Abstract
This paper investigates a truncated predictive control (TPC) strategy for delayed conic-type nonlinear networked control systems (CNNCSs). The proposed framework addresses key issues such as sensor distortion, system uncertainty, extended dissipativity performance (EDP), and cyber-attacks. Specifically, cyber-attacks are modeled using a Bernoulli distribution, while sensor distortion is represented by a Markov jump system (MJS) model. To handle these challenges, lyapunov stability theory (LST) and linear matrix inequalities (LMIs) are employed to establish sufficient conditions that guarantee global stability of the networked control systems (NCSs). The TPC approach effectively manages the combined effects of nonlinearities, time delays, and network imperfections. By constructing a suitable Lyapunov–Krasovskii functional (LKF) and applying appropriate inequality techniques, the conditions are formulated in an LMI framework. The derived results ensure that CNNCSs maintain desired performance levels under adverse conditions. Finally, two numerical examples are presented to demonstrate the validity and effectiveness of the proposed method.
Similar content being viewed by others
Introduction
The concept of NCSs was introduced in the 1970s, driven by advancements in control technology, computer technology, and network communication. Since the 21st century, NCSs have drawn attention and advanced significantly. Signal transmission between many locations is crucial in many practical systems because it is frequently challenging to have the plant, controller, sensor, and actuator all in one place. These elements are frequently connected via network media in contemporary industrial systems, resulting in the creation of so-called NCSs1,2.
In NCSs, parametric uncertainty and external disturbances pose a significant challenge, making it crucial to address the both. It is particularly difficult to achieve an exact implemented controller that satisfies the needs in real-time operations. Because errors or uncertainties may emerge during the development of controllers. Time delays in control systems can manifest in various forms, such as constant delays, time-varying delays, and infinitely distributed delays3. In many systems, including NCSs, chemical processing, aircraft, underwater exploration, mechanical and electrical engineering, biology, and especially remote control systems, time delays are a common occurrence. This study specifically addresses time-varying delay among the three forms4,5,6.
Many earlier studies were based on the assumption of accurate sensors; however, in practical applications, sensor distortion is common and therefore should not be ignored. In Ref7., sensor distortion was modeled by a Bernoulli distribution. However, assuming a Bernoulli distribution neglects the dependence between sensor distortion occurrences over time. To further address this issue, sensor distortion can be more accurately modeled using approaches such as the MJSs. MJSs have been extensively researched because they may describe systems whose parameters or structures may exhibit abrupt changes, which illustrates many real-world issues with an efficient solution8. For instance9, models network time delay as a Markov process.
Nonlinearities are unavoidable in practice due to disturbances, modeling errors, and limitations in analysis. Nonlinearities remain a key focus in control theory, as many engineering nonlinearities can be represented by forms such as conic-type, Lipschitz, locally sinusoidal, or dead-zone nonlinearities, for instance10,11. Conic-type nonlinear systems have recently gained significant attention as a special class of systems, where the nonlinearity is confined within an n-dimensional hypersphere defined by two linear systems determining its radius and center. Studying conic-type nonlinear NCSs is therefore of practical relevance12.
Network security research has gained popularity in the last few decades. Malevolent adversaries may alter or steal data while it is being transmitted, which could lead to a decline in system performance or even a loss of control as the communication networks are publicly accessible. To enhance the security of the system, cyber-attacks are taken into consideration. Replay attacks, denial-of-service attacks (DoSA) and deception attacks (DA) are the three typical attacks that have been identified and thoroughly examined for NCSs13. The DoSA is to disrupt or stop normal network traffic by overwhelming the servers, infrastructure, and services in the targeted systems14. DA involves the attacker interfering with the system’s regular data using the restricted tampering model, then injecting the tampered data to reduce system performance and undermine stability15. In Ref16., the combination of DoSA with DA is considered for nonlinear NCSs under dynamic event-triggered fault-tolerant control. The network has been enhanced with a few new features, which take the shape depicted in Refs17,18,19,20,21,22..
External disturbances can significantly degrade the performance of control systems. To address this, the concept of EDP was proposed in Ref23. as a means to enhance system stability under such conditions. The EDP encompasses special cases such as \(H_{\infty }, L_2-L_{\infty },\) passivity and \((\mathcal {Q},\mathcal {S},\mathcal {R})\)-dissipativity. The idea of EDP has supported the analysis of stability in various systems, including NCSs that are mean-square asymptotically stable (MSAS) as shown in Ref23., and networked singular systems in Ref24..
Stability analysis of systems with input delay is a central issue in control theory. To manage such delays, prediction-based feedback strategies are introduced to estimate system states across the delay interval for control purposes. Classical methods like the Smith predictor25, finite spectrum assignment26, and model reduction27have contributed foundational solutions. In particular, model reduction through state transformation using a finite integral over the input history allows the original delayed system to be represented in a delay-free form. When disturbances are present, this transformation is adapted to support control design for linear time-invariant systems, as shown in Ref28.. However, despite their conceptual simplicity, predictor-based approaches often involve distributed terms in the feedback law, making them difficult to implement in practice. To avoid the infinite-dimensionality of feedback laws, a finite-dimensional predictor-based method, referred to as the TPC, is introduced.
Various control strategies have been explored for NCSs affected by time delays and cyber attacks. However, TPC for NCSs is still an open problem. In Ref29., TPC is formulated for delayed semi-Markovian jump systems. In Ref30., the TPC is investigated for interconnected time-varying delayed non-linear systems, extending further to Lipschitz nonlinear systems in Ref11. . Furthermore, in Ref31., reinforcement learning-based tracking control is investigated for NCSs under DoSA. In Ref32., truncated predictor feedback effectively compensates for long time-varying input delays. Prior works studied uncertainty and disturbance estimator (UDE) control for time-varying systems33. Although several studies have explored dissipative control and delay-dependent stability in NCS, the combined influence of sensor distortion, system uncertainty, and cyber attacks under a novel TPC has received limited attention. To address this gap, this study develops an extended dissipative control framework for delayed CNNCSs via TPC. In a nutshell, the contributions of our work are outlined below.
-
1.
Contrary to Refs23,34,35., the CNNCSs is designed to account for time-varying delays, uncertainty, sensor distortion, and cyber attacks. Simultaneously, sensor distortion is modeled using an MJS.
-
2.
A novel attempt is made to apply the TPC technique to the proposed system to ensure stability, EDP, and compensation for input delay.
-
3.
The LMI is formulated using the LST method, and the corresponding controller gains are derived to ensure both stability and EDP.
The following are the arrangements for the remaining portions of the paper: In Sect. "Problem Statement", the investigation’s core topic is presented, accompanied by essential definitions and lemmas. Stability analysis and EDP are carried out in Sect. "Main results". Section "Numerical example" presents two numerical simulations with illustrative figures, and Sect. "Conclusion" concludes the study.
Notations
In this paper, \(\mathbb {R}^n\) denotes the n-dimensional Euclidean space. The mathematical expectation is represented by \(\mathbb {E}\). The symbol \(\mathbb {R}_+\) represents the set of all positive real numbers. The superscripts \(``T'',\) and \(``-1''\) indicate the matrix transpose and inverse, respectively. \(``I''\) is the identity matrix with appropriate dimension.
Problem statement
Consider the following nonlinear system with an external disturbance term:
where \(x(t)\in \mathbb {R}^n,~\mathfrak {u}(t)\in \mathbb {R}^m,~y(t)\in \mathbb {R}^l,\) and \({\omega }(t) \in L_2[0, \infty )\) are state, control input, measurement output, and external disturbance vectors, respectively. \(\Gamma (t):\mathbb {R}_+\rightarrow \mathbb {R}\) is a continuously differentiable function representing time-varying delay, intuitively expressed as \(\Gamma (t)=t-\varepsilon (t)\) with \(\varepsilon (t)\ge 0\).
Assumption 1
\(\Gamma (t)\) is a known, continuously differentiable, and invertible function, ensuring \(0<\eta \le \dot{\varepsilon }(t)<\delta\), \(\forall ~t\ge 0\). Given a finite \(\varepsilon _2\ge 0\), \(\varepsilon (t)\) satisfies \(0\le \varepsilon (t)\le {\varepsilon }_2\).
The nonlinearity \(\mathfrak {g}(x(t),{\omega }(t))\) lies within the conic sector described below:
From (1) and (2), the system can be reformulated as follows:
where \(\mathfrak {N_\varpi }={N}_\varpi +\Delta {{N}_\varpi (t)}, \varpi =1,2,3,4.\) The matrices \({N}_\varpi , (\varpi =1,2,3,4),~\mathcal {N}_1,\) and \(\mathcal {N}_3\) are considered known. The uncertain parameters satisfies the following: \(\Delta {{N}_\varpi } (t)= W^{T}\phi (t)\mathcal {J}_{\varpi },~(\)for\(~\varpi =1,2,3,4)\), where \(\phi (t)\) is assumed to satisfy \(\phi^T(t) \phi (t)\le I\), and the matrices \(W,~\mathcal {J}_{\varpi },\) are known. \(\Im (x(t),{\omega }(t))=\mathfrak {g}(x(t),{\omega }(t))-[\mathfrak {N_1}x(t)+\mathfrak {N_3}\omega (t)].\) Alternatively, inequality (2) yields the following expression:
Remark 1
Zames36 initially introduced the conic-type condition (2), which has since been extensively utilized in modeling nonlinear systems. The function \(\Im (x(t),{\omega }(t))\) is typically bounded within an n-dimensional hypersphere centered at a linear system \(\mathfrak {N_1}x(t)+\mathfrak {N_3}\omega (t)\), with radius \(\mathcal {N}_1 x(t)+\mathcal {N}_3 \omega (t)\), which reflects the structure of conic-type nonlinearities.
Remark 2
Under Assumption 1, the delay \(\varepsilon (t)\) is bounded as \(0 \le \varepsilon (t) \le \varepsilon _2\). Thus, the prediction time satisfies \(0\le \Gamma ^{-1}(t)-t \le {\varepsilon }_2.\)
Sensor distortion
Internal and external factors frequently cause sensor distortion in real-world applications, which results in differences between measured and actual data. This problem is taken into account in this research to make the study more realistic.
This work uses the Markov process to model sensor distortion due to its ability to capture sudden changes. When such distortion occurs,
where the sensor’s state signal is \(x_{\mathfrak {s}(t)}\), and \(\psi _{\mathfrak {q}(t)}\) is the distortion parameter with distinct values determined by the Markov process through the random variable \(\mathfrak {q}(t)\).
Consider the Markov process \(\{\mathfrak {q}(t),t \ge 0\}\), which evolves in continuous time and adopts discrete values from a finite set \(\mathbb {V} = \{1,2,...,\mathfrak {a}\}\), uses the following mode transition probabilities:
where \(\pi _{\mathfrak {s}\mathfrak {m}}\ge 0,\forall ~\mathfrak {s},\mathfrak {m}\in \mathbb {V}\) and \(\sum _{\mathfrak {s}=1}^{\mathfrak {a}}\pi _{\mathfrak {s}\mathfrak {m}}=1.\) Then the Markov process has the following transition probability matrix:
TPC design with cyber attacks
Consider the TPC structure as in Ref30.:
where the control gain matrix is K to be determined. In NCSs, data transmission is vulnerable to malicious interference. This study focuses on two prevalent types of network attacks: DA and DoSA. DA compromise communication integrity by injecting false data \(\mathcal {G}(x_\mathfrak {s} (t))\) into the network, effectively replacing the genuine information and disrupting system performance. DA typically arise at random, and this process can be readily described by Bernoulli distribution. It follows that:
where \(\alpha (t)\in \{0,1\}\), with \(\alpha (t)=1\) denoting an active DA and \(\alpha (t)=0\) indicating no DA. It is further assumed that \(\alpha (t)\) satisfies \(\mathbb {E}[\alpha (t)] = \bar{\alpha }\) and \(\mathbb {E}[(\alpha (t) - \bar{\alpha })^2] = \bar{\alpha }(1 - \bar{\alpha })\).
Assumption 2
Reference37 Given a constant matrix \(\mathfrak {S}>0,\) the cyber attack signal \(\mathcal {G}(x_\mathfrak {s} (t))\) satisfies
Remark 3
Assumption 2 imposes a bounded-gain condition on the cyber attack signal \(\mathcal {G}(x_\mathfrak {s} (t))\), ensuring \(\Vert \mathcal {G}^T(x_\mathfrak {s}(t))\Vert \le \Vert x^T(t)\mathfrak {S}\Vert\) with \(\mathfrak {S}> 0.\) This constraint makes the attacker’s effect tractable in stability analysis. In practice, attackers often proactively limit attack energy to avoid detection by an intrusion detection system.
During transmission, the information may be exposed to interference caused by DoSA. In the absence of DoSA, data is transmitted; under attack, it fails to reach the system. The DoSA indicator \(\beta (t)\) equals 0 during an attack and 1 when the system is attack-free. Based on this and (7), we have
Remark 4
The \((n+1)\)-th DoSA’s, dormant and active periods are denoted by \(\mathfrak {D}_{1,n}\) and \(\mathfrak {D}_{2,n}\), with lengths \(\mathfrak {L}_n\) and \(\mathfrak {H}_n\), respectively, where \(n \in \mathbb {N}\) is the attack index. Then the duration of each jamming signal is bounded below and upper by the positive scalars \(\mathfrak {L}_{n}^{\min },\mathfrak {H}_{n}^{\min }\) and \(\mathfrak {L}_{n}^{\max },\mathfrak {H}_{n}^{\max }\) which satisfy \(\mathfrak {L}_{n}^{\min }<\mathfrak {L}_{n}< \mathfrak {L}_{n}^{\max },\mathfrak {H}_{n}^{\min }<\mathfrak {H}_{n}< \mathfrak {H}_{n}^{\max }\). Also, \(\beta (t)\) satisfies \(\mathbb {E}[\beta (t)]=\bar{\beta }.\)
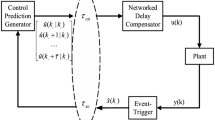
The structure of the formulated problem is depicted in Fig. 1. It provides a clear representation of the system components and their interactions, offering insight into the overall framework.
Assumption 3
Consider matrices \(\Lambda _1, \Lambda _2, \Lambda _3,\) and \(\Lambda _4\) under the following conditions:
-
1.
\(\Lambda _1=\Lambda _1^T \le 0,~\Lambda _3=\Lambda _3^T>0,~\Lambda _4=\Lambda _4^T\ge 0,\)
-
2.
\((\Vert \Lambda _1\Vert +\Vert \Lambda _2\Vert )\Lambda _4=0.\)
Definition 1
Reference23 Given matrices \(\Lambda _1, \Lambda _2, \Lambda _3,\) and \(\Lambda _4\) satisfying Assumption 3, for any \(\bar{T}> 0\) and \(\omega (t) \in L_2[0,\infty ]\), system (10) is said to be EDP if the following inequality holds:
where \(\mathfrak {J}(t)=y^T (t)\Lambda _1 y(t)+2y^T(t)\Lambda _2 \omega (t)+\omega ^T(t)\Lambda _3\omega (t).\)
Remark 5
The EDP covers four main cases. The following matrices are employed:
\(\mathbf {C_1}.~H_{\infty }: \Lambda _1=-I, \Lambda _2=0, \Lambda _3= \nu ^2 I, \Lambda _4=0;\)
\(\mathbf {C_2}.~L_2 - L_{\infty }: \Lambda _1=0, \Lambda _2=0, \Lambda _3= \nu ^2 I, \Lambda _4=0.09I;\)
\(\mathbf {C_3}\). Passivity: \(\Lambda _1=0, \Lambda _2=I, \Lambda _3= \nu I, \Lambda _4=0;\)
\(\mathbf {C_4}.~(\mathcal {Q},\mathcal {S},\mathcal {R})\)-dissipativity: \(\Lambda _1=\mathcal {Q}, \Lambda _2=\mathcal {S}, \Lambda _3= \mathcal {R}-\nu ^2 I, \Lambda _4=0.\)
Lemma 1
Reference38 Given \(\varphi> 0\) and an integral function \(J:[u,v] \rightarrow R^n\), the following inequality holds, if the required integration is adequately defined as
Lemma 2
Reference39 Let \(\mathcal {C}\) be a positive definite matrix. It follows that a scalar \(\sigma \ge 0\) exists for which the subsequent relation is valid
where \(\mathcal {D} = -\mathcal {C}E - E^T\mathcal {C}+ \sigma \mathcal {C}\). Moreover, if \(\mathcal {D}\) is positive definite, it follows that:
Main results
In this section, we analyze system (10) with EDP and derive sufficient conditions for its stability, summarized in the following theorem.
Theorem 1
Given scalars \(\varepsilon _2,~\xi ,~\mu ,~{z}>0\) and matrices \(\mathfrak {S}>0,~\Lambda _1~\Lambda _2,~\Lambda _3,~\Lambda _4\). System (10) is MSAS with \(\mathcal {X}=P^{-1}\) and the controller gain \({K}=-\mathfrak {N}_2^TP\), if positive symmetric matrices \(P,Q_1,Q_2\) exists and meets the following conditions:
where
\(\Theta _{11}=P\mathfrak {N}_1+\mathfrak {N}_1^TP-2(1-\bar{\alpha })\bar{\beta }P^2 \mathfrak {N}_2^2 \psi _{\mathfrak {q}(t)}+\Pi +(1-\bar{\alpha })^4\bar{\beta }^4 \xi ^2 P^2 \psi ^2_{\mathfrak {q}(t)}\) \(+(1-\bar{\alpha })^2\bar{\alpha }^2\bar{\beta }^4 \xi ^2 P^2 \psi ^2_{\mathfrak {q} (t)}+2(1-\bar{\alpha })^2\bar{\beta }^2 \xi ^2 P^2 \psi ^2_{\mathfrak {q} (t)}+\bar{\alpha }^2\bar{\beta }^2 \mathfrak {N}_2^4 P^4+5\mathfrak {S}^T\mathfrak {S}+P^2+4\mathcal {N}_1^2+Q_1+Q_2+2\varepsilon _2^2\xi ^2 e^{2\mu \varepsilon _2}\eta ^{-1}\) \(+2\varepsilon _2^2\xi ^2e^{2\mu \varepsilon _2}\eta ^{-1}\mathfrak {S}\mathfrak {S}^T+2\varepsilon _2^2 e^{\mu \varepsilon _2}\eta ^{-1}\mathcal {N}_1^2-\mathfrak {N}_4\Lambda _1\mathfrak {N}_4^T+P-\mathfrak {N}_4\Lambda _4\mathfrak {N}_4^T,\) \(\Theta _{13}=2zP\mathfrak {N}_1,\Theta _{15}=2zP\mathfrak {N}_1,\Theta _{16}=P\mathfrak {N}_3+\mathfrak {N}_3^T P+8\mathcal {N}_1\mathcal {N}_3+4\varepsilon _2^2 e^{\mu \varepsilon _2} \eta ^{-1}\mathcal {N}_1\mathcal {N}_3-2zP\mathfrak {N}_1-\mathfrak {N}_4\Lambda _2, \Theta _{22}=-Q_1(1-\delta ),\) \(\Theta _{33}=-Q_2-2zP^2 (1-\bar{\alpha })\bar{\beta }\mathfrak {N}_2^2 e^{\mathfrak {N}_1 \varepsilon _2}\psi _{\mathfrak {q} (t)}+z^2 P^4\bar{\alpha }^2\bar{\beta }^2\mathfrak {N}_2^4+z^2P^2,\Theta _{35}=-2zP-2zP^2 (1-\bar{\alpha })\bar{\beta }\mathfrak {N}_2^2 e^{\mathfrak {N}_1\varepsilon _2}\psi _{\mathfrak {q} (t)}+z^2 P^4\bar{\alpha }^2\bar{\beta }^2\mathfrak {N}_2^4,\) \(\Theta _{36}=2zP\mathfrak {N}_3+2zP^2 (1-\bar{\alpha })\bar{\beta }\mathfrak {N}_2^2 e^{\mathfrak {N}_1 \varepsilon _2}\psi _{\mathfrak {q}(t)},\Theta _{44}=-I,\Theta _{55}=-2zP+z^2 P^2,\) \(\Theta _{56}=2zP\mathfrak {N}_3+2z P,\Theta _{66}=4\mathcal {N}_3^2+2\varepsilon _2^2 e^{\mu \varepsilon _2}\eta ^{-1}\mathfrak {N}_3^2+2\varepsilon _2^2 e^{\mu \varepsilon _2}\eta ^{-1}\bar{N}_3-2zP\mathfrak {N}_3+z^2 P^4\bar{\alpha }^2\bar{\beta }^2\mathfrak {N}_2^4+z^2P^2-\Lambda _3,\) \(\tilde{\Theta }_{11}=P\mathfrak {N}_1+\mathfrak {N}_1^TP+\Pi +P^2+\mathcal {N}_1^2+Q_1+Q_2-\mathfrak {N}_4\Lambda _1\mathfrak {N}_4^T+P-\mathfrak {N}_4\Lambda _4\mathfrak {N}_4^T,\) \(\tilde{\Theta }_{14}=P\mathfrak {N}_3+\mathfrak {N}_3^T P+2\mathcal {N}_1 \mathcal {N}_3-2\mathfrak {N}_4\Lambda _2,\tilde{\Theta }_{22}=-Q_1(1-\delta ),\tilde{\Theta }_{33}=-Q_2,\tilde{\Theta }_{44}=-I+\mathcal {N}_3^2.\)
Proof
This theorem covers two cases.
Case 1: Considering the DoSA in sleeping period. Then we construct the LKF as:
Then, applying infinitesimal operator \(\mathcal {L}\) and taking expectation along (14) yields
The analytical solution of the system (3) can be written as
The compact form of (16) is obtained as
where
According to Ref39., for any two vectors \(\mathfrak {h}_1\) and \(\mathfrak {h}_2\), we have
Using this result, we obtain
Similarly, for the other terms
We know that \(K=-\mathfrak {N}_2^TP\). Then, the first term of the right-hand side of (19)–(23) is derived as
With the aid of Lemmas 1 and 2, and relations (11) and (12), the second term on the right-hand side of inequalities (19)–(22) is reformulated as follows:
Using the transformation \(\varrho =\Gamma (\hbar )\), we obtain \(d\hbar =\Bigg (\frac{d}{d\hbar }\Gamma (\hbar )\Bigg |_{\hbar =\Gamma ^{-1}(\varrho )}\Bigg )^{-1}d\varrho .\) Then,
Similarly,
So the Total LKFs are
where
Then the corresponding time derivatives are given by
From system (10) it is observed that
where \(\Xi ^T(t)=[x^T(t)~x^T(t-\varepsilon (t))~x^T(t-\varepsilon _2)~\mathcal {G}^T(x_\mathfrak {s}(t))~\dot{x}^T(t)~w^T(t)]\).
Case 2: Consider the occurrence of DoSA, i.e. \(\bar{\beta }= 0.\) The corresponding LKFs are selected as in (15) and (32). Thus,
Proceeding similarly to Theorem 1, we arrive at the following expression
where \(\tilde{\Xi }^T(t)=[x^T(t)~x^T(t-\varepsilon (t))~x^T(t-\varepsilon _2)~w^T(t)]\).
Combining (40) and (41), we have
where \(\dot{V}(t)\) takes different forms over the domains \(\mathfrak {D}_{1,n}\) and \(\mathfrak {D}_{2,n}\) as given below
Integrating (42) from 0 to \(\bar{T}\), then we have
From Definition 1, \(H_{\infty }\), passivity, and \((\mathcal {Q},\mathcal {S}, \mathcal {R})\)-dissipativity hold for \(\Lambda _4 =0\), while \(L_2-L_{\infty }\) performance applies when \(\Lambda _4>0\). Considering \(\Lambda _4 =0\), we obtain
Accordingly, Definition 1 holds when \(\Lambda _4=0.\) Now, consider \(\Lambda _4>0\) with \(\Lambda _1=\Lambda _2=0\) and \(\Lambda _3>0\) as in Assumption 3. For any \(0\le t\le \bar{T}\) and considering (43), we can obtain \(\mathbb {E}\{\int _{0}^{\bar{T}}\mathfrak {J}(t)dt\}\ge \mathbb {E}\{\int _{0}^{{T}}\mathfrak {J}(t)dt\}\ge \mathbb {E}\{x^T(t)Px(t)\}>0.\) Hence, it follows that:
For both \(\Lambda _4=0\) and \(\Lambda _4>0\), system (10) is asymptotically stable and satisfies the EDP with respect to \(\omega (t)\). Hence, the proof is concluded.\(\square\)
Remark 6
Considering the uncertain parameters \(\Delta N_{\varpi } (t)=0~(\varpi =1,2,3,4)\) with the sleeping period of DoSA \((i.e. \beta =1).\) Then (10) can be written as
Correspondingly, the above system (44) is MSAS, which is carried out via the following Corollary.
Corollary 1
Given scalars \(\varepsilon _2,~\xi ,~\mu ,~{z}>0\) and matrices \(\mathfrak {S}>0,~\Lambda _1~\Lambda _2,~\Lambda _3,~\Lambda _4.\) System (44) is MSAS with \(\mathcal {X}=P^{-1}\) and the controller gain \({K}=-{N}_2^TP\), if positive symmetric matrices \(P,Q_1,Q_2\) exists and meets the following conditions:
where
\(\Omega _{11}=P{N}_1+{N}_1^TP-2(1-\bar{\alpha })\bar{\beta }P^2 {N}_2^2 \psi _{\mathfrak {q}(t)}+\Pi +(1-\bar{\alpha })^4\bar{\beta }^4 \xi ^2 P^2 \psi ^2_{\mathfrak {q}(t)}+(1-\bar{\alpha })^2\bar{\alpha }^2\bar{\beta }^4 \xi ^2 P^2 \psi ^2_{\mathfrak {q} (t)}+2(1-\bar{\alpha })^2\bar{\beta }^2 \xi ^2 P^2 \psi ^2_{\mathfrak {q} (t)}\) \(+\bar{\alpha }^2\bar{\beta }^2 {N}_2^4 P^4+5\mathfrak {S}^T\mathfrak {S}+P^2+4\mathcal {N}_1^2+Q_1+Q_2+2\varepsilon _2^2\xi ^2 e^{2\mu \varepsilon _2}\eta ^{-1}+2\varepsilon _2^2\xi ^2 e^{2\mu \varepsilon _2}\eta ^{-1}\mathfrak {S}\mathfrak {S}^T+2\varepsilon _2^2 e^{\mu \varepsilon _2}\eta ^{-1}\mathcal {N}_1^2-{N}_4\Lambda _1{N}_4^T\) \(+P-{N}_4\Lambda _4 {N}_4^T, \Omega _{13}=2zP {N}_1,\Omega _{15}=2zP {N}_1,\Omega _{16}=P {N}_3+ {N}_3^T P+8\mathcal {N}_1\mathcal {N}_3+4\varepsilon _2^2 e^{\mu \varepsilon _2} \eta ^{-1}\mathcal {N}_1\mathcal {N}_3-2zP {N}_1- {N}_4\Lambda _2,\) \(\Omega _{22}=-Q_1(1-\delta ),\Omega _{33}=-Q_2-2zP^2 (1-\bar{\alpha })\bar{\beta } {N}_2^2 e^{ {N}_1 \varepsilon _2}\psi _{\mathfrak {q} (t)}+z^2 P^4\bar{\alpha }^2\bar{\beta }^2 {N}_2^4+z^2P^2,\Omega _{35}=-2zP-2zP^2 (1-\bar{\alpha })\bar{\beta } {N}_2^2 e^{ {N}_1 \varepsilon _2}\psi _{\mathfrak {q} (t)}\) \(+z^2 P^4\bar{\alpha }^2\bar{\beta }^2 {N}_2^4,\Omega _{36}=2zP {N}_3+2zP^2 (1-\bar{\alpha })\bar{\beta } {N}_2^2 e^{ {N}_1 \varepsilon _2}\psi _{\mathfrak {q}(t)},\) \(\Omega _{44}=-I,\Omega _{55}=-2zP+z^2 P^2,\Omega _{56}=2zP {N}_3+2z P,\Omega _{66}=4\mathcal {N}_3^2+2\varepsilon _2^2\) \(e^{\mu \varepsilon _2}\eta ^{-1} {N}_3^2+2\varepsilon _2^2 e^{\mu \varepsilon _2}\eta ^{-1}\bar{N}_3-2zP {N}_3+z^2 P^4\bar{\alpha }^2\bar{\beta }^2 {N}_2^4+z^2P^2-\Lambda _3.\)
Proof
It is clear that Theorem 1 is true. Then (45) and (46) are easily found to be identical to (11) and (12), respectively. By using (13), we can confirm that \(\Theta <0\) is equivalent to \(\Omega <0,\) with \(\mathcal {X}=P^{-1}\). The system (44) is therefore MSAS, according to Definition 1. Hence, the proof is concluded. \(\square\)
Numerical example
To validate the results, two computational examples are provided in this section.
Example 1
The matrix variables of (10) are considered to be
Furthermore, the matrix associated with (2) are
Case 1: Without DoSA
Let \(\varepsilon _2=0.001,~\eta =0.04,~\xi =0.2,~\mu =0.001,\delta =0.9,~z=6.0600e-05,~\bar{\alpha }=0.1,\) and \(~\bar{\beta }=0.1\). We utilize MATLAB’s LMI Toolbox to solve the LMI formulated in Theorem 1, and the corresponding optimal performance indices for \(H_\infty\) performance, \(L_2-L_\infty\) performance, passivity performance, and \((\mathcal {Q}, \mathcal {S}, \mathcal {R})\)– dissipative performance are simultaneously obtained.
Chaotic behavior of system (10).
\(\mathbf {C_1}.~H_{\infty }\) performance: Let \(\Lambda _1=-I,\Lambda _2=0,\Lambda _3=\nu ^2I,\Lambda _4=0.\) Also, one may derive the performance index as \(\nu =2.17\). Then, the corresponding controller gain is
\(\mathbf {C_2}.~L_2-L_{\infty }\) performance: Let \(\Lambda _1=0,\Lambda _2=0,\Lambda _3=\nu ^2I,\Lambda _4=I.\) Also, one may derive the performance index as \(\nu =2.3247\). Then, the controller gain is derived as
\(\mathbf {C_3}\). Passivity performance: Let \(\Lambda _1=0,\Lambda _2=I,\Lambda _3=\nu ^2I,\Lambda _4=0.\) Also, one may derive the performance index as \(\nu =2.3247\). Then, the LMI solution yields the controller gain as
\(\mathbf {C_4}\). Dissipative performance: Let \(\Lambda _1=\mathcal {Q},\Lambda _2=\mathcal {S},\Lambda _3=\mathcal {R}-\nu ^2I,\Lambda _4=0.\) Also, one may derive the performance index as \(\nu =-5\). The matrices \(\mathcal {Q},\mathcal {S}\) and \(\mathcal {R}\) are given by \(\mathcal {Q}=I,\mathcal {S}=I,\mathcal {R}=\left[ \begin{array}{cc} 0.1 & 0.01 \\ 0.01 & 0.1 \end{array} \right] .\) Then, the corresponding controller gain is obtained as
Case 2: With DoSA
Let the parameter are considering as in case 1 with \(\bar{\beta }=0.\) Then the system (10) is found to be MSAS by using the \(\hbox {MATLAB}^{\circledR }\) LMI tool box. Accordingly, the gain matrices corresponding to the four cases \(\mathbf {C_1-C_4}\) are obtained as follows:
Control input \(\mathfrak {u}(t)\) of system (10).
Let \(\omega (t)=[\frac{22}{(1+0.8*t)^{5}};\frac{23}{(1+0.5*t)^{5}}],~\mathcal {G}(x_{\mathfrak {s}}(t))=[-tanh(0.01x_2(t)); -tanh(0.01x_1(t))],\) are the external disturbance and nonlinear attack functions, respectively. Chaotic behavior of system (10) is shown in Fig. 2. Figures 3, 4, 5 and 6 depict the system’s convergence behavior across the four cases with and without uncertainty under the sleeping period of DoSA. Correspondingly, the state trajectory results without DoSA are presented in Fig. 7. The external and control input dynamics are depicted in Figs. 8 and 9, respectively. Figure 10 shows a Markov model of sensor distortion for the given system. For system (10), Table 1 shows identical upper bounds of \(\varepsilon _2\) with and without uncertainty for various \(\bar{\alpha }\) and \(\bar{\beta }\). Table 2 shows that the proposed method provides a larger upper bound of \(\varepsilon _2\) and achieves superior performance compared to the existing approach. Example 1 considers uncertainty, and the controller gains without uncertainty are listed in Table 3. Clearly, the CNNCS (11) achieves MSAS with EDP under sensor distortion and cyber attacks via TPC.
Remark 7
In a similar manner, when \(\Lambda _1=-\kappa I,\Lambda _2=(1-\kappa )I,\Lambda _3=[(\nu ^2 - \nu )\kappa + \nu ]I,\Lambda _4=0,\) with \(0 \le \kappa \le 1\), the EDP reduces to a mixed \(H_\infty\)/passivity performance. The corresponding performance index can be obtained similarly using Theorem 1.
Example 2
Consider the system (44) with the same parameters as in Example 1. In addition, \(\Delta N_{\varpi } (t)=0~(\varpi =1,2,3,4).\) The LMI presented in Corollary 1 is solved by using LMI \(\hbox {MATLAB}^{\circledR }\) Tool box, and the corresponding optimal performance indices for \(H_\infty\), \(L_2\)–\(L_\infty\), passivity, and \((\mathcal {Q}, \mathcal {S}, \mathcal {R})\)-dissipativity are simultaneously obtained. This yields the follwoing gain matrices for the four cases \(\mathbf {C_1-C_4}\):
Thus, the system (44) is found to be MSAS.
Remark 8
The computational complexity of the proposed algorithm primarily arises from solving the LMIs derived from the LKF conditions. As linear, convex quadratic, and control-related constraints, such as Lyapunov and Riccati inequalities, can be represented as LMIs, they serve as an efficient tool for optimization and control design. In this work, Theorem 1 establishes sufficient LMI-based conditions for the asymptotic stabilization of CNNCSs under EDP and TPC. The computational load mainly depends on the number of decision variables and the size of the LMIs. In the numerical example, feasibility was verified under four cases of EDP, and the desired controller gain was obtained using MATLAB’s LMI Toolbox, which effectively reduces computational burden.
Conclusion
An extended dissipative TPC strategy is proposed for delayed CNNCSs subject to uncertainty, sensor distortion, and cyber attacks. The EDP is addressed in terms of \(H_{\infty }, L_2-L_{\infty },\) passivity and \((\mathcal {Q},\mathcal {S},\mathcal {R})\)-dissipativity. Transmitting the sampled signal over the network introduces vulnerability to cyber attacks, which are represented by a Bernoulli distribution. Simultaneously, sensor distortion is represented using a Markov jump model. By applying LST, sufficient conditions are derived to guarantee system stability along with extended dissipativity, and the corresponding controller gain can be systematically computed. Two numerical examples are provided to validate the proposed approach. Also, the results demonstrate a significant reduction in conservatism compared to existing approaches. Future research can be focused on diverse attack mechanisms in network communication, on extending the analysis to more complex dynamic networks-especially T-S fuzzy-based NCSs-and on practical implementation of the proposed method to further validate its effectiveness and applicability.
Data availability
No datasets were generated or analysed during the current study
References
Tajudeen, M. M., Ali, S., Perumal, R., Ibrahim, T. F. & Alanazi, F. D. Adaptive event-triggered secure control for IT2 fuzzy systems vulnerable to hybrid attacks and its application. J. Franklin Inst. 362, 107365. https://doi.org/10.1016/j.jfranklin.2024.107365 (2025).
Solyman, L., El-Badawy, A. & Meroth, A. Conservation of bandwidth for networked control systems under time delays and packet dropouts using hidden Markov models. Int. J. Dyn. Control 13, 123. https://doi.org/10.1007/s40435-025-01616-7 (2025).
Cao, Y., Jacob, J., Dharani, S. & Sivakumar, M. Improved stability analysis for quaternion-valued neural networks with proportional and mixed time-varying delays. Mathematics and Computers in Simulation. https://doi.org/10.1016/j.matcom.2025.11.005 (2025).
Narenshakthi, T. & Dharani, S. Hybrid-triggered control for uncertain networked control system with time-varying delay and DoS attacks via two-sided looped functional. Complex Anal. Oper. Theory 19, 206. https://doi.org/10.1007/s11785-025-01829-w (2025).
Kaviarasan, B., Kwon, O.-M., Park, M. J. & Sakthivel, R. Stabilization of periodic piecewise time-varying systems with time-varying delay under multiple cyber attacks: An augmented lyapunov functional approach. IEEE Trans. Cybern. 54(8), 4389–4401. https://doi.org/10.1109/TCYB.2023.3311609 (2024).
Pavithra, G. & Dharani, S. Global Mittag-Leffler projective synchronization of distinct fractional-order delayed neural networks with inconsistent orders and interaction terms via integral sliding mode control. Neural Process. Lett. 57, 73. https://doi.org/10.1007/s11063-025-11793-3 (2025).
Gu, Z., Yang, L., Tian, E. & Zhao, H. Event-triggered reliable \(H_\infty\) filter design for networked systems with multiple sensor distortions: A probabilistic partition approach. ISA Trans. 66, 2–9. https://doi.org/10.1016/j.isatra.2016.09.011 (2017).
Wang, S. & Chang, X.-H. Quantized fuzzy \(H_\infty\) control for networked systems with a Markovian sensor distortion under hybrid attacks. Int. J. Comput. Math. https://doi.org/10.1080/00207160.2025.2505024 (2025).
Zhu, X., Zhang, H., Wang, J. & Fang, Z. Robust lateral motion control of electric ground vehicles with random network-induced delays. IEEE Trans. Veh. Technol. 64(11), 4985–4995. https://doi.org/10.1109/TVT.2014.2383402 (2015).
Tajudeen, M. M., Ali, M. S., Thakur, G. K., Priya, B. & Perumal, R. Non-fragile control of discrete-time conic-type nonlinear Markovian jump systems under deception attacks using event-triggered scheme and its application. Math. Comput. Simul. 227, 209–225. https://doi.org/10.1016/j.matcom.2024.08.007 (2025).
Zuo, Z., Lin, Z. & Ding, Z. Truncated predictor control of Lipschitz nonlinear systems with time-varying input delay. IEEE Trans. Autom. Control 62, 5324–5330. https://doi.org/10.1109/TAC.2016.2635021 (2017).
Ali, M. S., Vigneshwar, B., Rajchakit, G., Priya, B. & Thakur, G. K. Event-triggered \(H_{\infty }\) filtering for T-S fuzzy discrete-time conic-type nonlinear networked control systems. Iran. J. Fuzzy Syst. 21, 137–154. https://doi.org/10.22111/ijfs.2024.46459.8184 (2024).
Banu, K. Asmiya., Aparna, T., Tajudeen, M. Mubeen., Rajchakit, G. & Huang, T. \(H_\infty\) control for fractional order neural networks with uncertainties subject to deception attacks via improved memory-event-triggered scheme and its application. Neural Netw. 184, 107092. https://doi.org/10.1016/j.neunet.2023.107092 (2024).
Selva Kumar, V. et al. Adaptive distributed honeypot detection network for enhanced cybersecurity against DoS and DDoS attacks. Results Eng. 26, 105521. https://doi.org/10.1016/j.rineng.2025.105521 (2025).
Xu, Z., Yang, X., Li, X. & Lu, J. Input-to-state stability of switched network control systems under unknown deception attacks. IEEE Trans. Cybern. 54, 5483–5492. https://doi.org/10.1109/TCYB.2024.3376695 (2024).
Xing, S. & Meng, M. Dynamic event-triggered fault-tolerant control of nonlinear networked control systems with parameter uncertainties under dual cyber attacks. In Proc. 14th Asian Control Conference (ASCC), 1–6 (2024).
Wang, M., Shi, L., Liu, R. & Liu, S. Adaptive control of networked control systems under DoS attacks. Syst. Sci. Control Eng. 12, 2409123. https://doi.org/10.1080/21642583.2024.2409123 (2024).
Mahmoud, M. S., Hamdan, M. M. & Baroudi, U. A. Secure control of cyber physical systems subject to stochastic distributed DoS and deception attacks. Int. J. Syst. Sci. 51, 1653–1668. https://doi.org/10.1080/00207721.2020.1772402 (2020).
Chen, Y., Li, Y., He, N. & Cheng, F. Resilient self-triggered model predictive control of cyber-physical systems under two-channel false data injection attacks. J. Dyn. Syst. Meas. Contr. 147, 021004. https://doi.org/10.1115/1.4066316 (2024).
Chen, Y., Zhao, H., Xu, D., Xie, L., Peng, L. & Yu, H. Event-triggered model-free adaptive sliding-mode control for CPSs under DoS attacks. In Proc. 36th Chinese Control and Decision Conference (CCDC), 4528–4533 (2024). https://doi.org/10.1109/CCDC62350.2024.10587586
Sakthivel, R., Santra, S. & Kaviarasan, B. Resilient sampled-data control design for singular networked systems with random missing data. J. Franklin Inst. 355(3), 1040–1072. https://doi.org/10.1016/j.jfranklin.2017.12.011 (2018).
Li, W., Ding, Y. & Liu, H. Pth moment asymptotic stability for stochastic complex networked control systems with Lèvy noise. Int. J. Dyn. Control 12, 4263–4273. https://doi.org/10.1007/s40435-023-01292-5 (2024).
Wang, L., Ge, C., Zhang, R., Zhang, X. & Guo, W. Event-triggered scheme for networked control systems with extended dissipative control and cyber attacks. IEEE Access 10, 134491–134501. https://doi.org/10.1109/ACCESS.2022.3231982 (2022).
Li, M., Xia, J., Zhao, J., Zhang, H. & Shen, H. Event-triggered extended dissipative control for networked singular systems. Int. J. Control Autom. Syst. 19, 382–391. https://doi.org/10.1007/s12555-020-0807-4 (2021).
Smith, O. J. A controller to overcome dead time. ISA J. 6(2), 28–33 (1959).
Manitius, A. W. & Olbrot, A. Finite spectrum assignment problem for systems with delays. IEEE Trans. Autom. Control 24(4), 541–552. https://doi.org/10.1109/TAC.1979.1102124 (1979).
Kwon, W. & Pearson, A. Feedback stabilization of linear systems with delayed control. IEEE Trans. Autom. Control 25(2), 266–269. https://doi.org/10.1109/TAC.1980.1102288 (1980).
Léchappé, V., Moulay, E., Plestan, F., Glumineau, A. & Chriette, A. New predictive scheme for the control of LTI systems with input delay and unknown disturbances. Automatica 52, 179–184. https://doi.org/10.1016/j.automatica.2014.11.003 (2015).
Harshavarthini, S. & Lee, S. M. Truncated predictive tracking control design for semi-Markovian jump systems with time-varying input delays. Appl. Math. Comput. 474, 128686. https://doi.org/10.1016/j.amc.2024.128686 (2024).
Zhang, L., Liu, S. & Hua, C. Truncated predictor stabilization control for interconnected nonlinear systems with time-varying input delay. Nonlinear Dyn. 107, 2421–2428. https://doi.org/10.1007/s11071-021-07001-w (2022).
Liu, J., Dong, Y., Zha, L., Xie, X. & Tian, E. Reinforcement learning-based tracking control for networked control systems with DoS attacks. IEEE Trans. Inf. Forensics Secur. 19, 4188–4197. https://doi.org/10.1109/TIFS.2024.3376250 (2024).
Zhong, Q.-C., Kuperman, A. & Stobart, R. K. Design of UDE-based controllers from their two-degree-of-freedom nature. Int. J. Robust Nonlinear Control 21, 1994–2008. https://doi.org/10.1002/rnc.1674 (2011).
Zhou, B., Lin, Z. & Duan, G. Truncated predictor feedback for linear systems with long time-varying input delays. Automatica 48, 2387–2399. https://doi.org/10.1016/j.automatica.2012.06.032 (2012).
Narenshakthi, T. & Dharani, S. Truncated predictive control for delayed networked control systems under dual attacks. Int. J. Dyn. Control 13, 378. https://doi.org/10.1007/s40435-025-01882-5 (2025).
Gao, H. & Chen, T. Network-based \(H_\infty\) output tracking control. IEEE Trans. Autom. Control 53, 655–667. https://doi.org/10.1109/TAC.2008.919850 (2008).
Zames, G. On the input-output stability of time-varying nonlinear feedback systems Part one: Conditions derived using concepts of loop gain, conicity, and positivity. IEEE Trans. Autom. Control 11, 228–238. https://doi.org/10.1109/TAC.1966.1098316 (1966).
Zhi, Y.-L., Liu, X., He, S., Lin, W. & Chen, W. Adaptively event-triggered \(H_\infty\) control for networked autonomous aerial vehicles control systems under deception attacks. IEEE Trans. Industr. Inf. 21, 3458–3465. https://doi.org/10.1109/TII.2025.3528560 (2025).
Sakthivel, R., Santra, S., Kaviarasan, B. & Venkatanareshbabu, K. Dissipative analysis for network-based singular systems with non-fragile controller and event-triggered sampling scheme. J. Franklin Inst. 354, 4739–4761. https://doi.org/10.1016/j.jfranklin.2017.05.026 (2017).
Anusuya, S., Sakthivel, R., Mohammadzadeh, A. & Kwon, O. M. Truncated predictive control for delayed cyber-physical systems under deception attacks. J. Franklin Inst. 362, 107361. https://doi.org/10.1016/j.jfranklin.2024.107361 (2025).
Liu, D. & Yang, G.-H. Robust event-triggered control for networked control systems. Inf. Sci. 459, 186–197. https://doi.org/10.1016/j.ins.2018.02.057 (2018).
Funding
Open access funding provided by Vellore Institute of Technology.
Author information
Authors and Affiliations
Contributions
Mr. T. Narenshakthi developed and performed the calculations, analyzed and wrote the manuscript text and Dr. S. Dharani reviewed the manuscript, contributed in preparation of simulation results and supervised the work.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Narenshakthi, T., Dharani, S. Extended dissipative truncated predictive control strategy for conic-type delayed networked control systems affected by cyber attacks and sensor distortion. Sci Rep 16, 1238 (2026). https://doi.org/10.1038/s41598-025-30817-5
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-30817-5