Abstract
The advances in the Internet of Things (IoT) involve a technology of interconnected devices that interact over the internet, providing convenience and efficiency while also posing significant security risks. Privacy-preserving techniques play a vital role in safeguarding sensitive user data while maintaining system efficiency. The rising tendency of cybersecurity threats and the need to recognize harmful activities in heterogeneous but resource-constrained settings have led to the development of sophisticated intrusion detection systems (IDSs) for quickly identifying intrusion efforts. Conventional IDSs are becoming more inefficient in classifying new attacks (zero-day attacks) whose designs are similar to any threat signatures. To reduce these restrictions, projected IDS depend on deep learning (DL). Due to DL techniques learning from vast amounts of data, they can identify novel, emerging attacks, making them an alternative method to classical cybersecurity. This study proposes an Optimised Multi-Head Self-Attention Model for an Intelligent Intrusion Detection Framework Using Plant Rhizome Growth Optimisation (OMHSA-IDPRGO) method to advance IoT security. The primary focus is on developing an automated cyberattack detection system for an IoT environment by employing advanced techniques. Initially, the mean normalization process is used to measure input data into a structured format. Furthermore, the Crayfish Optimisation Algorithm (COA) is used for optimal feature subset selection, identifying the most relevant features from the dataset. For the cybersecurity detection process, the OMHSA-IDPRGO method uses a hybrid model that encompasses a convolutional neural network and a bidirectional gated recurrent unit with a multi-head self-attention mechanism (CNN-BiGRU-MHSAM) technique. Finally, the hyperparameter selection is performed using the plant rhizome growth optimization (PRGO) approach to enhance classification performance. The experimentation of the OMHSA-IDPRGO model is examined under Edge-IIoT and ToN-IoT datasets. The comparison study of the OMHSA-IDPRGO model showed superior accuracy values of 99.11 and 99.18% compared to existing techniques on the dual datasets.
Similar content being viewed by others
Introduction
Advances in the IoT relate to a system of physical entities, tools, automobiles, and other components equipped with electronic hardware, circuits, sensors, software, and internet connectivity that enable these elements to gather and share information1. The IoT permits these items to be monitored and managed remotely through available network setups, generating possibilities for tighter connection of the physical environment with digital platforms, ultimately leading to enhanced performance and precision2. The IoT stands as a ground-breaking advancement that signals the future of digital technology and communication, and its progress relies on evolving technical breakthroughs in numerous key areas, including wireless detection systems and nanoscale technologies. The IoT concept offers an infinite amount of availability, accessibility, scalability, integrity, confidentiality, and other benefits related to connected devices3. Nevertheless, IoT devices are vulnerable to cyber threats due to a combination of numerous potential vulnerabilities and their relative novelty, resulting in the absence of established security norms and protocols. A broad spectrum of cyber threats is employed against IoT systems, based on the specific component being targeted and the attacker’s objectives4.
However, the deployment of IoT systems has also introduced several significant cybersecurity challenges, where loopholes and unauthorized access to information and critical infrastructure have become major concerns5. The IoT represents a global web of smart devices connected to the internet without human intervention, which is beneficial yet prone to cyberattacks, like any conventional system. Studies focus on integrating machine learning (ML)- driven solutions with IoT. An IDS is a reliable method for identifying cyberattacks within any system6. Many modern IDS frameworks employ ML models to detect cyber threats in the system. This IDS alerts the network administrator about any doubtful behaviour occurring within the network and therefore serves as an information security mechanism that blocks harmful intrusions7. An intrusion occurs when an individual gains unauthorized entry to, or manipulates data assets with malicious intent. A tangible entity aiming to extract information unlawfully, cause harm to others, or perform malicious tasks is referred to as a cybercriminal or an intruder8. Figure 1 denotes the general architecture of IDSs in IoT.
Cybersecurity threats have expanded rapidly in several fields, including healthcare, smart homes, agriculture, energy, industrial processes, and automation. Due to its extensive range of services, IoT sensors generate vast volumes of data, which necessitate privacy, security, and authentication9. Previously, classical techniques were used to ensure IoT security. The employment of more artificial intelligence (AI) techniques for identifying cybersecurity threats has become increasingly popular over time. Consequently, there is a substantial body of investigation concentrated on IoT cybersecurity10. This encompasses AI strategies for safeguarding IoT systems against threats, typically by detecting abnormal activities that could indicate an ongoing attack. As interconnected devices are widely utilized in various sectors, they have created a demand for smarter environments and automated processes. However, this growth is accompanied by increasingly advanced security threats, which may compromise data integrity and user privacy. Efficient threat detection methods that can operate in real-time and on resource-constrained devices are urgently required. Improving security while maintaining system performance is significant to unlocking the full potential of connected technologies. This drives the development of innovative, optimized models that balance accuracy, interpretability, and privacy protection in intrinsic network environments.
This study proposes an Optimised Multi-Head Self-Attention Model for an Intelligent Intrusion Detection Framework Using Plant Rhizome Growth Optimisation (OMHSA-IDPRGO) method to advance IoT security. The primary focus is on developing an automated cyberattack detection system for an IoT environment by employing advanced techniques. Initially, the mean normalization process is used to measure input data into a structured format. Furthermore, the Crayfish Optimisation Algorithm (COA) is used for optimal feature subset selection, identifying the most relevant features from the dataset. For the cybersecurity detection process, the OMHSA-IDPRGO method employs a hybrid model that encompasses a convolutional neural network and a bidirectional gated recurrent unit with a multi-head self-attention mechanism (CNN-BiGRU-MHSAM) technique. Finally, the hyperparameter selection is performed using the plant rhizome growth optimization (PRGO) approach to enhance classification performance. The experimentation of the OMHSA-IDPRGO model is examined under Edge-IIoT and ToN-IoT datasets. The key contribution of the OMHSA-IDPRGO model is listed below.
-
The OMHSA-IDPRGO method applies mean normalization during pre-processing to convert raw input data into a uniformly scaled format, thereby improving consistency across features. This enhances training stability and learning efficiency. It also assists in better convergence during model optimization.
-
The OMHSA-IDPRGO approach utilizes the COA technique to identify the most relevant features, effectively mitigating dimensionality while preserving crucial data. This selection improves detection accuracy and mitigates computational complexity. As a result, the model becomes more efficient and reliable in processing IoT data.
-
The OMHSA-IDPRGO methodology employs a hybrid CNN-BiGRU architecture integrated with the MHSAM model for capturing intrinsic temporal and spatial patterns in IoT network data. This enhances the model’s ability to detect a wide range of cyber threats accurately. It significantly improves intrusion detection performance in dynamic environments.
-
The OMHSA-IDPRGO technique implements the PRGO model to fine-tune hyperparameters, improving learning efficiency and predictive accuracy automatically. This optimization reduces manual tuning efforts and accelerates convergence. Consequently, it enhances overall model performance in complex IoT scenarios.
-
The integration of COA-based FS with the CNN-BiGRU-MHSAM model, optimized through PRGO, presents a novel and efficient solution for intelligent threat detection. This incorporation uniquely balances dimensionality reduction, deep temporal-spatial feature extraction, and automated hyperparameter tuning. It significantly improves detection accuracy and computational efficiency in complex IoT environments, setting it apart from existing methods.
Related works
Alzahrani11 proposed a gorilla troops optimizer and DL-assisted BAD (GTODL-BADC) method. This method utilizes feature selection (FS) in conjunction with fine-tuned DL-aided classification to achieve security within the IoT landscape. The min–max data normalization technique was employed for data pre-processing, and the GTO framework for FS selects the optimal feature subclasses. Furthermore, the multi-head attention-driven LSTM model is used for BAD. Sekhar et al.12 provided an effective model for identifying and classifying cyber intrusions. The authors employed a new model with honeybees mating optimization (HBMO) and stochastic gradient boosted distributed decision trees (SGB-DDT) techniques. To advance the recognition precision, an SGD-DDT is a learning approach that is effective and scalable. Alotaibi13 suggested an innovative structure, which integrates DL, blockchain (BL), and software-defined networking (SDN) technologies for improving IoT cybersecurity. This study aims to identify a potential method for forming a cybersecurity system for IoT-enabled smart settings to safeguard data privacy, identify appropriate threats, and secure financial transactions. The suggested method is an amalgamation of numerous state-of-the-art techniques. The SDN control plane incorporates the SE-driven Bi-LSTM approach for traffic management. In14, a smart IDS model is presented for identifying cyber threats in the IoAT. The presented model utilizes the downsized kernel partial least squares (DKPLS) and reduced kernel approach for extracting and reducing data features to improve the recognition efficiency. This DRKPLS technique was employed to reduce the dimensions of the kernel matrix produced by the kernel partial least squares (KPLS) model by selecting relevant features. In15, the Ant Colony-Optimised Artificial Neural-Adaptive Tensorflow (ACO-ANT) approach was recommended for identifying suspicious software. To highlight the importance of tokens in source duplicate data, the noise data underwent processing by weighted attribute and tokenization approaches. DL methods are later deployed for detecting source code duplication. Aljebreen et al.16 developed a new DDoS attack detection method using the snake optimizer and ensemble learning (DDAD-SOEL) technique in the IoT landscape. The motivation behind this method lies in the effective and automatic detection of DDoS attacks. To fulfil this, the created method leverages the SO procedure for selecting a feature subset.
Kumar et al.17 combined SDN, digital twin (DT) BC, and DL techniques in the SG network structure. Specifically, a secure communication network was initially established using an authentication model based on BC technology, which mitigates some identified security threats. Then, a different DL design, which contains a softmax classifier, Bi-GRU, and a self-attention mechanism, is proposed to enhance the threat recognition step in SG networks. In18, an advanced cybersecurity framework assisted in trucking the heuristic process was introduced with three methodologies: improved virtual honeypot (IVHD), IDS, and hidden Markov models (HMM) for segmenting devices into four diverse stages based on their planned task, and observing communication traffic to identify suspicious edge devices. Saheed, Misra, and Chockalingam19 proposed a model by using an autoencoder with a deep convolutional neural network (DCNN) and long short-term memory (LSTM) for feature reduction and anomaly detection in Industrial Control Systems (ICS), enabling accurate, low-cost, and real-time cyber-attack detection. Thayalan et al.20 presented a collaborative federated learning framework with edge-cloud architecture using the two-stage attention integrated graph-based multi-source spatio-temporal data fusion (2S-AGMSTDF) network, including Attention-based LSTM, attention-based knowledge graph convolutional network (AKGCN), and graph convolutional network-residual network-based transformer (GCN-ResNet Transformer or GRCMT) method to enhance accurate, scalable, and privacy-preserving predictive security in IoT consumer applications. Saheed, Abdulganiyu, and Ait Tchakoucht21 presented a framework that integrates a modified genetic algorithm (MGA) model for feature selection with a deep LSTM network, optimized via a genetic algorithm (GA) for hyperparameter tuning, to efficiently detect cyberattacks in IoT networks within an edge computing environment. Kumar, Jolfaei, and Islam22 proposed a DL-based threat hunting framework (DLTHF) technique by using an LSTM contractive sparse autoencoder (LSTM-CSAE) model for feature extraction and a multi-head self-attention bidirectional recurrent neural network (MhSaBiGRNN) methodology for accurate cyber threat detection in Software Defined-IoT (SD-IoT) networks. Paul et al.23 presented a model to enhance cybersecurity in deep web environments, utilizing a novel framework that integrates federated learning (FL), graph-based analysis, and a hybrid web crawler with an ontology-based scoring system to detect threats and safeguard sensitive data across cloud, fog, and edge systems.
Kathole et al.24 developed a secure attack detection framework for Vehicular Ad-Hoc Networks (VANETs) using a modernized random parameter-based green anaconda optimization (MRP-GAO) model for feature selection and an ensemble ML model (EMLM) integrating multi-layer perceptron (MLP), support vector machine (SVM), AdaBoost, and Bayesian network for effective intrusion detection and classification. Amer, Al-Rimy, and El-Sappagh25 proposed the Modbus-NFA Behaviour Distinguisher (MNBD) model, which applies a non-deterministic finite automaton (NFA) framework to analyze Modbus frame sequences and identify abnormal device behaviour with high accuracy and generalization. Sardar et al.26 introduced a model by using a graph neural network (GNN) model trained on various datasets and evaluated via NS2 simulations. Kathole et al.27 presented an ensemble DL model (EDLM) technique that integrates multiple DL models to improve detection accuracy, reduce false alarms, and strengthen network security by averaging prediction scores for robust anomaly detection. Saheed and Chukwuere28 developed a robust cyber-attack detection system for cyber-physical industrial IoT (CPS-IIoT) that utilizes the Pearson correlation coefficient and agglomerative clustering for privacy preservation, as well as a bidirectional LSTM with scaled dot-product attention (BiLSTM-SDPA) method for accurate threat detection. Kathole et al.29 developed a secure federated cloud storage system for Internet of Medical Things (IoMT) using a hybrid Mexican axolotl with energy valley optimizer (HMO-EVO)-based attribute-based encryption (ABE) for secure data encryption and multi-scale bi-long short-term memory and gated recurrent unit (MBiLSTM-GRU) technique with FL for accurate disease prediction. Saheed, Omole, and Sabit30 developed a model using a genetic algorithm with an attention mechanism and a modified adaptive moment estimation optimized LSTM (GA-mADAM-IIoT) methodology, incorporating explainability via Shapley Additive Explanations (SHAP). Saheed and Chukwuere31 developed an explainable AI (XAI) ensemble transfer learning (TL) model using SHAP and a hybrid bidirectional long short-term memory with autoencoders (BiLAE) technique for zero-day botnet attack detection, optimized by barnacle mating optimizer (BMO). Saheed and Misra32 presented an explainable and privacy-preserving deep neural network (DNN) framework with SHAP for accurate and interpretable anomaly detection in Cyber-Physical Systems enabled IoT (CPS-IoT) networks. Ullah et al.33 developed SecNet-FLIDS, a Blockchain-based FL model with a TOP-K Node selection scheme and context-aware transformer networks, incorporated with synthetic minority over-sampling technique (SMOTE) and edited nearest neighbours (ENN) for imbalanced data handling, to enable accurate, privacy-preserving, and scalable cyberattack detection in the Internet of Vehicles (IoV).
Despite various advanced methods, such as GTO, HBMO, Bi-LSTM, and FL, being applied across IoT, CPS-IIoT, IoV, and SDN environments, several limitations still exist. Various models rely on large, labelled datasets, which are often scarce or imbalanced, thereby affecting detection accuracy and generalizability. Trust among users and security experts is reduced as few models suffer from interpretability issues. Furthermore, various solutions lack scalability or are computationally intensive, which restricts their real-time deployment on resource-constrained edge devices. The integration of multiple technologies, such as BC, DL, and optimization algorithms, remains complex, resulting in increased system overhead. The research gap in addressing these challenges lies in developing lightweight, explainable, and privacy-preserving IDS that efficiently handle imbalanced data, optimize feature selection, and adapt to heterogeneous IoT and CPS environments with minimal human intervention.
Methodology
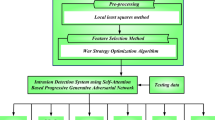
This study designs and develops an OMHSA-IDPRGO model to advance IoT security. The primary focus of this novel is to enhance automatic cyberattack detection in IoT environments by employing advanced techniques. To achieve this, the OMHSA-IDPRGO technique contains numerous stages, namely data pre-processing, FS, classification model, and parameter tuning process. Figure 2 signifies the overall working flow process of the OMHSA-IDPRGO technique.
Mean normalization
To achieve this, the proposed method initially executes a mean normalization method to transform the input data into a structured format34. This normalization is chosen due to its effective capability in scaling features to have a mean of zero, which assists in stabilizing and speeding up the training process of ML models. This method mitigates the impact of outliers by centring the data around zero without strictly bounding it within a fixed range. This enhances gradient descent convergence, especially in DL methods, by preventing features with large magnitudes from dominating the learning process. Additionally, mean normalization maintains the relative distribution of data, which is significant when dealing with complex IoT datasets. Overall, it presents a balanced approach that enhances model stability and accuracy compared to simpler scaling techniques.
This method signifies a frequently implemented data normalization model in data analysis and ML domains. It comprises scaling the data so that the mean (average) of the feature becomes 0. This procedure focuses on the data around the mean, effectually extracting some bias in the value of features. A feature \(x\)’ is specified:
Now, \(\text{min}\left(x\right)\) and \(\text{max}\left(x\right)\) signify the minimal and maximal values of \(x\), and \(mean(x)\) depicts the mean of feature \(x\).
FS using COA model
Next, the COA approach is employed for the optimal selection of feature subsets35. This model is chosen for its robust global search capability and effective balancing. This technique also avoids local optima, ensuring the selection of the most relevant and informative features. Its bio-inspired nature allows it to adapt dynamically to complex, high-dimensional IoT datasets, enhancing feature relevance and mitigating redundancy. Furthermore, COA requires relatively low computational resources, making it appropriate for real-time applications. Overall, COA improves detection accuracy and model efficiency better than many conventional FS models. The mathematical model for the optimization issue is developed by considering the natural behaviours of crayfish at diverse phases. COA is a metaheuristic swarm intelligence model. The significant stages of COA are given.
Initialize population
During this initial stage of the model, the crayfish population is described as a matrix \(X\), where \({X}_{i}\) \(({X}_{i}=\left\{{X}_{i,1}, {X}_{i,2},\dots ,{X}_{i,dim}\right\},\) with \(dim\) depicting the dimension) indicates the location of \({the l}^{th}\) crayfish. Every \({X}_{i}\) is constrained within a predefined boundary and represented as a \(1\times dim\) vector, equivalent to a possible solution. The function \(f\left(\cdot \right)\) is presented to assess \({X}_{i}\), offering its fitness value. According to the size of population \(N\) and dimension \(dim\), the COA initializes the procedure by arbitrarily generating a set of candidate solutions \(X\). The location of individual \(i\) in dimension \({X}_{\text{i},\text{j}}\cdot\) is specified:
Here, \(u{b}_{j}\) and \(l{b}_{j}\) refer to the upper and lower bounds, respectively, while \(rand\) indicates an arbitrary value.
Define temperature
Temperature variations influence the behaviour of crayfish, prompting them to enter various phases. The temperature is specified:
While the ambient temperature ranges from 15 to 30 °C, particularly at 25 °C, crayfish display searching behaviour. The feeding amount is assessed by employing the expression specified in Eq. (4).
Here, \(\mu\) depicts the optimum feeding temperature. The crayfish’s food intake is influenced by the parameters \({C}_{1}\) and \(\sigma\), and set to 3 and 0.2, respectively.
Summer resort and competition stage
The temperature \(temp\) is greater than 30 during these dual stages, and the cave \({X}_{shade}\) is deliberated as:
Now, \({X}_{L}\) and \({X}_{G}\) refer to the optimal locations attained through iterative calculations for individuals and populations.
While \(rand<0.5\), no other individuals participate in the competition, and the crayfish immediately enters the cave, upgrading its location.
Now \(t\) and \(t+1\) indicate the next and existing iteration stages. \({C}_{2}\) is specified:
Here, \(T\) specifies the upper limit of iterations. While rand \(\ge 0.5\), other individuals are also interested in the cave, inducing competition, and their locations are upgraded accordingly.
Now, \(z\) refers to an arbitrarily selected individual from the population.
Foraging stage
During this phase, the temperature does not exceed 30 °C, and the crayfish will evaluate the dimensions of the food after positioning it and select diverse feeding approaches. The position of food \({X}_{food}\) is specified:
The size of food \(Q\) is given:
Here, \(fitness_{i}\) and \(fitness_{food}\) represent the fitness values of the crayfish and the food, respectively. \(C_{3}\) represents the food factor, set to a value of 3, correspondingly. The crayfish will assess the size of the food based on its type. While \(Q > \left( {C_{3} + 1} \right)/2\), it specifies that the food is huge, inducing the crayfish to tear it apart, utilizing its primary claw foot.
Once the food is torn apart and turns small, the preceding dual paws will alternatively pinch the food to consume it. This alternative approach is designed by integrating \(sine\) and \(cosine\) functions. Additionally, food diversity is achieved by simulating the feeding behaviour of the animals.
While \(Q \le \left( {C_{3} + 1} \right)/2\), the crayfish might instantly move towards the nutrition and upgrade its location:
Due to its simplicity, fast convergence speed, and higher computational efficiency, the COA is used to address the SRB optimizer concern.
The fitness function (FF) determines the classifier’s precision and the various features chosen. It increases the classifier’s precision and decreases the size of the desired feature set. Thus, the subsequent FF is used to evaluate different solutions presented in Eq. (15).
Here, \(ErrorRate\) signifies the rate of classification errors using the chosen features. \(ErrorRate\) is computed as the percentage of improperly classified instances to the total number of classifications made, expressed as a value between 0 and 1. \(\#SF\) is the number of chosen aspects, and \(\#All\_F\) is the total number of attributes in the original dataset. \(\alpha\) is utilized to control the significance of subset length and classifier quality.
Hybrid classification model
For the cybersecurity detection process, the hybrid model, named CNN-BiGRU-MHSAM, is used36. This technique is chosen for its ability to capture both spatial and temporal patterns in complex IoT network data. CNN layers outperform in extracting local features, while BiGRU handles long-term dependencies in sequential data. The addition of the MHSAM improves the capability of the technique in concentrating on the most relevant parts of the input, enhancing detection accuracy. Compared to standalone models, this hybrid approach mitigates overfitting and increases robustness against diverse cyber threats. It also presents better interpretability and scalability, making it superior to conventional ML and simpler DL methods. Figure 3 represents the structure of the CNN-BiGRU-MHSAM technique.
CNN reduces the parameter counts and sizes of the data by removing spatial features from the input data through methods such as pooling, weight sharing, and local connections. These processes improve the analytical capabilities and computational efficiency of the CNN. The network includes pooling, input, output, convolutional, and fully connected (FC) layers. As a fundamental module of CNNs, the convolutional process focuses on capturing spatial relationships and various patterns. This framework combines dual convolutional components—the first layer uses 16 \(3{\text{x}}3\) kernel filters, whereas the subsequent layer uses 32 \(3{\text{x}}5\). dimensional matrices to analyze the combined input resources. The pooling layer decreases the input data dimensionality, improving CNN calculation speed and alleviating overfitting. Normal pooling techniques include stochastic pooling, max pooling, and mean pooling. The FC layer connects every neuron to each neuron in the previous layer.
The GRU method effectively transfers its capability to process time-series data, successfully addressing problems such as exploding and vanishing gradients. In comparison with LSTM, the GRU requires fewer parameters, provides faster training, and reduces overfitting, making it particularly effective for time-series prediction. This method is primarily composed of two segments: the gate of reset \(r_{t}\) and the gate of update \(z_{t}\). The data processing process executed by the GRU model is as demonstrated:
-
(i)
The update gate \(z_{t}\) controls the extent to which the data from the preceding instant is preserved at present moments. The greater the update gate’s output value \(z_{t}\), the additional data from the prior instant is preserved. The evaluation equation of the update gate \(z_{t}\). is as stated in Eq. (16).
$$z_{t} = \sigma \left( {w_{z} \cdot \left[ {h_{{t - 1^{\prime}}} x_{t} } \right] + b_{z} } \right){ }$$(16)Here, \(\sigma \left( \cdot \right)\) refers to the sigmoid function, \(w_{z}\) denotes the update gate weight, \(h_{t - 1}\) signifies the hidden layer (HL) of the preceding moment, \(x_{t}\) stands for the present moment input, and \(b_{z}\). Means the bias value.
-
(ii)
The reset gat \(r_{t}\). Controls the extent to which the data from the preceding moment is maintained on the present moment candidate HL \(\tilde{h}_{t}\). The greater the reset gate’s output value, s \(r_{t}\). The more additional data from the prior instant is kept in the candidate HL, \(\tilde{h}_{t}\). The prediction formula for the reset gate, \(r_{t}\), is represented in Eq. (17).
$$r_{t} = \sigma \left( {w_{r} \cdot \left[ {h_{{t - 1^{\prime}}} x_{t} } \right] + b_{r} } \right)$$(17)N, \(w_{r}\). denot reset gate weight, and \(b_{r}\) signifies bias value.
-
(iii)
The upgrade of the ndidate HL information \(\tilde{h}_{t}\) is as stated in Eq. (18).
$$\tilde{h}_{t} = tanh\left( {w_{h} \cdot \left[ {r_{t} \odot h_{t - 1} , x_{t} } \right] + b_{h} } \right)$$(18)Whereas, \(tanh\left( \cdot \right)\) symbolizes activation function, \(w_{h}\) characteristics ndidate HL weight, and \(b_{h}\) denotes bias value of the candidate HL.
-
(iv)
Compute the present moment HL \(h_{t}\) according to \(\tilde{h}_{t}\) and \(h_{t - 1}\):
$$h_{t} = \left( {1 - z_{t} } \right) \odot h_{t - 1} + z_{t} \odot \tilde{h}_{t}$$(19)
This model successfully takes the forward characteristics. Nevertheless, time series data are also affected by previous data, not only upcoming values. To address either forward or backwards dependencies, the BiGRU model is presented. This method combines either forward or backwards GRU elements to well-examine the relationships in time-series data. This model comprises a forward GRU, an input, an output and a reverse GRU. The forward and reverse GRUs extract data from the relevant reverse and forward sequences of the input data.
Here, \(\vec{w}\) and \(\mathop{w}\limits^{\leftarrow}\). represent output weights of the forward and backwards GRU HLs, individually, and \(b_{t}\) denotes the bias value of the Bi-GRU method.
The MHSA model creates numerous data sequences by using dissimilar linear projections. Every prediction, or “head”, captures different data features. These sequences are then concatenated and passed through additional linear projections to form the final sequence. For the input sequence of data \(X = \left[ {x_{1} , x_{2} , x_{3} , \cdots , x_{m} } \right]\), multiply the put sequence of data by the matrices of linear transformation \(W_{j}^{Q} ,\) \(W_{j}^{K}\), and \(W_{j}^{V}\), correspondingly, to get the vectors \(Q_{j} ,\) \(K_{j}\), and \(V_{j} ,\) \(j \in \left( {1,2,3, \cdots , N} \right)\), and \(N\) characterizes head counts. The particular computation procedure is presented in Eqs. (23–25).
Formerly, the attention computation equation of the \(jth\) head is presented in Eq. (26).
The output is measured by Eq. (27).
Now, \(W^{o}\) refers to the output weighted matrix. Table 1 describes the key parameters utilized in the CNN-BiGRU-MHSAM model.
PRGO-based parameter tuning model
Finally, the hyperparameter range is implemented by the PRGO approach37. This model is chosen for its effective global search capability, motivated by the natural rhizome growth patterns. This model helps avoid local minima and find optimal hyperparameter values, thereby efficiently balancing the exploration and exploitation phases. Compared to conventional tuning methods, such as grid or random search, PRGO requires fewer iterations and computational resources while achieving better convergence. Its adaptability to complex, high-dimensional search spaces make it ideal for optimizing DL techniques in IoT environments. Overall, PRGO enhances model accuracy and training speed, outperforming many conventional optimization techniques.
In this paper, a method is required to model plant rhizome growth and explain the fundamental meaning of five terms: soil space, adventitious, fibrous, lateral, and primary roots, in the context of root system development. Indeterminate and fibre roots serve as searching agents within the solution area and represent primary elements to discover the solution area. Lateral roots stimulate development by combining food absorbed by earlier fibre roots with nutrients taken up by the fibre roots. The primary root stimulates development by combining nutrition formerly absorbed by lateral and fibre roots with food intake by now evolving fibre roots.
Numerical growth method for taproot plants
Assume that taproot plants arbitrarily have \(N\) fibrous roots, signified by \(\left( {\left\{ {X_{1} ,X_{2} \ldots ,X_{N} } \right\}} \right)\). Fibrous roots additionally absorb nutrients from the soil, apart from exploring the nutrition‐rich parts of the soil individually; therefore, all fibrous root is considered as an experimental solution to the optimization issue, and the consistent soil region is observed as the solution area of the targeted problem.
-
1.
The numerical representation of fibrous root growth.
whereas \(Seed_{1}\) denote \(ith\) fiber root at the \(tth\) growth time, \(X_{best}\) signifies the optimal fiber root \(,r_{1}\) refers to randomly generated numbers amongst \(\left( {1, N} \right)\), \(X_{r1}^{t}\) signifies the fiber root ars, \(\alpha_{1} \in 2 \times rand\left( {0,1} \right) - 0.5\) denote randomly generated number applied to produce \(\left( { - 0.5,1.5} \right)\) intervals, if \(\alpha_{1} \in \left( {0,1.5} \right)\), it means that the arbitrarily chosen fiber root \(X_{r1}^{t}\) advance to the historic finest fiber root \(X_{best}\), and if \(\alpha_{1} \in \left( { - 0.5,0} \right)\), then \(X_{best}\) develops to \(X_{r1}^{t}\). The model of this searching mechanism, in addition, guarantees that the historic finest fibre root \(X_{best}\) plays an integral part in directing each fibre root to mature in the best way. It is additionally guaranteed that a few arbitrary fibre roots \(X_{r1}^{t}\) direct the remaining fibre roots to carry out arbitrary searching that may prevent the search from dropping into a local best to the particular area.
-
2.
The numerical modelling of lateral root growth in the soil area.
whereas \(Seed_{2}\) means the nutrition capture by lateral roots at the \(t + lst\) development, \(X_{mean}^{t}\) represents average value, \(r_{2}\) refers to a randomly generated number among \(\left( {1, N} \right),X_{r2}^{t}\) signifies the fiberous root arbitrarily chosen from the \(N\) fibre roots inside the \(tth\) development, \(\alpha_{2} \in 2 \times rand\left( {0,1} \right) - 1\) signifies randomly generated numbers applied to create the interval \(\left( { - 1,1} \right)\). If \(\alpha_{2} \in \left( {0,1} \right)\), it means that the root absorbs nutrients, and if \(\alpha_{2} \in \left( { - 1,0} \right)\), it indicates that the root permits organic mixtures to the nearby atmosphere.
-
3.
The numerical modelling of primary root growth in the soil area.
Here \(Seed_{3}\) embodies the food absorbs by the primary root at the \(t + 1st\) growing, \(R_{l}^{u}\) refers to complete soil area (for example: the targeted problem search area), \(u\) and \(l\) characterize lower and upper limits of the problem area, \(\alpha_{3} \in \varepsilon \times rand\left( {0,1} \right) + \tilde{\varepsilon },\varepsilon\) denote randomly generated integer of \(0\) or 1 produced by \(randi\left( {0,1} \right)\) function, \(\tilde{\varepsilon }\) stands for reverse of \(\varepsilon\). If \(\varepsilon\) is selected as 1, \(\alpha_{3} \in \left( {0,1} \right)\), which specifies that fibre roots do not get sufficient food intake, and if \(\varepsilon\) is set to \(0,\) \(\alpha_{3} = 1\), which stipulates that the fibrous roots can get the nutrition. This randomly generated number rule ensures that \(\alpha_{3}\) is an arbitrary number within the range of (0, 1), which accurately reflects the actual food intake by the plant root system. \(Seed_{1} - R_{l}^{u}\) characterizes the food intake by the fibrous roots.
Numerical model of plant growth in the fibre root system
The primary root of the fibrous root system deteriorates during seed germination, and simultaneously, the adventitious or fibrous root matures at the bottom of the stem. The adventitious root’s growing point \(X_{i}^{t + 1}\) at the following instant is jointly defined by the present \(X_{i}^{t}\), the thick (best) \(X_{lbest}\), \(X_{r3}\) and \(X_{r4}\) inside the soil area, and this searching method guarantees that \(X_{i}^{t}\) emerges from the local optimal with a higher possibility. Besides, while the growth of adventitious roots within the fibre root system is highly arbitrary, each of the adventitious roots maintains a particular number of aggregations, which allows the adventitious roots to discover additional nutrition‐rich regions. According to the preliminary study, the root growth of fibrous-root plants is demonstrated as shown.
whereas \(X_{c}\) signifies the food intake by the present adventitious root \(X_{i}^{t}\), directing the remaining portion of the rhizomes, apart from the thick adventitious root, to mature extensively within the soil, \(X_{lbest}\) refers to the global best for the present fiber root. \(\alpha_{4} \in \sigma \times rand\left( {0, 1} \right)\), \(\sigma\) signifies randomly generated integer of 0 or 1 made by utilizing the \(rand\;i\left( {0, 1} \right)\) function, if \(\sigma = 1\), \(\alpha_{4} \in \left( {0, 1} \right)\) specifies that \(X_{c}\) has initiated the area comprising the nutrition by developing extendedly within the soil, if \(\sigma = 0\), \(\alpha_{3} = 0\) designates that \(X_{c}\) failed to detect the region consisting of the nutrition in Eq. (5) defines the stochastic searching method, with r3 and r4 denote randomly chosen integers.
The PRGO model creates an FF to achieve enhanced classification performance. It calculates a positive integer to depict the enhanced performance of the candidate solution. In this manuscript, the minimization of the classification error rate is deliberated as the FF, as shown in Eq. (33).
Experimental outcome
The experimental study of the OMHSA-IDPRGO technique is examined under the Edge-IIoT dataset38. The dataset comprises 30,000 total records with 12 types of events, as summarised in Table 2. The complete no. of features is 63, but only 35 were chosen.
Figure 4 represents the classifier results of the OMHSA-IDPRGO technique on the Edge-IIoT dataset. Figure 4a, b portray the confusion matrices, which precisely classify all classes under a 70:30 ratio. Figure 4c exhibits the PR investigation, demonstrating maximum performance for each class. Finally, Fig. 4d exemplifies the ROC examination, signifying capable outcomes with greater values of ROC.
Table 3 and Fig. 5 denote the intrusion detection result of the OMHSA-IDPRGO model on the Edge-IIoT dataset. With 70%TRPHE, the OMHSA-IDPRGO model provides average \(accu_{y}\), \(prec_{n}\), \(reca_{l} , F1_{Score}\), and \(G_{Measure}\) of 99.11%, 94.67%, 94.66%, 94.66%, and 94.66%, respectively. Moreover, under 30%TSPHE, the OMHSA-IDPRGO method provides average \(accu_{y}\), \(prec_{n}\), \(reca_{l} , F1_{Score}\), and \(G_{Measure}\) of 99.06%, 94.38%, 94.37%, 94.37%, and 94.37%, correspondingly.
Figure 6 depicts the classifier outcomes of the OMHSA-IDPRGO model on the Edge-IIoT dataset. Figure 6a presents the accuracy study of the OMHSA-IDPRGO model. The figure indicates that the OMHSA-IDPRGO model yields increasing values across successive epochs. Furthermore, the rising validation over training demonstrates that the OMHSA-IDPRGO method proficiently learns from the test dataset. Finally, Fig. 6b illustrates the loss analysis. The findings indicate that the OMHSA-IDPRGO method achieves similar validation and training loss values.
Also, the OMHSA-IDPRGO technique is examined under the ToN-IoT dataset39. The dataset contains a total of 119,957 samples across nine classes. The complete details are presented in Table 4 below. The no. of attributes present in this dataset is 42, but only 31 were selected.
Figure 7 displays the classifier results of the OMHSA-IDPRGO model on the ToN-IoT dataset. Figure 7a, b illustrate the confusion matrices with precise classification across all classes under a 70:30 ratio. Figure 7c illustrates the PR investigation, which specifies the maximum performance for all class labels. Lastly, Fig. 7d exemplifies the ROC study, representing skilful outcomes with increased ROC values.
Table 5 and Fig. 8 signify the intrusion detection result of the OMHSA-IDPRGO technique on the ToN-IoT dataset. Under 70%TRPHE, the OMHSA-IDPRGO model gives average \(accu_{y}\), \(prec_{n}\), \(reca_{l}\), \(F1_{Score}\), and \(G_{Measure}\) of 99.18%, 91.34%, 84.72%, 86.47%, and 87.18%, respectively. Furthermore, depending on 30%TSPHE, the OMHSA-IDPRGO model provides an average \(accu_{y}\), \(prec_{n}\), \(reca_{l}\), \(F1_{Score}\), and \(G_{Measure}\) of 99.17%, 91.59%, 84.77%, 86.70%, and 87.38%, respectively.
Figure 9 establishes the classifier outcomes of the OMHSA-IDPRGO method on the ToN-IoT dataset. Figure 9a determines the accuracy of the OMHSA-IDPRGO method. The figure indicates that the OMHSA-IDPRGO method yields increasing values over successive epochs. Additionally, the growing validation over training exhibits that the proposed approach learns efficiently on the testing dataset. Lastly, Fig. 9b illustrates the loss examination of the OMHSA-IDPRGO model. The outcomes denote that the OMHSA-IDPRGO model accomplishes close values of training and validation loss.
Table 6 presents a comparative study of the OMHSA-IDPRGO model on Edge-IIoT and ToN-IoT datasets, evaluating various measures against existing techniques22,23,25,26,40,41,42,43.
Figure 10 shows the comparison findings of the OMHSA-IDPRGO model on the Edge-IIoT dataset. The results highlighted that the LSTM-CSAE, MhSaBiGRNN, FL, EECA-LSTM, LSTM-KPCA, ML-PCC, IF, Shallow ANN, Baseline DNN, DAE-LSTM, and XCT-DF methods performed the worst. Additionally, the OMHSA-IDPRGO model demonstrated enriched performance with maximum \(accu_{y} ,{ }prec_{n}\), \(reca_{l} ,\) and \(F1_{score}\) of 99.11%, 94.67%, 94.66%, and 94.66%, respectively.
The comparative exploration of the OMHSA-IDPRGO approach on the ToN-IoT dataset with current approaches is displayed in Fig. 11. The OMHSA-IDPRGO approach achieves the highest performance, with \(accu_{y} ,{ }prec_{n}\), \(reca_{l} ,\) and \(F1_{score}\) of 99.18%, 91.34%, 84.72%, and 86.47%, correspondingly. Whereas the present models, namely MNBD, NFA, GNN, CNN, DNN, LSTM, DT, kNN, PCA, and NB, obtain lesser values across diverse metrics.
Conclusion
This study designs and develops an OMHSA-IDPRGO model to advance IoT security. The primary focus of this novel is improving the automatic cyberattack detection in an IoT environment by employing advanced techniques. To achieve this, the OMHSA-IDPRGO method executes a mean normalization method to transform the raw data into a structured format. Following this, the COA approach is employed to select the optimal feature subset, thereby identifying the most relevant features from a dataset. For the cybersecurity detection process, the OMHSA-IDPRGO method uses a hybrid model named CNN-BiGRU-MHSAM. Finally, the hyperparameter selection is implemented by the PRGO approach to enhance the classification performance. The experimentation of the OMHSA-IDPRGO model is examined under Edge-IIoT and ToN-IoT datasets. The comparison study of the OMHSA-IDPRGO model yielded superior accuracy values of 99.11 and 99.18% compared to existing techniques on the dual datasets. The limitations of the OMHSA-IDPRGO model comprise the use of static datasets, which may not fully capture the real-time dynamics of evolving network environments. The model also faces scalability threats when deployed in large-scale or heterogeneous networks. Additionally, the absence of real-world deployment restricts practical validation. Environmental factors, such as varying mobility patterns or interference, were not extensively considered. The framework may require frequent updates to keep pace with newly emerging threats. Future work may explore real-time adaptive systems with continuous learning capabilities. Expanding the model to handle multi-domain and cross-platform data sources will also improve its robustness and applicability.
Data availability
The data that support the findings of this study are openly available in the Kaggle repository at https://www.kaggle.com/datasets/mohamedamineferrag/edgeiiotset-cyber-security-dataset-of-iot-iiot, https://www.kaggle.com/datasets/dhoogla/cictoniot reference numbers38,39.
References
Lee, I. Internet of things (IoT) cybersecurity: Literature review and IoT cyber risk management. Future Internet 12(9), 157 (2020).
Kuzlu, M., Fair, C. & Guler, O. Role of artificial intelligence in the internet of things (IoT) cybersecurity. Discov. Internet Things 1(1), 7 (2021).
Andrade, R. O., Yoo, S. G., Tello-Oquendo, L. & Ortiz-Garcés, I. A comprehensive study of the IoT cybersecurity in smart cities. IEEE Access 8, 228922–228941 (2020).
Raimundo, R. J. & Rosário, A. T. Cybersecurity in the internet of things in industrial management. Appl. Sci. 12(3), 1598 (2022).
AlSalem, T. S., Almaiah, M. A. & Lutfi, A. Cybersecurity risk analysis in the IoT: A systematic review. Electronics 12(18), 3958 (2023).
Altulaihan, E., Almaiah, M. A. & Aljughaiman, A. Cybersecurity threats, countermeasures and mitigation techniques on the IoT: Future research directions. Electronics 11(20), 3330 (2022).
Jun, Y., Craig, A., Shafik, W. & Sharif, L. Artificial intelligence application in cybersecurity and cyberdefense. Wirel. Commun. Mob. Comput. 2021(1), 3329581 (2021).
Abdullahi, M. et al. Detecting cybersecurity attacks in internet of things using artificial intelligence methods: A systematic literature review. Electronics 11(2), 198 (2022).
Zeadally, S., Adi, E., Baig, Z. & Khan, I. A. Harnessing artificial intelligence capabilities to improve cybersecurity. IEEE Access 8, 23817–23837 (2020).
Abdalla Musa, A.I. & Al-Hagery, M.A., Integrating machine learning with two-person intuitionistic neutrosophic soft games for cyberthreat detection in blockchain environment. Int. J. Neutros. Sci. (IJNS), 25(2) (2025).
Alzahrani, A., An optimized approach to deep learning for botnet detection and classification for cybersecurity in internet of things environment. Comput. Mater. Continua 80(2) (2024).
Sekhar, J.C., Priyanka, R., Nanda, A.K., Josephson, P.J., Ebinezer, M.J.D. & Devi, T.K., Stochastic gradient boosted distributed decision trees security approach for detecting cyber anomalies and classifying multiclass cyber-attacks. Comput. Secur., p. 104320. (2025).
Alotaibi, J. A hybrid software-defined networking approach for enhancing IoT cybersecurity with deep learning and blockchain in smart cities. Peer-to-Peer Netw. Appl. 18(3), 123 (2025).
Zidi, K., Abdellafou, K. B., Aljuhani, A., Taouali, O. & Harkat, M. F. Novel intrusion detection system based on a downsized kernel method for cybersecurity in smart agriculture. Eng. Appl. Artif. Intell. 133, 108579 (2024).
Sadu, V.B., Abhishek, K., Al-Omari, O.M., Nallola, S.R., Sharma, R.K. & Khan, M.S., Enhancement of cyber security in IoT based on ant colony optimized artificial neural adaptive tensor flow. Netw. Comput. Neural Syst., pp.1–17. (2024).
Aljebreen, M. et al. Enhancing DDoS attack detection using snake optimizer with ensemble learning on internet of things environment. IEEE Access 11, 104745–104753 (2023).
Kumar, P. et al. Digital twin-driven SDN for smart grid: A deep learning integrated blockchain for cybersecurity. Sol. Energy 263, 111921 (2023).
Lamir, I.M., Gital, A.Y.U., Ibrahim, K.M., Lawal, M.A., Danlami, M. and Yakubu, I.Z., Improved cybersecurity framework based on truckingc heuristics algorithm for detecting malicious devices in fog computing and internet of things (IoT) environments. In: 2023 IEEE Fifth International Conference on Advances in Electronics, Computers and Communications (ICAECC) pp. 1–9. IEEE. (2023).
Saheed, Y.K., Misra, S. and Chockalingam, S., Autoencoder via DCNN and LSTM models for intrusion detection in industrial control systems of critical infrastructures. In: 2023 IEEE/ACM 4th International Workshop on Engineering and Cybersecurity of Critical Systems (EnCyCriS) pp. 9–16. IEEE. (2023).
Thayalan, S., Radhakrishnan, N., Ramana, T.V., Devarajan, G.G., Karuppiah, M. and Al Dabel, M.M., Real-time threat detection and AI-driven predictive security for consumer applications. IEEE Trans. Consumer Electron. (2025).
Saheed, Y. K., Abdulganiyu, O. H. & Ait Tchakoucht, T. Modified genetic algorithm and fine-tuned long short-term memory network for intrusion detection in the internet of things networks with edge capabilities. Appl. Soft Comput. 155, 111434 (2024).
Kumar, P., Jolfaei, A. & Islam, A. N. An enhanced deep-learning empowered threat-hunting framework for software-defined internet of things. Comput. Secur. 148, 104109 (2025).
Paul, S., Mitra, A., Shambhavi, S., Ghosh, S. & Bandyopadhyay, A. Holistic cyber security framework for deep web using federated learning in healthcare and distributed computing. Proc. Comput. Sci. 258, 2405–2414 (2025).
Kathole, A. B. et al. Enhanced security mechanism in vehicular networks using ensemble machine learning to detect malicious activity in VANETs. J. Discret. Math. Sci. Cryptogr. 27(7), 2005–2014 (2024).
Amer, E., Al-rimy, B. A. S. & El-Sappagh, S. Strengthening ICS defense: Modbus-NFA behavior model for enhanced anomaly detection. J. Inf. Secur. 89, 103990 (2025).
Sardar, T. H. et al. Enhancing security in MANETs with deep learning-based intrusion detection. Proc. Comput. Sci. 259, 120–129 (2025).
Kathole, A. B. et al. A novel approach to IoT security for intrusion detection system using ensemble network and heuristic-assisted feature fusion. J. Discret. Math. Sci. Cryptogr. 27(7), 2207–2217 (2024).
Saheed, Y.K. and Chukwuere, J.E., 2025. CPS-IIoT-P2 attention: Explainable privacy-preserving with scaled dot-product attention in cyber physical system-industrial IoT network. IEEE Access.
Kathole, A.B., Vhatkar, K.N., Goyal, A., Kaushik, S., Mirge, A.S., Jain, P., Soliman, M.S. and Islam, M.T., 2024. Secure federated cloud storage protection strategy using hybrid heuristic attribute-based encryption with permissioned blockchain. IEEE Access.
Saheed, Y. K., Omole, A. I. & Sabit, M. O. GA-mADAM-IIoT: A new lightweight threats detection in the industrial IoT via genetic algorithm with attention mechanism and LSTM on multivariate time series sensor data. Sens. Int. 6, 100297 (2025).
Saheed, Y. K. & Chukwuere, J. E. Xaiensembletl-iov: A new explainable artificial intelligence ensemble transfer learning for zero-day botnet attack detection in the internet of vehicles. Results Eng. 24, 103171 (2024).
Saheed, Y. K. & Misra, S. CPS-IoT-PPDNN: A new explainable privacy preserving DNN for resilient anomaly detection in cyber-physical systems-enabled IoT networks. Chaos Solitons Fractals 191, 115939 (2025).
Ullah, I., Deng, X., Pei, X., Mushtaq, H. & Khan, Z. Securing internet of vehicles: A blockchain-based federated learning approach for enhanced intrusion detection. Clust. Comput. 28(4), 256 (2025).
Kim, Y. S. et al. Investigating the impact of data normalization methods on predicting electricity consumption in a building using different artificial neural network models. Sustain. Cities Soc. 118, 105570 (2025).
Chen, S., Huang, X., Jiang, Z. and Ma, M., Reliability-Based Design Optimization of Spherical Roller Bearing for Wind Turbines. Available at SSRN 5222291.
Mao, J., Zhao, J., Zhang, H. & Gu, B. A novel hybrid deep learning model for day-ahead wind power interval forecasting. Sustainability 17(7), 3239 (2025).
Zhang, J., Yan, F. & Yang, J. Binary plant rhizome growth-based optimization algorithm: An efficient high-dimensional feature selection approach. J. Big Data 12(1), 13 (2025).
https://www.kaggle.com/datasets/mohamedamineferrag/edgeiiotset-cyber-security-dataset-of-iot-iiot
Bukhari, S. M. S. et al. Enhancing cybersecurity in Edge IIoT networks: An asynchronous federated learning approach with a deep hybrid detection model. Internet Things 27, 101252 (2024).
Izuazu, U. U., Nwakanma, C. I., Kim, D. S. & Lee, J. M. Explainable and perturbation-resilient model for cyber-threat detection in industrial control systems networks. Discov. Internet Things 5(1), 9 (2025).
Kalaria, R., Kayes, A. S. M., Rahayu, W., Pardede, E. & Salehi, A. IoTPredictor: A security framework for predicting IoT device behaviours and detecting malicious devices against cyber attacks. Comput. Secur. 146, 104037 (2024).
Li, J., Chen, H., Shahizan, M. O. & Yusuf, L. M. Enhancing IoT security: A comparative study of feature reduction techniques for intrusion detection system. Intell. Syst. Appl. 23, 200407 (2024).
Acknowledgments
Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2025R755), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. Ongoing Research Funding program, (ORF-2025-537), King Saud University, Riyadh, Saudi Arabia. The authors extend their appreciation to Northern Border University, Saudi Arabia, for supporting this work through project number “NBU-CRP-2025-1564. The authors are thankful to the Deanship of Graduate Studies and Scientific Research at University of Bisha for supporting this work through the Fast-Track Research Support Program. The author would like to acknowledge the support of Prince Sultan University for paying the Article Processing Charges (APC) of this publication and for their support.
Author information
Authors and Affiliations
Contributions
Mimouna Abdullah Alkhonaini: Conceptualization, methodology, validation, investigation, writing—original draft preparation, funding Sara Abdelwahab Ghorashi: Conceptualization, methodology, writing—original draft preparation, writing—review and editing Ghalib H. Alshammri: methodology, validation, writing—original draft preparation Saied Alshahrani: software, visualization, validation, data curation, writing—review and editing Shouki A. Ebad: Project administration, validation, original draft preparation, writing—review and editing Sami Saad Albouq: methodology, validation, Conceptualization, writing—review and editing Fahad Alzahrani: methodology, validation, original draft preparation. Menwa Alshammeri: validation, original draft preparation, writing—review and editing.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Alkhonaini, M.A., Ghorashi, S.A., Alshammri, G.H. et al. Advances in IoT networks using privacy-preserving techniques with optimized multi-head self-attention model for intelligent threat detection based on plant rhizome growth optimization. Sci Rep 15, 34233 (2025). https://doi.org/10.1038/s41598-025-16052-y
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-16052-y