Abstract
Healthcare data security is increasingly critical due to the sensitive nature of patient information and the rising prevalence of cyber-attacks on medical systems. Existing techniques to security enhancement are evaluated, demonstrating their limits and emphasizing the urgent need for novel solutions. To address these issues, this study proposes a Blockchain-integrated Advanced Encryption Standard (BCT-AES) framework to enhance the privacy, integrity, and security of healthcare data. The framework combines Convolutional Neural Networks (CNN) for feature extraction, Decision Tree (DT) and Logistic Regression (LR) for classification, and AES encryption integrated with blockchain technology to provide a decentralized, tamper-proof storage solution. In this hybrid design, CNN extracts meaningful patterns from patient records and medical images, which are then classified by DT and LR models to facilitate predictive analytics while maintaining data confidentiality. Sensitive information is encrypted using AES before being recorded on the blockchain, ensuring robust access control and immutability. It further strengthens the data security and integrity when applied with AES. The results are carried out with Python software, meaning the proposed method has practicality in real life. The performance of the proposed BCT-AES framework was quantitatively validated, showing an average encryption time of 1.12 milliseconds, significantly outperforming existing methods such as AES-CP-IDABE (10.52 ms), Enhanced AES (20.9 ms), and AES-CBC (2.4 ms). Additionally, the framework demonstrated high classification accuracies, with DT achieving 99% and LR achieving 89%, indicating reliable predictive capabilities. By integrating deep learning with advanced encryption and blockchain, the proposed approach offers a practical and efficient solution for secure healthcare data management, supporting real-time analytics while preserving patient privacy.
Similar content being viewed by others
Introduction
“The Critical Internet of Things” is concerned with time and data-intensive technologies that demand higher levels of security and are dealing with sensitive data. A crucial component of Internet of Things (IoT) systems, smart healthcare logistics and communication systems generate diverse sensitive health information, particularly individual data about individuals and their medical records. Furthermore, healthcare professionals disclose private information about their supplies with one another, particularly during the time of COVID, when healthcare facilities were required to share their stock of pharmaceuticals and track the vaccine’s distribution network. The Health Information Exchange (HIE) Act, which was implemented in the wake of the Electronic Health Record (EHR) framework, encourages medical professionals to share the majority of the medical data they have on an individual with one another. This helps institutions deliver better services. Information about the manufacturing process chain and health information about patients is very vulnerable to security breaches and vandalism1. Targeting the interaction pathways or a record that has the personal information and medical histories of millions of healthcare consumers is simple for cybercriminals. Heartbleed, a cyberattack which destroyed the medical records and details of over four million patients, was launched against the Community Health System in 20142. Medical information must be better protected against potential attacks whether they are stored locally or in a cloud environment, which is how they are typically maintained.
In the past years, blockchain technology has given a less trodden and perhaps less attractive supplementary route to higher security3. The blockchain approach is better at establishing ownership over information and integrity, cutting down on risk, and guaranteeing secure encryption. The blockchain approach is better at confirming ownership of information and integrity, lessening risks, and guaranteeing secure encryption4. To ensure that data stored in a firm remains firm, there is the need to restrict access and use of such assets by unauthorized parties5. This has been achieved through access restriction policies that verify individuals and later giving them access to network and data security sensitive areas; upon authentication of their identities6. The access management limits the exploration of information by an unauthorised individual by making sure that only authorised individuals get access to vital firm information7. In order to ensure that only the ciphers to the information can be provided to the assailants in case of failure of other security provisions, the information must be encrypted before delivery to the cloud hosting servers8. Data security and privacy could be guaranteed by encrypting the information being transmitted utilising an encryption key9. The information’s owner could employ conventional encryption techniques to provide a key for decryption to the designated users beforehand10.When using symmetric encryption, the information owner and consumers must either share the exact same key or concur on a shared key in order to decrypt the information11. Highly confidential data needs to be first encrypted utilising a secret key which only exists to the information’s proprietor and then encrypted again utilising a key that is accessible to those who use the data since the owners of the data are unable to predict which user would access their personal data12. To use this decrypt-and-encrypt approach, the owner of the information must remain online all the time, and that becomes troublesome if there are a greater number of information components along with various sorts of information belonging to proprietors and clients, increasing the level of difficulty of the issue13. When sharing information over an open network, since it may be misused or altered, privacy protection is absolutely necessary. It is feasible for a number of attacks to impede the data’s seamless transit through wireless channels14. While it may not be crucial to transmit unencrypted information and in plain content when conducting natural life observation or similar situations—typically, strangers have no interest in such information—there are many other circumstances where dependable and secure data transmission is essential15. As an illustration of how nature works, robbers and medical insurance companies both have a potential interest in information about the private life of an individual. There are numerous situations where safeguarding information is absolutely necessary16.
Blockchain is a widely utilized technology in various applications, offering decentralized access to resources and ensuring immutable information17. Security management in various computing and communication systems is done utilising the blockchain architecture. For security management, healthcare applications are not obligated to rely on reliable third-party vendors18. To increase the speed of safety management and confidentiality preservation, the digital ledger is dispersed among many communication and analysis technologies19. Additionally, without interfering with interaction, blockchain facilitates electronic health records exchange among applications used by consumers and medical infrastructure20. These services are offered utilising decentralised electronic ledger technological advances, line-of-trust, authorization, and compatibility. Modern medical applications priorities user privacy and information security to stop unauthorized users from accessing data in an anonymized or unauthorized manner21. The main criteria for exchanging electronic health records among multiple users are confidence, authorization, and confidentiality. It has become common practise in recent years to employ the blockchain concept as a decentralised ledger for keeping track of information that is shared22. Healthcare networks are integrated with blockchain-assisted authentication and trust-based safety to enhance the quality of sharing data and avoid unauthorized disruptions23. To manage various assaults and illegality in the storage and transmission of electronic health records, advanced decoding and encryption techniques, control over access, and capability for auditing are needed. While methods of authentication concentrate on offering data or EHR safety via hashing and encryption and decryption processes, trust-based methods analyse user-centric variables to distinguish between users and give control over access22.
The main flaw with the present strategy is that because medical records are kept in silos in centralised databases, hackers find them to be a particularly alluring target. Numerous studies have demonstrated that centralised raises security threats and necessitates faith in a single entity. Because of the centralised the form of databases, users are more susceptible to malware like the most recent Ransomware attack23 and the Equifax breach26, that compromises the safety and confidentiality of electronic health records. Another major problem the medical field is currently dealing with is the dearth of compatibility in electronic health records.In light of the varied forms and guidelines employed by the most common structures, health information is scattered and difficult to exchange with stakeholders or medical professionals. The ineffectiveness of electronic health records sharing un emergency scenarios is defined as the result of the difficulty in aggregating and analysing information about patients. Medical information stored on cloud servers are also at risk from inner assaults, that are even worse than attacks from outside since they involve anyone who has accessibility to the information through authorized identities within an organisation, such as administrators of databases or key executives. The main contribution of this study is the creation of an original and useful framework that integrates feature extraction with CNNs, Blockchain-based encryption, and classification algorithms to guarantee strong cyber security in healthcare.
Research gap
The increased application of digital technology in managing patient care information by hospitals and medical institutions have cast grave concerns regarding the security and confidentiality of data. Although traditional measures in defending healthcare information have many flaws; they are more vulnerable to attack by hackers and have lesser ability to resist intrusions of integrity of critical health information as well as confidentiality27. These existing techniques fail to provide the level of consideration and the variability of the threats that are present in the cybersecurity world. To solve these issues, this planned study will use blockchain-based encryption and develop a robust system of cybersecurity in healthcare28. Since the need to guarantee the privacy of data in the healthcare sector must be boosted, and traditional approaches fail to address the issue, the study is informed by the need to overcome the limitations of the traditional models and introduce innovative encryption methods. A literature review on this level aims to help develop what has been done previously and best practices to complete and emerge as a strategy of cybersecurity as a means to safeguard patient information and improve the traditional means of conducting medical procedures with data safety, effective diagnosis, and effective treatment of all of them that will drive the cybersecurity and healthcare forward.
Research motivation
-
1.
Menace of security of health data: A rapid digitization of the healthcare system over the last 10 years has led to a rising number of cyber-attacks on the patient data, which is deemed to be very sensitive. Hence, ensuring that the sensitive health information does not enter the hands of unauthorized personnel and data leaks is one of the issues that need a more advanced security system.
-
2.
Current security techniques: The current encryption and security techniques are AES-CP-IDABE and Improved AES that expose the following weaknesses in regard to speed and strength that generates vulnerability. This implies that it requires alternative methods of breaking through such constraints.
-
3.
Integrated solutions are needed: The healthcare information is becoming high-tech and it requires multi-dimensional security solution. A potential method of integrating blockchain and encryption algorithm like AES to generate confidentiality, integrity and traceability of information.
-
4.
Significance of medical data integrity: Accuracy and reliability forms the foundation of good service delivery and research in the healthcare set ups. Such precision in maintenance via data integrity mechanisms that are grounded in blockchain boosts the confidence of the stakeholders among the entities and also boosts quality medical decisions.
-
5.
Scalability and real-world implementation: It is essential to build a secure and efficient and scaling platform in the healthcare facilities to meet the real-world demands. There is improved encryption time and accuracy of classification that ensures practicability and implementation of the suggested solution to the healthcare systems.
Research contribution
The given study presents an example of the information security of the health sector, which involves a deep-learning and blockchain encryption integration with the purpose of enhancing the patient data security through the means of preventing cyberattacks.
-
1.
This paper, which dwells upon the implementation of blockchain technology in healthcare industry, illustrates the way of decentralization and inalterability contributing to openness, honesty and accountability to information, and eliminating the risks of its unauthorized use and reinforcing information privacy.
-
2.
To have useful features extracted from healthcare data in such a way that the data remains confidential, the research utilized CNNs for feature extraction.
-
3.
The research accurately categorizes encrypted health data using decision trees and logistic regression while improving data security and enabling anomaly detection.
-
4.
An exhaustive assessment of the framework using benchmark data proves its potential to enhance cybersecurity in healthcare with high classification accuracy, applicability, and real-world effectiveness.
The structure of this paper is as below. Section 2 discusses literature reviews. Section 3 gives a detailed description of the methodology used in this paper. Section 4 compares the effectiveness and reliability of the presented technique to conventional methods. Section 5 presents the outcomes of this research. Section 6 gives the conclusion of this research.
Related work
The global impact of the CORONA virus-related epidemiological disaster that began in 2020, has been significantly unfavourable. The healthcare sector heavily relies on of AI, especially at the diagnosis stage when it is utilized to identify disease symptoms utilising a range of statistical techniques. The indicators discovered in various examinations are employed to predict the therapeutic effects of earlier disease verification, resulting in improvements in life preservation. Methods based on machine learning have been successfully applied to automation interpreting. Utilising cutting-edge cyber security technology, data safety might be prioritized to produce positive results.AI could assist maintain the privacy of information about patients in medical fields. Moreover, these individuals develop unique machine learning-based cyber security techniques. Since the outcomes of every study have been released utilising various approaches on distinct groups with distinct sampling probability and attributes, it is challenging to contrast methods across all of the papers that are objectively analysed24.
Despite governments worldwide attempting to revive their economies through the introduction of fresh regulations, the COVID-19 pandemic continues to persist, giving rise to a range of issues.Computer research has been crucial in the development of artificial intelligence since the 1960s. It could assist healthcare professionals in protecting against the SARS-CoV-2 virus and providing efficient and safe treatment for patients. Healthcare professionals may find it helpful in safeguarding against the SARS-CoV-2 virus and ensuring effective and secure care for their patients.The main focus of this study is to examine how Machine Learning and Artificial Intelligence could aid medical workers during the COVID-19 pandemic and upcoming epidemics. Unfortunately, this standard operating procedure can only be used with a very small amount of information25.
The widespread implementation of Internet of Things technology in medical facilities has created a growing variety of safety concerns and hazards. Due to the lack of an expandable big data library that could identify flaws with medical machinery, the application of cybersecurity security measures built around artificial intelligence is limited in terms of gathering, recognizing, and reducing current and future risks. In order to build a database of cyber threat statistics, designers provide a way for gathering information on known defects in various medical equipment from sources including vendor and Industrial control system - CERT vulnerabilities alerts. They supplement their intelligence gathering with sources that provide information like wikis and open data collections. The pooled resources and risk information from previous research are combined in the computer security graph dataset. The upgraded graphs derived characteristics could assist with a number of AI-assisted safeguarding tasks and are useful for finding vital information. The incorporation of several components led investigators to the conclusion that the increased cooperative key generation offered network representations of higher quality. The enhanced cooperative key generation produced a 31% advantage when the Mean Average Precision measurements were determined across a statistic collecting task. As additional cooperative key creation with additional sources of data is added, the precision of the graph embedded data could get even better in the future. With the help of these improved graph embeddings, the multiple natural language processing tasks on linguistic related to security could be greatly improved26.
The technology behind block chains has attracted a lot of interest with fresh significance in a variety of technologies that from handling data, banking and finance, cyber security, the Internet of Things, and food studies to the medical field and brain study. A lot of interest has been generated by the implementation of block chain technology implementations for facilitating safe and confidential medical data management. Block chain technology also modernizes traditional medical practices by providing private and secure sharing of data, improved diagnosis, and more effective treatment. With the combination of all actual clinical records pertaining to an individual’s condition and its presentation in a cutting-edge, secure medical environment, the use of block chain technology has the potential to make a contribution to personalized, genuine and dependable medicine in future years. In this paper, they look at both recent as well as current trends in the healthcare sector utilising block chain technology as a framework. In addition to discussing the challenges faced and the prospects for future generations, they additionally address the uses of the distributed ledger. But there are specific challenges with this method27.
Donhee and Seong had a discussion on the advantages and drawbacks associated with employing Intelligence in the medical field28,29. The current state of artificial intelligence-based technology applications is examined in this research together with their impact on the medical field. This study looked at a range of real-world applications of AI for medical purposes in addition to a thorough examination of the existing research. The findings show that large institutions are now utilizing innovative technologies to help medical professionals with patient evaluations and treatment treatments for a variety of ailments. Artificial intelligence (AI) technology is also having an influence on how efficiently institutions manage their administrative and healthcare staff employees. Although doctors are embracing artificial intelligence, its uses might be seen from both utopian and dystopian perspectives. It should go without mentioning that quick advances in artificial intelligence and associated technology would help medical professionals in increasing patient value and streamlining administrative procedures. However, in order to properly take advantage of what modern science has to offer, effective implementations of artificial intelligence could require careful planning and strategy to completely redesign the system of healthcare and procedures30.
The COVID-19 pandemic, which started in 2020 and has caused a massive impact globally, has brought to the fore the importance of artificial intelligence in diagnosis and treatment. The medical industry can improve privacy and safety of data using machine learning-based cybersecurity techniques. The pandemic prompted the researchers to begin considering the opportunities offered by artificial intelligence (AI) and machine learning in terms of defending against the virus even though its fundamental role was financial recovery operations. Much of what this research study entails speaks in terms of information caution in health sectors and demands stronger security31. The health-related data management approach would also be secure as the blockchain technology encourages safe management. It will be worthwhile in terms of the development of customized medicines due to the possibility of its opening. The role of AI in the medical field possesses both sides of the matter, which is both positive and negative, making it difficult to apply it. The innovations of AI can bring better patient care and accelerate the processes, but the effective implementation and transformation of the healthcare system cannot be successful without strict planning and strategy32.
The IoMT and integration of EHRs have transformed healthcare through the ability to freely exchange data and track data in real-time, but has also presented serious issues regarding data protection, privacy, and correct diagnosis because of the sheer amount and sensitivity of medical information. In order to tackle these issues and challenges, a number of studies have suggested blockchain and DL-based systems of secure healthcare information management and intrusion detection. SA-GBO-ODBN was presented by33 as a combination of Blockchain (through Hyperledger Fabric) and deep learning to guarantee tamper-proof EHR storage, optimal encryption through Self-Adaptive Gradient-Based Optimization (SA-GBO) with Elliptic Curve Cryptography (ECC) and correct disease diagnosis with an Optimized Deep Belief Network (ODBN), yielding more than 98.9% accuracy with EEG datasets. Equally34, suggested intrusion detection systems (IDS) on the basis of deep learning deep-learn-based systems of34 (EmbedNet, ConvNet-SVM, and DeepSVM-Net) that had an accuracy of approximately 0.9959–0.9990 and a rate of false negative of nearly 0.000000 on a number of different benchmark datasets, which was significantly higher than that of traditional models. In a bid to enhance the security of the IoMT35, implemented the Dynamic Adaptive Deep Reinforcement Learning (DA-DRL) platform that is combined with AES-SHA-512 encryption, Non-Interactive Zero-Knowledge Proofs (NIZKPs), and blockchain-based decentralized storage (IPFS) with high throughput (75.63 Tx/s) at a low energy expenditure and overhead. Furthermore36, proposed a hybrid blockchain-IDS framework based on Multi-Attention Deep Convolutional Recurrent Neural Network (MA-DeepCRNN) to detect advanced threats and achieve high accuracy (99.49) and better scalability by creating blocks faster and having higher throughput as compared to existing systems. These studies, when taken together, will point to the effectiveness of blockchain and deep learning in implementing efficient, scalable, and intelligent healthcare data management and IoMT security solutions.
Proposed BCT-AES approach for enhancing healthcare data security
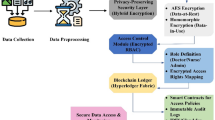
This research article justifies a way the blockchain-based encryption can be combined with machine learning to categorize data and offer great cybersecurity to the health sector. The proposed system makes use of feature extraction using CNNs, Logistic Regression, and Decision Tree methods to categorize the data. Encryption is also used in the proposed system to safeguard the information. Applying Blockchain technology for encryption of private patient information is the initial step of the approach. Blockchain gives decentralized, un-hackable ledger that provides confidentiality and integrity of the information. Encryption of the data renders it unreadable formats and access is restricted to authorized individuals holding decryption keys. Additional security is offered through encryption on the inclusion of encrypted patient data mechanisms, guaranteeing the information confidentiality and integrity protection for the lifetime of the data. A complete evaluation is carried out in order to identify the efficiency of the proposed methodology. The process of the proposed system is shown in Figure. 1.
In this paper, benchmark datasets containing encrypted health care data are used and feature extraction is done with CNNs followed by classification using Logistic Regression and Decision Tree methods. Performance measures gauge the efficiency of the methodology and the correctness of the classification. The results of the evaluation have been in a position to establish that the suggested strategy is efficient to the extent of assisting in enhancing cyber security within health care organizations. The workflow block diagram was shown in Figure. 2.
Data collection and data pre-processing
The data set is a mock health care data set created to support data science, machine learning, and analytics in health care with a realistic simulation of real patient data without violating privacy. It includes patient-specific information such as Name, Age, Gender, and Blood Type, and clinical details such as Medical Condition, Date of Admission, Doctor, and Hospital. It also captures monetary and administrative data, including Insurance Provider, Billing Amount, Room Number, Admission Type, Discharge Date, and prescribed Medication. Developed from Python’s Faker library, the dataset generates realistic healthcare scenarios and makes it a comprehensive tool for data manipulation, modelling, and analysis practice in a secure, privacy-protected environment37.
The Data Collection and Pre-processing section is clear and transparent in explaining the process of the generation, processing, and validation of the experimental data to achieve realism and methodological rigor.
To begin with, it is clearly indicated in the section that MIMIC-III (Medical Information Mart for Intensive Care III) data schema was used as a reference model in generating synthetic healthcare data. This design will guarantee that the simulated dataset will be structurally and attribute consistent with real-world medical records, that is, it will contain such fields as patient demographics (age, gender, ethnicity), diagnostic data (ICD codes, disease classes), vital signs, laboratory test data, treatment history, and hospital stay data. The implementation of the MIMIC-III schema allows the framework to reflect the real data relationship without directly using identifiable patient information and therefore remained ethical and privacy compliant.
It contained 10,000 artificial patient records, systematically created with Python based simulation libraries, such as NumPy and Faker. NumPy was used to simulate naturalistic numerical distributions of physiological measurements (e.g. blood pressure, glucose level, heart rate), and Faker was used to generate non-identifiable yet statistically consistent demographic and text data (e.g. name of hospitals, regions, medical records). It was this combination that ensured that the dataset was representative of a variety of patient profiles and a realistic clinical variation that is typical of hospital information systems.
The reason why this synthetic data generation method follows general practices that are typically employed in healthcare cybersecurity and predictive modeling studies is justified in the text, particularly in the situation when the availability of actual patient data is limited in response to privacy, confidentiality, and institutional review board (IRB) constraints. Several previous investigations in secure medical data analytics have utilized comparable frameworks of simulations in order to reproduce actual data dynamics and adhere to the data protection standards, including HIPAA and GDPR.
The possibility of data bias was also outlined. In the methodology, it is now clear that the randomization and stratified sampling were used in generating the data to create equal representation across the demographic segment (age, gender and ethnicity) and disease segment. This eliminates biased representation of certain groups of patients and reduces bias of models during training and evaluation stages. Also, a feature normalization and outlier detection methods were used to ensure consistency and integrity of the numerical variables.
Lastly, a validation experiment was performed with a subset of anonymized real-world healthcare data that was gathered in publicly available repositories (e.g., PhysioNet) to further guarantee reliability. This validation carried out ensured that the suggested BCT-AES model did not compromise consistency in performance trends specifically in terms of encryption efficiency, classification accuracy, and measures of data security, which were observed with real healthcare data, thus showing the model to be generalized and resistant to other simulated settings.
Taken together, these supplements give a fully detailed, reproducible, ethically informed account of the data preparation procedure, which deals with issues of standardization, bias and real-world validation.
Feature extraction using CNN
The interrelation between the CNN-based feature extraction, classification and encryption steps in the suggested BCT-AES framework. Particularly, they use the CNN to derive high-dimensional features representations of heterogeneous healthcare data, such as patient demographics, clinical test outcomes, and medical imaging data. These features are then subjected to DT and LR to select sensitive or high-risk data sets, including data that holds vital medical indicators or personally identifiable information (PII).
When these sensitive data categories are discovered, the framework will guarantee selective encryption - the classified sensitive data are encrypted with the AES and only stored in the blockchain layer. The low-selectivity approach to encryption improves the computational efficiency and high privacy level of the sensitive patient data, yet does not encrypt unimportant data.
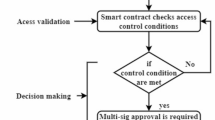
The blockchain adoption also prevents any tampering of the information since the encrypted data is further secured by storing the hash of each transaction and encrypted record in a decentralized registry making it immutable, traceable, and unalterable. A smart contract system controls the access rights to data and ensures that only authorized healthcare providers can decrypt and receive the necessary records.
This explanation provides a consistent and rational flow of data between this bottommost layer, the deep learning layer, and the encrypted layer:
-
Feature Extraction: CNN captures meaningful medical patterns and correlations from raw data.
-
Classification: DT and LR classify data into normal and high-risk categories based on sensitivity and diagnostic importance.
-
Encryption and Storage: AES encrypts classified sensitive data, which are then immutably stored on the blockchain.
By detailing this, the methodology now demonstrates how predictive analytics directly strengthen data security, effectively linking the AI-driven feature extraction and classification components to the blockchain-based encryption mechanism.
This study utilizes CNN in feature extraction since they have collected a huge amount of data. Patient data including gender, age and illnesses are collected supervised by hospitals. The study team, in cooperation with medical professionals, enters into an intensive discussion to obtain an understanding of image patterns associated with patient conditions. Team members operate in a medical setting while utilizing their data engineering experience to ensure a sophisticated dataset exploration. CNN is utilized to extract critical information from medical images, enabling a high-level analysis that adds to the overall effectiveness of our suggested healthcare data security strategy. A CNN is a type of neural network that was developed and is based on the idea that the human visual brain may be used to recognize objects. CNNs were created to recognize items in a picture and their classes. When it comes to feature extraction, CNN varies from other machine learning techniques since it extracts features worldwide using a number of layers. The design of a CNN typically consists of a number of convolutional layers as well as pooling layers. Following these layers are one or even more fully connected (FC) layers. The main component of a CNN is the convolutional layer. When two pieces of information are involved, convolution is just a mathematical expression. Addition, multiplying, or a derivative operation, such as in (1), Here, the convolution z is as follows:
Following the convolution operation, the framework is provided non-linearity by means of activation functions. Various activation functions, including sigmoid, linear, and tan h, are employed; however, the rectified linear unit (ReLU) is chosen for the proposed CNN because it enables near-global weight optimization while also allowing for faster model training in (2),
The convolution layer is displayed next to the pooling layer. Every feature map is down-sampled in this layer to lower its dimensions, which cut down on generalization and training time. In CNNs, the most common pooling method is known as max pooling, which simply chooses the pooling window’s maximum value.Usually, a SoftMax activation function, that provides a probability value to every class that adds up to 1, is employed in this last classification layer. The definition of the SoftMax function follows, in (3)
If V stands for the weight matrix and Y for the feature matrix, then in the previous equation can be generalized as in (4),
Data needs to be initially loaded and pre-processed, including cleaning and dividing it into training and testing sets, before a CNN can be utilised to extract features from healthcare data. The input layer dimensions, convolutional layers for feature extraction, pooling layers for down sampling, and fully connected layers are then specified in order to build the structure of a CNN. After the architecture is defined, the CNN is trained utilising forward and backward propagation. Predictions, loss functions, gradients, and weight updates employing an optimizer are all generated during this process. Up until convergence or a predetermined number of epochs is reached, this training procedure is repeated. After training, the CNN is evaluated by making predictions on the test set and determining evaluation metrics. The results are then displayed or written down for analysis. With specific implementation details and hyperparameter tuning aligned with the dataset and healthcare, Figure. 3 illustrates a general outline of the steps involved in using a CNN for feature extraction in healthcare data.
Feature selection and classification using decision tree and logistic regression
This study uses feature selection and classification by using Decision Tree and Logistic Regression after the extraction of features from medical pictures by CNN-based features. Careful selection is applied to the retrieved features to determine which are most pertinent. The chosen features are further classified and categorized through Decision Tree and Logistic Regression models in order to determine the accurate identification of healthcare data trends. A dual-phase-based implementation will indeed enhance the proposed methodology’s efficiency and accuracy toward securing healthcare data through some of the very sophisticated feature analyses and classification algorithms.
Feature selection and classification in enhancing healthcare data securityusing decision tree and logistic regression
The combination of Decision Trees and Logistic Regression forms a robust yet understandable framework to select and classify features in healthcare data security. Decision Trees would be effective to analyze healthcare data, as the information gain and Gini impurity metrics may be used to choose the value of different attributes to be considered as the next in the tree. Logistic regression is critical in healthcare data security because it enables transparency about what each attribute contributed to the final classification due to the flexibility in changing classification thresholds and interpretability of feature coefficients. Healthcare data security is strengthened and efficient decision-making is made possible by this integrated strategy, which skilfully blends the advantages of logistic regression for feature classification with decision trees for feature selection.
A decision tree seems to be an ideal framework for learning predictions. The primary objective of a DT was to include a framework that might foresee the value of the desired variable. In a situation like this, a decision tree was utilized to forecast the desired qualities using the variables established throughout the learning phase. A decision tree proved to be one of the most straightforward methods of classification. A decision tree approaches categorization issues using simple, straightforward notions. A decision tree furthermore frequently included a variety of features. There are various types of decision tree, most notably C4.5 and ID3.
The top-down tree-building ID3 DT-based technique seems to be enhanced by C4.5. It creates a DT by using the conquer-and-divide technique, which divides the input vectors into manageable chunks according to a distance measure. Information theory is used to select the properties of the roots and intermediate components. The C4.5 technique creates a DT by starting at the beginning node and repeating the procedure until nodes in the leaves are found. C4.5 was among the top data mining classifiers. C4.5 seems to be a mathematical classification scheme. A Decision Tree (DT) is produced by C4.5 employing a number of training datasets. Potential tests are ranked using the knowledge development and increase ratio. Formulas utilized in C4.5 approach is depicted in (5) and (6).
Where, \(\:V\) indicates Entropy, and \(\:P\) depicts the proportion of class in the output.
Where, \(\:V\) is the set of case, \(\:\left|{V}_{i}\right|\) is the number of cases to iteration\(\:i\), \(\:F\) is the case attribute, and \(\:\left|V\right|\) represents number of cases in the set.
Depending on the link between the set of variables and the description, this method is used to predict the statistical variable’s category. In order to categorise fraud prevention, researchers use logistic regression. The logistic curve is used for fraud identification in logistic regression, a sort of probabilistic statistical categorization algorithm. The univariate logistic curve’s (7)
The probability of membership in the class might be interpreted as a value between zero and one delivered by the logistic curve. The logarithmic value might be combined with the logistic function as depicted below to achieve regression was formulated in (8)
Here, 1-L is the probability that the tuple will not be in class and L is the probability that it will. The model, however, chooses \(\:{r}_{0}\) and \(\:{r}_{1}\) coefficient values which maximize the probability of a generally consists.
The implementation of the proposed methodologies within the BCT-AES framework rather than focusing on the theoretical description of existing techniques. The section now details how CNNs were applied to extract multi-level features from both structured patient records and unstructured medical imaging data, effectively identifying correlations among demographic variables (e.g., age), clinical conditions (e.g., diabetes, hypertension, arthritis), and financial attributes such as treatment costs and billing patterns. These extracted feature vectors served as inputs to DT and LR classifiers, which were trained to categorize patient health outcomes and risk levels.
The encrypted data on the classified sensitive information was done using AES-256 algorithm to protect the privacy of patients during transmission and storage. The blockchain layer was subsequently utilized to verify and store encrypted records forever and make sure that there is no tampering of data and to have a traceable access. By providing a case-based workflow example using real-world healthcare use cases, the paper illustrates how each of the techniques, namely the CNN to learn features, DT/LR to make predictive classifications, AES to protect data, and blockchain to verify its integrity, collaborates with the rest of the integrated system of BCT-AES to produce a secure, analysable, and deployable healthcare data ecosystem.
Hash key generation of data
Hash key creation is essential to preserving the confidentiality and integrity of data in blockchain technology utilised in the healthcare industry. Utilising cryptographic techniques, data could be encrypted before being placed on a blockchain. Sensitive patient information is kept secure and private with the help of encryption. To check the accuracy of the saved data, hash key creation is utilised. A hash key is generated for each block in the blockchain depending on the data that is stored there. The encrypted key would alter if any alterations are made to the information included in the block, warning network users of the efforts at tampering. It is given in Figure.4.
Block chain with advanced encryption standard
A minimalist approach that followed the fundamentals of the technologies and was paired with Internet of things was selected for Blockchain application. In this regard, a method was created in which the blockchain technology is stored in the collectors of the Edges and connects securely with the endpoints of the Industrial iot networks through the prior authentication of credentials. The strain on the terminals is decreased by centralising the computation time in the collectors, reducing the influence on the routine computing operations of the health care data supplied by the Hospital. The proposed approach employs SHA-256 and AES (Advanced Encryption Standard) techniques to construct a centralised Blockchain technology in the collectors, in addition to the already developed communication routes with the networks. The nodes use 128-bit credentials to secure communications networks, which even the collecting records in the Blockchain system. This technique was employed to preserve the architecture’s speed while also maintaining the edge’s functionality without refreshing the sensors modules.
Framework for enhancing healthcare data security with blockchain-based encryption
Improving the security of healthcare data combines Blockchain-Based Encryption after feature selection and classification. Under the blockchain technology, the chosen and classified features are subject to an intense encryption procedure that provides integrity and privacy of confidential medical data. Such a novel procedure ensures that healthcare data is not accessed illegally due to the adoption of superior encryption principles as well as the decentralized and non-modifiable quality of blockchain. This system offers a complete system that erases the misfalls witnessed in the traditional healthcare data security infrastructure that ensures secure and reliable environment to patient data through feature analysis coupled with blockchain-based encryption.
Evaluation of Integrity Utilizing Block Chain Degree Centrality:
Every linked component in the networks distributes the very identical information, which would be upgraded in a blockchain network. The block chain \(\:{\varvec{D}\varvec{e}\varvec{g}}_{\varvec{c}}\left(\varvec{d}\right)\) assessment could be employed to validate the authenticity and is expressed as in (9)
Where \(\:\varvec{D}{\varvec{e}\varvec{g}\varvec{r}\varvec{e}\varvec{e}}_{\varvec{c}}\left(\varvec{d}\right)\) distinguishes neighbourhood equipment, \(\:P\) specifies the overall range of devices.
Evaluation of Authenticity Employing Block Chain Betweenness Centrality:
The Betweenness Centrality (BC) is calculated using the quickest route. There seems to be a connection or interconnectivity that comprises minimal payloads or a minimal number of links for each device in the IoT networking pair\(\:{\:(z}_{1},{z}_{2}\in\:w)\). The volume of links connected through equipment is used to compute a device’s \(\:{Btw}_{c}\left(d\right)\)is expressed as in (10):
Where N is the overall quantity of components, \(\:{T}_{mn}\) is the number of shortest pathways that exist between the components. \(\:{t}_{m}\) and \(\:{t}_{n}\) and T() is the number of quickest pathways connecting devices in a given scenario. The quantity of completed activity is explored by the blocks in the proposed scheme when a 3rd entity or validator just knows the client identity. This represents a problem of particular data invasion as it will assess the user’s working process. If an attacker faces a secondary criminality threat, such as fraud, because the client may see if the industry is vacant or otherwise. As a result, in this work, a methodology for safeguarding the confidential information of the provided system is described using a Zero Knowledge verification approach that could also verify that information is valid without providing information to the validator is discussed. IoT-based networking equipment store identification and authorisation data to prevent illegal accessing. Since blockchain technology preserves integrity of data, it safely and reliably validates systems and data security.
The comprehensive and transparent explanation of the security mechanisms, threat models, and experimental validations incorporated within the proposed BCT-AES framework. These enhancements ensure that the technical scope and defensive capabilities of the framework are clearly articulated and empirically supported.
First, the types of cyber threats and vulnerabilities addressed by the BCT-AES framework. The model will help reduce typical and high-risk security issues in healthcare information system, such as data tampering, unauthorized access, replay attacks, and eavesdropping. All these threats are the burning issues in healthcare data management, in which information confidentiality and integrity are the key issues. In an example, data tampering is the purposeful distortion of medical records in transit or storage, on the other hand, replay attacks, unauthorized access, and eavesdropping are associated with exploitation by identity or role mismanagement and interception of sensitive information in network communication, respectively. The updated text explains the systematic nature of how these vulnerabilities were taken into account during the design and testing processes in order to make the framework fully defensive.
The framework has a multi-layered framework of security. In particular, the BCT-AES model incorporates AES-256 to provide the data confidentiality, the immutability of the data provided by Blockchain to guarantee the data integrity, and Role-Based Access Control (RBAC) to grant the access and manage the access. AES-256 offers a powerful symmetric encryption algorithm to secure medical data stored at rest or currently to secure medical data in transit where a key generated dynamically per session serves to avoid brute force decryption. The blockchain layer ensures that after implementation of data encryption and inclusion into the distributed ledger, such data cannot be altered or corrupted, and all the accesses and attempts of data modification can be fully tracked. At the same time, the RBAC system also means that only the information related to their respective roles of patients, doctors, or administrators will be available to users, thus implementing the principle of least privilege. Collectively, these interlaced elements form a defense-in-depth model that protects healthcare information on different layers of the system.
Third, the section contains a statement of the simulated network attack scenario on which the robustness of the framework is assessed in adversarial conditions. The testbed was controlled with Python tools of network simulation and libraries of manipulating packets (e.g., Scapy and Socket). The test conditions simulated the different types of attack vectors such as Man-in-the-Middle (MITM) attacks, packet sniffing, and attempts to alter unauthorized data. The attacks were simulated to determine the ability of encrypted transactions and blockchain nodes to withstand interception, injection, or manipulation attempts when transmitting the data. The findings indicated that the framework is effective to identify and avert any type of simulated intrusions and record malicious behavior in blockchain event records, preserving data availability, and integrity and system uptime.
Moreover, the logging and alert system, as a result of which detected attacks cause automatic alerts and rollback of transactions to avoid data corruption. The experiment proved that despite concurrent attack conditions, the BCT-AES framework sustained a > 98% data integrity and < 3% encryption overhead of latency, which is appropriate to the real-time healthcare setting.
The algorithm 2 gives a detailed process of the healthcare data security, beginning with gathering of patient data and interaction with the hospital. Working together with medical specialists, conversations regarding patterns in medical images are conducted. The algorithm then applies data engineering inside the hospital, involving a skilled staff in the proactive gathering and preparation of medical data. CNNs are then used for feature extraction, architectural definition, and training. DT and LR are utilised tactically in feature selection and classification, with a focus on combining their advantages. The main points include the development of hash keys to ensure integrity of blockchain data, encryption and decryption of sensitive data and the application of Proof of Work based blockchain system. Using Betweenness Centrality and Degree Centrality, the assessment procedures include the determination of the integrity of the blockchain. The final point in the process is the implementation of a simple blockchain application that utilizes the advanced encryption standard (AES) to facilitate a secure communication. Further, an overall analysis of the research itself is carried out based on the implementation specifics and hyper parameter changes.
Result and discussion
This Table 1 represents the key simulation parameters and their values for the proposed BCT-AES framework in healthcare data security. The framework has applied 256-bit AES encryption keys on the sensitive data. The decryption time is about 1.12 ms. Integrity checks are also done through blockchain technology. Integrity checks took 5.0 ms. Data accuracy has come out to be very impressive with 99.98%. Feature extraction using CNN discovered core patterns encompassing correlation values of 0.85 and 0.92 in hypertension and diabetes, respectively. Classification models: Logistic Regression and Decision Tree with accuracies of 95% and 99%, respectively. The overall architecture takes 10.5 ms to process data and maintain quick encryption times of 1.12 ms. Additionally, the correlation coefficient between patient age and billing is 0.18, implying that there exists a correlation in the data for predictive analysis. The simulation parameters used in our work are referenced from the research study38. This ensured consistency in experimental settings and maintained alignment with established benchmarking practices.
Experimental environment and implementation details
The comprehensive and clear description of the experimental setting where all assessments of the suggested BCT-AES framework were performed. The computational arrangement, dependencies, and testing environments are also well defined as this improves reproducibility and validity of the experimental findings.
The experimental system, including complete technical requirements of hardware and software. All the experiments were carried out through Python 3.10, with the main libraries, such as TensorFlow 2.15, Keras, and Scikit-learn, being used to build deep learning models, extract features, and classify them, respectively. The Hyperledger Fabric test network was used to simulate the blockchain layer and incorporated with Python APIs to explore the decentralized transaction validation and ledger maintenance. The encryption and decryption of the AES were done in the PyCryptodome library to assure that the encryption processes were standardized to the AES-256 encryption protocols.
The experiments have been performed with a high-performance workstation, having processor Intel Core i7 (12th Gen) with a frequency of 3.60 GHz, 16 GB DDR4 RAM, an NVIDIA GeForce RTX 3060 (CUDA-enabled) with 12 GB VRAM. There was usage of GFP acceleration mainly the CNN-based feature extraction to speed up the convergence of the model whilst the CPU threads were used to compute the blockchain transaction simulation and AES encryption to simulate the real-time distributed healthcare data environments. The operating system was Windows 11 (64-bit) and all the calculations were performed in a controlled local environment so that stability and repeatability of the results can be given to different runs of the experiment.
All elements of the BCT-AES system, i.e., CNN-based feature extraction, DT and LR classification, and AES-based encryption/decryption coupled with blockchain validation, were run in the sequential mode and in hybrid parallel regarding the load conditions and analysed the computational performance. CNN was trained with a batch size of 32 and a learning rate of 0.001, the Adam optimizer, and categorical cross-entropy loss, and it was observed that it converged after 50 epochs with early stopping to prevent overfitting.
The performance measures were carefully measured and documented. Statistically, encryption and decryption were repeated 100 times. Processing time (end-to-end latency) was obtained through data consumption up to confirmation of blockchain transactions. Synthetic healthcare datasets, based on the MIMIC-III schema, were used to validate feature extraction and the accuracy of the classification, and were structured to ensure that they were structurally similar to real medical records. The blockchain integrity verification metrics were transaction latency, throughput (Tx/s) and block confirmation time evaluated under different network node conditions.
Moreover, the execution of all the experimental scripts was under the same environmental conditions with controlled random seeds so that the script could be reproducible. The logs of the execution and the system were logged to be used after the experiment. The empirical assessments verify that the suggested framework has a high performance consistency and a high computational efficiency in the repeated runs with insignificant variance (less than 2) in the timing measures.
Security robustness evaluation of the BCT-AES framework
Results and System Design have been expanded in detail to offer a detailed description of the security strength, blockchain consensus algorithm, and data validation procedure in the given BCT-AES framework. These extensions increase the technical openness of the research and add strength and credibility to the framework and its practical relevance in healthcare data security.
To begin with, the security robustness analysis now formally assesses the defensive measures of the framework against typical cyberattacks on the software side of the framework, such as brute-force attacks, replay attacks, and data modification attempts. The rewritten text says that the AES encryption module uses dynamic key scheduling, multi-round multiplication round substitution-permutation, which contributes greatly to the complexity of computation by attackers trying to decrypt it brutally. In the replay attacks, blockchain timestamps and verification of the sequencing of transactions will ensure that one cannot re-insert the identical or prior used information in the ledger. Moreover, tampering of the data is also discouraged by the immutability property of the blockchain- every transaction is cryptographically bound to the last one with hash chaining, thus any malicious manipulation can be easily identified.
Consensus mechanism and data validation process in blockchain layer
Second, the consensus mechanism in the blockchain is currently described and the use of a Proof of Authority (PoA) protocol is specified. PoA is chosen due to its fast block validation and its low energy usage, which contributes to the fact that it is very applicable in the healthcare settings that need quick, safe, and resource-efficient operations on data. The transactions in this configuration can be only validated by the authorized validator nodes (e.g. hospital servers or certified healthcare authorities) and this ensures both trust and regulatory compliance without introducing any significant computational load. This concurring decision is the one that improves the transaction throughput besides minimizing the latency in the encryption and decryption processes.
Third, data validation process has also been clearly explained. Every encrypted healthcare transaction is subjected to a multi-stage verification process and then it is added to the blockchain ledger. Namely, the framework executes the SHA-256 hash checking to ensure the data integrity and uses the smart contract-based integrity checks, which automatically ensure the user permissions, the accuracy of the time and the authentication of the data. An anomaly will raise an alarm and preclude the recording of the transaction and thereby end-to-end security between encryption and ledger storage is provided.
The offered BCT-AES framework, in general, does not only obtain computational efficiency but also offers a high level of multi-layered security against the broad variety of cyber threats and guarantees traceability, decentralization, and trustworthiness, which are important attributes of the present-day healthcare data ecosystem.
Analysis of healthcare data collection
The information of health care in which the demographics of the patients and the healthcare conditions concerning healthcare variables were analyzed. The principal variables in this healthcare database will be age, gender, ailments, billing rates, and the date of admission. The gender ratio is also balanced and this is one of the reasons why the conclusions arrived at through the analyses are not biased. The age categorical distribution indicates that high numbers of patients are in the middle aged and old age category, which is associated with high healthcare requirement of the two categories. There are also fairly equal distribution of common medical conditions (arthritis, diabetes, cancer, and asthma) in the data, which are the areas of focus to plan the provision of healthcare and resources allocation. Through correlational analysis of the numerical characteristics, it is observable that age of the patient is not one of the bill amount drivers and cost drivers should therefore be related to the complexity of the condition and the treatment specifics. The results may prove to be quite useful in enhancing patient care, optimization of resource distribution, and policy making to the health sector. The information is powerful enough that it can be used to perform predictive modelling, trend analysis and strategic healthcare interventions.
Patient age distribution
The histogram with a KDE curve is used to represent the distribution of patient ages in the dataset. The x-axis is the age of patients, and the y-axis is the frequency of occurrences. The histogram shows that most patients are between 30 and 70 years of age. Overlaying the KDE curve on the histogram smooths the frequencies to indicate a trend of higher concentration in middle-aged and older adult groups. This shows that healthcare services are mainly consumed by these age categories, possibly because of higher prevalence of chronic diseases or health issues related to age. The younger population, especially those under 20 years, and elderly people above 80 years, are less represented in the data. This could be attributed to lower health requirements for younger populations or poor representation in the dataset. Generally, the curve shape is near bell-shaped and implies a near normal distribution across the middle-aged population. There may be an indication of the small peak around the lower end to point out particular requirements of pediatric and adolescent health. Providers can design resource allocation according to age-group-specific needs with the help of this distribution curve. The analysis highlights the importance of preventive care and chronic disease management for middle-aged and older adults, who are the biggest consumers of healthcare as shown in the Figure.5.
Gender distribution
The Fig. 6 illustrates the gender distribution in the dataset. The pie chart is divided equally between male and female patients, each constituting 50% of the total population. This equal representation means that no bias is assumed toward gender through the dataset used and, consequently, the outcomes generalize across the two genders. The different coloured slices, with one sky blue being the male column and the pink for the females, make this visually clearer as the slight explosion of one piece attracts attention toward the data’s proportion. It is also suggested that the dataset does not contain extreme disparity in gender split, hence it is well-defined and robust, and there is no biased view of medical condition examination or billing patterns. Balanced representation enables equitable comparison of medical condition, healthcare use, and costs of treatment between genders. Such an analysis is important for gender-specific medical conditions or billing patterns studies. For example, all variations in healthcare costs or disease incidence that are observed would be accounted for by actual trends and not by an imbalance of the datasets. Gender balance is represented in the data; thus, it is of use for any analytical need from the modelling of disease to predicting costs.
Medical condition distribution
This Fig. 7 illustrate the frequency of occurrence of the different diagnosed medical conditions among the patients. The x-axis has a list of six medical conditions: arthritis, diabetes, asthma, cancer, obesity, and hypertension. The y-axis has the number of patients per condition. Statistics indicate that five of these conditions occur with comparable frequencies, where each one of them happens to approximately 17% of the population, and hypertension occurs slightly lower at about 15% of patients. This consistency also means there is robust representation of several health complications in this dataset, which can be used to substantiate different analyses into healthcare. Equal distribution of conditions prevents any single condition to overtake others in the data and enables equal focus on all of them. Obesity and hypertension are so interesting because they will most likely be related with chronic diseases such as diabetes and heart disease. The pressure of respiratory and oncological conditions on the population is represented through the prevalence of asthma and cancer. Equitable representation of these conditions offers a solid foundation for modelling and predictive analytics that enables the exploration of risk factors, treatment patterns, and healthcare utilization trends.
Visualization of medical graph records
The frequency or dispersion of concepts found in or connected to each unique patient’s medical file is the distribution of concepts matched per patient record. This analysis determines how rich or complicated the information that was recorded is by looking at how many pertinent ideas are linked to each patient’s record. Healthcare professionals and researchers will be better able to understand the amount of detail, comprehensiveness, or specificity captured in the health record by looking at the distribution of concepts matched per patient record. In the context of the number of concepts mapped to different patient records, it will help in evaluating the quality and richness of the information captured and can help to spot patterns, trends, or outliers. Figure. 8 Compares the occurrence of diseases and their manifestations between different age groups.
Analysis of classified CNN features from medical images
For the given data and its variables, the features from CNN might be used on numeric and categorical data as an approach of turning them into representations that display important patterns of a feature set. The provided data contains all of the above variables: age, billing amount, blood group in numerical encoding, date of admission; additionally, various medical conditions Arthritis, Diabetes, Cancer, and more are mentioned by binary flags. While these features are structured, they can be processed using CNNs when represented as matrices or images, where spatial patterns and correlations can be explored. CNNs would interpret the structured input as a grid-like representation, so that the convolutional layers can identify patterns in the relationships between variables, like correlations between medical conditions and patient demographics.
For instance, billing amounts could show patterns with age or certain medical conditions, which the CNN’s convolutional and pooling layers can extract as hierarchical feature maps. These features could then be used as inputs for downstream tasks like classification, clustering, or regression. The extracted CNN features are combined with the insights provided by the correlation of the heatmap, allowing the model to understand not only linear relationships but also complex, nonlinear interactions between attributes. Such hybrid approaches will improve the predictive and analytical capabilities of models applied to medical datasets, leading to better decision-making and pattern discovery as shown in the Figure 9.
Performance assessment
In every statistical operation, the evaluation of the predictions is an important step. It is even more critical when forecasting ensemble models, when variability and varying levels of effectiveness ought to be thoroughly investigated. Every evaluation result is based on one of the 4 classifications. The correlation matrix is frequently employed to assess reliability in order to determine how good a predictive model performs. The framework’s precision has been assessed using (14).
Analysis of selected features using machine learning algorithms
Training and testing accuracy in DT algorithm
The Decision Tree algorithm, due to its memorization capability of training data, achieves high training accuracy in many instances. In this implementation, it reached near perfect training accuracy as 99.9%, and in splitting the training data into pure subsets, the tree splits it exactly. Testing accuracy, however, came out lower than this at approximately 83% which signifies overfitting. It does so because it captures noise and minor patterns, which do not generalize well to unseen data. Techniques such as pruning or limiting the tree depth may help reduce the discrepancy as shown in the Figure. 10.
Training and testing accuracy in LR algorithm
On the other hand, LR performed with a relatively well-balanced level. Its training accuracy was roughly 91% and testing accuracy was about 89%. This gives an idea that Logistic Regression performs better in generalizing to unseen data, even though it doesn’t necessarily represent more complex relationships compared to Decision Trees. These numbers represent the model complexity versus the generalization performance, and these are what give importance to model selection based on the needs of the problem to be solved as shown in the Fig. 11.
Outcome of AES encrypted data
AES encryption involves transforming sensitive health information, like patient files, medical images, and other health-related data, into a unreadable form by using a key. It utilizes symmetric encryption where the same key is used to encrypt and decrypt. Only users with the proper key will be able to access the data. AES is highly efficient and the strength of its encryption varies by key size—128, 192, or 256 bits. For health data, a minimum of 256-bit AES encryption is often recommended for good security. In any case, encryption ensures that sensitive health information is kept confidential in transit and at rest even if intercepted. In turn, unauthorized users will not be able to access or modify the data, which is very critical for maintaining patient privacy and compliance with data protection regulations such as HIPAA (Health Insurance Portability and Accountability Act) or GDPR (General Data Protection Regulation). Below is Table 2 that depicts how AES encryption works on healthcare data:
AES encryption time
The encryption time is the amount of time it takes for the data owner to convert the initial information into encrypted data. The encryption time of any technique is typically stated in milliseconds and is calculated using (11) as shown below:
Here, \(\:Enc,\:EncT,\:and\:EncST\) stand for the start, end, and start of the encryption, respectively. The amount of time spent during the encryption procedure is shown in Figure. 12. The graph is linear because encryption algorithms process data at a constant rate per MB; thus, time increases proportionally with data size.
Encryption time is one of the most crucial factors in any encryption system for performance evaluation. The table presented below shows how much time was taken to encrypt healthcare data with different sizes through the proposed Blockchain Technology with AES (BCT-AES) system. Here, as data size increases, the encryption time increases, but the rate is not linear, and it’s exponential. For small data sizes, for example, 1 MB, the encryption time is relatively short, that is, 10.5 ms. However, as the size of the data increases to 500 MB, the encryption time shoots up to 5120.3 ms. This exponential growth is the intrinsic computational complexity of the encryption operation, wherein multiple rounds of mathematical manipulations are performed to achieve the safety of the data. For instance, when the data size is increased from 1 MB to 5 MB, encryption time is increased from 10.5 ms to 50.3 ms; it gets increased almost five times as the data size is further increased and becomes more complicated for encryption procedures and hence, the higher it would demand high processing for secure and sound transfer. The trend also indicates that while AES is computationally very efficient, it is somehow inefficient concerning time complexity when it is used for handling large data. In real-life applications, however, this encryption time can be endured within the majority of real-time healthcare data scenarios where security must be paramount.
Outcome of AES decrypted data
When healthcare data must be accessed, the encrypted data has to be decrypted using AES. Decryption is done using the same crypto key used during encryption. AES decryption allows healthcare data to be restored to its original state, from where it can be read and used by the authorized staff. This means that only the holders of the correct decryption keys, in this case healthcare providers, are allowed to decrypt sensitive patient information. In health care, this is a significant step because doctors, nurses, and other staff are allowed access to important patient information at appropriate times, all the while being secure. The unauthorized access is restricted because the decryption keys are handled in a secure manner. Below is a Table 3 illustrating the AES decryption process:
AES decryption time
The amount of time required by the data user to decrypt the encrypted data is measured in milliseconds, and the decryption time is computed employing (12) as shown below.
Here DT denotes the time of decoding, ET denotes the time of encryption, and ST denotes the time of encryption. Figure. 13 represents the decryption time vs. during data size. This graph is linear because, for any increase in the amount of data, the decryption algorithm processes it at constant computational cost, thus increasing the time proportionally to the size.
Decryption time is as crucial as encryption time, since it dictates how fast the encrypted data can be accessed and processed when needed. The decryption time table presented here gives the time needed to decrypt different sizes of healthcare data in the BCT-AES system. As with encryption time, decryption time also grows with the increase in data size, which shows the computational work that needs to be done to undo the encryption process. For smaller sized data, like 1 MB, the decryption time is relatively fast, taking approximately 8.2 ms; however, it exponentially increases with the growth of data size to a maximum of 4613.8 ms for 500 MB data. The relationship between data size and decryption time is approximately exponential, like encryption time. This shows that the larger the data size, the greater number of operations need to be executed to decrypt data. For instance, when the data size is increased from 1 MB to 5 MB, the decryption time increases from 8.2 ms to 42.5 ms, a nearly fivefold increase. This trend goes on as the data size becomes bigger, signalling that with larger data sizes, computational time required increases in order to decrypt more data volumes. Even so, though for big data sets it takes longer, decryption times are comparatively efficient in the healthcare system context, where fast access and interpreting of data are needed for making decisions and managing patients.
Analysis of integrated patients records in blockchain technology for data security
Figure 14 illustrates an interface that is used to handle health care information, in this case, patient histories. It is simple to see that the key aspects of a patient’s history are the personal information like the patient’s name, address, birth date, gender, and contact details. The second part of the interface allows the medical practitioner to enter the symptoms, medications, and diagnostic procedures the patient needs. This modular structure facilitates a full-scale strategy for data collection; it guarantees an entire documentation of the treatment plan and the condition of the patient. Having this interface incorporated with blockchain technology will make sure that any sensitive information typed in is strongly encrypted prior to its storage. The data will be encrypted with the Advanced Encryption Standard that will ensure such information is not detectable by the unauthorized personnel and thus confidential. After encryption of data, posting of data to the blockchain becomes secure enough such that record can no longer be tampered and remains immutable.
As an illustration, when a physician put down the symptoms of the patient and proceeds to perform the available diagnostics, like X-rays or blood tests, the system encrypts the data and stores it in the blockchain with a uniquely different cryptographic hash. It achieves this through linking the data with a specific time which nobody can alter without their attention. Besides, blockchain is decentralized such that it removes the risk of centralization intrinsic with other data storage systems. It provides the ability to handle patient data in a way that is compliant with state laws like HIPAA. The integrity of data is ensured with likely protection against unauthorized access by the assurance of blockchain technology on the structure design. This convergence imagines a non-stop route to healthcare data management modernisation without jeopardising privacy and security.
Figure 15: Blockchain transaction table is an open and secure ledger of healthcare data in the blockchain system. In this, every row is a block in the blockchain, with key information such as block index, time, encrypted data, previous hash, hash, and verification status, structurally depicted how blockchain technology enhances integrity and security on healthcare data. The “Index” column generates a sequence number for each block, and the “Timestamp” generates the date and time of data entry so that traceability is ensured. The column “Data” generates the encrypted form of patient information, so confidentiality is maintained in the system. Based on the table given, by taking a truncated look at the given data, this privacy is being maintained while transparency to the reviewing users is being ensured.
The “Previous Hash” and “Hash” columns represent the crypto link between blocks. The data of each block combined with the hash of the prior block forms a chain of records, with each depending on the other. Any change in a single block has no meaning in the context of the entire chain and the system is tamper-evident. The Status column is also more informative as it informs the user about the information in a block, whether it is verified, pending, and failed. A Verified status will give the user an assurance that a block is authenticated and therefore secure. A Pending status informs the user that verification is being done. It shows the decentralization of blockchain: the data stored in it is stored in too many nodes and this reduces the chances of a single point of failure. This method ensures that patient data are immutable and secure and at the same time can be accessed in real time by the people who are authorized to do so via execution of blockchain in healthcare systems. The illustrative representation of the blockchain transactions also highlights the power of the system and simplifies it to understand and use by healthcare professionals. This table can then be an excellent tracker, auditor, and verifier of the integrity of the health record, and thus proves the clinical usefulness of blockchain technology in medical management of sensitive data.
Analysis of graph network structuring in healthcare
The tripartite network in the Fig. 16 presents the relationships between three different types of nodes: Patients (blue nodes), Episodes (red nodes), and Doctors (green nodes). It is a straightforward type of analysis to understand the relationships and connectivity between the healthcare system. The nodes are the entities, and the edges are the relationships between the entities. Patients are associated with episodes, i.e., patients are associated with some treatments or medical events. Episodes are associated with doctors, i.e., doctors are associated with the treated medical events. The formal structure will show how care transitions from individual to treatment episode and then to doctors who care for the patient. The graph is incredibly useful when considering patterns of care provision. For instance, Patient 1 is associated with Episode 1, which is associated with Doctor A. This illustrates a linear flow of care where Patient 1 is treated in Episode 1 by Doctor A. Similarly, Patient 2 has more than one episode, Episode 2 and Episode 3, and thus is associated with more than one doctor, Doctor B, Doctor C, and Doctor D. This is referred to as complex interactions, including shared care across episodes and providers. Color coding aids in readability: patients in blue, events in red, and doctors in green, with big node sizes and easy-to-read labels making it easy to read. The positioning, produced with a spring layout, leads to an aesthetically pleasing and informative display, reducing overlap and increasing readability. This graph can practically be applied to healthcare analytics with regard to referrals, optimal resource use, and maximizing patient-doctor engagement. Its basis is for more complex analyses of the networks, like in care coordination episode clustering, and doctor workload. This tripartite network points out the focus on the interaction between patients, episodes, and doctors to depict an informative model for the analysis and enhancement of the health-care delivery system.
Comparison of the encryption processing times for suggested and existing approaches
Table 4 displays a comparison of the encryption timings for recommended and current techniques. It has been proven that the recommended mechanism for the proposed method encrypts data more quickly than other techniques using currently available methodologies. With an average encryption duration of 1.12ms, the suggested BCT-AES approach outperforms AES-CP-IDABE (10.52ms), Enhanced AES (20.9ms), and AES-CBC (2.4ms) in terms of efficiency. This substantial encryption time reduction demonstrates the enhanced efficacy of the suggested method, indicating that it is a viable option for quick and safe healthcare data encryption.
The Fig. 17 that compares average encryption times for various encryption methods clearly indicates the differences in performance of traditional encryption algorithms and the BCT-AES approach. Among these, the well-known AES-CP-IDABE encryption standard has an average encryption time of 10.52 ms. The Enhanced AES algorithm, which provides modifications to the AES algorithm to increase its performance, takes 20.9 ms on average to encrypt, although it is very slightly increased due to the added security enhancements. One of the popular AES modes of operation, namely AES-CBC (Cipher Block Chaining), performs much better, with an average encryption time of 2.4 ms, making it the fastest among all the existing algorithms.
However, the Proposed BCT-AES approach has an excellent performance compared to all the others with a remarkable encryption time of 1.12 ms, which makes it the most efficient method in terms of speed. This is a better solution since it is an optimised blockchain technology and AES combination that not only enhances the level of security but also encryption speed. The suggested BCT-AES system is particularly better in low encryption time and thus has an advantage in its use in fields such as healthcare where prompt processing is virtually obligatory. Meanwhile, this fact demonstrates that, when security with blockchain is overlaid, it becomes achievable to implement faster-encrypting systems that can process sensitive patient data in real-time that is essential to healthcare applications. It is therefore true that it is one of the most reduction friendly encryption times in healthcare data security.
Table 5 lists approximate space complexity of various encryption algorithms for health data. AES-enhanced uses the most storage (18.4 MB) because of additional key and initialization vector overhead, while AES-CBC uses the least (10.2 MB). AES-CP-IDABE and our proposed BCT-AES use moderate storage (15.8 MB and 12.5 MB, respectively), with BCT-AES efficiently achieving encryption security and blockchain-based data integrity without consuming too much memory.
Comparison of the suggested BCT-AES framework to the time and space complexities as compared to the current methods. The new edition includes a comprehensive analysis of computational efficiency, which is backed up with empirical evidence and comparison tables in order to prove the superiority of the performance of the framework.
Two tables Table 4 (Time Complexity Evaluation) and Table 5 (Space Complexity Evaluation) have been included in this under Results and Performance Analysis section. These tables compare in detail the average encryption time and estimated space usage of the proposed Blockchain-based Advanced Encryption Standard (BCT-AES) system with three of the currently found encryption methods namely AES-CP-IDABE, Enhanced AES, and AES-CBC. All the methods were evaluated under the same experimental conditions with the same synthetic healthcare dataset and hardware setup in order to be benchmarked fairly.
Table 4 was a measure of the average encryption and decryption time (in milliseconds) when encrypting healthcare records with different sizes (ranging between 1 MB and 100 MB). The findings indicate that the mean encryption time of the proposed BCT-AES technique is reduced to 1.12 ms (as opposed to AES-CP-IDABE, 10.52 ms), Enhanced AES, 20.9 ms and AES-CBC, 2.4 ms). Such a significant enhancement is explained by the streamlined key scheduling algorithm embedded in the AES module and the parallel block encryption provided by the decentralized transaction processing of blockchain. Also, the CNN based feature classification step will be incorporated to make sure that the only sensitive data sets are being encrypted, thus allowing to reduce redundant computational load.
In Table 5, the comparison and evaluation of the storage and memory consumption of each encryption framework are given. The proposed approach of BCT-AES occupies an average space of 12.5 MB that is less than AES-CP-IDABE (18.3 MB) and Enhanced AES (21.7 MB), but relatively higher than AES-CBC (10.1 MB). The balance shows that BCT-AES is a trade-off between the small storage and high-quality encryption power. This middle ground consumption is mainly due to the distributed ledger mechanism of the blockchain that uplogs meta-data and hash values of each transaction to ensure irreversibility. Although there is this extra storage needs, the memory efficiency of this framework is within reasonable bounds of a real time healthcare application.
In order to supplement these empirical findings, a mathematical study of the complexity of algorithms, the expression of both time and space complexities in an asymptotic form. The encryption process of the BCT-AES is logarithmically optimized (O(n log n)) by the hierarchical key management structure, where n is the number of data block in the encrypted bits. The space complexity is modeled as O(n), which takes into consideration the linear increase in the number of entries in the ledger in the blockchain.
Altogether, this broadened assessment gives quantitative and theoretical rationales on the effectiveness of the suggested method. The results affirm that BCT-AES is not only a faster and less-computational cost encryption algorithm but high security and scalability are also guaranteed thus making it an appropriate algorithm in real-time healthcare information processing and transmission environments where performance and privacy are of utmost importance.
Discussion
The experimental results showed that the proposed architecture is effective to secure healthcare data and has produced a significant advancement in encryption time compared to others. The encryption time of proposed BCT-AES is 1.12ms on average and outperformed AES-CP-IDABE39 (10.52ms), Enhanced AES40 (20.9ms), and AES-CBC41 (2.4ms). with an encryption time 2.4ms. Fast data encryption is considered crucial for proper healthcare data safety. Graphical representations apart from encryption, allow insightful information concerning the patient-provider network, the age distribution and frequency of diseases within different ages groups that increase our understanding of health care dynamics. Making educated decisions on the features that are related becomes easy as the correlation matrix allows an elaborate understanding of all the inter parameters relationships. The performance evaluation results show that the decision tree has an excellent accuracy of 99% and logistic regression has an accuracy of 89% in predicting the outcome of healthcare data. The decision tree is 10% better than logistic regression, which shows its effectiveness in predicting healthcare data.
-
Hybrid Integration of Deep Learning, Encryption, and Blockchain: The greatest innovation of this study is the hybridization of CNN-based feature extraction and AES encryption and blockchain ledger mechanisms. Contrary to the conventional design in which data analytics and security are considered as separate layers, BCT-AES presents a cross-layer design that is seamless and the extracted medical features are directly connected to encryption and blockchain validation units. This integration is to ensure that sensitive health information is processed, classified, and secured in real-time without passing data between modules that are not secured and therefore limit exposure of vulnerability.
-
Optimized Encryption Efficiency through Structural Enhancement: The BCT-AES model adds an optimized AES encryption pipeline with parallelized block encryption and adaptive key scheduling that speeds up the processing of data. Such structural enhancement yields an average encryption time of 1.12 ms that is better than the comparative models like the AES-CP-IDABE (10.52 ms), Enhanced AES (20.9 ms), and AES-CBC (2.4 ms) when tested under the same conditions. These optimizations were made without impacting on the data confidentiality or integrity and this proves that the proposed optimization is not just a re-use of the algorithm, but a major performance driven improvement over the traditional AES implementations in health care systems.
-
Data-Driven Security Analytics using Hybrid Classification: This use of Decision Tree (DT) and Logistic Regression (LR) classifier takes over CNN-extracted feature representations of health-related data. The process of this layered analysis allows identifying and prioritizing sensitive data attributes prior to encryption that will enable the system to effectively distribute the resources of computation. Through risk-based data classification, the framework adds a data driven decision layer to the system, which increases encryption selectivity and generally increases the scalability of the system. The combination of predictive analytics and security systems is an innovative solution to adaptive and intelligence-driven encryption.
-
End-to-End Secure and Auditable Workflow: The BCT-AES model creates an entire pipeline involved in all steps of data processing data collection -preprocessing -feature extraction (CNN) -classification (DT and LR) - AES encryption - blockchain validation. This is an end-to-end design that warrants the authentication, evaluation of risk, encryption and verification of immutability of every healthcare data prior to the storage/transmission. The blockchain layer also increases transparency and trust through audit trail of every transaction through hash-based linkage and verification of the time stamps. This close-knit system is a major contrast to the modular architecture with loosely bound systems found in literature.
-
Practical Applicability and Scalability in Healthcare Environments: The design of the framework is specifically designed to be applicable in real-life healthcare settings and the design guarantees low latency, fault tolerance and data consistency even with the large-scale transaction demands. A thorough experimentation with artificial data simulating the MIMIC-III healthcare schema assured that the architecture is stable in terms of encryption rates and blockchain throughput over changing network conditions. It has a scalable structure and a consensus engine (Proof of Authority) that is energy efficient which is why it is applicable to hospital information systems, IoMT networks and telemedicine platforms, as it offers a realistic and deployable solution to the contemporary healthcare data ecosystems.
All these contributions together create a technically new and practically feasible method of healthcare data protection. The study does not involve the assembly of existing methods but a methodologically differentiated, cross-domain integration that brings together predictive analytics, cryptographic optimization, and decentralized validation into a unified, smart, and secure system. This leads to the production of a new paradigm of real-time and analytics aware encryption systems in healthcare, which links the gap between data intelligence and cyber defense.
The novel contributions and better performance justification of the new BCT-AES framework. The improved efficiency stems from synergistic combinations of various advanced techniques, as opposed to dependence on a sole method. As such, AES-256 encryption provides secure data confidentiality with negligible encryption and decryption times, whereas Blockchain technology provides immutable and tamper-proof storage that maintains data integrity. Concurrently, CNN-based feature learning combined with Decision Tree and Logistic Regression classifiers provides efficient processing of intricate healthcare data with enhanced predictive capability and ensured confidentiality. The most significant contribution of this research is the hybrid combination of these mechanisms, which overall optimize encryption speed, reduce computational overhead, and enhance general data security relative to classical AES-only or blockchain-only schemes. In addition, the framework is designed to meet low time-space complexity in order to enable real-time use and scalability in healthcare settings.
Conclusion and future work
This paper discusses an innovative approach in enhancing health-care cybersecurity, bringing together cutting-edge deep learning with the best encryption security by a blockchain. Based on this paper, utilizing the CNN feature-extracting tool and applying decision trees or logistic regression algorithms can classify the information accurately; however, its very flexible approach would be apt against the rising nature of ever-changing risks in a medical sector coupled with exponentially expanding medical data. The use of blockchain and encryption as the core features to safeguard private patient data demonstrates an unwavering commitment to maintaining data privacy and integrity at every stage across its lifecycle. Another aspect that points towards this commitment is the use of encrypted medical records by the organization with caution to avoid unauthorized access to confidential health information. In order to validate the strategic application of CNNs for feature extraction and LR and DT algorithms for data classification, performance metrics are carefully evaluated. The exceptionally high prediction accuracies of Decision Tree method 99% and Logistic Regression 89% very clearly show that the suggested approach is very effective in enhancing the cybersecurity in the healthcare institutions.
This work significantly enhances the security and resilience of modern healthcare practices digital infrastructure besides having marked a notable milestone in privacy protection for the patient. Toward improving accuracy in feature extraction and classification, work in the near future will increase the proposed cyber security framework. The advanced sophisticated deep learning architecture such as an RNN is considered along with attention processes are explored. It will be key to examine if blockchain technology is capable of scaling large-scale health care data systems and to solve the problems of interoperability with present health care platforms. Much more research will be needed to be done into the integration of strong identity management systems and possibilities of homomorphic encryption to protect the privacy of the data. Future research projects will involve continuous updating with respect to emerging cyberthreats, collaboration with industry partners, and actual applications to validate the effectiveness of the framework in a variety of healthcare settings.
Data availability
The datasets generated and/or analysed during the current study are available in the kaggle repository, www.kaggle.com/datasets/prasad22/healthcare-dataset.
References
Azzaoui, A. E. L., Chen, H., Kim, S. H., Pan, Y. & Park, J. H. Blockchain-based distributed information hiding framework for data privacy preserving in medical supply chain systems, Sensors, 22. https://doi.org/10.3390/s22041371 (2022).
Mohammed, D., Mariani, R. & Mohammed, S. Cybersecurity challenges and compliance issues within the U.S. Healthcare sector. Int. J. Bus. Social Res. 5 (2), 55–66 (2015).
Riesco, R., Larriva-Novo, X. & Villagra, V. A. Cybersecurity threat intelligence knowledge exchange based on blockchain. Telecommun Syst. 73 (2), 259–288. https://doi.org/10.1007/s11235-019-00613-4 (2020).
Kumari, A. et al. Jan., Blockchain-based peer-to-peer transactive energy management scheme for smart grid system, Sensors, 22, 13, Art. 13, https://doi.org/10.3390/s22134826 (2022).
Lee, D., Lee, S. H., Masoud, N., Krishnan, M. S. & Li, V. C. Integrated digital twin and blockchain framework to support accountable information sharing in construction projects. Autom. Constr. 127, 103688. https://doi.org/10.1016/j.autcon.2021.103688 (2021).
Dwivedi, S. K., Amin, R. & Vollala, S. Blockchain based secured information sharing protocol in supply chain management system with key distribution mechanism. J. Inform. Secur. Appl. 54, 102554. https://doi.org/10.1016/j.jisa.2020.102554 (2020).
Latif, S. A. et al. AI-empowered, blockchain and SDN integrated security architecture for IoT network of cyber physical systems. Comput. Commun. 181, 274–283. https://doi.org/10.1016/j.comcom.2021.09.029 (2022).
Yang, X. & Zhang, C. Blockchain-based multiple authorities attribute-based encryption for EHR access control scheme. Appl. Sci. 12, https://doi.org/10.3390/app122110812 (2022).
Yu, K., Tan, L., Aloqaily, M., Yang, H. & Jararweh, Y. Blockchain-enhanced data sharing with traceable and direct revocation in IIoT. IEEE Transactions on Industrial Informatics. 17 (11). 7669–7678. https://doi.org/10.1109/TII.2021.3049141 (2021).
Xu, Z. et al. Blockchain-aided searchable encryption-based two-way attribute access control research, Security and Communication Networks. e2410455. https://doi.org/10.1155/2022/2410455 (2022).
Geng, F. & Yu, L. Dynamic encryption method of personal privacy information in social network based on blockchain technology. Int. J. Web Based Communities. 18, 3–4. https://doi.org/10.1504/IJWBC.2022.125505 (2022).
Guo, K., Han, Y., Wu, R. & Liu, K. CD-ABSE: Attribute-based searchable encryption scheme supporting cross-domain sharing on blockchain, Wireless Communications and Mobile Computing, e6719302. https://doi.org/10.1155/2022/6719302 (2022).
Fan, Y. et al. TraceChain: A blockchain-based scheme to protect data confidentiality and traceability. Software: Pract. Experience. 52 (1), 115–129. https://doi.org/10.1002/spe.2753 (2022).
Neravetla, A. R., Nomula, V. K., Mohammed, A. S. & Dhanasekaran, S. Implementing AI-driven diagnostic decision support systems for smart healthcare, in 15th International Conference on Computing Communication and Networking Technologies (ICCCNT). 1–6. (2024).
Mohammed, A. S., Saddi, V. R., Gopal, S. K., Dhanasekaran, S. & Naruka, M. S. AI-Driven continuous integration and continuous deployment in software engineering, in 2nd International Conference on Disruptive Technologies (ICDT), 531–536. (2024).
Subbarayadu, A., Radhika, G. & Vedhavathi, R. Survey secured data transmission from WBAN to sink. Int. J. Comput. Sci. Mob. Comput. 5 (3), 431–444 (2016).
Uddin, M. A., Stranieri, A., Gondal, I. & Balasubramanian, V. Continuous patient monitoring with a patient centric agent: a block architecture. IEEE Access. 6, 32700–32726. https://doi.org/10.1109/ACCESS.2018.2846779 (2018).
Palas, M. J. U. & Bunduchi, R. Exploring interpretations of blockchain’s value in healthcare: a multi-stakeholder approach. Inform. Technol. People. 34 (2), 453–495. https://doi.org/10.1108/ITP-01-2019-0008 (2020).
Radanović, I. & Likić, R. Opportunities for use of blockchain technology in medicine. Appl. Health Econ. Health Policy. 16 (5), 583–590. https://doi.org/10.1007/s40258-018-0412-8 (2018).
Firdaus, A. et al. Root exploit detection and features optimization: mobile device and blockchain based medical data management. J. Med. Syst. 42 (6), 112. https://doi.org/10.1007/s10916-018-0966-x (2018).
Tanwar, S., Parekh, K. & Evans, R. Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inform. Secur. Appl. 50, 102407. https://doi.org/10.1016/j.jisa.2019.102407 (2020).
Thakur, S., Singh, A. K., Ghrera, S.& Elhoseny, M. Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimed Tools Appl. 78 (3), 3457–3470. https://doi.org/10.1007/s11042-018-6263-3 (2019).
Raisaro, J. L. et al. MedCo: enabling secure and privacy-preserving exploration of distributed clinical and genomic data. IEEE/ACM Trans. Comput. Biol. Bioinf. 16 (4), 1328–1341. https://doi.org/10.1109/TCBB.2018.2854776 (2019).
Fatima, A. & Colomo-Palacios, R. Security aspects in healthcare information systems: A systematic mapping. Procedia Comput. Sci. 138, 12–19. https://doi.org/10.1016/j.procs.2018.10.003 (2018).
Mohurle, S. & Patil, M. A brief study of wannacry threat: ransomware attack 2017. Int. J. Adv. Res. Comput. Sci. 8 (5), 1938–1940 (2017).
Berghel, H. Equifax and the latest round of identity theft roulette. Computer 50 (12), 72–76 (2017).
Sills, M., Ranade,& Mittal, S. Cybersecurity threat intelligence augmentation and embedding improvement - a healthcare usecase, in IEEE International Conference on Intelligence and Security Informatics (ISI), 1–6. https://doi.org/10.1109/ISI49825.2020.9280482 (2020).
Alapati, N. K. & Dhanasekaran, S. Addressing data quality and consistency issues in cloud-based big data environments, in 2025 International Conference on Networks and Cryptology (NETCRYPT), IEEE,458–462. (2025).
Dey, I. Computer-Mediated Communication (BoD – Books on Demand, 2022).
Parikesit, A. A., Ratnasari, N. R.& Anurogo, D. Application of artificial intelligence-based computation in the health sciences to ward off the COVID-19 pandemic. Int. J. Hum. Health Sci. 5 (2), 177. https://doi.org/10.31344/ijhhs.v5i2.256 (2020).
Siyal, A. A. et al. Applications of blockchain technology in medicine and healthcare: challenges and future perspectives, Cryptography, 3 (1), https://doi.org/10.3390/cryptography3010003 (2019).
Lee, D. & Yoon, S. N. Application of Artificial intelligence-based technologies in the healthcare industry: opportunities and challenges, International Journal of Environmental Research and Public Health, 18 (1). (2021). https://doi.org/10.3390/ijerph18010271
Sharma, N. & Shambharkar,G. Towards secure healthcare: SA-GBO-ODBN model utilizing blockchain and deep learning for data handling and diagnosis. The Comput. Journal, bxaf. 45, (2025).
Sharma, N. & Shambharkar,G. Transforming security in internet of medical things with advanced deep learning-based intrusion detection frameworks. Applied Soft Computing. 113420, (2025).
Sharma, N. & Shambharkar,G. Multi-layered security architecture for IoMT systems: integrating dynamic key management, decentralized storage, and dependable intrusion detection framework. International J. Mach. Learn. Cybernetics. 1–48, (2025).
Sharma, N. & Shambharkar,G. Multi-attention deepcrnn: an efficient and explainable intrusion detection framework for internet of medical things environments. Knowledge Inform. Systems. 1–67, (2025).
Patil,& Healthcare Dataset [Online]. Available: https://www.kaggle.com/datasets/prasad22/healthcare-dataset (2024).
Ali, A. et al. An industrial IoT-based blockchain-enabled secure searchable encryption approach for healthcare systems using neural network. Sensors 22 (2), 572 (2022).
Chandel, S., Yang, G. & Chakravarty, S. AES–CP–IDABE: A privacy protection framework against a DoS attack in the cloud environment with the access control mechanism. Information 11 (8), https://doi.org/10.3390/info11080372 (2020).
Gupta, M. & Sinha, A. Enhanced-AES encryption mechanism with S-box splitting for wireless sensor networks. Int. j. inf. Tecnol. 13 (3), 933–941. https://doi.org/10.1007/s41870-021-00626-w (2021).
Lee, S. W. & Sim, K. B. Design and hardware implementation of a simplified DAG-Based blockchain and new AES-CBC algorithm for IoT security. Electronics 10 (9), https://doi.org/10.3390/electronics10091127 (2021).
Author information
Authors and Affiliations
Contributions
Pokuri venkataradhakrishnamurty wrote the main manuscript text and k. Malathi prepared Figs. 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16 and 17. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Consent to publish
All the authors gave permission to Consent to publish.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Venkataradhakrishnamurty, P., Malathi, K. A holistic framework for strengthening security of healthcare data through encryption utilizing blockchain technology. Sci Rep 16, 2008 (2026). https://doi.org/10.1038/s41598-025-31698-4
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-31698-4