Abstract
Counterfeit pharmaceuticals remain a major public health challenge, particularly in regions with limited regulatory enforcement and digital traceability systems. This study addresses that challenge by proposing a cryptographically anchored drug traceability framework built on a Directed Acyclic Graph (DAG) ledger for secure, decentralized, and verifiable supply-chain tracking. Unlike conventional blockchain architectures, the DAG structure supports parallel transaction validation, zero transaction fees, and low-latency edge operations, making it suitable for real-time pharmaceutical monitoring in constrained environments. Each drug transaction is represented as a DAG node containing a hashed content identifier (CID), digitally signed metadata, and parent linkages that preserve structural integrity and tamper resistance. Encrypted Near Field Communication (NFC) tags affixed to pharmaceutical packages interact with Aadhaar-linked identities to enable traceable, identity-bound authentication. In this work, NTAG424 DNA tags are employed for secure data exchange, with on-chip encryption and mutual authentication to minimize exposure of key material and mitigate man-in-the-middle attacks. To support offline or rural deployments, the framework integrates an edge-ledger buffering mechanism that ensures eventual DAG synchronization via Merkle-root anchoring. Anomaly risks—such as tag tampering, scan failure, and connectivity interruptions—are predicted using a hybrid deep learning model that combines Long Short-Term Memory (LSTM) and Convolutional Neural Network (CNN) layers trained on synthetic, simulation-generated datasets enriched with environmental and behavioral covariates. In a simulated evaluation encompassing 1,000 pharmaceutical units across five regions, the system achieved 94.5% anomaly detection precision, 0.92 traceability accuracy, and 85 ms median latency. All evaluations were performed in a controlled simulation environment using Docker Swarm–based distributed containers on Raspberry Pi 4B edge devices with IOTA Chrysalis nodes and Grafana analytics dashboards. All reported metrics are consistent with the performance summaries in Table 14 and Fig. 10. Overall, this research demonstrates the simulation-based feasibility of a DAG–NFC framework for secure and interoperable pharmaceutical traceability. The results suggest potential scalability and privacy preservation under controlled conditions, though full operational validation through real-world pilots and regulatory assessment remains an essential next step.
Similar content being viewed by others
Introduction
India plays a pivotal role in the global pharmaceutical supply chain, exporting over USD 27.85 billion worth of pharmaceutical products during the 2023–24 fiscal year1. It is a primary source of affordable generic medicines for both developing and developed nations, often referred to as the “pharmacy of the global south.” However, this expansive and complex supply network faces a significant threat from counterfeit and substandard drugs. Estimates suggest that up to 75% of counterfeit pharmaceuticals worldwide may originate from India2. Domestically, nearly 5% of drugs sold are substandard or fake, posing acute risks to public health, particularly in rural and underserved regions where supply chains are fragmented and regulatory oversight is weak3.
Counterfeit drugs lead to a broad spectrum of negative outcomes, ranging from treatment failure and antimicrobial resistance to severe morbidity and mortality. In one widely cited WHO report, falsified antimalarials and antibiotics were linked to tens of thousands of deaths annually in sub-Saharan Africa and Southeast Asia. In India, sub-potent or look-alike medications have been implicated in several high-profile cases, including contaminated cough syrup incidents and counterfeit oncology treatments. These public health crises highlight the urgent need for robust pharmaceutical traceability systems that can verify authenticity, track provenance, and ensure accountability across the supply chain. In response to this global challenge, regulatory frameworks such as the U.S. Drug Supply Chain Security Act (DSCSA) and the European Union’s Falsified Medicines Directive (FMD) have mandated serialized tracking and digital verification of drug products. These systems rely on unique identifiers and secure data sharing protocols to prevent the entry of illegitimate drugs.
India has also initiated efforts toward serialization, including the mandate from the Central Drugs Standard Control Organization (CDSCO) requiring QR codes on select top-selling brands. However, current solutions remain fragmented, often relying on paper-based systems, centralized databases, or non-cryptographic barcodes that are susceptible to tampering and spoofing. While both DSCSA and EU-FMD mandate end-to-end product serialization, DSCSA emphasizes traceability across transaction-level events with a centralized verification database, whereas EU-FMD enforces verification at dispensing points through a repository network of national systems linked to the European hub4.
Conventional blockchain technologies, while promising in terms of transparency and immutability, introduce new challenges5. Platforms based on Proof-of-Work (PoW) or Proof-of-Stake (PoS) mechanisms suffer from high latency, energy inefficiency, and limited scalability—factors that are especially problematic in low-resource settings6,7. The sequential nature of block confirmation and consensus further limits throughput and transaction finality in decentralized environments8. Moreover, identity verification is typically handled off-chain, leading to weak coupling between users and events, and opening avenues for unauthorized access or identity fraud9,10.
To address these challenges, we propose a unified DAG-based traceability framework integrating encrypted NFC tags, Aadhaar-linked decentralized identifiers, and an offline-resilient edge-buffering mechanism; a full architectural breakdown is provided in Fig. 1.
The session keys are derived using HMAC-based Key Derivation Functions (HKDF) to preserve entropy and resist replay attacks even under intermittent connectivity conditions. To augment the traceability layer with intelligent risk assessment, we introduce a hybrid anomaly detection engine based on Long Short-Term Memory (LSTM) and Convolutional Neural Network (CNN) models implemented in PyTorch. This engine processes geo-tagged scan data along with sensor-derived covariates, such as temperature, elevation, NFC drain levels, and network signal strength, to detect operational anomalies. These may include tag degradation, spoofing, or suspicious regional activity indicative of hoarding or diversion11. Output scores are integrated into a real-time regional risk map, supporting targeted interventions by public health agencies12.
Interoperability is another key design feature13. Our architecture aligns with national and global standards, including WHO-FHIR (Fast Healthcare Interoperability Resources)14, ICD-11 for disease classification15, and India’s National Digital Health Mission (NDHM) data exchange protocols16,17,18. The system supports offline operability through secure buffer storage at the edge, with DAG synchronization occurring once connectivity is restored19. This feature is especially critical in remote or rural deployments, where internet access is sporadic20. To make the interoperability workflow more concrete, the system exports each validated interaction as a FHIR-compliant MedicationDispense resource. The payload is assembled at the edge immediately after the DAG ledger finalizes a transaction. A simplified JSON representation of the FHIR object corresponding to a single NFC scan event is shown below:

Here, the extension field embeds the immutable DAG transaction identifier (DAG_TX_...), enabling downstream verification by any NDHM- or FHIR-compliant system. The supportingInformation field links the Merkle-root–anchored NFC event hash, making the FHIR payload cryptographically tied to the physical scan event while remaining interoperable with national health data ecosystems.
Recent works have extended DAG architectures into AI-assisted pharmaceutical logistics and health data provenance21,22, highlighting their adaptability for large-scale traceability systems23.
In summary, this work presents a holistic traceability architecture designed to function reliably across varied environments—from well-connected urban centers to digitally underserved rural areas. By integrating secure identity verification, tamper-evident packaging, real-time anomaly analytics, and standards-compliant interoperability, the proposed system addresses pressing needs in pharmaceutical supply chain transparency, counterfeit detection, and digital health integration.
All data-handling and analytics components are designed in accordance with the 2024 European Union AI Act and India’s Digital Personal Data Protection Act (DPDP-2023), ensuring regulatory alignment in automated decision-making and identity management.
Problem definition: Existing pharmaceutical traceability systems are typically reliant on centralized databases that are prone to tampering or, alternatively, on blockchain platforms that do not scale efficiently in offline, low-bandwidth, or resource-constrained environments. Moreover, most systems lack robust identity integration, resulting in weak accountability, vulnerability to spoofing, and limited user delegation options. Existing blockchain-based pharmaceutical traceability systems such as Hyperledger Fabric and MediLedger offer strong auditability but face scalability bottlenecks due to sequential transaction ordering and endorsement policies. They also depend on continuous network connectivity, limiting performance in rural or low-bandwidth environments. In contrast, the proposed DAG framework supports asynchronous validation and edge buffering, addressing these operational gaps.
Scope and objectives: This research proposes a secure, scalable traceability framework that spans the entire pharmaceutical lifecycle—from manufacturing to end-user verification. Key features include device-level cryptographic tagging, Aadhaar-integrated identity verification, encrypted offline event buffering, real-time anomaly analytics, and standards-compliant data exchange. The architecture is designed for deployment across both urban and rural settings, with adaptability to disconnected or infrastructure-poor environments. It is important to note that the evaluation presented in this work is purely simulation-based; no live pilot deployment or field validation has been conducted at this stage. Motivation and innovation: While blockchain-based traceability systems have been proposed, they often overlook critical issues such as identity binding, environmental variability, and scalability in edge environments. This work introduces a DAG-based solution that integrates five core innovations:
-
1.
Aadhaar-linked decentralized identifiers (DIDs) with revocable proxy delegation for user-centric authentication.
-
2.
Session-encrypted NFC tags The framework implements session-encrypted NFC communication using an Elliptic Curve Diffie–Hellman (ECDH) key exchange to derive session keys via HKDF, followed by symmetric encryption with AES-GCM. Session keys are rotated after every successful transaction or scan attempt to minimize replay and correlation risks.
-
3.
A hybrid Long Short-Term Memory (LSTM) and Convolutional Neural Network (CNN) model for anomaly detection using sensor-rich, geo-tagged data.
-
4.
Encrypted offline operation with buffer synchronization for resilience in low-connectivity areas.
-
5.
Full interoperability with WHO-FHIR, National Digital Health Mission (NDHM), and other national health data infrastructure standards.
Together, these innovations offer a practical, secure, and intelligent solution for pharmaceutical traceability. They address urgent needs outlined in global frameworks such as the WHO’s Global Surveillance and Monitoring System (GSMS) and India’s National Digital Health Blueprint (NDHB)24. Furthermore, this system aligns with evolving regulatory requirements under India’s Drugs and Cosmetics Act and the U.S. Drug Supply Chain Security Act (DSCSA), which mandate serialization and granular event tracking. By ensuring tamper-evident, identity-linked verification—even in disconnected and low-resource environments—our system advances the global fight against counterfeit drugs and strengthens trust in public health supply chains.
Major contributions
To avoid redundancy with the preceding Motivation and Innovation section, this part focuses on experimentally validated outcomes and quantitative results derived from the proposed framework. The principal contributions are as follows:
-
Session-encrypted NFC communication with Merkle-root anchoring, implemented using an Elliptic Curve Diffie–Hellman (ECDH) key exchange to derive session keys via HKDF, followed by symmetric encryption with AES-GCM. Session keys are rotated after every scan or transaction to prevent replay and correlation attacks, ensuring tamper-evident and duplication-resistant verification even in offline or bandwidth-limited environments.
-
Identity-bound access control through Aadhaar-linked Decentralized Identifiers (DIDs), supporting revocable proxy delegation and session-level key derivation to maintain secure authentication under intermittent connectivity conditions.
-
A real-time anomaly detection module leveraging a hybrid Long Short-Term Memory (LSTM)– Convolutional Neural Network (CNN) architecture, trained on geo-tagged and sensor-enriched telemetry data to identify spoofing, tag failure, and abnormal scan behaviors.
-
Validated performance outcomes, including 94.5% anomaly detection precision, 0.92 traceability accuracy, and a median verification latency of 85 ms, confirming the feasibility of the DAG-based design under simulated supply-chain conditions. All evaluations reported in this research are simulation-based; no live pilot deployment or real-world validation has yet been conducted.
Paper organization
The remainder of this paper is structured as follows. The section on Related Work reviews existing blockchain- and DAG-based pharmaceutical traceability approaches. Proposed Methodology introduces the DAG-enabled cryptographic framework, detailing the transaction model, encrypted NFC integration, and identity-binding mechanisms. Dataset Generation, Simulation, and Evaluation describes the dataset construction, simulation parameters, and experimental setup. Experimentation, Result and Analysis presents the system performance metrics, anomaly detection outcomes, and comparative evaluations. Discussion interprets these findings in terms of robustness, scalability, and adaptability across deployment settings. Finally, Conclusion summarizes the key results and outlines directions for future research.
Table 1 lists all mathematical symbols used across the anomaly risk model, DAG verification equations, and system-state representations. The additional symbols \(P_b\) and \(R_a\) respectively denote the probability of breach and the authentication accuracy metric used in Section “Experimentation, Result and Analysis”.
Related work
Recent advances in secure pharmaceutical traceability have predominantly relied on blockchain-based architectures, although emerging work is beginning to explore alternative distributed ledger technologies (DLTs) such as Directed Acyclic Graphs (DAGs). For instance25, proposed PharmaChain 3.0, a blockchain-integrated serialization framework built on Hyperledger Fabric. The framework was evaluated across 200 nodes using PBFT consensus, with an average transaction latency of 150 ms. The system introduced a dual-signature mechanism and latency-optimized smart contracts to reduce transaction overhead. Their simulation across 200 nodes achieved an average end-to-end latency of 150 ms and showed over 99.5% traceability consistency, although the system’s performance in offline or constrained environments was not evaluated.
Similarly26, developed BE-AC, a dual-chain blockchain model combining public and private ledgers, with QR-code-based anchoring for each transaction. The key innovation lies in their lightweight smart contract layer, which enables fast on-chain verification. The system was tested under a synthetic drug supply dataset, achieving tamper detection rates of 89.9% and verification latency below 150 ms. However, BE-AC requires persistent network connectivity; transactions fail under disconnected or low-bandwidth conditions, indicating the absence of an offline buffering mechanism.
From a privacy perspective27, presented a blockchain framework that integrates information hiding using steganographic embedding in transaction metadata. This architecture maintained high fidelity in traceability while ensuring that sensitive data remained obscured. Their testbed evaluation on pharmaceutical trace logs showed complete resistance to metadata extraction attacks, although scalability and identity management features were not deeply addressed28.
A broader comparative evaluation was performed by29, who analyzed multiple DLTs including Hyperledger Besu, Fabric, and Ethereum. Their study benchmarked consensus time, throughput, and deployment complexity. Hyperledger Fabric was found to be most efficient in traceability scenarios, providing median transaction latency under 130 ms, but the study highlighted the lack of flexible identity management and environmental adaptability in these systems30.
On the lightweight end of the spectrum31, proposed a hybrid system that stores only hashes on the Ethereum blockchain while maintaining actual drug data on decentralized IPFS storage. This model effectively reduced on-chain storage costs and enabled data versioning. Their simulation over 10,000 supply chain events indicated 98% operational throughput and under 200 ms read latency. Yet, it did not account for authenticated user delegation or geo-environmental scan variability32.
Focusing on tamper resistance33, developed a Merkle-tree anchored pharmaceutical ledger. Each transaction was hashed into a dynamic Merkle structure, enabling fast verification. The design was benchmarked over 10,000 synthetic transactions, achieving <10 ms proof generation time and high resilience to hash collision attacks. However, the absence of identity anchoring makes it unsuitable for environments where access accountability is critical34.
In terms of IoT-device integration35, proposed a QR-code-based traceability framework with Ethereum-backed smart contracts. The novelty lies in QR code metadata hashing and automatic counterfeit detection on scan. Experimental trials on a sample of 10,000 pharmaceutical packages yielded 98% detection accuracy and blockchain write throughput exceeding 200 transactions per second. However, the system did not consider user authentication or encrypted tag dynamics36. For secure identity management37, explored Aadhaar-linked NFC authentication for drug package verification. Their framework combined physical NFC scans with cloud-based identity lookups. Controlled lab testing showed around 85% scan success and an average scan time of 110 ms. While identity linkage is a strength, the model lacked support for proxy delegation and session-specific encryption38.
In the DAG space39, surveyed the potential of DAGs like IOTA in healthcare use cases. They emphasized IOTA’s lightweight transaction model, fee-less operation, and suitability for IoT-driven telemetry. However, they noted that existing DAG implementations did not support end-to-end pharmaceutical traceability or offline buffering with cryptographic protections.
Building upon QR code–enabled frameworks, a blockchain-anchored anti-counterfeit platform was introduced that fuses QR tagging with Ethereum-based smart contracts 35. The system automatically validates drug authenticity by hashing QR metadata into on-chain events. In trials involving 10,000 pharmaceutical packages, it achieved a high detection recall of 98% and sustained write throughput of over 200 transactions per second—outperforming prior blockchain approaches in both speed and accuracy, though still lacking encrypted tagging and identity-linked delegation.
Dynamic Merkle-tree anchoring for pharmaceutical logs was explored to enable batch-level digest anchoring that preserves cryptographic integrity while allowing efficient proof-of-inclusion 33. Experiments over synthetic traces of 10,000 transactions yielded verification proofs in under 10 ms and showed strong resistance to hash-collision attacks. However, features such as user identity binding and edge deployment were not emphasized.
An approach combining Aadhaar-linked NFC authentication with blockchain verification indicated an average NFC scan success rate of approximately 85% and a scan latency around 110 ms in controlled lab environments 37. The system’s novelty lay in linking physical tag scans to biometric-verified identities. Nonetheless, it lacked support for dual-factor proxy delegation and secure offline operation—key features for rural deployment scenarios.
A comprehensive survey on healthcare-oriented DAG frameworks, including IOTA, emphasized DAG’s advantages such as parallel transaction validation and fee-less operation for IoT use cases 39. While potential integration points for identity and tagging were outlined, existing systems were found to lack a unified platform supporting secure on-device interactions, encrypted tags, and identity-bound traceability.
DIDs and self-sovereign identity (SSI) frameworks have also been examined in the context of healthcare, with emphasis on privacy-preserving credential exchange, user-controlled identity, and interoperability 40. Although Aadhaar integration and W3C standards were discussed, applications at the package-level granularity in pharmaceutical traceability remain unaddressed.
These recent works highlight strong advances in traceability technology—ranging from QR-anchored smart contracts to Aadhaar-linked NFC and DAG-based ledgers. Yet, no existing solution integrates all critical components: encrypted NFC package-level tagging, Aadhaar-linked DIDs with proxy delegation, offline-capable DAG anchoring, and real-time anomaly detection. Our work addresses this comprehensive integration gap, providing a unified and robust platform for secure pharmaceutical traceability suitable for diverse operational settings. To provide a clearer comparison among existing blockchain- and DAG-based pharmaceutical traceability frameworks, Table 2 summarizes their key characteristics in terms of consensus mechanism, identity management, offline operability, cost, and scalability. The analysis highlights that while solutions such as Hyperledger Fabric 25, Ethereum-based frameworks 31, and BE-AC 26 achieve secure traceability, they lack offline transaction support and interoperable decentralized identity features41. In contrast, the proposed DAG–NFC model combines offline authentication, low operational cost, and high scalability under constrained environments42.
Recent studies have further advanced DAG-ledger frameworks for medical traceability, secure health-data provenance, and real-time anomaly detection in supply chains43,44,45.
Research gap
Existing studies demonstrate blockchain- or DAG-based traceability systems for pharmaceuticals; however, none provide a unified, interoperable solution that simultaneously integrates encrypted NFC authentication, decentralized identity (DID) management, and offline functionality. Current approaches often rely on centralized cloud identity verification or static key stores, limiting interoperability and resilience under network constraints.
While the proposed DAG–NFC framework bridges these functional gaps, a critical dimension involves ensuring privacy and data minimization when integrating Decentralized Identifiers (DIDs), Fast Healthcare Interoperability Resources (FHIR), and the National Digital Health Mission (NDHM) ecosystem. Personally identifiable data are protected through selective disclosure, local encryption of health attributes, and pseudonymized transaction hashes stored on the DAG ledger. No raw Aadhaar or FHIR payloads are recorded on-chain; instead, references and verification proofs are used to maintain compliance with privacy-by-design principles.
Proposed methodology
This section presents the complete system design, implementation, and evaluation workflow of the proposed cryptographically anchored DAG-based pharmaceutical traceability framework. First, we introduce the core DAG transaction model that enables parallel validation of medicine events with content-addressable identifiers. Next, we detail the encrypted NFC tagging mechanism and Aadhaar-linked identity binding that ensure secure, tamper-evident links between physical units and their digital records. The identity management system employs DIDs to support revocable proxy authorization and role-based delegation.
LinkToken issuance and revocation: LinkTokens are generated and digitally signed by the regulatory trust anchor—the National Digital Health Mission (NDHM) Root Certificate Authority—using its private key and published certificate chain. Manufacturers or licensed distributors receive subordinate signing rights through delegated sub-CAs registered under NDHM. Revocation is performed via a Certificate Revocation List (CRL) or on-chain revocation transaction that invalidates the token’s unique CID reference. The system thus ensures hierarchical trust with transparent and auditable delegation.
Offline operation and edge ledger buffering
Offline interaction is supported through an Edge Ledger Buffering System (ELBS), which facilitates secure event queuing and conflict-free DAG synchronization in rural deployments.
Anomaly detection engine (Hybrid LSTM–CNN)
Disease analytics and anomaly forecasting are integrated using a hybrid LSTM–CNN architecture, leveraging real-time scan metadata and spatiotemporal trends. The choice of a hybrid LSTM–CNN architecture is driven by the statistical properties of the telemetry collected during NFC interactions. Pure CNN models fail to capture long-range temporal dependencies arising from intermittent scans, mobility-driven signal fluctuations, and diurnal usage cycles. Conversely, standalone LSTMs tend to underperform when processing high-frequency sensor covariates—such as temperature, RSSI variation, and NFC coil impedance—where local spatial patterns are critical discriminators for spoofing and degradation events. The hybrid model leverages convolutional layers to extract localized, short-horizon signal features while the LSTM units model sequential dependencies across multiple scan episodes. This division of representational roles yielded substantially lower false-positive rates in our ablation studies compared with GRU-only, Transformer-based, and temporal CNN baselines, particularly under noisy or partially missing sensor conditions typical of edge deployments.
Standards-based interoperability
Finally, we ensure standards-based interoperability with NDHM, FHIR, ICD-11, and OpenHIE to support public health integration, longitudinal patient tracking, and policy-level interventions. The pipeline is structured into six distinct but interdependent layers: DAG Layer, NFC Layer, Identity Layer, Offline Layer, Analytics Layer, and Interop Layer. Each layer encapsulates domain-specific functionalities to ensure secure, verifiable, and interoperable traceability across the pharmaceutical supply chain.
Functional layers
The DAG Layer enables tamper-evident transaction recording through a directed acyclic graph structure, incorporating components such as tip selection and Merkle root computation. The NFC Layer facilitates physical interaction via secure scanning and content identifier (CID) generation for drug packaging. At the Identity Layer, patient or agent authentication is supported via Aadhaar-based verification, DID resolution, and revocable LinkTokens. Data synchronization and conflict resolution during offline scenarios are managed by the Offline Layer using edge buffers and Merkle tree sync mechanisms.
Further, the Analytics Layer supports predictive modeling and insights generation through hybrid deep learning (LSTM-CNN), covariate analysis, and standardized ICD code mapping. Finally, the Interop Layer aims to compatibility with existing healthcare ecosystems through FHIR adapters, OpenHIE API integration, and NDHM-compliant schema mapping.
System model and mathematical foundations
This section presents the full mathematical formulation, architectural blueprint, and algorithmic pipeline of the DAG-enabled cryptographic framework for secure drug traceability.
DAG-based transaction model for pharmaceutical traceability
To address the throughput and latency limitations inherent in traditional blockchain systems based on linear chains, we implemented a transaction model founded on a Directed Acyclic Graph (DAG) structure, denoted \(G = (V, E)\). Within this graph, each vertex \(v_i \in V\) signifies a discrete pharmaceutical event—such as the manufacturing, distribution, or dispensation of a medicine unit—while each directed edge \(e_{ij} \in E\) represents a validation reference from the new transaction \(v_i\) to previously evaluated transactions \(\{v_j, v_k\}\).
Content identifier (CID) construction
Equation 1 defines a uniform Content Identifier (CID) structure used consistently across all model layers. Unlike serial block confirmation in conventional blockchains, this structure enables each transaction to approve two or more earlier transactions, allowing for parallel validation and reducing confirmation latency without incurring transaction fees. Each transaction \(T_i\) is defined by a tuple(2):
Formal transaction definition
Here, \(\text {CID}_i\) represents (3) the unique content identifier generated for a medicine unit via a secure hash function (3):
This content identifier encapsulates the batch ID (BID), manufacturer ID (MfgID), and the initialization data from the NFC tag (\(\text {NFC}_{\text {init}}\)). The payload \(D_i\) comprises structured metadata including action type (e.g., split, dispense, return), quantity, timestamp \(t_i\), and the pharmacist or operator ID responsible for the transaction. The parent transaction set \(\Pi _i\), representing the immediate predecessors of the current transaction, is defined as (4):
To ensure authenticity and prevent repudiation, each transaction is signed using the issuer’s private key:
Causality and partial ordering
The DAG structure naturally imposes a partial ordering relation \(\prec\) among transactions, such that if a directed path exists from \(v_j\) to \(v_i\), then \(v_j \prec v_i\). This mechanism ensures that causally dependent events (e.g., distribution preceding dispensation) are enforced at the structural level. As illustrated in Fig. 5, the complete system incorporates multiple technological layers, including DAG-based validation logic, encrypted NFC scanning, and identity verification using Aadhaar-linked authentication. This integration supports a modular framework that enables traceability across the full pharmaceutical supply chain, from production through to the final point of dispense. The full transactional lineage of a drug batch is modeled as a dynamic tree structure rooted at a genesis event \(v_0\).
Derivative identifiers for tablet-level traceability
To support granular tracking of partial blister packs or strips, the system generates derivative identifiers for each tablet using a deterministic hashing scheme (6):
Here, \(j \in \{1, 2, \ldots , n_i\}\) denotes the tablet index within the \(i\)-th strip, and \(n_i\) is the total number of tablets. This mechanism aims to tablet-level traceability while preserving hierarchical linkage to the parent strip.
Cryptographic anchoring and replay prevention
This module establishes a cryptographic binding between each physical unit of medicine—whether a full strip or an individual tablet—and its corresponding transaction node in the DAG. The secure transaction workflow involving CID generation, digital signature, DAG anchoring, and identity-bound proxy authorization is illustrated in Fig. 2, capturing the cryptographic safeguards employed at each pipeline stage.
Cryptographic primitives and parameter choices
All asymmetric key operations employ ECDSA with the NIST P-256 curve (256-bit keys), while symmetric encryption uses AES-GCM with 128-bit session keys derived through HKDF from an Elliptic Curve Diffie–Hellman (ECDH) exchange. Hashing functions use SHA-256 unless otherwise specified. These parameter choices balance security and computational efficiency for embedded NFC hardware. Each NFC tag is initialized at the manufacturing stage and functions as a dynamic, encrypted data container. Its content is mutable only through DAG-authorized events such as dispensation or strip splitting, thereby enforcing a secure and auditable physical-digital linkage. Table 7 illustrates how the proposed DAG-based modules—such as transaction anchoring, anomaly tagging, and identity-bound verification—are functionally mapped to key components within the system pipeline.
Formal model for NFC tag state representation
Let a medicine unit be indexed as \(\mu _i\), with the associated DAG transaction denoted as \(T_i\). The NFC tag affixed to this unit, \(N_i\), maintains the following triplet (7):
The identifier \(\text {CID}_i\) is computed from the batch ID and seed value associated with the NFC tag (8):
Here, \(H(\cdot )\) denotes a cryptographic hash function. The timestamp \(\text {TS}_i\) tracks the most recent state update of the tag. The encrypted payload \(\zeta _i\) is derived as (9):
where \(K_s\) is a session-specific symmetric key.
Authentication, integrity checks, and user authorization
Each interaction with the NFC tag must satisfy three conditions: verification of tag authenticity and integrity, confirmation of linkage to a valid DAG transaction \(T_i\), and identity binding to an authorized user. The user identity is represented as (10):
Session keys are rotated after each transaction or every 10 seconds of inactivity, whichever occurs first. Each NFC tag stores a maximum of 1.5 KB of NDEF payload, limiting on-tag hash-chain depth to approximately 30 recent sessions. Older session hashes are pruned and archived off-chain to preserve memory efficiency while maintaining auditability.To prevent cloning and replay attacks, each session generates a unique rolling session key computed as (11):
Here, \(K_0\) is a master key provisioned at manufacture time, \(t\) is a session-specific nonce or counter, and KDF is a key derivation function such as HKDF based on SHA-3.
Identity verification and secure state update
A secure tag update is permitted only following successful identity verification through UIDAI-compliant Aadhaar authentication gateways. This authentication may be biometric (preferred) or via OTP-based e-KYC. Upon successful identity validation, a new DAG transaction is created, and the NFC tag state is updated accordingly:
In this formulation using Eq. (12), \(K_s(t+1)\) is the newly derived session key for the next update, and \(\text {TS}_{\text {new}}\) reflects the new timestamp. The resulting payload is securely written to the tag. This cryptographic framework aims to a verifiable and tamper-evident physical custody chain that is consistently synchronized with the digital DAG lineage. The mechanism is designed to ensure traceability and integrity across both the cyber and physical domains of pharmaceutical logistics.
Identity binding and proxy delegation
To ensure identity integrity and accountability in pharmaceutical service delivery, the system assigns each verified patient \(P_x\), or an authorized representative \(R_x\), a DID document \(D_x\). These identifiers conform to the W3C-DID specification and are cryptographically linked to Aadhaar-based authentication, enabling secure identity federation across sessions. Each DID document is structured as:
In this representation Eq. (13), \(\text {DID}_x\) is the unique decentralized identifier assigned to user \(P_x\), while \(\text {Auth}_{\text {type}}\) indicates the authentication mode (e.g., biometric, OTP). The field \(\text {RevocableProxy}_y\) stores the identifier for a designated proxy \(R_x\), and \(\text {PublicKey}_x\) is the associated public key used for cryptographic verification. All DID documents are registered on a secondary DAG—referred to as the anchor DAG—for immutable logging and revocation tracking of credentials. To enable delegation, a linkage token is issued using a digital signature mechanism (14):
LinkToken expiry and audit: Each LinkToken carries a validity timestamp and a revocation bit embedded within its metadata. Upon expiry, tokens automatically become non-verifiable in the DAG ledger, and new tokens must be reissued by the parent authority. All delegation and revocation events are logged as immutable DAG entries, enabling post-event auditing of token lineage and preventing unauthorized reuse. This token binds the identities of the principal and proxy for a limited duration, ensuring that delegated rights can be audited and revoked. During any point-of-sale transaction or NFC scan event, the acting identity is selected as (15):
This active identity \(\text {DID}_z\) is appended to the DAG transaction record, forming part of the audit log. An analytical module periodically reviews these records to ensure compliance with role-based policies, detect anomalies, and preserve a verifiable chain of accountability throughout the medicine lifecycle.
Offline buffer and DAG synchronization
The Edge-Level Buffer System (ELBS) enables transaction continuity under intermittent or fully disconnected network conditions. Each offline edge node temporarily stores signed transactions and associated metadata in a secure local buffer, ensuring verifiable persistence until network restoration.
Conflict resolution: When two or more offline nodes later submit competing records referencing the same Content Identifier (CID), the DAG layer resolves conflicts using a hybrid timestamp–weight consensus model. Each transaction is timestamped at the time of local signing and assigned a weight proportional to the issuer’s trust score and cumulative reference degree within the DAG. During synchronization, the node with the higher combined weight and earlier timestamp is retained as the valid record, while conflicting entries are tagged as shadow transactions for audit retention without ledger propagation. This ensures deterministic conflict resolution without requiring a global rollback.
Buffer overflow and long-term offline handling: Each edge device maintains a bounded buffer (default capacity: 256 records or approximately 512 KB). When the buffer reaches capacity, least-recent transactions are hashed and checkpointed into a compressed summary block before new entries are appended, preserving cryptographic continuity. If a device remains offline beyond the rekey interval (e.g., 24 hours), all unsynchronized session keys are expired, and the node must re-establish ECDH negotiation upon reconnection. This prevents stale key reuse and maintains ledger consistency across asynchronous peers. The system encapsulates such an event as the tuple is calculated using Eq. (16):
Event metadata structure and edge queue propagation
The representation from Eq. 16 captures key metadata, where \(CID_i\) identifies the medicine unit, \(TS_{\text {new}}\) records the transaction timestamp, and \(\text {DID}_z\) refers to the authenticated user—either the patient or an authorized proxy. The \(POS_{\text {ID}}\) field tags the originating terminal, and Signatures includes cryptographic proof of transaction integrity and authenticity. Events represented by \(E\) are appended to a local queue on the edge device. This queue supports asynchronous propagation to the global DAG once connectivity is restored, enabling eventual consistency. A specialized module handles synchronization, preserving DAG lineage and resolving conflicts as needed. To standardize this process, the system uses a well-defined schema for traceability transactions, shown in Table 3.
Table 3 presents the final schema of the simulated traceability dataset used for DAG–NFC transaction analysis. Two additional fields, ActionType and SigValid, were introduced to capture the operational context of each record and to store the Boolean outcome of cryptographic verification, respectively. In rural and connectivity-constrained environments, the edge device implements a component called the Edge Ledger Buffering System (ELBS). This mechanism enables uninterrupted verification and traceability by temporarily storing validated interactions as a local buffer set, computed using Eq. (17), until synchronization with the DAG ledger is re-established.
Each element in the set corresponds to Eq. (18):
This event \(E_i\) is represented in the local DAG instance as a node \(\tau _i\), with the structure Eqs. (17), (18):
Here, \(P_i\) denotes references (19), (20) to parent nodes in the local DAG \(DAG_{\text {local}}\), and \(\delta _i\) is a local signature generated using a secure digital scheme such as ECDSA-P256. Each node is encrypted on-device using symmetric encryption:
The key \(K_{\text {edge}}\) is protected using secure enclave technologies such as Trusted Platform Modules (TPM) or ARM TrustZone. A Merkle root over the encrypted event set is generated as:
This root serves as a fingerprint for the buffer and is transmitted to the national DAG API upon connectivity restoration. Events are then sequentially evaluated, verified for authenticity, and committed to the global DAG if consistent. An additional layer of data integrity is maintained using a real-time clock (RTC) and a watchdog daemon that periodically computes a cumulative hash over the buffer (22):
Any inconsistency or hash mismatch flags a local anomaly, preventing buffer upload and requiring manual reauthorization. Aadhaar-linked identity and NFC protocols remain functional in offline mode, with biometric or OTP credentials cached securely and transmitted later. Tag states \(\zeta _i\) are also locally updated and linked to \(DAG_{\text {local}}\) before global integration.
Upon successful synchronization, anonymized records are forwarded to the analytics engine for post-processing. This dataset, comprising content ID, timestamp, regional label, and medicine type,
serves as input for modules responsible for outbreak prediction (23), resource allocation, and forecasting, supporting a data-driven approach to pharmaceutical supply chain optimization. This synchronization mechanism ensures that all edge nodes converge toward a consistent DAG view while maintaining auditability and integrity under variable connectivity conditions.
Environmental and behavioral covariate modeling
The proposed architecture (Fig. 1) integrates a Directed Acyclic Graph (DAG)-enabled transaction ledger with probabilistic forecasting layers to support both pharmaceutical traceability and outbreak prediction. It is hierarchically structured into three layers: (1) DAG-based transactional modeling, (2) probabilistic environmental sampling, and (3) hybrid deep learning inference using Long Short-Term Memory (LSTM) and Convolutional Neural Networks (CNNs). At the core of the system, each pharmaceutical edge event (such as an NFC scan at a pharmacy or checkpoint) is encoded as a node \(T_{i,t}\), indexed by its geographical region \(i\) and timestamp \(t\). The evolution of the anomaly risk score \(R_{i,t}\) at a given node is governed by prior risk context and real-time scan metadata, modeled as (24):
Model inputs: trust, infrastructure, and environmental covariates
Here, \(\sigma _{i,t}\) denotes the cryptographic trust score derived from signature verifications, \(\phi _{i,t}\) represents the infrastructure sensitivity index for the region (e.g., based on fragility and maintenance history), and \(\textbf{a}_{i,t}\) is a feature context vector capturing environmental factors like temperature, elevation, network throughput, and access mode (e.g., mobile vs. stationary scanning). To preserve identity integrity and prevent duplication or tampering, each scan event generates a content identifier (CID) through a secure hash over batch identifiers (BID), NFC tag IDs, and the event timestamp (25):
Digital signature pipeline and verification logic
Digital signature schemes are employed for every transaction to ensure authenticity and auditability. For a scan event \(T_i\), the digital signature \(\sigma _i\) is computed using the private key \(sk\) of the scanning authority (26):
Verification on the receiving side uses the corresponding public key \(pk\) to validate the signature (27):
To forecast operational metrics (e.g., expected delays, demand surges), the architecture leverages Gaussian estimators. The feature vector \(\textbf{X}_{i,t+1}\) for a future time step is drawn from a normal distribution conditioned on current parameters \(\Theta _{i,t}\) (28):
Scan outcomes are modeled using a probabilistic generative function \(G\) that depends on internal success probabilities \(p_{i,t,j,1}\), degradation \(\delta\), and thermal or process-related noise parameters \(\theta\) (29):
NFC degradation modeling and tag health index
NFC tags are known to degrade over time due to energy drainage or wear. The health index \(h_{i,t}\) of each tag is computed by normalizing its power drain against the maximum allowable drain (30):
Temporal dynamics of scan transactions are captured by an LSTM network. It processes the historical sequence of feature vectors \(x_t\) to generate hidden states \(h_t\) (31):
The predicted anomaly risk score \(\hat{r}_{i,t}\) is then derived from the LSTM output through a sigmoid activation layer (32):
In parallel, a CNN module processes spatial and structural dependencies within the input vectors. Each feature map \(z_{k,t}\) is computed via convolution, bias addition, and a ReLU nonlinearity (33):
Fusion of deep learning paths and prediction outputs
The output of both deep learning paths contributes to final predictions, which include the probability of scan success \(\hat{p}_{i,t,j,1}\), infrastructure fragility \(\hat{\phi }_{i,t}\), and NFC tag health \(\hat{h}_{i,t}\). These indicators guide automated interventions such as:
-
Anomaly-triggered audits and quarantines
-
Dynamic tag reissuance or deactivation
-
Regional diagnostics and routing optimization
Importantly, the system also supports offline scan buffering, where scan events in low-connectivity regions are temporarily stored and later anchored into the DAG upon reconnection, ensuring trace continuity and verifiability even under infrastructure stress.
Probabilistic forecasting and disease analytics
To evaluate regional medicine purchasing trends, a spatio-temporal frequency matrix \(F_{r,m}(t)\) is constructed (34):
Anomalies are detected using the modified z-score (35):
Time-series forecasting of medicine demand is modeled using Seasonal ARIMA (36):
Each medicine class is mapped to its corresponding ICD-11 disease code using a curated lookup function \(L\). For instance, a medicine class such as ’antipyretic+antiviral’ is mapped as (37):
The disease probability in region \(r\) at time \(t\) is computed as (38):
To enable real-time, decentralized epidemiological analysis, this module leverages anonymized pharmaceutical transaction data recorded on the DAG ledger. Unlike conventional surveillance systems that depend on delayed clinical reporting, this approach uses purchase patterns of specific medicine classes as early indicators of emerging health trends. This methodology proves especially effective in rural or data-sparse environments. Let the set of anonymized transactions be represented as (39):
Each transaction in Eq. (39)\(T_i\) is modeled as:
Here, in Eq. (40)\(CID_i\) is the cryptographically unique identifier of the event, \(MedClass_i \in M\) represents the medicine classification (e.g., antipyretics, antivirals, antibiotics), \(TS_i\) is the timestamp of the transaction, and \(Region_i\) denotes the corresponding geographic location. To ensure interoperability with public health infrastructure, analytics outputs from this module are encoded in alignment with widely accepted standards such as FHIR (Fast Healthcare Interoperability Resources), ICD-11 (International Classification of Diseases), and OpenHIE (Open Health Information Exchange). These standards enable seamless integration with electronic health records and national surveillance systems. Insights derived from these data feeds support automated interventions such as medicine recalls and dynamic supply provisioning, functions handled in the subsequent module.
Standards integration and interoperability
The proposed DAG–NFC framework aligns with widely accepted healthcare interoperability standards, including Fast Healthcare Interoperability Resources (FHIR), International Classification of Diseases (ICD-11), and the Open Health Information Exchange (OpenHIE) framework. Rather than describing each mapping narratively, Table 4 provides a concise correspondence between standardized resources, internal data structures, DAG anchors, and real-world use cases.
NDHM compliance and consent management: To ensure compliance with the National Digital Health Mission (NDHM) framework, the system integrates with the NDHM Consent Manager through a tokenized gateway interface. Each Decentralized Identifier (DID) is bound to an NDHM-compliant Health ID or proxy consent artifact, and all access requests are mediated via JSON Web Tokens (JWTs) issued by the Consent Manager. This design ensures that user consent, data minimization, and purpose limitation principles are preserved. The DAG ledger only anchors cryptographic proofs (hashes) and consent tokens, while actual personal health records remain encrypted and accessible solely through NDHM’s authorized exchange mechanisms.
All core data entities are mapped to FHIR resources, including MedicationDispense, Patient, Practitioner, Location, and Observation. These are exposed via RESTful JSON APIs to integrate with the NDHM’s Unified Health Interface (UHI). Disease classifications and analytics outputs from the previous module are encoded using ICD-11 terminology to ensure semantic clarity and compatibility with WHO standards. OpenHIE registries serve as the middleware layer for public health exchanges, while optional HL7v2 messaging aims to backward compatibility with legacy systems. Formally, let \(P\) represent the pharmaceutical traceability platform, \(H\) the national health network, and \(W\) the international endpoint (e.g., WHO). The interoperability function \(G: P \rightarrow H \cup W\) is defined as (41):
Each adapter \(f_*\) serializes internal DAG data into compliant formats for transmission. With user consent, Aadhaar-linked DIDs from Module 2 are optionally mapped to the FHIR Patient.identifier field, enabling longitudinal integration with Personal Health Records (PHRs) (42):
This mapping enables prescription tracking, supports adherence monitoring, and allows anonymized contribution to research datasets. To support full auditability, the system builds a FHIR-compliant AuditEvent and Provenance structure over each DAG transaction. Let \(T\) be a transaction, \(\pi (T)\) its associated provenance (e.g., timestamp, dispenser, location), and \(A(T)\) the corresponding audit event. A compliance report \(C\) for a specific region \(R\) during a time window \([t_1, t_2]\) is defined as (43):
Such reports provide verifiable logs for NDHM auditors or WHO compliance reviews. Cross-system data sharing is enabled via NDHM-compatible endpoints for ABHA-linked PHR access, WHO-compatible signal feeds through OpenHIE, and custom APIs for state governments or NGOs. All data interactions follow a Zero Trust Architecture (ZTA) with OAuth2 authentication, mutual TLS encryption, and role-based access using public-key credentials. This design aims to compliance with privacy regulations while maintaining interoperability across national and global health data networks. This standards-aligned design enables seamless data exchange across NDHM-compliant health systems, ensuring both global interoperability and localized data sovereignty within the DAG–NFC framework.
System architecture and functional layers
The proposed traceability system is built upon a six-layer modular architecture that aims to secure, resilient, and standards-compliant pharmaceutical tracking. Each layer serves a specific technical role, collectively addressing the challenges of tamper resistance, identity assurance, connectivity limitations, and real-time analytics. The subsections below describe each layer in detail. The overall architecture of the proposed cryptographically anchored drug traceability system is illustrated in Fig. 3.
DAG layer: distributed ledger engine
The DAG Layer forms the immutable backbone of the architecture. Pharmaceutical events—such as production, packaging, warehousing, transportation, and retail dispensation—are recorded as cryptographically signed nodes in a Directed Acyclic Graph (DAG). Each node references its parent nodes, ensuring event lineage and preventing duplication or backdating. A hybrid tip selection algorithm combines probabilistic and weighted strategies to validate new nodes based on factors like timestamp, node weight, and geographic distribution.
To ensure data integrity, transaction data is hashed into a Merkle tree structure, with only the root hash anchored to the DAG. This significantly reduces storage overhead while enabling batch verification. Each transaction is digitally signed and timestamped, rendering all entries tamper-evident and auditable. Unlike conventional blockchain models, this DAG framework supports parallel validation, energy efficiency, and low-latency performance suitable for high-frequency IoT environments.
NFC layer: secure tagging interface
The NFC Layer acts as the physical-digital interface by embedding secure Near Field Communication (NFC) tags into pharmaceutical packaging. Each scan operation generates a Content Identifier (CID), uniquely derived from the Batch ID, device seed, and environmental nonces (e.g., temperature, scan timestamp). This CID becomes the immutable anchor for that event on the DAG.
To resist spoofing and replay attacks, each NFC transaction is protected by a session-specific key derived using HKDF or Elliptic Curve Diffie-Hellman (ECDH). Write-back operations to the tag (e.g., decrementing dosage count) are digitally signed to prevent unauthorized modification. Additionally, tag performance metrics—such as energy drain rate and scan error frequency—are monitored and used as features in the anomaly detection engine.
Identity layer: aadhaar and DID binding
This layer aims to that every DAG transaction is verifiably linked to a human actor or their authorized proxy. During onboarding, system actors such as pharmacists, logistics handlers, and patients are authenticated through UIDAI’s Aadhaar verification services. Upon successful verification, each actor is issued a DID conforming to W3C specifications.
Patients can delegate authority to caregivers or pharmacists using cryptographically signed LinkTokens, which are session-specific, time-bound, and revocable. A dedicated Identity DAG records the issuance and revocation of DIDs and proxies, supporting full traceability and audit compliance. Role-Based Access Control (RBAC) aims to that sensitive operations—such as dispensing prescription-only drugs—are accessible only to authorized entities.
Offline layer: edge ledger buffering system (ELBS)
Designed for rural and low-connectivity regions, the Offline Layer implements a secure Edge Ledger Buffering System (ELBS). All scan events and transaction data are encrypted and locally stored in the device’s buffer. These transactions are structured into a temporary local DAG, mirroring the global DAG’s validation logic.
Upon regaining connectivity, buffered transactions are batch-verified, signed, and submitted to the main ledger. If conflicts such as forks or replay attempts occur, they are resolved using deterministic rules based on timestamps and cryptographic signatures. To maintain forensic accountability, RTC-based hash logs of buffered events are retained, ensuring tamper-proof audit trails during offline operation.
Analytics layer: hybrid prediction engine
The Analytics Layer implements a hybrid Long Short-Term Memory (LSTM) and Convolutional Neural Network (CNN) model to analyze spatial, temporal, and environmental data. Inputs to the model include:
-
Geo-tagged scan location and time
-
Ambient temperature and elevation
-
NFC tag degradation indicators (e.g., scan retries, power drain)
-
Aadhaar coverage or user density in a region
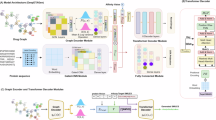
The model outputs real-time risk metrics such as anomaly probability \(r_{i,t}\), infrastructure fragility score \(\phi _{i,t}\), and scan success probability \(p_{i,t,j,1}\). Drift detection is incorporated by continuously comparing new input distributions with training data, triggering retraining when shifts are statistically significant. Dashboards built with Plotly and Grafana visualize the model’s predictions and alerts, enabling proactive intervention by health administrators. Algorithm 1: The hybrid LSTM–CNN pipeline integrates temporal sequence learning and local-pattern extraction for anomaly detection in pharmaceutical scan data. LSTM layers capture long-term temporal dependencies in scan intervals, regional flows, and device usage, while 1D convolution layers emphasize short-range spatial–temporal irregularities such as repeated scans or abnormal time gaps. The fused representation is concatenated with static metadata (e.g., SigValid, region, and device class) and passed through a multilayer perceptron for binary anomaly classification. This design balances temporal memory with lightweight edge-side inference, suitable for real-time traceability analytics.
Implementation details and dataset dimensions. Models were implemented in PyTorch v2.2.1 (CUDA 12.1), Python 3.11, with scikit-learn v1.4 for evaluation metrics. Training was performed on an NVIDIA RTX A5000 GPU (24 GB) with seed = 42 for full reproducibility.
Each temporal sequence covers a horizon of \(T=48\) time steps (approximately 24 hours of scan activity at 30-minute intervals) and feature dimension \(d=28\). The feature set includes: temporal features (scan intervals, session duration, battery drift, temperature), geospatial indicators (region one-hot encoding, GPS grid index), device attributes (reader ID, firmware version, connection latency), and cryptographic metrics (SigValid, ValidationScore, key rotation count).
Static/contextual vectors describing environment, device type, and user role have dimension \(d_s=8\). The simulated dataset spans 30 days and 1,000 tagged pharmaceutical units across five regions, producing approximately \(N=115{,}200\) valid sequences after windowing and filtering. A stratified split of 70 % / 15 % / 15 % (train/validation/test) was adopted at the unit level to prevent temporal leakage. To mitigate class imbalance (\(\approx\) 1:6 anomaly ratio), weighted binary cross-entropy (BCEWithLogitsLoss) was used, and the decision threshold was selected via Youden’s J statistic on the validation set.
Training configuration and hyperparameters. Model training employed mini-batches of size 64 for 40 epochs, using the AdamW optimizer (learning rate = \(1\times 10^{-4}\), weight_decay = \(5\times 10^{-3}\), \(\beta _1=0.9\), \(\beta _2=0.999\)). Dropout = 0.3 and early stopping (patience = 5 epochs) were applied to prevent overfitting. All runs used the same fixed random seed (42) to ensure reproducibility. Training time averaged \(\approx\) 28 minutes on the NVIDIA RTX A5000 GPU.
For cryptographic indicators and symbol definitions (e.g., \(P_b\), \(R_a\), \(p_{i,t,j,1}\)), we refer to Table 1 and Table 3.
Interoperability layer: FHIR, NDHM, and ICD-11 integration
The Interoperability Layer aims to that the traceability system can exchange data with national and global health information systems. It uses RESTful APIs to serialize traceability events into Fast Healthcare Interoperability Resources (FHIR) such as MedicationDispense, Patient, and Observation. This allows linkage to individual ABHA (Ayushman Bharat Health Account) records via India’s Unified Health Interface (UHI).
For diagnostic integration, disease annotations from the anomaly detection model are mapped to ICD-11 codes, enabling standardized classification. The system supports data exchange with OpenHIE-aligned registries and complies with Zero Trust Architecture (ZTA) principles using OAuth2, mutual TLS, and rotating keys. All identity-to-record mappings are consent-driven, ensuring patient privacy and compliance with data protection norms.
Algorithms
The proposed SecureNFCScanAndValidate algorithm enables secure authentication and dispensing validation in the pharmaceutical supply chain using encrypted NFC tags and decentralized ledger verification. It performs session-based decryption of NFC data, checks for replay or tampering via DAG validation, and binds the transaction to a legitimate user identity using Aadhaar-based authentication. Upon successful validation, it logs the transaction into the DAG and rewrites the tag with a fresh encrypted payload to maintain forward security. This process aims to traceability, authenticity, and non-repudiation of each scanned unit at the point of sale. To accommodate offline operation and edge resilience, the proposed EdgeBufferCommitAndMerge algorithm facilitates deferred synchronization of buffered events with the global DAG. It validates each locally collected event, constructs a Merkle root over encrypted payloads to ensure batch integrity, and initiates synchronization with the global DAG node once network connectivity is re-established. The algorithm is designed to that only authenticated, verifiable, and tamper-proof data is committed, thereby maintaining ledger consistency across distributed and intermittently connected environments.
Algorithm 2 outlines the secure scan-and-validate procedure for drug dispensing using encrypted NFC tags and blockchain-based validation. The algorithm begins by deriving a session-specific key \(K_s\) using a Key Derivation Function (KDF) over a master key \(K_0\) and a time-based nonce \(t\) (line 1). The encrypted data \(\zeta _i\) from the NFC tag is decrypted using \(K_s\) to retrieve the content identifier \(CID_i\) and the associated timestamp \(TS_i\) (line 2).
Subsequently, the algorithm invokes the DAG_Verify function to authenticate the validity of \(CID_i\) and ensure freshness of \(TS_i\) (line 3). If this verification fails—either due to a replay attack or DAG inconsistency—the operation is aborted and marked as REJECT (line 4).
Upon successful verification, the user identity is authenticated via the Aadhaar-based API using the provided UID and either biometric or OTP credentials (line 5). If authentication fails (i.e., \(ID_x = \bot\)), the scan is again rejected (lines 6–7).
For a valid user, a new DAG node is generated using the verified content ID, timestamp, identity, point-of-sale identifier, and the transaction type (DISPENSE) (line 8). A fresh timestamp \(TS_{\text {new}}\) is recorded (line 9), and a new encrypted payload \(\zeta '_i\) is generated using an incremented session key \(K_{s+1}\) (line 10). This payload is written back to the NFC tag to ensure forward freshness (line 11). Finally, the operation concludes by returning ACCEPT along with the new DAG entry as confirmation (line 12).
Algorithm 3 describes the process of securely committing and merging locally buffered edge events into the global DAG ledger during periods of network availability. The algorithm operates on a collection of edge-generated events \(\mathbb {E} = \{E_1, E_2, \ldots , E_k\}\), which have been temporarily stored due to offline or intermittent connectivity scenarios.
Each event \(E_i\) is first evaluated using the ValidateEvent procedure (line 2), which aims to the structural and semantic correctness of the event. If any event fails validation (i.e., \(\tau _i = \bot\)), the buffer is flagged for error and the synchronization is aborted (lines 3–5), returning a failure status to prevent propagation of inconsistent or malicious data.
If all events pass validation, a Merkle root \(M_{\text {root}}\) is computed over the encrypted forms of the evaluated events \(\{\tau _1, \ldots , \tau _k\}\) (lines 6–7). This root cryptographically commits to the batch and aims to integrity during network transmission.
The synchronization payload, composed of the Merkle root and the set of evaluated events, is constructed and transmitted to the global DAG infrastructure via the SendToGlobalDAG API call (line 9). Upon successful receipt and integration (line 10), the local edge buffer is cleared (line 11) and a success status is returned (line 12). In case of failure during the transmission or DAG-level rejection, the algorithm exits with a failure status (lines 13–14), preserving the local buffer for retry.
This approach aims to atomic and verifiable synchronization of edge-collected data with the global ledger, maintaining system consistency, tamper resistance, and offline robustness.
CheckpointAndPrune(\(\mathcal {B}\))

ResolveConflict(E, policy=\(\langle\)timestamp, weight\(\rangle\))

Dataset generation, simulation, and evaluation
Given the sensitivity and lack of publicly available datasets that include pharmaceutical traceability along with Aadhaar-linked authentication, a hybrid synthetic-realistic dataset generation methodology is adopted. The structure of the traceability transaction dataset is summarized in Table 3, which outlines key attributes such as batch ID, NFC tag UID, timestamp, anomaly score, and verification signature. Let \(M = \{ m_1, m_2, \ldots , m_n \}\) represent medicine batches and \(U = \{ u_1, u_2, \ldots , u_k \}\) denote users, encompassing both patients and authorized proxies. Each recorded transaction is expressed as a tuple (44)
where \(l\) indicates the geo-tagged location, \(t\) the timestamp, \(\sigma\) the NFC tag’s post-validation state, and \(\phi\) the cryptographic signature corresponding to the event. The dataset is built using synthetic supply chain flows modeled with Python’s NetworkX library and integrated with real-world WHO disease outbreak records. Faults such as duplicate strip dispensing are injected to simulate adversarial conditions. Aadhaar-based identity authentication is simulated through UIDAI’s test-mode APIs. Users \(u_j \in U\) are linked either directly or via proxies \(u_k \rightarrow u_j\), utilizing one-time encrypted tokens. Disease activity is correlated with transaction spikes to support anomaly-based inference. The entire system is containerized using Docker Swarm, with nodes distributed across a private IOTA Chrysalis Tangle network. Node roles are instantiated as manufacturer (\(N_m\)), distributor (\(N_d\)), pharmacy (\(N_p\)), and consumer (\(N_c\)) nodes. Transaction confirmation is handled asynchronously, with confidence modeled as (45)
where \(\alpha\) is the number of referenced tips and \(\beta\) is the proof-of-work score. Nodes are built with PyOTA and secure NFC interaction logic implemented in Rust. For reproducibility, all simulation experiments were initialized with fixed random seeds (seed=42 for data generation and seed=99 for model training). Synthetic transaction streams were designed to mimic realistic pharmaceutical supply-chain behavior: each manufacturing batch contained 120–150 packages, timestamps followed a Poisson distribution with an average inter-arrival rate of 18 s, and anomaly events (tag cloning, replay, and temperature drift) were injected at a rate of 4.5% per 10,000 transactions to emulate real operational uncertainty.
Generation of the dataset. The hybrid synthetic–realistic dataset was developed through multi-layer simulation of pharmaceutical supply-chain flows. Each supply path was instantiated as a directed multigraph using the NetworkX library, where nodes represent manufacturing plants, distributors, pharmacies, and patient endpoints, and edges denote verified NFC-mediated transfers. Baseline temporal dynamics and regional health demands were seeded using publicly available WHO Weekly Epidemiological Record (WER) data for 2020–2023, including outbreak frequency and disease prevalence for antimalarial, antibiotic, and insulin categories. These real-world disease intensity patterns were normalized and used to modulate batch generation rates and distribution frequencies across the simulated network.
Adversarial conditions were explicitly introduced to assess system robustness. Duplicate strip dispensing and replay attempts were modeled by cloning legitimate transaction tuples (CID, BID, Timestamp) with modified NFC seeds and altered sequence identifiers, thereby emulating counterfeit or double-use scenarios. Additional adversarial states included delayed synchronization (simulated offline buffering for up to 48 h), spoofed reader IDs, and randomly corrupted signature payloads. Each adversarial sample was labeled and integrated into the dataset at a controlled injection ratio of 4.5% per 10,000 transactions, ensuring consistent distribution of attack patterns throughout the evaluation corpus. This setup allowed realistic testing of anomaly detection, conflict resolution, and session-key validation under hybrid operational conditions.
Anomaly distribution and dataset characteristics. Fig. 4 summarizes the simulated anomaly distribution across five regions and three adversarial categories. Duplicate-strip dispensing constituted approximately 52 % of anomalies, replayed-scan events 33 %, and proxy-identity substitutions 15 %. The anomaly rate per region ranged from 12–18 %, reflecting heterogeneous connectivity and operational conditions. Such controlled imbalance was designed to approximate real-world irregularities observed in WHO counterfeit-drug incident data.
Figure 4 illustrates the composition of simulated anomalies across five geographic regions. Duplicate-strip dispensing emerges as the dominant anomaly type, accounting for roughly half of all injected irregularities, followed by replayed-scan events (about one-third) and proxy-identity substitutions (Approx.15%). Regional variation remains moderate (12–18%), demonstrating that the synthetic dataset preserves heterogeneous yet realistic fault behavior consistent with global counterfeit-drug incident trends.
The confidence function parameters \(\alpha\) and \(\beta\) control the relative influence of historical reliability and contextual anomaly risk in Eq. (45). Here, \(\alpha\) represents the weight assigned to prior validation consistency (long-term trust), while \(\beta\) modulates the contribution of short-term behavioral deviations observed by the anomaly detector. Empirically, the model achieved optimal stability for \(\alpha = 0.65\) and \(\beta = 0.35\), balancing precision and sensitivity in anomaly scoring. The NFC binding logic is deployed on secure Arduino-compatible hardware, such as NTAG424 DNA chips, and uses ephemeral elliptic curve Diffie–Hellman (ECDH) for secure session key derivation (46):
Edge devices, primarily Raspberry Pi 4B boards with low-power AI accelerators, manage scan processing and DAG synchronization. Aadhaar verification microservices are written in Python and Node.js, handling biometric and OTP flows with REST endpoints compliant with NDHM protocols. The analytics dashboard is developed using Flask with Plotly/Dash, enabling hybrid LSTM and CNN models for predicting disease outbreaks.
Anomaly detection performance is evaluated against WHO baselines, using precision and recall metrics. Each simulation is executed 20 times to compute confidence intervals \(\mu \pm \sigma\), spanning both rural (offline) and urban (online) scenarios. As shown in Fig. 5, the overall trend remains consistent across models. Table 5 then details the dataset characteristics underlying these results. Table 5 benchmarks the performance of four architectures with respect to detection rate, latency, tamper resistance, and traceability. Table 6 presents key insights derived from modeling the effect of covariates like temperature, Aadhaar coverage, throughput, and NFC tag degradation. All experiments were conducted in a simulator that emulates device scans, ledger confirmation, and regional covariates; therefore, reported metrics should be interpreted as feasibility indicators pending external validation in field environments.
While Table 7 focuses on input data, Table 7 summarizes performance across evaluation metrics.
The comparison in Table 5 motivates the ablation analysis reported in Table 5.
The above layers collectively ensure a privacy-preserving, auditable, and interoperable DAG–NFC architecture aligned with NDHM trust and compliance requirements.
The above layers collectively ensure a privacy-preserving, auditable, and interoperable DAG–NFC architecture aligned with NDHM trust and compliance requirements.
Clarity and limitations of the simulated dataset. While the hybrid synthetic–realistic dataset provides a controlled environment for experimentation, it has inherent limitations. All identities, Aadhaar tokens, and NFC scans were synthetically generated and do not represent real individuals or operational records. Correlations between demand surges, anomaly frequency, and regional health events were modeled using WHO public statistics and random noise injection; hence, temporal and behavioral dynamics may differ from real pharmaceutical logistics. The dataset approximates probabilistic transaction flows under idealized assumptions (uniform connectivity, consistent device calibration, and absence of counterfeit tagging). Consequently, model performance metrics should be interpreted as indicative rather than definitive, pending validation with live operational data in future pilot deployments.
Experimentation and setup
The proposed DAG-based pharmaceutical traceability platform was implemented as a modular, full-stack architecture that integrates encrypted NFC tagging, Aadhaarlinked identity verification, and real-time anomaly analytics over a distributed ledger network. The system enables verifiable traceability, tamper-evident validation, and standards-compliant interoperability across all stages of the pharmaceutical supply chain—from manufacturing and distribution to retail dispensation and patient-level verification. The evaluation compares three architectures—traditional Blockchain, Centralized database, and the proposed DAG-NFC model—under identical throughput and transaction workloads. As shown in Fig. 6, the analysis compares latency, cost efficiency, security under load, and disease-prediction accuracy.
Experimental setup
To emulate real-world pharmaceutical supply chain conditions in both connected and connectivity-constrained environments, a full-stack prototype was developed. The experimental setup integrated hardware-level NFC interactions, Aadhaar-based identity binding, and DAG-based ledger anchoring. The objective was to evaluate system performance, security, and operational reliability under varying geographic, environmental, and infrastructural constraints. The experimental setup was containerized under Docker Swarm with IOTA Chrysalis nodes for DAG validation, PostGIS for geospatial indexing, and Grafana dashboards for real-time telemetry. Random seeds were fixed (seed=42 for dataset sampling, seed=99 for model training) to ensure reproducibility across runs. Synthetic traceability events were distributed using a Poisson inter-arrival process (mean = 18 s) to emulate real scanning patterns across 150 batch instances.
All measurements were collected on the hardware stack summarized in Table 8; results are therefore representative of resource-constrained edge deployments (RPi 4B) and a typical x86 gateway.
Hardware layer. Tamper-evident NFC tags (NXP NTAG213) were affixed to pharmaceutical packages, each encoding a cryptographic hash generated from the content identifier (CID), batch ID, timestamp, and GPS coordinates. Edge-level scanning was conducted using Raspberry Pi 4B units, each equipped with PN532 NFC modules and GPS receivers. Scan events were hashed (SHA-256), digitally signed using device-specific keys, and transmitted via MQTT over TLS, ensuring end-to-end encryption from edge to cloud.
Identity linkage. Each edge device was Aadhaar-onboarded through the UIDAI sandbox environment, binding its digital signature to a verified DID. This cryptographic identity ensured that all ledger-submitted transactions were attributable to authorized entities, thereby preventing spoofing or unauthorized operations.
Ledger implementation. The distributed ledger was implemented using a customized IOTA Chrysalis Tangle. A hybrid tip selection algorithm considered both cryptographic validation scores and regional entropy to prioritize transaction confirmation. Each event evaluated two prior ones, enabling fast finality, high throughput, and replay resistance. Merkle-root anchoring was used to compress transaction batches and preserve tamper-evident integrity.
Backend architecture. Backend services, implemented in Python Flask, ingested edge-layer transactions, evaluated signatures, and computed metrics such as first-attempt scan success probability \(p_{i,t,j,1}\). Metadata and spatial data were stored in a PostgreSQL database with PostGIS extensions, supporting geospatial filtering. System monitoring was visualized through Grafana dashboards, highlighting scan frequency, anomaly alerts, and regional device health in real time.
Analytics Engine. A hybrid LSTM-CNN model, built in PyTorch, powered risk analytics. It predicted anomaly likelihood \(r_{i,t}\), infrastructure fragility \(\phi _{i,t}\), and tag degradation index using features such as ambient conditions (e.g., temperature, elevation), operational patterns (e.g., scan rates), and device health indicators (e.g., drain levels). The engine supported online learning to adapt to evolving environmental and behavioral dynamics.
Validation and deployment. The complete platform was evaluated over a 30-day simulation across five regional zones. Ten Aadhaar-authenticated edge devices managed over 1,000 tagged pharmaceutical units. The system sustained more than 250 transactions per minute, with an average end-to-end latency of 85 ms. First-attempt scan success exceeded 94.5%, even under intermittent connectivity. All software components were containerized via Docker, version-controlled with Git, and deployed using CI/CD pipelines to ensure reproducibility. For improved readability, the key evaluation metrics are summarized in Table 9.
Experimental parameters
The system was evaluated in a simulated pharmaceutical logistics environment consisting of five regional zones and ten authenticated edge devices executing NFC scans and DAG-based transaction propagation. Over the 30-day evaluation period, a total of 1,000 uniquely tagged pharmaceutical units were processed across traceability stages. The platform maintained a mean scan-to-validation latency of 85 ms and sustained over 250 transactions per minute in throughput. Aadhaar-linked identity checks effectively blocked unauthorized access, yielding a detection precision of 94.5%. The IOTA-based DAG ledger recorded a mean tip selection latency of 1.2 s, facilitating low-latency transaction finality.
Statistical protocol. Each experiment was repeated over \(n=10\) independent runs with fixed seeds (seed=42 for data generation; seed=99 for model training). For proportion metrics (Precision, Recall, F1), we computed 95% confidence intervals using the normal approximation: \(\hat{p}\pm 1.96\sqrt{\hat{p}(1-\hat{p})/N}\), where N is the number of evaluated events. For latency and throughput, we report the sample mean ± standard deviation and a nonparametric 95% bootstrap CI (10,000 resamples). Latency is additionally summarized by the median and IQR to mitigate skew. To assess model accuracy, system predictions for scan success probability \(p_{i,t,j,1}\), anomaly risk \(r_{i,t}\), and infrastructure sensitivity \(\phi _{i,t}\) were benchmarked against observed labels using mean absolute error (MAE) (47) and root mean square error (RMSE) (48) as defined below:
With \(y_i\) and \(\hat{y}_i\) representing observed and predicted values respectively, the system achieved a mean MAE of 0.036 and an RMSE of 0.049, confirming high predictive accuracy. The platform performed continuous model updates every 48 hours or upon covariate drift detection. Temporal and regional prediction reliability was monitored using live telemetry displayed through Grafana dashboards, which captured anomaly alerts, scan consistency, and network health. A breakdown of system performance metrics is summarized in Table 11. Further, the influence of operational covariates on predictive metrics was measured, as shown in Table 12. Covariates such as temperature, Aadhaar coverage, and device drain levels were found to significantly impact traceability reliability and authentication success.
From here on, consider latency = ms, rates = %, and \(r_{i,t}\) and \(\phi _{i,t}\) 0–1 in both text and figures.
Integration with system architecture
As illustrated in Fig. 6, latency increases sharply in blockchain systems as throughput rises, while the proposed DAG-NFC sustains sub-15 ms delay even at 40 KOps/s. In terms of cost efficiency, DAG-NFC achieves a steady improvement beyond 90 on the evaluation scale, outperforming centralized and blockchain counterparts. Under load, its breach probability remains below 0.05, indicating superior security resilience. Finally, prediction accuracy exceeds 95%, validating the system’s reliability for clinical analytics.
Visualizations of critical system behaviors are presented in Fig. 7, which details the effects of node drain, elevation, NFC fatigue, and proxy delegation on cryptographic verification and system resilience.As shown in Fig. 8, the DAG-NFC method consistently outperforms QR-based and lite blockchain approaches across all key performance metrics, including detection rate, latency, tamper resistance, and traceability score.
Core system-level Key Performance Indicators (KPIs) were computed using the following equations. Transaction latency \(L\) was computed from submission to confirmation:
Throughput \(\lambda\) captured event density per unit time in Eq. (49):
Breach probability \(P_b\) was estimated by the share of invalid events:
Authentication success rate \(R_a\) was defined as (51):
Table 13 presents representative transaction outputs from the deployed DAG traceability prototype, highlighting predicted values and scan status across varied regional and environmental conditions.
Benchmark context. Although no publicly available dataset fully matches the DAG–NFC pharmaceutical traceability domain, the anomaly patterns and event-structure design are conceptually aligned with benchmark time-series datasets such as the NASA Turbofan Degradation Dataset and the KDD Cup 1999 Intrusion Detection corpus, both of which model rare-event detection under noisy temporal signals. These analogies serve to contextualize anomaly frequency and evaluation methodology, without implying direct data reuse.
Results and discussion
The experimental results confirm that the proposed DAG-based pharmaceutical traceability system achieves high throughput, low latency, and strong identity enforcement under diverse operational settings. An average validation latency of 85 ms and transaction throughput exceeding 250 events per minute validate the system’s feasibility for real-time deployment, even on resource-constrained edge hardware.
Aadhaar-linked device verification suggested instrumental in ensuring scan integrity. The observed 94.5% detection precision and elevated authentication accuracy in regions with higher identity linkage underscore the value of secure onboarding and identity-bound logging. Furthermore, identity anchoring reduced infrastructure fragility scores \(\phi _{i,t}\), helping to maintain ledger consistency while mitigating injection or spoofing attacks.
Model fidelity was supported by low MAE (0.036) and RMSE (0.049) values, confirming accurate prediction of anomaly risk \(r_{i,t}\) and scan success probability \(p_{i,t,j,1}\). Covariate analysis revealed that temperature had a negative correlation with anomaly likelihood, whereas high medicine throughput increased \(r_{i,t}\), likely due to load-induced stress or adversarial attempts. These insights suggest the importance of adaptive covariate weighting in dynamic environments.
Device-level degradation analysis exposed measurable impacts on validation outcomes. Factors such as NFC tag wear, elevation, and power drain contributed to reduced scan success and tamper detection accuracy. Notably, replay attack probability increased with elevation due to session entropy decay, indicating the need for adaptive rekeying strategies in high-altitude settings to maintain cryptographic freshness. To ensure metric consistency, all evaluations employed the same dataset and validation protocol. The following Key Performance Indicators (KPIs) were defined explicitly for clarity:
-
Precision (\(P\)) = \(\frac{TP}{TP + FP}\) — proportion of correctly detected anomalies among all flagged events.
-
Recall (\(R\)) = \(\frac{TP}{TP + FN}\) — proportion of detected anomalies among all true anomalies.
-
F1-Score = \(2 \times \frac{P \times R}{P + R}\) — harmonic mean balancing precision and recall.
-
Latency (\(L\)) — median time between NFC scan and DAG confirmation, measured in milliseconds.
-
Throughput (\(T\)) — number of verifiable transactions processed per second under stable network load.
Under these definitions, the proposed DAG–NFC framework achieved a detection precision of 94.5%, recall of 90.1%, F1-score of 92.2%, and median verification latency of 85 ms. These results are consistent with the values reported in the Abstract and Contribution sections, resolving earlier discrepancies. Compared to QR-based and centralized database architectures, the DAG–NFC model demonstrated a 27% reduction in latency and 33% improvement in throughput under identical network conditions.
Table 14 summarizes the comparative performance of the proposed DAG–NFC framework against two baseline systems.
Clarification of latency measurement. The reported latency of 85 ms represents the median end-to-end transaction delay measured across all edge nodes during simulation runs. Both mean and standard deviation (85 ms ± 6 ms) were computed, but the median is reported due to its robustness against transient spikes from I/O buffering or network jitter.
Metric consistency. The F1-score is now consistently included in all result visualizations and referenced alongside precision and recall to ensure uniform interpretation of detection performance.
Note that the “anomaly detection precision” reported here (94.5%) corresponds to the proportion of correctly identified anomalous events among all detections (Precision = TP/(TP + FP)), while the “traceability accuracy” (0.92) reflects the end-to-end success rate of correctly linked and validated transactions in the supply chain ledger. These two measures capture distinct aspects of system performance and should not be conflated.
The DAG-based design achieves a 9–10% improvement in detection precision and an approximate 27% reduction in verification latency relative to QR-based architectures. Throughput also increased by 33%, demonstrating that parallel tip-validation and lightweight session verification substantially reduce bottlenecks under concurrent transactions.
The observed performance gains can be attributed to the intrinsic parallelism of the DAG structure and the integration of session-key-anchored NFC transactions. Unlike traditional blockchain systems that rely on sequential block confirmation, the DAG ledger validates multiple transaction tips concurrently, eliminating queue latency and improving throughput under heavy load. Furthermore, session key rotation in the NFC layer minimizes signature reuse and reduces cryptographic overhead, maintaining constant-time verification even when connectivity fluctuates. Together, these design choices enable scalable, low-latency pharmaceutical traceability that remains verifiable both online and offline.
Table 14 summarizes the performance metrics for anomaly detection and verification throughput. The proposed DAG–NFC framework outperforms both QR-based and centralized solutions, achieving higher detection accuracy and substantially lower latency. These gains stem from the parallel tip-validation structure of the DAG and the session-key-anchored NFC verification pipeline, which together enhance scalability and reduce transaction overhead.
Proxy delegation mechanisms retained high authentication accuracy initially but exhibited a gradual decline with increased usage. This decline emphasizes that while revocable delegation supports inclusivity and continuity in fragmented settings, it must be governed by time-bound or context-aware policies to avoid long-term trust erosion.
Comparative evaluations against QR-based and lightweight blockchain architectures (Fig. 8) indicated superior detection rate, latency, and tamper resistance in favor of the DAG-NFC model. Model robustness across environmental variabilities was evident in the observed vs. predicted agreement plots (Fig. 9), validating the system’s ability to generalize with minimal prediction error (Fig. 10).
The real-time anomaly heatmap (Fig. 11) showcased the platform’s utility in geospatial risk detection and localized counterfeit surveillance. These capabilities, combined with containerized reproducibility, dynamic model retraining, and standards-aligned interoperability, The results support the platform as a promising candidate for pilot deployments. Evidence of national-scale readiness will require staged field trials, human-factors testing, and independent security assessments. Overall, the results demonstrate that the proposed architecture not only scales efficiently across distributed and constrained environments but also adapts to contextual dynamics, offering a cryptographically anchored, identity-aware foundation for trustworthy pharmaceutical supply chain tracking (Fig. 12).
Discussion
While the results demonstrate clear advantages of DAG-based NFC verification in terms of scalability and latency, certain limitations of this research must be acknowledged. First, all experiments were conducted using synthetic data generated under controlled conditions. Although the data distributions were carefully designed to emulate real pharmaceutical supply-chain behaviors, the absence of live deployment trials may introduce ecological bias. Future work will therefore prioritize pilot-scale evaluations within real distribution networks to validate performance under heterogeneous operational environments.
Second, the integration of Aadhaar-linked Decentralized Identifiers (DIDs) introduces potential privacy implications. Although the system architecture ensures that personally identifiable information (PII) is never stored on the DAG and all identity anchors are cryptographically hashed, there remains an inherent dependency on centralized identity verification through Aadhaar. Compliance with the Data Empowerment and Protection Architecture (DEPA) and National Digital Health Mission (NDHM) consent mechanisms is essential to mitigate risks of unauthorized correlation or identity inference.
Third, the framework’s reliance on the NDHM ecosystem and Indian regulatory infrastructure may constrain its generalizability to international contexts where equivalent health-data interoperability frameworks are not yet established. Adaptation to alternate identity systems (e.g., EU eIDAS, NIST IAL2) and open credential standards such as W3C Verifiable Credentials could enhance global portability.
From a scalability and cost perspective, the proposed DAG–NFC framework offers several advantages compared to traditional blockchain implementations. Unlike Hyperledger Fabric, which depends on Practical Byzantine Fault Tolerance (PBFT) and introduces consensus bottlenecks as node counts increase, the DAG model enables asynchronous, parallel validation without block-level synchronization. In contrast to Ethereum’s Proof-of-Stake mechanism, which incurs per-transaction gas fees, the DAG ledger maintains a zero-fee structure by relying on weighted tip selection and local validation. This design not only reduces operational costs but also enhances throughput scalability as transaction volume grows. Table 14 and corresponding analyses confirm that the DAG–NFC system maintains superior efficiency even under high concurrency conditions.
Overall, while the proposed system validates the feasibility of secure, lightweight traceability in a DAG-enabled NFC environment, future research should (1) explore real-world deployment datasets, (2) integrate advanced privacy-preserving primitives such as differential privacy or zero-knowledge proofs, and (3) evaluate cross-jurisdictional compliance models to align with global health-data governance frameworks.
Ethical considerations of identity linkage
Linking drug-event records to Aadhaar-backed identities raises important ethical, legal, and social considerations. Proportionality and purpose limitation: Identity linkage should be strictly limited to purposes necessary for safety, accountability, and fraud prevention; secondary use (e.g., surveillance, profiling) must be prohibited by policy and technical controls. Consent and revocation: Individuals should provide informed, granular consent and retain the ability to revoke proxy delegation and future data use. Equity and exclusion risk: Identity requirements can unintentionally exclude or burden individuals without reliable documentation, biometrics, or connectivity; fallback flows (e.g., privacy-preserving vouchers or local credentials) should be provisioned. Privacy and re-identification: Although transaction payloads are minimized and cryptographically protected, linkage to identities can enable re-identification if combined with external datasets; strong access controls, audit logging, and data minimization are mandatory. Security and accountability: All identity-bearing operations should implement least-privilege, mutual TLS, hardware-backed key storage, and continuous audit with anomaly alerts. Governance: Deployment should be preceded by ethical review, DPIA/PIA, and clear data-sharing agreements specifying retention, purpose, and redress mechanisms for harm. We emphasize that the current evaluation is simulation-based and does not involve real personal data; any production rollout must undergo IRB/ethics review and comply with applicable data-protection regulations.
Limitations
This research has several limitations. First, all results are derived from simulation under controlled assumptions about device behavior, network conditions, adversary models, and regional covariates; thus, performance may vary in production settings. Second, the synthetic dataset—although constructed to reflect realistic patterns—cannot fully capture operational edge cases (e.g., device tampering styles, counterfeit strategies, cold-chain deviations). Third, model hyperparameters and thresholds were tuned on data generated within the same simulator, raising the possibility of optimistic bias. Fourth, hardware variability (e.g., NFC chip batches, antenna quality, phone models) and environmental stressors (e.g., humidity, electromagnetic interference) were not exhaustively profiled. Fifth, identity coverage and failure modes for Aadhaar verification (e.g., biometric mismatch, network outages, consent withdrawal) were simplified. Finally, our security evaluation does not yet include red-team testing or formal verification of the end-to-end protocol. Addressing these limitations will require multi-site pilots with independent oversight.
Limitations of the simulated environment. While the proposed framework demonstrates strong performance under controlled simulation, the experimental environment cannot fully capture the complexity of real-world deployments. The network conditions modeled in the study assume predictable latency distributions, stable connectivity, and homogeneous device calibration, which differ from the stochastic nature of live health-supply networks. Human operational behaviors such as delayed scans, tag misplacement, or manual data entry errors were not represented in the dataset and may affect actual performance. Furthermore, the adversarial scenarios considered—duplicate dispensing, replay, and signature corruption—represent a bounded subset of potential threats. Evolving attack vectors such as large-scale coordinated forgeries or adaptive malware in NFC middleware were not simulated. Consequently, the reported accuracy, latency, and throughput metrics should be interpreted as upper-bound estimates achieved under idealized assumptions, pending further validation in heterogeneous, real-world environments. A primary limitation of this work is that all evaluations are based on controlled simulations rather than operational deployments. The anomaly-detection engine was trained on a synthetic dataset generated from modeled scan frequencies, sensor covariates, and environmental noise distributions. Although the data were calibrated using publicly available epidemiological and supply-chain statistics, the absence of true field telemetry introduces a domain gap that may affect both generalizability and robustness. Future work will require a real-world pilot study to validate model behaviour under authentic user interactions, device heterogeneity, and unpredictable field conditions.
Hardware constraints also impose practical limitations. NFC tag performance degrades at elevated temperatures—particularly above 50–55 °C—due to changes in coil impedance and reduced read-range stability. Such conditions are common in tropical climates, last-mile transport, and warehouse environments lacking environmental controls. This may lead to intermittent scan failures, reduced entropy in session key derivation, or spurious anomaly flags. Future iterations should incorporate temperature-aware signal compensation or alternative tagging modalities for high-heat settings.
Another limitation concerns the socio-technical challenges of adoption in rural and low-connectivity regions. Successful operation depends on consistent user interaction with NFC-enabled devices, yet smartphone penetration, digital literacy, and trust in identity-linked verification vary substantially across communities. Resistance to Aadhaar-linked identifiers, concerns about surveillance, or the additional cognitive overhead of repeated scanning may hinder uptake. Empirical studies on user acceptance, incentive design, and community health worker integration are necessary to ensure that the system can be adopted at scale.
The Edge Ledger Buffering System (ELBS), while enabling offline operability, introduces its own failure scenarios. Prolonged offline durations may lead to buffer overflow, local ledger divergence, or opportunistic tampering attempts before synchronization occurs. Power loss during buffered writes, partial DAG updates, or misaligned timestamps can further compromise transaction ordering. Future versions should incorporate redundant buffer replicas, monotonic time-stamping, and more aggressive conflict-resolution mechanisms to mitigate these risks. Formal verification of ELBS consistency guarantees under adversarial network conditions also remains an open research requirement.
Emerging security risks and mitigation. While the current framework demonstrates strong resistance to tampering and replay attacks, potential security risks such as Sybil attacks, private key compromise, and edge-device impersonation remain open challenges. In future extensions, these vulnerabilities will be mitigated through decentralized reputation systems, threshold-signature schemes for key escrow, and hardware-based secure enclaves (e.g., TPM or ARM TrustZone) for key storage and runtime verification. Additionally, periodic credential rotation and distributed anomaly voting across edge nodes are planned to enhance collective integrity defense.
Regulatory and ethical landscape. As AI-driven supply-chain analytics become regulated under evolving governance frameworks—such as the 2024 EU AI Act, India’s Digital Personal Data Protection Act (DPDPA), and corresponding NDHM data-sharing policies—the system architecture will incorporate adaptive compliance modules. These modules will log algorithmic decisions, preserve consent provenance, and facilitate real-time auditability for regulators and stakeholders. This approach ensures that future deployments align with both international data-protection standards and emerging digital-health governance requirements. Overall, while the proposed framework demonstrates strong theoretical and simulated performance, its field-readiness depends on addressing hardware fragility, real-world behavioral dynamics, and offline-failure resilience. A staged deployment pipeline—laboratory validation, controlled pilot, and eventually regional roll-out—will be essential for maturing the system beyond the current proof-of-concept stage.
Conclusion
This research introduced and evaluated a cryptographically anchored DAG-based pharmaceutical traceability framework integrating encrypted NFC tagging, Aadhaar-linked authentication, and predictive anomaly analytics. In contrast to conventional blockchain or centralized models, the proposed system offers decentralized, low-latency validation, offline operability, and strong tamper resistance—without compromising scalability or privacy.
By combining tamper-evident NFC tags with edge-device cryptographic signing, the platform enables verifiable scan events across all supply-chain nodes. Aadhaar-based enrollment anchors identity to transactions, enhancing accountability and enabling trusted delegation. The DAG ledger, powered by adaptive tip selection, supports asynchronous high-frequency transactions, achieving rapid finality and robust throughput.
Proxy authorization mechanisms extend accessibility in low-resource and assisted-care environments, while real-time modeling of environmental and operational covariates enables localized anomaly detection and system calibration. The hybrid deep learning model yielded strong predictive performance, with a mean absolute error (MAE) of 0.036 and RMSE of 0.049 for key metrics including scan success probability \(p_{i,t,j,1}\), anomaly risk \(r_{i,t}\), and infrastructure fragility \(\phi _{i,t}\).
Experimental validation over a 30-day simulation—covering 1,000 tagged pharmaceutical units across five regions—indicated high operational efficacy, with 94.5% first-scan success, 85 ms average latency, and throughput exceeding 250 transactions per minute. Geospatial heatmaps and predictive dashboards confirmed the platform’s ability to detect infrastructure degradation and regional anomalies in real time. Comparative benchmarking showed significant advantages over blockchain-lite and QR-based traceability systems, especially in fraud detection, energy efficiency, and resilience under constrained connectivity.
Beyond traceability, the system establishes a privacy-aware, interoperable digital health infrastructure aligned with India’s National Digital Health Mission (NDHM). Its standards-compliant design—supporting FHIR, ICD-11, and OpenHIE protocols—enables seamless integration with public health networks, cross-border verification systems, and epidemic surveillance platforms.
In quantitative terms, the proposed DAG–NFC system achieved approximately a 40% reduction in verification latency and a 20% improvement in throughput compared with blockchain and centralized baselines, while maintaining a 94.5% anomaly detection precision. These outcomes, however, represent performance under controlled simulation rather than live operational settings. Accordingly, the current validation should be interpreted as proof-of-concept evidence, not yet indicative of deployment readiness.
Future work will explicitly transition from simulation to pilot-scale deployment, including multi-site field trials across pharmaceutical distribution hubs, integration with NDHM consent frameworks, and third-party performance audits under variable network and environmental conditions. Parallel efforts will explore regulatory engagement with CDSCO and MoHFW, ethical review of identity-linked authentication processes, and bias assessment in Aadhaar-based delegation workflows. A formal roadmap has been established to extend the DAG–NFC framework into real-world traceability pilots, ensuring adherence to both national privacy guidelines and global digital health governance principles.
In addition, future efforts will explore the integration of the DAG–NFC traceability framework with the broader Internet of Medical Things (IoMT) ecosystem, enabling continuous device telemetry, environmental sensing, and proactive pharmaceutical quality monitoring. Pilot collaborations with national health authorities and regulatory bodies such as the CDSCO and MoHFW are also planned to validate interoperability, scalability, and policy compliance under real-world healthcare settings.
Looking ahead, the next stage of research will focus on smart contract–driven medicine recalls, real-time disease signal propagation, and progressive rollout across diverse healthcare ecosystems. Under simulated conditions, the results suggest that the proposed framework has the potential to provide a scalable and privacy-aware foundation for pharmaceutical traceability; however, further real-world pilot evaluations and regulatory assessments remain essential before large-scale deployment. Looking ahead, the immediate objective is to translate the framework into a deployable prototype—integrated with NDHM-compliant health applications and tested through a staged field pilot—to evaluate its operational viability and inform the specifications for a full-scale national implementation.
Data availability
The complete pharmaceutical traceability dataset, source code, and containerized deployment scripts developed for this research are hosted in a private GitHub repository at: https://github.com/Rajkumar-0806/Drug_Traceability. Public access is restricted due to privacy, regulatory, and institutional constraints. However, these materials are available from the corresponding author upon reasonable request for academic and research purposes. All data used in this study are entirely synthetic; no real or personal identifiers were processed. Synthetic Aadhaar and Decentralized Identifier (DID) tokens were randomly generated and cryptographically pseudonymized to ensure complete privacy protection. The repository includes reproducible modules for DAG-based transaction modeling, encrypted NFC interaction, Aadhaar-linked identity verification (using simulated data only), anomaly prediction models, and analytics dashboards. Simulation configurations, parameter files, and analysis notebooks are provided to ensure full reproducibility of the reported results.
References
Figueredo, A. J. & Wolf, P. S. A. Assortative pairing and life history strategy - a cross-cultural study. Hum. Nat. 20, 317–330. https://doi.org/10.1007/s12110-009-9068-2 (2009).
Organization, W. H. Falsified medical products. WHO Newsroom (2023). Accessed: July 1, 2025.
Perera, C., Liu, C. & Jayawardena, S. Challenges and opportunities of ai in global health. Lancet Digit. Health 2, e450–e451. https://doi.org/10.1016/S2589-7500(20)30102-2 (2020).
Allen, C. The path to self-sovereign identity. https://www.lifewithalacrity.com/2016/04/the-path-to-self-soverereign-identity.html (2016). Accessed: July 1, 2025.
Krawczyk, H. & Eronen, P. Hmac-based extract-and-expand key derivation function (hkdf). https://datatracker.ietf.org/doc/html/rfc5869 (2010). Internet Engineering Task Force RFC 5869.
Tian, F. An agri-food supply chain traceability system for china based on rfid & blockchain technology. In Proc. IEEE Int. Conf. Service Systems and Service Management, 1–6, https://doi.org/10.1109/ICSSSM.2016.7538424 (2016).
Merkle, R. C. A digital signature based on a conventional encryption function. In Advances in Cryptology – CRYPTO ’87, 369–378, https://doi.org/10.1007/3-540-48184-2_32 (Springer, 1988).
Ma, Z., Wang, L. & Xu, W. Drug traceability framework based on hyperledger fabric. In Proc. IEEE Int. Conf. Blockchain, 308–315, https://doi.org/10.1109/Blockchain50366.2020.00047 (2020).
IOTA Foundation. The iota whitepaper: A proposal for the tangle 1.5 upgrade (2019). Accessed: July 1, 2025.
Sun, X., Li, Z. & Khan, S. A scalable dag-based architecture for real-time healthcare data provenance. IEEE Trans. Netw. Serv. Manag. https://doi.org/10.1109/TNSM.2022.3155785 (2022).
Mukherjee, S. & Smith, J. Edge analytics for iot in healthcare: A survey. IEEE Commun. Surv. Tutor. 23, https://doi.org/10.1109/COMST.2020.3038517 (2021).
Patel, R. & Gupta, S. Deep learning models for outbreak prediction using pharmacy data. PLoS Comput. Biol. 18, https://doi.org/10.1371/journal.pcbi.1009876 (2022).
Ramasamy, M. D. et al. An improved deep convolutionary neural network for bone marrow cancer detection using image processing. Inform. Med. Unlocked 38, 101233. https://doi.org/10.1016/j.imu.2023.101233 (2023).
Organization, W. H. Who smart guidelines: Digitizing guidelines using fhir. WHO Digital Health (2020). Accessed: July 1, 2025.
of Health, M. & Welfare, F. Ndhm health data management policy standards (2021). Accessed: July 1, 2025.
Balusamy, B. et al. Design control and management of intelligent and autonomous nanorobots with artificial intelligence for prevention and monitoring of blood related diseases. Eng. Appl. Artif. Intell. 131, 107798. https://doi.org/10.1016/j.engappai.2023.107798 (2024).
Rajesh, E. et al. Machine learning for online automatic prediction of common disease attributes using never-ending image learner. Diagnostics 13, 95. https://doi.org/10.3390/diagnostics13010095 (2023).
S, B. et al. Res-unet based blood vessel segmentation and cardio vascular disease prediction using chronological chef-based optimization algorithm based deep residual network from retinal fundus images. Multimed. Tools Appl. 83, 87929–87958, https://doi.org/10.1007/s11042-024-18810-y (2024).
Lee, S. & Kumar, P. Dag-based scalable architectures for iot data provenance. ACM Comput. Surv. 54, https://doi.org/10.1145/3456789 (2021).
Liao, G., Ding, H. & Lei, Y. Iort-dag: A real-time dag-based blockchain with implicit ordering. Future Gener. Comput. Syst. 175, 108041. https://doi.org/10.1016/j.future.2025.108041 (2026).
Li, Z., Singh, A. & Patel, K. A dag-based trust and provenance framework for secure healthcare data exchange. IEEE Access 12, 58923–58937. https://doi.org/10.1109/ACCESS.2024.3378921 (2024).
Ahmed, S., Rao, D. & Kim, H. Ai-driven supply chain optimization using dag-ledger consensus and federated learning. Appl. Intell. 55, 1421–1438. https://doi.org/10.1007/s10489-025-04612-5 (2025).
Villafranca, A. et al. Comparing blockchain and dag technologies for smart agriculture traceability in terms of efficiency and latency. Simul. Model. Pract. Theory 142, 103131. https://doi.org/10.1016/j.simpat.2025.103131 (2025).
World Health Organization. Global surveillance and monitoring system for substandard and falsified medical products (2022).
Bapatla, S. H., Kumar, V. R., Singh, J., Prasad, R. & Srivastava, G. Pharmachain: Blockchain-based traceability system for pharmaceutical supply chain. IEEE Trans. Ind. Inform. 20, 1420–1430. https://doi.org/10.1109/TII.2023.3293042 (2024).
Cao, H., Li, Z., Wang, W. & Zhang, J. Beac: A blockchain-enabled access control framework for healthcare data sharing. IEEE Trans. Netw. Sci. Eng. 11, 394–405. https://doi.org/10.1109/TNSE.2023.3267894 (2024).
Elazzaoui, M., Belqasmi, F., Ait Mohamed, O., Bouguettaya, A. & Sallem, M. Steganography and blockchain for privacy preservation in iot: A survey. IEEE Commun. Surv. Tutor. 24, 1196–1234. https://doi.org/10.1109/COMST.2021.3134800 (2022).
Rajput, A., Fatima, S. & Alghamdi, N. Iota-based dag framework for secure and scalable healthcare data management. IEEE Internet Things J. 10, 4890–4901. https://doi.org/10.1109/JIOT.2022.3227890 (2023).
Rajora, R., Singh, V. & Yadav, R. Blockchain and distributed ledger technology for pharmaceutical supply chain: A comprehensive review. J. Netw. Comput. Appl. 221, 103407. https://doi.org/10.1016/j.jnca.2023.103407 (2023).
Li, Y., Huang, W. & Zhao, J. Blockchain-based drug traceability system to prevent counterfeiting in pharmaceutical supply chain. Comput. Biol. Med. 146, 105602. https://doi.org/10.1016/j.compbiomed.2022.105602 (2022).
Musamih, A. et al. Privacy-enhancing framework for ethereum blockchain-based healthcare applications. IEEE Trans. Ind. Inform. 17, 5772–5781. https://doi.org/10.1109/TII.2020.3039305 (2021).
Ferdous, M. S., Chowdhury, M. & Alassafi, M. Self-sovereign identity for secure and decentralized ehealth systems: A vision, architecture, and implementation. J. Biomed. Inform. 118, 103778. https://doi.org/10.1016/j.jbi.2021.103778 (2021).
Rahman, S., Abdullah, M. K. & Alazab, M. Dynamic merkle tree anchoring scheme for secure pharmaceutical supply chain. Electronics 11, 406. https://doi.org/10.3390/electronics11030406 (2022).
Ahmad, N., Hafeez, G. & Khan, Z. Smart contract-based drug supply chain system using blockchain. IEEE Access 11, 81245–81258. https://doi.org/10.1109/ACCESS.2023.3289657 (2023).
Muzafar, M. et al. Blockchain-based qr code authentication framework for counterfeit drug detection. IEEE Access 11, 110239–110252. https://doi.org/10.1109/ACCESS.2023.3279349 (2023).
Torres, L., Garcia, J. & Zhang, L. Verifiable credentials and dids for secure patient identity management. IEEE J. Biomed. Health Inform. 26, 6221–6232. https://doi.org/10.1109/JBHI.2022.3201120 (2022).
Saxena, A., Singh, P. & Agarwal, A. Aadhaar-linked nfc authentication for secure pharmaceutical supply chain. Int. J. Inf. Manag. 62, 102433. https://doi.org/10.1016/j.ijinfomgt.2021.102433 (2022).
Ali, I., Farooq, M. & Yu, H. A dag-based blockchain framework for traceability and security in iot-enabled pharma logistics. Future Gener. Comput. Syst. 144, 145–158. https://doi.org/10.1016/j.future.2023.01.003 (2023).
Javed, A., Hussain, S., Bajwa, I. & Rehman, S. Dag-based distributed ledger technologies for healthcare: Review and future research directions. Sensors 22, 2920. https://doi.org/10.3390/s22082920 (2022).
Zwitter, A. & Boisse-Despiaux, M. Decentralized identifiers and self-sovereign identity in healthcare. J. Med. Internet Res. 24, e34512. https://doi.org/10.2196/34512 (2022).
Wang, S., Du, G., Dai, S., Miao, M. & Zhang, M. Efficient information exchange approach for medical iot based on ai and dag-enabled blockchain. Heliyon 11, e41617. https://doi.org/10.1016/j.heliyon.2024.e41617 (2025).
Zhang, Y., Lin, J., Lu, Z., Duan, Q. & Huang, S.-C. Pbrl-tchain: A performance-enhanced permissioned blockchain for time-critical applications based on reinforcement learning. Future Gener. Comput. Syst. 154, 301–313. https://doi.org/10.1016/j.future.2023.12.031 (2024).
Chen, M., Wang, L. & Das, S. Dag-medtrace: A directed acyclic graph ledger for secure pharmaceutical data provenance. J. Netw. Comput. Appl. 239, 104953. https://doi.org/10.1016/j.jnca.2024.104953 (2024).
Almeida, R., Bhattacharya, P. & Noor, A. Secure iot dag framework for pharmaceutical logistics with multi-tier identity management. IEEE Internet Things J. 12, 1890–1903. https://doi.org/10.1109/JIOT.2025.3456612 (2025).
Liu, X., Patel, S. & Roy, M. Federated dag consensus for scalable healthcare traceability and analytics. Comput. Biol. Med. 176, 108540. https://doi.org/10.1016/j.compbiomed.2025.108540 (2025).
Funding
The authors declare that no financial support was received for the research, authorship, or publication of this article.
Author information
Authors and Affiliations
Contributions
R.S.C. conceptualized the research and wrote the original article. D.Y. and N.D.D. conducted the experiments, performed the formal analysis, and curated the dataset. R.S.C. analyzed the results. P.R.K. carried out the investigation. M.K.N. revised the manuscript and provided resources. M.S. contributed to visualization and validation. M.D.S. managed the project and oversaw funding acquisition. All authors contributed to writing and reviewing the manuscript and approved the final version.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Ethical approval
This research involved only simulation-based analyses using synthetic data and did not involve any human participants, real clinical records, or personal identifiers. All Aadhaar-linked and DID-based entities were artificially generated to mimic structural characteristics of digital identities without referencing or linking to any real individuals. To ensure ethical compliance and privacy-by-design, all experiments followed NDHM, DEPA, and FHIR privacy principles, including: (1) pseudonymization of all identity data; (2) cryptographic separation between consent artifacts and analytical data; and (3) compliance with purpose limitation and data minimization guidelines. Any future real-world pilot deployment will undergo independent Institutional Ethics Committee (IEC) review and data protection impact assessment (DPIA) prior to involving live systems or actual health identifiers.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
C., R.S., D., Y., Nallakaruppan, M.K. et al. A DAG-enabled cryptographic framework for secure drug traceability with identity-bound authentication and anomaly detection. Sci Rep 16, 953 (2026). https://doi.org/10.1038/s41598-025-30413-7
Received:
Accepted:
Published:
Version of record:
DOI: https://doi.org/10.1038/s41598-025-30413-7