Abstract
Data security during transmission over public networks has become a key concern in an era of rapid digitization. Image data is especially vulnerable since it can be stored or transferred using public cloud services, making it open to illegal access, breaches, and eavesdropping. This work suggests a novel way to integrate blockchain technology with a Chaotic Tent map encryption scheme in order to overcome these issues. The outcome is a Blockchain driven Chaotic Tent Map Encryption Scheme (BCTMES) for secure picture transactions. The idea behind this strategy is to ensure an extra degree of security by fusing the distributed and immutable properties of blockchain technology with the intricate encryption offered by chaotic maps. To ensure that the image is transformed into a cipher form that is resistant to several types of attacks, the proposed BCTMES first encrypts it using the Chaotic Tent map encryption technique. The accompanying signed document is safely kept on the blockchain, and this encrypted image is subsequently uploaded to the cloud. The integrity and authenticity of the image are confirmed upon retrieval by utilizing blockchain’s consensus mechanism, adding another layer of security against manipulation. Comprehensive performance evaluations show that BCTMES provides notable enhancements in important security parameters, such as entropy, correlation coefficient, key sensitivity, peak signal-to-noise ratio (PSNR), unified average changing intensity (UACI), and number of pixels change rate (NPCR). In addition to providing good defense against brute-force attacks, the high key size of \({10}^{72}\) further strengthens the system’s resilience. To sum up, the BCTMES effectively addresses a number of prevalent risks to picture security and offers a complete solution that may be implemented in cloud-based settings where data integrity and privacy are crucial. This work suggests a promising path for further investigation and practical uses in secure image transmission.
Similar content being viewed by others
Introduction
The Internet has transformed many facets of society, including virtual worlds, and it has both beneficial and detrimental effects on crime. Experts have presented distributed computing, a new development in internet-dependent apps, to make the Web safer and more reliable1. For this, another innovation called as distributed computing has been presented.
The idea of organization-dependent registering started in the mid-1960s, albeit countless trust the expression “distributed computing” was earliest utilized in quite a while similar significance. Eric Schmidt who was the President of Google presented it on the industrial get-together dated to 9 August, 20062,3.
Distributed computations have filled fundamentally in modern innovation, like International Business Machines (IBM), Amazon, Oracle, and Apple4,5,6. It is generally utilized for the telehealth business too. Telehealth is a quickly developing field where in clinical consideration is given to sufferers who aren’t truly accessible at a similar spot as the doctor7.
Besides, safe web trades of patient clinical data including clinical outputs are turning out to be more far-reaching. Since therapeutic information is normally accessible in a perceivable way it should be strongly safeguarded. Therefore, a convoluted clinical framework needs skills equipped for gathering clinical reports in a design that permits approved clients to get to them from any location8,9. Obviously, clinical information is developing constantly and we really want to protect it for some time later. To appropriately deal with such a mind-boggling and immense measure of information fundamentally explicit innovations for example a dispersed information organization, versatile capacity, equal processing, frameworks, frameworks, etc. are essential. Since distributed computing depends on help-situated engineering it can deal with these complicated issues in a virtualized climate at a negligible cost10,11.
Moreover, public services, data access management, integrity control, individuality, and risk management give rise to security concerns in cloud computing. By verifying the sender’s identity, individual emails and phone numbers can be shielded from access by hackers seeking to obtain information12. Although there are certain limitations several solutions have been employed to address the privacy and security issues with cloud communication. The primary concern related to cloud computing is the security of sensitive data which makes it necessary to address the cloud computing defense issue. The current conventional system has greatly improved to provide safety measures in the healthcare sector but the costs are higher and more computational resources are used in the interim13.
It is crucial to preserve medical photographs while maintaining their dependability because of this. The guarantee that unauthorized parties won’t alter medical images is known as data integrity. An unauthorized operator can alter medical images. A mistaken disease diagnosis will result from the data manipulation or erosion in the image. Hence, a trustworthy and robust method for securely sending sensitive medical information across open channels is needed14.
To prevent anyone from seeing the data not even the cloud server we must first encrypt it before transferring it to a cloud server. Conventional cryptosystems, such as Data Encryption Standard (DES)15 and Advanced Encryption Standard (AES)16 require a lot of processing power and take a long time to finish making them inappropriate for fast image encryption.
While employing chaotic mappings to send encrypted data over public networks additional security measures such as data authentication and data integrity are required to ensure that the decrypted picture and the original image are identical to the recipient. This concept suggests using blockchain technology to allay these worries. Numerous stakeholders including those in the real estate, banking, healthcare, infrastructure, and government sectors have expressed interest in blockchain technology17,18.
It will be effective and secure to accumulate and manage electronic health data using blockchain. When cloud storage and blockchain technology are combined to accumulate medical data, premium services can be provided at affordable prices10. The blockchain technology is not dependent on a centralized reliable third party for its services. Since the network is decentralized there is not any chance of failure. There would be sufficient redundancy to maintain web functionality even if one or more nodes fail19.
In an effort to improve picture transmission security, Wen et al.20 introduced Quantum Chaotic Map and De-oxyribo Nucleic Acid (DNA) Coding Image Encryption Algorithm (QCMDC-IEA), an image encryption technique that combines DNA coding with quantum chaotic mapping. The algorithm is susceptible to chosen-plaintext attacks due to serious security vulnerabilities, such as the availability of an equivalent key and a lack of confusion and diffusion in the DNA domain encryption.
Through theoretical analysis and actual results, Wen et al.21 demonstrate the vulnerabilities of the Improved Color Image Cipher De-oxyribo Nucleic Acid (ICIC-DNA) and offer a chosen-plaintext attack method that effectively targets it. This technique draws attention to the weaknesses in the encryption procedure, specifically in the domain and DNA-base permutation encryption. The main drawback of the study is that it exposes a number of critical security holes in ICIC-DNA, including the separation of encryption sequences from plaintext and the simplification of many DNA processes, which can jeopardize the overall security of the cipher.
A new picture encryption technique depend on the Feistel Network and Dynamic DNA encoding is thoroughly analyzed by Feng et al.22, who also pinpoint important issues with the scheme’s security and effectiveness. Through simulated experiments, it demonstrates the effectiveness of the chosen plaintext attack algorithm and suggests necessary modifications. The study identifies important flaws in the secret key design, such as ambiguous descriptions and excessively long key lengths, which jeopardize the security and viability of the encryption.
The remaining of the research article is systematized as follows: The scheme’s associated works are shown in the Related Literature in “Related literature” section. Preliminaries in mathematics are covered in “Mathematical preliminaries” section. The suggested BCTES and its encryption/decryption procedure are presented in the “Suggested blockchain architecture for chaotic tent map medical image encryption scheme (BCTMES)” section, titled Suggested Blockchain Architecture for Chaotic Tent Map Medical Image Encryption Scheme (BCTMES). “Proposed model of personification origination and identification” section contains the proposed model of Personification Origination and Identification along with its suggested model. “Image encryption technique” section comprises of Image Encryption Technique along with the implementation of Algorithm. Comparative Results and Performance Evaluation are covered in “Comparative results and performance evaluation” section. Statistical Analysis is carried out in “Expertise reporting” section. “Security analysis” section will cover the Conclusion along with the Future work.
Previous frameworks include blockchain-based data transactions and image encryption in cloud environments. This project combines the two ideas because we desire a system that allows us to exchange private information such as medical photographs securely and globally. To achieve this our suggested plan offers the following benefits.
-
I.
We use the model that is provided in23. This model is updated using our newly suggested encryption technique to improve security. Better outcomes and performance are demonstrated by this newly suggested encryption strategy.
-
II.
The disorderly foundation Tent map employs three separate keys along with big key size, unpredictability, and high complexity in the Tent map using a Circulant key matrix encryption system. It prevents unauthorized individuals from accessing authentic medical images.
-
III.
By employing blockchain technology, the BCTMES verifies medical data and safeguards private health information. Data integrity and privacy have both increased as a result.
-
IV.
The introduction of cloud servers and blockchain infrastructure is designed to ensure the validity and truthfulness of medical picture statistics. After an image is confirmed by the blockchain data users may easily verify it. Finally, the blockchain accumulates all Images and signed papers.
Related literature
An efficient honeypot solution for protecting documents in cloud computation was presented by Mondal and Goswami24. Initially, unwanted missing values are replaced and removed from the collection using a normalization process. After that, the attack types are predicted and categorized by the Convolution Neural Network (CNN) classifier and the Gray Level Co-Occurrence Matrix (GLCM) quality selection algorithm25. The data in this strategy is encrypted using the honeypot cryptography technique. Together with the operator for authentication, the Cloud Server (CS) is in charge of key creation and verification. Subsequently, the cloud server receives the request from the data sender. Afterwards, when the user enters the key, the information is decrypted using the honeypot technique. This provides important security but at a high cost.
Ali et al. in their study presented an encryption method for healthcare data based on a Logistic tent map and Henon chaotic map26. Utilizing the public key of the medical center the operator generates a private encryption key in this encryption method. Next, a private key is used to encrypt medical images using the suggested chaos-based encryption technique. Afterward along with the authentication criteria and digital signature the operator digitally signs the encrypted image and forwards it to the managers. Ultimately the healthcare company creates the secret key and shares it by combining it with a digital signature, a secret key, and a cipher image. The image is then decrypted using that secret key by the authority who subsequently verifies its authorization by using an authenticating factor.
An advanced cloud-dependent solution for rural health accounts is proposed by Padhy et al.27 which offers rural populations low-cost services. They proposed a cloud-dependent architecture for storing data that offers access to the physicians and researchers to the latest personal information for the betterment of healthcare services and remote ailment diagnosis.
The secure Blockchain-based Chaotic Deep Generative Adversarial Network Encryption (BCDGANE) paradigm which is founded on blockchain technology is proposed by Neela and Kavitha23. In this architecture after utilizing Chaotic Deep Generative Adversarial Network (GAN) for encryption medical records are stored in the cloud server. It produces a private key after then the diffusion and confusion processes take place. The generated private key is then used by the XOR method to decrypt the image. Next, the sender uses the hash function to digitally sign the encrypted picture upload it to the cloud, and store it in a blockchain. The authenticity of the ciphertext image can then be confirmed using the digital signature. Experimental results and security investigations indicate that suggested Chaotic Deep GAN technique has unpredictability, a huge key size, and is especially vulnerable to moderation.
The Hopfield Neural Network Images Encryption Scheme (HNNIES) was first presented by Lakshmi et al.28 for Medical Image (MI) cloud storage. There are five phases in this structure. The underlying stage shows how a recursive neural network is used to generate flexible keys. The stage then displays a picture of an explicit and erratic arrangement created with Hopfield Neural Network (HNN). Phases 3 and 4 consequently feature separate arrangements for the diffusion and confusion measures. Lastly, it illustrates how the cloud and cryptography function together.
A cloud-dependent platform for exchanging medical data MeDShare29 is powered by blockchain technology. The system’s creators used smart contracts along with authentication and permission on a different platform for data access. MeDShare can securely achieve and preserve record accountability and authenticity when moving healthcare data between cloud structures. A powerful cloud-dependent verification solution called Provchain30 seeks to address privacy concerns and boost availability. This method is entirely decentralized and uses blockchain technology in cloud computing to provide tamper-proof access.
Biplane and chaotic picture encryption were created by Afzal et al.31 to safeguard medical photos stored on cloud storage. Initially, the medical images were converted to cipher using a biplane along with chaotic encryption (BCE). Two keys that were produced by the logistic map and a linear feedback shift register are combined to make the chaotic key sequence. The process is finally used to takeout the plain MI from the computerized system once the encrypted image has been successfully retrieved from it. There is a high computational cost associated with this method.
To increase security and efficiency Shamsa et al.32 presented an innovative public key encryption strategy that leverages the conjugacy search issue and automorphisms which is based upon general linear groups and groupings. A novel digital signature and public key cryptosystem based on non-commutative algebraic structures suggested by Shamsa et al.33 in which security of the system is based on the difficulty of polynomial symmetric decomposition issues and matrix discrete logarithm problems.
Addressing the problem of creating a strong and IE process by applying chaotic maps and color codes for permutation, substitution, and diffusion Shamsa et al.34 offer a unique three-phase image encryption method.
Shamsa et al.35 offer a novel method of encrypting images that makes use of circulant matrices, sine maps, and chaotic tent maps. They perform several security and statistical tests to show that the algorithm is safe and reliable.
Shamsa et al.36 demonstrate the effectiveness of the new picture encryption method by putting it through a series of security tests and utilizing an orthogonal matrix and chaotic maps in a Substitution technique.
Shamsa et al.37 suggest using the Blockchain-based Chaotic Arnold’s Cat Map Encryption Scheme (BCAES) to safely transmit and store medical photos in a cloud setting while guaranteeing the data’s authenticity, secrecy, and integrity.
A unique algorithm called Cross-Channel Color picture Image Encryption (CCC-IE) is presented by Feyza et al.38. It uses sophisticated techniques like bi-directional sequential diffusion and diagonal permutation to improve picture security and make it much more resistant to different types of attacks.
The Modular Integrated Logistic Exponential (MILE) map, a new 1- Dimensional (1D) chaotic map presented by Kocak et al.39, solves predictability problems and parameter range limitations in previous chaotic maps. The image encryption (IE) system utilizes the Particle Swarm Optimization (PSO) algorithm, which improves the security and efficiency of the encryption process. Although optimization techniques help IE schemes, their applicability may be limited by the particular algorithm employed and the parameters selected.
By using adaptive embedding and parallel compressive sensing techniques, Feng et al.40 created a unique picture encryption algorithm that improves image data security without sacrificing visual quality.
Using dynamic DNA-level two-way diffusion and non-adjacent parallelable permutation, Li et al.41 present a unique image encryption system that improves the security of image data against privacy breaches and illegal access. The study shows that the suggested approach can be used in real-world applications with great success in lowering correlation coefficients (CC) post-encryption; however, it does not address possible computational difficulties or performance issues that may develop.
The Image Encryption Algorithm -Image Filtering-Discrete Logarithmic Transformation (IEA-IF-DLT) is an image encryption algorithm proposed by Feng et al.42. It improves security by utilizing three rounds of 3-Dimensional (3D) chaotic image superposition, solving weaknesses in conventional techniques that depend on pixel-by-pixel superimposing. Although the suggested approach increases security, it can still have difficulties fending off sophisticated attacks because the implementation and surrounding conditions can affect how effective chaotic systems are.
A latest fractional-order 3D Lorenz chaotic system and a 2-Dimensional (2D) Sinusoidally Constrained Polynomial Hyper-Chaotic Map (2D-SCPM) are presented by Feng et al.40. Due to their distinct dynamical features and bigger key space which are essential for strong encryption these systems increase the difficulty and security of image encryption. Further studies are required to assess its resilience to different cryptanalytic methods and make sure it can survive new risks in the picture encryption space.
A new Image Encryption (IE) technique named Image Encryption Algorithm Pixel Fusion Strategy (IEASP), which makes use of 2-Dimensional Sinusoidally Quadratic Polynomial Map (2D-SQPM) and a pixel fusion method, was proposed by Feng et al.43. The two primary components of the technique are the encryption process, which involves pixel fusion and chaotic pixel superposition, and initialization, which involves creating a shared keystream. Random noise is provided to increase security and fend off plaintext assaults. Table 1 gives a comparative analysis of some studies with our proposed work.
Mathematical preliminaries
Our suggested encryption scheme utilizes the following mathematical foundations which prove to be a unique in the implementation of the encryption process. The Sine Map, the Prime Circulant Matrix, and the Chaotic Tent Map are very sensitive to the initial conditions. A minor change in the initial conditions greatly influences the outcomes. Real-time picture encryption and resource-constrained contexts benefit greatly from the simplicity and computational efficiency of classical maps, including the Tent map and Sine map. Their well-defined chaotic behavior ensures unpredictability in encryption keys, and they have demonstrated security in cryptographic applications. Classical maps are simpler to use and evaluate in practical situations because they strike a compromise between performance and complexity.
Sine map
Mathematical expression for Sine Map is demarcated as follows44:
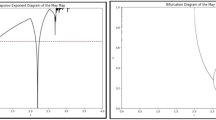
possesses several useful properties including uniform thickness work, arbitrary conduct, and Lyapunov type. For this reason, a Sine map is thought to be a good option for use in cryptography. Figure 1 displays Sine Map bifurcation illustration.
Prime circulant matrix
A circulant matrix represents a matrix having an equal number of rows and columns in which each column vector is shifted relative to the preceding line vector from one component to the next one. Every element in the circulant vector is prime if its general coefficient of determination (gcd) is 1. For instance, the \(4\times 4\) Square matrix having a circulant matrix with circulant vector \((\text{2,3},\text{5,11})\) is prime circulant when the \(\text{gcd }(\text{2,3},\text{5,11}) = 1\).
Chaotic tent map
The 3rd cycle is finished by combining a CTM45 with an Exclusive-OR operation to change their pixel value. As a result, even tiny adjustments made to the original image cause the pixel frequency of the jumbled snip to remarkably change. In literature chaotic tent map that is described and characterized as follows creates an irregular arrangement to accomplish this target.
where the system parameter \(\upsilon\)’s range is \([0, 4]\). Figure 2 presents a Chaotic Tent Map bifurcation illustration. Its range of chaos is \(\upsilon \epsilon [\text{2,4}]\).
Suggested blockchain architecture for chaotic tent map medical image encryption scheme (BCTMES)
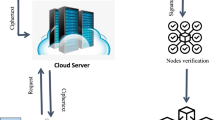
Data Dispatcher, Cloud Server, Data Operator, Blockchain, and encryption \(\&\) decryption procedure are the five main parts of the BCTMES. The BCTMES system architecture is displayed in Fig. 3. First, the data dispatcher digitally signs and encodes the medical photographs using the SHA-256 hash algorithm. Next, the dispatcher will encipher the healthcare image using the algorithm outlined in “Proposed model of personification origination and identification” section Image encryption algorithm. The enciphered photo will be deposited on a CS and the signed paper will be preserved on blockchain technology. When the operator requires the MI, he will have to apply for ciphertext to the cloud server. The necessary encrypted file will subsequently be passed on to the operator by the CS. Once the cipher image is obtained the operator will utilize the Chaotic Tent Map (CTM) decryption approach as shown in Algorithm 4 to decode it. To confirm the authenticity and integrity of the picture the data user will now submit the plain image to the blockchain which will check it and provide a confirmation note in the form of a yes or no. The following is a list of the main elements of our suggested model. Figure 3 elaborates on the Proposed Model of BCTMES.
-
i.
Data Dispatcher Before transferring the returned data to Cloud Solution Provider (CSP), the data dispatcher who could be a patient encrypts the healthcare pictures using the CTM encryption technique. After that the data sender signs and stores the encrypted photo on the blockchain web.
-
ii.
Cloud Server The cloud server is driven by two goals:
-
(a)
The first is to store vast volumes of healthcare picture records.
-
(b)
The second is to respond to an operator’s request for data by locating and transmitting the relevant ciphertext.
-
(a)
-
iii.
Data Operator The data operator (health professionals) asks the CS for the medical records to receive the encrypted image. In addition, the users cross-reference the encrypted identity stored on the blockchain to confirm its legitimacy.
-
iv.
Blockchain We generated an image hash value using the SHA-1 technique to construct a digital signature. The blockchain verifies the embedded signature to verify the authenticity of the ciphertext when the data operator applies for a confirmation check. It returns 1 if it is true and 0 otherwise.
-
v.
Encryption \(\&\) Decryption Process Before being transferred to the cloud server the healthcare image is first converted to a cipher image using a Chaotic Tent Map (CTM) with a Prime Circulant key matrix and Sine Map. The decryption procedure is the inverse of the encryption procedure.
Proposed model of personification origination and identification
Personification origination
Following the completion of the encryption process, the dispatcher forwarded the encrypted healthcare data to the CS which utilizes a hashing method to add the hash value of the healthcare image to the blockchain. This could be carried out for the purposes of validity and ciphertext integrity. We will utilize SHA-256 in our proposed technique to generate a hash value of the cipher image prohibiting intruders from obtaining the picture since hash functions are uni-directional functions. Hence that is not possible to recover the hash value to access the original medical image33.
Personification identification
The user then verifies the signature that has been added to the blockchain to guarantee that the cipher is authentic afterwards the cipher image is uploaded to the blockchain by the data user. The original image that data sender uploaded on the blockchain will be compared to the hash outcome of the image that the blockchain used SHA-256 to decipher. The data is authentic if it matches if not it does not. The blockchain will notify the data user via a yes or no verification message if the data is valid or not. Figure 4 shows the Proposed Model of Personification Orientation and Identification.
The uniqueness property of SHA-256 hash functions guarantees irreversible, deterministic, and non-collision outputs, ensuring data integrity and authenticity. In the suggested technique, the uniqueness of SHA-256 allows secure verification of healthcare data by comparing hash values and validating ciphertext authenticity. Any alteration to the ciphered image will result in a different hash value, providing a robust security technique for healthcare data transmission and storage. Further, the performance analysis of the “Blockchain-Driven Medical Image Encryption” stands out for its thorough approach, employing various security measures like histogram analysis, entropy, and differential techniques (UACI and NPCR) to test resilience against attacks. With a key space size of \({10}^{72}\), the encryption method is highly resistant to brute-force attacks, and key sensitivity ensures unpredictability. Visual representations, such as bar graphs, highlight its superiority over other systems. Overall, the encryption scheme demonstrates robust security, making it highly effective for practical applications in medical image encryption.
Image encryption technique
This section describes how to create a symmetric encryption method using Sine map (1) and CTM (2). The suggested method creates a sequence for permutation using a sine map. Prime circulant matrices are utilized in the substitution process. Lastly, a bit of XOR is used in conjunction with CTM (2) to produce the jumbled image. Figure 5 shows the Workflow of Encryption Algorithms.
Selection of control settings and creation of keys
The following three hidden keys and related control settings can be chosen for the enciphering of the picture that contains pixels \(r\times c\).
1st hidden key for performing permutation is \(J=\left({w}_{o},\alpha \right)\) here \({w}_{o}\) is an incentive cost of the sequence created with Sine map and the control settings \(\alpha \epsilon (0,\left.1\right]\) utilized. For performing a substitution, the 2nd key \(\overline{J} = \left( {\acute{b},b_{1} ,b_{2} ,b_{3} } \right)\) is obtained by selecting four arbitrary integers \(b,\acute{b}_{1} ,b_{2} ,b_{3} \epsilon \left[ {0,255} \right]\) where \(\acute{b}_{1} ,b_{2} ,b_{3}\) are materialized to make a prime circulant square matrix.
CTM (2) repeatedly calculated \(r\times c\) times utilizing 3rd key \(\overline{\overline{J}} = \left( {X_{O} ,\upsilon } \right)\) with starting value \({X}_{O}\) And the control setting \(\upsilon\). For the execution process, the values of keys are pre-defined as \(J=\left(\text{0.99,0},79\right)\), \(\overline{J} = \left( {123,6,24,11} \right)\) and \(\overline{\overline{J}} = \left( {0.66,3,78} \right)\).
Permutation technique
This phase involves a Sine map to alter the picture pixel placement of the taken image. Chaotic sequence is formulated by iterating the sine map and arranging the resulting terms in increasing manner. Comparing the positions of the chaotic and disordered sequences determine the transformation sequence. The pixels in the original image (OI) are permuted using this permutation sequence. The first algorithm provides the pixel permutation.
Substitution technique
The 2nd hidden key \(\overline{j }\) Is used to execute the substitution on the pixel of the permuted image. Components \({b}_{1}, {b}_{2}, {b}_{3}\) of \(\overline{j }\) Are used to create a prime circulant matrix.
Diffusion technique
Diffusion is produced by using the third key \(\overline{\overline{j}}\). CTM (2) and \(\overline{\overline{j}}\) Help to generate a unique sequence that then transforms into a numerical arrangement. The encryption image is generated by bitwise XORing this integer sequence in combination with the output of the substitution method.
Decoding techniques
The process of the encoding technique is reversed in the decoding technique. The jumbled image can be decoded using the secret keys \(J\), \(\overline{J }\) and \(\overline{\overline{J}}\) Following the opposite encryption operations.
Comparative results and performance evaluation
The trials were conducted on desktop PC fortified with an Intel(R) Core (TM) i7-6700 @ 3.40 GHz CPU, running UBUNTU 16.04. The MATLAB 2018a is used to run the simulation. Utilizing the Geth Ethereum client we take a private blockchain and simulate the proposed system. Researchers and developers have examined the performance of Ethereum a well-known blockchain technology. Table 2 provides a list of the applications used for execution.
Because the trial photos depict three distinct anatomical regions, they are taken from the BraTS18 dataset34, Ultrasonic Brachial Plexus dataset35, and Montgomery Country Chest X-rat dataset 3646. The length (256 × 256) pixel values are applied to the sample photos. After the encryption procedure, we are left with an encoded image that is 256 × 256 in size. Applying a decryption technique results in both the plain and the encoded data. The image is reconstructed using the following techniques: pixel dispersion by Chaotic tent map, pixel substitution utilizing with Prime Circulant key matrix, and pixel permutation by Sine map. The results of our recommended encryption technique are shown in Table 3.
Evaluating extensive experiment using color images
Our new image encryption method addresses scalability, computational efficiency, and security. Experimentation with different image sizes and types ensures excellent security and performance. Comparative research with recent encryption techniques will assess the method’s advantages, identify areas for development, and compare it to other methods in terms of encryption strength, attack resistance, and processing demands. We test photos in our investigations with MATLAB 2018a. We obtain pictures from University of Southern California- Signal and Image Processing Institute (USC-SIPI). Table 4 shows the experimental results of images of different sizes.
Expertise reporting
A set of statistical analyses on the developed procedures is started to evaluate the dependability of the proposed encryption scheme. This section contains the detailed results.
Histogram analysis
The Red, Green, and blue portions of the encrypted picture histogram are displayed in Table 5. The graphic below illustrates how generally consistent the encrypted image histograms are. An initial image has no information about the movement of its pixels.
Table 6 displays the relationship values for the authentic and encoded result in the diagonal, vertical, and horizontal standards.
Entropy analysis
Information entropy is the primary qualitative requirement for image arbitration44. Formula (3) is used to determine the data entropy through data entropy assessment to calculate the coded image’s irregularity.
where \(Q\left({F}_{i}\right)\) Represents probability that indicate character will appear in the decoded image and \(F\) is the encrypted image. The encrypted image and original image cannot be distinguished from one another so that the photo encryption method to be considered secure. There are some possibilities for predicting an original image by the entropy value of the encrypted image. An attacker can crack the snip when the value gets near to 8. The encrypted image’s entropy value which was obtained using the developed encryption scheme has 7.9990 by applying MATLAB R2018a. The results presented in Table 7 show that updated data entropy value is nearer to the standard value of 8 and sufficient which ensures that no information would be omitted from the process. Figure 6 elaborates the Data Entropy Values Comparison outcomes of our proposed algorithm as compared to the existing schemes with the help of line graph representation by considering entropy values of blood image, brain image, and chest x-ray image respectively. From graphical analysis, we can easily infer that the blood image represented by blue color has shown the highest level of entropy.
Differential analysis
While employing a certified encryption method one should exercise extra caution while making small changes to the hidden key44. An algorithm that is considered valid must be highly sensitive to its secret key that implies even a little change in the hidden key should produce fully different code outputs.
Additionally, with a slightly change original key, the method would be disabled to extract a few samples from the original image or decrypt a coded image. With the utilization of the present approach, a small change made with any element of the key could produce a completely different or valid result for the encoded calculation. The result of decoding our plan will change if you make a minor change with any three specific keys. That illustrates that adding \(0.798079790000001\) to any key will make it impossible for us to decode and recover the original image.
In the world of cryptanalysis plain-text affectability evaluation is also known as differential research. We employ the combination of typical developing force of contrast (UACI) between the plain and cipher picture. The net pixel transformation rate (NPCR) for the original image swap of a single pixel value confirms that a single pixel swap is presented in both the cipher and unique images. The estimating properties can be obtained using the following formulas:
The width and stature of the encoded picture are shown separately in the preceding equation by variables \(r\) and \(c\). \(Y\) displays an encrypted image, and \(\acute{Y}\) Denotes a single pixel change to the main image. \(J\left( {u,v} \right) = 1\,if\,\acute{Y} \ne Y; else, J\left( {u,v} \right) = 0.\) It has to be resistant against differential attacks when the UACI and NPCR upsides become closer to their true values. In Table 8, we distinguish between the values of UACI and NPCR in the cipher image. Figure 7 explicitly shows the Comparison of UACI and NPCR values for different cryptosystems. These are the two most significant tests for creating the best encryption scheme in the form of bar graphs. From this bar graph, we can conclude that our proposed encryption scheme has the best results as compared to other schemes.
Analysis of mean square error
The difference in between the actual and coded photos is calculated using the Mean Square Error (MSE). When there is a major difference in between the real and coded snap, the mean square error is highly valuable. It is made using the formula specified in condition (6)
Here c indicates the number of distinct segments and \(r\) indicates the number of lines. \(\text{MSE} \ge 30 db\) is required to fulfill a divergence in between the guanine and scrambled image. MSE of the proposed scheme is represented in Table 9.
Analysis of peak signal-to-noise ratio
The terminology PSNR47 expresses the ratio in between the highest value (force) for the force of bending and a sign volume that affects its portrayal. Original and compressed image quality can be estimated using this ratio. The maximum the PSNR, the superior the idea of the revised or condensed image is. NPCR uses both the original and distorted images to evaluate a similarity. Equation (7) can be utilized to obtain it.
The PSNR value connecting the uncoded and coded images should be as less as possible for an optimal encryption computation. Table 9 below shows the developed cryptosystem’s MSE and PSNR values. Figure 8 represents comparison of MSE and Fig. 9 represents the comparison of PSNR values with the previous encryption scheme and from this pictorial representation, we can conclude that our formulated encryption scheme is best.
Security analysis
Testing our encryption scheme by the following developed analysis namely Key Space Analysis, Complexity of Computation, and Key Sensitivity Analysis for evaluating the best encryption scheme in performance and security. Following is the detailed discussion which further elaborates this analysis both theoretically and mathematically.
Key space analysis
Security points should have functional key space. A secure coded image requires a highly ordered key space to fend off the vicious power attack. It is a fundamental component of all cryptosystems. It is reasonable to use a large key space for common sense. As time goes on, a PC’s encryption cryptosystem can avoid a total strike48 if the hidden key size is larger as compared to \({10}^{38}\). Our devised encryption scheme hidden key is composed of three hidden keys, each of which is unique for a different part of the scheme. The 1st key is utilized for sine map implementation, the 2nd one is made with the circulant matrix, and the 3rd key is utilized for the turbulent tent guide’s recommended course of action. In this manner, the size of the key for the developed encryption scheme is \({10}^{72}>{10}^{38}\), which is too big to consider protecting the data from severe power attacks. Table 10 provides the association of Key space size. Figure 10 shows the Comparison of the key size of our proposed encryption scheme with the three existing schemes. In Bar Graph representation of the key size along y-axis we consider only exponent value of the key size shown in Table 10. From this comparison, we can see that our proposed algorithm sweeps out other schemes in key size comparison.
Complexity of computation
Computational complexity associated with our proposal is illustrated below. The fastest registration machine can calculate \({10}^{24}\) times in a second. As a result, the processing machine does \({10}^{24}\times 365\times 24\times 60\times 60\) estimations annually. Therefore, to break the suggested computation,\(\frac{{10}^{72}}{{10}^{24}}\times 365\times 24\times 60\times 60={10}^{43}\) years are required. The \({10}^{43}\) year time horizon is sufficiently large to protect our suggested encryption cryptosystem from a monstrous power strike.
Key sensitivity analysis
Modest modifications with the enigmatic key should be extremely careful when using a recognized encryption method48. An adequate approximation needs to be highly sensitive to its enigmatic key, revealing even the slightest alteration in the mystery key should produce incredibly fascinating code outcomes. The security of the chaotic flow cryptosystem is demonstrated by the anti-dynamic theory of deterioration theorem discussed in the research paper49. Furthermore, the algorithm should not be capable of cracking a coded picture or extracting a little sample from that original picture using a slightly altered real key. If there is even a slight alteration to any part of the key, the result of the encoded computation remains valid in the current cryptosystem. The result of decoding our approach is completely different with a small adjustment in any one of the three keys. This explains that if we were to add \(0.000000000000001\) to the 1st key, we wouldn’t have the original picture after decoding utilizing that key for the most popular method of interpretation. Ciphertext Difference Rate (CDR) which is defined by the following equations is utilized for their analytical analysis associated with key sensitivity50.
The small changes in the parameters \(\left({w}_{0},\alpha ,{x}_{0},\nu \right)\) Dominate the size of the key. Performing four distinct test analyses for four parameters and upgraded up to \(\pm \Delta L\) as \(\pm \Delta L=(\pm \Delta {\omega }_{0}\text{, }\pm\Delta \alpha ,\pm\Delta {x}_{0},\pm \Delta \nu )\) illustrate the minor change in these factors.
-
\(\omega_{0}\) is transformed from 0.99 to \(\omega_{0 + } = \omega_{0} + \Delta \omega_{0}\) and \(\omega_{0 - } = \omega_{0} - \Delta \omega_{0}\) for \(\Delta \omega_{0} = 10^{ - 15}\)
-
\(\beta\) is changed from 0.79 to \(\alpha_{ + } = \alpha + \Delta \alpha\) and \(\alpha_{ - } = \alpha - \Delta \alpha\) for \(\Delta \alpha = 10^{ - 15}\)
-
\(z_{0}\) is changed from 0.66 to \(x_{0 + } = x_{0} + \Delta x_{0}\) and \(x_{0 - } = x_{0} - \Delta x_{0}\) for j \(\Delta x_{0} = 10^{ - 15}\)
-
\(\mu\) is changed from 3.78 to \(\upsilon_{ + } = \upsilon + \Delta \upsilon\) and \(\upsilon_{ - } = \upsilon - \Delta \upsilon\) for \(\Delta \alpha = 10^{ - 15}\)
To calculate the values of \(X\), \({X}_{1}\) and \({X}_{2}\), \({\omega }_{0}=0.99\), \({\omega }_{0+}\)= and \({\omega }_{0-}=0.990000000000001\) and \(0.989999999999999\) have been utilized which resulted in the output value of CDR is 99.56%. The acceptance value for the key sensitivity over 99% is considered to be sufficient. Table 11 shows the values of CDR for other factors. From Table 10 we can conclude that the suggested encryption scheme has key sensitivity over the anticipated threshold value.
Efficiency analysis concerning execution time
The execution time is another important factor for the security level51. The suggested encryption algorithm’s execution time is assessed and contrasted with a few earlier suggestions for color photos of various sizes. Table 12 presents the findings, demonstrating the superiority of our Proposed Algorithm in terms of speed and efficiency.
Noise and data loss attacks
This study enhances the robustness of encryption schemes against noise and data loss in public networks. It emphasizes the importance of noise resistance in real-world interactions, with the recommended algorithm demonstrating efficacy against pepper and salt noises, preventing data loss or obscuration. The consequence of introducing salt-and-pepper noise to the encrypted image formed by the proposed cryptosystem is illustrated as a noise attack in Table 13. Consequently, the suggested method outperforms the strategies in withstanding the salt and pepper noise attack.
Likewise, we evaluated our suggested encryption strategy on an encrypted image (EI) with data loss in order to recover the original image. This test was run to assess the differences in the data loss rates of 20%, 59%, and 90% as shown in Table 14, we evaluated the decryption outcomes of encrypted photos with varying levels of data loss.
Conclusion
Information security has grown increasingly important as communication technologies and computer networks have developed. In order to ensure secure data communication, encryption techniques are essential, particularly when dealing with huge volumes of sensitive data like medical photographs. To overcome these difficulties, a modified picture encryption cryptosystem was created in this work. It makes use of a CTM, site map, and sine map to efficiently control the diffusion and confusion processes.
Strong security features, such as key sensitivity and large key space to withstand brute-force attacks, are demonstrated by the approach put forth here. Experiments on brain and chest X-ray pictures demonstrated the system’s efficacy in terms of entropy enhancement, security analysis, and correlation reduction. Even though the system shows a high level of stability and security, there may be obstacles to its practical implementation in real-world applications, including computational complexity and possible susceptibility to future developments in attack techniques.
Because cloud storage solutions are open, they can be subject to various security risks. A thorough examination of the security protocols is required when developing a cloud-based medical imaging database. A few intrinsic drawbacks of using classical chaotic systems are their periodicity, ease of phase space destruction, and low Lyapunov exponent. In order to address these problems, a large number of researchers have concentrated on enhancing the chaotic dynamic properties of classical chaotic systems by means of a process known as Chaotification. Chaotification aims to compensate for these drawbacks and enhance the efficacy of chaotic encryption techniques. One potential avenue for further development of this work would be to swap out the classical chaotic maps with the maps that result from the Chaotification process. Table 15 compiles the testing and efficiency check results and compares them to various approaches.
Data availability
The datasets analyzed during the current study are available in the kaggle repository, https://www.kaggle.com/c/ultrasound-nerve-segmentation/data/select=sample.
References
Ravi, D., Ramachandran, S., Vignesh, R., Falmari, V. R. & Brindha, M. Privacy-preserving transparent supply chain management through Hyperledger Fabric. Blockchain Res. Appl. 3(2), 100072 (2022).
Bokhari, M. U., Makki, Q. & Tamandani, Y. K. A survey on cloud computing. In Big Data Analytics: Proceedings of CSI 2015 149–164 (Springer, 2018).
Patel, R., Goswami, A., Mistry, H. K. & Mavani, C. Application layer security for cloud. Educ. Adm. Theory Pract. 30(6), 1193–1198 (2024).
Altowaijri, S. M. An architecture to improve the security of cloud computing in the healthcare sector. In Smart Infrastructure and Applications Foundations for Smarter Cities and Societies 249–266 (Springer, 2020).
Dutta, A., Misra, C., Barik, R. K., & Mishra, S. Enhancing mist-assisted cloud computing toward a secure and scalable architecture for smart healthcare. in International Conference on Advanced Communication and Computational Technology 1515–1526. (Springer, 2019).
Sri VignaHema, V. & Kesavan, R. ECC-based secure sharing of healthcare data in the health cloud environment. Wirel. Pers. Commun. 108, 1021–1035 (2019).
Kamal, S. T., Hosny, K. M., Elgindy, T. M., Darwish, M. M. & Fouda, M. M. A new image encryption algorithm for grey and color medical images. Ieee Access 9, 37855–37865 (2021).
Pourjabbar Kari, A., HabibizadNavin, A., Bidgoli, A. M. & Mirnia, M. A new image encryption scheme based on hybrid chaotic maps. Multimed. Tools Appl. 80, 2753–2772 (2021).
Vaseghi, B., Mobayen, S., Hashemi, S. S. & Fekih, A. Fast-reaching finite time synchronization approach for chaotic systems with application in medical image encryption. Ieee Access 9, 25911–25925 (2021).
Kaur, H., Alam, M. A., Jameel, R., Mourya, A. K. & Chang, V. A proposed solution and future direction for blockchain-based heterogeneous medicare data in the cloud environment. J. Med. Syst. 42, 1–11 (2018).
Devi, K. R., Suganyadevi, S., Karthik, S., & Ilayaraja, N. Securing medical big data through blockchain technology. in 2022 8th International Conference on Advanced Computing and Communication Systems (ICACCS) (Vol. 1, 1602–1607). (IEEE, 2022).
Zhang, Q., Yang, L. T., Castiglione, A., Chen, Z. & Li, P. Secure weighted possibilistic c-means algorithm on the cloud for clustering big data. Inf. Sci. 479, 515–525 (2019).
Sivaram, M. et al. Secure storage allocation scheme using the fuzzy-based heuristic algorithm for the cloud. J. Ambient Intell. Humaniz. Comput. 12(5), 5609–5617 (2021).
Haber, S. & Stornetta, W. S. How to time-stamp a digital document 437–455 (Springer, 1991).
Mandal, A. K., Parakash, C., & Tiwari, A. Performance evaluation of cryptographic algorithms: DES and AES. in 2012 IEEE Students’ Conference on Electrical, Electronics and Computer Science 1–5. (IEEE, 2012).
Mahajan, P. & Sachdeva, A. A study of encryption algorithms AES, DES and RSA for security. Global J. Comp. Sci. Technol. 13(15), 15–22 (2013).
Balasamy, K., Krishnaraj, N. & Vijayalakshmi, K. Improving the security of medical images through neuro-fuzzy-based ROI selection for reliable transmission. Multimed. Tools Appl. 81(10), 14321–14337 (2022).
Kanwal, S., Inam, S., Ali, R., Cheikhrouhou, O. & Koubaa, A. Lightweight noncommutative key exchange protocol for IoT environments. Front. Environ. Sci. 10, 996296 (2022).
Hasan, M. R., Deng, S., Sultana, N. & Hossain, M. Z. The applicability of blockchain technology in healthcare contexts to contain COVID-19 challenges. Library Hi Tech 39(3), 814–833 (2021).
Wen, H. & Lin, Y. Cryptanalysis of an image encryption algorithm using quantum chaotic map and DNA coding. Expert Syst. Appl. 237, 121514 (2024).
Wen, H. & Lin, Y. Cryptanalyzing an image cipher using multiple chaos and DNA operations. J. King Saud Univ. Comput. Inf. Sci. 35(7), 101612 (2023).
Feng, W., Qin, Z., Zhang, J. & Ahmad, M. Cryptanalysis and improvement of the image encryption scheme based on Feistel network and dynamic DNA encoding. IEEE Access 9, 145459–145470 (2021).
Neela, K. L. & Kavitha, V. Blockchain-based Chaotic Deep GAN Encryption scheme for securing medical images in a cloud environment. Appl. Intell. 53(4), 4733–4747 (2023).
Mondal, A. & Goswami, R. T. Enhanced Honeypot cryptographic scheme and privacy preservation for an effective prediction in cloud security. Microprocess. Microsyst. 81, 103719 (2021).
Pradeep, G., Bala, S., Satheesh, N. P., Mahalakshmi, M., Balasamy, K., & Suganyadevi, S. An effective framework for detecting epileptic seizures using CNN and encrypted EEG signals. in 2023 International Conference on Sustainable Computing and Smart Systems (ICSCSS) 611–617. (IEEE, 2012).
Ali, T. S. & Ali, R. A novel medical image encryption scheme using TLTS and Henon chaotic map. IEEE Access 8, 71974–71992 (2020).
Padhy, R. P., Patra, M. R. & Satapathy, S. C. Design and implementation of a cloud based rural healthcare information system model. Univers. J. Appl. Comput. Sci. Technol. 2(1), 149–157 (2012).
Lakshmi, C. et al. Neural-assisted image-dependent encryption scheme for medical image cloud storage. Neural Comput. Appl. 33, 6671–6684 (2021).
Sharma, P. K., Moon, S. Y. & Park, J. H. Block-VN: A distributed blockchain-based vehicular network architecture in the smart city. J. Inf. Process. Syst. 13(1), 184–195 (2017).
Liang, X., Shetty, S., Tosh, D., Kamhoua, C., Kwiat, K., & Njilla, L. Provchain: A blockchain-based data provenance architecture in the cloud environment with enhanced privacy and availability. in 2017 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGRID) 468–477. (IEEE, 2017).
Afzal, I., Parah, S. A., Hurrah, N. N. & Song, O. Y. Secure patient data transmission on a resource-constrained platform. Multimed. Tools Appl. 83, 1–26 (2020).
Inam, S., Kanwal, S. & Ali, R. A new encryption scheme based on grouping. Contemp. Math. 2, 103–112 (2021).
Inam, S., Kanwal, S., Zahid, A. & Abid, M. A novel public key cryptosystem and digital signatures. Eur. J. Eng. Sci. Technol. 3(1), 22–30 (2020).
Kanwal, S. et al. Analytic study of a novel color image encryption method based on the chaos system and color codes. Complexity 2021(1), 5499538 (2021).
Kanwal, S. et al. A New image encryption technique based on sine map, chaotic tent map, and circulant matrices. Secur. Commun. Netw. 2022, 1 (2022).
Kanwal, S. et al. An effective color image encryption based on henon map, tent chaotic map, and orthogonal matrices. Sensors 22(12), 4359 (2022).
Inam, S., Kanwal, S., Firdous, R. & Hajjej, F. Blockchain-based medical image encryption using Arnold’s cat map in a cloud environment. Sci. Rep. 14(1), 5678 (2024).
Toktas, F., Erkan, U. & Yetgin, Z. Cross-channel color image encryption through 2D hyperchaotic hybrid map of optimization test functions. Expert Syst. Appl. 249, 123583 (2024).
Kocak, O., Erkan, U., Toktas, A. & Gao, S. PSO-based image encryption scheme using modular integrated logistic exponential map. Expert Syst. Appl. 237, 121452 (2024).
Feng, W. et al. Exploiting newly designed fractional-order 3D Lorenz chaotic system and 2D discrete polynomial hyper-chaotic map for high-performance multi-image encryption. Fractal Fract. 7(12), 887 (2023).
Li, H. et al. Exploiting dynamic vector-level operations and a 2D-enhanced logistic modular map for efficient chaotic image encryption. Entropy 25(8), 1147 (2023).
Feng, W. et al. Image encryption algorithm based on plane-level image filtering and discrete logarithmic transform. Mathematics 10(15), 2751 (2022).
Feng, W. et al. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst. Appl. 246, 123190 (2024).
Hua, Z. & Zhou, Y. Image encryption using 2D logistic-adjusted-sine map. Inf. Sci. 339, 237–253 (2016).
Hayat, U. & Azam, N. A novel image encryption scheme based on an elliptic curve. Signal Process. 155, 391–402 (2019).
www.kaggle.com/c/ultrasound-nerve-segmentation/data/select=samplesubmission.csv
Zhongyun, H., Fan, J., Binxuan, X. & Hejiao, H. 2D logistic-sine-coupling map for image encryption. Signal Process. 149, 148–161 (2018).
Wang, X., Zhao, H., Feng, L., Ye, X. & Zhang, H. High-sensitivity image encryption algorithm with random diffusion based on dynamic-coupled map lattices. Opt. Lasers Eng. 122, 225–238 (2019).
Wang, X. & Liu, P. A new full chaos coupled mapping lattice and its application in privacy image encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 69, 1291–1301 (2021).
Erdem, Y., Rifat, Y., Kasapbaşı, M. C. & Ezgi, Y. A chaos-based image encryption algorithm with simple logical functions. Comput. Electr. Eng. 54, 471–483 (2016).
Yavuz, E. A new parallel processing architecture for accelerating image encryption based on chaos. J. Inf. Secur. Appl. 63, 103056 (2021).
Chidambaram, N., Thenmozhi, K., Raj, P. & Amirtharajan, R. DNA-chaos governed cryptosystem for cloud-based medical image repository. Clust. Comput. 27, 1–18 (2024).
Aashiq Banu, S., Rao, L. K., Priya, P. S., Hemalatha, M., Dhivya, R., & Rengarajan, A. A review of genome to chaos: Exploring DNA dynamics in security. Multimed. Tools Appl. 1–28. (2024).
Padmapriya, V. M., Thenmozhi, K., Hemalatha, M., Thanikaiselvan, V., Lakshmi, C., Chidambaram, N., & Rengarajan, A. Secured IIoT against trust deficit flexi cryptic approach. Multimed. Tools Appl. 1–28. (2024).
Wei, X., Guo, L., Zhang, Q., Zhang, J. & Lian, S. A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J. Syst. Softw. 85(2), 290–299 (2012).
Huang, L., Cai, S., Xiong, X. & Xiao, M. On symmetric color image encryption system with permutation-diffusion simultaneous operation. Opt. Lasers Eng. 115, 7–20 (2019).
Yaseer, I. & Khalifa, F. A new image encryption scheme based on hybrid chaotic maps. Complexity 2020, 23 (2020).
Alvarez, G. & Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 16(08), 2129–2151 (2006).
Wang, X., Liu, L. & Zhang, Y. A novel chaotic block image encryption algorithm based on dynamic random growth technique. Opt. Lasers Eng. 66, 10–18 (2015).
Zou, D., Li, M., Li, J. & Li, Z. An image encryption algorithm based on a new hybrid power exponent power system. Inf. Sci. 579, 128–149 (2021).
Souyah, A. & Faraoun, K. M. An image encryption scheme combining chaos-memory cellular automata and weighted histogram. Nonlinear Dyn. 86(1), 639–653 (2016).
Mohamed, F. K. A parallel block-based encryption schema for digital images using reversible cellular automata. Eng. Sci. Technol. Int. J. 17(2), 85–94 (2014).
Wang, X. & Zhang, H. A color image encryption with heterogeneous but-permutation and correlated chaos. Opt. Commun. 342, 51–60 (2015).
Acknowledgements
The authors extend their appreciation to the Deanship of Research and Graduate Studies at King Khalid University for funding this work through Large Research Project under grant number RGP2/212/45.
Author information
Authors and Affiliations
Contributions
Conceptualization, Methodology & Formal analysis: S.K. 2. Supervision: M.B. 3. Writing original draft & Formal analysis: U.S. 4. Methodology, Review & editing: S.I. 5. Experimental Results: M.E.M.A. 6: Review & editing of figures: Z.A.S
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Shahid, U., Kanwal, S., Bano, M. et al. Blockchain driven medical image encryption employing chaotic tent map in cloud computing. Sci Rep 15, 6236 (2025). https://doi.org/10.1038/s41598-025-90502-5
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-90502-5
Keywords
This article is cited by
-
Industrial progress with quantum algorithms: an in-depth review
The Journal of Supercomputing (2025)
-
Accurate prediction of college students' information anxiety based on optimized random forest and category boosting fusion model
Discover Artificial Intelligence (2025)