Abstract
We analyze realistic vulnerabilities of decoy-state quantum key distribution (QKD) arising from the combination of laser damage attack (LDA) and unambiguous state discrimination (USD). While decoy-state QKD is designed to protect against photon-number-splitting and beam-splitting attacks by accurately estimating the single-photon fraction, it relies on stable attenuation to prepare pulses with fixed mean-photon numbers. An eavesdropper (Eve) can exploit LDA to irreversibly alter the optical components on Alice’s side, effectively increasing the mean-photon numbers beyond the decoy-state security regime. We show that once the alteration exceeds a critical threshold—on the order of 10–20 dB—Eve can implement an efficient USD-based intercept-resend strategy using current off-the-shelf technology, thus obtaining the entire secret key. Numerical simulations confirm that for sufficiently elevated mean-photon numbers, Eve’s conclusive measurement outcomes skew the decoy-state statistics, yet remain undetected by standard security checks. We further demonstrate how a modified USD setup employing an additional beam splitter can reduce the required threshold, facilitating Eve’s attack. Additionally, we introduce the pseudo-photon-number resolution USD attack, which allows Eve to emulate all observable gains at Bob’s side so that she remains fully undetectable even with advanced statistical checks. Our findings emphasize the need for robust safeguards against high-power laser damage in QKD systems, including careful hardware selection, rigorous testing under high-power illumination, and real-time monitoring to ensure the integrity of the decoy-state protocol.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD) is believed to provide a secure communication guaranteed by the laws of quantum physics. For the majority of QKD protocols the security proof is present for single-photon implementation. However, real-world QKD systems usually operate with faint laser pulses, since appropriate single-photon sources are not widely available. This inconsistency is often resolved by the GLLP approach1 combined with the decoy-state method2, which allow legitimate parties (Alice and Bob) to produce a secret key, even though the unwanted multiphoton component is present. QKD then becomes resilient to multiphoton-component attacks, such as photon number splitting (PNS)4, beam splitting (BS)5, conditional beam splitting (CBS)6 and unambiguous state discrimination (USD)7,8. This, however, is only the case when the proper operation of the decoy-state method is implied, i.e. the mean-photon numbers in Alice’s pulses are fixed (apart from the small fluctuations which can be incorporated into the security proof9,10). In turn, an eavesdropper (Eve) can launch the laser damage attack (LDA)11,12,13,14 to alter the attenuation at Alice’s side. This results in the increase in Alice’s pulse intensities, which is not addressed by the decoy-state method. Thus, when the system is subject to LDA, the multiphoton attacks should be reexamined.
LDA is a well-known strategy to affect the mean photon numbers in Alice’s pulses by altering the attenuation of the fixed or variable attenuators using high-power radiation11,13,14. It has been reported that the continuous-wave radiation with 0.3–5 W mean power can reduce the attenuation coefficient by up to 10 dB and more for the fixed attenuators11,13,14 and by up to 14.5 dB for the variable attenuators11. It has been postulated that such alteration compromises the security of the decoy-state QKD17, making it vulnerable to PNS attack. However, to complete PNS, Eve needs to handle quantum non-demolition (QND) measurement of the photon number, save the quantum state into the quantum memory and replace the quantum channel with a lossless line. This is argued to be beyond the present-day technologies15,16, although some progress has arisen in this area18,19. This raises the question, what are the real risks assosiated with LDA?
Ideally, every imaginable security drawback of a QKD system should be assessed and eliminated. In reality, infinite security is unattainable and practical security analysis of real-world QKD systems should be performed15 (for example, such security analysis was recently presented in context of the Trojan-horse attack20). LDA has been addressed in several research works posing themselves as a guide to certification procedure, such as ETSI White Paper21, and practical security analysis of a commercial QKD system22. Among other things, ETSI White Paper postulates that LDA does not appear to be intrinsically more threatening than other attacks. In22 authors introduce the risk evaluation system of the attacks under investigation. Each loophole is evaluated by three criteria: (1) loophole likelihood, (2) future or current technology, and (3) amount of key leakage. LDA got mark M (2 points out of 3)—medium risk, because it requires research and possibly future technology to exploit. We, however, believe that the real risks associated with LDA are underestimated in these works. Therefore, by providing a realistic strategy for Eve to steal the whole key using present-day technologies in our paper we try to illustrate that LDA is among the most dangerous attacks, and the corresponding security risks are the highest.
Let us consider all possibilities for Eve to succeed in LDA and evaluate them as in22. The straightforward way for her is to increase the radiation intensity to classical level (large number of photons), so that she can perform classical measurements and effortlessly extract the whole key. The reported values for attenuation alteration of a single attenuator do not exceed 14.5 dB, therefore, such opportunity appears unlikely and obtains 0 + 1 + 1 = 2 points. The ultimate strategy is to perform PNS or the full version of CBS using QND measurements and/or quantum memory. This obtains 1 + 0 + 1 = 2 points due to practical unattainability. Alternatively, Eve can use BS or more practical version of CBS without long-term qubit storage, but she will never obtain the whole key this way, as discussed in6, so the result is 1 + 1 + 0 = 2. We also note that even this lighter version of CBS requires a large number of near-perfect single-photon detectors, as well as a lossless communication line, which seems hard to implement in practice.
Finally, Eve can perform the USD attacks. They allow Eve to steal the entire key using only linear optical elements and single-photon detectors7,8. She also does not need to use a lossless channel. Such attacks have recenly been shown to compomise the security of the coherent-one-way QKD protocol23. Bennet et. al.5 suggested a simple scheme to permorm USD by dividing the pulses into two halves and conducting measurements in different basis for each half (which is essentially a copy of Bob’s setup). When three detectors click, Eve can be sure about the state sent by Alice. While this scheme is not optimal (see24 for its comparison with other USD schemes), it is completely technologically available. In this paper, we show that this USD strategy will work with realistic attenuation alterations, starting from some critical value, and give the whole key to Eve. Thus, all three criteria are not mutually exclusive for LDA and the total score is 1 + 1 + 1 = 3, which corresponds to the highests risks for decoy-state QKD systems.
Results
USD attacks
The decoy-state method is commonly employed to estimate the single-photon gain \(Q_1\), i.e., the rate of detection events on Bob’s side that originate from the single-photon component of Alice’s emitted pulses. When operating properly, the decoy-state method guarantees security against multiphoton-component attacks, including USD, since the key is shortened during the privacy-amplification stage in accordance with the \(Q_1\) estimation (Eqs. 9–12).
Let us consider the attack against weak+vacuum decoy-state BB84 QKD (see Methods). First, Eve launches LDA and modifies mean photon numbers for the signal and decoy states as follows:
where \(\kappa\) is the attenuation alteration coefficient, determined by the particular high-power radiation effect on the attenuator under attack.
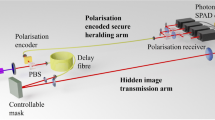
Eve’s polarization-encoding setup for the USD attack. The depicted distribution of photons corresponds to a conclusive outcome for horizontally polarized state as an example. Det\(_\text {H,V,D,A}\), detectors for horizontal, vertical, diagonal and anti-diagonal polarization; PBS, polarization beam-splitter; BS 50:50, symmetric beam-splitter; \(\lambda /2\), half-wave plate for diagonal basis selection. The same setup can be designed for phase encoding.
Next, we consider the USD strategy without QND measurements and quantum memory, hence, achievable by today’s technologies. In fact, Eve only needs a copy of Bob’s setup with passive basis choice for the full key distinction (Fig. 1). Having a conclusive outcome, when strictly 3 detectors have clicked (meaning that the two clicks in one basis are wrong, and the single click in another basis is correct), she sends a corresponding classical pulse to Bob, so he detects it with near-100% probability. The gains are then determined by the probability of Eve’s conclusive measurements outcome. Alternatively, Eve can employ a “translucent” USD variant, preserving part of Alice’s pulse and forwarding it to Bob only when an unambiguous state-elimination measurement succeeds; in this case, two Eve’s detectors in different bases must click so that the bit becomes known after basis reconciliation. This approach is likely comparable in effectiveness, but here we adopt the standard USD formulation to avoid dealing explicitly with channel transmittance and Bob’s detection efficiency and later exploit its built-in state-selection capability in the PPNR USD attack.
It turns out that there exists the critical value for \(\kappa\) where the decoy-state secret key length estimation starts giving non-zero value, while the whole key leaks. This threshold \(\kappa _{USD}\) can be found numerically. However, for small \(\tilde{\mu }\) and \(\tilde{\nu }\), the approximate analytical estimation takes place:
where \(\kappa _{3ph}\) is the threshold for 3-photon PNS attack (see Methods). This relation underlines the connection between the USD attack and the straightforward, yet impractical, way to extract bits from 3-photon pulses, i.e., 3-photon PNS attack. The main difference between them is that the conclusive outcomes in USD sometimes arise from \(n>3\) photon components (for example, when two photons arrive at the same detector). Consequently, Eve needs additional 3 dB to exceed this 3-photon threshold. This result illuminates that \(n>3\) photon component gain complicates concealing the multiphoton attack.
Modified USD attack
Eve can then modify her setup by adding a beamsplitter with transmittance T to divert and detect “odd” photons—those contributing to \(n>3\) detection events, i.e., events requiring at least four photons (a conclusive USD outcome plus an extra click)—and thus suppress yields from the \(n>3\) components (Fig. 2). Although, the gains at Bob’s side will drop, it will provide the reduced USD threshold value \(\kappa _{T}\) (see the derivation in “Methods”):
Surprisingly, stronger blocking the multiphoton signals with \(n>3\) even for conclusive outcomes increases the efficiency of USD attack and reduces the critical value \(\kappa _{T}\), meaning that the attack becomes succesfull at lower intensities. Asymptotically, \(\kappa _{T}\) coincides with 3-photon attack limit \(\kappa _{3ph}\) for \(T\rightarrow 0\). However, the gain \(Q_{\mu }\) will drop significantly:
Therefore, this strategy should be applied carefully, as gain drop may cause a timeout error at Bob’s side.
USD attacks simulation results
The yields for the described USD attacks are determined by the probabilities for Eve’s conclusive measurements outcome for n–photon component. Considering such yields, we have simulated the decoy-state single-photon gain estimation \(Q_1\) over different attenuation alterations \(\kappa\) (Fig. 3). As seen, the estimated single-photon gain starts to rise rapidly after exceeding the threshold. The critical \(\kappa\) values correspond to those, derived by numerically solving Eq. (18). In the worst studied case, corresponding to decoy-state parameters \(\mu = 0.5\) and \(\nu = 0.1\), the threshold lies near 11 dB, which can be further reduced below 10 dB by proper selection of the beam splitter transmittance T in the modified USD. The reported experimental demonstrations of more than 10 dB attenuation alteration11,14 thus provide strong evidence of the practical attainability of the proposed attack. Table 1 shows the comparison between these numerical values with 0.1 dB rounding precision and analytical values from Eq. (3). There is a noticeable difference around 1 dB between numerical and analytical values. However, analytical estimations are conservative, which makes it acceptable to use them during security analysis.
Dependence of the simulated single-photon gain estimation using Eq. (10) on the attenuation alteration for different decoy-state parameters during the USD attack: \(\mu =0.5\), \(\nu =0.1\) (red); \(\mu =0.5\), \(\nu =0.01\) (purple); \(\mu =0.1\), \(\nu =0.01\) (blue). The threshold values (11.1 dB, 14.5 dB and 18.3 dB, respectively) are indicated by the grey lines.
The rapid rise of the single-photon gain estimation in Fig. 3 gives Eve the possibility to set the desirable \(Q_{1}\) value by slightly adjusting \(\kappa\). The typical \(Q_{1}\) values for proper functioning QKD systems are dependent on the channel length, mean-photon number \(\mu\) and detection efficiency and lie in the region \(10^{-6}-10^{-2}\). The total gain \(Q_{\mu }\) is also dependent on mentioned parameters and usually should be of the same order of magnitude as \(Q_{1}\). Eve can reach this picking up the proper beam-splitter for the modified USD. Operating with typical altered mean-photon numbers \(\tilde{\mu }\approx 5-15\) Eve can tune the gain to match the expected values at Bob’s station by selecting the proper T value (Fig. 4).
Pseudo-PNR USD attack
In the general case, any intercept-resend attack that involves blocking (including PNS) alters the detection statistics observed by Alice and Bob. Niederberger et al.25 showed that, in principle, Eve can reproduce the statistics of the original pulses while performing PNS attack. The decoy-state protocol, however, prevents this: blocking single photons produces non-proportional changes in the gains of signal and decoy pulses. Quantitatively, the single-photon gain \(Q_1\)—the target parameter of the decoy-state method—will therefore be affected. Above, we heve shown that the USD attack, and the modified USD attack combined with LDA, can nevertheless allow Eve to produce such gains that Alice and Bob incorrectly estimate \(Q_1\) as a non-zero value.
The decoy-state protocol targets two primary parameters: the single-photon gain \(Q_1\) and the single-photon error probability \(E_1\). However, a QKD system can, in principle, monitor additional statistical quantities and abort the session if any of them deviate from their expected values (for instance,the machine-learning methods can be employed to detect Eve using statistical anomalies26). Moreover, numerical key-rate estimation methods cast the secret-key length calculation as an optimization problem and thus permit bounding Eve’s information using the full set of measured parameters (see, e.g., Refs.27,28). Our USD and modified-USD strategies are designed solely to falsify \(Q_1\) and are therefore, in principle, detectable by such additional checks. Below we construct a more sophisticated USD-based attack that employs pseudo-photon-number resolution (PPNR); this strategy enables Eve to reproduce every parameter observable at Bob’s side, thereby evading detection based on the monitored statistics.
The following four parameters in addition to the error rates can be monitored by Bob in our weak+vacuum decoy-state BB84 protocol to detect Eve’s presence:
-
\(Q_\mu \approx \mu \eta \eta _B + p_{\textrm{dcr}}\)—gain for signal pulses;
-
\(Q_\nu \approx \nu \eta \eta _B + p_{\textrm{dcr}}\)—gain for decoy pulses;
-
\(Q_\mu ^{(2)} \approx (\frac{\mu \eta \eta _B}{2})^2 + \mu \eta \eta _B\,p_{\textrm{dcr}} + p_{\textrm{dcr}}^2\)—double-click gain in mismatch bases for signal pulses;
-
\(Q_\nu ^{(2)} \approx (\frac{\nu \eta \eta _B}{2})^2 + \nu \eta \eta _B\,p_{\textrm{dcr}} + p_{\textrm{dcr}}^2\)—double-click gain in mismatch bases for decoy pulses,
where \(\,\eta \,\) is the channel transmittance (assumed known to Alice and Bob), \(\eta _B\) is the quantum efficiency of Bob’s detectors, and \(p_{\textrm{dcr}}\) is the dark-count rate.
Note that the gains for vacuum states do not change under any USD strategy, since Eve forwards a signal to Bob only when at least three of her detectors fire. If Eve’s detectors have the same dark-count rate as Bob’s, then the probability that Bob detects a pulse forwarded by Eve scales as \(p_{\textrm{dcr}}^3\), while Bob’s own dark-count probability is \(p_{\textrm{dcr}} \gg p_{\textrm{dcr}}^3\).
The setup for the PPNR USD attack is depicted in Fig. 5. The measurement setup is a variant of the modified-USD station augmented with a pseudo-PNR detector resolving up to three photons. Such a detector can be realized, for example, with one 50:50 and one 66:33 beamsplitter so that the probability for a photon to reach each output port is equal (see Fig. 1a). PPNR detectors can also be implemented in integrated optics architectures used for quantum computing29,30. Each conclusive (3-click) outcome of the USD station is now accompanied by a PPNR measurement result that yields 0, 1, 2, or 3 photon counts. Eve associates these outcomes with four events—single decoy-pulse click, double decoy-pulse click, single signal click, and double signal click, respectively—and uses this association to guess which event is most likely to occur at Bob’s station.
To impose her guess on Bob, Eve prepares the corresponding state using her emitter (Fig. 1b). Instead of sending a classical pulse, she now chooses between a laser pulse and a single photon. In the latter case, she must employ a single-photon source (SPS), which is less accessible than standard telecom lasers but can nevertheless be utilized by Eve31. If the PPNR result corresponds to a single-click event (0- or 2-photon count) she sends a single photon from SPS to produce a click with controllable probabilities \(p_{\nu ,1}\) and \(p_{\mu ,1}\) (adjusted via an intensity modulator, IM). If the PPNR result corresponds to a double-click event (1- or 3-photon count) she sends a weak coherent pulse with a controllable intensity \(\nu '\) and \(\mu '\) (tuned by IM). In all cases Eve sets the polarization according to the USD outcome using a polarization modulator (PM).
Pseudo-PNR USD attack simulation results
By selecting the proper values for her signals (\(\nu '\), \(\mu '\), \(p_{\nu ,1}\), and \(p_{\mu ,1}\)) according to the Eqs. (49)–(52), Eve can match all four parameters monitored by Bob with a small margin, as long as the certain threshold \(\kappa _{PPNR}\) is exceeded. This threshold is depended on the communication channel losses and Eve’s beamsplitter transparency T, as well as on the quantum efficiency of Eve’s and Bob’s detectors, and the dark-count rate of Bob’s detectors (the dark-count rate of Eve’s detectors is negligible since Eve operates with relatively high intensities).
(a) The optimal value for the beamsplitter transmittance \(T_o\) and (b) the threshold value for attenuation alteration for PPNR USD attack \(\kappa _{PPNR}\) over the channel transmittance \(\eta\) for different decoy-state parameters. The following parameter values have been used: \(\eta _E=100\%\), \(\eta _B=10\%\), \(p_{dcr}=0\). The gains produced by the attack have matched the expected ones with a relative tolerance of \(10\%\). The different colors in both figures represent different decoy-state parameters: \(\mu =0.5\), \(\nu =0.1\) (red); \(\mu =0.5\), \(\nu =0.01\) (purple); \(\mu =0.1\), \(\nu =0.01\) (blue).
(a) The threshold attenuation alteration for PPNR USD attack \(\kappa _{PPNR}\) over the channel transmittance \(\eta\) for different dark-count rate of Bob’s detectors (\(p_{dcr}=0\)—blue, \(p_{dcr}=10^{-7}\)—purple, \(p_{dcr}=10^{-6}\)—red, \(p_{dcr}=10^{-5}\)—orange); \(\eta _E=1\), \(\eta _B=0.1\); the dotted lines for each dark-count rate mark the critical losses for decoy-state BB84, the gradient colors show the areas for each dark-count rate where positive key rates are possible. (b) The threshold attenuation alteration for PPNR USD attack \(\kappa _{PPNR}\) over the channel transmittance \(\eta\) for different quantum efficiency of Eve’s detectors (\(\eta _{E}=0.1\)—blue, \(\eta _{E}=0.5\)—purple, \(\eta _{E}=0.9\)—red, \(\eta _{E}=1\)—orange). The decoy-state parameters are \(\mu =0.5\), \(\nu =0.1\).
We have obtained the numerical dependence of the attenuation-alteration threshold \(\kappa _{PPNR}\) on the channel transmittance \(\eta\) for three sets of decoy-state parameters and for the beamsplitter transmittance \(T_{o}\) that minimizes the corresponding threshold value. The results are shown in Fig. 6. One can see that, in the case of Bob’s noiseless detection, additional losses make it easier for Eve to emulate the expected statistics. As seen in Fig. 6(b), the asymptotic \(\kappa _{PPNR}\) values lie relatively close to the estimates obtained for our standard USD strategy (see Table 1). On the other hand, the \(\kappa _{PPNR}\) values at zero loss are 2–3 dB higher than those values. A similar effect can be observed in Fig. 3 for the standard USD attack, where Eve also requires a few additional decibels of attenuation alteration for the estimated \(Q_1\) to reproduce the expected statistics at low losses.
We have also run the simulations with the presence of the dark counts at Bob’s detectors. In opposite to the ideal case, the threshold values grow starting from the certain amount of channel losses (see Fig. 7a). This is explained by the fact the dark counts statistics becomes significant at long distances and complicate Eve’s attempts to reproduce the expected gain values. This, however, does not represent a serious obstacle for Eve, since the dark-count rate itself limits the maximum losses for QKD. According to Eq. (12) the single-photon error rate is mainly determined by the signal-to-noise ratio for the decoy pulses. Conservatively considering the dark counts as the only source of errors, we can find the critical losses \(\eta _{c}\) for which 11% error-rate bound is reached:
Therefore, the QKD session can take place only for \(\eta ~>~\eta _{c}\). These regions are highlighted in Fig. 7(a) for different dark-count rates. As seen, the threshold values \(\kappa _{PPNR}\) begin to increase approximately 5 dB above the critical-loss point and rise by only a few additional decibels when approaching the upper bound.
Finally, we have studied the influence of Eve’s detectors efficiency \(\eta _E\) on the threshold value \(\kappa _{PPNR}\). The simulated \(\kappa _{PPNR}\) over channel transmittance \(\eta\) for different \(\eta _E\) is depicted Fig. 7(b). As seen, decreasing the efficiency results in proportional increase of the threshold. The reason of such behavior is that the imperfect detection effectively reduces the altered mean-photon numbers
When \(\eta _E\) is small, Eve needs to increase \(\kappa\) to reach the same altered mean-photon numbers and, consequently, the same threshold value. For example, for \(\eta _E=0.1\) the threshold values rise by 10 dB.
Discussion
We have described a realistic attack on QKD systems, which combines the laser damage and the USD. We have presented Eve’s USD setup, which is essentially a copy of Bob’s station. We have also presented the setup for modified USD by adding an asymmetric beam-splitter, which advances the efficiency of the attack. Unlike PNS or BS attack, such USD can be implemented using present-day technologies. Finally, we have presented the PPNR USD attack, which allows Eve to reproduce all the parameters monitored by Bob, thus, completely evading detection.
Let us now discuss the practical limitations for Eve to implement the proposed attacks. First, we have assumed that Eve can place her laboratory near Alice’s station, therefore, we neglected the channel losses. If this is not the case and the signal must travel through, say, 10 km of standard optical fiber from Alice, the resulting channel loss would raise the threshold by approximately 2 dB. Second, one should take into account Eve’s imperfect detection. We have determined that the efficiency of Eve’s detectors \(\eta _{E}\) raises the threshold value for the attenuation alteration (Fig. 7b). For typical InGaAs SPADs efficiency values \(\eta _{E}=5-30\%\) it means that Eve needs additional 5–15 dB to reach the attack threshold. It then appears that the required attenuation alteration is significantly larger than the experimentally reported 10–14 dB. While for some QKD solutions this may seem like a safeguard, others often employ two attenuators in series (e.g., a variable and a fixed attenuator, as in Ref.22), whose combined attenuation may fall even below this “pragmatic” threshold. Moreover, Eve can avoid these limitations for QKD systems operating in the visible region (free-space QKD), where she can use high-efficiency Si SPADs. She can also upgrade her apparatus by using superconducting detectors with near-unity efficiency, which are available as a full-fledged device32.
Another practical limitation for Eve is the deadtime of her detectors. For InGaAs SPADs, the deadtime is typically set to 0.1–10 \(\mu\)s to reduce the afterpulsing probability. This restricts the repetition rate of Eve’s USD measurements to 100 kHz–10 MHz. If the QKD system operates at a higher repetition rate, Eve may wish to reduce the deadtime. This, however, would lead to parasitic afterpulsing detection events, which could introduce errors into Eve’s measurements. To avoid this, Eve may employ state-of-the-art InGaAs SPADs with negligible afterpulsing probabilities and deadtimes as short as 3–10 ns33. Alternatively, she could use superconducting detectors, which do not suffer from afterpulsing and have deadtimes of only a few nanoseconds32. Thus, considering the worst-case scenario, we can imply that Eve possesses sufficient resources to buy (or steal) state-of-the-art apparatus.
It is important to note that USD measurements allow Eve to identify the state without intrinsic errors. Nevertheless, Eve may still obtain an incorrect result or impose an erroneous state on Bob due to imperfections in state preparation and detection within the QKD system. As stated in Ref.8, such effects do not require separate consideration, since USD attacks provide Eve with complete information about the key, even though Bob may register some errors. Moreover, it may even be advantageous for Eve to introduce a small additional QBER (for instance, by sending states orthogonal to her USD outcomes) to conceal her presence, as a nonzero QBER is typically observed even in the absence of any attack.
It is worth noting that, according to the reported experimental results11,14, the attenuation alteration induced by LDA is inherently unpredictable. This leads to two possible scenarios for the adversary. In the first case, the alteration does not exceed the required threshold, and the attack fails. In the second case, the attenuation alteration exceeds the threshold, but its exact value remains unknown to Eve. The latter scenario is of primary interest in our analysis, as we focus on conditions under which the attack becomes feasible—even if such conditions are not always guaranteed in practice. After applying LDA, Eve may seek to verify whether the modification was successful and to estimate the actual attenuation alteration in order to select optimal parameters for the subsequent USD attack. This can be accomplished, in principle, using optical reflectometry techniques34, or by directly measuring the intensity of Alice’s radiation with a high-sensitivity power meter or a single-photon detector. Once this measurement is performed, Eve can acquire the necessary information to initiate the USD attack and proceed with the USD attack as outlined above.
We have found that such USD attacks give the whole key to Eve whenever the attenuation alteration threshold is overcome. It is the 3-photon nature of these USD attacks that accounts for the existence of the threshold, which is found to lie in the region of 10–20 dB, depending on the decoy-state parameters. Such attenuation alterations have been previously experimentally demonstrated for several types of attenuators under high-power radiation11,14.
Therefore, one must make sure that the attenuators used in a QKD system are resilient to LDA. One mitigation approach is to monitor the functioning of optical components during the QKD session by placing a beam splitter with a high-sensitivity photodetector at the output of Alice’s setup. Another option is to detect external light injection using a watchdog detector, which, however, can be circumvented by Eve35. A more promising method is the use of passive monitoring devices, such as optical fuses, which are permanently damaged under high-power radiation, thereby interrupting the communication36. This effect can be achieved through the fiber-fuse phenomenon37 or by employing carbon nanomaterials38. Finally, appropriate types of attenuators should be selected—those experimentally shown to be more resistant to high-power radiation, such as neutral filters13 or manual variable attenuators11. The actual sustainability of the attenuators used in a particular QKD system should be tested as part of the certification process11,14,22. In that case, the security of the QKD will be preserved.
Methods
Decoy-state method
The decoy-state QKD utilizes auxiliary coherent states and monitors their detection statistics. Two decoy states with mean photon numbers \(\nu _{1}\) and \(\nu _{2}\) are known to be sufficient for the estimation of the single-photon fraction. The secret key rate for the decoy-state BB84 is expressed as follows2,3:
where q is the fraction of sifted bits (1/2 for the standard version of BB84), \(Q_{1}\) is the single-photon gain, \(Q_{\mu }\) is the gain for signal pulses with mean photon number \(\mu\), \(E_{1}\) is the quantum bit error rate (QBER) for the single-photon fraction, \(E_{\mu }\) is the overall QBER for the signal pulses, f(x) is the error correction efficiency, \(h(x)\equiv -x\log _{2}x-(1-x)\log _{2}(1-x)\) is the binary entropy function. For simplicity, we assume an infinite key length and the lack of side channels (the security analysis for the decoy-state method in the presence of side channels and finite-key effects can be found in Refs.39,40).
Next we consider the optimal vacuum+weak decoy-state variant (\(\nu _{1}\equiv \nu\), \(\nu _{2}\equiv 0\)). The decoy-state method considers an estimation of \(Q_{1}\) and \(E_{1}\) given by3:
where \(Q_{\mu ,\nu ,0}\) are the measured gains for signal, decoy and vacuum states, \(E_{\nu ,0}\) is the QBER for decoy and vacuum states correspondingly, \(Y_{1}\) is the yield for the single-photon component.
For the gains \(Q_{\mu ,\nu }\) we have:
where \(p_{\mu ,\nu }(n)\) is a Poisson probability function for a photon number n and the mean value \(\mu\) or \(\nu\). Here, we have implied a proper functioning of Alice’s apparatus which guarantees that the desired mean-photon numbers are prepared. The yields for n-photon components \(Y_{n}\) can be modified by Eve during PNS, BS or USD attack. That, however, will be detected by the decoy-state method and reflected in the single-photon fraction value estimation.
Analytical estimation for USD thresholds
When the USD attack is performed, the gains are determined by the probability of Eve’s conclusive measurement outcome, which is given by the product of three probabilities corresponding to detector clicks at the USD station: two detectors receiving pulses with mean photon number \(\tilde{\mu }/4\) or \(\tilde{\nu }/4\), and one detector receiving a pulse with mean photon number \(\tilde{\mu }/2\) or \(\tilde{\nu }/2\). Therefore, the gains for the signal and decoy states are expressed as:
Here, we considered perfect noiseless detection at Eve’s station and ideal bit imposition. Such strict requirements, in principle, can be relaxed (See “Pseudo-PNR USD attack simulation results”).
Let us derive the critical value for \(\kappa\) where the secret key length estimation starts giving a non-zero value:
Considering \(Q_0<<1\), Eq. (16) takes the following form:
Note that the assumption on low \(Q_0\) value holds even for high channel losses scenario, since the the gains \(Q_\mu\) and \(Q_\nu\) are fully determined by Eve.
Modifying the left part of the expression we obtain the transcendental equation for \(\kappa _{USD}\):
This equation can be solved numerically. However, for approximate estimation, we will use the Taylor expansion of the left part:
Substituting the right part of the approximation (19) into the transcendental Eq. (18) we obtain the following equation for \(\kappa _{USD}\):
This equation can be solved analytically resulting in Eq. (3).
For the modified USD attack with an additional beam-splitter the gains are modified as follows:
For the transcendental equation we have:
Using approximation (19) we found an estimate for \(\kappa _{T}\) resulting in Eq. (4).
3-Photon PNS attack
Let us consider a specific PNS strategy with blocking all n–components with \(n\ne 3\). This strategy leads to a more significant drop in secret key rate in comparison to the standard PNS strategy with preserving \(n=2\) component. This 3-photon attack, however, does not require a quantum memory as the measurements in two different bases can be conducted simultaneously. Hence, only classical memory for the measurements outcome is required.
We consider the zero yields for 3-photon attack, except for the \(Y_{3}\):
LDA modifies mean photon numbers as dictated by Eqs. (1) and (2). The gains are then:
The critical value for \(\kappa\) where the secret key length estimation starts giving non-zero value can be derived from the following equation:
Considering \(p_{dcr}<<1\), we obtain the equation:
Solving Eq. (29) for \(\kappa _{3ph}\) we obtain the 3-photon attack threshold:
The threshold is proportional to those for the described USD attacks (3) and (4). This underlines the 3-photon nature of the described USD strategies.
Simulation of USD attack
Considering noiseless and lossless detection at Eve’s station, we can express the yields for the USD attack, i.e. the probabilities of conclusive measurements outcome for n–photon components. For this, we use the binomial distribution of photons after the 50:50 beam-splitter and pick up the scenarios, when only 3 detectors click (we assume Eve using threshold detectors without photon number resolution):
where the first sum denotes the probability of k photons to arrive at the correct-basis measurement side and the second sum denotes the probability of the the remaining \(n-k\) photons to be divided along two paths in the incorrect-basis measurement side.
For the modified USD attack the yields are multiplied by the probability of n photons passing through the beamsplitter T:
We have simulated the single-photon gain estimation and the total gain for signal pulses using Eqs. (10)–(11), (13), (31) and (32) for different decoy-state parameters. The series in Eq. (13) was truncated at \(n = 600\), since the cumulative probability of the Poisson distribution beyond this point becomes negligible within the precision of the 8-digit floating-point arithmetic used in our simulations. The results are presented in “USD attacks simulation results.”
Simulation of pseudo-PNR USD attack
The purpose of PPNR USD attack is to match all four parameters monitored by Bob, which in absence of Eve are given by:
By performing PPNR USD attack, Eve modifies the gains as follows:
where
are the probabilities of a conclusive USD outcome for the signal and the decoy state, respectively;
are the binomial probabilities of a k-photon count on the PPNR detector for the signal and the decoy state, respectively;
are the probabilities of a single click at Bob’s station induced by a laser pulse sent by Eve with a mean photon number \(\mu '\) and \(\nu '\), respectively;
are the probabilities of a double click at Bob’s station induced by a laser pulse sent by Eve with a mean photon number \(\mu '\) and \(\nu '\), respectively; \(p_{\mu , 1}\), \(p_{\nu , 1}\) are the probabilities of a single click at Bob’s station induced by a single photon sent by Eve after 2- and 0-photon click at PPNR detector, respectively.
By equating expressions (33)–(36) to (37)–(40) and combibing the resulting equations, we obtain two systems of linear equations. The first one is:
By solving this system using Cramer’s rule, we express the linear relation between \(p_{\mu '}\) and \(p_{\mu '}^{(2)}\) and between \(p_{\nu '}\) and \(p_{\nu '}^{(2)}\). Using explicit expressions (45)–(48) we express \(\mu '\) and \(\nu '\).
The second system of linear equations is
This system can be also solved for \(p_{\mu ,1}\) and \(p_{\nu ,1}\) using Cramer’s rule and substituting the previously found \(\mu '\) and \(\nu '\).
For the solution to be valid, the following conditions must be satisfied:
These constraints cannot be satisfied for arbitrary \(\kappa\). The solution becomes consistent only above a certain threshold value. Eve, however, does not necessarily need to satisfy the equations exactly. Alice and Bob would likely not notice if the observed statistics deviated from the expected values by a small margin. To determine the threshold in this case, we numerically search for the smallest \(\kappa\) at which the ratios of observable to expected gains equal unity within a nonzero tolerance. To this end, we set Eve’s parameters \(\mu '\), \(\nu '\), \(p_{\nu ,1}\), and \(p_{\mu ,1}\) according to the closed-form solution, clipping their values within the constraint interval, and perform a sweep over \(\kappa\) and the beamsplitter transmittance \(T \in [0,1]\) using the golden-section search.
We have peformed numerical simulations to find threshold values for attenuation alteration \(\kappa _{PPNR}\) for PPNR USD attack. We have employed different decoy-state parameters, channel losses, Eve’s detection efficiency and the dark-count rates of Bob’s detectors. The results are presented in “Pseudo-PNR USD attacks simulation results.”
Data availability
All the data that support the results of the current work are available from the corresponding authors upon reasonable request.
References
Gottesman, D., Lo, H.-K., Lütkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect devices, Proc. IEEE Int. Symp. Inf. Theory (ISIT), p. 136 (2004).
Lo, H., Ma, X. & Chen, K. Phys. Rev. Lett. 94, 230504 (2005).
Ma, X., Qi, B., Zhao, Y. & Lo, H.-K. Practical decoy state for quantum key distribution. Phys. Rev. A 72, 012326 (2005).
Brassard, G., Lütkenhaus, N., Mor, T. & Sanders, B. C. Limitations on practical quantum cryptography. Phys. Rev. Lett. 85, 1330 (2000).
Bennett, C. H., Bessette, F., Brassard, G., Salvail, L. & Smolin, J. Experimental quantum cryptography. J. Cryptol. 5, 3 (1992).
Calsamiglia, J., Barnett, S. M. & Lütkenhaus, N. Conditional beam-splitting attack on quantum key distribution. Phys. Rev. A 65, 012312 (2001).
Yuen, H. P. Quantum amplifiers, quantum duplicators, and quantum cryptography. Quantum Semiclass. Opt. 8, 939 (1996).
Dušek, M., Jahma, M. & Lütkenhaus, N. Unambiguous state discrimination in quantum cryptography with weak coherent states. Phys. Rev. A 62, 022306 (2000).
Sixto, X., Zapatero, V. & Curty, M. Security of decoy-state quantum key distribution with correlated intensity fluctuations. Phys. Rev. Appl. 18, 044069 (2022).
Kamin, L., Burniston, J. & Tan, E. Y.-Z. Rényi security framework against coherent attacks applied to decoy-state QKD, arXiv:2504.12248 (2025).
Huang, A. et al. Laser-damage attack against optical attenuators in quantum key distribution. Phys. Rev. Appl. 13, 034017 (2020).
Ruzhitskaya, D. D. et al. Vulnerabilities in the quantum key distribution system induced under a pulsed laser attack. J. Sci. Tech. Inf. Tech. Mech. Opt. 136, 837 (2021).
Alferov, S. V., Bugai, K. E. E. & Pargachev, I. A. Study of the vulnerability of neutral optical filters used in quantum key distribution systems against laser damage attack. JETP Lett. 116, 123 (2022).
Bugai, K. E., Zyzykin, A. P., Bulavkin, D. S., Bogdanov, S. A., Sushchev, I. S. & Dvoretskiy, D. A. Laser damage attack on a simple optical attenuator widely used in fiber-based QKD systems, Proc. 2022 Int. Conf. Laser Optics (ICLO), p. 1 (2022).
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145 (2002).
Kulik, S. P., Kravtsov, K. S. & Molotkov, S. N. Experimental resources needed to implement photon number splitting attack in quantum cryptography. Laser Phys. Lett. 19, 025203 (2022).
Huang, A. et al. Laser-seeding attack in quantum key distribution. Phys. Rev. Appl. 12, 064043 (2019).
Liu, W.-T., Sun, S.-H., Liang, L.-M. & Yuan, J.-M. Proof-of-principle experiment of a modified photon-number-splitting attack against quantum key distribution. Phys. Rev. A 83, 042326 (2011).
Ashkenazy, A. et al. Photon number splitting attack—Proposal and analysis of an experimental scheme. Adv. Quantum Technol. 3, 2300437 (2024).
Sushchev, I. S., Bulavkin, D. S., Bugai, K. E., Sidelnikova, A. S. & Dvoretskiy, D. A. Trojan-horse attack on a real-world quantum key distribution system: Theoretical and experimental security analysis. Phys. Rev. Appl. 22, 034032 (2024).
ETSI White Paper No. 27, Implementation security of quantum cryptography, European Telecommunications Standards Institute, Sophia Antipolis, France (2020). URL: https://www.etsi.org/images/files/ETSIWhitePapers/etsi_wp27_qkd_imp_sec_FINAL.pdf
Makarov, V. et al. Preparing a commercial quantum key distribution system for certification against implementation loopholes. Phys. Rev. Appl. 22, 044076 (2024).
Rey-Domínguez, J., Navarrete, Á., van Loock, P. & Curty, M. Hacking coherent-one-way quantum key distribution with present-day technology. Quantum Sci. Technol. 9, 035044 (2024).
van Enk, S. J. Unambiguous state discrimination of coherent states with linear optics: Application to quantum cryptography. Phys. Rev. A 66, 042313 (2002).
Niederberger, A., Scarani, V. & Gisin, N. Photon-number-splitting versus cloning attacks in practical implementations of the Bennett-Brassard 1984 protocol for quantum cryptography. Phys. Rev. A 71, 042316 (2005).
Xu, J. et al. Automatically identifying imperfections and attacks in practical quantum key distribution systems via machine learning. Sci. China Inf. Sci. 67, 202501 (2024).
Coles, P. J., Metodiev, E. M. & Lütkenhaus, N. Numerical approach for unstructured quantum key distribution. Nat. Commun. 7, 11712 (2016).
Winick, A., Lütkenhaus, N. & Coles, P. J. Reliable numerical key rates for quantum key distribution. Quantum 2, 77 (2018).
Deng, Y.-H. et al. Gaussian boson sampling with pseudo-photon-number-resolving detectors and quantum computational advantage. Phys. Rev. Lett. 131, 150601 (2023).
Skryabin, N. N. et al. Heralded generation of programmable two-qubit entangled states on a linear-optical platform. Opt. Quantum 3, 162–167 (2025).
Senellart, P., Solomon, G. & White, A. High-performance semiconductor quantum-dot single-photon sources. Nat. Nanotechnol. 12, 1026–1039 (2017).
Holzman, I. & Ivry, Y. Superconducting nanowires for single-photon detection: Progress, challenges, and opportunities. Adv. Quantum Technol. 2, 1800058 (2019).
Restelli, A., Bienfang, J. C. & Migdall, A. L. Single-photon detection efficiency up to 50% at 1310 nm with an InGaAs/InP avalanche diode gated at 1.25 GHz. Appl. Phys. Lett. 102, 141104 (2013).
Barnoski, M. K. & Jensen, S. M. Fiber waveguides: A novel technique for investigating attenuation characteristics. Appl. Opt. 15, 2112–2115 (1976).
Sajeed, S. et al. Attacks exploiting deviation of mean photon number in quantum key distribution and coin tossing. Phys. Rev. A 91, 032326 (2015).
Lucamarini, M. et al. Practical security bounds against the Trojan-horse attack in quantum key distribution. Phys. Rev. X 5, 031030 (2015).
Bugai, K. E., Sushchev, I. S., Bulavkin, D. S., Lokhmatov, R. Y. & Dvoretskiy, D. A. Protection method against powerful emission attacks based on optical-fiber fuse element, Proc. 2024 Int. Conf. Laser Optics (ICLO), p. 446 IEEE (2024).
Borisova, E. V., Ponosova, A. A., Galagan, B. I., Koltashev, V. V., Rutyunyan, N. A. & Makarov, V. V. Optical fuse as a countermeasure against light injection attacks on quantum key distribution systems, Proc. 2024 Int. Conf. Laser Optics (ICLO), pp. 103–103, IEEE (2024).
Navarrete, Á. & Curty, M. Improved finite-key security analysis of quantum key distribution against Trojan-horse attacks. Quantum Sci. Technol. 7, 035021 (2022).
Ding, H.-J. et al. Improved finite-key security analysis of measurement-device-independent quantum key distribution against a Trojan-horse attack. Phys. Rev. Appl. 19, 044022 (2023).
Acknowledgements
I.S.S. thanks S.P. Kulik for numerous discussions. I.S.S. also acknowledges the scholarship from the Foundation for the Advancement of Theoretical Physics and Mathematics “BASIS”.
Funding
No funding was received for conducting this study.
Author information
Authors and Affiliations
Contributions
I.S. developed the theoretical framework and wrote the manuscript, I.S. and K.B. introduced the scenario for combined LDA and USD attack, I.S. and R.L. executed the numerical simulations, D.B., A.S., V.V. and D.M. aided in interpreting the results and worked on the manuscript, S.M. and D.D. conceptualized and supervised the work.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interests.
Code availability
The code for simulation is available from the corresponding author upon reasonable request.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Sushchev, I., Bugai, K., Molotkov, S. et al. Realistic vulnerabilities of decoy-state quantum key distribution. Sci Rep 15, 44820 (2025). https://doi.org/10.1038/s41598-025-29144-6
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-29144-6