, A. O. et al. Integrating Industrial Appliances for Security Enhancement in Data Point Using SCADA Networks with Learning Algorithm. Int. Trans. Electr. Energy Syst. (2022).
Boyaci, O. et al. Cyberattack detection in large-scale smart grids using chebyshev graph convolutional networks. In 9th International Conference on Electrical and Electronics Engineering (ICEEE) IEEE. (2022).
Rabie, O. B. J. et al. A proficient ZESO-DRKFC model for smart grid SCADA security. Electronics 11 (24), 4144 (2022).
Zhang, W. et al. Resilient economic control for distributed microgrids under false data injection attacks. IEEE Trans. Smart Grid. 12 (5), 4435–4446 (2021).
Agung, A. A. G. & Handayani, R. Blockchain for smart grid. J. King Saud Univ. Comput. Inform. Sci. 34 (3), 666–675 (2022).
Huseinović, A. et al. A survey of denial-of-service attacks and solutions in the smart grid. IEEE Access. 8, 177447–177470 (2020).
Monday, H. N. et al. The Capability of Wavelet Convolutional Neural Network for Detecting Cyber Attack of Distributed Denial of Service in Smart Grid. In 18th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP) IEEE. (2021).
Wlazlo, P. et al. Man-in‐the‐middle attacks and defence in a power system cyber‐physical testbed. IET Cyber Phys. Syst. Theory Appl. 6 (3), 164–177 (2021).
Hadjidemetriou, L. et al. Demonstration of man in the middle attack on a feeder power factor correction unit. In 2020 IEEE PES Innovative Smart Grid Technologies Europe (ISGT-Europe). IEEE. (2020).
Yılmaz, E. N. et al. Cyber security analysis of DoS and MitM attacks against PLCs used in smart grids. In 7th International Istanbul Smart Grids and Cities Congress and Fair (ICSG), Istanbul, Turkey. (2019).
Fatima, R. et al. How persuasive is a phishing email? A phishing game for phishing awareness. J. Comput. Secur. 27 (6), 581–612 (2019).
Deb, D. et al. Security analysis of MITM attack on SCADA network. In Machine Learning, Image Processing, Network Security and Data Sciences: Second International Conference, MIND 2020, Silchar, India, July 30–31, 2020, Proceedings, Part II 2 Springer. (2020).
Bashir, A. K. et al. Comparative analysis of machine learning algorithms for prediction of smart grid stability. Int. Trans. Electr. Energy Syst. 31 (9), e12706 (2021).
Maqbool, H. et al. An optimized fuzzy based control solution for frequency Oscillation reduction in electric grids. Energies 15 (19), 6981 (2022).
Kaveh, M. & Mosavi, M. R. A lightweight mutual authentication for smart grid neighborhood area network communications based on physically unclonable function. IEEE Syst. J. 14 (3), 4535–4544 (2020).
Darwish, I. & Saadawi, T. Attack detection and mitigation techniques in industrial control system-smart grid dnp3. In 1st International Conference on Data Intelligence and Security (ICDIS) IEEE. (2018).
Su, Q. et al. Observer-based detection and reconstruction of dynamic load altering attack in smart grid. J. Franklin Inst. 358 (7), 4013–4027 (2021).
Xun, P. et al. Successive direct load altering attack in smart grid. Computers Secur. 77, 79–93 (2018).
Gharghory, S. M. Deep network based on long short-term memory for time series prediction of microclimate data inside the greenhouse. Int. J. Comput. Intell. Appl. 19 (02), 2050013 (2020).
An, D. et al. Defending against data integrity attacks in smart grid: A deep reinforcement learning-based approach. IEEE Access. 7, 110835–110845 (2019).
Lee, L. & Hu, P. Vulnerability analysis of cascading dynamics in smart grids under load redistribution attacks. Int. J. Electr. Power Energy Syst. 111, 182–190 (2019).
Yuan, Y., Li, Z. & Ren, K. Quantitative analysis of load redistribution attacks in power systems. IEEE Trans. Parallel Distrib. Syst. 23 (9), 1731–1738 (2012).
Najafabadi, S. G., Naji, H. R. & Mahani, A. Sybil attack Detection: Improving security of WSNs for smart power grid application. In Smart Grid Conference (SGC) IEEE. (2013).
Jahangir, H. et al. Deep learning-based forecasting approach in smart grids with microclustering and bidirectional LSTM network. IEEE Trans. Ind. Electron. 68 (9), 8298–8309 (2020).
El Mrabet, Z. et al. Cyber-security in smart grid: survey and challenges. Comput. Electr. Eng. 67, 469–482 (2018).
Sharma, M. & Agarwal, A. Survey on authentication and encryption techniquesfor smart grid communication. In 7th India International Conference on Power Electronics (IICPE) IEEE. (2016).
Flå, L. H. et al. Tool-assisted threat modeling for smart grid cyber security. In International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA) IEEE. (2021).
Tavana, M. et al. Efficiency decomposition and measurement in two-stage fuzzy DEA models using a bargaining game approach. Comput. Ind. Eng. 118, 394–408 (2018).
Jindal, A. et al. Decision tree and SVM-based data analytics for theft detection in smart grid. IEEE Trans. Ind. Inf. 12 (3), 1005–1016 (2016).
Khadam, U. et al. Advanced security and privacy technique for digital text in smart grid communications. Comput. Electr. Eng. 93, 107205 (2021).
Chen, G. et al. Blockchain-based cyber security and advanced distribution in smart grid. In IEEE 4th International Conference on Electronics Technology (ICET) IEEE (2021).
Vance, T. R. & Vance, A. Cybersecurity in the blockchain era: a survey on examining critical infrastructure protection with blockchain-based technology. In IEEE International Scientific-Practical Conference Problems of Infocommunications, Science and Technology (PIC S&T) IEEE (2019).
Appasani, B. et al. Blockchain-enabled smart grid applications: architecture, challenges, and solutions. Sustainability 14 (14), 8801 (2022).
Mengidis, N. et al. Blockchain and AI for the next generation energy grids: cybersecurity challenges and opportunities. Inform. Secur. 43 (1), 21–33 (2019).
Liang, G. et al. A review of false data injection attacks against modern power systems. IEEE Trans. Smart Grid. 8 (4), 1630–1638 (2016).
Chadd, A. DDoS attacks: past, present and future. Netw. Secur. 2018 (7), 13–15 (2018).
Ferrag, M. A. & Maglaras, L. DeepCoin: A novel deep learning and blockchain-based energy exchange framework for smart grids. IEEE Trans. Eng. Manag. 67 (4), 1285–1297 (2019).
Deng, R., Zhuang, P. & Liang, H. CCPA: coordinated cyber-physical attacks and countermeasures in smart grid. IEEE Trans. Smart Grid. 8 (5), 2420–2430 (2017).
Li, X. et al. A novel dynamic watermarking-based EKF detection method for FDIAs in smart grid. IEEE/CAA J. Autom. Sin.. 9 (7), 1319–1322 (2022).
Turner, S. & Uludag, S. Interaction and Synergy of the Smart Grid and Intelligent Transportation Systems Towards Smart Cities (CRC Press, 2016).
Priyadarshini, I. et al. Identifying cyber insecurities in trustworthy space and energy sector for smart grids. Comput. Electr. Eng. 93, 107204 (2021).
Paul, P. et al. Blockchain technology and its Types—A short review. Int. J. Appl. Sci. Eng. (IJASE). 9 (2), 189–200 (2021).
Jerbi, W. et al. A blockchain based authentication scheme for mobile data collector in IoT. In 2021 International Wireless Communications and Mobile Computing (IWCMC). IEEE (2021).
Shah, S. F. A. et al. Applications, challenges, and solutions of unmanned aerial vehicles in smart City using blockchain. PeerJ Comput. Sci. 10, e1776 (2024).
Kubler, S. et al. Decision support system for blockchain (DLT) platform selection based on ITU recommendations: A systematic literature review approach. Expert Syst. Appl. 211, 118704 (2023).
Six, N., Herbaut, N. & Salinesi, C. Which Blockchain to choose? A decision support tool to guide the choice of a Blockchain technology. arXiv (2020).
Faquir, D. et al. Cybersecurity in smart grids, challenges and solutions. AIMS Electron. Electr. Eng. 5 (1), 24–37 (2021).
Rao, P. U., Sodhi, B. & Sodhi, R. Cyber Security Enhancement of Smart Grids Via Machine Learning-A Review. In 21st National Power Systems Conference (NPSC) IEEE (2020).
Yin, X. C. et al. Toward an applied cyber security solution in IoT-based smart grids: an intrusion detection system approach. Sensors 19 (22), 4952 (2019).
Sahu, L. K. et al. Analysis of Security Issues in IoT System, in Cognitive Computing Using Green Technologies: Modeling Techniques and Applications CRC, 147–170 (2021).
Irita, T. & Namerikawa, T. Detection of replay attack on smart grid with code signal and bargaining game. In American Control Conference (ACC) IEEE (2017).
Yao, D. et al. Energy theft detection with energy privacy preservation in the smart grid. IEEE Internet Things J. 6 (5), 7659–7669 (2019).
Kuznetsov, A. et al. Malware correlation monitoring in computer networks of promising smart grids. In IEEE 6th International Conference on Energy Smart Systems (ESS) IEEE (2019).
Abdulaal, M. J. et al. Real-time detection of false readings in smart grid AMI using deep and ensemble learning. IEEE Access. 10, 47541–47556 (2022).
Wang, H. et al. Deep learning-based interval state Estimation of AC smart grids against sparse cyber attacks. IEEE Trans. Ind. Inf. 14 (11), 4766–4778 (2018).
Mohammadi, F. Emerging challenges in smart grid cybersecurity enhancement: A review. Energies 14 (5), 1380 (2021).
Ibrahim, M. S., Dong, W. & Yang, Q. Machine learning driven smart electric power systems: current trends and new perspectives. Appl. Energy. 272, 115237 (2020).
Ahmad, T. et al. Data-driven probabilistic machine learning in sustainable smart energy/smart energy systems: key developments, challenges, and future research opportunities in the context of smart grid paradigm. Renew. Sustain. Energy Rev. 160, 112128 (2022).
Handa, A., Sharma, A. & Shukla, S. K. Machine learning in cybersecurity: A review. Wiley Interdiscipl. Rev. Data Min. Knowl. Discov. 9 (4), e1306 (2019).
Shaukat, K. et al. Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies 13 (10), 2509 (2020).
Halbouni, A. et al. Machine learning and deep learning approaches for cybersecurity: A review. IEEE Access. 10, 19572–19585 (2022).
Berghout, T., Benbouzid, M. & Muyeen, S. Machine learning for cybersecurity in smart grids: A comprehensive review-based study on methods, solutions, and prospects. Int. J. Crit. Infrastruct. Prot. 100547 (2022).
Khattab, A. & Youssry, N. Machine learning for IoT systems. Internet Things Concepts Appl. 105–127 (2020).
Shafiq, M. et al. CorrAUC: A malicious bot-IoT traffic detection method in IoT network using machine-learning techniques. IEEE Internet Things J. 8 (5), 3242–3254 (2020).
Aldaej, A. et al. Smart cybersecurity framework for IoT-empowered drones: machine learning perspective. Sensors 22 (7), 2630 (2022).
Larriva-Novo, X. et al. An IoT-focused intrusion detection system approach based on preprocessing characterization for cybersecurity datasets. Sensors 21 (2), 656 (2021).
Khan, S. et al. Artificial intelligence framework for smart city microgrids: State of the art, challenges, and opportunities. In third international conference on Fog and Mobile Edge Computing (FMEC) IEEE (2018).
Ni, Z. & Paul, S. A multistage game in smart grid security: A reinforcement learning solution. IEEE Trans. Neural Netw. Learn. Syst. 30 (9), 2684–2695 (2019).
Wang, Y. et al. KFRNN: an effective false data injection attack detection in smart grid based on Kalman filter and recurrent neural network. IEEE Internet Things J. 9 (9), 6893–6904 (2021).
Gawade, A., N.M.A.P.U. & PUF Authentication in smart grid. Int. J. Adv. Sci. Technol. 29, 12321–12331 (2020).
Ma, M. et al. Detecting replay attacks in power systems: A data-driven approach. In Advanced Computational Methods in Energy, Power, Electric Vehicles, and Their Integration: International Conference on Life System Modeling and Simulation, LSMS and International Conference on Intelligent Computing for Sustainable Energy and Environment, ICSEE 2017, Nanjing, China, September 22–24, 2017, Proceedings, Part III Springer (2017).
Xiao, H. et al. Application and comparison of metaheuristic and new metamodel based global optimization methods to the optimal operation of active distribution networks. Energies 11 (1), 85 (2018).
Svetec, E. et al. Blockchain application in renewable energy microgrids: an overview of existing technology towards creating climate-resilient and energy independent communities. In 16th international conference on the European Energy Market (EEM) IEEE (2019).
Musleh, A. S., Yao, G. & Muyeen, S. Blockchain applications in smart grid–review and frameworks. IEEE Access. 7, 86746–86757 (2019).
Andoni, M. et al. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sustain. Energy Rev. 100, 143–174 (2019).
Livingston, D. et al. Applying Blockchain Technology To Electric Power Systems (JSTOR, 2018).
Armin, M. et al. Robust extended H ∞ control strategy using linear matrix inequality approach for islanded microgrid. IEEE Access. 8, 135883–135896 (2020).
Khalili, S., Disfani, V. & Ahmadi, M. Impact of Blockchain Technology on Electric Power Grids–A case study in LO3 Energy. arXiv (2021).
Sivén, S. et al. Social and Economic Sustainability from the Perspective of SMEs. (2023).
Gough, M. et al. A Panorama of Applications of Blockchain Technology To Energy, in Blockchain-based Smart Grids (Elsevier, 5–41) (2020).
Spiess-Knafl, W. Artificial Intelligence and Blockchain for Social Impact: Social Business Models and Impact Finance (Taylor & Francis, 2022).
Bekhuis, K. The transition towards a sustainable way of living: an evaluation of the energy system at De Ceuvel. (2018).
Singh, S., Hosen, A. S. & Yoon, B. Blockchain security attacks, challenges, and solutions for the future distributed Iot network. IEEE Access. 9, 13938–13959 (2021).
Kreps, D. M. Microeconomics for Managers (Princeton University Press, 2019).
Von Stackelberg, H. Market Structure and Equilibrium (Springer Science & Business Media, 2010).
Malik, S. A. et al. Towards optimization approaches in smart grid a review. In 2nd International Conference on Computing, Mathematics and Engineering Technologies (iCoMET). IEEE (2019).
Kaveh, M. & Mesgari, M. S. Application of meta-heuristic algorithms for training neural networks and deep learning architectures: A comprehensive review. Neural Process. Lett. 55 (4), 4519–4622 (2023).
Manokaran, J. et al. An efficient anomaly detection system in IoT edge using Chi Square-Improved particle swarm optimization feature selection with ensemble classifiers. Int. J. Comput. Digit. Syst. 16 (1), 1–14 (2024).
Sohail, A. Genetic algorithms in the fields of artificial intelligence and data sciences. Ann. Data Sci. 10 (4), 1007–1018 (2023).
Aslam, S. et al. A survey on deep learning methods for power load and renewable energy forecasting in smart microgrids. Renew. Sustain. Energy Rev. 144, 110992 (2021).
Sharadga, H., Hajimirza, S. & Balog, R. S. Time series forecasting of solar power generation for large-scale photovoltaic plants. Renew. Energy. 150, 797–807 (2020).
Zheng, Z. et al. Meta-heuristic techniques in microgrid management: A survey. Swarm Evol. Comput. 78, 101256 (2023).
Dai, Y. et al. Real-time pricing scheme based on Stackelberg game in smart grid with multiple power retailers. Neurocomputing 260, 149–156 (2017).
Hua, W. et al. Stackelberg game-theoretic model for low carbon energy market scheduling. IET Smart Grid. 3 (1), 31–41 (2020).
Dutta, P. et al. Blockchain technology in supply chain operations: applications, challenges and research opportunities. Transp. Res. E. 142, 102067 (2020).
Sutopo, A. H. Blockchain Programming Smart Contract on Polygon (Topazart, 2023).
Popa, A. B., Stan, I. M. & Rughiniş, R. Instant payment and latent transactions on the Ethereum Blockchain. In 2018 17th RoEduNet Conference: Networking in Education and Research (RoEduNet) IEEE (2018).
Khan, L. U. et al. Metaverse for wireless systems: Architecture, advances, standardization, and open challenges. Internet Things 101121 (2024).
Rivas, A. E. L. & Abrao, T. Faults in smart grid systems: monitoring, detection and classification. Electr. Power Syst. Res. 189, 106602 (2020).
Wu, Y. et al. Hierarchical operation of electric vehicle charging station in smart grid integration applications—An overview. Int. J. Electr. Power Energy Syst. 139, 108005 (2022).
Ma, S., Zhang, H. & Xing, X. Scalability for smart infrastructure system in smart grid: a survey. Wirel. Pers. Commun. 99, 161–184 (2018).
Fotis, G. et al. Scalability and replicability for smart grid innovation projects and the improvement of renewable energy sources exploitation: the FLEXITRANSTORE case. Energies 15 (13), 4519 (2022).
Giannelos, S. et al. Modelling smart grid technologies in optimisation problems for electricity grids. Energies 16 (13), 5088 (2023).
Kim, Y., Hakak, S. & Ghorbani, A. Smart grid security: attacks and defence techniques. IET Smart Grid. 6 (2), 103–123 (2023).
Bhattarai, T. N. et al. Applications of smart grid technology in nepal: status, challenges, and opportunities. Environ. Sci. Pollut. Res. 30 (10), 25452–25476 (2023).
Abdalzaher, M. S. et al. A survey on key management and authentication approaches in smart metering systems. Energies 16 (5), 2355 (2023).
Rajasekaran, A. S., Azees, M. & Al-Turjman, F. A comprehensive survey on security issues in vehicle-to-grid networks. J. Control Decis. 10 (2), 150–159 (2023).
Elrawy, M. F. et al. Detecting and classifying man-in-the-middle attacks in the private area network of smart grids. Sustain. Energy Grids Netw. 36, 101167 (2023).
Rathor, S. K. & Saxena, D. Energy management system for smart grid: an overview and key issues. Int. J. Energy Res. 44 (6), 4067–4109 (2020).
Ghadi, Y. Y. et al. Machine Learning Solution for the Security of Wireless Sensor Network (IEEE Access, 2024).
Azzopardi, E. A. et al. Chromophores in operative surgery: current practice and rationalized development. J. Controlled Release. 249, 123–130 (2017).
Patel, I. et al. Stochastic optimisation and economic analysis of combined high temperature superconducting magnet and hydrogen energy storage system for smart grid applications. Appl. Energy. 341, 121070 (2023).
Lei, S. et al. Radiality constraints for resilient reconfiguration of distribution systems: formulation and application to microgrid formation. IEEE Trans. Smart Grid. 11 (5), 3944–3956 (2020).
Belz, A. et al. Missing information, unresponsive authors, experimental flaws: The impossibility of assessing the reproducibility of previous human evaluations in NLP. arXiv (2023).
Deepa, N. et al. A survey on blockchain for big data: approaches, opportunities, and future directions. Future Gener. Comput. Syst. 131, 209–226 (2022).
Jerbi, W. et al. A blockchain-based storage intelligent. in 2022 International Wireless Communications and Mobile Computing (IWCMC). IEEE (2022).
Ahl, A. et al. Exploring blockchain for the energy transition: opportunities and challenges based on a case study in Japan. Renew. Sustain. Energy Rev. 117, 109488 (2020).
Bodemer, O. The Unseen Guardian: How Blockchain, Java, and AI Stealthily Became the Sherlock Holmes of Cybersecurity (Authorea Preprints, 2023).
Zainab, A. et al. Big data management in smart grids: technologies and challenges. IEEE Access. 9, 73046–73059 (2021).
Pandya, S. et al. Federated learning for smart cities: A comprehensive survey. Sustain. Energy Technol. Assess. 55, 102987 (2023).
Funding
Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2025R845), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Author information
Authors and Affiliations
Contributions
Tehseen Mazhar and Habib Hamam perform the Original Writing Part, Software, and Methodology; Yazeed Yasin Ghadi and Tehseen Mazhar perform Rewriting, investigation, design Methodology, and Conceptualization; Tariq Shahzad, Yazeed Yasin Ghadi and Muhammad Amir khan perform the related work part and manage results and discussions; Tehseen Mazhar Sanwar khan and Muhammad Amir khan perform related work part and manage results and discussion; , Ines Hilali Jaghdam, Tehseen Mazhar and Sanwar khan perform Rewriting, design Methodology, and Visualization; , Habib Hamam, Tariq Shahzad and Ines Hilali Jaghdam performs Rewriting, design Methodology, and Visualization.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Ghadi, Y.Y., Mazhar, T., Shahzad, T. et al. A hybrid AI-Blockchain security framework for smart grids. Sci Rep 15, 20882 (2025). https://doi.org/10.1038/s41598-025-05257-w
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-05257-w
Keywords
This article is cited by
-
Synergizing blockchain and AI to fortify IoT security: a comprehensive review
Artificial Intelligence Review (2026)
-
Energy-efficient graph learning with blockchain–IoT integration for secure smart city energy management
Electrical Engineering (2026)
-
Quantum deep learning-enhanced ethereum blockchain for cloud security: intrusion detection, fraud prevention, and secure data migration
Scientific Reports (2025)